- Table of Contents
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 01-Denying Access to a Specific Subnet by Using Packet Filtering | 69.62 KB |
Denying Access to a Specific Subnet by Using Packet Filtering
Copyright © 2024 New H3C Technologies Co., Ltd. All rights reserved.
No part of this manual may be reproduced or transmitted in any form or by any means without prior written consent of New H3C Technologies Co., Ltd.
Except for the trademarks of New H3C Technologies Co., Ltd., any trademarks that may be mentioned in this document are the property of their respective owners.
The information in this document is subject to change without notice.
Contents
Introduction
The following information provides examples for denying access to a specific subnet by using packet filtering.
Prerequisites
This document is not restricted to specific software or hardware versions. Procedures and information in the examples might be slightly different depending on the software or hardware version of the device.
The configuration examples were created and verified in a lab environment, and all the devices were started with the factory default configuration. When you are working on a live network, make sure you understand the potential impact of every command on your network.
The following information is provided based on the assumption that you have basic knowledge of ACL.
Configuration example
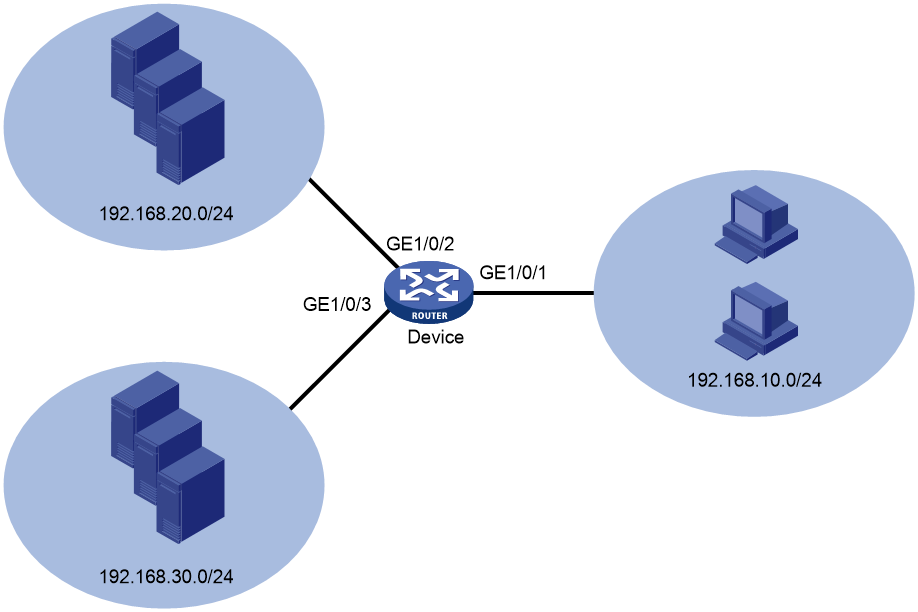
Network configuration
As shown in Figure 1, the device acts as the gateway for the 192.168.10.0/24, 192.168.20.0/24, and 192.168.20.0/24 subnets. Configure ACLs to meet the following requirements:
· Prevent hosts on the 192.168.10.0/24 subnet from accessing servers on the 192.168.20.0/24 subnet, and allow hosts on the 192.168.20.0/24 subnet to access servers on the 192.168.30.0/24 subnet.
· Prevent hosts on any other subnet to access servers on the 192.168.20.0/24 and 192.168.30.0/24 subnets.
Analysis
To prevent hosts on a subnet from accessing hosts on another subnet, configure an ACL on GigabitEthernet 1/0/1 to deny the incoming packets with a destination IP address on the destination subnet.
Procedure
# Assign IP addresses to interfaces.
<Device> system-view
[Device] interface gigabitethernet 1/0/1
[Device-GigabitEthernet1/0/1] ip address 192.168.10.1 24
[Device-GigabitEthernet1/0/1] quit
[Device] interface gigabitethernet 1/0/2
[Device-GigabitEthernet1/0/2] ip address 192.168.20.1 24
[Device-GigabitEthernet1/0/2] quit
[Device] interface gigabitethernet 1/0/3
[Device-GigabitEthernet1/0/3] ip address 192.168.30.1 24
[Device-GigabitEthernet1/0/3] quit
# Create IPv4 advanced ACL 3000, configure a rule to deny the the packets with a destination IP address on the 192.168.20.0/24 network, and configure another rule to permit all other packets.
[Device] acl advanced 3000
[Device-acl-ipv4-adv-3000] rule deny ip destination 192.168.20.0 0.0.0.255
[Device-acl-ipv4-adv-3000] rule permit ip
# Apply ACL 3000 to filter the incoming packets on GigabitEthernet 1/0/ 1.
[Device] interface gigabitethernet 1/0/1
[Device-GigabitEthernet1/0/1] packet-filter 3000 inbound
Verifying the configuration
# Use the display packet-filter command to display ACL application information for packet filtering.
[Device] display packet-filter interface inbound
Interface: GigabitEthernet1/0/1
In-bound policy:
ACL 3000
The output shows that GigabitEthernet 1/0/1 has been successfully applied with an ACL for packet filtering. Ping a server on the 192.168.20.0/24 subnet from a host on the 192.168.10.0/24 subnet. The ping fails. Ping a server on any other subnet from a host on the 192.168.10.0/24 subnet. The ping succeeds.
Configuration files
#
interface GigabitEthernet1/0/1
port link-mode route
combo enable copper
ip address 192.168.10.1 255.255.255.0
packet-filter 3000 inbound
#
interface GigabitEthernet1/0/2
port link-mode route
combo enable copper
ip address 192.168.20.1 255.255.255.0
#
interface GigabitEthernet1/0/3
port link-mode route
combo enable copper
ip address 192.168.30.1 255.255.255.0
#
acl advanced 3000
rule deny ip destination 192.168.20.0 0.0.0.255
rule permit ip
#
Related documentation
· ACL and QoS Configuration Guide in H3C MSR Router Series Comware 7 Configuration Guides
· ACL and QoS Command Reference in H3C MSR Router Series Comware 7 Command References