- Released At: 06-03-2022
- Page Views:
- Downloads:
- Table of Contents
- Related Documents
-
H3C FIST
Technology White Paper
Copyright © 2022 New H3C Technologies Co., Ltd. All rights reserved.
No part of this manual may be reproduced or transmitted in any form or by any means without prior written consent of New H3C Technologies Co., Ltd.
The information in this document is subject to change without notice.
Login security information configuration
Repositories and repository inventory
Software push and installation
Introduction
Background
With the fast development of Internet technologies, the enterprises need more and more computing and networking resources. To ensure the reliable, stable operation of the whole data system, some enterprises pose higher requirements on the O&M system, which gradually increases the O&M cost.
Fast Intelligent Scalable Toolkit (FIST) developed by H3C can effectively help enterprises to improve the datacenter O&M capabilities. An enterprise user can use FIST to flexibly monitor, configure, and deploy devices in the datacenter as required to build a dedicated O&M environment. FIST can effectively help enterprises to improve the O&M efficiency and reduce the O&M costs.
FIST can be deployed on VMs as the server O&M software. Additionally, FIST can be embedded in the H3C UniServer B16000 AE modules to help users to configure and manage enclosure servers. In the AE module application scenarios, FIST can not only manage the local enclosure of the AE module, but also other enclosures, rack servers, and switches. FIST in an AE module is applicable to a hybrid IT architecture.
Benefits
· Deployment through VM file import—FIST can be easily deployed on a VM through the import of a VM file.
· Bulk server deployment—Provides bulk server deployment, which greatly improves the deployment efficiency before server onboarding. FIST can manage a maximum of 5000 servers and 30 switches.
· Template-based configuration—Adds support for template-based server configuration to separate the server configuration from hardware, and provides stateless computing.
· Open integration—Provides HTTPS/HTTP-based RESTful APIs, and allows the third-party vendors to integrate FIST into their service processes.
Software compatibility
In some scenarios, FIST needs to cooperate with other software products. This section describes the FIST compatibility with other software products:
· HDM—HDM is a remote management system (BMC software) developed by H3C to manage servers. FIST can cooperate with HDM to implement out-of-band server management.
· FIST SMS—FIST SMS is management software installed in the server operating system to enhance HDM and FIST management functions. FIST SMS enriches the server management function through in-band communication, and can cooperate with HDM to enable the in-band management information and out-of-band management information to communicate. In cooperation with FIST SMS, FIST can centrally manage servers.
· OM—OM is the software in the onboard management module of the H3C UniServer B16000 enclosure. Through the backplane, the onboard management module is connected to all the other modules in the enclosure to centrally manage and monitor each module in the enclosure. FIST can cooperate with OM to manage devices in enclosures.
· AE—An AE module is a management node of an H3C UniServer B16000 enclosure. An AE module is a special enclosure node and is preinstalled with FIST when shipped.
· Repository—A repository is a component package developed by H3C and is a set of server firmware and drivers. A repository is an .iso file and supports automatic startup.
· iFIST—iFIST is a single-device intelligent deployment software product embedded in servers developed by H3C. In the underlayer, iFIST runs the H3Linux operating system. Some functions of FIST must use iFIST as the operation medium.
System architecture
System design
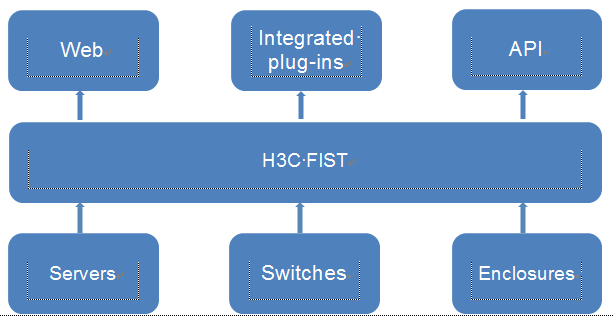
Figure 1 System framework
The southbound and northbound connections of FIST are as follows:
· Northbound—FIST uses the Web interface to meet the graphical configuration requirements of users, and provides RESTful APIs and plug-ins for integration with third-party software.
· Southbound—FIST manages physical devices in the southbound direction and uses the interfaces provided by physical devices to exchange information with devices.
Security management
Introduction
FIST security management includes data security and usage security. Data security includes secure transmission channels and sensitive information encryption. Software usage security includes user management, whitelist management, FIST software backup and restoration, cluster management, and login security information configuration.
Operating mechanism
Data security
FIST allows users to access it through HTTP or HTTPS channels. If you have a high security requirement for the data transmission channel, as a best practice, use the HTTPS data access channel.
Additionally, regardless of the channel type, FIST always encrypts the sensitive data. For example, when a user is logging in, FIST will encrypt the password that the user entered by using the RSA 2048 algorithm and then transmit it to the backend for authentication. This mechanism avoid password leak when the data channel is monitored. At the same time, the user password must be saved in the FIST database. To avoid password leak when the database is leaked, FIST encrypts the plaintext passwords by using the MD5+Salt algorithm.
User management
In the current software version, FIST supports two user roles, admin and guest. Users with the admin privilege have all the operation privileges. Uses with the guest privilege have only the read privilege. At the same, to enhance the account security, FIST provides the function of configuring the password policies. In a password policy, you can enable or disable password complexity check, set the password validity period, set the number of disabled history passwords, set the password lockout period and duration, and force password modification upon password expiration. FIST supports a maximum of 10 users and up to 30 concurrent online user sessions.
At the same time, FIST supports interoperating with the LDAP domain name server and adding user groups with the same permissions. Then, the users can be uniformly managed and assigned permissions.
Whitelist management
FIST allows you to configure a login whitelist. On the whitelist, you can configure up to 10 login rules. A user matching any rule can log in. In a rule, you can configure the allowed login time range and IP range.
Backup & restore
FIST allows you to back up and restore the software. A user can periodically back up the configuration in FIST and save it locally as a restoration point. When you need to migrate the FIST software, you can import a backup configuration file to restore the FIST software to the specified restoration point.
The backup and restoration function involves the following information: device information, task information in component updates, HDM configuration templates, BIOS configuration templates, configuration templates, and user information, excluding repositories and image files. When you restore the backup data, the current FIST data will be overwritten.
Cluster management
FIST supports the 1+1 primary/backup cluster. In the current software version, this feature is supported only when FIST runs in an AE module. After a cluster is created, FIST can automatically monitor the running state of the primary node. When the primary node fails, FIST automatically switches to the backup node. This mechanism reduces the service failures caused by AE module failure.
Login security information configuration
FIST supports multiuser management. Therefore, multiple users can log in to the same device and operate it. Login security information configuration allows you to customize a prompt message on the FIST login page to reduce the misoperation risks.
Device management
Introduction
FIST supports uniformly managing the H3C servers, switches, and enclosures. Through only FIST, you can gain the insights into the usage conditions of multiple device nodes in the equipment room. This feature assists O&M.
Restrictions and guidelines
Enclosure management is available only when FIST runs in an AE module.
Operating mechanism
As shown in Figure 2, FIST obtains information through the APIs provided by the physical devices and displays the information in the Web interface. The involved interfaces include the following:
· HDM—FIST can interact with HDM through RESTful, IPMI, or SNMP.
· FIST SMS—FIST can interact with FIST SMS through the TCP socket. At the same time, FIST SMS can interact with HDM through the in-band channel (USB). Therefore, FIST can obtain the HDM-related information when managing only FIST SMS.
· Chassis OM—FIST can interact with OM through the RESTful APIs.
· Switch—FIST can interact with the H3C switches through NETCONF.
Figure 2 Device interaction interfaces
Manage servers
Add servers
You can add servers to FIST through manually adding devices (single or bulk) and IP range-based device discovery. You can add servers to FIST in one of the following methods:
· Manual addition—Add a server to FIST through its IP address, username, and password.
· Bulk import—Upload a device information file in .txt, .xls, or .xlsx format to bulk add devices.
· Discovery—After you enter the stat IP, end IP, username, password, and search cycles, FIST can automatically search for matching servers.
¡ If the Add Manually method is used, FIST lists all the discovered servers on a list. You can select the servers add to FIST, and then click Add.
¡ If the Add Automatically method is used, FIST automatically adds a server once it discovers the server.
FIST will also automatically add all the blade servers installed in a managed enclosure to the managed server list.
The following types of devices can be added:
· HDM—FIST can add HDM devices to implement out-of-band server management.
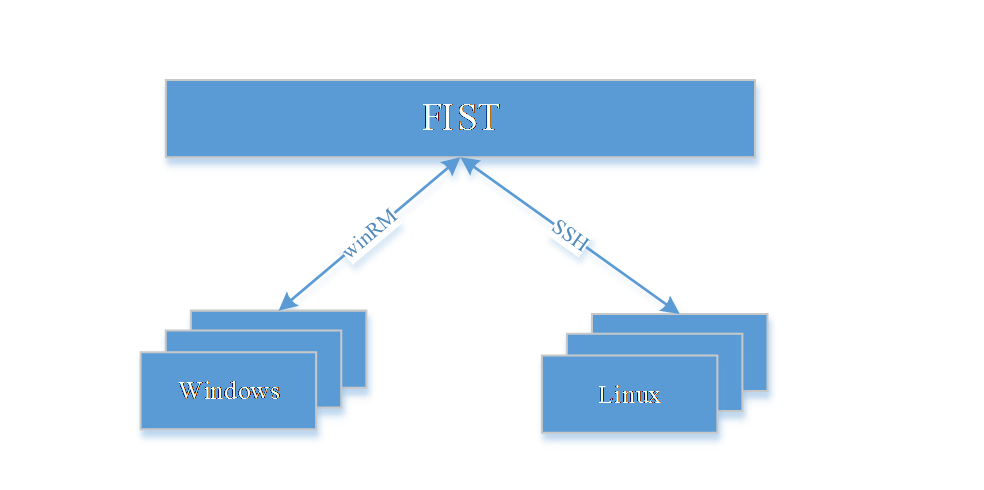
· FIST SMS—FIST can add FIST SMS devices to implement in-band server management. FIST SMS must run in the server operating systems. To reduce the FIST SMS software installation workload on a large number of servers, FIST provides the function of bulk installing FIST SMS. This function allows you to use winRM and SSH to push and install the FIST SMS software in Windows and Linux operating systems.
Figure 3 Bulk FIST SMS installation
View basic device information
On the server list page, you can view basic information about servers, including:
· For HDM devices: HDM connection state, HDM version, BIOS version, BIOS boot options, boot mode, overall device health state, device name, memory information, CPU information, PCIe information, storage information, temperature information, power state, UID LED state, and power information.
· For FIST SMS devices: FIST SMS state, HDM version, BIOS version, BIOS boot options, boot mode, overall device health state, product name, memory information, system drive information, CPU information, network information, and performance motioning information for critical server hardware components. The performance monitoring information includes the CPU usage, memory usage, disk usage, and network throughput. FIST SMS obtains the information above through the in-band IPMI commands and commands in the operating system.
When the HDM device and FIST SMS device added by a user are on the same server, the HDM device and FIST SMS device will be combined into one device.
Device operations
FIST supports bulk operating a large number of servers. You can perform the following bulk operations for servers: power management, downloading SDS logs, downloading the configuration list, rebooting HDM, UID LED control, editing devices, and deleting devices.
In addition to bulk operations, FIST allows you to perform the following operations for a single server: accessing HDM, opening the remote console, and configuring the server power.
Server groups
FIST allows you to group servers. You can assign labels to servers according to the service types. Then, the user can quickly filter the servers according to the labels.
Server autoconfiguration
FIST provides the autoconfiguration feature for rack servers and blade servers. FIST automatically configures a blade server or rack server by using the predefined server template in the following conditions:
· A blade server is installed in an enclosure slot that has a bound server template.
· The management port of a rack server is connected to a switch port that has a bound server template.
Manage switches
Add devices
FIST allows you to add a switch through the switch IP, username, and password.
View basic switch information
After a switch is managed by FIST, FIST can exchange information with the switch through the interface provided by the switch. FIST allows you to view basic switch information, including:
· Switch summary information: Vendor and model.
· Switch card information: Slot number, CPU usage, and memory usage.
· Switch port information: Port name and traffic information.
· Switch interface information: Interface name and state information.
Switch traffic statistics information
Through FIST, you can view the traffic statistics information of switch ports, including:
· Number of received or sent bytes.
· Number of received or sent unicast packets.
· Number of received or sent non-unicast packets.
· Number of received or sent dropped packets.
· Number of received or sent error packets.
· Rate of received or sent bytes.
· Number of received unsupported packets.
Remotely manage switches
Through FIST, you can open the SSH console of a switch. You can enter the username and password on the console to enter the CLI of the switch. At the CLI, you can enter commands to remotely manage the switch.
Switch groups
FIST allows you to group switches. You can assign labels to switches to facilitate switch management.
Rack server autoconfiguration through switch port-to-server template binding
You can bind a server template to a switch port to enable automated configuration of the server connected to that port.
When a rack server is added to FIST, FIST checks whether the server is connected to a switch port that has a bound server template. If yes, FIST will automatically apply the bound server template to the server.
Manage enclosures
Add enclosures
You can add an enclosure to FIST through entering the OM IP, username, and password. At the same time, FIST will automatically add the enclosure hosting the AE module to FIST for management. The two methods above add all cascaded enclosures by default.
Obtain the enclosure information
FIST supports managing multiple enclosures. FIST exchanges information with OM modules through the RESTful APIs to obtain overall information about enclosures, so that the O&M staff can obtain the overall state of enclosures. FIST supports obtaining the following enclosure information:
· Basic information: Front view and rear view of the enclosure, enclosure state, subsystem state, OM IP, location, and asset label.
· AE module: Slot number, custom name, product name, management IP, health state, UID LED state, power, air outlet temperature, serial number, manufacture name, CPU info, and memory info.
· Blade server: Slot number, custom name, product name, management IP, health state, UID LED state, power, air outlet temperature, serial number, manufacture name, CPU info, memory info, and node interconnect info.
· OM module: Health state, UID LED state, management IP, slot number, device model, manufacturer, firmware address, serial number, CPU usage, temperature, and system logs.
· Interconnect module: Slot number, health state, UID LED state, power state, IP address, product name, and CPU usage.
· Power system: Slot number, health state, power redundancy mode, dynamic power saving mode, firmware version, output power, and rated power.
· Fan system: Slot number, health state, firmware version, and rotating speed.
· Power information: Enclosure rated power, available power, power cap, total input power, total output power, real-time power of each enclosure module, and history power trend.
Basic enclosure operations
Through FIST, you can perform the following basic operations for enclosures: configuring the power redundancy mode, configuring the power saving mode, allocating power, setting the UID LEDs and power supplies for the blade servers and AE modules, and setting the one-time boot option and PXE installation for blade servers. When allocating power, you can set the power cap for a single enclosure or set the total power cap for multiple enclosures. When you set the total power cap for multiple enclosures, FIST first allocates a minimum power to each enclosure, and then allocates the remaining power to the enclosures in proportion to the current used power of each enclosure.
Enclosure network topology
FIST supports displaying the topology for enclosures and the network, including the cascade topology between enclosures, the network topology of OM modules and AE modules, the network topology of OM modules and blade servers, and the network topology of blade servers and interconnect modules.
Monitor
Introduction
FIST allows you to monitor the managed devices in multiple methods, which helps the O&M staff to gain better visibility into the datacenter operating state. FIST monitors devices and generates alarms in the following aspects:
· Basic device information: You can view basic information of devices on FIST. For more information, see “Device management.”
· Server activity logs: FIST can receive SNMP traps of managed servers, so that the O&M staff can know the server alarms very well.
· SNMP settings: After FIST receives traps sent from managed servers, FIST can forward them to the specified SNMP server.
· SMTP settings: After FIST receives traps or health state change information sent from managed servers, FIST can forward them to the specified SNMP server.
Operating mechanism
Status monitoring
After a device is added to FIST, the device can be managed and monitored by FIST. On FIST, you can view information and running conditions of the device. For more information, see “Device management.”
In cooperation with FIST SMS, FIST can obtain the server-side performance information. FIST collects performance indexes from FIST SMS periodically. FIST SMS obtains related information through the system-side interfaces. The performance monitoring information includes the CPU usage, memory usage, disk usage, and network throughput.
Server alarm monitoring
FIST supports uniformly monitoring the traps sent from servers, and uniformly displays the trap information on the webpages. The following alarm information attributes can be displayed: alarm occurrence time, alarm level, alarm state (cleared or not), alarm server, and alarm details. On FIST, you can view the state of all servers in the equipment room.
SNMP forwarding
FIST supports the SNMP forwarding feature, which can report faults on the servers to the specified SNMP server. Supported SNMP protocol versions include v1, v2c, and v3.
SMTP forwarding
FIST supports the SMTP forwarding feature, which can report faults on the servers through mails. After FIST receives traps or health state change information, FIST can send such information to the specified recipient through the embedded mail server.
WeCom notifications
FIST implements the WeCom notifications function. When a server fails, a notification is sent to the corresponding WeCom account. When FIST receives traps from a server, FIST converts the traps into the user-defined format, and pushes the traps to the target WeCom account.
SMS and voice notifications
FIST implements the SMS and voice notification function. When a server fails, a SMS message or voice message is sent. When FIST receives traps from a server, FIST converts the traps into the user-defined format, and sends the traps in an SMS or voice notification to the target cellphone.
Images
Introduction
FIST supports multiple OS installation methods, and supports installing multiple types of OS. For users to uniformly manage the OS images, FIST provides the image management feature. This feature can manage OS image files, volumes for diskless boot, and image cloning. In cooperation with the Templates feature, the images managed by FIST can be used to install OSs on servers.
Restrictions and guidelines
Volumes for diskless boot are supported only when FIST runs in an AE module.
Operating mechanism
· OS image files—The OS image files must be uploaded to FIST through a browser. FIST will save these image files in the file system of FIST. On FIST, you can upload, delete, classify, and download image files. Additionally, you can view the name, version, type, and size of each image file.
· Volumes for diskless boot—To implement diskless boot, you must install the OS of a server on a remote end. When the server starts, it reads the system files from the remote end. A volume is an image file saved in the AE module. A blade server installs the OS on a disk of the AE module through the iSCSI protocol. Then, the blade server can start with the volume file through the iSCSI protocol. On FIST, you can create, delete, and copy volume files. Additionally, you can view the name, size, connection state, description, and authentication information of each volume file.
· Image cloning—Image cloning directly clones the OS installed on a server to another server. This feature clones not only the OS but also the applications and OS drivers. FIST sends a command to start a server through iFIST. After iFIST starts, iFIST runs related scripts to export the OS files from the server. The exported OS files are packaged into one compressed image package, and saved on the FIST server through the Samba software. On FIST, you can export and delete OS files. Additionally, you can view the name, type, and size of each OS file.
Templates
Introduction
On FIST, you can preconfigure server templates, switch templates, and enclosure templates. A template is a set of device configurations. After configuring a template, you can bind a template to the specified devices. Then, configurations in the template are applied to these devices, which reduces the waiting time. The template feature of FIST is a powerful tool for initial deployment and redeployment of servers.
A server template is a set of server configurations that can be bulk applied to multiple servers. A server configuration file will be generated for each server based on the applied server template.
An enclosure template is a set of server template-to-enclosure slot bindings. After an enclosure template is applied to an enclosure, FIST binds the server templates to the enclosure slots according to the settings in the enclosure template. Whenever a server is installed in a slot of the enclosure, FIST automatically configures the server by using the bound server template.
Restrictions and guidelines
Driver installation must cooperate with OS installation, and takes effect only when the image installation method is selected.
Operating mechanism
Server templates
A server configuration template separates the hardware from configurations on a server, and is a logical virtualization of a physical server. A server configuration template can implement stateless configuration of the server. Before a new server comes online, you can bind a server configuration template to the server. FIST will deploy configurations in the file to the server to quickly deploy the server. When a server fails, you can bind the saved configuration file to the new server to implement quick configuration migration and quick device replacement. Server templates include HDM configuration templates, BIOS configuration templates, connection settings, RAID configuration templates, and system configuration templates. A server template can be applied to individual servers managed by FIST, bound to enclosure slots in an enclosure template, or bound to switch ports.
· HDM&BIOS configuration templates—You can select HDM configuration templates and BIOS configuration templates.
· RAID settings—You can select a storage controller module, create a logical drive, delete a logical drive, and one-key create RAID 0. One-key creating RAID 0 means to use the remaining physical drives that have not been added to any RAID array to create RAID 0 or simple volume.
· OS settings—The mainstream operating systems, including Windows Server, RedHat Linux Enterprise, SUSE Linux Enterprise, CentOS, VMware ESXi, Ubuntu, and H3C CAS can be newly installed. The RedHat Linux Enterprise, CentOS, and VMware ESXi operating systems support image cloning.
· Connection settings—Allows you to configure the network parameters for the servers' service interfaces.
A server configuration template can be bulk applied to multiple servers.
HDM&BIOS settings
FIST support managing HDM configuration templates and BIOS configuration templates. A typical application scenario of this feature is the scenario where you need to configure one or several types of HDM/BIOS settings for a large number of servers. To do that, first select a server, and manually configure the target HDM/BIOS settings for the server. Then, export the settings of the server into a template. At last, bulk apply the configuration template to other servers. This feature greatly reduces the workload of deploying a large number of servers. This feature reduces not only the O&M cost but also the misconfiguration probability. HDM&BIOS settings are configured through calling the RESTful APIs of HDM. Through FIST, you can back up the HDM&BIOS settings of a server. When creating a server configuration template, you can select a backup file. When the server configuration template is bound to a server, FIST call the RESTful APIs of HDM to restore the backup file to the target server.
The HDM/BIOS configuration templates deliver the following benefits:
· One-key export. Simple, easy operation.
· Bulk copy to simplify the HDM/BIOS configuration management for servers.
· Out-of-band environment, which is separated from the customer service environment.
RAID settings
When a storage controller supports out-of-band RAID configuration, FIST can call the interfaces of HDM to configure RAID settings. When a storage controller does not support out-of-band RAID configuration, FIST will start the server through iFIST, and deploy the RAID settings to iFIST, which will complete the RAID settings for the server.
The RAID configuration delivers the following benefits:
· Out-of-band environment, which is separated from the customer service environment.
Connection settings
For a rack server, you can define switch port-to-server port connections and assign a network to each connection. Then, you can bind the server template to the corresponding switch port by using the auto-configuration feature. FIST can then automatically configure the VLAN ID for the switch port through NETCONF according to the connection settings in the server template.
For a blade server in an enclosure, you can deploy connection settings to the Mezzanine card of the server and the downlink and uplink ports of the interconnect module when you apply a server template. Through calling OM-related interfaces, FIST can set the network mode, port speed, and VLAN ID for ports.
This feature can set up the network transmission path from a rack server's system application to the switch downlink port or from a blade server's system application to the interconnect module uplink ports to enable quick service switchover.
System Settings
In the current software version, you can install operating systems for servers through image installation or image cloning. Both methods need the cooperation between FIST and iFIST.
· Automatic image installation is implemented through customizing the automatic installation scripts for operating systems. For example, you must customize a ks.cfg file for Linux operating systems and an Unattend.xml file for Windows operating systems. First configure related parameters on FIST. When a server configuration template is bound to a device, FIST will mount the image file to the target server through KVM and start the server through iFIST. After iFIST starts, FIST sends related configurations to iFIST. Then, iFIST will install the OS for the server.
· Image cloning is implemented through copying image files. Image cloning reduces the application and driver installation time. FIST starts iFIST on the server. Then, FIST can cooperate with iFIST to partition the target drive and copy the startup files and OS files to the corresponding partition.
|
|
NOTE: · You can specify an installation drive for image installation and image cloning. Make sure the operating system is not installed in a data drive. Otherwise, the user data might be lost. · A ks.cfg file is used for automatic Linux operating system installation. In this file, you can configure parameters such as the username and password. There is a set of detailed syntax specifications for ks.cfg files. For more information, see the documents provided by the operating system vendors. · Similar to a ks.cfg file, an Unattend.xml file is used for automatic Windows operating system installation. |
Installing drivers
A server configuration template supports driver settings. In the driver settings, you can select the drivers to be installed when you select an operating system image of a vendor. The driver sources are the repositories uploaded by a user. After you select a repository, FIST mount the repository to KVM and starts iFIST. After iFIST starts, iFIST copies the driver packages to the target drive, and automatically inserts a new deployment phase between the OS installation completion and the first OS usage. In this new phase, iFIST will automatically execute related scripts to automatically install drivers.
Switch templates
A switch template is a backup switch configuration file. FIST exports the backup switch configuration file through NETCONF and saves it on the FIST server. On FIST, you can export, import, and delete switch templates. To avoid management IP address conflicts, FIST does not modify the management IP address of a switch when importing a switch template to the switch.
Enclosure templates
In an enclosure template, you can configure one-to-one bindings between server templates and enclosure slots. After you apply an enclosure template to an enclosure, FIST binds the server templates to the enclosure slots according to the settings in the enclosure template. Whenever a server is installed in a slot of the enclosure, FIST automatically configures the server by using the bound server template.
Address pools
You can create IPv4 address pools, IPv6 address pools, and host name pools in FIST. After creating address pools, you can select a host name pool, IPv4 address pool, or IPv6 address pool rather than manually configure it in the OS Settings area when adding a server template. This feature significantly improves the configuration efficiency.
Networks
You can create network templates. In a network template, you can configure the VLAN IDs, PVID, and VLAN tunnel for a port and the maximum network bandwidth. You can use a network template together with a rack server to configure the VLAN IDs for the switch's interface connecting to the rack server's service interface. If the VLAN for system traffic changes, use this function together with the “Connection settings” feature to fast change the VLAN for the connected network port. When you use a network template together with an enclosure server, you can configure services for the whole network channel from the blade server service interfaces to the interconnect module.
Interconnect modules
An interconnect module refers to the network switching control unit within the enclosure, provides the data switching function for blade servers in the enclosure, and also centrally provides external data interfaces for the blade servers to communicate with the external network. FIST supports configuring the connection mode for the interconnect module's uplink interfaces. Available connection modes include dynamic aggregation, static aggregation, and master/standby. Additionally, you can select a network template. An interconnect module template can help users to implement the network channels among the blade servers, interconnect module downlink interfaces, and uplink interfaces, which effectively solves the network isolation, blocking, and security redundancy issues.
Update components
Introduction
Components collectively refer to the hardware (HDM, BIOS, CPLD, RAID, NIC, and so on) drivers and firmware. This feature allows you to update components of servers. In the current software version, the following features are supported:
· Inventorying the repositories uploaded by users, and displaying the version number and basic information of each component.
· Automatically comparing component versions in a repository and component versions on a server. When the component versions in the repository are later, FIST will recommend installing the repository.
· Downgrading, update within the same version, and upgrading.
The remote component update feature delivers the following benefits:
· Supports customizing repositories, and improves the O&M flexibility and accuracy.
· Supports bulk update, improves the O&M efficiency, and reduces the O&M costs.
· Available in multiple scenarios, and basically meets the requirements of all customers.
Operating mechanism
FIST supports multiple component update methods, including component update, offline firmware update, out-of-band HDM firmware update, and automatic driver installation.
· Component update—Component update includes updating firmware through the out-of-band network and updating firmware or drivers through an in-band network. In out-of-band component update, FIST calls the RESTful APIs of HDM to update the components. This feature must be used together with HDM and repositories. Out-of-band component update depends on HDM. In the current software, this method can update only HDM, BIOS, and CPLD firmware. Out-of-band component update requires only FIST to connect to the HDM management network, and can be completely separated from the customer service network. For hardware drivers and components that cannot be updated by using HDM, use in-band component update. This feature must be used together with FIST SMS and repositories. Because FIST SMS runs in the customer's operating system, FIST must be connected to the customer service network when this feature is used. FIST sends the component packages selected by the user to the operating system of the customer through TCP. FIST SMS will use these component packages to update components.
· Offline firmware update—This feature is used when no operating system is installed on the server and the out-of-band component update feature cannot be used to update all components. This feature must be used together with FIST and repositories. FIST mounts a repository image to the server to update through KVM, and then starts the server with the image. After the repository image is started, it will call the update script to update the firmware.
· Out-of-band HDM firmware update—This feature applies to the scenario where the current service cannot be immediately restarted on the server and only the out-of-band network is available. This feature must be used together with HDM, iFIST, and repositories. FIST uploads the repository file to the HDM for storage. After the server is restarted the next time, the server automatically enters iFIST. iFIST will update the firmware for the server.
· Automatic driver installation—This feature automatically installs the selected drivers when FIST is installing an operating system. This feature must be used together with iFIST and repositories. For more information about automatic driver installation, see “Installing drivers.”
Repositories and repository inventory
Add a repository
FIST allows you to add a repository through a UNC path, HTTP path, or local path. An HTTP path uses the HTTP protocol for communication. A UNC path uses the SMB protocol for communication. A local path is a path in the FIST running environment.
Inventory a repository
After adding a repository, you can inventory it. Inventorying a repository is to copy the repository from the specified path to the FIST installation directory, read the component information from the repository, and display the information on FIST. Component information includes the component name, component description, component version, supported update method (HDM or FIST SMS), and whether reboot is required.
Create a custom repository
FIST allows you to create a custom repository. To add a custom repository, you must first add a standard repository. Then, you can use certain criteria to obtain the required components. FIST will automatically package the selected components into a custom repository. A custom repository is easy to transmit, which improves the O&M flexibility and accuracy. Alternatively, you can add a custom repository at supportrepo.h3c.com.
Deploy a node or node group
A node is a single server. A node group is a set of servers. Deploying a node or node group means to update server components. FIST supports updating a node or a node group.
· In cooperation with HDM, FIST can perform out-of-band component update for HDM, BIOS, and CPLD firmware.
· In cooperation with FIST SMS, FIST can perform in-band component update for HDM, BIOS, and CPLD firmware, various optional modules, and hard disk drivers and firmware.
· In cooperation with repositories, FIST can perform offline component update for HDM, BIOS, and CPLD firmware, various optional modules, and hard disk firmware.
· In cooperation with HDM, iFIST, and repositories, FIST can perform out-of-band HDM firmware update, and update the firmware for optional cards and hard disks.
· Through the system settings function in a server configuration template, the selected drivers can be automatically installed after operating systems are installed on servers.
· If FIST also runs on a server, FIST can update components for the local node.
DHCP server
Introduction
FIST is integrated with the DHCP server feature through implementing the related DHCPv4 protocols. This feature automatically allocates HDM management IP addresses or system IP addresses to servers on the same LAN. FIST supports the following IP address allocation methods:
· Dynamic method—When a client requests an IP address from the DHCP server, the DHCP server automatically selects an IP address from the IP pool and assigns the IP address to the client.
· Static method—Manually binds an IP address to a client. When the client requests an IP address from the DHCP server, the DHCP server assigns the bound IP address to the client.
PXE server
Introduction
Pre-boot eXecution Environment (PXE) provides a mechanism of using a network interface to boot servers. FIST is integrated with a PXE server, which allows you to bulk install operating systems on servers. The PXE server of FIST supports multiple BootLoader configuration options, including PXELINUX, GRUB2, and iPXE. Additionally, you can customize the installation parameters when installing RedHat Linux Enterprise and CentOS images.
Restrictions and guidelines
PXE servers are supported only when FIST runs in an AE module.
Software push and installation
Introduction
FIST supports bulk pushing software products to the server operating system and bulk installing these software products in the system. FIST uses the WinRM technique in the Windows operating system and uses the SSH technique in the Linux operating system to push software products to the operating system and execute the corresponding system command. At the same time, the software push and installation feature supports bulk installing FIST SMS. Other functions
Introduction
Network settings
FIST supports setting the IP address, mask, and gateway for user access. At the same time, to enable FIST to access external networks, FIST supports interoperating with DNS and proxy servers.
Time settings
FIST allows you to manually set the time and interoperate with the NTP server. This feature allows you to manually set or automatically update the system time for the environment where FIST resides.
Acronyms
|
Term |
Definition |
|
AE |
APP Engine. A special node in an enclosure. FIST runs in this node. |
|
BMC |
Baseboard Management Controller. |
|
BIOS |
Basic Input Output System. |
|
CPLD |
Complex Programmable Logic Device. |
|
CPU |
Central Processing Unit. |
|
DHCP |
Dynamic Host Configuration Protocol. |
|
FIST |
Fast Intelligent Scalable Toolkit. FIST allows you to quickly, flexibly, and intelligently configure and use servers, for example, configure HDM&BIOS settings, update firmware, and view server information. Additionally, FIST allows users to develop tools based on FIST. |
|
FIST SMS |
FIST System Management Service, which is in-band server management software in cooperation with FIST. |
|
GUI |
Graphical User Interface. |
|
HDM |
Hardware Device Management, BMC developed by H3C. |
|
iFIST |
Integrated Fast Intelligent Scalable Toolkit. |
|
IPMI |
Intelligent Platform Management Interface, a standard hardware management interface that uses HDM to perform out-of-band management. |
|
OM |
Onboard Manager, a management module for an enclosure. |
|
OS |
Operating System. |
|
PXE |
Preboot eXecution Environment. |
|
RAID |
Redundant Arrays of Independent Disks. |
|
winRM |
Windows Remote Management. |
|
DNS |
Domain name resolution. |
|
NTP |
Network Time Protocol. |
|
LDAP |
Lightweight Directory Access Protocol. |