- Table of Contents
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 19-MAC Address Authentication Operation | 87.1 KB |
Table of Contents
1 MAC Authentication Configuration
Performing MAC Authentication on a RADIUS Server
Performing MAC Authentication Locally
Configuring Basic MAC Authentication Functions
MAC Address Authentication Enhanced Function Configuration
MAC Address Authentication Enhanced Function Configuration Tasks
Configuring a Guest VLAN or Auth-Fail VLAN
Configuring the Maximum Number of MAC Address Authentication Users Allowed to Access a Port
Configuring the Quiet MAC Function on a Port
Displaying and Debugging MAC Authentication
MAC Authentication Configuration Example
MAC Authentication Overview
MAC authentication provides a way for authenticating users based on ports and MAC addresses, without requiring any client software to be installed on the hosts. Once detecting a new MAC address, it initiates the authentication process. During authentication, the user does not need to enter username or password manually.
For S3100 Series Ethernet switches, MAC authentication can be implemented locally or on a RADIUS server.
After determining the authentication method, users can select one of the following types of user name as required:
l MAC address mode, where the MAC address of a user serves as both the user name and the password.
l Fixed mode, where user names and passwords are configured on a switch in advance. In this case, the user name, the password, and the limits on the total number of user names are the matching criterion for successful authentication. For details, refer to AAA of this manual for information about local user attributes.
Performing MAC Authentication on a RADIUS Server
When authentications are performed on a RADIUS server, the switch serves as a RADIUS client and completes MAC authentication in combination of the RADIUS server.
l In MAC address mode, the switch sends the MAC addresses detected to the RADIUS server as both the user names and passwords.
l In fixed mode, the switch sends the user name and password previously configured for the user to the RADIUS server for authentication.
The RADIUS authentication process is the same as that of the 802.1x PAP authentication method. For details, refer to 802.1x and System-Guard Operation.
A user can access a network upon passing the authentication performed by the RADIUS server.
Performing MAC Authentication Locally
When authentications are performed locally, users are authenticated by switches. In this case,
l In MAC address mode, the local user name to be configured is the MAC address of an access user. Hyphens must or must not be included depending on the format configured with the mac-authentication authmode usernameasmacaddress usernameformat command; otherwise, the authentication will fail.
l In fixed mode, all users’ MAC addresses are automatically mapped to the configured local passwords and usernames.
l The service type of a local user needs to be configured as lan-access.
Related Concepts
MAC Authentication Timers
The following timers function in the process of MAC authentication:
l Offline detect timer: At this interval, the switch checks to see whether an online user has gone offline. Once detecting that a user becomes offline, the switch sends a stop-accounting notice to the RADIUS server.
l Quiet timer: Whenever a user fails MAC authentication, the switch does not initiate any MAC authentication of the user during a period defined by this timer.
l Server timeout timer: During authentication of a user, if the switch receives no response from the RADIUS server in this period, it assumes that its connection to the RADIUS server has timed out and forbids the user from accessing the network.
Quiet MAC Address
When a user fails MAC authentication, the MAC address becomes a quiet MAC address, which means that any packets from the MAC address will be discarded simply by the switch until the quiet timer expires. This prevents an invalid user from being authenticated repeatedly in a short time.
![]()
l If the quiet MAC is the same as the static MAC configured or an authentication-passed MAC, then the quiet function is not effective.
l The S3100 series Ethernet switches support quiet MAC function on ports.
Configuring Basic MAC Authentication Functions
Table 1-1 Configure basic MAC authentication functions
|
Operation |
Command |
Remarks |
||
|
Enter system view |
system-view |
— |
||
|
Enable MAC authentication globally |
mac-authentication |
Required Disabled by default |
||
|
Enable MAC authentication for the specified port(s) or the current port |
In system view |
mac-authentication interface interface-list |
Use either method Disabled by default |
|
|
In interface view |
interface interface-type interface-number |
|||
|
mac-authentication |
||||
|
quit |
||||
|
Set the user name in MAC address mode for MAC authentication |
mac-authentication authmode usernameasmacaddress [ usernameformat { with-hyphen | without-hyphen } { lowercase | uppercase } | fixedpassword password ] |
Optional By default, the MAC address of a user is used as the user name. |
||
|
Set the user name in fixed mode for MAC authentication |
Set the user name in fixed mode for MAC authentication |
mac-authentication authmode usernamefixed |
Optional By default, the user name is “mac” and no password is configured. |
|
|
Configure the user name |
mac-authentication authusername username |
|||
|
Configure the password |
mac-authentication authpassword password |
|||
|
Specify an ISP domain for MAC authentication |
mac-authentication domain isp-name |
Required By default, no ISP domain is specified and the default domain is used. |
||
|
Configure the MAC authentication timers |
mac-authentication timer { offline-detect offline-detect-value | quiet quiet-value | server-timeout server-timeout-value } |
Optional The default timeout values are as follows: 300 seconds for offline detect timer; 60 seconds for quiet timer; and 100 seconds for server timeout timer |
||
|
Enter Ethernet interface view |
interface interface-type interface-number |
— |
||
|
Set the offline detect timer for MAC authentication on the Ethernet port view |
mac-authentication timer offline-detect offline-detect-value |
Optional 300 seconds for offline detect timer by default |
||
![]()
l If MAC authentication is enabled on a port, you cannot configure the maximum number of dynamic MAC address entries for that port (through the mac-address max-mac-count command), and vice versa.
l If MAC authentication is enabled on a port, you cannot configure port security (through the port-security enable command) on that port, and vice versa.
l You can configure MAC authentication on a port before enabling it globally. However, the configuration will not take effect unless MAC authentication is enabled globally.
l The offline detect timer configured in system view applies to all MAC authentication-enabled ports.
l The offline detect timer configured in Ethernet port view applies to the current port only. You can set the offline detect timer to different values on different Ethernet ports.
l The offline detect timer configured in Ethernet port view takes precedence over the one configured in system view.
MAC Address Authentication Enhanced Function Configuration
MAC Address Authentication Enhanced Function Configuration Tasks
Table 1-2 MAC address authentication enhanced function configuration tasks
|
Operation |
Description |
Related section |
|
Configure a guest VLAN or Auth-Fail VLAN |
Optional |
|
|
Configure the maximum number of MAC address authentication users allowed to access a port |
Optional |
Section “Configuring the Maximum Number of MAC Address Authentication Users Allowed to Access a Port” |
|
Configuring quiet MAC function on a port |
Optional |
Configuring a Guest VLAN or Auth-Fail VLAN
![]()
l Different from guest VLANs or Auth-Fail VLANs described in the 802.1x and System-Guard manual. Guest VLANs or Auth-Fail VLANs mentioned in this section refer to guests VLANs or Auth-Fail VLANs dedicated to MAC address authentication.
l The guest VLAN and Auth-Fail VLAN for MAC authentication are VLANs for users failing MAC authentication to access for certain resources.
l At present, among the S3100 series Ethernet switches, only the S3100-EI series supports the Auth-Fail VLAN function for MAC authentication.
After completing configuration tasks in Configuring Basic MAC Authentication Functions for a switch, this switch can authenticate access users according to their MAC addresses or according to fixed user names and passwords. The switch will not learn MAC addresses of the clients failing in the authentication into its local MAC address table, thus prevent illegal users from accessing the network.
In some cases, if the clients failing in the authentication are required to access some resources in the network (such as the virus library update server), you can use the guest VLAN or Auth-Fail VLAN.
A guest VLAN/Auth-Fail VLAN for MAC authentication can be a port-based guest VLAN/Auth-Fail VLAN (PGV/PAFV) or MAC-based guest VLAN/Auth-Fail VLAN (MGV/MAFV), depending on the VLAN assignment mode.
l PGV/PAFV: If a user fails MAC authentication on a port configured with a PGV/PAFV, the device will add the port to the guest VLAN or Auth-Fail VLAN, and then all users on the port can access the resources in the guest VLAN or Auth-Fail VLAN.
l MGV/MAFV: For the MGV/MAFV configured on a port to take effect, the MAC VLAN function must also be enabled. If a user fails MAC authentication on the port, the device will bind the MAC address of the user with the guest VLAN/Auth-Fail VLAN, and thus the user can access resources in only the guest VLAN or Auth-Fail VLAN.
![]()
In PGV or PAFV mode, when a user fails MAC authentication on a port, the device adds the port to the guest VLAN or Auth-Fail VLAN. Therefore, the guest VLAN can separate unauthenticated users on an access port. When it comes to a trunk port or a hybrid port, if a packet itself carries a VLAN tag and the VLAN is allowed on the port, the port will forward the packet according to the VLAN tag, regardless of the guest VLAN or Auth-Fail VLAN. That is, packets can be forwarded to the VLANs other than the guest VLAN or Auth-Fail VLAN through the Trunk or Hybrid port, even if users fail to pass authentication.
Table 1-3 Configure a guest VLAN or Auth-Fail VLAN
|
Operation |
Command |
Description |
|
Enter system view |
system-view |
— |
|
Enter Ethernet port view |
interface interface-type interface-number |
— |
|
Configure the guest VLAN for MAC authentication |
mac-authentication guest-vlan vlan-id |
Required Not configured by default. |
|
Configure the Auth-Fail VLAN for MAC authentication |
mac-authentication auth-fail vlan authfail-vlan-id |
Optional Not configured by default. |
|
Return to system view |
quit |
— |
|
Configure the interval at which the switch re-authenticates users in guest VLANs |
mac-authentication timer guest-vlan-reauth interval |
Optional By default, the switch re-authenticates the users in guest VLANs at the interval of 30 seconds by default. |
![]()
l The Auth-Fail VLAN for MAC authentication takes precedence over the guest VLAN for MAC authentication. When both of them are configured on a user access port and they are different VLANs, a user failing MAC authentication on the port will be added to the Auth-Fail VLAN, that is, the user is authorized to access resources in the Auth-Fail VLAN.
l The undo vlan command cannot be used to remove the VLAN configured as a guest VLAN. If you want to remove this VLAN, you must remove the guest VLAN configuration for it first. Refer to the VLAN module in this manual for the description on the undo vlan command.
l Only one guest VLAN can be configured for a port, and the VLAN configured as the guest VLAN must be an existing VLAN. Otherwise, the guest VLAN configuration does not take effect. If you want to change the guest VLAN for a port, you must remove the current guest VLAN and then configure a new guest VLAN for this port.
Configuring the Maximum Number of MAC Address Authentication Users Allowed to Access a Port
You can configure the maximum number of MAC address authentication users for a port in order to control the maximum number of users accessing a port. After the number of access users has exceeded the configured maximum number, the switch will not trigger MAC address authentication for subsequent access users, and thus these subsequent access users cannot access the network normally.
Table 1-4 Configure the maximum number of MAC address authentication users allowed to access a port
|
Operation |
Command |
Description |
|
Enter system view |
system-view |
— |
|
Enter Ethernet port view |
interface interface-type interface-number |
— |
|
Configure the maximum number of MAC address authentication users allowed to access a port |
mac-authentication max-auth-num user-number |
Required By default, the maximum number of MAC address authentication users allowed to access a port is 256. |
![]()
l If both the limit on the number of MAC address authentication users and the limit on the number of users configured in the port security function are configured for a port, the smaller value of the two configured limits is adopted as the maximum number of MAC address authentication users allowed to access this port. Refer to the Port Security manual for the description on the port security function.
l You cannot configure the maximum number of MAC address authentication users for a port if any user connected to this port is online.
Configuring the Quiet MAC Function on a Port
You can configure whether to enable the quiet MAC function on a port. When this function is enabled, the MAC address connected to this port will be set as a quiet MAC address if its authentication fails. When this function is disabled, the MAC address will not become quiet no matter whether the authentication is failed.
Table 1-5 Configure the quiet MAC function on a port
|
Operation |
Command |
Description |
|
Enter system view |
system-view |
— |
|
Enter Ethernet port view |
interface interface-type interface-number |
— |
|
Configure quiet MAC function on the port |
mac-authentication intrusion-mode block-mac enable |
Required Enabled by default. |
Displaying and Debugging MAC Authentication
After the above configuration, you can execute the display command in any view to display system running of MAC Authentication configuration, and to verify the effect of the configuration. You can execute the reset command in user view to clear the statistics of MAC Authentication.
Table 1-6 Display and debug MAC Authentication
|
Operation |
Command |
Description |
|
Display global or on-port information about MAC authentication |
display mac-authentication [ interface interface-list ] |
Available in any view |
|
Clear the statistics of global or on-port MAC authentication |
reset mac-authentication statistics [ interface interface-type interface-number ] |
Available in user view |
MAC Authentication Configuration Example
Network requirements
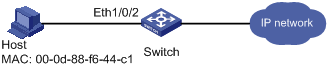
As illustrated in Figure 1-1, a supplicant is connected to the switch through port Ethernet 1/0/2.
l MAC authentication is required on port Ethernet 1/0/2 to control user access to the Internet.
l All users belong to domain aabbcc.net. The authentication performed is locally and the MAC address of the PC (00-0d-88-f6-44-c1) is used as both the user name and password.
Network Diagram
Figure 1-1 Network diagram for MAC authentication configuration
Configuration Procedure
# Enable MAC authentication on port Ethernet 1/0/2.
<Sysname> system-view
[Sysname] mac-authentication interface Ethernet 1/0/2
# Set the user name in MAC address mode for MAC authentication, requiring hyphened lowercase MAC addresses as the usernames and passwords.
[Sysname] mac-authentication authmode usernameasmacaddress usernameformat with-hyphen lowercase
# Add a local user.
l Specify the user name and password.
[Sysname] local-user 00-0d-88-f6-44-c1
[Sysname-luser-00-0d-88-f6-44-c1] password simple 00-0d-88-f6-44-c1
l Set the service type to “lan-access”.
[Sysname-luser-00-0d-88-f6-44-c1] service-type lan-access
[Sysname-luser-00-0d-88-f6-44-c1] quit
# Add an ISP domain named aabbcc.net.
[Sysname] domain aabbcc.net
New Domain added.
# Specify to perform local authentication.
[Sysname-isp-aabbcc.net] scheme local
[Sysname-isp-aabbcc.net] quit
# Specify aabbcc.net as the ISP domain for MAC authentication
[Sysname] mac-authentication domain aabbcc.net
# Enable MAC authentication globally (This is usually the last step in configuring access control related features. Otherwise, a user may be denied of access to the networks because of incomplete configuaration.)
[Sysname] mac-authentication
After doing so, your MAC authentication configuration will take effect immediately. Only users with the MAC address of 00-0d-88-f6-44-c1 are allowed to access the Internet through port Ethernet 1/0/2.
