| Title | Size | Downloads |
|---|---|---|
| 06-Unbinding Area Application-Unbinding Area Application.rar | 2.65 MB |
- Table of Contents
- Related Documents
-
1 Unbinding Area Application
To view this video, click the download link.
Software Version Used
This video was recorded based on the following versions:
l iMC: iMC PLAT 3.20-E2403, iMC UAM 3.20-E0402
l iNode: iNode 2.40-C0341
Web interfaces of different versions may vary.
Application Scenario
An enterprise network is usually divided into multiple areas. In some more sensitive areas, for example, the R&D department, user accounts are required to be bound with access devices or user PCs, while in some less controlled areas, for example, meeting rooms, no binding is required. To allow users to access less-controlled areas without changing their accounts, iMC UAM introduces the concept of unbinding area where binding rules do not apply to access accounts.
Recommended Configuration Flow
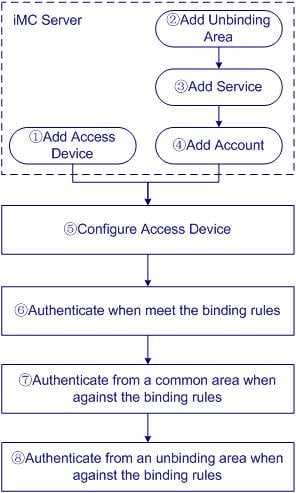
Step1 Add Access Device.
Add an access device that supports 802.1X and AAA to the iMC system, so that the access device can cooperate with the iMC system to deliver 802.1X and AAA features.
Step2 Add Unbinding Area.
An unbinding area is identified by the IP address of the access device in that area. When users access the network through the access device configured for the unbinding area, they are not constrained by binding rules.
This step shows how to configure the access device of an unbinding area in iMC.
Step3 Add Service.
A service is a set of policies for user authentication and authorization.
The service configured in this step includes the unbinding area (configured at step 2), an access device binding policy (the access device’s IP and access port are to be bound with user account), and a user PC binding policy (the PC’s IP is to be bound with user account). Users using this service are constrained by the access device binding policy and the user PC binding policy.
Step4 Add Account.
Each user accessing the network must have an account configured in the iMC. It contains information such as the account name, password, IP of the access device, access port, and IP address of the user PC.
This step shows how to add an account to the iMC system and apply for the service configured at step 3 for this account.
Step5 Configure Access Device.
An access device is used to control access of users. It authenticates users and denies unauthorized users.
This step shows how to configure a RADIUS scheme, an ISP domain, and the 802.1X feature.
Step6 Authenticate When Binding Rules Are Met.
Create an 802.1X connection, and initiate authenticate using the account configured at step 4. Because this account meets all the access device and user PC binding rules, the user passes authentication.
Step7 Authenticate from Common Area When Binding Rules Are Not Met.
In an area other than the unbinding area, initiate authentication using the account that does not meet the binding rules. The user cannot pass authentication.
Step8 Authenticate from Unbinding Area When Binding Rules Are Not Met.
This step shows that an account that does not meet the binding rules passes authentication in the unbinding area.

