- Released At: 12-05-2025
- Page Views:
- Downloads:
- Table of Contents
- Related Documents
-
DHCP Attack Protection Technology White Paper
Copyright © 2024 New H3C Technologies Co., Ltd. All rights reserved.
No part of this manual may be reproduced or transmitted in any form or by any means without prior written consent of New H3C Technologies Co., Ltd.
Except for the trademarks of New H3C Technologies Co., Ltd., any trademarks that may be mentioned in this document are the property of their respective owners.
The content in this article consists of general technical information, some of which may not be applicable to the product you have purchased.
Contents
Implementation of DHCP attack prevention
Introduction to DHCP attack prevention
DHCP starvation attack prevention function
DHCP flood attack prevention functions
DHCP interface attack suppression
DHCP snooping packet rate limiting
Limiting the maximum number of DHCP snooping entries dynamically learned on an interface
Bogus DHCP server attack prevention function
Preventing forged DHCP requests
Integrated networking with DHCP attack prevention technologies deployed
Overview
As the scale of the network expands and the complexity of the network environment increases, DHCP services are being applied to more and more network environments. Although DHCP provides a simple and efficient host configuration mechanism, it has many security vulnerabilities due to insufficient consideration of security factors in its design, making DHCP servers vulnerable to attacks.
This document summarizes the technical features and application scenarios of H3C DHCP attack prevention functions, aimed at various common DHCP attacks, to help users better utilize these functions. For details about DHCP, see DHCP Technology White Paper.
Types of DHCP attacks
In real networks, the following DHCP attack types are supported:
· DHCP starvation attack.
· DHCP flood attack.
· Bogus DHCP server attack.
· Forged DHCP request.
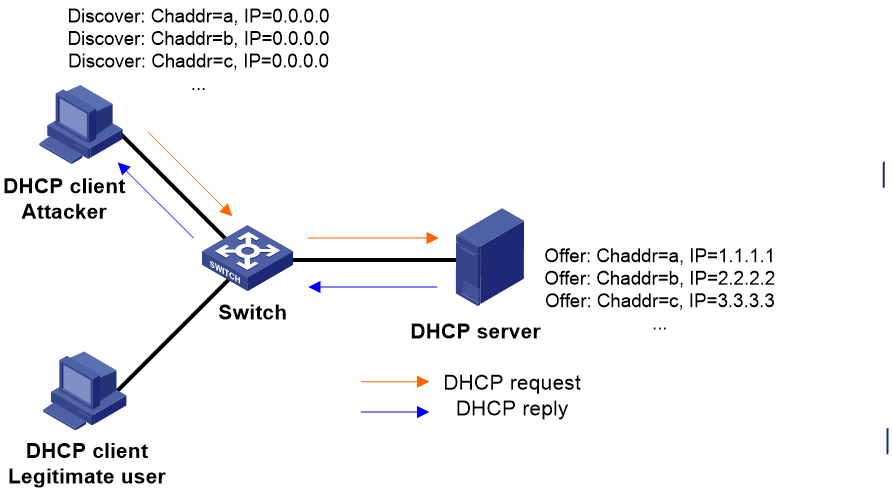
DHCP starvation attack
The attacker generates fake DHCP requests with different client hardware address (chaddr) values, applying for a large number of IP addresses from the DHCP server. This not only exhausts the address pool of the DHCP server, making it unable to allocate IP addresses to legitimate DHCP clients, but also possibly overloads the server system resources, preventing it from processing regular operations.
Figure 1 DHCP starvation attack
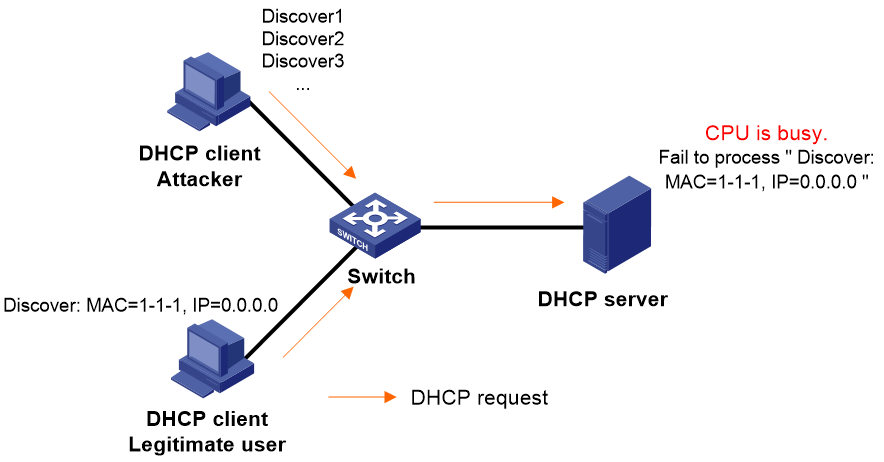
DHCP flood attack
The attacker maliciously transmits a large number of DHCP request messages to the DHCP server in a short period of time to apply for an IP address. This occupies the system resources of the DHCP server, disabling other legitimate DHCP interactions from proceeding normally.
Figure 2 DHCP flood attack
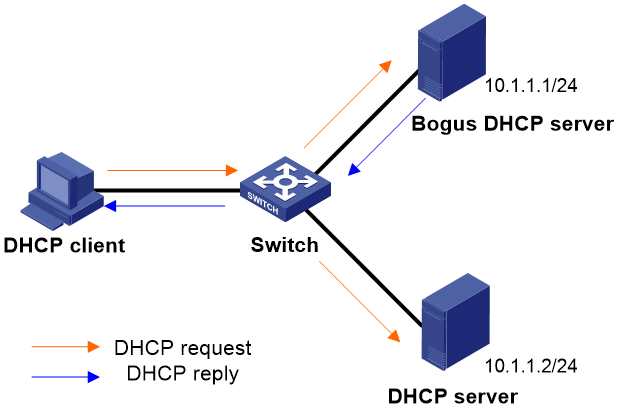
Attack by bogus DHCP server
After illicitly installing and running a DHCP server program, an attacker disguises as a DHCP server. The DHCP client, upon receiving a DHCP response packet from the DHCP server, cannot determine if the server is legitimate. If the first response packet the client receives is from the fake DHCP server, the server will allocate an incorrect IP address to the DHCP client, preventing the client from accessing the network.
Figure 3 Bogus DHCP server
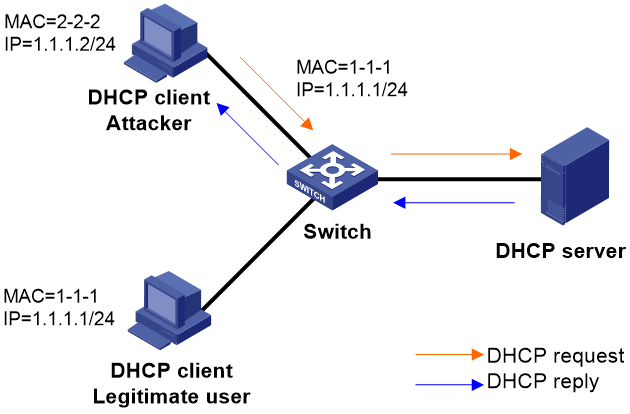
Forged DHCP request
Illegal clients forge DHCP renewal messages, DHCP-DECLINE, and DHCP-RELEASE messages to attack the DHCP server.
· A forged DHCP renewal message attack occurs when an attacker disguises as a legitimate DHCP client, transmitting fake DHCP renewal messages to the DHCP server. This results in the server and client being unable to release their IP address leases as desired. If the attacker sends a large number of forged messages, many IP addresses will be occupied for a long time, leaving the DHCP server without enough addresses to allocate to new clients.
· A DHCP-DECLINE/DHCP-RELEASE message attack occurs when an attacker disguising as a legitimate DHCP client, transmitting forged DHCP-DECLINE/DHCP-RELEASE messages to the DHCP server. This results in the server mistakenly terminating the IP address lease.
Figure 4 Forged DHCP request
Implementation of DHCP attack prevention
Introduction to DHCP attack prevention
For the above common DHCP attack types, the preventive measures and deployment locations are shown in Table 1.
Table 1 DHCP preventive measures
|
Attack class |
Preventive measures |
Deployment location of prevention measures |
|
DHCP starvation attack |
Use the DHCP starvation attack prevention function |
DHCP server, DHCP relay agent, DHCP snooping |
|
When there are numerous DHCP starvation attack packets, use the DHCP starvation attack prevention function and the related functions to prevent DHCP flood attacks simultaneously. |
DHCP server, DHCP relay agent, DHCP snooping |
|
|
DHCP flood attack |
Use the DHCP flood attack protection function |
DHCP server, DHCP relay agent |
|
Use the DHCP interface attack suppression function |
DHCP server, DHCP relay agent |
|
|
Limit the maximum number of dynamic DHCP snooping entries that the interface can learn |
DHCP snooping |
|
|
Use the DHCP snooping packet rate limiting function |
DHCP snooping |
|
|
Bogus DHCP server attack |
Use the DHCP snooping trust function |
DHCP snooping |
|
Forged DHCP request attack |
Use the related function to prevent forged DHCP request attacks |
DHCP snooping |
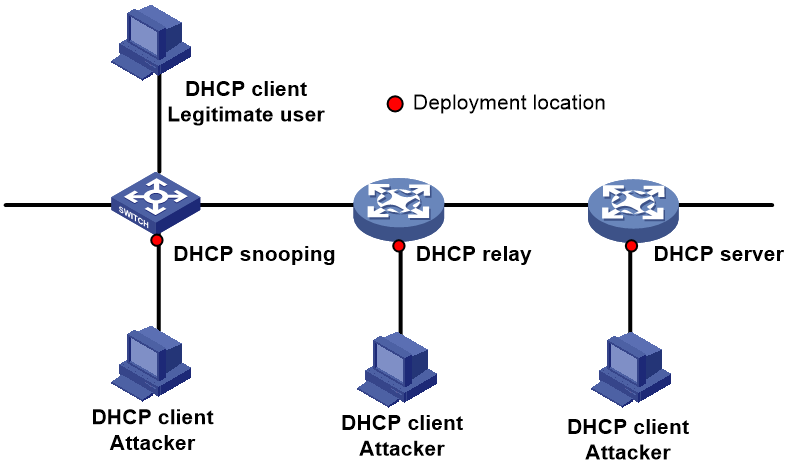
DHCP starvation attack prevention function
The DHCP starvation attack prevention function is used to prevent DHCP starvation attacks. This function is configurable on DHCP servers, DHCP relay, and DHCP snooping devices, and the deployment location is as shown in Figure 5.
Figure 5 Deployment of the DHCP starvation attack prevention function
Different anti-starvation attack measures can be implemented against the source MAC (SMAC) address of the packet transmitted (Tx) by the attacker.
· If the source MAC (SMAC) addresses of the data frames encapsulating the DHCP request messages are all different, the interface accessed by the attacker will learn a large amount of MAC addresses. At this point, by setting the maximum number of MAC addresses that the interface can learn and configuring to prevent forwarding messages whose source MAC address is not in the MAC address table when reaching the upper limit of the interface's MAC address learning, starvation attacks can be mitigated. When the number of MAC addresses learned by the interface reaches the upper limit, the interface will discard request messages whose source MAC address is not in the MAC address table, thus preventing the attacker from applying for too many IP addresses and preventing the DHCP starvation attack. Other client-facing interfaces that are not experiencing DHCP starvation attacks, can still normally obtain IP addresses.
· To prevent starvation attacks, enable the MAC address check function on the DHCP device if the source MAC (SMAC) addresses of the data frames encapsulating DHCP request messages are the same. When this function is enabled, the DHCP device checks whether the chaddr field in the received DHCP request messages is consistent with the source MAC address field of the data frame. If they match, the message is considered legitimate and proceeds to further processing. If they do not match, the message is discarded.
DHCP flood attack prevention functions
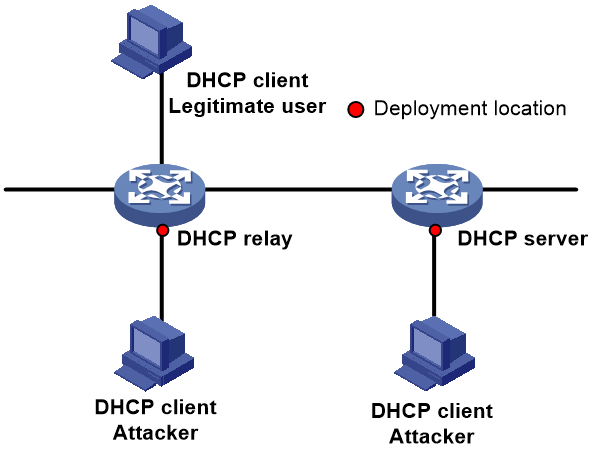
DHCP flood attack protection
The DHCP flood attack protection function is used to defend against flood attacks with fixed source MAC (SMAC) addresses. This function is configurable on DHCP servers and DHCP relay, with deployment locations as shown in Figure 6.
Figure 6 Deployment of the DHCP flood attack protection function
After the DHCP flood attack protection function is enabled on an interface:
1. The DHCP device counts the number of DHCP request messages received based on the source MAC (SMAC) in the DHCP request message. At the same time, it creates a DHCP flood attack protection entry in check state.
2. When the number of DHCP request messages sent by a DHCP client with a certain source MAC address reaches the configured threshold within a certain period, it is considered that the DHCP device has been subjected to a DHCP message attack. The state of the corresponding DHCP flood attack protection entry for this DHCP client is set to restrain state. The DHCP device will discard any subsequent DHCP request messages received from this DHCP client.
3. When the DHCP flood attack protection entry with the source MAC (SMAC) address ages, the number of DHCP request packets received from this DHCP client within a certain period on this interface will be recounted.
¡ If the threshold is not exceeded, the DHCP device will delete this entry. When a DHCP request packet with the same source MAC is received again, the number of received packets will be recounted and a DHCP flood attack protection entry in check state will be established.
¡ If the value still exceeds the threshold, the DHCP device will refresh the DHCP flood attack protection attack entry aging timer and continue to discard the DHCP request packets received from the client.
DHCP interface attack suppression
The DHCP interface attack suppression function is used to prevent DHCP flood attacks on a specific interface. This function is configurable on DHCP servers and DHCP relay. Its deployment location is consistent with that of the DHCP flood attack prevention function.
After the DHCP interface attack suppression function is enabled on an interface:
1. The DHCP device counts the number of DHCP request messages received by the interface and simultaneously creates a DHCP interface attack suppression entry in check state.
2. When the number of DHCP request messages received by the interface reaches the configured threshold within a certain period, it is considered that the DHCP device is under attack by DHCP messages. The state of the DHCP interface attack suppression entry changes from check to restrain. The device will limit the rate at which this interface receives DHCP request messages, to prevent continued CPU impact from DHCP attack messages.
3. When the DHCP interface attack suppression entry expires, the DHCP device will recount the number of DHCP request messages received within the specified time for that interface.
¡ If the threshold is not exceeded, the DHCP device will delete this entry. When the DHCP request packet is received again, the DHCP device will re-count the number of packets received and establish a DHCP interface attack suppression entry in check state.
¡ If the threshold is exceeded, the DHCP device will refresh the aging timer of the DHCP interface attack suppression entry, and continue to limit the rate of DHCP request messages received by this interface.
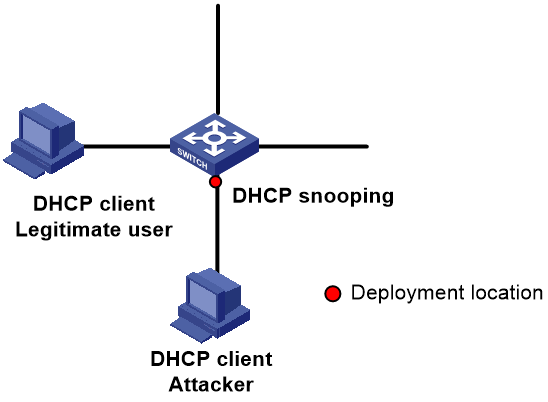
DHCP snooping packet rate limiting
Unauthorized users might transmit numerous DHCP packets, which can potentially initiate unwarranted attacks on the network. To prevent this issue, DHCP snooping supports the packet rate limiting function. This function restricts the rate at which an interface receives DHCP packets. When the interface's DHCP packet reception rate exceeds the maximum number, the DHCP snooping device will discard the excess packets. The deployment location for the packet rate limiting function is shown as indicated in Figure 7.
Figure 7 Deployment of the DHCP snooping packet rate limiting function
Limiting the maximum number of DHCP snooping entries dynamically learned on an interface
This function can prevent the interface from learning too many DHCP snooping entries and occupying excessive system resources. When the number of dynamically learned DHCP snooping entries reaches the maximum, the normal operation of the DHCP snooping function is not affected. However, the interface cannot learn new DHCP snooping entries. The deployment location of this function is consistent with that of the packet rate limiting function.
Bogus DHCP server attack prevention function
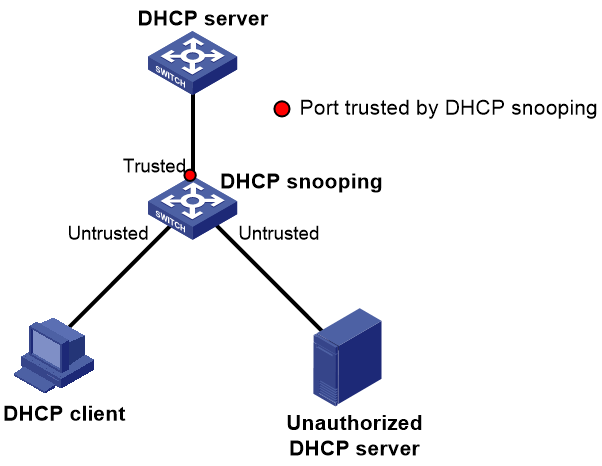
DHCP snooping trust
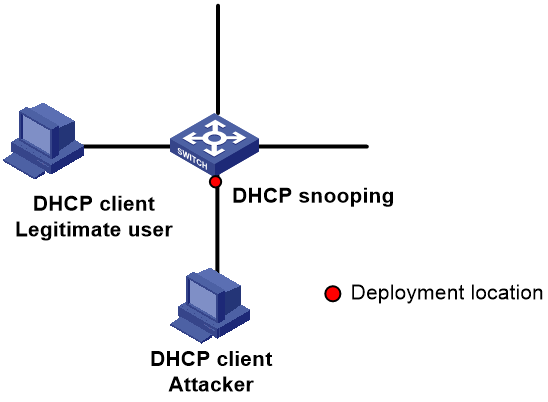
The DHCP snooping trust function controls the source of responses from DHCP servers, effectively blocking fake or illegal servers from allocating IP addresses and other profile information to DHCP clients.
This function divides ports into trusted ports and untrusted ports.
· Sets the ports directly or indirectly connected with the legal DHCP server as trusted ports. A trusted port normally forwards the received DHCP messages, thus ensuring the DHCP client obtains the correct IP address.
· Sets all ports that are not connected to a legal DHCP server as untrusted ports. DHCP-ACK, DHCP-NAK, and DHCP-OFFER messages received from untrusted ports are discarded to prevent DHCP clients from obtaining incorrect IP addresses and network parameters.
The deployment of this function is as shown in Figure 8.
Figure 8 Deployment of the DHCP snooping trust function
Preventing forged DHCP requests
After the DHCP request check function is enabled on the DHCP snooping device, when the DHCP snooping device receives a DHCP request, it will look up for a matching local DHCP snooping entry.
· If there is an entry that matches the request orientation message:
¡ When the message information in the request direction is consistent with the DHCP snooping entry information, the DHCP request is considered legitimate and it is forwarded to the DHCP server.
¡ When the packet information of the request direction is inconsistent with the DHCP snooping entry information, the packet is considered to be a forged DHCP request and is discarded.
· If no DHCP snooping entry matches with the request, the message is considered valid and it will be forwarded to the DHCP server.
The deployment location of this function is shown in Figure 9.
Figure 9 Preventing forged DHCP requests
Integrated networking with DHCP attack prevention technologies deployed
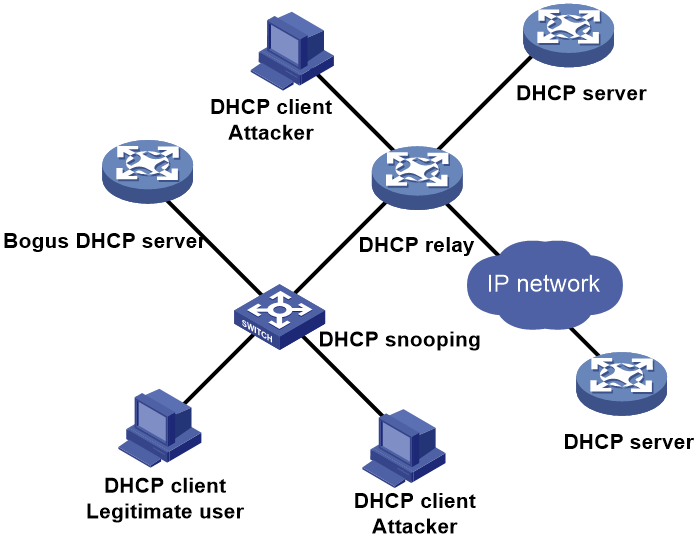
As shown in Figure 10, users dynamically acquire IP addresses across network segments using DHCP. The following measures are taken to prevent DHCP attacks:
· Set the port connected to the DHCP relay device on the DHCP snooping device as a trusted port, and set the remaining interfaces as untrusted ports. This prevents receiving messages from bogus DHCP servers.
· On the interface connected to the attacker on the DHCP snooping device, limit the number of dynamic DHCP snooping entries, configure the rate limiting function of DHCP snooping messages, and enable the DHCP request check function.
· Configure the DHCP starvation attack prevention function, DHCP flood attack prevention function, and DHCP interface attack suppression function for the interface connected to the attacker on the DHCP relay agent.
Figure 10 Comprehensive application of DHCP attack prevention technologies