Egress Security of Regional Healthcare
Background:
With the vigorous development of information system construction, network security risks faced by the healthcare industry increase gradually. Issues such as the poor implementation of the classified protection practice, high overall security risks, and poor HIS security level are still unsolved and the situation of network security in the healthcare industry is severe.
According to the data shown in the Observation Report for Health and Medical Industry 2019, the cybersecurity of the health and medical industry is generally at a "high risk" level. The industry bears weak security protection capability since there are various network security risks and a large number of potential risks that may be maliciously exploited. The report shows that through the observation of 15,339 medical industry-related units, a total of 1,029 units have malicious programs such as zombies, Trojans, or worms. The service ports of 6,446 units have been exposed to public networks. The websites of 4,546 units have the risk of being tampered with, among which 261 have been tampered with.
Challenges:
Internal threats: In many cases, private devices of hospital staff are often unencrypted due to a lack of security awareness. Their private devices may contain malicious viruses or "worms" that may damage the network to which they are connected, threatening hospital network security.
Social engineering attacks: This kind of attack is made via social engineering techniques and may attack the most restrictive system. Phishing is one of the common social engineering techniques. In a phishing attack, an attacker uses a message sent by email to trick a victim into clicking a link to a malicious website or entering certain password information, or trick them into downloading malicious software and installing it into the system, to unscrupulously steal confidential information of medical institutions and damage network systems.
DDoS attacks: DDoS attack is the most destructive and common type of cyber threat used by hackers to disrupt a network as a protest or anarchist demonstration. This attack can be initiated from hundreds or thousands of computers, causing overloading of traffic in the network or server until they become unavailable.
Solution:
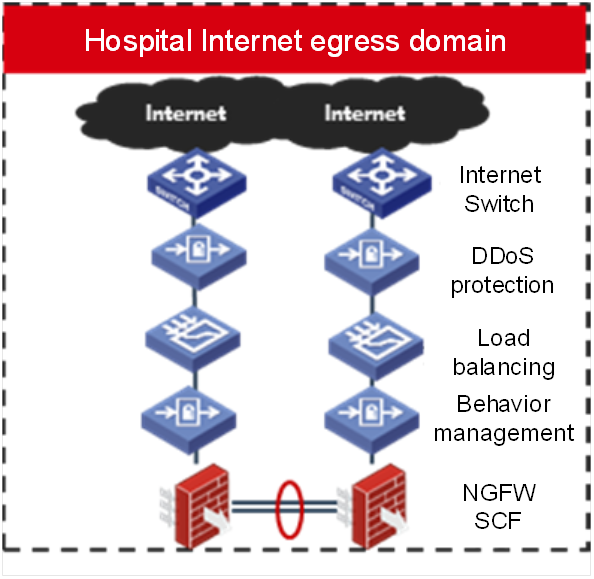
Benefits:
Comprehensive network security protection
* The solution is an excellent intrusion prevention/detection system with comprehensive protection technologies in the industry that integrates functions such as intrusion prevention and detection, virus protection, bandwidth management, and URL filtering Through an in-depth layer 7 analysis and detection, the system compares the historical average baseline to judge the abnormal traffic and give alarms based on the traffic condition, and blocks attacks and malicious behaviors in the network in real time such as hidden viruses, worms, Trojans, spyware, web page tampering. This enables comprehensive protection of network applications, network infrastructure, and network performance.
All-round and timely attack signature database
* The professional security team of H3C closely tracks the security bulletins released by world-known security organizations and manufacturers. By analyzing and verifying all threats collected, the team has established a signature database to protect OSs, application systems, and database vulnerabilities.
* The signature database covers many ranges. It not only includes all vulnerability signatures of mainstream OSs, mainstream network devices, mainstream database systems, and mainstream application software systems, but attack or abuse signatures such as hackers, worms, viruses, Trojans, DoS/DDoS, scanning, spyware, phishing, P2P, IM, and online games.
Comprehensive management and monitoring means
* Supports device management via various means such as Web GUI, CLI, and SSH.
* The role-based authorization mechanism enables function permission control, command line permission control, and menu permission control.
* The unified SSM management platform enables configuration management, performance monitoring, and log audit of the device.


