- Table of Contents
-
- 10-Security Configuration Guide
- 00-Preface
- 01-AAA configuration
- 02-802.1X configuration
- 03-MAC authentication configuration
- 04-Portal configuration
- 05-Port security configuration
- 06-Password control configuration
- 07-Public key management
- 08-SSL configuration
- 09-PKI configuration
- 10-IPsec configuration
- 11-SSH configuration
- 12-IP source guard configuration
- 13-ARP attack protection configuration
- 14-uRPF configuration
- 15-FIPS configuration
- 16-Attack detection and prevention configuration
- 17-MACsec configuration
- 18-MFF configuration
- 19-ND attack defense configuration
- 20-Keychain configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 17-MACsec configuration | 167.25 KB |
Feature and hardware compatibility
General restrictions and guidelines
MACsec configuration task list
Configuring the MKA key server priority·
Configuring MACsec protection parameters in interface view
Configuring the MACsec confidentiality offset
Configuring MACsec replay protection
Configuring the MACsec validation mode
Configuring MACsec protection parameters by MKA policy
Displaying and maintaining MACsec
Device-oriented MACsec configuration example
Configuring MACsec
Overview
Media Access Control Security (MACsec) secures data communication on IEEE 802 LANs. MACsec provides services such as data encryption, frame integrity check, and data origin validation for frames on the MAC sublayer of the Data Link Layer.
Basic concepts
CA
Secure connectivity association (CA) is a group of CA participants that use the same key and key algorithm. The encryption key used by CA participant is called connectivity association key (CAK). CAK has the following types:
· Pairwise CAK—Used by CAs that have two participants.
· Group CAK—Used by CAs that have more than two participants.
The pairwise CAK is used most often because MACsec is typically applied to point-to-point networks.
A CAK can be an encryption key generated during 802.1X authentication or a user-configured preshared key. The user-configured preshared key takes precedence over the 802.1X-generated key. In the current software version, the device does not support the 802.1X-generated key for MACsec.
SA
Secure association (SA) is an agreement negotiated by CA participants. The agreement includes a cipher suite and keys for integrity check.
A secure channel can contain more than one SA. Each SA uses a unique secure association key (SAK). The SAK is generated from the CAK, and MACsec uses the SAK to encrypt data transmitted along the secure channel.
MACsec Key Agreement (MKA) limits the number of packets that can be encrypted by an SAK. When the limit is exceeded, the SAK will be refreshed. For example, when packets with the minimum size are sent on a 10-Gbps link, an SAK rekey occurs about every 300 seconds.
MACsec services
MACsec provides the following services:
· Data encryption—Enables a port to encrypt outbound frames and decrypt MACsec-encrypted inbound frames.
· Integrity check—Performs integrity check when the device receives a MACsec-encrypted frame. The integrity check uses the following process:
a. Uses a key negotiated by MKA to calculate an integrity check value (ICV) for the frame.
b. Compares the calculated ICV with the ICV in the frame trailer.
- If the ICVs are the same, the device verifies the frame as legal.
- If the ICVs are different, the device determines whether to drop the frame based on the validation mode.
· MACsec replay protection—When MACsec frames are transmitted over the network, frame re-sequencing might occur. MACsec replay protection allows the device to accept the out-of-order packets within the replay protection window size and drop other out-of-order packets.
MACsec applications
MACsec supports the following application modes:
· Client-oriented mode—Operates with 802.1X authentication and secures data transmission between the client and the access device. In this mode, the authentication server generates and distributes the CAK to the client and the access device.
Figure 1 Client-oriented mode
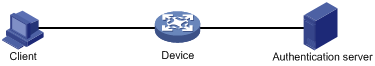
|
|
NOTE: · In client-oriented mode, an MKA-enabled port on the access device must perform port-based 802.1X access control. The authentication method must be EAP relay. · In the current software version, the device does not support the client-oriented mode. |
· Device-oriented mode—Secures data transmission between devices. In this mode, the devices do not perform identity authentication, and the same preshared key must be configured on the MACsec ports that connect the devices. The devices use the configured preshared key as the CAK.
Figure 2 Device-oriented mode

MACsec operating mechanism
Operating mechanism for client-oriented mode
Figure 3 illustrates how MACsec operates in client-oriented mode.
|
|
NOTE: In the current software version, the device does not support the operating mechanism in client-oriented mode. |
Figure 3 MACsec interactive process in client-oriented mode
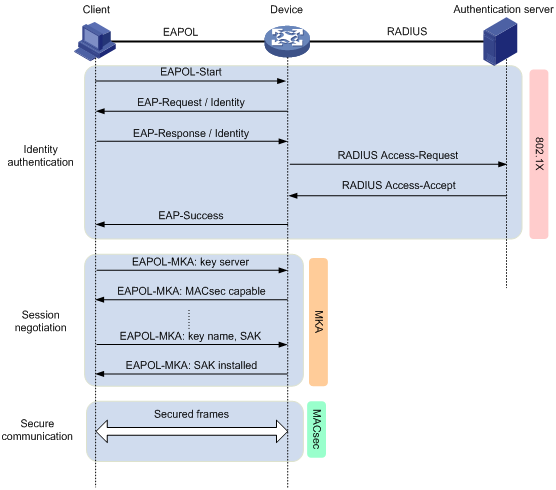
The following shows the MACsec process:
1. After the client passes 802.1X authentication, the RADIUS server distributes the generated CAK to the client and the access device.
2. After receiving the CAK, the client and the access device exchange EAPOL-MKA packets.
The client and the access device exchange the MACsec capability and required parameters for session establishment. The parameters include MKA key server priority and MACsec desire.
During the negotiation process, the access device automatically becomes the key server. The key server generates an SAK from the CAK for packet encryption, and it distributes the SAK to the client.
3. The client and the access device use the SAK to encrypt packets, and they send and receive the encrypted packets in secure channels.
4. When the access device receives a logoff request from the client, it immediately removes the associated secure session from the port. The remove operation prevents an unauthorized client from using the secure session established by the previous authorized client to access the network.
The MKA protocol also defines a session keepalive timer. If one participant does not receive any MKA packets from the peer after the timer expires, the participant removes the established secure session. The keepalive time is 6 seconds.
Operating mechanism for device-oriented mode
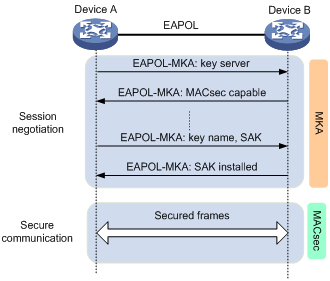
As shown in Figure 4, the devices use the configured preshared keys to start the session negotiation.
In this mode, the session negotiation, secure communication, and session termination processes are the same as the processes in client-oriented mode. However, MACsec performs a key server selection in this mode. The port with higher MKA key server priority becomes the key server, which is responsible for the generation and distribution of SAKs.
Figure 4 MACsec interactive process in device-oriented mode
Protocols and standards
· IEEE 802.1X-2010, Port-Based Network Access Control
· IEEE 802.1X-2006, Media Access Control (MAC) Security
Feature and hardware compatibility
MACsec is supported only on the following ports:
· Ports that are numbered from 1 to 8 on the following modules:
¡ LSUM2GP24TSSE0.
¡ LSUM2GP44TSSE0.
¡ LSUM2GT24PTSSE0.
¡ LSUM2GT24TSSE0.
¡ LSUM2GT48SE0.
¡ LSUM2GV48SE0.
· Ports that are numbered from 1 to 4 on the LSUM1TGS48SG0 module.
· Ports that are numbered from 45 to 48 on the LSUM1GP44TSEC0 module.
General restrictions and guidelines
When you configure MACsec, follow these restrictions and guidelines:
· In device-oriented mode, the MACsec configuration takes effect on Layer 2 and Layer 3 Ethernet ports.
· MACsec is not supported on an aggregate interface, but it is supported on the member ports of the aggregate interface.
· The MACsec header occupies 38 bytes in each frame. Please take into consideration the header when you plan the network capacity.
MACsec configuration task list
|
Tasks at a glance |
|
(Required.) Enabling MKA |
|
(Optional.) Enabling MACsec desire |
|
(Required.) Configuring a preshared key |
|
(Optional.) Configuring the MKA key server priority |
|
(Optional.) Use one of the following methods to configure MACsec protection parameters: · Configuring MACsec protection parameters in interface view: ¡ Configuring the MACsec confidentiality offset ¡ Configuring MACsec replay protection ¡ Configuring the MACsec validation mode |
Enabling MKA
MKA establishes and manages MACsec secure channels on a port. It also negotiates keys used by MACsec.
You cannot enable MKA on a MACsec-incapable port.
To enable MKA:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter interface view. |
N/A |
|
|
3. Enable MKA. |
By default, MKA is disabled on the port. |
Enabling MACsec desire
The MACsec desire feature expects MACsec protection for outbound frames. The key server determines whether MACsec protects the outbound frames.
MACsec protects the outbound frames of a port when the following requirements are met:
· The key server is MACsec capable.
· Both the local participant and its peer are MACsec capable.
· A minimum of one participant is enabled with MACsec desire.
To enable MACsec desire:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter interface view. |
interface interface-type interface-number |
N/A |
|
3. Enable MACsec desire. |
By default, the port does not expect MACsec protection for outbound frames. |
Configuring a preshared key
In device-oriented mode, configure a preshared key as the CAK to be used during MKA negotiation. To successfully establish an MKA session between two devices, make sure the connected MACsec ports are configured with the same preshared key.
To configure a preshared key:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter interface view. |
interface interface-type interface-number |
N/A |
|
3. Configure a preshared key. |
By default, no MKA preshared key exists on the port. |
Configuring the MKA key server priority
Configure an MKA key server priority for key server selection. The lower the priority value, the higher the priority.
In device-oriented mode, the port that has higher priority becomes the key server. If a port and its peers have the same priority, MACsec compares the SCI values on the ports. The port with the lowest SCI value (a combination of MAC address and port ID) becomes the key server.
A port with priority 255 cannot become the key server. For a successful key server selection, make sure a minimum of one participant's key server priority is not 255.
To configure the MKA key server priority:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter interface view. |
interface interface-type interface-number |
N/A |
|
3. Configure the MKA key server priority. |
The default setting is 0. |
Configuring MACsec protection parameters in interface view
If you configure a parameter in interface view after applying an MKA policy, the configuration in interface view overwrites the configuration of the parameter in the MKA policy. Your configuration also removes the MKA policy application from the port. However, other parameter settings of the MKA policy are effective on the port.
If the parameter value in interface view is the same as the value in the MKA policy, your configuration does not take effect. The policy remains active on the port.
Configuring the MACsec confidentiality offset
The MACsec confidentiality offset specifies the number of bytes starting from the frame header. MACsec encrypts only the bytes after the offset in a frame.
MACsec uses the confidentiality offset propagated by the key server.
To configure the MACsec confidentiality offset:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter interface view. |
interface interface-type interface-number |
N/A |
|
3. Configure the MACsec confidentiality offset. |
The default setting is 0, and the entire frame needs to be encrypted. The offset value can be 0, 30, or 50. |
Configuring MACsec replay protection
The MACsec replay protection feature allows a MACsec port to accept a number of out-of-order or repeated inbound frames. The configured replay protection window size is effective only when MACsec replay protection is enabled.
To configure MACsec replay protection:
|
Step |
Command |
Remarks |
|
system-view |
N/A |
|
|
interface interface-type interface-number |
N/A |
|
|
By default, MACsec replay protection is enabled on the port. |
||
|
4. Configure the MACsec replay protection window size. |
The default setting is 0, and frames are accepted only in the correct order. |
Configuring the MACsec validation mode
The MACsec validation allows a port to perform integrity check based on the following validation modes:
· check—Performs validation only, and does not drop illegal frames.
· strict—Performs validation, and drops illegal frames.
To avoid data loss, use the default validation mode check on the MACsec devices in case of MKA negotiation failure. After you use the display macsec command to verify that MKA negotiation has succeeded, change the validation mode to strict.
To configure the MACsec validation mode:
|
Step |
Command |
Remarks |
|
system-view |
N/A |
|
|
interface interface-type interface-number |
N/A |
|
|
The default setting is check. If you execute this command multiple times, the most recent configuration takes effect. |
Configuring MACsec protection parameters by MKA policy
Configuring an MKA policy
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Create an MKA policy, and enter MKA policy view. |
By default, an MKA policy named default-policy exists. The settings for parameters in the default policy are the same as the default settings for the parameters on a port. You cannot delete or modify the default MKA policy. You can create multiple MKA policies. |
|
|
3. (Optional.) Configure the MACsec confidentiality offset. |
macsec confidentiality-offset offset-value |
The default setting is 0. MACsec uses the confidentiality offset propagated by the key server. |
|
4. (Optional.) Configure MACsec replay protection. |
a. Enable MACsec replay protection: b. Configure the replay protection window size: |
By default, MACsec replay protection is enabled. The default replay protection window size is 0. Frames are accepted only in the correct order. |
|
5. Configure the MACsec validation mode. |
macsec validation mode { check | strict } |
The default setting is check. |
Applying an MKA policy
MKA policy provides a centralized method to configure MACsec confidentiality offset, replay protection, and validation mode. An MKA policy can be applied to a port or multiple ports. When you apply an MKA policy to a port, follow these restrictions and guidelines:
· The MACsec parameter settings configured in the MKA policy overwrite the MACsec parameters previously configured on the port.
· Any modifications to the MKA policy take effect immediately.
· When you remove an MKA policy application from the port, the MACsec parameter settings on the port restore to the default.
· When you apply a nonexistent MKA policy to the port, the port automatically uses the default MKA policy. If you create the policy, the policy will be automatically applied to the port.
To apply an MKA policy to a port:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter interface view. |
interface interface-type interface-number |
N/A |
|
3. Apply an MKA policy. |
By default, no MKA policy is applied to the port. |
Displaying and maintaining MACsec
Execute display commands in any view and reset commands in user view.
|
Task |
Command |
|
Display MACsec information on ports. |
display macsec [ interface interface-type interface-number ] [ verbose ] |
|
Display MKA session information. |
display mka session [ interface interface-type interface-number | local-sci sci-id ] [ verbose ] |
|
Display MKA policy information. |
display mka { default-policy | policy [ name policy-name ] } |
|
Display MKA statistics on ports. |
display mka statistics [ interface interface-type interface-number ] |
|
Reset MKA sessions on ports. |
reset mka session [ interface interface-type interface-number ] |
|
Clear MKA statistics on ports. |
reset mka statistics [ interface interface-type interface-number ] |
Device-oriented MACsec configuration example
Network requirements
As shown in Figure 5, Device A is the MACsec key server.
To secure data transmission between the two devices by MACsec, perform the following tasks on Device A and Device B, respectively:
· Set the MACsec confidentiality offset to 30 bytes.
· Enable MACsec replay protection, and set the replay protection window size to 100.
· Set the MACsec validation mode to strict.
· Configure the CAK name (CKN) and the CAK as E9AC and 09DB3EF1, respectively.

Configuration procedure
1. Configure Device A:
# Enter system view.
<DeviceA> system-view
# Enter GigabitEthernet 1/0/1 interface view.
[DeviceA] interface gigabitethernet 1/0/1
# Enable MACsec desire on GigabitEthernet 1/0/1.
[DeviceA-GigabitEthernet1/0/1] macsec desire
# Set the MKA key server priority to 5.
[DeviceA-GigabitEthernet1/0/1] mka priority 5
# Configure the CKN as E9AC and the CAK as 09DB3EF1 in plain text.
[DeviceA-GigabitEthernet1/0/1] mka psk ckn E9AC cak simple 09DB3EF1
# Set the MACsec confidentiality offset to 30 bytes.
[DeviceA-GigabitEthernet1/0/1] macsec confidentiality-offset 30
# Enable MACsec replay protection.
[DeviceA-GigabitEthernet1/0/1] macsec replay-protection enable
# Set the MACsec replay protection window size to 100.
[DeviceA-GigabitEthernet1/0/1] macsec replay-protection window-size 100
# Set the MACsec validation mode to strict.
[DeviceA-GigabitEthernet1/0/1] macsec validation mode strict
# Enable MKA on GigabitEthernet 1/0/1.
[DeviceA-GigabitEthernet1/0/1] mka enable
[DeviceA-GigabitEthernet1/0/1] quit
2. Configure Device B:
<DeviceB> system-view
# Enter GigabitEthernet 1/0/1 interface view.
[DeviceB] interface gigabitethernet 1/0/1
# Enable MACsec desire on GigabitEthernet 1/0/1.
[DeviceB-GigabitEthernet1/0/1] macsec desire
# Set the MKA key server priority to 10.
[DeviceB-GigabitEthernet1/0/1] mka priority 10
# Configure the CKN as E9AC and the CAK as 09DB3EF1 in plain text.
[DeviceB-GigabitEthernet1/0/1] mka psk ckn E9AC cak simple 09DB3EF1
# Set the MACsec confidentiality offset to 30 bytes.
[DeviceB-GigabitEthernet1/0/1] macsec confidentiality-offset 30
# Enable MACsec replay protection.
[DeviceB-GigabitEthernet1/0/1] macsec replay-protection enable
# Set the MACsec replay protection window size to 100.
[DeviceB-GigabitEthernet1/0/1] macsec replay-protection window-size 100
# Set the MACsec validation mode to strict.
[DeviceB-GigabitEthernet1/0/1] macsec validation mode strict
# Enable MKA on GigabitEthernet 1/0/1.
[DeviceB-GigabitEthernet1/0/1] mka enable
[DeviceB-GigabitEthernet1/0/1] quit
Verifying the configuration
# Display MACsec information on GigabitEthernet 1/0/1 of Device A.
[DeviceA] display macsec interface gigabitethernet 1/0/1 verbose
Interface GigabitEthernet1/0/1
Protect frames : Yes
Replay protection : Enabled
Replay window size : 100 frames
Confidentiality offset : 30 bytes
Validation mode : Strict
Included SCI : No
SCI conflict : No
Cipher suite : GCM-AES-128
Transmit secure channel:
SCI : 00E00100000A0006
Elapsed time: 00h:05m:00s
Current SA : AN 0 PN 1
Receive secure channels:
SCI : 00E0020000000106
Elapsed time: 00h:03m:18s
Current SA : AN 0 LPN 1
Previous SA : AN N/A LPN N/A
# Display MKA session information on GigabitEthernet 1/0/1 of Device A.
[DeviceA] display mka session interface gigabitethernet 1/0/1 verbose
Interface GigabitEthernet1/0/1
Tx-SCI : 00E00100000A0006
Priority : 5
Capability: 3
CKN for participant: E9AC
Key server : Yes
MI (MN) : 85E004AF49934720AC5131D3 (182)
Live peers : 1
Potential peers : 0
Principal actor : Yes
MKA session status : Secured
Confidentiality offset: 30 bytes
Current SAK status : Rx & Tx
Current SAK AN : 0
Current SAK KI (KN) : 85E004AF49934720AC5131D300000003 (3)
Previous SAK status : N/A
Previous SAK AN : N/A
Previous SAK KI (KN) : N/A
Live peer list:
MI MN Priority Capability Rx-SCI
12A1677D59DD211AE86A0128 182 10 3 00E0020000000106
# Display MACsec information on GigabitEthernet 1/0/1 of Device B.
[DeviceB] display macsec interface gigabitethernet 1/0/1 verbose
Interface GigabitEthernet1/0/1
Protect frames : Yes
Replay protection : Enabled
Replay window size : 100 frames
Confidentiality offset : 30 bytes
Validation mode : Strict
Included SCI : No
SCI conflict : No
Cipher suite : GCM-AES-128
Transmit secure channel:
SCI : 00E0020000000106
Elapsed time: 00h:05m:36s
Current SA : AN 0 PN 1
Receive secure channels:
SCI : 00E00100000A0006
Elapsed time: 00h:03m:21s
Current SA : AN 0 LPN 1
Previous SA : AN N/A LPN N/A
# Display MKA session information on GigabitEthernet 1/0/1 of Device B.
[DeviceB] display mka session interface gigabitethernet 1/0/1 verbose
Interface GigabitEthernet1/0/1
Tx-SCI : 00E0020000000106
Priority : 10
Capability: 3
CKN for participant: E9AC
Key server : No
MI (MN) : 12A1677D59DD211AE86A0128 (1219)
Live peers : 1
Potential peers : 0
Principal actor : Yes
MKA session status : Secured
Confidentiality offset: 30 bytes
Current SAK status : Rx & Tx
Current SAK AN : 0
Current SAK KI (KN) : 85E004AF49934720AC5131D300000003 (3)
Previous SAK status : N/A
Previous SAK AN : N/A
Previous SAK KI (KN) : N/A
Live peer list:
MI MN Priority Capability Rx-SCI
85E004AF49934720AC5131D3 1216 5 3 00E00100000A0006
Troubleshooting MACsec
Symptom
The devices cannot establish MKA sessions when the following conditions exist:
· The link connecting the devices is up.
· The ports at the ends of the link are MACsec capable.
Analysis
The symptom might occur for the following reasons:
· The ports at the link are not enabled with MKA.
· A port at the link is not configured with a preshared key or configured with a preshared key different from the peer.
Solution
To resolve the problem:
1. Enter interface view.
2. Use the display this command to check the MACsec configuration:
¡ If MKA is not enabled on the port, execute the mka enable command.
¡ If a preshared key is not configured or the preshared key is different from the peer, use the mka psk command to configure a preshared key. Make sure the preshared key is the same as the preshared key on the peer.
3. If the problem persists, contact H3C Support.

