- Released At: 14-04-2022
- Page Views:
- Downloads:
- Table of Contents
- Related Documents
-
|
|
|
Control Plane Protocol Packet Rate Limit |
|
Technology White Paper |
|
|
|
|
Copyright © 2022 New H3C Technologies Co., Ltd. All rights reserved.
No part of this manual may be reproduced or transmitted in any form or by any means without prior written consent of New H3C Technologies Co., Ltd.
Except for the trademarks of New H3C Technologies Co., Ltd., any trademarks that may be mentioned in this document are the property of their respective owners.
This document provides generic technical information, some of which might not be applicable to your products.
The information in this document is subject to change without notice.
Overview
Technical background
As the network environment gets increasingly complicated, the network becomes vulnerable to eavesdropping, and malicious modification and forwarding. Denial of Service (DoS) attack is a common network attack in which the attacker exploits network protocol vulnerabilities and floods packets from unknown sources to consume network resources and increase the burden of the CPU. In this case, normal client requests might fail to be responded.
To resolve the issue, you can configure protocol packet rate limit to control the number of packets sent to the CPU to ensure the correct operation of the CPU.
Benefits
Protocol packet rate limit supports protocol-based rate limit and flow-based rate limit for flexible packet control:
· Protocol-based protocol packet rate limit—Limits the maximum transmission rate of packets of a specific protocol. Excessive protocol packets are dropped.
· Flow-based protocol packet rate limit—Identifies flows of a protocol by source IP or MAC address, limits the maximum transmission rate per flow, and then limits the maximum transmission rate of packets of a specific protocol. Excessive protocol packets are dropped. This method collects traffic statistics by flow and protocol for traffic anomaly and user behavior monitoring.
This feature effectively prevents flood and DoS attacks, ensuring that the control plane maintains correct forwarding and protocol state when the plane is being attacked or is transmitting a large amount of traffic.
Protocol rate limit implementation
Concepts
· Denial-of-Service (DoS) attack—An attacker exploits protocol vulnerabilities to attack the network or floods the target with a large number of protocol packets to disable the target from providing services or make the target inaccessible.
· Token Bucket—A token bucket is analogous to a container that holds a certain number of tokens. Each token represents a certain forwarding capacity. The system looks at the number of tokens in the bucket every time it receives a packet. If the number of tokens in the bucket is enough for forwarding the packet, the system forwards the packet. If the number of tokens is not enough, the system discards the packet.
· Committed Information Rate (CIR)—Rate at which the system puts tokens into the bucket, in kbps.
Mechanism
Protocol types
Table 1 lists protocol types that can be identified and controlled by protocol packet rate limit.
For packets that use multiple protocols, the system uses the protocol type that is last identified as the packet protocol type. For example, for an IP packet that uses the HTTP protocol, the system identifies the packet as an HTTP packet instead of an IP packet.
Table 1 Protocol types supported by protocol packet rate limit
|
Protocol type |
Description |
|
acsei |
ACFP Client and Server Exchange Information (ACSEI) protocol packets exchanged between ACFP client and server. |
|
arp |
ARP packets. |
|
capwap_ctrl |
CAPWAP control packets. |
|
capwap_data |
CAPWAP data packets. |
|
dhcp |
DHCP packets. |
|
dot11_action |
802.11 acknowledge packets. |
|
dot11_assoc |
802.11 association requests. |
|
dot11_auth |
802.11 authentication packets. |
|
dot11_ctrl |
Other 802.11 packets. |
|
dot11_deauth |
802.11 deauthentication packets. |
|
dot11_disassoc |
802.11 disassociation packets. |
|
dot11_null |
802.11 null data packets. |
|
dot11_reassoc |
802.11 reassociation requests. |
|
dot1x |
802.1X authentication packets. |
|
ethernet |
Packets that do not match any other protocol types in the list. |
|
http |
HTTP protocol packets. |
|
iactp |
Inter Access Controller Tunneling Protocol (IACTP) packets. |
|
icmp |
ICMP protocol packets. |
|
icmpv6_nd |
ICMPv6 neighbor discovery protocol packets. |
|
icmpv6_other |
Other ICMPv6 protocol packets. |
|
igmp |
IGMP protocol packets. |
|
ip |
IPv4 protocol packets. |
|
ipv6 |
IPv6 protocol packets. |
|
ntp |
NTP protocol packets. |
|
openflow |
Communication interface standard between the controller and forwarding plane in a Software Defined Network (SDN). |
|
portal_syn |
Portal redirection packets. |
|
radius |
RADIUS protocol packets. |
|
snmp |
SNMP protocol packets. |
|
tcp |
TCP protocol packets. |
|
telnet |
Telnet protocol packets. |
|
udp |
UDP protocol packets. |
|
vrrp |
VRRP protocol packets. |
Packet rate limit
Protocol-based packet rate limit
Protocol-based rate limit enables the system to rate limit packets of all or the specified protocols.
If the number of packets received per second is smaller than or equal to the maximum transmission rate (in pps) for the packet protocol, the system forwards the packets to the control plane. If the number of packets received per second is larger than the maximum rate, the system drops the packet.
The system uses the token bucket mechanism to control the packet transmission rate. The number of tokens in the bucket is determined by both the maximum transmission rate and the token generation interval.
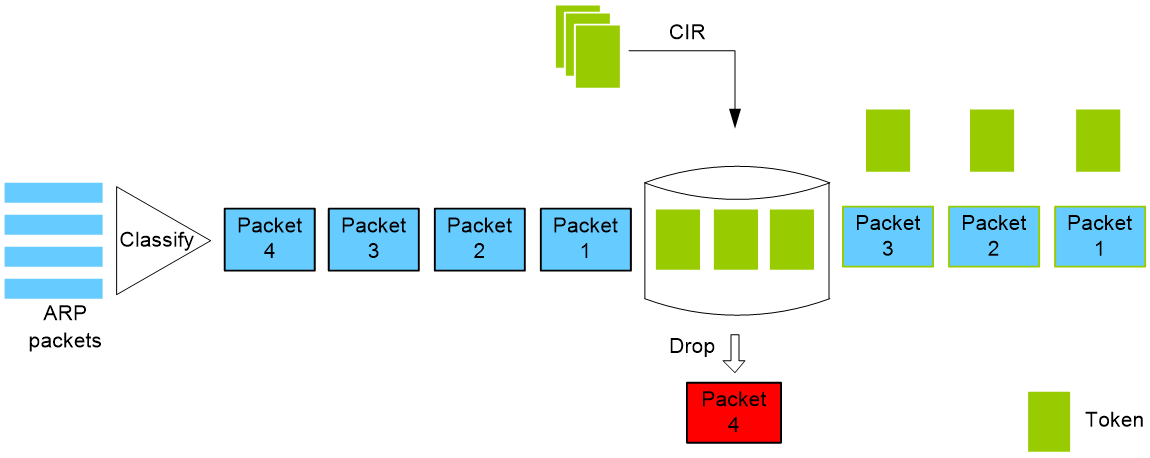
For example, as shown in Figure 1, if three tokens exist in the token bucket and the device receives four ARP packets, the first three packets obtain the tokens and can be forwarded to the CPU. The fourth packet is discarded.
Figure 1 Protocol-based packet rate limit
Flow-based packet rate limit
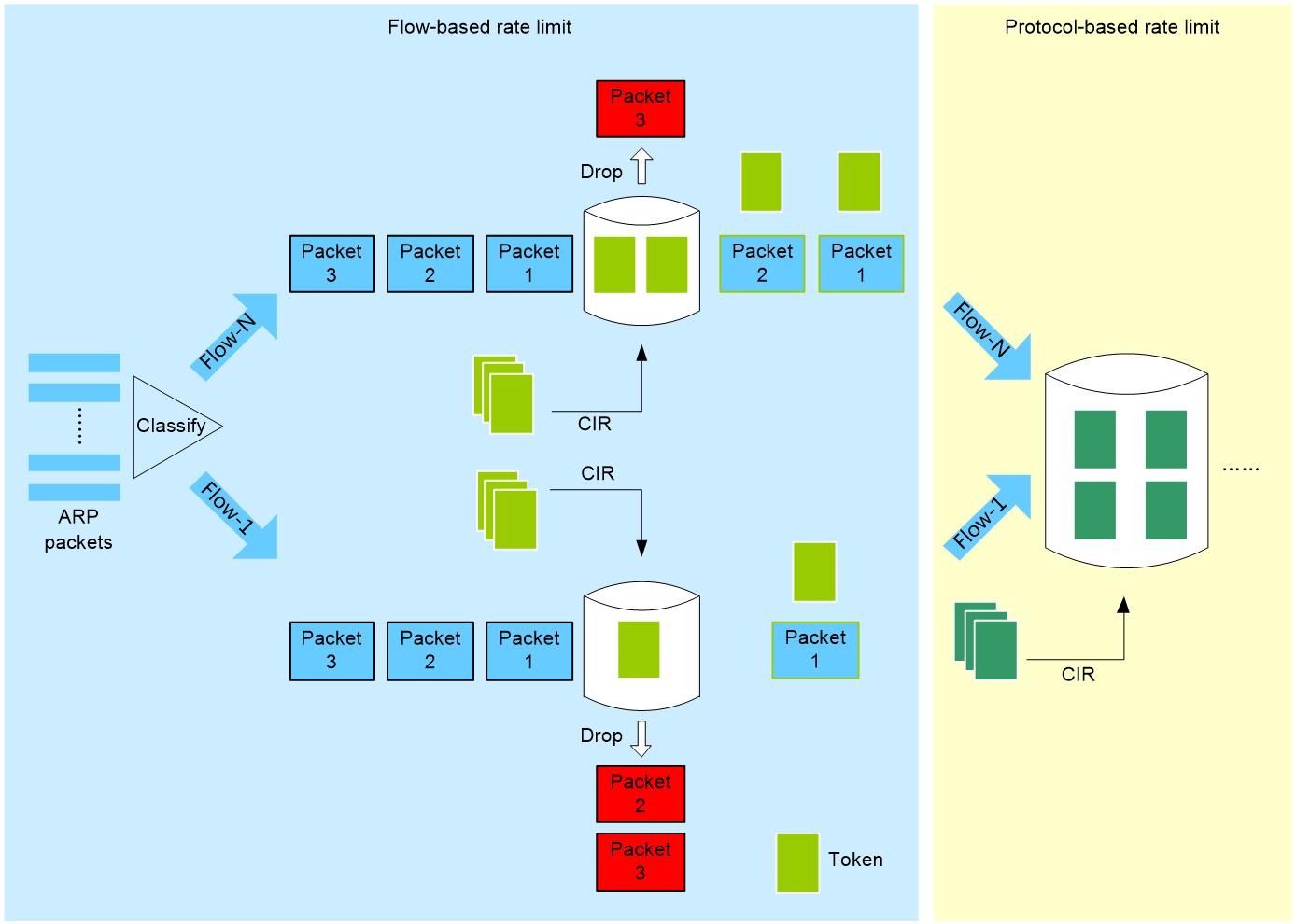
Flow-based rate limit controls packet forwarding first by the maximum transmission rate per flow (in pps) and then by the maximum transmission rate for the packet protocol.
Flow-based rate limit operates as follows:
1. Classifies packets by source IP address or source MAC address.
2. Rate limits packets based on the maximum transmission rate per flow (in pps).
¡ If the number of packets received per second is smaller than or equal to the maximum transmission rate per flow, the system proceeds to the next step.
¡ If the number of packets received per second is larger than the rate per flow, the system drops the packet.
3. Rate limits packets based on the maximum transmission rate for the packet protocol. For more information, see "Protocol-based packet rate limit."
The system uses the token bucket mechanism to control packet transmission. The number of tokens in a bucket is determined by the maximum transmission rate and the token generation interval.
As shown in Figure 2, with flow-based protocol packet rate limit enabled, packets are rate limited based on the maximum transmission rate per flow and then the maximum transmission rate for the packet protocol.
Figure 2 Flow-based packet rate limit
Application scenarios
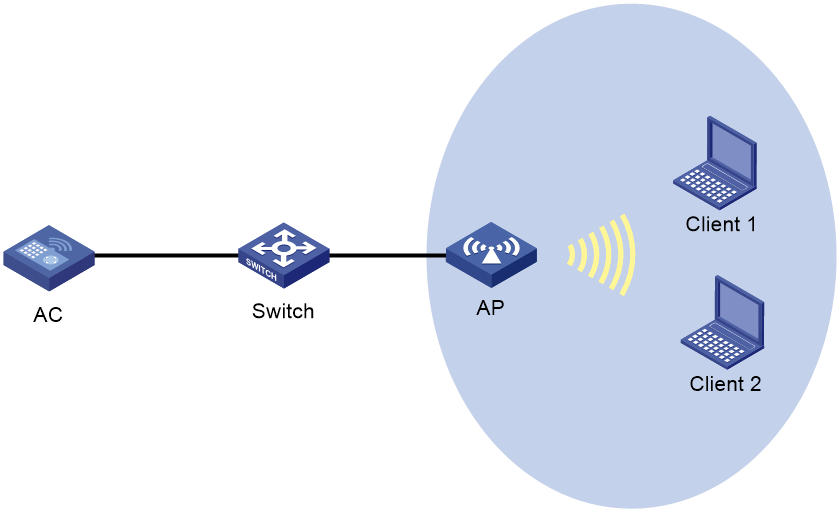
In a WLAN as shown in Figure 3, you can configure protocol-based or flow-based protocol rate limit on the AC to prevent flood attacks.
Figure 3 Protocol packet rate limit network diagram