- Released At: 19-12-2020
- Page Views:
- Downloads:
- Table of Contents
- Related Documents
-
|
|
|
WPA3 |
|
Technology White Paper |
|
|
|
|
Copyright © 2020 New H3C Technologies Co., Ltd. All rights reserved.
No part of this manual may be reproduced or transmitted in any form or by any means without prior written consent of New H3C Technologies Co., Ltd.
Except for the trademarks of New H3C Technologies Co., Ltd., any trademarks that may be mentioned in this document are the property of their respective owners.
The information in this document is subject to change without notice.
Contents
Overview
Wi-Fi Protected Access 3 (WPA3) is the next-generation Wi-Fi security solution developed based on WPA2 to provide enhanced security protection. WPA3 provides the WPA3-Personal and WPA3-Enterprise security modes. WPA3-Personal is applicable to personal and home networks and WPA3-Enterprise provides additional protections for middle- to large-sized networks such as governments and enterprises.
Technical background
The Wi-Fi Alliance introduced WPA in 2003 to replace the highly crackable Wired Equivalent Privacy (WEP), and introduced Temporal Key Integrity Protocol (TKIP) as a cipher suite for WPA to protect wireless traffic. In 2006, the alliance launched WPA 2, which introduced Advanced Encryption Standard (AES)-based CCMP as a cipher suite. Compared with TKIP, Counter mode with CBC-MAC Protocol (CCMP) provides greatly improved security performance.
In 2018, the Wi-Fi Alliance launched WPA3 to eliminate the vulnerabilities of WPA2 by forbidding the use of TKIP and mandating the use of 802.11w protected management frames (PMF).
To provide compatibility with wireless devices of earlier versions, the Wi-Fi Alliance designed a transition mode for WPA3-Personal, which allows devices that do not support WPA3 to access WPA3 WLANs through WPA3-Personal.
Benefits
WPA3 supports the following security modes to perform scenario-specific security protection:
· WPA3-SAE—Uses Simultaneous Authentication of Equals (SAE) instead of Pre-Shared Key (PSK) to provide more robust password-based authentication. A wireless client must complete a 4-way handshake with the target AP during authentication to associate with the AP. SAE is able to resist offline dictionary attacks, allowing network administrators to specify simple personal network passwords without affecting network security. Attackers cannot decode encrypted wireless traffic even if they obtain the passwords because the system assigns a unique session key to each wireless client after the SAE exchange and 4-way handshake.
· WPA3-Enterprise—Offers an optional mode that uses 192-bit minimum-strength security protocols and cryptographic tools to better protect sensitive data. In an enterprise network deployed with an AAA server, the 192-bit mode requires all cryptographic algorithms used in the network to be compliant with the Commercial National Security Algorithms (CNSA) Suite. This ensures a minimum of 192-bit strength performance for wireless traffic.
WPA3 implementation
WPA3-Personal
As shown in Figure 1, in WPA3-Personal, a client exchanges probe, authentication, and association packets with a target AP to come online from the AP.
During the authentication phase, the client exchanges SAE commit and confirm frames with the AP. SAE exchange can be triggered by either the client or the AP. They negotiate the Key Confirmation Key (KCK) and Pairwise Master Key (PMK) during commit frame exchange and confirm the negotiated PMK during confirm frame exchange. The PMK is a temporary key used for a 4-way handshake and the KCK is used to verify confirm frames. During the 4-way handshake, the client and the AP negotiate the temporary session key.
Figure 1 Client association in WPA3-Personal
|
|
NOTE: SAE uses discrete logarithm cryptography for key negotiation and uses Finite Field Cryptography (FFC) or Elliptic Curve Cryptography (ECC) to calculate key-related parameters. The Wi-Fi Alliance requires ECC implementation to use ECC group 19 defined by the Internet Assigned Numbers Authority (IANA). Unless otherwise stated, this document describes SAE implementation that uses ECC Group 19. |
Commit frame exchange
Before sending a commit frame, the sender uses the Hunting and Pecking algorithm to generate a Password Element (PWE) based on the PSK and MAC addresses of the sender and the receiver. The PWE is a point on the elliptic curve.
As shown in Figure 2, a commit frame contains six fields. The first three fields are fixed in an authentication frame. The Group ID field contains the group ID, which is typically 19. If group 19 is used, the Scalar field contains a large integer and the Element field contains the coordinates of the PWE point on the elliptic curve.
The scalar integer and element coordinates are generated by the sender based on a random value and the PWE through elliptic curve operation.
Upon receiving the commit frame, the receiver verifies the frame, and uses both the local and received frame content to generate a KCK and PMK.
Confirm frame exchange
As shown in Figure 3, a confirm frame contains five fields. The first three fields are fixed in an authentication frame. The Send-Confirm field contains the counter of sent confirm frames. The Confirm field contains a verification code calculated by using the KCK, Send-Confirm, local and peer Scalars, and local and peer Elements through a hash algorithm.
Upon receiving a confirm frame, the receiver compares the verification code in the frame with the code calculated locally. If the codes are the same, the verification succeeds and the client and the AP proceed to the association and 4-way handshake phase.
WPA3-Enterprise
Compared with WPA2-Enterprise, WPA3-Enterprise 192-bit mode increases the key length, uses a new cipher suite, and adds consistency requirements on component security. This mode has the following requirements:
· 802.1X authentication with the 384-bit elliptic curve algorithm or an over 3072-bit RSA algorithm.
· One of the following Transport Layer Security cipher suites:
¡ TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384
¡ TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
¡ TLS_DHE_RSA_WITH_AES_256_GCM_SHA384
· HMAC-SHA-384 for key export during a 4-way handshake.
· Galois Counter Mode Protocol (GCMP)-256 for client wireless traffic and multicast management frame protection.
· Support of 192-bit security on both the AAA server and wireless clients.
|
|
NOTE: · Although GCMP-192 can deliver equivalent strength, GCMP-256 was selected based on its wider adoption. · Some servers and clients can be updated to support 192-bit security. |
Typical applications
WPA3-Personal networking
As shown in Figure 4, deploy a WPA3-Personal network in the following modes:
· Mandatory mode—Prohibits clients that do not support WPA3 from accessing the WLAN.
· Optional mode—Allows clients that do not support WPA3 to access the WLAN.
As a best practice, use the mandatory mode because WPA2 vulnerabilities still exist in optional mode.
WPA3-Enterprise networking
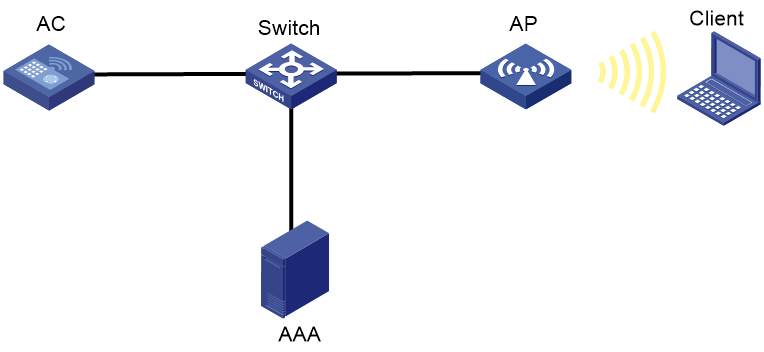
As shown in Figure 5, deploy an AAA server and install an ECC P-384 or 3072-bit RSA certificate on the server. If the EAP method is EAP-TLS, you must also install the corresponding certificate on wireless clients.
Related documents
· IEEE Std 802.11-2016
· Wi-Fi CERTIFIED WPA3™ Technology Overview
· WPA3™-Enterprise 192-bit Security Test Plan
· WPA3™-SAE Test Plan