EAD solution at a glance
As shown in the following figure, the EAD solution admits the network access of a user endpoint as follows:
1. When a user attempts to access the network, the EAD solution first verifies the user identity.
2. When the user passes identity verification, the EAD solution performs security authentication on the user endpoint. The following items are examined based on the customized security policy: virus definition upgrade, system updates, whitelisted and blacklisted software, usage of USB storage device and other peripherals, and software and hardware assets.
3. The EAD solution authorizes available network resources to the user based on the security check result. If the user is placed in the isolation zone, the user must fix the endpoint vulnerabilities to pass the security authentication.
4. If the user is unauthenticated or unauthorized, EAD will block the client’s access to the network.
5. After the user passes security authentication, the user is allowed to access the enterprise network. The EAD solution also audits and monitors the endpoint running status and network behaviors of the user.
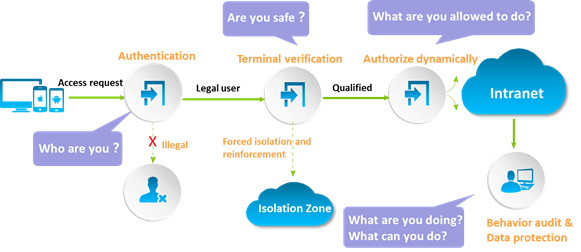
EAD solution workflow
Network architecture
As shown in the following figure, an EAD network includes the following components.
 Security clients—Installed on user endpoints, H3C iNode clients initiate identity authentication and perform the security check on endpoints.
Security clients—Installed on user endpoints, H3C iNode clients initiate identity authentication and perform the security check on endpoints.
 Security collaboration devices—Include switches, routers, and VPN gateway devices. The EAD solution supports various network architectures so that security collaboration devices can be deployed at the access layer or distribution layer.
Security collaboration devices—Include switches, routers, and VPN gateway devices. The EAD solution supports various network architectures so that security collaboration devices can be deployed at the access layer or distribution layer.
 EAD security policy server—Assigns security policies to clients, receives and approves security check results, and authorizes network resources to clients through the security collaboration devices.
EAD security policy server—Assigns security policies to clients, receives and approves security check results, and authorizes network resources to clients through the security collaboration devices.
 Third-party servers—Deployed in the isolation zone, third-party servers include the update server, virus definition server, and security proxy server. If a user passes identity authentication but fails security authentication, EAD places the user in the isolation zone. The user uses third-party servers in the isolation zone to fix security vulnerabilities until it meets the requirement of the security policy.
Third-party servers—Deployed in the isolation zone, third-party servers include the update server, virus definition server, and security proxy server. If a user passes identity authentication but fails security authentication, EAD places the user in the isolation zone. The user uses third-party servers in the isolation zone to fix security vulnerabilities until it meets the requirement of the security policy.
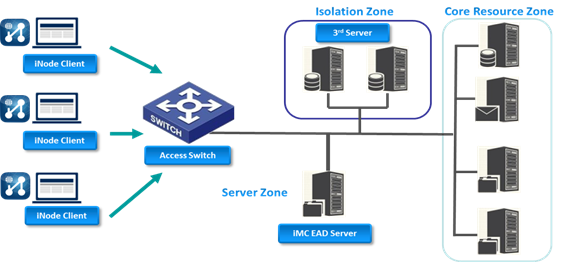
Network architecture of EAD solution
Features and benefits
All-round admission control
With all-round access control, EAD supports LAN, WAN, VPN, and wireless network access methods and can be deployed in a heterogeneous network that contain hubs and Cisco devices. Users can securely access the network from anywhere by using any one of these methods.
Strict identity authentication
The EAD solution supports the following identity authentication types:
 Authentication based on the username and password.
Authentication based on the username and password.
 Enhanced authentication based on the binding between the user identity and specific information of the endpoint (MAC address, IP address, and VLAN) or access device (IP address and port number).
Enhanced authentication based on the binding between the user identity and specific information of the endpoint (MAC address, IP address, and VLAN) or access device (IP address and port number).
 Enhanced authentication through intelligent cards and digital certificates.
Enhanced authentication through intelligent cards and digital certificates.
Complete security state evaluation
The administrator can customize security policies to enable EAD to check the following items on endpoints for security authentication: virus definition version, patch updates, applications, proxy status, dial-up setting, USB storage device, peripheral devices, and desktop assets. EAD clients collaborate with anti-virus products of mainstream vendors, such as Symantec, MacAfee, Trend Micro, and Kaspersky, and supports high-end desktop security products including Microsoft SMS, LANDesk, and BigFix. When EAD works with Microsoft SMS, EAD controls the network access, and SMS manages assets, patch updates, and software distribution and installation in various Windows environments. With this, H3C iMC EAD solution can identify suspected security-compromised devices and do corrective remediation action as well as respond to threats immediately, whether advertently or inadvertently introduced to the network by malicious and innocent actors via external third party devices on a BYOD environment or external devices such as USBs.
Precise privilege control
After a user endpoint passes the security check, EAD assigns an access control policy to the security collaboration device based on the role of the endpoint user. The network behavior of the user is regulated by the policy. EAD allows the administrator to manage endpoint users in a centralized way by configuring the following parameters: user VLANs, ACLs, proxy service, and dual NIC usage.
Flexible customization of security policies
The administrator can customize security policies to enable EAD to apply a security check method and a handling mode based on the user identity (for example, VIP guest, common guest, and employee). Available handling modes include Monitor, Inform, Isolate, and Kick Out.
Comprehensive monitoring and management of desktop assets and peripherals
The EAD solution monitors the endpoint hardware and software usage and changes, and manages desktop assets by managing endpoint asset configuration, unified software distribution, and remote desktop control. It also manages USB storage devices and other peripherals to avoid information leakage, and monitors the user behavior of copying files through the USB storage device.
Easily deployed clients
When a user accesses the network, the EAD server automatically pushes the EAD client to the user endpoint for identification authentication and security check. EAD ensures network security of users without changing their network behaviors.
Multi-level high availability
Stateless failover and hot backup features effectively avoid single point of failure and interruption of the authentication process. If the EAD server fails, users can bypass authentication and access network resources.
Extended and open solution
The extended and open framework of the EAD solution substantially protects user investment. EAD extensively and deeply works with domestic and foreign vendors of virus definitions, operating systems, and desktop security products, and makes full use of their advantages. Based on the standard and open protocols, the interoperation within the EAD framework can be easily implemented.
Application scenarios
EAD solution for a LAN network
Typically, endpoints access the network through switches in an enterprise network. The collaboration between the EAD server and switches performs forced security check on virus definitions and system updates, reducing the risk of virus or worm spreading. The EAD server also assigns security policies to access users through switches to block internal security threats from source, whether the device is connected using wired or wireless.
EAD solution for a WAN network
Branches and partners of a large-scale enterprise typically access the enterprise headquarter through dedicated lines or a WAN network. This access method might bring tremendous security risks to the enterprise internal network. To ensure the security of the internal network, deploy the admission control on the egress router of the branch network or the ingress router or gateway of the enterprise network. Only users who have legal identities and are compliant with security requirement can access the internal network.
EAD solution for VPN access
To allow mobile employees and partners to access the enterprise internal network, EAD cooperates with the VPN gateway to check the security status of user endpoints and assign security policies after these users pass authentication. If a user does not have the security client installed, the administrator can reject or limit the network access of the user.
EAD solution for a WLAN network
As more and more guests and mobile users use wireless NICs to access the enterprise network, security challenges increases. The EAD server works with FIT APs and ACs to perform forced identity authentication and security state check, allowing users to access network securely and quickly.


 Products and Solutions
Products and Solutions
