| Title | Size | Downloads |
|---|---|---|
| FIST_SMS-1.62.tar.gz | 233.04 MB | |
| H3C FIST SMS-1.62 Release Notes.pdf | 973.84 KB |
|
H3C FIST SMS-1.62 Release Notes |
|
|
Copyright © 2023 New H3C Technologies Co., Ltd. All rights reserved.
No part of this manual may be reproduced or transmitted in any form or by any means without prior written consent of New H3C Technologies Co., Ltd.
Except for the trademarks of New H3C Technologies Co., Ltd., any trademarks that may be mentioned in this document are the property of their respective owners.
The information in this document is subject to change without notice.
Contents
Software operating environments
Hardware and software compatibility matrix
Upgrade restrictions and guidelines
Software feature and command updates
List of tables
Table 2 Software operating environments
Table 3 Hardware and software compatibility matrix (for the H3C UniServer G3/G5/G6 servers)
Introduction
This document describes the features, restrictions and guidelines, open problems, and workarounds for version 1.62. Before you use this version on a live network, back up the configuration and test the version to avoid software upgrade affecting your live network.
Use this document in conjunction with the documents listed in "Related documentation."
Version information
Version number
Image file name and MD5 checksum for this version:
FIST_SMS-1.62.tar.gz: 66580cd9cdf112f756ba53d46ec83ffa
| NOTE: To identify the FIST SMS version, execute the cat version.conf command under the directory of the configuration/version.conf file of the installation package. |
Version history
Version number | Last version | Release date | Release type | Remarks |
1.62 | 1.61 | 2023-11-30 | Release version | (Optional update.) |
1.61 | 1.60 | 2023-10-31 | Release version | (Optional update.) |
1.60 | 1.59 | 2023-09-27 | Release version | (Optional update.) |
1.59 | 1.58 | 2023-08-31 | Release version | (Optional update.) |
1.58 | 1.57 | 2023-07-14 | Release version | (Optional update.) |
1.57 | 1.56 | 2023-06-30 | Release version | (Optional update.) |
1.56 | 1.55 | 2023-04-28 | Release version | (Optional update.) |
1.55 | 1.54 | 2023-03-30 | Release version | (Optional update.) |
1.54 | 1.52 | 2023-02-28 | Release version | (Optional update.) |
1.52 | 1.51 | 2022-12-30 | Release version | (Optional update.) |
1.51 | 1.50 | 2022-11-29 | Release version | (Optional update.) |
1.50 | 1.49 | 2022-10-31 | Release version | (Optional update.) |
1.49 | 1.48 | 2022-9-29 | Release version | (Optional update.) |
1.48 | 1.47 | 2022-8-29 | Release version | (Optional update.) |
1.47 | 1.46 | 2022-7-29 | Release version | (Optional update.) |
1.46 | 1.45 | 2022-6-21 | Release version | (Optional update.) Fixed bugs. |
1.45 | 1.44 | 2022-5-20 | Release version | (Optional update.) Fixed bugs. |
1.44 | 1.43 | 2022-4-29 | Release version | (Optional update.) Fixed bugs. |
1.43 | 1.42 | 2022-3-30 | Release version | (Optional update.) Fixed bugs. |
1.42 | 1.41 | 2022-2-28 | Release version | (Optional update.) Fixed bugs. |
1.41 | 1.40 | 2022-1-24 | Release version | (Optional update.) Fixed bugs. |
1.40 | 1.39 | 2021-12-30 | Release version | (Optional update.) Fixed bugs. |
1.39 | 1.38 | 2021-11-30 | Release version | (Optional update.) Fixed bugs. |
1.38 | 1.37 | 2021-10-29 | Release version | (Optional update.) Released with devices. |
1.37 | 1.36 | 2021-9-29 | Release version | (Optional update.) Released with devices. |
1.36 | 1.35 | 2021-8-27 | Release version | (Optional update.) Released with devices. |
1.35 | 1.34 | 2021-7-28 | Release version | (Optional update.) Released with devices. |
1.34 | 1.33 | 2021-6-25 | Release version | (Optional update.) Fixed bugs. |
1.33 | 1.32 | 2021-5-30 | Release version | (Optional update.) Fixed bugs. |
1.32 | 1.31 | 2021-4-30 | Release version | (Optional update.) Fixed bugs. |
1.31 | 1.30 | 2021-3-31 | Release version | (Optional update.) Fixed bugs. |
1.30 | 1.29 | 2021-2-8 | Release version | (Optional update.) Fixed bugs. |
1.29 | 1.03.28 | 2020-12-30 | Release version | (Optional update.) Fixed bugs. |
1.03.28 | 1.03.27 | 2020-11-30 | Release version | (Optional update.) Fixed bugs. |
1.03.27 | 1.03.26 | 2020-10-30 | Release version | (Optional update.) Fixed bugs. |
1.03.26 | 1.03.25 | 2020-09-30 | Release version | (Optional update.) Fixed bugs. |
1.03.25 | 1.03.24 | 2020-08-31 | Release version | (Optional update.) Fixed bugs. |
1.03.24 | 1.03.23 | 2020-07-30 | Release version | (Optional update.) Fixed bugs. |
1.03.23 | 1.03.22 | 2020-06-30 | Release version | (Optional update.) Fixed bugs. |
1.03.22 | 1.03.21 | 2020-05-28 | Release version | (Optional update.) Fixed bugs. |
1.03.21 | First release | 2020-04-30 | Release version | First release. |
Software operating environments
Table 2 Software operating environments
Operating system | Hardware requirements | Remarks | |
Windows | Microsoft Windows Server 2012R2 Datacenter | CPU: x86-64, a minimum of 4 cores Memory: 8 GB or above Hard drive: 20 GB or above NIC: A minimum of one 10/100/1000 Mbps autosensing Ethernet card | Only 64-bit OSs are supported. OpenJDK 1.8 version (64 bit) is required on the server. |
Microsoft Windows Server 2016 | |||
Linux | CentOS 6.9 (64 bit) (includes KVM) | CPU: x86-64, a minimum of 4 cores Memory: 8 GB or above Hard drive: 20 GB or above NIC: A minimum of one 10/100/1000 Mbps autosensing Ethernet card | Only 64-bit OSs are supported. OpenJDK 1.8 version (64 bit) is required on the server. |
CentOS 6.10 (64 bit) (includes KVM) | |||
CentOS 7.7 (64 bit) (includes KVM) | |||
CentOS 8.2 (64 bit) (includes KVM) | |||
Red Hat Enterprise Linux 6.8 (64 bit) (includes KVM) | |||
Red Hat Enterprise Linux 6.9 (64 bit) (includes KVM) | |||
Red Hat Enterprise Linux 6.10 (64 bit) (includes KVM) | |||
Red Hat Enterprise Linux 7.3 (64 bit) (includes KVM) | |||
Red Hat Enterprise Linux 7.7 (64 bit) (includes KVM) | |||
Red Hat Enterprise Linux 8.6 (64 bit) (includes KVM) | |||
Kylin-Server-10-SP2-x86_64 | |||
Kylin-Server-10-SP3-x86_64 | |||
Ubuntu Server 20.04 (64 bit) | |||
Supported browsers
N/A.
Supported languages
English
Chinese
Supported device
Hardware and software compatibility matrix
CAUTION: To avoid an upgrade failure, use the following tables to verify the hardware and software compatibility before performing an upgrade. |
Table 3 Hardware and software compatibility matrix (for the H3C UniServer G3/G5/G6 servers)
Item | Specifications |
Product family | H3C UniServer G3/G5/G6 servers |
UniSystem | Version 2.62 and later |
FIST SMS | Version 1.62 and later |
iFIST | Version 1.62 and later |
Upgrade recommendations
As a best practice, upgrade the software to this version.
Upgrade restrictions and guidelines
Verify the hardware and software compatibility before performing an upgrade.
Hardware feature updates
Software feature and command updates
FIST SMS-1.62
FIST SMS supports running on ubuntu-20.04-live-server-amd64.
FIST SMS supports obtaining resource information from the following systems:
Ubuntu Server 20.04 (64 bit)
CentOS 7.6 (64 bit)
Ubuntu Server 18.04 (64 bit)
Red Hat Enterprise Linux 7.9 (64 bit)
Kylin advanced server operating system V10
Kylin advanced server operating system V10 SP1
NeoKylin advanced server operating system V7.6 (64 bit)
FIST SMS-1.61
Integrated Linux OpenJDK 1.8 64 bit in FIST SMS.
FIST SMS-1.60
Added support for running FIST SMS on Kylin-Server-10-SP2-x86_64.
Added support for running FIST SMS on Kylin-Server-10-SP3-x86_64.
FIST SMS-1.59
None.
FIST SMS-1.58
None.
FIST SMS-1.57
None.
FIST SMS-1.56
Optimize G6 servers judgment logic.
FIST SMS-1.55
Added support for HDM2 host communication enhancement.
FIST SMS-1.54
None.
FIST SMS-1.52
None.
FIST SMS-1.51
None.
FIST SMS-1.50
Added support for collecting information about high-performance and low-performance drives.
FIST SMS-1.49
Added support for collecting GPU usage information.
MIB updates
None.
Operation changes
Restrictions and cautions
Restrictions
Only a user with the administrator role can run FIST SMS.
FIST SMS uses port number 12580 to communicate with UniSystem. For FIST SMS to start correctly, make sure this port number is not used by any other service.
Disable the firewall feature on the server that runs FIST SMS or configure the firewall to permit traffic destined for or originated from port number 12580.
Port 6900 might be used for component update, so you must disable the firewall feature or set exceptions.
Make sure the program path of FIST SMS meets the following requirements:
The path name does not contain spacers and the following special characters: #%;&
The path name contains a maximum of 200 characters.
Cautions
Verify the hardware and software compatibility before performing an upgrade.
Open problems and workarounds
None.
List of resolved problems
Resolved problems in 1.62
None.
Resolved problems in 1.61
None.
Resolved problems in 1.60
None.
Resolved problems in 1.59
202303270155
Symptom: If you use UniSystem to manage FIST SMS running on a Redhat 8.4 system and view the network throughput information in UniSystem performance monitoring, the interface shows only information about network ports in running state.
Condition: This symptom might occur if you use UniSystem to manage FIST SMS running on a Redhat 8.4 system and view the network throughput information in UniSystem performance monitoring.
202307180425
Symptom: Under the Red Hat 9.0 system, if you use a version of FIST SMS prior to 1.59 and perform registered service startup, FIST SMS fails to start.
Condition: Under the Red Hat 9.0 system, if you use a version of FIST SMS prior to 1.59 and perform registered service startup.
Resolved problems in 1.58
202306251238
Symptom: When you use FIST to manage the R4950 G6 servers with FIST SMS, but have not performed any related operations for a long time, the power status will display Unknown after you refresh the server list.
Condition: This symptom might occur if you use UniSystem to manage the R4950 G6 servers with FIST SMS but have not performed any related operations for a long time.
Resolved problems in 1.57
202305111671
Symptom: If you use FIST SMS of a version earlier than 1.57 to monitor system resources, the latest time of system resource monitoring differs from the OS time, BMC time, and the BIOS time by one hour.
Condition: This symptom might occur if you use FIST SMS of a version earlier than 1.57 to monitor system resources.
Resolved problems in 1.56
None.
Resolved problems in 1.55
202303171025
Symptom: If you run FIST SMS log dumping for a long period of time, FIST SMS dumps all the history logs in case of dumping failures.
Condition: This symptom occurs if you run FIST SMS log dumping for a long period of time and dumping fails for specific log entries.
Resolved problems in 1.54
202212141398
Symptom: When the Linux system installed with FIST SMS and the hdmdrv.ko driver restarts, the hdmdrv.ko driver will not take effect. In this case, HDM will repeatedly generate the same log messages.
Condition: This symptom occurs if the Linux system installed with FIST SMS and the hdmdrv.ko driver restarts.
Resolved problems in 1.52
202211290637
Symptom: SQLite input verification error CVE-2022-35737 was detected by vulnerability scanning in a version earlier than FIST SMS-1.52.
Condition: This symptom occurs if you perform vulnerability scanning in a version earlier than FIST SMS-1.52.
Resolved problems in 1.51
202211080672
Symptom: Vulnerability CVE-2019-10086 was detected by vulnerability scanning in a version earlier than FIST SMS-1.51.
Condition: This symptom occurs if you perform vulnerability scanning in a version earlier than FIST SMS-1.51.
202211080701
Symptom: Vulnerabilities CVE-2016-1000031 and CVE-2016-3092 were detected by vulnerability scanning in a version earlier than FIST SMS-1.51
Condition: This symptom occurs if you perform vulnerability scanning in a version earlier than FIST SMS-1.51.
202211080984
Symptom: Vulnerability CVE-2020-13956 was detected by vulnerability scanning in a version earlier than FIST SMS-1.51.
Condition: This symptom occurs if you perform vulnerability scanning in a version earlier than FIST SMS-1.51.
202211080749
Symptom: When vulnerability scanning was performed in a version earlier than FIST SMS-1.51, the following vulnerabilities were detected: CVE-2019-12406, CVE-2019-12419, CVE-2019-12423, CVE-2019-17573, CVE-2020-13954, CVE-2020-1954, CVE-2021-22696, and CVE-2021-30468.
Condition: This symptom occurs if you perform vulnerability scanning in a version earlier than FIST SMS-1.51.
202211081021
Symptom: Vulnerability CVE-2017-12626 was detected by vulnerability scanning in a version earlier than FIST SMS-1.51.
Condition: This symptom occurs if you perform vulnerability scanning in a version earlier than FIST SMS-1.51.
Resolved problems in 1.50
None.
Resolved problems in 1.49
None.
Resolved problems in 1.48
None.
Resolved problems in 1.47
None.
Resolved problems in 1.46
None.
Resolved problems in 1.45
202205110408
Symptom: When you view the sellog.properties file in the FIST SMS configuration folder, no description in English is available for the file.
Condition: This symptom occurs if you view the sellog.properties file in the FIST SMS configuration folder.
Resolved problems in 1.44
None.
Resolved problems in 1.43
None.
Resolved problems in 1.42
202201181132
Symptom: The CPU, memory and drive usage lines of a FIST SMS server node are not interrupted when you view the physical resource usage information from UniSystem after the FIST SMS server node restarts.
Condition: This symptom occurs if you view the physical resource usage information of a FIST SMS server node from UniSystem after the FIST SMS server node restarts.
Resolved problems in 1.41
202112300696
Symptom: On a server with Redhat 8.2 and running FIST SMS, FIST SMS cannot record performance monitoring data after the stress exceeds the threshold during stress test on CPUs, memory, and drives.
Condition: This symptom might occur if stress test is performed on CPUs, memory, and drives on a server with Redhat 8.2 and running FIST SMS and the stress exceeds the threshold.
Resolved problems in 1.40
202112211343
Symptom: CVE-2021-4104 is found when vulnerability scanning is performed for a version earlier than FIST SMS-1.40.
Condition: This symptom occurs if vulnerability scanning is performed for a version earlier than FIST SMS-1.40.
Resolved problems in 1.39
202111091584
Symptom: If you use UniSystem to push and install the FIST SMS software of a new version to a server running FIST SMS, FIST SMS software push and installation fail.
Condition: This symptom occurs if you use UniSystem to push and install the FIST SMS software of a new version to a server running FIST SMS.
202111121112
Symptom: When you use UniSystem to incorporate a FIST SMS device running in the CAS-E0706 system, the OS information is incorrect on the server details page.
Condition: This symptom occurs if you use UniSystem to incorporate a FIST SMS device running in the CAS-E0706 system.
202111050547
Symptom: If UniSystem incorporates servers only through FIST SMS, you cannot obtain information of all devices from the server list.
Condition: This symptom occurs if UniSystem incorporates servers only through FIST SMS.
Resolved problems in 1.38
None.
Resolved problems in 1.37
202104300763
Symptom: If you use UniSystem to frequently push FIST SMS software to servers running Windows, push and installation might fail.
Condition: This symptom occurs if you use UniSystem to frequently push FIST SMS software to servers running Windows.
202108260864
Symptom: If you use UniSystem to push FIST SMS software to servers running Windows when the OpenJDK environment variables are user variables rather than system variables, the system prompts that installation fails.
Condition: This symptom occurs if you use UniSystem to push FIST SMS software to servers running Windows when the OpenJDK environment variables are user variables rather than system variables.
Resolved problems in 1.36
202107300910
Symptom: Vulnerability CVE-2021-30640 is found when vulnerability scanning is performed for a version earlier than FIST SMS-1.36.
Condition: This symptom occurs if vulnerability scanning is performed for a version earlier than FIST SMS-1.36.
Resolved problems in 1.35
None.
Resolved problems in 1.34
202105260523
Symptom: Vulnerability CVE-2021-28041 is found when vulnerability scanning is performed for a version earlier than FIST SMS-1.34.
Condition: This symptom occurs if vulnerability scanning is performed for a version earlier than FIST SMS-1.34.
Resolved problems in 1.33
202104290815
Symptom: The network field in UniSystem displays N/A after FIST SMS devices are added to UniSystem.
Condition: This symptom occurs if network port names in FIST SMS operating in the Linux operating system are in non-standard formats.
Resolved problems in 1.32
202104070376
Symptom: The information of a server in the server list disappears.
Condition: This symptom occurs if you add the server to the server list first through HDM and then through FIST SMS.
Resolved problems in 1.31
None.
Resolved problems in 1.30
202101190163
Symptom: A FIST SMS device running the Windows Server 2016 system fails to be added to UniSystem.
Condition: This symptom occurs if the FIST SMS device has been added to and then deleted from UniSystem before it is added to UniSystem again.
Resolved problems in 1.29
None.
Resolved problems in 1.03.28
202011190925
Symptom: The servers on the server list page are disordered.
Condition: This symptom occurs if you add multiple servers to UniSystem, bind each server to multiple labels, and then add FIST SMS devices to UniSystem.
Resolved problems in 1.03.27
202009281256
Symptom: The prompt message for FIST SMS upload or installation failure is incomplete.
Condition: This symptom occurs if FIST SMS fails to be uploaded or installed.
Resolved problems in 1.03.26
202008271400
Symptom: UniSystem displays an incorrect error message when the user attempts to add a FIST SMS server that already exists in UniSystem.
Condition: This symptom occurs if the user attempts to add a FIST SMS server that already exists in UniSystem.
Resolved problems in 1.03.25
202008101490
Symptom: UniSystem fails to push and install FIST SMS on a server.
Condition: This symptom occurs if the server runs Windows Server 2019 and has the openssh service installed.
Resolved problems in 1.03.24
202006290699
Symptom: After installing FIST SMS on a Windows server, UniSystem cannot automatically add the FIST SMS server node to its system.
Condition: None.
Resolved problems in 1.03.23
202006280923
Symptom: After FIST SMS is installed on a server, ports 12580 and 6900 are automatically opened in the server's firewall.
Condition: This symptom occurs if FIST SMS is installed on the server with the firewall disabled.
Resolved problems in 1.03.22
201911120208
Symptom: The component update module of UniSystem reports a node unavailable error during node inventory.
Condition: This symptom occurs if you re-inventory a group of FIST SMS nodes after a previous inventory failure.
Resolved problems in 1.03.21
Troubleshooting
You can obtain help from the following links:
• Access https://www.h3c.com/en/Support/Resource_Center/Technical_Documents/, select the product category and model, and search for related cases in the Maintain section.
• Access https://zhiliao.h3c.com/, and search for related cases by product model or feature keyword.
Related documentation
H3C Servers FIST SMS User Guide
Technical support
To obtain support services, contact H3C Support at [email protected].
The following information describes how to install and upgrade FIST SMS.
Screenshots in this section are for illustration only. They might vary as the software version changes.
FIST SMS is a service program running in the OS of a server to collect server failure information and send the information to HDM and UniSystem for fault isolation. FIST SMS can cooperate with UniSystem and REPO to complete firmware and driver update.
You can upgrade FIST SMS in both Linux and Windows.
Installing and upgrading FIST SMS in Linux
Online upgrade of FIST SMS is not supported in Linux. Before you upgrade FIST SMS in Linux, first stop FIST SMS.
Installing FIST SMS in Linux
1.Download the installation package of FIST SMS and copy the package to the root directory of the server. This example uses FIST SMS of version 1.03.08.
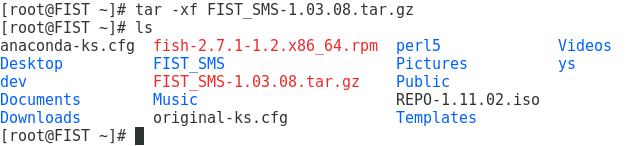
2.Execute the tar -xf FIST_SMS-1.03.08.tar.gz command and press Enter to decompress the installation package, as shown in Figure 1.
Figure 2 Decompressing the FIST SMS installation package
Upgrading FIST SMS in Linux
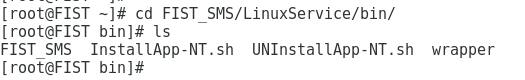
1.Execute the cd /FIST SMS/LinuxService/bin command to enter the directory where FIST SMS starts.
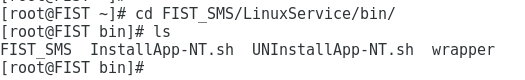
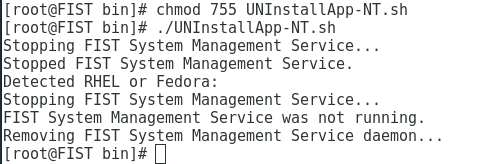
2.Execute the chmod 755 UNInstallApp-NT.sh command and press Enter to make the FIST SMS service script file executable. Then, execute the /UNInstallApp-NT.sh command to stop and uninstall FIST SMS.
3.Copy the new installation package of FIST SMS to the root directory of the server.
4.Execute the cd /FIST_SMS/LinuxService/bin command to enter the directory where FIST SMS starts.
5.Execute the chmod 755 InstallApp-NT.sh command and press Enter to make the FIST SMS service script file executable.
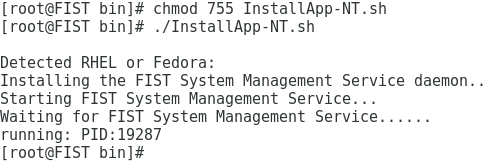
6.Execute the ./InstallApp-NT.sh command to install and start FIST SMS.
If the environment meets the requirements, FIST SMS starts correctly. If the environment does not meet the requirement, the system prompts an error and quits.
Installing and upgrading FIST SMS in Windows
Installing FIST SMS in Windows
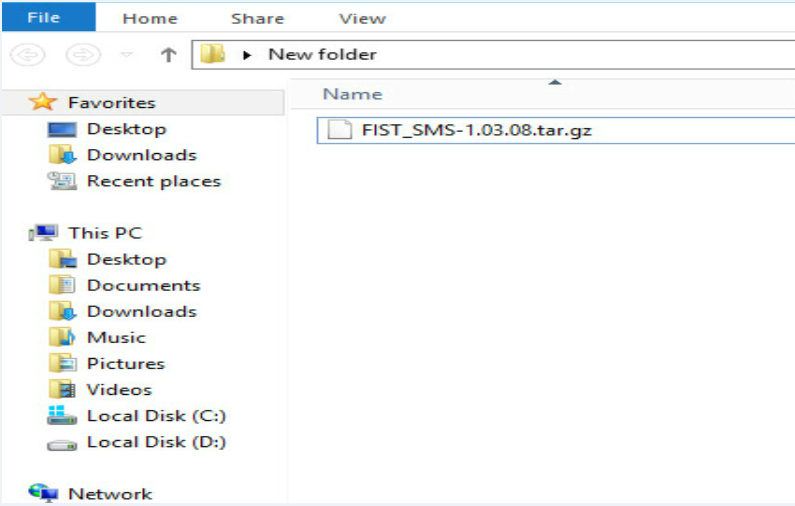
1.Copy the downloaded installation package of FIST SMS to the directory of the server to install FIST SMS, as shown in Figure 2. This example uses version 1.03.08.
Figure 3 Copying the FIST SMS installation package to the directory to install FIST SMS
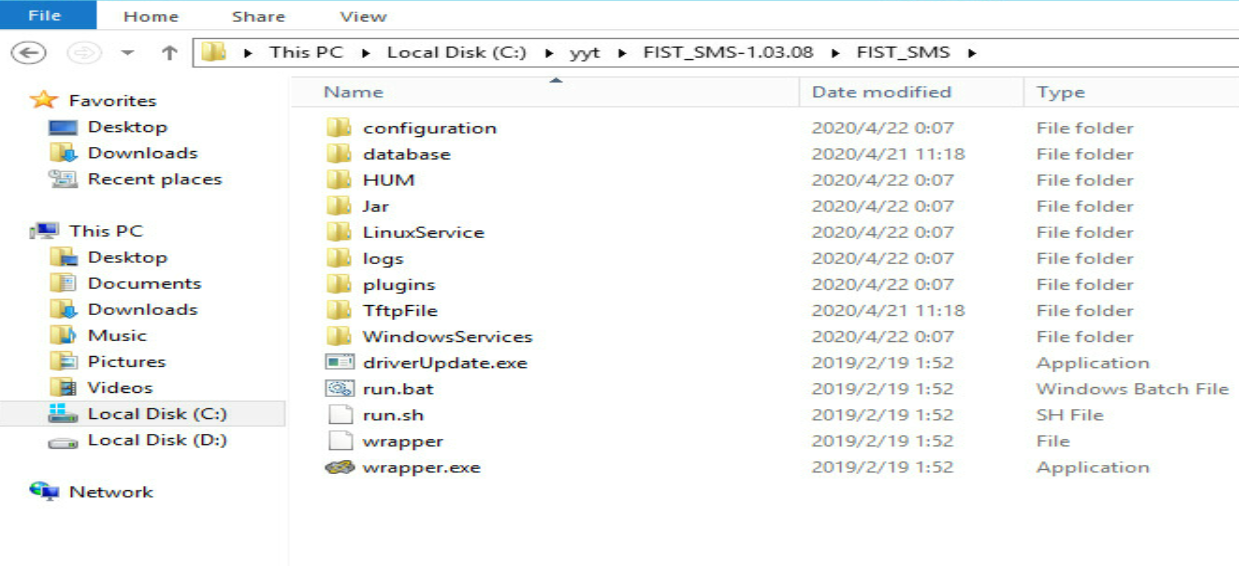
2.Decompress the installation package, as shown in Figure 3.
Figure 4 Decompressing the FIST SMS installation package
You can start FIST SMS by using one of the following methods:
Method 1—Start FIST SMS directly by double clicking the run.bat file as shown in Figure 3. FIST SMS will stop running after a system reboot.
Method 2—Use the registry to start FIST SMS. FIST SMS will keep running after a system reboot. As a best practice, use this method.
To use method 2, perform the following steps:
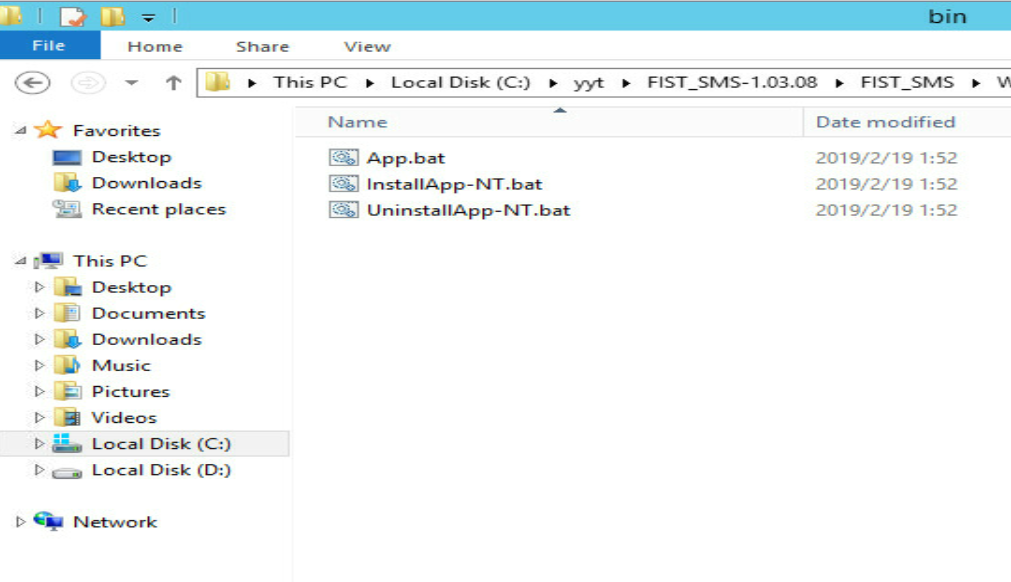
a.Enter the \WindowsServices\bin directory of FIST SMS, as shown in Figure 4, and then double-click the InstallApp-NT.bat script file.
Figure 5 Entering the \WindowsServices\bin directory
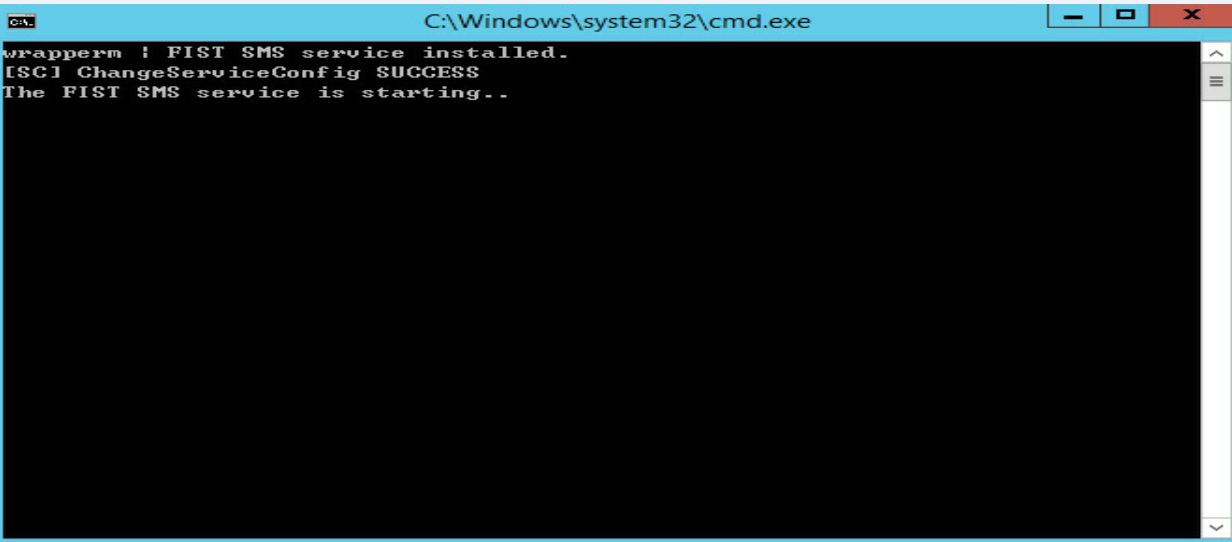
b.In the window that opens, register and start FIST SMS.
Figure 6 Register and start FIST SMS
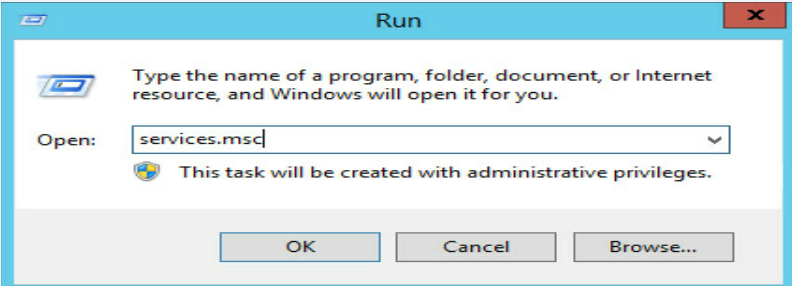
c.Press WIN+R to open the Run dialog box, execute the serices.msc command, and then press Enter or click OK.
Figure 7 Executing the services.msc command in the Run dialog box
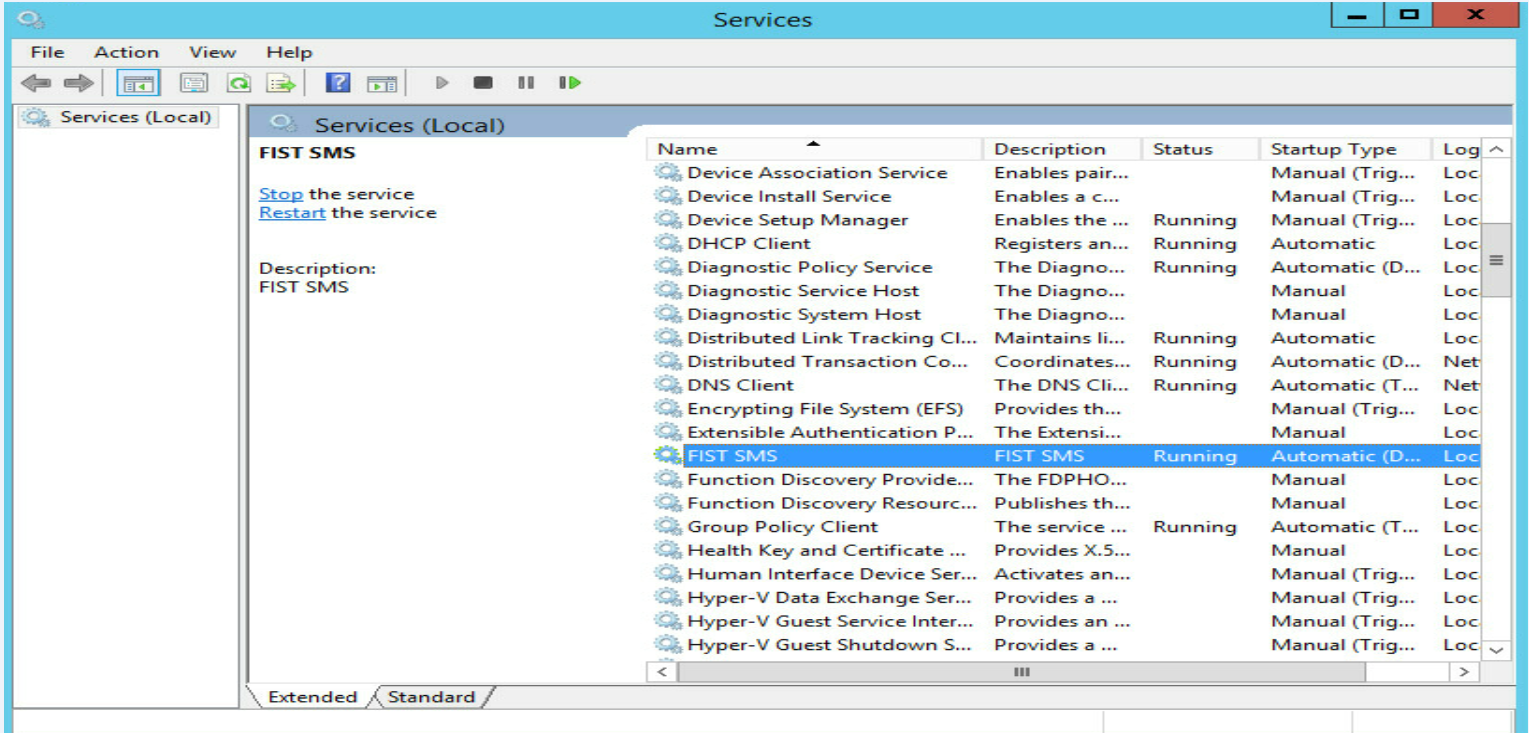
d.Verify that FIST SMS is running.
Figure 8 Verifying the status of FIST SMS
Upgrading FIST SMS in Windows
The method to upgrade FIST SMS in Windows varies by start method.
If FIST SMS is started by using the run.bat script file, perform the following steps to upgrade FIST SMS:
1.Stop the run.bat script file from running.
2.Copy the installation package of the new software version to a new directory of the server and decompress the package.
3.Double-click the run.bat script file in the new directory of FIST SMS.
If FIST SMS is started by using the registry, perform the following steps to upgrade FIST SMS:
1.Enter the \WindowsServices\bin directory of FIST SMS, as shown in Figure 8.
Figure 9 Entering the \WindowsServices\bin directory
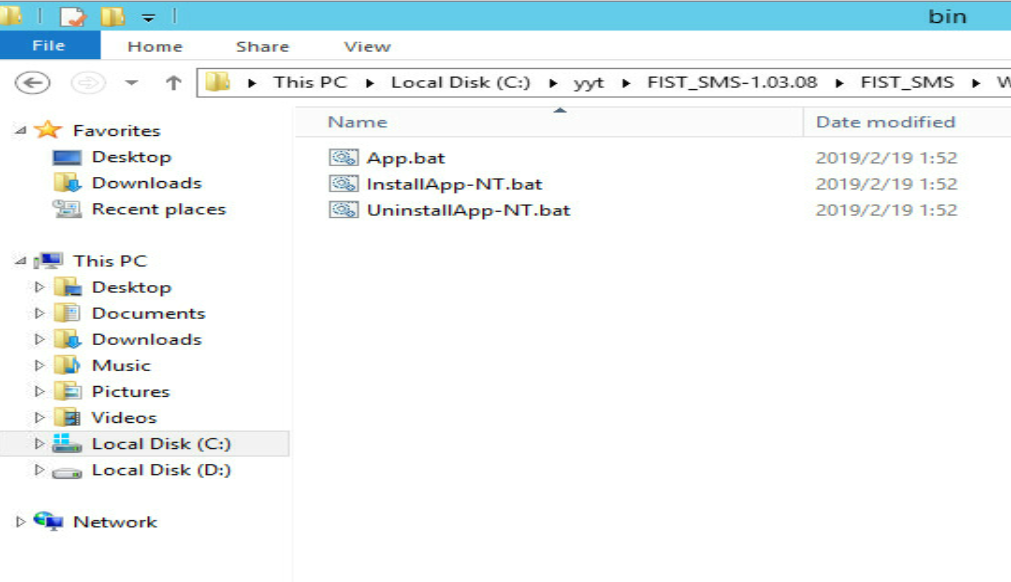
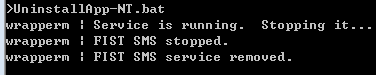
2.Double-click the UninstallApp-NT.bat script file to uninstall FIST SMS, as shown in Figure 9.
Figure 10 Uninstalling FIST SMS
3.Install FIST SMS of the new version as described in "Installing FIST SMS in Windows."
Appendix B Feature list
Software features
Category | Features |
Component update | Update the hardware and drivers on the server managed by UniSystem and installed with FIST SMS. |
Multi-OS compatibility | Compatible with part of 64-bit Linux OSs. Compatible with part of 64-bit Windows OSs. |
Device management | View the CPU usage, memory usage, and drive space usage of the system. View the CPU, memory, drive, and network adapter specifications of the system. |
Appendix C Acronyms
Acronym | Full name |
HDM | Hardware Device Management |
BIOS | Basic Input/output System |
REPO | Repository |

