| Title | Size | Downloads |
|---|---|---|
| FIST-2.54_upgrade.bin.rar | 693.57 MB | |
| FIST-2.54.zip | 280.49 MB | |
| FIST-2.54.ova.rar | 2.75 GB | |
| FISTC FIST-2.54(0501A0S5) Release Notes.pdf | 1.84 MB |
|
H3C FIST-2.54 Release Notes |
|
|
.
Copyright © 2023 New H3C Technologies Co., Ltd. All rights reserved.
No part of this manual may be reproduced or transmitted in any form or by any means without prior written consent of New H3C Technologies Co., Ltd.
Except for the trademarks of New H3C Technologies Co., Ltd., any trademarks that may be mentioned in this document are the property of their respective owners.
The information in this document is subject to change without notice.
Contents
Software operating environments
Hardware and software compatibility matrixes
Upgrade restrictions and guidelines
From FIST-2.00.22 to FIST-2.31
Software feature and command updates
Resolved problems in FIST 2.44
Resolved problems in FIST 2.43
Resolved problems in FIST 2.42
Resolved problems in FIST 2.41
Resolved problems in FIST 2.40
Resolved problems in FIST 2.39
Resolved problems in FIST 2.38
Resolved problems in FIST 2.37
Resolved problems in FIST 2.36
Resolved problems in FIST 2.35
Resolved problems in FIST 2.34
Resolved problems in FIST 2.33
Resolved problems in FIST 2.32
Resolved problems in FIST 2.31
Resolved problems in FIST 2.30
Resolved problems in FIST 2.29
Resolved problems in FIST 2.00.28
Resolved problems in FIST 2.00.27
Resolved problems in FIST 2.00.26
Resolved problems in FIST 2.00.25
Resolved problems in FIST 2.00.24
Resolved problems in FIST 2.00.23
Resolved problems in FIST 2.00.22
Resolved problems in FIST 2.00.21
Appendix A Software feature and version compatibility and software feature list
Software feature and version compatibility matrix
Updating FIST on a Windows server by using the .tar installation package
Updating FIST on a Linux server by using the .tar installation package
Updating and starting FIST from the GUI
Updating and starting FIST from the CLI
Updating and starting FIST by using the ISO image
Handling firmware update failures
Deleting the browsing history in Internet Explorer
Deleting the browsing history in Firefox
Deleting the browsing history in Chrome
Appendix C Upgrading FIST software by using the upgrade package
Procedure (for FIST on a VM or AE module)
Procedure (for FIST of the package version)
List of tables
Table 1 MD5 checksums for individual software installation files
Table 3 Software operating environments
Table 5 Hardware and software compatibility matrix (for the H3C UniServer R4950 G3 servers)
Table 6 Hardware and software compatibility matrix (for the H3C UniServer R6900 G3 servers)
Table 7 Hardware and software compatibility matrix (for the H3C UniServer R8900 G3 servers)
Table 8 Hardware and software compatibility matrix (for the H3C UniServer R6700 G3 servers)
Table 9 Hardware and software compatibility matrix (for the H3C UniServer R5300 G3 servers)
Table 11 Hardware and software compatibility matrix (for the AE100)
Table 12 Hardware and software compatibility matrix (for the H3C UniServer E3200 G3 servers)
Table 13 Hardware and software compatibility matrix (for the H3C UniServer R4300 G3 servers)
Table 14 Hardware and software compatibility matrix (for the H3C UniServer R4500 G3 servers)
Table 15 Hardware and software compatibility matrix (for the H3C UniServer R6900 G5 servers)
Table 16 Hardware and software compatibility matrix (for the H3C UniServer R4900 G5 servers)
Table 17 Hardware and software compatibility matrix (for the H3C UniServer R4700 G5 servers)
Table 18 Hardware and software compatibility matrix (for the H3C UniServer R4950 G5 ROME servers)
Table 19 Hardware and software compatibility matrix (for the H3C UniServer R4950 G5 MILAN servers)
Table 20 Hardware and software compatibility matrix (for the H3C UniServer R5500 G5 AMD servers)
Table 21 Hardware and software compatibility matrix (for the H3C UniServer R5500 G5 INTEL servers)
Table 22 Hardware and software compatibility matrix (for the H3C UniServer B5700 G5 servers)
Table 23 Hardware and software compatibility matrix (for the H3C UniServer R5300 G5 servers)
Table 24 Hardware and software compatibility matrix (for the H3C UniStor X10828 G5 servers)
Table 25 Hardware and software compatibility matrix (for the H3C UniServer R4930 G5 servers)
Table 26 Hardware and software compatibility matrix (for the H3C UniServer R4930 G5 H3 servers)
Table 27 Hardware and software compatibility matrix (for the H3C UniServer R4300 G5 servers)
Table 28 Hardware and software compatibility matrix (for the H3C UniServer R4330 G5 servers)
Table 29 Hardware and software compatibility matrix (for the H3C UniServer R4330 G5 H3 servers)
Table 30 Hardware and software compatibility matrix (for the H3C 4900 G2 servers)
Table 31 Hardware and software compatibility matrix (for the H3C UniServer R4900/R4700 G6 servers)
Table 32 Ports/protocols for FIST to communicate with HDM
Table 33 Ports/protocols for FIST to communicate with OM
Table 34 Ports/protocols for FIST to communicate with FIST SMS
Table 35 Ports/protocols for FIST to communicate with iFIST
Table 36 Software feature and version compatibility matrix
Introduction
This document describes the features, restrictions and guidelines, open problems, and workarounds for version FIST-2.54. Before you use this version on a live network, back up the configuration and test the version to avoid software update affecting your live network.
Use this document in conjunction with the documents listed in "Related documentation."
Screenshots in this document are for illustration only.
Version information
Version number
Version 2.54
Table 1 shows the MD5 checksums for the installation files in this package.
Table 1 MD5 checksums for individual software installation files
Software | Installation file name | MD5 checksum |
VM installation package | FIST-2.54.ova.rar | 41c5149bf00417dd2b62ffcc09e30b4d |
Standalone installation package | FIST-2.54.tar.gz | c01ce48e66a824caebe57f22fb19432c |
Upgrade package | FIST-2.54_upgrade.bin.rar | 077e084f98322a46d7ed602c9d269752 |
| NOTE: You can access the FIST Web interface to identify the FIST version by clicking the i icon in the top right corner of the FIST Web interface. |
The version history is as shown in Table 2.
Version number | Last version | Release date | Release type | Remarks |
2.54 | 2.52 | 2023-02-28 | ESS | Added features and fixed bugs. |
2.52 | 2.51 | 2022-12-30 | ESS | Added features and fixed bugs. |
2.51 | 2.50 | 2022-11-29 | ESS | Fixed bugs. |
2.50 | 2.49 | 2022-10-31 | ESS | Fixed bugs. |
2.49 | 2.48 | 2022-9-29 | ESS | Fixed bugs. |
2.48 | 2.47 | 2022-8-29 | ESS | Fixed bugs. |
2.47 | 2.46 | 2022-7-29 | ESS | Fixed bugs. |
2.46 | 2.45 | 2022-6-21 | ESS | Fixed bugs. |
2.45 | 2.44 | 2022-5-20 | ESS | Fixed bugs. |
2.44 | 2.43 | 2022-4-29 | ESS | Fixed bugs. |
2.43 | 2.42 | 2022-3-30 | ESS | Added features and fixed bugs. |
2.42 | 2.41 | 2022-2-28 | ESS | Fixed bugs. |
2.41 | 2.40 | 2022-1-24 | ESS | Added features and fixed bugs. |
2.40 | 2.39 | 2021-12-30 | ESS | Added features and fixed bugs. |
2.39 | 2.38 | 2021-11-30 | ESS | Added features and fixed bugs. |
2.38 | 2.37 | 2021-10-29 | ESS | Fixed bugs. |
2.37 | 2.36 | 2021-9-29 | ESS | Added features and fixed bugs. |
2.36 | 2.35 | 2021-8-27 | ESS | Added features and fixed bugs. |
2.35 | 2.34 | 2021-7-28 | ESS | Added features and fixed bugs. |
2.34 | 2.33 | 2021-6-25 | ESS | Added features and fixed bugs. |
2.33 | 2.32 | 2021-5-30 | ESS | Added features and fixed bugs. |
2.32 | 2.31 | 2021-4-30 | ESS | Added features and fixed bugs. |
2.31 | 2.30 | 2021-3-31 | ESS | Added features and fixed bugs. |
2.30 | 2.29 | 2021-2-8 | ESS | Fixed bugs. |
2.29 | 2.00.28 | 2020-12-30 | ESS | Added features and fixed bugs. |
2.00.28 | 2.00.27 | 2020-11-30 | ESS | Added features and fixed bugs. |
2.00.27 | 2.00.26 | 2020-10-30 | ESS | Added features and fixed bugs. |
2.00.26 | 2.00.25 | 2020-9-30 | ESS | Added features and fixed bugs. |
2.00.25 | 2.00.24 | 2020-8-31 | ESS | Added features and fixed bugs. |
2.00.24 | 2.00.23 | 2020-7-30 | ESS | Fixed bugs. |
2.00.23 | 2.00.22 | 2020-6-30 | ESS | Added features and fixed bugs. |
2.00.22 | 2.00.21 | 2020-5-28 | ESS | Added features and fixed bugs. |
2.00.21 | 2.00.18 | 2020-4-30 | ESS | First release. |
Software operating environments
Table 3 Software operating environments
Operating system | Hardware requirements | Remarks | |
Windows | Windows 10 | CPU: x86-64, a minimum of 4 cores Memory: 8 GB or above (less than 2000 devices) 16 GB or above (2000 to 5000 devices) Drive: 20 GB or above NIC: A minimum of one 10/100/1000 Mbps autosensing Ethernet card | Only 64-bit OSs are supported. |
Windows 7 | |||
Microsoft Windows Server 2012R2 Datacenter | |||
Linux | CentOS 7.4 (64 bit) (includes KVM) | CPU: x86-64, a minimum of 4 cores Memory: 8 GB or above (less than 2000 devices) 16 GB or above (2000 to 5000 devices) Drive: 20 GB or above NIC: A minimum of one 10/100/1000 Mbps autosensing Ethernet card | Only 64-bit OSs are supported. |
CentOS 7.5 (64 bit) (includes KVM) | |||
VMware | ESXi | CPU: x86-64, a minimum of 8 cores Memory: 32 GB or above Drive: 500 GB or above | Only. Ova version import is supported. |
Supported browsers
The following browsers are recommended:
Internet Explorer 11 or higher
Mozilla Firefox 60.0 or higher
Google Chrome 66.0 or higher
Supported languages
English
Chinese
Supported hardware platforms
This document is applicable to the following products:
AE modules
H3C UniServer B5700 G5
H3C UniServer R4300 G5
H3C UniServer R4330 G5
H3C UniServer R4700 G5
H3C UniServer R4900 G5
H3C UniServer R4930 G5
H3C UniServer R4950 G5
H3C UniServer R5300 G5
H3C UniServer R5500 G5 AMD
H3C UniServer R5500 G5 INTEL
H3C UniServer R6900 G5
H3C UniServer B5700 G3
H3C UniServer B5800 G3
H3C UniServer B7800 G3
H3C UniServer E3200 G3
H3C UniServer R2700 G3
H3C UniServer R2900 G3
H3C UniServer R4300 G3
H3C UniServer R4500 G3
H3C UniServer R4700 G3
H3C UniServer R4900 G3
H3C UniServer R4950 G3
H3C UniServer R5300 G3
H3C UniServer R6700 G3
H3C UniServer R6900 G3
H3C UniServer R8900 G3
H3C UniServer R4900 G2
H3C UniServer R4900 G6
H3C UniServer R4700 G6
Hardware and software compatibility matrixes
CAUTION: To avoid an update failure, use the following tables in this section to verify the hardware and software compatibility before performing an update. |
Table 4 Hardware and software compatibility matrix (for the H3C UniServer R4900/R4700/R2900/R2700 G3 servers)
Item | Specifications |
Product family | H3C UniServer R4900/R4700/R2900/R2700 G3 servers |
BIOS | Version 2.00.39 and later |
HDM | Version 1.30.19 and later |
FIST | Version 2.54 and later |
FIST SMS | Version 1.54 and later |
iFIST | Version 1.54 and later |
Table 5 Hardware and software compatibility matrix (for the H3C UniServer R4950 G3 servers)
Item | Specifications |
Product family | H3C UniServer R4950 G3 servers |
BIOS | Version 3.01.17 and later (non-H3C-proprietary version) |
HDM | Version 1.30.19 and later |
FIST | Version 2.54 and later |
FIST SMS | Version 1.54 and later |
iFIST | Version 1.54 and later |
Table 6 Hardware and software compatibility matrix (for the H3C UniServer R6900 G3 servers)
Item | Specifications |
Product family | H3C UniServer R6900 G3 servers |
HDM | Version 1.30.19 and later |
BIOS | Version 2.00.39 and later |
FIST | Version 2.54 and later |
FIST SMS | Version 1.54 and later |
iFIST | Version 1.54 and later |
Table 7 Hardware and software compatibility matrix (for the H3C UniServer R8900 G3 servers)
Item | Specifications |
Product family | H3C UniServer R8900 G3 servers |
HDM | Version 1.30.19 and later |
BIOS | Version 2.00.39 and later |
FIST | Version 2.54 and later |
FIST SMS | Version 1.54 and later |
iFIST | Version 1.54 and later |
Table 8 Hardware and software compatibility matrix (for the H3C UniServer R6700 G3 servers)
Item | Specifications |
Product family | H3C UniServer R6700 G3 servers |
HDM | Version 1.30.19 and later |
BIOS | Version 2.00.39 and later |
FIST | Version 2.54 and later |
FIST SMS | Version 1.54 and later |
iFIST | Version 1.54 and later |
Table 9 Hardware and software compatibility matrix (for the H3C UniServer R5300 G3 servers)
Item | Specifications |
Product family | H3C UniServer R5300 G3 servers |
HDM | Version 1.30.19 and later |
BIOS | Version 2.00.39 and later |
FIST | Version 2.54 and later |
FIST SMS | Version 1.54 and later |
iFIST | Version 1.54 and later |
Table 10 Hardware and software compatibility matrix (for the H3C UniServer B5700/B5800/B7800 G3 servers)
Item | Specifications |
Product family | H3C UniServer B5700/B5800/B7800 G3 servers |
HDM | Version 1.30.19 and later |
BIOS | Version 2.00.39 and later |
FIST | Version 2.54 and later |
FIST SMS | Version 1.54 and later |
iFIST | Version 1.54 and later |
Table 11 Hardware and software compatibility matrix (for the AE100)
Item | Specifications |
Product family | AE100 |
HDM | Version 1.30.19 and later |
BIOS | Version 1.00.09 and later |
FIST | Version 2.46 and later |
Table 12 Hardware and software compatibility matrix (for the H3C UniServer E3200 G3 servers)
Item | Specifications |
Product family | H3C UniServer E3200 G3 servers |
HDM | Version 2.32 and later |
BIOS | Version 5.15 and later |
FIST | Version 2.54 and later |
iFIST | Version 1.54 and later |
Table 13 Hardware and software compatibility matrix (for the H3C UniServer R4300 G3 servers)
Item | Specifications |
Product family | H3C UniServer R4300 G3 servers |
HDM | Version 1.30.19 and later |
BIOS | Version 2.00.39 and later |
FIST | Version 2.54 and later |
FIST SMS | Version 1.54 and later |
Table 14 Hardware and software compatibility matrix (for the H3C UniServer R4500 G3 servers)
Item | Specifications |
Product family | H3C UniServer R4500 G3 servers |
HDM | Version 2.98 and later |
BIOS | Version 2.00.58 and later |
FIST | Version 2.54 and later |
FIST SMS | Version 1.54 and later |
iFIST | Version 1.54 and later |
Table 15 Hardware and software compatibility matrix (for the H3C UniServer R6900 G5 servers)
Item | Specifications |
Product family | H3C UniServer R6900 G5 servers |
HDM | Version 2.32 and later |
BIOS | Version 5.15 and later |
FIST | Version 2.54 and later |
FIST SMS | Version 1.54 and later |
iFIST | Version 1.54 and later |
Table 16 Hardware and software compatibility matrix (for the H3C UniServer R4900 G5 servers)
Item | Specifications |
Product family | H3C UniServer R4900 G5 servers |
HDM | Version 2.32 and later |
BIOS | Version 5.09 and later |
FIST | Version 2.54 and later |
FIST SMS | Version 1.54 and later |
iFIST | Version 1.54 and later |
Table 17 Hardware and software compatibility matrix (for the H3C UniServer R4700 G5 servers)
Item | Specifications |
Product family | H3C UniServer R4700 G5 servers |
HDM | Version 2.32 and later |
BIOS | Version 5.09 and later |
FIST | Version 2.54 and later |
FIST SMS | Version 1.54 and later |
iFIST | Version 1.54 and later |
Table 18 Hardware and software compatibility matrix (for the H3C UniServer R4950 G5 ROME servers)
Item | Specifications |
Product family | H3C UniServer R4950 G5 ROME servers |
HDM | Version 2.60 and later |
BIOS | Version 5.30 and later |
FIST | Version 2.54 and later |
FIST SMS | Version 1.54 and later |
iFIST | Version 1.54 and later |
Table 19 Hardware and software compatibility matrix (for the H3C UniServer R4950 G5 MILAN servers)
Item | Specifications |
Product family | H3C UniServer R4950 G5 MILAN servers |
HDM | Version 2.70 and later |
BIOS | Version 5.08 and later |
FIST | Version 2.54 and later |
FIST SMS | Version 1.54 and later |
iFIST | Version 1.54 and later |
Table 20 Hardware and software compatibility matrix (for the H3C UniServer R5500 G5 AMD servers)
Item | Specifications |
Product family | H3C UniServer R5500 G5 AMD servers |
HDM | Version 2.69 and later |
BIOS | Version 5.27 and later |
FIST | Version 2.54 and later |
FIST SMS | Version 1.54 and later |
iFIST | Version 1.54 and later |
Table 21 Hardware and software compatibility matrix (for the H3C UniServer R5500 G5 INTEL servers)
Item | Specifications |
Product family | H3C UniServer R5500 G5 INTEL servers |
HDM | Version 2.70 and later |
BIOS | Version 5.30 and later |
FIST | Version 2.54 and later |
FIST SMS | Version 1.54 and later |
iFIST | Version 1.54 and later |
Table 22 Hardware and software compatibility matrix (for the H3C UniServer B5700 G5 servers)
Item | Specifications |
Product family | H3C UniServer B5700 G5 servers |
HDM | Version 2.18 and later |
BIOS | Version 5.07 and later |
FIST | Version 2.54 and later |
FIST SMS | Version 1.54 and later |
iFIST | Version 1.54 and later |
Table 23 Hardware and software compatibility matrix (for the H3C UniServer R5300 G5 servers)
Item | Specifications |
Product family | H3C UniServer R5300 G5 servers |
HDM | Version 2.18 and later |
BIOS | Version 5.09 and later |
FIST | Version 2.54 and later |
FIST SMS | Version 1.54 and later |
iFIST | Version 1.54 and later |
Table 24 Hardware and software compatibility matrix (for the H3C UniStor X10828 G5 servers)
Item | Specifications |
Product family | H3C UniStor X10828 servers |
HDM | Version 2.18 and later |
BIOS | Version 5.09 and later |
FIST | Version 2.54 and later |
FIST SMS | Version 1.54 and later |
Table 25 Hardware and software compatibility matrix (for the H3C UniServer R4930 G5 servers)
Item | Specifications |
Product family | H3C UniServer R4930 G5 servers |
HDM | Version 2.32 and later |
BIOS | Version 5.15 and later |
FIST | Version 2.54 and later |
FIST SMS | Version 1.54 and later |
iFIST | Version 1.54 and later |
Table 26 Hardware and software compatibility matrix (for the H3C UniServer R4930 G5 H3 servers)
Item | Specifications |
Product family | H3C UniServer R4930 G5 H3 servers |
HDM | Version 3.30 and later |
BIOS | Version 5.65 and later |
FIST | Version 2.54 and later |
FIST SMS | Version 1.54 and later |
iFIST | Version 1.54 and later |
Table 27 Hardware and software compatibility matrix (for the H3C UniServer R4300 G5 servers)
Item | Specifications |
Product family | H3C UniServer R4300 G5 servers |
HDM | Version 2.18 and later |
BIOS | Version 5.09 and later |
FIST | Version 2.54 and later |
FIST SMS | Version 1.54 and later |
iFIST | Version 1.54 and later |
Table 28 Hardware and software compatibility matrix (for the H3C UniServer R4330 G5 servers)
Item | Specifications |
Product family | H3C UniServer R4330 G5 servers |
HDM | Version 2.18 and later |
BIOS | Version 5.09 and later |
FIST | Version 2.54 and later |
FIST SMS | Version 1.54 and later |
iFIST | Version 1.54 and later |
Table 29 Hardware and software compatibility matrix (for the H3C UniServer R4330 G5 H3 servers)
Item | Specifications |
Product family | H3C UniServer R4330 G5 H3 servers |
HDM | Version 3.30 and later |
BIOS | Version 5.65 and later |
FIST | Version 2.54 and later |
FIST SMS | Version 1.54 and later |
iFIST | Version 1.54 and later |
Table 30 Hardware and software compatibility matrix (for the H3C 4900 G2 servers)
Item | Specifications |
Product family | H3C 4900 G2 servers |
HDM | Version 1.03.07P01 and later |
BIOS | Version 1.01.07 and later |
FIST | Version 2.54 and later |
Table 31 Hardware and software compatibility matrix (for the H3C UniServer R4900/R4700 G6 servers)
Item | Specifications |
Product family | H3C UniServer R4900/R4700 G6 servers |
HDM | Version 1.11 and later |
BIOS | Version 6.00.09 and later |
FIST | Version 2.54 and later |
FIST SMS | Version 1.54 and later |
iFIST | Version 1.54 and later |
Upgrade recommendations
As a best practice, upgrade the software to this version.
Upgrade restrictions and guidelines
Verify the hardware and software compatibility before performing an upgrade.
After FIST is upgraded, delete the browsing history before you re-log in to FIST. For more information, see Appendix B Updating software.
Hardware feature updates
The model name of a hardware option in this document might differ slightly from its model name label. A model name label might add a prefix or suffix to the hardware-coded model name for purposes such as identifying the matching server brand or applicable region. For example, memory module model DDR4-2666-8G-1Rx8-R represents memory module label UN-DDR4-2666-8G-1Rx8-R, UN-DDR4-2666-8G-1Rx8-R-F, or UN-DDR4-2666-8G-1Rx8-R-S, all of which has a prefix of UN-.
FIST-2.54
Support for FIST on H3C UniServer R4900 G6 servers was added.
Support for FIST on H3C UniServer R4700 G6 servers was added.
FIST-2.52
None.
FIST-2.51
Support for FIST on H3C UniServer R4330 G5 H3 servers was added.
Support for FIST on H3C UniServer R4930 G5 H3 servers was added.
FIST-2.50
None.
FIST-2.49
None.
FIST-2.48
None.
FIST-2.47
None.
FIST-2.46
None.
FIST-2.45
Support for FIST on H3C 4900 G2 servers was added.
FIST-2.44
None.
FIST-2.43
Support for FIST on H3C UniServer R4500 G3 servers was added.
From FIST-2.36 to FIST-2.42
None.
FIST-2.35
Support for FIST on H3C UniServer R4300 G3 servers was added.
Support for FIST on H3C UniServer R4300 G5 servers was added.
Support for FIST on H3C UniServer R4330 G5 servers was added.
From FIST-2.33 to FIST-2.34
Support for FIST on H3C UniServer R4930 G5 servers was added.
FIST-2.32
Support for FIST on H3C UniServer X10828 G5 servers was added.
Support for FIST on H3C UniServer R5300 G5 servers was added.
Support for FIST on H3C UniServer B5700 G5 servers was added.
Support for FIST on H3C UniServer R5500 AMD G5 servers was added.
Support for FIST on H3C UniServer R5500 INTEL G5 servers was added.
Support for FIST on H3C UniServer R4950 G5 ROME servers was added.
Support for FIST on H3C UniServer R4900 G5 servers was added.
From FIST-2.00.22 to FIST-2.31
Support for FIST on H3C UniServer R6900 G5 servers was added.
FIST-2.00.21
First release.
Software feature and command updates
FIST-2.54
Added support for bulk installing Red Hat Enterprise Linux 8.5 (64 bit).
FIST-2.52
Added support for exporting chassis routing inspection reports.
FIST-2.51
None.
FIST-2.50
Added support for displaying information about high-performance and low-performance drives.
FIST-2.49
Added support for displaying the GPU usage.
FIST-2.48
Added support for configuring the BIOS from FIST.
FIST-2.47
None.
FIST-2.46
None.
FIST-2.45
Checking H3C 4900 G2 devices.
FIST-2.44
Bulk setting HDM IP addresses.
FIST-2.43
Configuring HDM settings online from the Menu > Templates > Server Templates page.
Adding exporting inspection reports in PDF format.
FIST-2.42
None.
FIST-2.41
Configuring IPv6 settings from the System > Network page.
Adding the QR code for viewing feature diagrams or giving feedback from the Templates > Server Templates page.
FIST-2.40
Added the scheduled deployment feature in the Deployment > Apply Server Templates module.
FIST-2.39
Added support for FIST software upgrade on the Maintain and Upgrade page.
Added support for hardware information display on the Reports > Server Inventory page.
FIST-2.38
None.
FIST-2.37
Added the mezzanine card configuration for blade servers and the interconnect module configuration features in the server configuration templates.
Added support of clone-mode OS installation for the CentOS 7.6 operating system in FIST.
From FIST-2.35 to FIST-2.36
None.
FIST-2.34
Added support for mobile alarm notifications in FIST.
Added support of clone-mode OS installation for Red Hat Enterprise Linux 8.2 (64 bit) in FIST.
FIST-2.33
Added support for software pushing and installation.
FIST-2.32
Added support for displaying history power data and history temperature data.
Added support for retaining RAID settings of the server templates.
Added support for H3C OEM VMware images of the OS settings.
Added support for displaying out-of-band firmware update progress and result.
Added support for out-of-band firmware update based on HDM&iFIST.
FIST-2.31
Support for LDAP management.
FIST-2.30
For more information about the software feature update history, see H3C FIST-2.30(0501A0S5) Release Notes (Software Feature Changes).
MIB updates
Operation changes
Restrictions and cautions
Restrictions
To use the OS installation feature of FIST, you must first upload OS image files to FIST. Make sure the FIST running environment has enough space to store the OS image files.
Administrative privileges are required for running FIST installed on a server or AE module.
Run the ISO image version of FIST only on AE100.
Follow these best practices to set the FIST installation path:
Make sure the FIST installation path contains no more than 200 characters.
Avoid using spaces and the following special characters in the path: pound signs (#), percent sign (%), semi-colon (;), and ampersand (&).
In FIST-2.39 or earlier, as a best practice, do not use the backup and restore feature across different FIST versions.
Cautions
Verify the hardware and software compatibility for FIST. For more information, see "H3C UniServer B16000
H3C UniServer B5700 G5
H3C UniServer R4300 G5
H3C UniServer R4330 G5
H3C UniServer R4700 G5
H3C UniServer R4900 G5
H3C UniServer R4930 G5
H3C UniServer R4950 G5
H3C UniServer R5300 G5
H3C UniServer R5500 G5 AMD
H3C UniServer R5500 G5 INTEL
H3C UniServer R6900 G5
H3C UniServer B5700 G3
H3C UniServer B5800 G3
H3C UniServer B7800 G3
H3C UniServer E3200 G3
H3C UniServer R2700 G3
H3C UniServer R2900 G3
H3C UniServer R4300 G3
H3C UniServer R4500 G3
H3C UniServer R4700 G3
H3C UniServer R4900 G3
H3C UniServer R4950 G3
H3C UniServer R5300 G3
H3C UniServer R6700 G3
H3C UniServer R6900 G3
H3C UniServer R8900 G3
H3C UniServer R4900 G2
H3C UniServer R4900 G6
H3C UniServer R4700 G6
Hardware and software compatibility matrixes."
FIST can push FIST SMS to managed devices, but it cannot push AGENT (predecessor of FIST SMS) to devices.
Do not log in to FIST by using multiple accounts from the same Web browser.
If FIST runs in an AE environment, do not use the OS cloning function before the FIST cluster is set up. As a best practice, set up the FIST cluster immediately upon FIST deployment.
When FIST has incorporated blade servers with IPv6 addresses that start with FE80, a 500 error occurs if you install PXE through FIST for these blade servers.
For this software to run properly, make sure firewall is enabled for the following communication ports/protocols:
Table 32 Ports/protocols for FIST to communicate with HDM
Service | Default port number/protocol | |
Insecure port number/protocol | Secure port number/protocol | |
CD-Media | 5120/TCP | 5124/TCP |
IPMI | 623/TCP | 664/TCP |
KVM | 7578/TCP | 7582/TCP |
SNMP Trap | 162/UDP | N/A |
Web | 80/TCP | 443/TCP |
Table 33 Ports/protocols for FIST to communicate with OM
Service | Default port number/protocol | |
Insecure port number/protocol | Secure port number/protocol | |
Web | 80/TCP | 443/TCP |
Table 34 Ports/protocols for FIST to communicate with FIST SMS
Service | Default port number/protocol |
Web | 12580/TCP |
TFTP | 6900/UDP |
Table 35 Ports/protocols for FIST to communicate with iFIST
Service | Default port number/protocol |
Web | 12580/TCP |
Open problems and workarounds
None
List of resolved problems
Resolved problems in 2.54
202301111100
Symptom: After you add servers in bulk through FIST, some servers fail to be assigned labels.
Condition: This symptom occurs if you assign labels to servers after adding the servers in bulk through FIST.
202302150481
Symptom: If you use FIST to specify a template name that contains Chinese characters, garbled characters in Chinese are displayed when you export operation logs and view the logs in Excel format.
Condition: This symptom occurs if you use FIST to specify a template name that contains Chinese characters and then export operation logs and view the exported operation logs in Excel format.
Resolved problems in 2.52
202212121158
Symptom: Net-SNMP code vulnerability CVE-2022-44793 was detected by vulnerability scanning in a version earlier than FIST-2.52.
Condition: This symptom occurs if you perform vulnerability scanning in a version earlier than FIST-2.52.
202211290633
Symptom: SQLite input verification error CVE-2022-35737 was detected by vulnerability scanning in a version earlier than FIST-2.52.
Condition: This symptom occurs if you perform vulnerability scanning in a version earlier than FIST-2.52.
202211171605
Symptom: Vulnerability CVE-2016-9310 was detected by vulnerability scanning in a version earlier than FIST-2.52.
Condition: This symptom occurs if you perform vulnerability scanning in a version earlier than FIST-2.52.
202212121167
Symptom: Apache Tomcat environment vulnerability CVE-2022-42252 was detected by vulnerability scanning in a version earlier than FIST-2.52.
Condition: This symptom occurs if you perform vulnerability scanning in a version earlier than FIST-2.52.
Resolved problems in 2.51
202211080999
Symptom: Vulnerability CVE-2017-12626 was detected by vulnerability scanning in a version earlier than FIST-2.51.
Condition: This symptom occurs if you perform vulnerability scanning in a version earlier than FIST-2.51.
202211080605
Symptom: Vulnerability CVE-2019-10086 was detected by vulnerability scanning in a version earlier than FIST-2.51.
Condition: This symptom occurs if you perform vulnerability scanning in a version earlier than FIST-2.51.
202211080642
Symptom: Vulnerabilities CVE-2016-1000031 and CVE-2016-3092 were detected by vulnerability scanning in a version earlier than FIST-2.51.
Condition: This symptom occurs if you perform vulnerability scanning in a version earlier than FIST-2.51.
202211080971
Symptom: Vulnerability CVE-2020-13956 was detected by vulnerability scanning in a version earlier than FIST-2.51.
Condition: This symptom occurs if you perform vulnerability scanning in a version earlier than FIST-2.51.
202211080721
Symptom: Vulnerabilities CVE-2019-12406, CVE-2019-12419, CVE-2019-12423, CVE-2019-17573, CVE-2020-13954, CVE-2020-1954, CVE-2021-22696, and CVE-2021-30468 were detected by vulnerability scanning in a version earlier than FIST-2.51.
Condition: This symptom occurs if you perform vulnerability scanning in a version earlier than FIST-2.51.
Resolved problems in 2.50
202209080538
Symptom: FIST cannot be start up in Windows 10.
Condition: This symptom might occur in Windows 10.
202209210514
Symptom: Security vulnerability CVE-2022-35252 was detected during software vulnerability scanning for versions earlier than FIST-2.50.
Condition: None.
Resolved problems in 2.49
202209160718
Symptom: The network throughput field displays negative values on the performance monitoring page if FIST is used to manage a server with a large network throughput.
Condition: This symptom might occur if FIST is used to manage a server with a large network throughput.
Resolved problems in 2.48
202207251353
Symptom: PDF export failed through the information report module if a device in abnormal state exists in the FIST server list.
Condition: This symptom occurs if you export PDF files through the information report module when a device in abnormal state exists in the FIST server list.
202207210834
Symptom: Vulnerability CVE-2022-32208 was detected by vulnerability scanning in a version earlier than FIST-2.48.
Condition: This symptom occurs if you perform vulnerability scanning in a version earlier than FIST-2.48.
202207040996
Symptom: Vulnerability CVE-2022-34305 was detected by vulnerability scanning in a version earlier than FIST-2.48.
Condition: This symptom occurs if you perform vulnerability scanning in a version earlier than FIST-2.48.
Resolved problems in 2.47
202207040999
Symptom: Security vulnerability CVE-2022-2068 is found during vulnerability scanning in a version earlier than FIST-2.47.
Condition: This symptom occurs if vulnerabilities are scanned for a version earlier than FIST-2.47.
Resolved problems in 2.46
202205250941
Symptom: The security vulnerability of FastJson remote code execution via deserialization is found when vulnerabilities are scanned for a version earlier than FIST-2.46.
Condition: This symptom occurs if vulnerabilities are scanned for a version earlier than FIST-2.46.
202205250390
Symptom: Curl security vulnerability CVE-2022-30115 is found when vulnerabilities are scanned for a version earlier than FIST-2.46.
Condition: This symptom occurs if vulnerabilities are scanned for a version earlier than FIST-2.46.
202205250386
Symptom: Apache Tomcat security vulnerability CVE-2022-29885 is found when vulnerabilities are scanned for a version earlier than FIST-2.46.
Condition: This symptom occurs if vulnerabilities are scanned for a version earlier than FIST-2.46.
202205190404
Symptom: The security vulnerability of OpenSSL OS command injection CVE-2022-1292 is found when vulnerabilities are scanned for a version earlier than FIST-2.46.
Condition: This symptom occurs if vulnerabilities are scanned for a version earlier than FIST-2.46.
202205190397
Symptom: XStream SSRF security vulnerability CVE-2021-39150 is found when vulnerabilities are scanned for a version earlier than FIST-2.46.
Condition: This symptom occurs if vulnerabilities are scanned for a version earlier than FIST-2.46.
202205190375
Symptom: XStream arbitrary code execution security vulnerability CVE-2021-39139 is found when vulnerabilities are scanned for a version earlier than FIST-2.46.
Condition: This symptom occurs if vulnerabilities are scanned for a version earlier than FIST-2.46.
202205171693
Symptom: On the server list, open the H5 KVM for a server, close the window, and then delete the session (or the session times out) on the HDM page. When you open the H5 KVM again, the system prompts that your access is denied.
Condition: This symptom occurs if the following operations are performed:
On the server list, open the H5 KVM for a server, close the window, and then delete the session (or the session times out) on the HDM page.
Open the H5 KVM again.
202205270670
Symptom: If you export a server list in Excel format when 3600 servers are managed, the servers fail to be exported.
Condition: This symptom occurs if you export a server list in Excel format when 3600 servers are managed.
202204290328
Symptom: When a 9311 storage controller is installed on the server and multiple RAID arrays are created, install an OS on a RAID array, and export the OS image for cloning. In this case, the system prompts an error and prompts you to immediately restart the device to clear related SCSI.
Condition: This symptom occurs if a 9311 storage controller is installed on the server, multiple RAID arrays are created, an OS is installed on a RAID array, and the OS is exported for cloning.
Resolved problems in 2.45
202204291196
Symptom: When you bulk configure HDM devices in FIST and configure and add devices by using SN+IP, the devices might fail to be added.
Condition: This symptom occurs if you bulk configure HDM devices in FIST and configure and add devices by using SN+IP.
202204280280
Symptom: After nodes in a cluster are replaced, the data of some functions cannot be obtained correctly. When the primary node is restarted to trigger primary/secondary node switchover, data is not synchronized.
Condition: This symptom occurs if nodes in a cluster are replaced.
202204280125
Symptom: If you use the component update function to update the HDM and BIOS firmware at the same time and select to restart HDM immediately to make it take effect, and the HDM to be deployed is of version 2.96 and later supported by FIST, the components will fail to be deployed after HDM is restarted and takes effect, and the system prompts failure to set the firmware type.
Condition: This symptom occurs if you use the component update function to update the HDM and BIOS firmware at the same time and select to restart HDM immediately to make it take effect, and the HDM to be deployed is of version 2.96 and later supported by FIST.
202204221518
Symptom: The HDM of the device managed by FIST has network exceptions. The HDM can be successfully pinged but you cannot log in to it. After a period of time, there are too many connections on the device, and exceptions occur on the FIST page.
Condition: This symptom occurs if the HDM of the device managed by FIST has network exceptions, the HDM can be successfully pinged, but you cannot log in to it.
Resolved problems in FIST 2.44
202203241389
Symptom: When you use FIST to manage an H3C UniServer R8900 G3 server installed with a RAID-LSI-9560-LP-16i-8GB controller, if you use the server configuration template function to perform out-of-band RAID configuration for hard drives in slots Front14 and Front15, the system prompts that the hard drives are not found.
Condition: This symptom occurs if you use FIST to manage an H3C UniServer R8900 G3 server installed with a RAID-LSI-9560-LP-16i-8GB controller and use the server configuration template function to perform out-of-band RAID configuration for hard drives in slots Front14 and Front15.
202203291578
Symptom: When you use FIST to manage an H3C UniServer R4500 G3 server and use the server configuration template to configure RAID and select member drives for a logical drive, the physical drives in slots Rear7 and Rear8 are not displayed in the dropdown list.
Condition: This symptom occurs if you use FIST to manage an H3C UniServer R4500 G3 server and use the server configuration template to configure RAID.
Resolved problems in FIST 2.43
202202230776
Symptom: An installation failure occurs when you use FIST to push and install the FIST SMS software in a Windows operating system.
Condition: This symptom occurs if you use FIST to push and install the FIST SMS software in a Windows operating system.
202203030131
Symptom: Failed to update HDM after FIST incorporates HDM and you change the HTTP port number of HDM to a non-default number.
Condition: This symptom occurs if you update HDM after FIST incorporates HDM and the HTTP port number of HDM is changed to a non-default number.
202203090672
Symptom: If you go to the Reports > Server Inventory page after FIST incorporates FIST SMS and a FIST SMS exception occurs, the server inventory list is empty. In addition, this page displays message Operation failed. Please refresh the page and try again. in the lower right corner.
Condition: This symptom occurs if you go to the Reports > Server Inventory page after FIST incorporates FIST SMS and a FIST SMS exception occurs.
202203210611
Symptom: OpenSSL vulnerability CVE-2022-0778 is found when vulnerabilities are scanned for a version earlier than FIST-2.43.
Condition: This symptom occurs if vulnerabilities are scanned for a version earlier than FIST-2.43.
202203221441
Symptom: OpenSSH security vulnerabilities CVE-2021-36368 and CNNVD-202203-1230 are found when vulnerabilities are scanned for a version earlier than FIST-2.43.
Condition: This symptom occurs if vulnerabilities are scanned for a version earlier than FIST-2.43.
202203041236
Symptom: cURL security vulnerabilities CVE-2020-8284, CVE-2020-8285, CVE-2020-8286, CVE-2021-22876, CVE-2021-22890, CVE-2021-22901, CVE-2021-22922, CVE-2021-22923, and CVE-2021-22946 are found when vulnerabilities are scanned for a version earlier than FIST-2.43.
Condition: This symptom occurs if vulnerabilities are scanned for a version earlier than FIST-2.43.
202203041198
Symptom: Libcurl security vulnerabilities CVE-2021-22924 and CVE-2021-22945 are found when vulnerabilities are scanned for a version earlier than FIST-2.43.
Condition: This symptom occurs if vulnerabilities are scanned for a version earlier than FIST-2.43.
202203041175
Symptom: Security vulnerability CVE-2019-17498 is found when vulnerabilities are scanned for a version earlier than FIST-2.43. With this vulnerability, in libssh2 v1.9.0 and earlier versions, the SSH_MSG_DISCONNECT logic in packet.c has an input check vulnerability.
Condition: This symptom occurs if vulnerabilities are scanned for a version earlier than FIST-2.43.
202202280448
Symptom: Security vulnerability CVE-2022-23181 (Apache Tomcat privilege permission and access control vulnerability) is found when vulnerabilities are scanned for a version earlier than FIST-2.43.
Condition: This symptom occurs if vulnerabilities are scanned for a version earlier than FIST-2.43.
Resolved problems in FIST 2.42
202201200400
Symptom: Failed to log in to FIST on an AE module after you configure DNS settings for FIST on the AE module that has joined a cluster.
Condition: This symptom occurs if you configure DNS settings for FIST on an AE module that that has joined a cluster.
202201251299
Symptom: The system detects the OpenSSL DoS vulnerability (CVE-2021-3712) when vulnerability scanning is performed in versions earlier than FIST-2.42.
Condition: This symptom occurs if vulnerability scanning is performed in versions earlier than FIST-2.42.
202201251276
Symptom: The system detects the OpenSSL buffer overflow vulnerability (CVE-2021-3711) when vulnerability scanning is performed in versions earlier than FIST-2.42.
Condition: This symptom occurs if vulnerability scanning is performed in versions earlier than FIST-2.42.
202201251330
Symptom: The Apache vulnerability caused by HTTPD packets is found when vulnerabilities are scanned for a version earlier than FIST-2.42.
Condition: This symptom occurs if vulnerabilities are scanned for a version earlier than FIST-2.42.
Resolved problems in FIST 2.41
202112291390
Symptom: The Apache Log4j remote code execution vulnerability CVE-2021-44832 occurs when you use a vulnerability scanner to scan for vulnerabilities in versions earlier than FIST-2.41.
Condition: This symptom might occur if you use a vulnerability scanner to scan for vulnerabilities in versions earlier than FIST-2.41.
202112301021
Symptom: The CVE-2021-42550 vulnerability occurs when you use a vulnerability scanner to scan for vulnerabilities in versions earlier than FIST-2.41.
Condition: This symptom might occur if you use a vulnerability scanner to scan for vulnerabilities in versions earlier than FIST-2.41.
202112291121
Symptom: The system fails to open H5 KVM when you access AE100 through VGA and click an IPv6 address that starts with FE80 on the node list.
Condition: This symptom might occur if you access AE100 through VGA and click an IPv6 address that starts with FE80 on the node list.
Resolved problems in FIST 2.40
202111251836
Symptom: When you use FIST to push and install the FIST SMS software in a Windows operating system, a connection error is reported.
Condition: This symptom occurs if you use FIST to push and install the FIST SMS software in a Windows operating system.
202112091349
Symptom: FIST failed to create a cluster. When creation failed, the FIST connection between the primary and secondary AE modules are faulty.
Condition: This symptom occurs when FIST creates a cluster.
202111240608
Symptom: When multiple scheduled deployment tasks with short intervals between their execution time are added for a node, the scheduled tasks are not triggered.
Condition: This symptom occurs if multiple scheduled deployment tasks with short intervals between their execution time are added for a node.
202112211343
Symptom: CVE-2021-4104 is found when vulnerabilities are scanned for a version earlier than FIST-2.40.
Condition: This symptom occurs if vulnerabilities are scanned for a version earlier than FIST-2.40.
202111291027
Symptom: Nginx vulnerability CVE-2021-23017 is found when vulnerabilities are scanned for a version earlier than FIST-2.40.
Condition: This symptom occurs if vulnerabilities are scanned for a version earlier than FIST-2.40.
202111291037
Symptom: Apache Tomcat resource management vulnerability CVE-2021-42340 is found when vulnerabilities are scanned for a version earlier than FIST-2.40.
Condition: This symptom occurs if vulnerabilities are scanned for a version earlier than FIST-2.40.
202111291149
Symptom: Nginx environment vulnerability CVE-2019-20372 is found when vulnerabilities are scanned for a version earlier than FIST-2.40.
Condition: This symptom occurs if vulnerabilities are scanned for a version earlier than FIST-2.40.
202112141622
Symptom: OpenSSH vulnerabilities CVE-2021-41617 and CNNVD-202109-1695 are found when vulnerabilities are scanned for a version earlier than FIST-2.40.
Condition: This symptom occurs if vulnerabilities are scanned for a version earlier than FIST-2.40.
202112141628
Symptom: OpenSSH vulnerabilities CVE-2016-20012 and CNNVD-202109-1073 are found when vulnerabilities are scanned for a version earlier than FIST-2.40.
Condition: This symptom occurs if vulnerabilities are scanned for a version earlier than FIST-2.40.
Resolved problems in FIST 2.39
202111081728
Symptom: FIST fails to record an operation log entry when the alarm forwarding feature is used to test whether an email recipient configured on the SMTP Settings tab can receive an alarm.
Condition: This symptom might occur when the alarm forwarding feature is used to test whether an email recipient configured on the SMTP Settings tab can receive an alarm.
202111060598
Symptom: The exported FIST data in the backup file is incomplete.
Condition: This symptom might occur when you export FIST data for backup.
Resolved problems in FIST 2.38
202109271027
Symptom: When you access FIST on an AE device in VGA method and then open KVM, the system prompts that the access is denied.
Condition: This symptom occurs if you access FIST on an AE device in VGA method and then open KVM.
Resolved problems in FIST 2.37
202108120553
Symptom: Vulnerability CVE-2019-16255 for Ruby is found when vulnerabilities are scanned for FIST-2.36 and earlier versions.
Condition: This symptom occurs if vulnerabilities are scanned for FIST-2.36 and earlier versions.
202108300349
Symptom: Vulnerability CVE-2017-3735 for OpenSSL is found when vulnerabilities are scanned for FIST-2.36 and earlier versions.
Condition: This symptom occurs if vulnerabilities are scanned for FIST-2.36 and earlier versions.
202107301157
Symptom: Vulnerabilities in vulnerable JavaScript libraries are found when vulnerabilities are scanned for FIST-2.36 and earlier versions.
Condition: This symptom occurs if vulnerabilities are scanned for FIST-2.36 and earlier versions.
Resolved problems in FIST 2.36
202107260700
Symptom: When FIST installs both the Windows Server 2016 system and VROC drivers at the same time, FIST reports an error of failing to find a PCIe device.
Condition: This symptom occurs if FIST installs both the Windows Server 2016 system and VROC drivers at the same time.
202107280586
Symptom: When you enter a username containing a special character at sign (@) in the device discovery module of FIST, FIST reports an error of invalid username.
Condition: This symptom occurs if you enter a username containing a special character at sign (@) in the device discovery module of FIST.
Resolved problems in FIST 2.35
202106240623
Symptom: If FIST uses an IPv6 address starting with FE80 to incorporate a server and then performs offline firmware update for the server, firmware update fails.
Condition: This symptom occurs if FIST uses an IPv6 address starting with FE80 to incorporate a server and then performs offline firmware update for the server.
202105190381
Symptom: If FIST uses an IPv6 address starting with FE80 to incorporate a server, you cannot open the KVM by clicking the KVM.
Condition: This symptom occurs if FIST uses an IPv6 address starting with FE80 to incorporate a server and then you click the KVM to open the KVM.
202106231546
Symptom: In the Linux environment, if FIST uses an IPv6 address starting with FE80 to incorporate a server, the HDM configuration template fails to be exported.
Condition: This symptom occurs if FIST uses an IPv6 address starting with FE80 to incorporate a server and then you export an HDM configuration template.
Resolved problems in FIST 2.34
202105270432
Symptom: If you modify the FIST system time to be earlier than the current time after applying a server configuration template to a server, applying a server configuration template to the server again fails.
Condition: This symptom occurs if you modify the FIST system time to be earlier than the current time after applying a server configuration template to a server.
202106041184
Symptom: After FIST incorporates a server and you open the KVM, you cannot zoom in or zoom out the KVM window, and related control buttons do not exist on the KVM window.
Condition: This symptom occurs if you add a server and click the KVM.
Resolved problems in FIST 2.33
202104271045
Symptom: The system failed to recognize the physical drives during RAID configuration on a server installed with a HBA-LSI-9311-8i-A1-X storage controller.
Condition: This symptom might occur if you configure RAID on a server that is installed with a HBA-LSI-9311-8i-A1-X storage controller.
Resolved problems in FIST 2.32
202104090129
Symptom: The bulk component update tasks were deleted successfully but failures were recorded in the operation log.
Condition: This This symptom occurs if you delete the component update tasks in bulk during the FIST component inventory process.
Resolved problems in FIST 2.31
202102220600
Symptom: The server template feature is not available after the backup configuration file is imported to FIST.
Condition: This symptom occurs if you import the backup configuration file across different FIST versions.
Resolved problems in FIST 2.30
202101221119
Symptom: The FIST server list page reports an error after the user initiates a server search operation on the page
Condition: This symptom occurs if the FIST server list contains unsupported servers and a user searches for servers on the page.
Resolved problems in FIST 2.29
202012040219
Symptom: CAS5.0 installation through a server template gets stuck
Condition: This symptom occurs if the root password specified for CAS5.0 in the server template contains spaces.
Resolved problems in FIST 2.00.28
202009291286
Symptom: The H5 KVM remote console cannot be launched for a server that has a link-local IPv6 address (starting with FE80) after it is added to FIST
Condition: This symptom occurs if FIST runs in a Linux environment and a server with a link-local IPv6 address (starting with FE80) is added to FIST.
Resolved problems in FIST 2.00.27
202010100985
Symptom: After a server template is automatically applied to a rack server, no related application log is displayed.
Condition: This symptom occurs if FIST is restarted after a server template is automatically applied to a rack server.
Resolved problems in FIST 2.00.26
202006190857
Symptom: A REPO package on a server running Windows 10 fails to be added to FIST by using the UNC Path type.
Condition: This symptom occurs when the user attempts to add a REPO package on a server running Windows 10 by using the UNC Path type.
Resolved problems in FIST 2.00.25
202008060957
Symptom: Failed to apply RAID settings to a server.
Condition: This symptom occurs if the server is installed with the HBA-H5408-Mf-8i storage controller.
Resolved problems in FIST 2.00.24
202006290699
Symptom: After installing FIST SMS on a Windows server, FIST cannot automatically add the FIST SMS server node to its system.
Condition: None.
Resolved problems in FIST 2.00.23
202006160665
Symptom: The power system status displayed for an enclosure in FIST does not match that displayed in the OM of the enclosure.
Condition: This symptom occurs if the rated power of the enclosure is lower than the power allocated to the enclosure.
Resolved problems in FIST 2.00.22
202004281254
Symptom: FIST fails to use a repository file to install a chipset driver on a server at the same time as Windows 2012R2 is installed.
Condition: None.
Resolved problems in FIST 2.00.21
First release.
Troubleshooting
You can obtain help from the following links:
Access https://www.h3c.com/en/Support/Resource_Center/Technical_Documents/, select the product category and model, and search for related cases in the Maintain section.
Access https://zhiliao.h3c.com/, and search for related cases by product model or feature keyword.
Related documentation
Documentation set
H3C Servers FIST Installation Guide.
H3C Servers FIST User Guide.
Technical support
To obtain support services, contact H3C Support at [email protected].
Appendix A Software feature and version compatibility and software feature list
Software feature and version compatibility matrix
Table 36 Software feature and version compatibility matrix
Category | Features | Compatible software version |
OS installation | Installation of the following operating systems: Red Hat Enterprise Linux 7.6 (64 bit) (includes KVM) Red Hat Enterprise Linux 7.7 (64 bit) (includes KVM) Red Hat Enterprise Linux 7.8 (64 bit) (includes KVM) CentOS 7.6 (64 bit) CentOS 7.7 (64 bit) CentOS 7.8 (64 bit) VMware ESXi 6.7 U3(64 bit) VMware ESXi 7.0 (64 bit) | iFIST-1.00.23 or later. |
Installation of Red Hat Enterprise Linux 7.2 (64 bit) | iFIST-1.00.14 or later. | |
Installation of the following operating systems: Red Hat Enterprise Linux 7.3 (64 bit) Red Hat Enterprise Linux 7.4 (64 bit) Windows server 2012 R2 Standard Windows server 2012 R2 Datacenter Windows server 2012 R2 Essentials | iFIST-1.00.14 or later. | |
Installation of the following operating systems: SLES 12 SP3(64 bit) CentOS 7.5 (64 bit) Windows Server 2016 Standard Windows Server 2016 Datacenter Windows Server 2016 Essential | iFIST-1.01.07 or later. | |
Installation of the following operating systems: Red Hat Enterprise Linux 6.7 (64 bit) Red Hat Enterprise Linux 6.8 (64 bit) Red Hat Enterprise Linux 6.9 (64 bit) SLES 11 SP4(64 bit) SLES 12 SP1(64 bit) SLES 12 SP2(64 bit) | iFIST-1.01.08 or later. | |
Installation of VMware ESXi 6.5 U2(64 bit) | iFIST-1.01.10 or later. | |
Installation of the following operating systems: Red Hat Enterprise Linux 7.5 (64 bit) (includes KVM) Microsoft Windows Server 2019 Standard Microsoft Windows Server 2019 Datacenter VMware ESXi 6.7 (64 bit) CentOS 7.4 (64 bit) | iFIST-1.01.12 or later. | |
Installation of the following operating systems: Microsoft Hyper-V Server 2012 R2 Microsoft Hyper-V Server 2016 Ubuntu Server 17.10 (64 bit) – LTS Ubuntu Server 17.10.1 (64 bit) – LTS Ubuntu Server 18.04 (64 bit) – LTS Ubuntu Server 18.04.1 (64 bit) – LTS Ubuntu Server 18.04.2 (64 bit) – LTS Ubuntu Server 18.04.3 (64 bit) – LTS CentOS 7.3 (64 bit) | iFIST-1.01.13 or later. | |
Installation of CAS5.0(E0513/E0526) | iFIST-1.01.14 or later. | |
Installation of Oracle Linux 8.2 | iFIST-1.29 or later | |
Installation of CentOS 8.3(64 bit) and Red Hat Enterprise Linux 8.3 (64 bit) (includes KVM) | iFIST-1.36 or later | |
Installation of CentOS 8.4 (64 bit) and Red Hat Enterprise Linux 8.4 (64 bit) (includes KVM) | iFIST-1.42 or later | |
Profile application | Server auto configuration | Use HDM-1.11.24 for optimal user experience. HDM-1.11.25 is not recommended because of the interface changes made in the version. NOTE: Before you use the server auto configuration feature to configure a server, make sure the server is powered off. The rack without status needs to be used with hdm-1.30.17 and later |
Copy BIOS configuration | BIOS-1.11.20 or later. | |
KS scripted OS deployment | iFIST-1.01.20 or later. | |
Out-of-band RAID configuration | HDM-1.30.15 or later. | |
Clone-mode OS installation | iFIST-1.01.21 or later. | |
Connection configuration | only supports H3C S6850-56HF and H3C S6800-54QF switches | |
Storage controllers supported by the profile application feature | HBA-1000-M2-1 RAID-P430-M1 RAID-P430-M2 HBA-H460-M1 RAID-P460-M4 HBA-H460-B1 RAID-P460-B4 RAID-LSI-9361-8i(1G)-A1-X RAID-LSI-9361-8i(2G)-1-X RAID-LSI-9460-8i(2G) RAID-LSI-9460-8i(4G) RAID-L460-M4 RAID-LSI-9460-16i(4G) RAID-LSI-9560-LP-8i(4GB) RAID-P5408-Mf-8i-4GB-BSF-F1 HBA-H5408-Mf-8i HBA-LSI-9400-8i HBA-LSI-9400-16i HBA-LSI-9440-8i HBA-LSI-9311-8i-A1-X | HDM-1.11.20 or later. |
Manage switches | Supported switch models: H3C S6800-54QT H3C S6850-56HF H3C S6800-54QF H3C UIS M8380-C H3C UIS M8310 | H3C Comware V700R001B70D012 or later. |
Deployment | Offline firmware update | If you use the offline firmware update feature together with HDM in version 2.42, the component update progress and result cannot be obtained. |
Managed modules | Modules that can be managed by FIST: AE module Compute module Interconnect module Power and fan modules Enclosure system logs. Compute node event logs Enclosure alarm summary Bulk power cap configuration. | OA UOA V500R002B01D007 or later. NOTE: For H3C UniServer R4950 G3 servers, the bulk power cap configuration feature is available only when the servers have HDM 1.30.05 or later installed. |
Server | Manually adding servers Device discovery Bulk importing and adding servers Bulk configuring IPs Managing labels | The function of bulk configuring IPs is available only in 3.10 and later |
Category | Features |
Web UI | Web interface in both Chinese and English Online help Compatible with IE 11 or later, Chrome 66 or later, and Firefox 60 or later |
RESTful API | Provides RESTful APIs for use by third-party systems. |
Device management | Server list Enclosure list Switch list |
Template management | Server configuration templates Enclosure configuration templates Switch configuration templates Repositories HDM/BIOS settings Image management Clone-mode OS installation Diskless boot |
Deployment | Applying enclosure configuration files Enclosure configuration files Applying server configuration files Service configuration files Component update Firmware update |
Monitor | Reports in Excel and PDF formats. Alarm forwarding (support SNMP, SMTP, SMS notification, voice, notification, and WeChat notification) |
Tools | DHCP server PXE Software push and installation |
System management | User management (local users and LDAP users) NTP settings Operation log |
The following information describes how to update the FIST firmware.
Screenshots in this section are for illustration only. They might vary as the software version changes.
FIST is an intelligent, extensible server management software product that uses the browser/server model. FIST provides comprehensive management capabilities, including device monitoring, firmware update, and configuration templates for customers to manage and maintain servers remotely from a unified, intuitive graphical user interface.
FIST provides two types of installation packages. One is the .tar installation package, which allows you to run FIST directly on a server after decompressing the installation package on the server.
FIST also provides an ISO image file, which allows you to install a CentOS system with the FIST software embedded. You can mount the ISO image to the target server and then have the server boot to the image to start the installation process. No further manual intervention is required. FIST automatically runs in the background upon the CentOS installation is complete.
Updating FIST on a Windows server by using the .tar installation package
1.Download the FIST installation package (AppFist-1.00.04.tar.gz, in this example), and then decompress the package.
Figure 2 Decompressed FIST installation package
2.Double-click the FistLaunch_x64.bat file.
The FIST console opens a few seconds later.
3.Verify the following FIST connection settings:
HTTP Port: HTTP service port number of FIST. The value range is 1 to 65535. By default, HTTP port 80 is used for login. Make sure the specified port number is not used by another service.
HTTPS Port: HTTPS service port number of FIST. The value range is 1 to 65535. Make sure the specified port number is not used by another service.
Session Timeout: Session timeout time in seconds. The value range is 600 to 1800, and the default is 1800.
Front Display: Whether or not to display the FIST console always in the foreground.
4.Click START.
5.Click Details to view the FIST startup progress and verify that it is started correctly.
Figure 4 Viewing FIST startup details
Updating FIST on a Linux server by using the .tar installation package
You must have root privileges to perform this task.
After installation, you can run FIST on the server by using an account with administrative privileges.
Updating and starting FIST from the GUI
1.Download the FIST installation package (AppFist-1.00.04.tar.gz, in this example), and then save the package to the Linux server. This examples save the package to the root directory of the Linux server.
2.Open the terminal window.
3.Enter tar -xf AppFist–1.00.04.tar.gz, and then press Enter to decompress the installation package.
Figure 5 Decompressing the FIST installation package
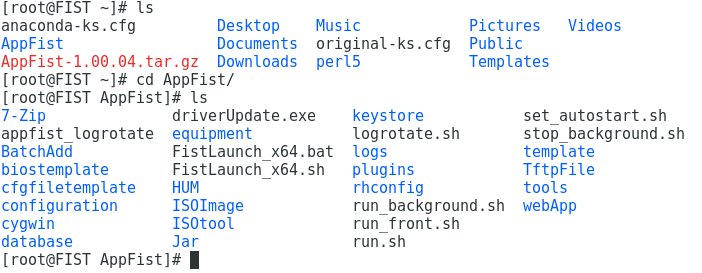
4.Enter cd AppFist/ to open the AppFist folder.
Figure 6 Opening the AppFist folder
5.Enter bash FistLaunch_x64.sh, and then press Enter to launch the FIST console window.
6.Verify the following FIST connection settings:
HTTP Port: HTTP service port number of FIST. The value range is 1 to 65535, and default is 80. Make sure the specified port number is not used by another service.
HTTPS Port: HTTPS service port number of FIST. The value range is 1 to 65535, and default is 443. Make sure the specified port number is not used by another service.
Session Timeout: Session timeout time in seconds. The value range is 600 to 1800, and the default is 1800.
Front Display: Whether or not to display the FIST console always in the foreground.
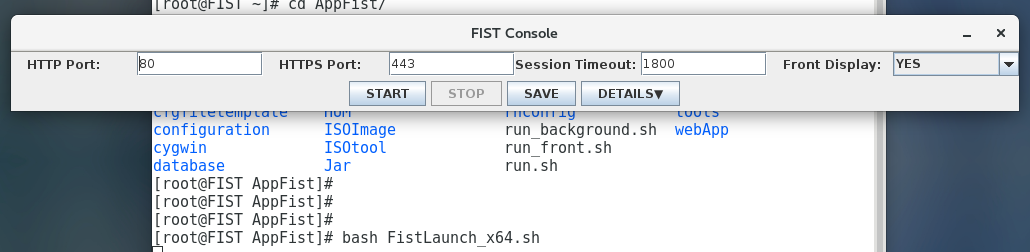
7.Click START.
IMPORTANT: Keep the FIST console window open while FIST is running. Closing the window will interrupt the FIST service. |
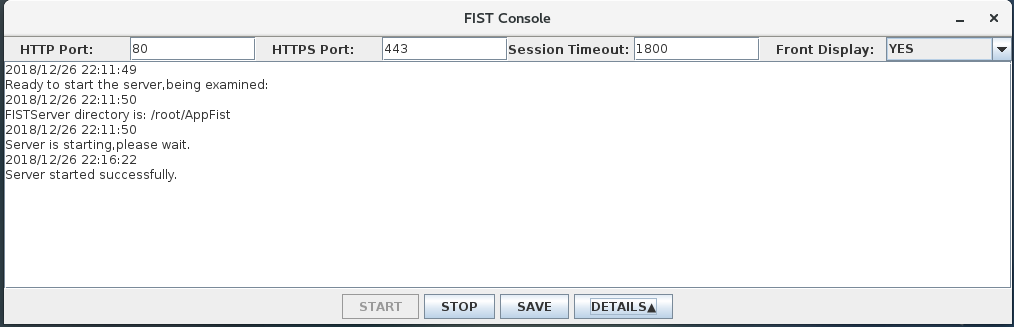
8.Click Details to view the FIST startup progress and verify that it is started correctly.
Figure 8 Viewing FIST startup details
Updating and starting FIST from the CLI
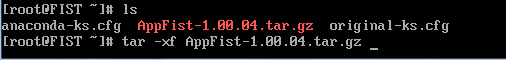
1.Download the FIST installation package (AppFist-1.00.04.tar.gz, in this example), and then save the package to the root directory of the Linux server.
2.Enter tar -xf AppFist–1.00.04.tar.gz, and then press Enter to decompress the installation package.
Figure 9 Decompressing the FIST installation package
3.Enter cd AppFist/ to open the AppFist folder.
Figure 10 Opening the AppFist folder
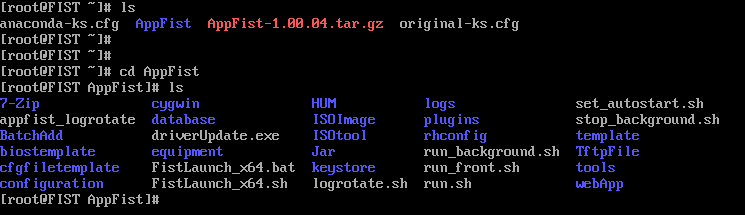
4.Execute the ./run.sh. command. At the Permission denied prompt, enter chmod u+x run.sh to grant the execute permission to the file.
Figure 11 Granting the execute permission
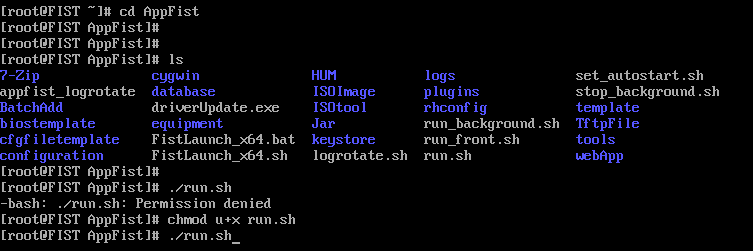
IMPORTANT: Do not start multiple FIST processes on the same server. Doing so might cause FIST startup failures. |
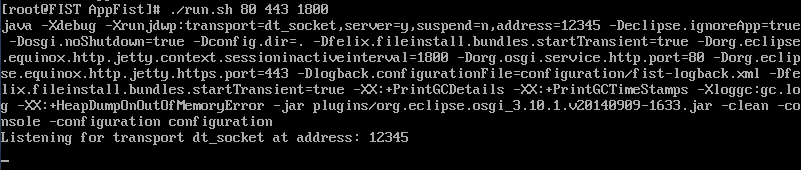
5.Enter ./run.sh 80 443 1800 to start FIST.
The values 80 and 443 are the default HTTP and HTTPS port numbers of FIST, both of which can be changed to a value in the range of 1 to 65535.
The value 1800 is the default session timeout time, which can be changed to a value in the range of 600 to 1800, in seconds.
Figure 12 Running FIST
Updating and starting FIST by using the ISO image
FIST provides an ISO image file which allows you to install a UI-equipped H3C Linux 1.1.2 system with the FIST software embedded. You can mount the ISO image to the target server and then have the server boot to the image to start the installation process. No further manual intervention is required. FIST automatically runs in the background upon completion of the Linux installation.
The AE module comes with FIST preinstalled. You can use the ISO image to update the FIST module in an AE module. For information about how to mount the ISO image, see H3C Servers Operating Systems Installation Guide.
The following information describes the procedure for using the ISO image to update FIST in an AE module.
1.Launch the HDM KVM console of the AE module.
2.Select Media > Virtual Media Wizard from the top menu bar.
The Virtual Media window opens.
Figure 13 Virtual Media window
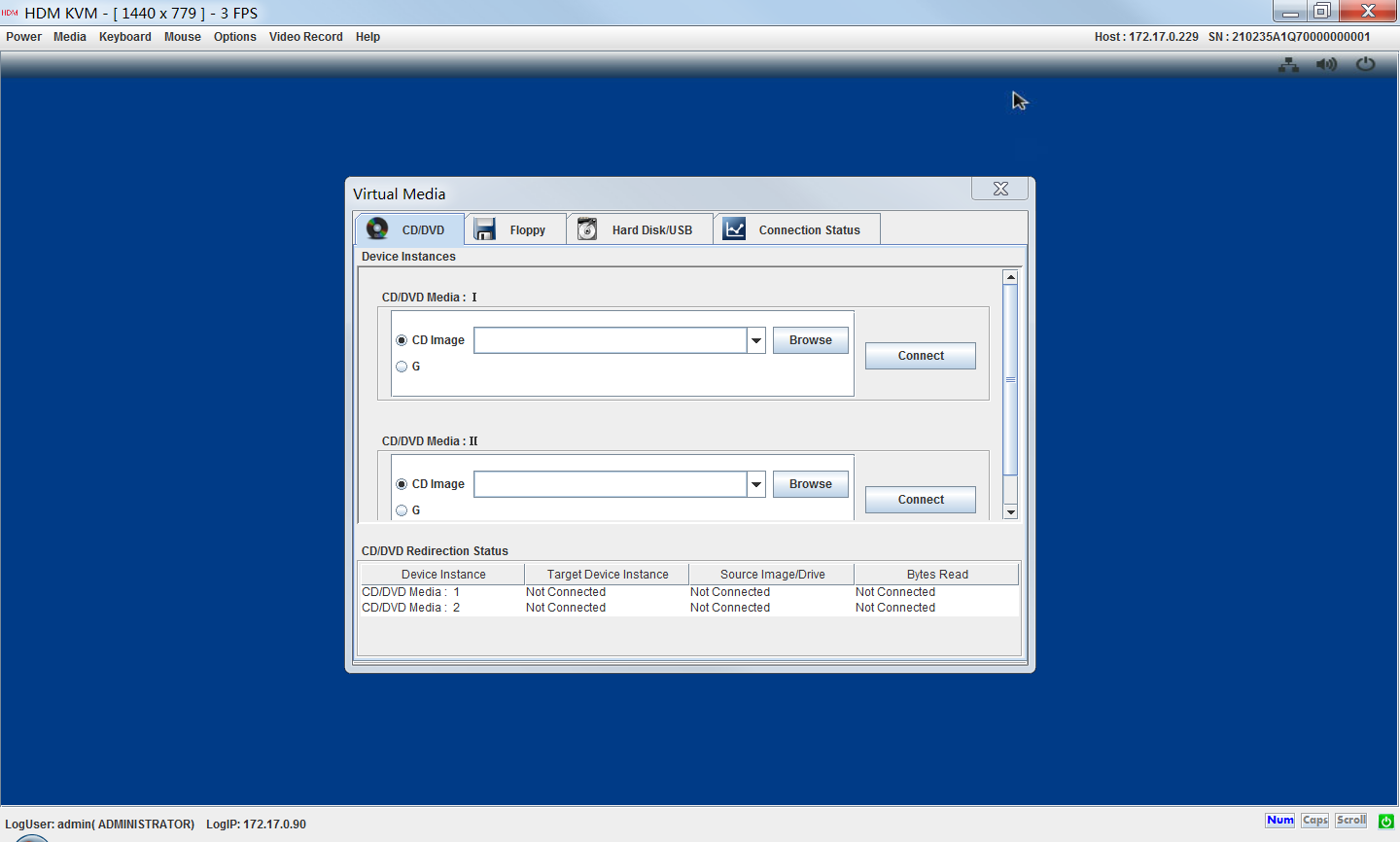
3.On the CD/DVD tab, click Browse next to a CD Image field to select the ISO image file, and then click Open.
4.Click Connect.
Figure 14 ISO image file mounted
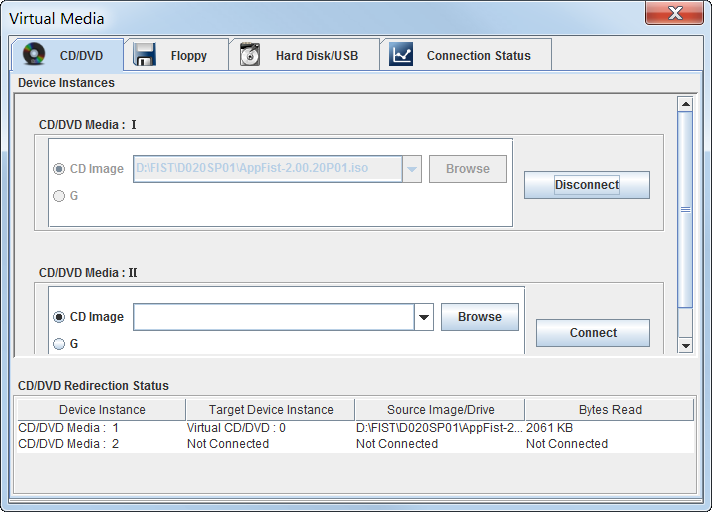
5.Reboot the server. The server automatically enters the virtual CDROM boot option.
6.The system starts to install FIST. The process takes about 30 minutes and does not require manual intervention.
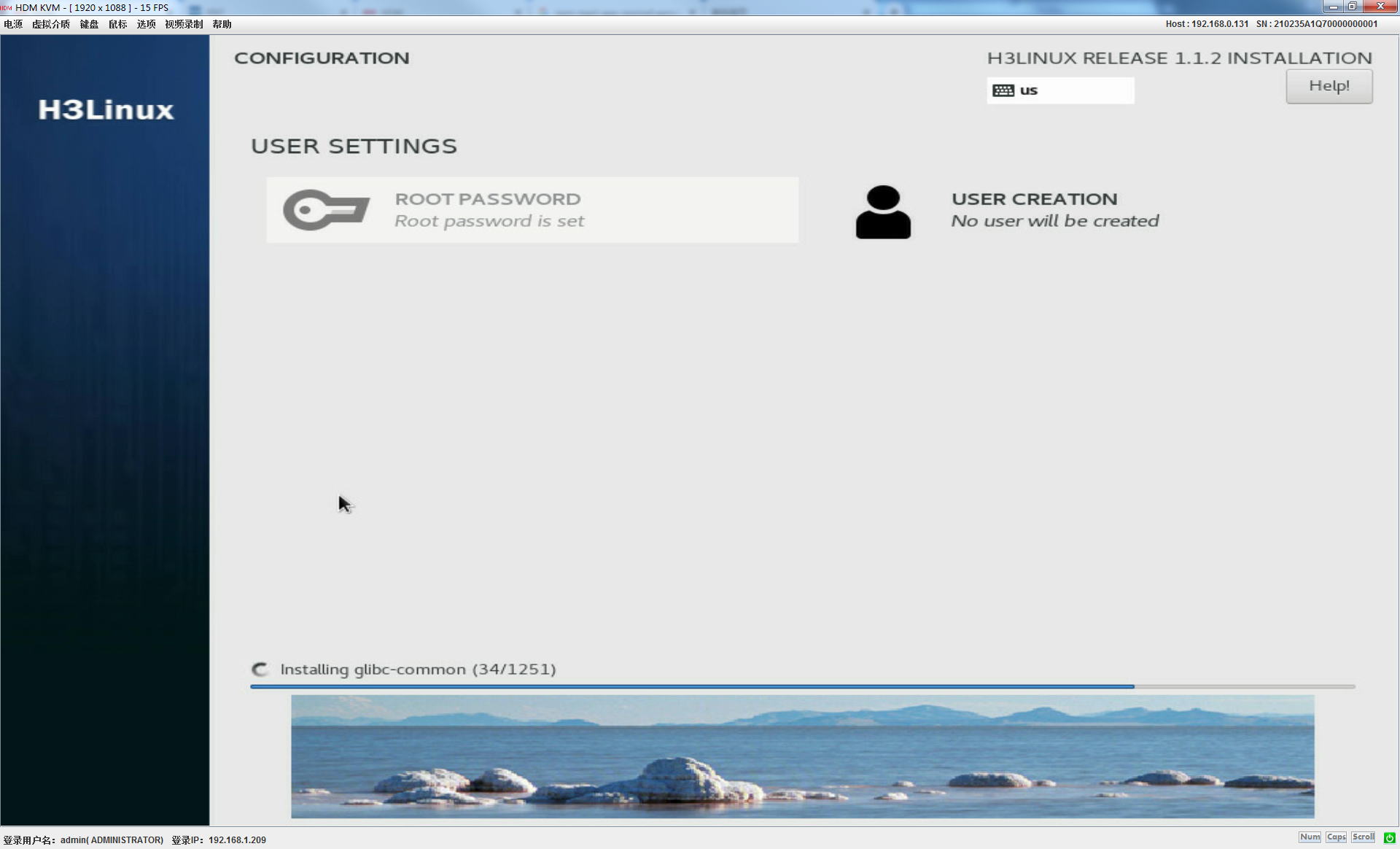
7.After the installation is complete, FIST automatically starts to run in the background.
Handling firmware update failures
If the FIST firmware update fails, the system starts up with the original firmware version.
To resolve the firmware update failure issue:
1.Verify that a root user account is used to perform the firmware update operation.
2.Verify that the firmware image file is not corrupted.
Deleting the browsing history in Internet Explorer
1.Click the Tools icon, and then select Internet options from the menu that opens.
Figure 16 Tools menu
2.Click Delete….
Figure 17 Internet options
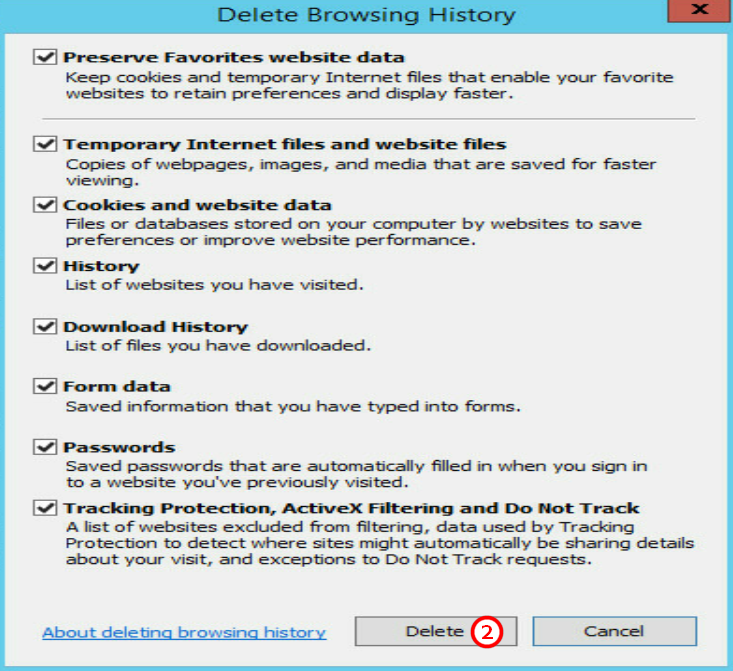
3.In the Delete Browsing History window, click Delete.
Figure 18 Deleting the browsing history
Deleting the browsing history in Firefox
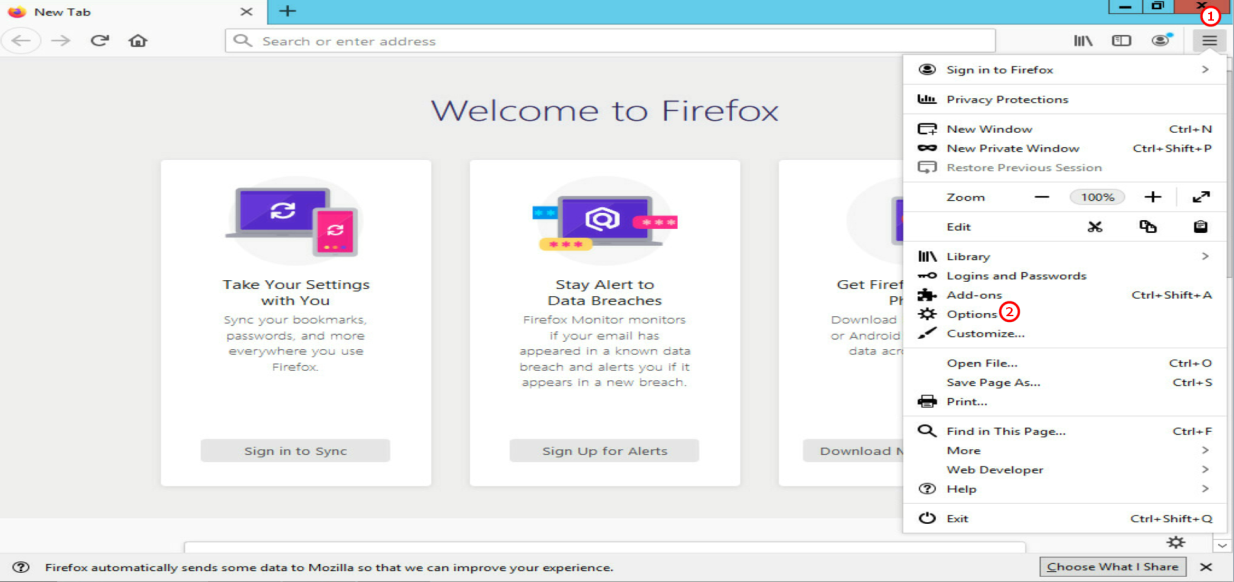
1.Click the Open menu icon, and then select Options from the menu that opens.
Figure 19 Menu options
2.In the left navigation pane, select Privacy & Security, and then select Clear History…
Figure 20 Privacy & Security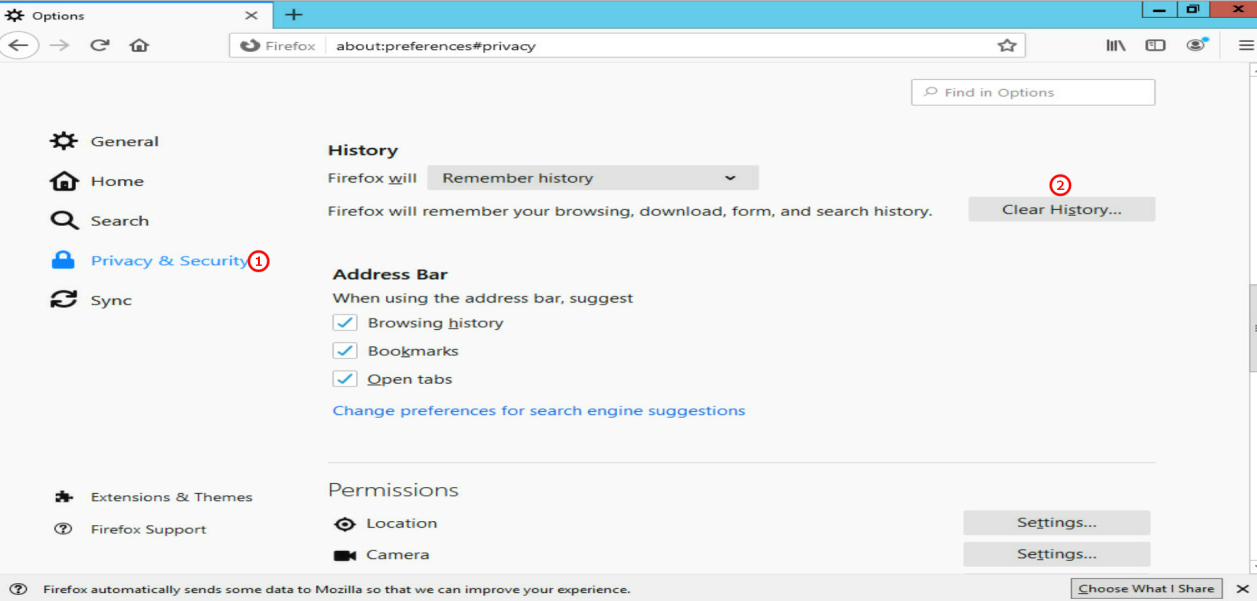
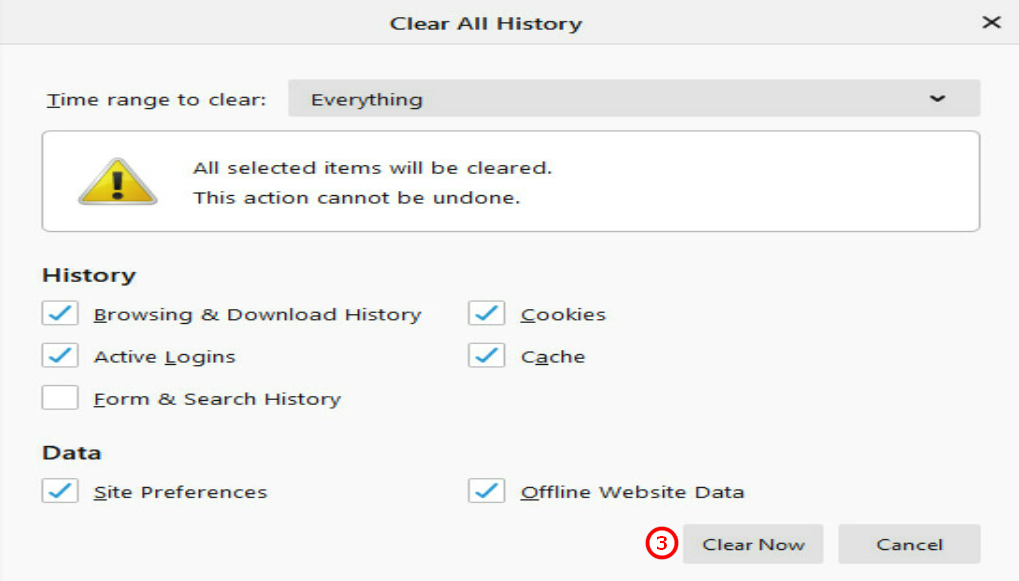
3.Click Clear Now.
Figure 21 Clearing history now
Deleting the browsing history in Chrome
1.Click the Customize and control Google Chrome menu icon, and then select History from the menu that opens.
Figure 22 Customize and control Google Chrome menu
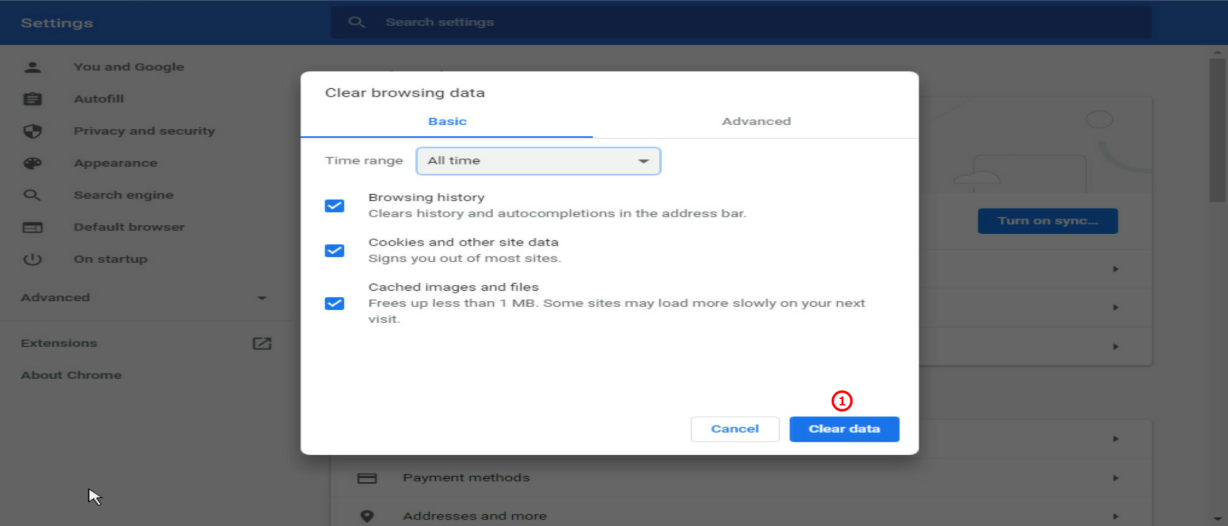
2.Click Clear data….
Figure 23 Clearing browsing data
Appendix C Upgrading FIST software by using the upgrade package
This feature is available in FIST-2.39 and later.
This feature allows you to upgrade or downgrade the FIST software version. FIST software upgrade will not cause FIST data loss. However, as a best practice, back up the critical data before upgrading FIST.
The FIST upgrade interface is available only for FIST running on a VM or AE module. FIST of the package version does not need installation. To upgrade FIST of the package version, replace the new package with the old package.
To ensure that FIST can be upgraded normally, first stop the other FIST operations in progress before upgrading FIST.
Upgrading FIST will log out all logged-in users except the current user. Additionally, other users cannot log in during the FIST upgrade process.
Upgrading FIST will interrupt or restart related processes in the system where FIST is installed. If these processes are being used, related services might be interrupted.
Procedure (for FIST on a VM or AE module)
1.In the navigation pane, select Menu > System > Maintain and Upgrade. Click the FIST Software Upgrade tab.
Figure 24 FIST Software Upgrade page
2.(Optional.) Click Obtain Latest FIST Image to download the needed FIST software upgrade package from the official website.
3.Click the … button for the software upgrade operation, select the FIST upgrade package, and click Upload to upload the upgrade package.
4.Click Start Upgrade. In the dialog box that opens, click OK to start upgrading FIST.
After the upgrade is finished, FIST will automatically restart and return to the login page. After FIST is restarted, refresh the page, and log in to use the new FIST version.
Procedure (for FIST of the package version)
IMPORTANT: After the upgrade, the port configuration cannot be retained. |
1.Obtain the FIST upgrade package from the official website, and then click STOP to stop FIST, as shown in Figure 24.
2.Select the new FIST upgrade package, decompress the package, and override the original FIST directory. Then, choose to replace all files as instructed, as shown in Figure 25.
3.Restart FIST.

