Full-scale log collection
UBA supports collecting various network logs, including NAT 1.0, Flow 3.0, NetStream V5/V9, NetFlow V5/V9, and DIG logs. When a device does not support any of the logs mentioned above, you can collect traffic on the device through a mirroring port on the device or a network test access point (TAP) and generate DIG logs.
Full-scale log collection
Distributed deployment
UBA uses the distributed architecture, and supports collecting logs on multiple devices and auditing the logs on a unified Web interface. With UBA, the network administrator can flexibly, efficiently monitor the network.
Powerful log auditing
UBA can fast audit network logs according to the following criteria and the combination of them as needed: access usernames, network access time, URLs of visited Web pages, names of files transmitted by FTP, email subject, and so on. Additionally, UBA can flexibly sort, group, and save the audit results.
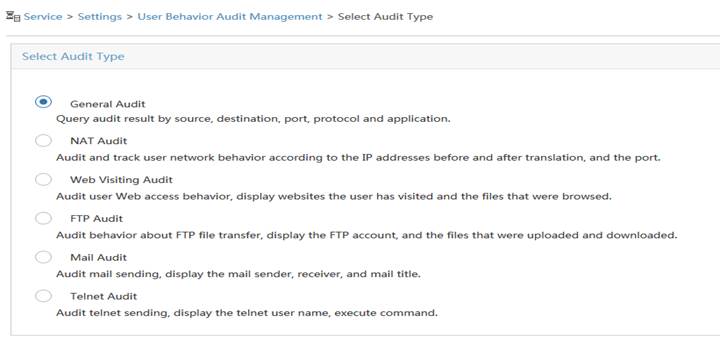
The network administrator can accurately audit the network access behaviors of endpoint users from massive network logs. The log audit results can include the following information: when an endpoint user accesses which website or Web page, what emails an endpoint user sends, what files an endpoint user sends, and so on. Log audit includes the following types:
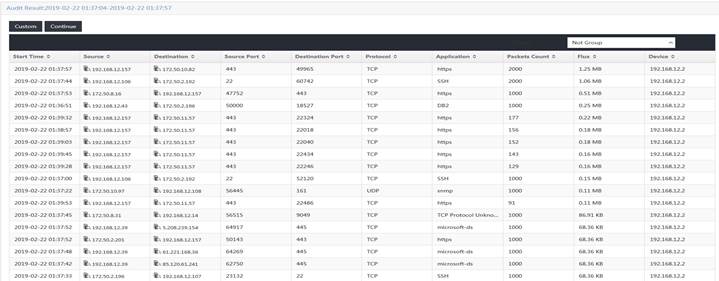
 General audit—Audits the access usernames, network access start time and end time, source and destination IP addresses, source and destination ports, protocols, and applications.
General audit—Audits the access usernames, network access start time and end time, source and destination IP addresses, source and destination ports, protocols, and applications.
 Web visiting audit—Audits the access usernames, network access start time and end time, source and destination IP addresses, ports, visited websites, and visited Web pages.
Web visiting audit—Audits the access usernames, network access start time and end time, source and destination IP addresses, ports, visited websites, and visited Web pages.
 FTP audit—Audits the access usernames, file transmission start time and end time, source and destination IP addresses, ports, FTP usernames, names of transmitted files, and transmission types (upload/download).
FTP audit—Audits the access usernames, file transmission start time and end time, source and destination IP addresses, ports, FTP usernames, names of transmitted files, and transmission types (upload/download).
 Mail audit—Audits the access usernames, mail sending time, source and destination IP addresses, senders, recipients, and mail subjects.
Mail audit—Audits the access usernames, mail sending time, source and destination IP addresses, senders, recipients, and mail subjects.
 NAT audit—Audits the access usernames, network access start time and end time, source and destination IP addresses, source and destination ports, protocols, applications, and IP addresses and ports before and after NAT.
NAT audit—Audits the access usernames, network access start time and end time, source and destination IP addresses, source and destination ports, protocols, applications, and IP addresses and ports before and after NAT.
 Telnet audit—Audits the source and destination IP addresses, ports, Telnet usernames, and executed commands.
Telnet audit—Audits the source and destination IP addresses, ports, Telnet usernames, and executed commands.
UBA log audit
User behavior-based audit
Working with the IMC EAD solution, UBA can efficiently manage network users, record detailed network access logs for users, and provide effective network management and user behavior auditing policies to help the administrator analyze network access behaviors of users.
Layer 7 application auditing
Applications with unfixed port numbers (for example, P2P) are recognized based on the application layer data characteristics of packets. Based on Layer 7 application recognition and classification, UBA can comprehensively audit Layer 7 application usage in the network. UBA configures most common applications with unfixed port numbers as predefined applications, for example, DC, eDonkey, Gnutella, Kazaa, MSN, QQ, and AIM. The administrator can define other applications as needed. Layer 7 application recognition takes effect only on DIG logs, and does not take effect on the other types of logs.
Task-based auditing
UBA provides task-based automatic tracing and auditing, which allows you to customize audit tasks flexibly based on access usernames, visited Web page URLs, and other criteria. After a task is customized, UBA will automatically trace and audit all users and their logs matching the criteria within the specified time range. Audit tasks include NAT audit, Web visiting audit, FTP audit, mail audit, and so on.
Log export
UBA supports exporting massive logs. You can regularly export the sensitive logs and the logs that cannot be saved because of limited database space to a database file to save them in a different place. Additionally, UBA provides a tool for users to query exported logs.
Auditing reports
UBA provides professional reports, including TopN reports by visited website, session count, application distribution, and unknown application and analysis reports for applications such as SMTP, HTTP, and FTP. Each report can be output in the graph or list form with the statistics collection period as day, week, and so on. With these reports, the administrator can clearly know the network usage conditions of users.


 Products and Solutions
Products and Solutions
