- Released At: 28-11-2022
- Page Views:
- Downloads:
- Table of Contents
- Related Documents
-
|
|
|
Cloudnet PPSK Authentication Technology White Paper |
|
|
|
|
Copyright © 2022 New H3C Technologies Co., Ltd. All rights reserved.
No part of this manual may be reproduced or transmitted in any form or by any means without prior written consent of New H3C Technologies Co., Ltd.
Except for the trademarks of New H3C Technologies Co., Ltd., any trademarks that may be mentioned in this document are the property of their respective owners.
The information in this document is subject to change without notice.
Contents
Overview
Technical background
Network security performance and easy user access are two important elements that must be taken into consideration at design and deployment of small- to medium-sized enterprise networks.
The 802.11i mechanism uses the following modes for authenticating user integrity and dynamically generating and updating keys:
· 802.1X—802.1X performs user authentication and generates the pairwise master key (PMK) during authentication. The client and AP use the PMK to generate the pairwise transient key (PTK).
· Pre-Shared Key (PSK)—The PSK is used to generate the PMK. The client and AP use the PMK to generate the PTK.
· Private PSK (PPSK)—The MAC address of the client is used as the PSK to generate the PMK. The client and AP use the PMK to generate the PTK through four-way handshake.
The 802.1X mode provides the highest security performance, but requires complicated configuration on an authentication server. It has high technical requirements on network administrators and is not suitable for small- to medium-sized enterprises. In PSK mode, passwords are easy to be cracked by brute-force and dictionary attacks and obtained through proactive sharing or social engineering methods. PSK disclosure can cause severe communication security threats because all users in the network use the same PSK.
The PPSK mode can resolve the issues in 802.1X and PSK and is most suitable for small- to medium-sized network deployment that does not have authentication servers or professional network administrators.
However, PPSK requires users to enter the MAC addresses of terminals, which is inconvenient and prone to MAC spoofing attacks.
To resolve the issue, H3C combined PPSK with the H3C Cloudnet platform and released a more robust and easy-to-use solution for wireless access in small- to medium-sized networks. In this solution, the cloud platform generates passwords and manages user and password mappings. To access a wireless network, users only need to apply for a password from the cloud platform through a WeChat mini program.
Cloudnet PPSK provides user authentication without the collaboration of AC hardware resources and an authentication server. It balances network security performance and ease-of-use while reducing the costs and workforce investment for maintenance and management.
Benefits
H3C Cloudnet PPSK authentication provides the following benefits:
· Unified password generation and management
H3C Cloudnet can generate time-specific strong passwords for a site and allow users to manage passwords as needed in a unified manner. For example, bind passwords to devices in advance, set the number of devices supported by a password, set the password validity period, add or delete passwords or supported devices.
Cloudnet PPSK can effectively avoid the use of weak passwords, reduce security risks arising after a long period of password use, and provide protection against brute-force and dictionary attacks.
· One user password for one or more devices
Cloudnet PPSK allows one user to use one password on one or multiple devices, which reduces the burden of remembering passwords for multiple terminals, and makes wireless network use more convenient while ensuring security.
· Independent and user-exclusive password use
Once used, a password is bound to the user terminal. Even if the password is obtained by an unauthorized user, the unauthorized user cannot use the password to log in to the network from another terminal. This effectively protects the network against social engineering methods.
· Highly available system
When a wireless access device is disconnected from Cloudnet, the device can still provide user access and key negotiation services, and online wireless clients are not affected. The devices synchronize key data with Cloudnet at specific intervals and after fault recovery, which further ensures the stable operation of wireless network and guarantees high availability.
· Good expandability
Cloudnet provides an interface for interoperation with other enterprise clouds. Users can synchronize passwords from a third-party cloud to Cloudnet as required by the interface protocol to achieve seamless interoperation between wireless devices and the third-party password management system.
· Ease-of-use
After applying for a password through the mini-program, users can view and directly copy the password from the mini-program to the Wi-Fi access page. Unlike in traditional PPSK authentication, no password remembering or manual input is required.
Implementation
Mechanism
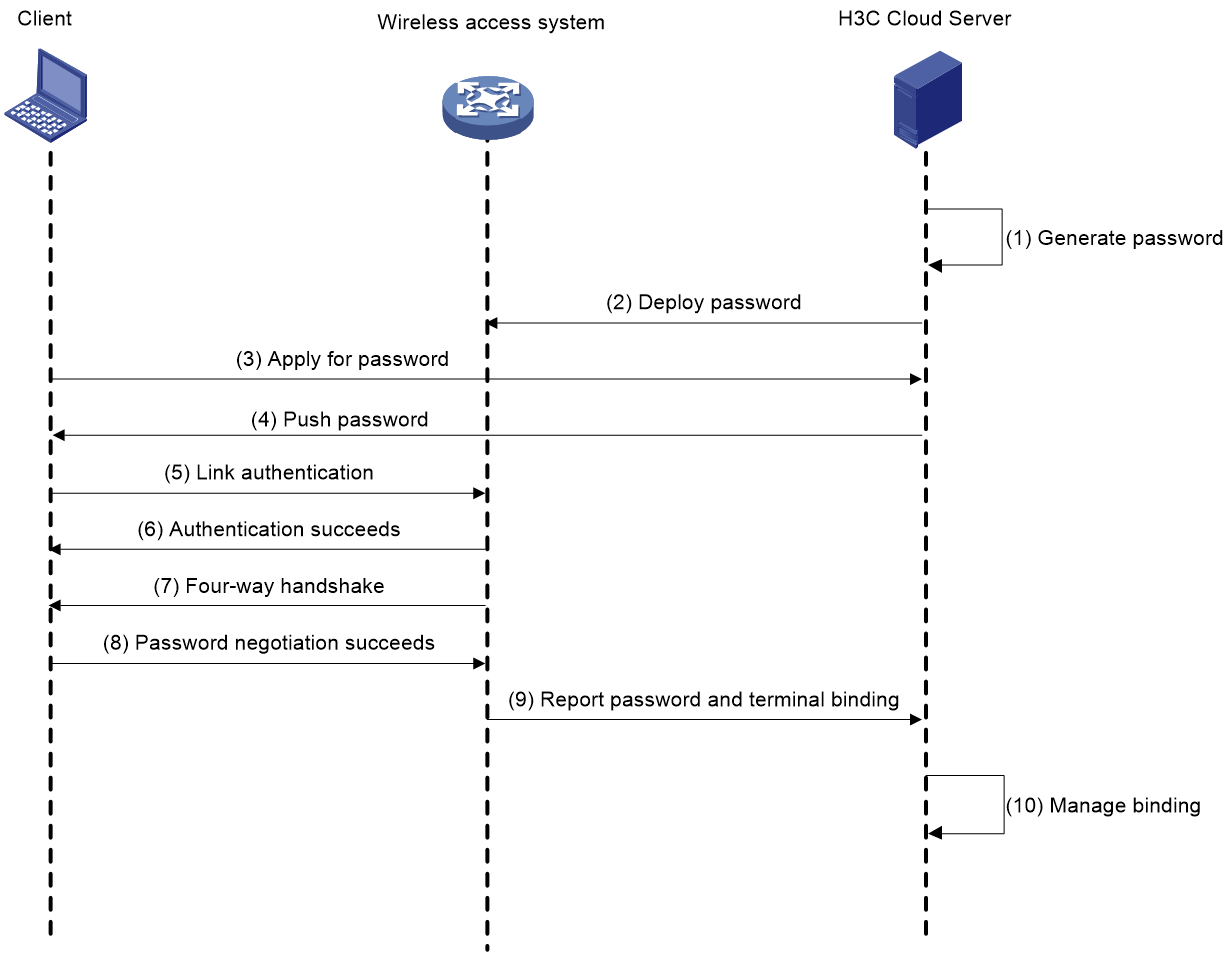
As shown in Figure 1, Cloudnet PPSK operates as follows:
1. The network administrator pre-configures passwords for wireless clients in a site from Cloudnet (https://oasiscloud.h3c.com).
2. Cloudnet deploys the configured passwords to the wireless access system (AC + fit AP for example) through encrypted tunnel transmission.
3. A user applies for a password from the Web interface.
4. Cloudnet pushes a password to the user.
5. The user scans wireless services and connects to a wireless service that supports Cloudnet PPSK, which triggers link authentication.
6. After user link authentication succeeds, the obtained password is input and four-way handshake key negotiation starts.
7. After key negotiation, the dedicated PTK is generated for user-specific data encryption. The user can now access and use the wireless network.
8. The wireless access device reports the password and user terminal binding to Cloudnet.
9. Cloudnet saves and manages the password and terminal binding.
Figure 1 User association in Cloudnet PPSK
Application scenarios
Cloudnet PPSK authentication is applicable to AC + fit AP networks, independent cloud-managed AP networks, and WBC networks. This section uses an AC+fit AP network and a cloud-managed AP network as examples.
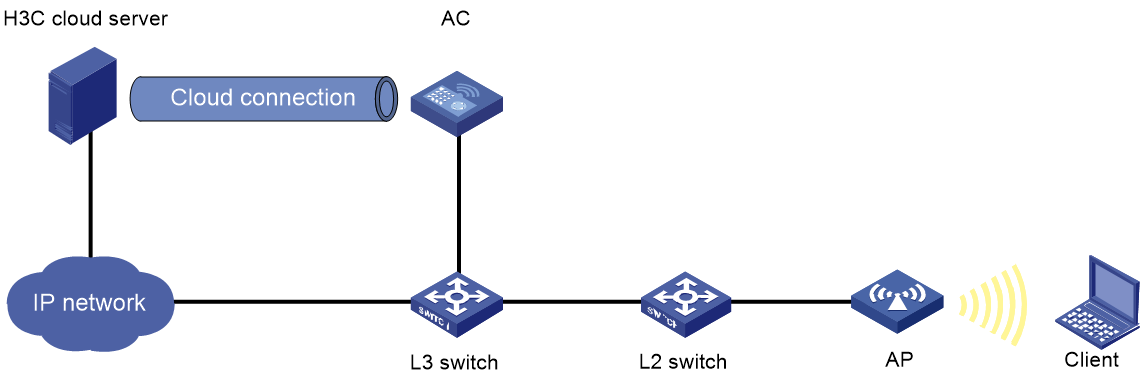
AC + fit AP network
As shown in Figure 2, the wireless access system (AC + fit AP) connects to Cloudnet through an encrypted tunnel. Cloudnet deploys, deletes, and synchronizes passwords to the access system, and the access system reports password and terminal bindings to Cloudnet.
In an AC+fit AP network, Cloudnet PPSK authentication operates as follows:
1. A user accesses the password application website through the 4G or 5G cellular network, inputs the application code, and specifies an email address for password receiving.
The applied password will be displayed on the password application page and sent to the user email address.
2. H3C Cloudnet deploys the password to the access device through the encrypted tunnel and triggers key installation.
3. The user uses the password to perform four-way handshake and accesses the network.
Figure 2 Cloudnet PPSK authentication in an AC + fit AP network
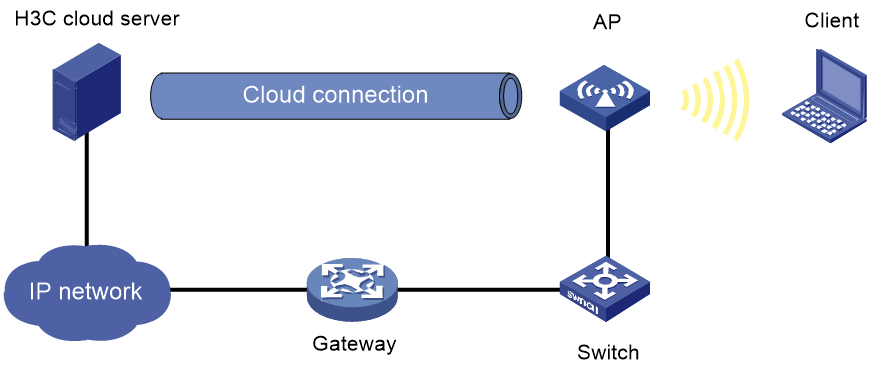
Cloud-managed AP network
As shown in Figure 3, the wireless access system (cloud-managed AP) connects to Cloudnet through an encrypted tunnel. Cloudnet deploys, deletes, and synchronizes passwords to the access system, and the access system reports password and terminal bindings to Cloudnet.
In a cloud-managed AP network, Cloudnet PPSK operates as follows:
1. A user accesses the password application website through the 4G or 5G cellular network, inputs the application code, and specifies an email address for password receiving.
The applied password will be displayed on the password application page and sent to the user email address.
2. H3C Cloudnet deploys the password to the access device through the encrypted tunnel and triggers key installation.
3. The user uses the password to perform four-way handshake and access the network.
Figure 3 Cloudnet PPSK authentication in a cloud-managed AP network