- Released At: 17-04-2024
- Page Views:
- Downloads:
- Table of Contents
- Related Documents
-
IP-SGT Mapping Technology White Paper
Copyright © 2024 New H3C Technologies Co., Ltd. All rights reserved.
No part of this manual may be reproduced or transmitted in any form or by any means without prior written consent of New H3C Technologies Co., Ltd.
Except for the trademarks of New H3C Technologies Co., Ltd., any trademarks that may be mentioned in this document are the property of their respective owners.
The content in this article is general technical information, and some information may not be applicable to the product you have purchased.
Contents
Decoupling security groups from VLANs
Storing IP-SGT mapping entries
Security group decoupling with VLAN (in AP local forwarding)
Multi-campus isolated domain (IP-transit)
Overview
Technical background
In traditional networks, only access authentication devices can receive and execute access policies issued by the EIA server, which restricts the user's access permissions on the connected device. Other devices in different locations cannot receive and execute access policies from the EIA server. Additionally, traditional networks typically divide permissions based on geographical location (such as VLAN or IP network segments). If a user's IP address changes after moving, it is not guaranteed that the user will still have the same network access permissions.
The IP address - Security Group Tag (IP-SGT) policy enables role-based policy segmentation by decoupling the association between user roles and the IP address. It binds user roles with security groups, allowing the same user to obtain the same access rights after authentication in different isolation domains. Additionally, the IP-SGT policy uses the EIA server to push user and security group mapping information to the subscribed devices, overcoming the limitation of authentication points being the policy execution points, thereby solving the issue of policy portability across different isolation domains.
Benefits
The IP-SGT mapping technology has the following advantages:
· Improve management efficiency by planning permissions using security groups.
· Achieve synchronized sharing of authenticated user information to enhance network control capabilities.
· Authentication points and policy execution points can be separated, enhancing the flexibility of network configuration.
· In the field of wireless services, decoupling the security group from VLAN enhances the specifications of the security group.
· Break through the geographical restrictions of the park, support the policy of multiple parks across isolated domains (IP-Transit) scenario.
IP-SGT mapping implementation
Concepts
Isolation domain
Isolation domains are used to segregate customer networks. An isolation domain has the same IP address section, while different isolation domains have different IP address sections. Isolation domains are generally divided based on physical locations, for example, a campus of a company, a hospital zone, or a school campus.
Microsegmentation
Microsegmentation, also known as security isolation based on fine-grained grouping, is essentially traffic control based on the group identification of packet segmentation. For instance, servers in the data center network are grouped according to certain principles, and traffic control policies are then deployed based on these groups, thus achieving the goals of simplified maintenance and security management.
Each microsegmentation section has a globally unique ID.
Security group
|
|
NOTE: · During the implementation of security group features, the security group can also be referred to as microsegmentation. The 'label' ID value set when creating a security group is the authorization microsegmentation ID that the EIA server issues to the device. · Microsegmentation technology can associate users with security groups (microsegmentation) and decouple users from IP address sections. When the same user authenticates online in different isolation domains using the same account/cipher, the EIA server will authorize the same microsegmentation ID based on the account/cipher, thereby realizing network mobility across isolation domains and policy following. |
A security group is a safety isolation scheme based on logical grouping. Communication objects (individual terminals, printers, and servers) within a certain zone with the same security isolation requirements can be divided into one security group. Inter-group policies are deployed between different security groups to control access amongst them. Users belonging to the same security group can gain the same access rights wherever they log in.
The security group supports segmentation across isolation domains, allowing users within different domains to belong to the same security group. The inter-group policy of the security group no longer needs to be configured based on each IP address section, effectively reducing the scale of the inter-group policy configuration matrix. Compared to traditional access control methods (VLAN+ACL), the network management scheme based on security groups greatly reduces the workload of the administrator.
System architecture
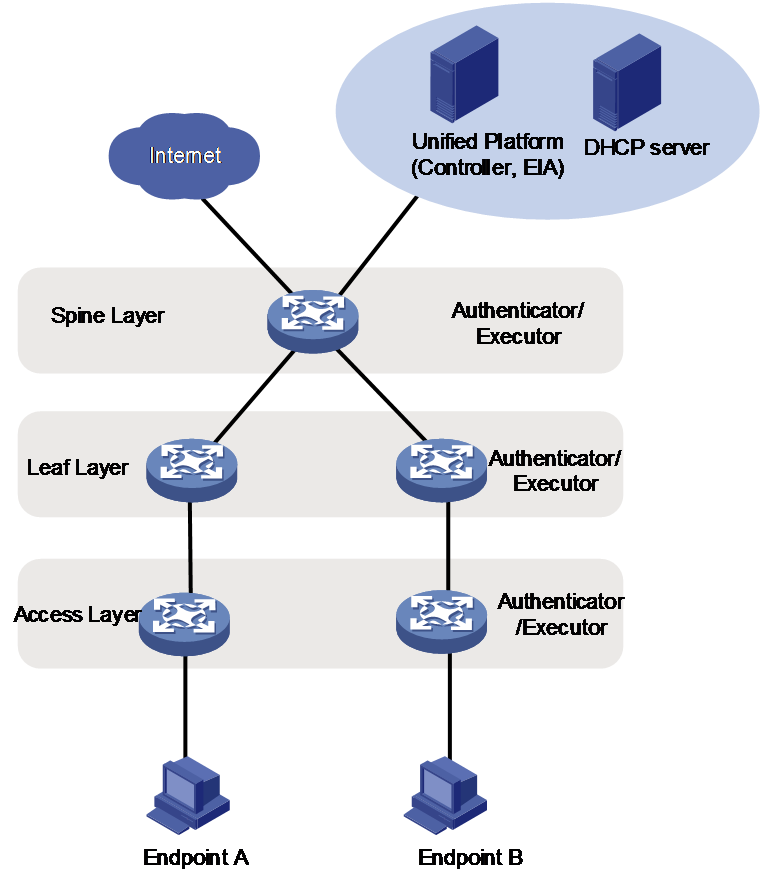
Figure 1 IP-SGT mapping system architecture
As shown in Figure 1, the device roles in the IP-SGT policy following system schema include:
· Unified Platform: Refers to Unified Platform installed on physical servers, which can complete user authentication and policy distribution by deploying controller, EIA server, and other components on Unified Platform.
¡ Controller: Manages device, creates security group and configures group policy.
¡ EIA server: Completes user authentication, authorization, and accounting; Selects devices under the control of the controller for subscription, and pushes IP-SGT mapping entries to subscribed devices.
· DHCP server: Responsible for allocating IP addresses to users. The DHCP server can be deployed on a separate physical server or as a component in Unified Platform.
· Authenticator: Responsible for authenticating access users. The authenticator device can be deployed in the access layer, distribution layer, or core layer.
· Executor: It is a subscribing device for the EIA server, which receives the IP-SGT mapping entries pushed by the EIA server, and controls user access rights. The executor can be deployed at the distribution layer or the core layer. The authenticator and the executor can be the same device or different devices.
· Endpoint: User equipment that requests access to the local area network (LAN). It is authenticated by the authentication devices within the LAN.
Mechanism
The implementation of the IP-SGT policy following tech mainly relies on the following three mechanisms:
· Dynamic mapping mechanism: The EIA server dynamically records the mappings between user IP addresses and security groups.
· IP-SGT subscription mechanism: The EIA server pushes IP-SGT mappings to the IP-SGT subscribed devices.
· Inter-group access control mechanism: The controller defines the security group and group policies, and issues inter-group access control policies to authenticators and executors.
|
|
NOTE: Unless specifically stated, the mentioned authenticators in this article only perform user authentication, and the IP-SGT mapping function is only enabled on the executing dot devices. |
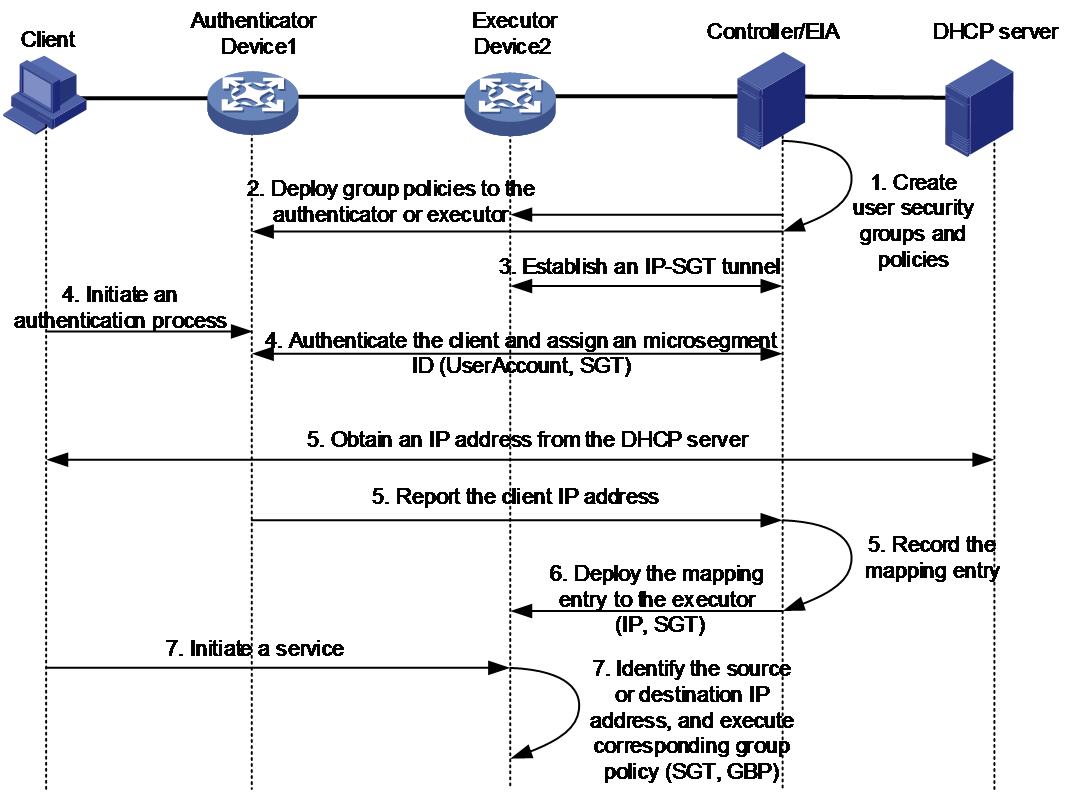
For example, when the authenticator and executor are not on the same device, the IP-SGT policy's accompanying work mechanism is shown in Figure 2.
Figure 2 Schematic Diagram of the IP-SGT Working Mechanism
1. The administrator completes the definition of the security group and group policy on the controller, and synchronizes the security group and group policy information to the EIA server.
2. During the automation deployment stage, the controller sends group policy information (Info) to the authenticator and executors.
3. An IP-SGT channel is established between the EIA server and the executor, which is used to push IP-SGT mapping entries.
4. The user initiates authentication.
5. After successful authentication, the EIA server assigns a microsegmentation ID to the user based on their login information, which adds the user to a specific security group.
6. After successful authentication, the client obtains the IP address from the DHCP server.
7. The authenticator reports the user's IP address to the EIA server.
|
IMPORTANT: · For users going through Portal authentication, since they have already obtained an IP address from the DHCP server prior to authentication, they will report the IP address during the authentication process. · For users authenticated via 802.1X, MAC authentication, and Web authentication, they report the acquired IP address through charging messages after passing the authentication. |
8. The EIA server records and maintains the mappings of user IP addresses to microsegmentation IDs.
9. The EIA server collects IP-SGT mappings and pushes them to the execution point device via the IP-SGT channel. After receiving the entry, the execution point device reports it to the route management module. The route management module then issues the FIB forwarding table, which includes the MicroSegID properties in the FIB forwarding entry corresponding to the user IP address. The driver stores the IP-SGT mapping entry through hardware resources based on the FIB forwarding table. When the user goes offline, the EIA server notifies the execution point device to delete the corresponding IP-SGT mapping entry.
10. The client transmits business traffic.
11. When the executor receives traffic messages, it identifies the source or destination IP address of the message, and queries the FIB table to obtain the corresponding microsegmentation ID. Then, it controls the network access permissions between different security groups based on the inter-group policies of the microsegmentation to which the source/destination IP address belongs.
Decoupling security groups from VLANs
In the traditional VXLAN network environment, since the wireless AC does not support authorization of VSI, once the wireless authentication user goes online, the EIA server needs to first authorize a corresponding VLAN based on the user's security group. After the user matches the Ethernet service instance belonging to that VLAN, they enter the related VXLAN and link up with the security group. In this scenario, one VLAN ID can only correspond to one security group. Since there are only 500 VLAN IDs allocated for security groups, the number of security groups in this scenario cannot exceed 500.
|
|
NOTE: The Ethernet service instance requires defining matching VLAN ID and associating it with VSI, which is also associated with the security group the user belongs to. The Ethernet service instance can be issued to the Leaf device interface connected to the AP via the controller, or it can be manually configured on the Leaf device interface. |
After adopting the IP-SGT policy follow-up function, wireless users no longer need to gain security group information through authorization VLAN, i.e., the security group and VLAN are decoupled. The specifications for security groups are not limited by the number of VLANs, and can reach up to 4000, to adapt to scenarios that require a large amount of security group planning. During wireless user authentication, the AC only returns the authentication result, no longer authorizing VLAN. Policy execution points can directly subscribe to IP-SGT mapping entries from the EIA server via the IP-SGT channel, thereby obtaining the corresponding security group information for user IPs.
Storing IP-SGT mapping entries
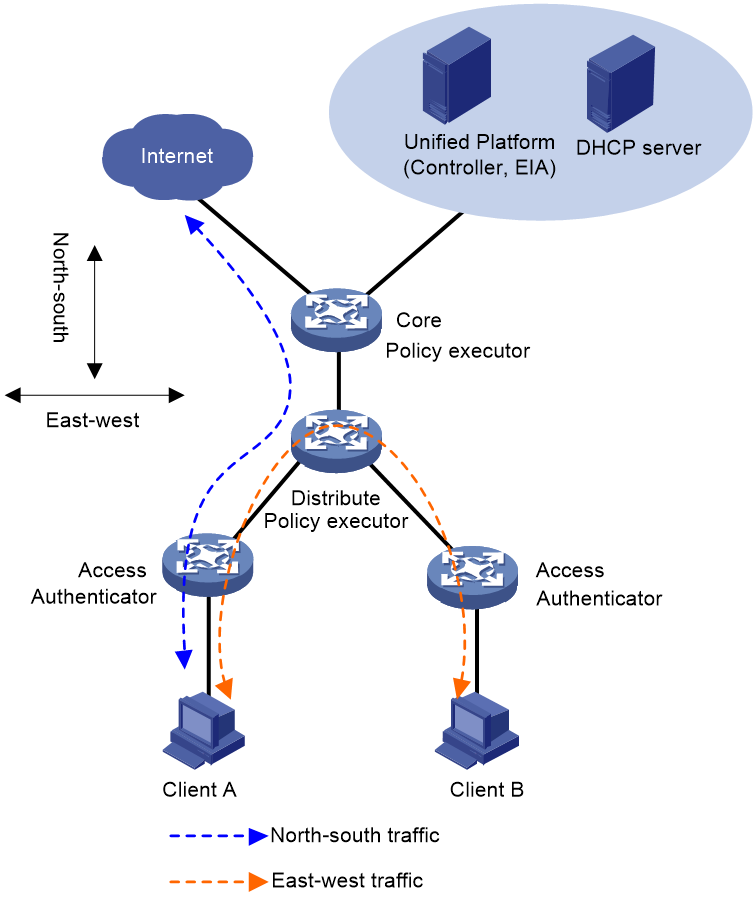
By default, all IP-SGT mapping entries pushed by the EIA server are stored in the device via hardware resources. When receiving a message from the corresponding IP address, the microsegmentation ID can be directly matched by querying the FIB forwarding table and the corresponding group policy is executed to improve transmission efficiency. However, as shown in Figure 3, in network groups where north-south traffic is high and east-west user traffic is low, if the execute device is on a link with fewer message exchanges, storing all pushed IP-SGT mapping entries on the execute device will waste a significant amount of hardware resources.
The device can improve forwarding efficiency and conserve hardware resources by storing IP-SGT mapping entries on-demand, based on network segments. Upon implementing on-demand address network segmentation, the device won't store the IP-SGT mapping entries corresponding to IP addresses in that network segment. Only when user traffic packets received have a source IP address within the on-demand address network segment does the device store its corresponding IP-SGT mapping entry. Upon receiving traffic with the same source IP address subsequently, traffic can be processed directly based on intergroup policy by querying the FIB forwarding table to match the microsegmentation ID and group policy.
Figure 3 Diagram of user traffic for on-demand storage of IP-SGT mapping entries
Restrictions and guidelines
The feature requires the use of iMC EIA server and SeerEngine-Campus controller. The DHCP server used must be a tightly coupled vDHCP server OR a Microsoft DHCP server.
Application scenarios
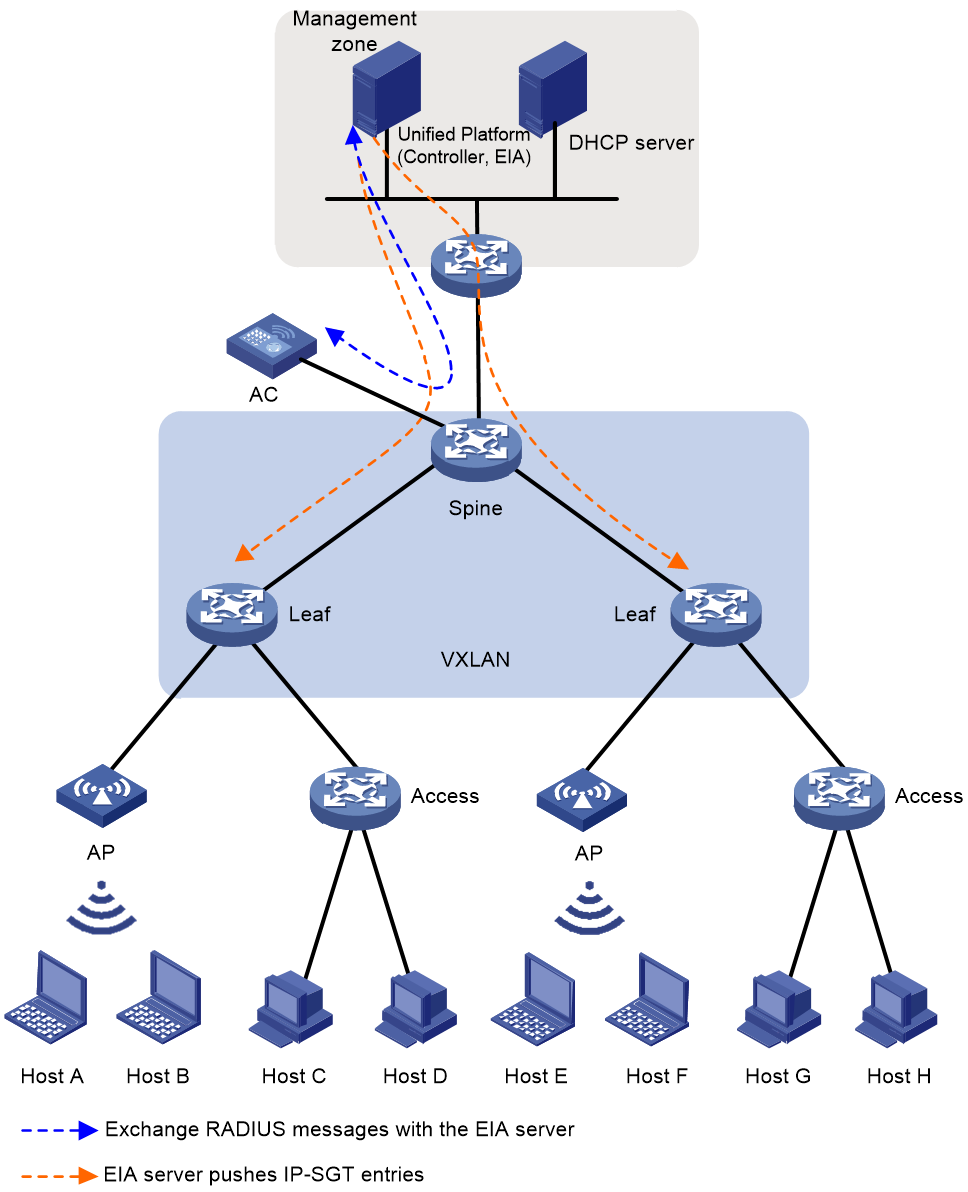
Security group decoupling with VLAN (in AP local forwarding)
As shown in Figure 4, under the local forwarding mode of AP, the AC acts as the wireless user authenticator, and the Leaf device serves as the policy executor. For wireless users, after authentication, the EIA server pushes the IP-SGT mapping entries to all policy-executing devices via the IP-SGT channel without associating the microsegmentation ID through authorization VLAN, thereby decoupling the security group and VLAN.
Figure 4 Decoupling security group with VLANs
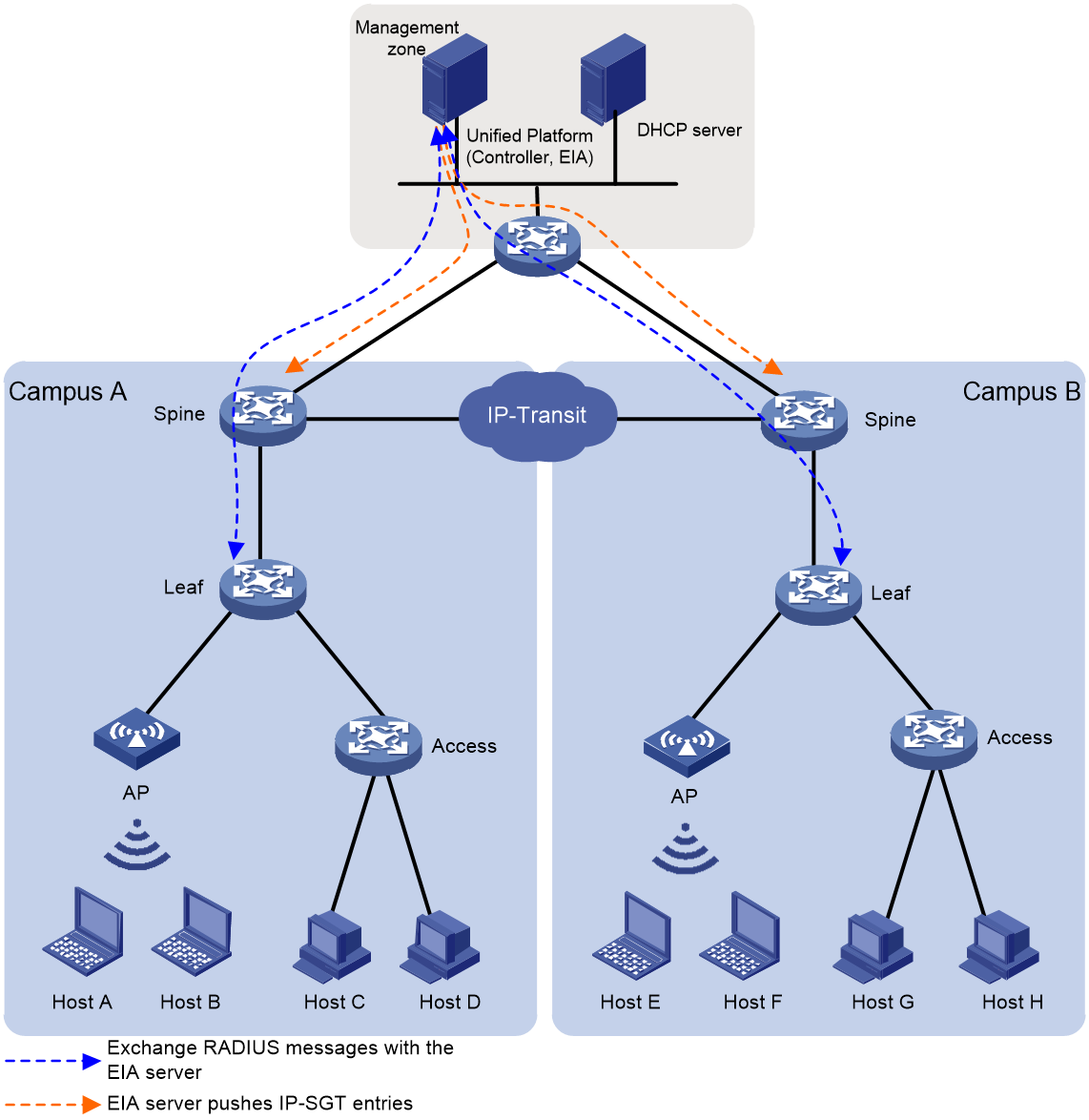
Multi-campus isolated domain (IP-transit)
As shown in Figure 5, in the multi-campus cross-isolation domain (IP-Transit) scenario, Campus A and Campus B belong to different isolation domains. Inter-domain traffic does not use EVPN interconnection nor pass through VXLAN encapsulation, instead, it directly uses IP packet for transmission.
In this scenario, the border device Spine, acting as the policy execution point, subscribes to the IP-SGT mapping information from the EIA server. Once user authentication is successful, the EIA server will push the IP-SGT mapping entries to the border device. Therefore, the border device will have the corresponding relationship between the user IP and SGT from other isolation domains. When users interact across isolation domains, policy control can be executed on the border device of the local isolation domain, controlling traffic forwarding.
Figure 5 Multi-campus isolated domain (IP-transit)