Campus Network - H3C Endpoints Profiling System (EPS) Solution
Demand background
Society is rapidly moving towards a new era of the Internet of everything (IoE). By 2020, 20 billion devices will be connected to the Internet. Smart networking devices are rapidly becoming an important part of people's work and life. However, this also brings security risks to be reckoned with. At present, network attacks have undergone a great transformation. The attack target is expanding to new types of smart devices, and these smart devices can be easily used as an attack method using by criminals as a jump-off point. Therefore, the network security protection in the IoE era must not only strengthen device security, but also pay attention to the compliance of device access, to ensure the legitimacy of the device when it is connected to the network. This ensures network security from the source.
Besides, the network scale and network device scale are increasing fast. Even if we invest lots of manpower and material resources, it is difficult for us to know the access status of all network devices. Moreover, it is impossible for us to conduct unified "visualized" monitoring and management of all network devices in real time. Therefore, it is imperative to build an advanced, safe, and reliable device access management system.
Current status analysis
Current status of network device access management in various industries:
It is difficult to effectively manage the "compliance" of device access in the whole network. Generally, for enterprises who need to deploy the network-wide device access management system, their network environments have been established with various network devices and complex endpoint devices in the network. The deployment of the device access management system shall consider whether the product supports a variety of network access perception and management technologies and whether it supports the identification of heterogeneous devices, to adapt to various complex network environments. The conventional endpoint access control system mainly adopts solutions such as the RADIUS solution, gateway solution, and interference solution to manage the access compliance of the whole network devices.
The gateway solution is a passively triggered mechanism. After the device is connected to the network, the access gateway cannot actively perceive devices when it is not triggered by upward traffic. The interference solution can only manage the access of unauthorized devices by ARP spoofing/TCP reset, which has unreliable access control methods. The RADIUS solution combines network devices and adopts mainstream technologies such as 802.1x and Portal to realize access control, which is highly accepted by customers. However, although the conventional solutions can well manage the access of PC endpoints, there is no effective solution for the management and control of network access devices. Moreover, MAC address spoofing is also difficult to solve for dumb endpoints.
The "visualized" information of network-wide devices is not comprehensive, and the built-in electronic map of the system has potential security risks and legal risks. The visualization management of most traditional IT systems is displayed on a large screen, including various statistical charts and trend charts that customers care about. For the visualization management of network-wide devices, some requirements such as electronic fencing are difficult to meet due to the lack of geographic location information, such as device positioning. At present, most IT systems in the industry support online maps or the downloading of cracked map data in forums to meet customers' geographic-based "visualization" management needs. However, the calling of online map APIs is subject to certain restrictions. Data is stored in the cloud which has security risks. The offline map data is basically not authorized by the map manufacturer, which has certain legal risks.
EPS solution
Campus network
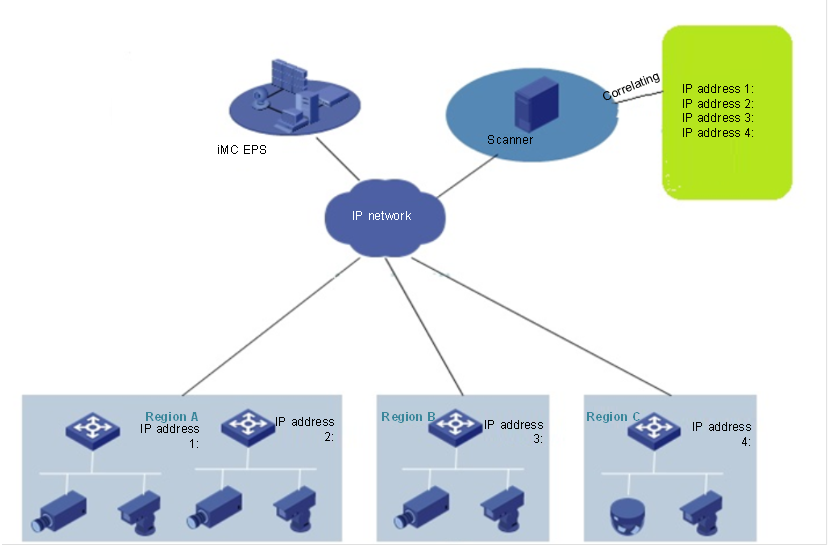
The network-wide device access management can be applied to all lines of business and industries, including enterprises, governments, finance, electricity, and education. Through the active scanning of the network-wide access devices, the analysis results of device legality are given based on the predefined device fingerprint database, which greatly facilitates uniform management of network-wide device access.
The scanner and EPS can cooperate with each other to accomplish the access management of the network-wide devices because there are one or more gateway devices in a region and a large number of access devices such as cameras, PCs, and storage devices in the network.
Scanner design
A scanner needs to be separated from the EPS and independently deployed in a server or virtual machine. To increase scanning speed, multiple scanners can be deployed. Different scanning tasks can be assigned to different scanners through gateways or IP address segments.
Endpoints profiling system (EPS/EPS-A)
Scanner can be designated for a region according to the region division. The scanning result can be shown on the EPS/EPS-A, and the scanned endpoint data can be displayed in various forms.

