Security Announcement-Statement on Multiple vulnerabilities in VMware products
25-02-2021Overview
The Background of security vulnerability
ESXi OpenSLP Remote Code Execution Vulnerability (CVE-2020-3992): OpenSLP used in ESXi has a reuse problem after release. Attackers with access to port 427 may use this problem to trigger remote code execution.
NSX-T man-in-the-middle attack vulnerability (CVE-2020-3993): NSX-T allows the KVM host to download and execute the installation package of the NSX management terminal. Attackers can use this feature to perform man-in-the-middle attacks and damage the transmission node.
TOCTOU out-of-band data read vulnerability (CVE-2020-3981): ESXi, Workstation, and Fusion products have TOCTOU issues, which lead to out-of-band data read vulnerabilities. Attackers with virtual machine administrator access rights can exploit this vulnerability Trigger the memory leak of the vmx process.
TOCTOU out-of-band data writing vulnerability (CVE-2020-3982): ESXi, Workstation and Fusion products have TOCTOU issues, which lead to out-of-band data writing vulnerabilities. Attackers with virtual machine administrator access rights can exploit this vulnerability The memory heap of the hypervisor that crashed or damaged the vmx process of the virtual machine.
vCenter Server Upgrade Function Session Hijacking Vulnerability (CVE-2020-3994): Due to the lack of certificate verification, there is a session hijacking vulnerability in the upgrade function of the Appliance management interface of the vCenter server. Attackers can place malware between the vCenter server and the update library. , When using the upgrade function of the Appliance management interface to download updates, the attacker can hijack the reply.
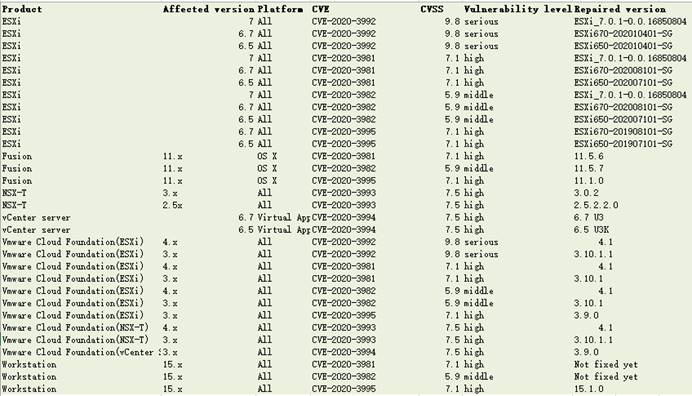
The scope of influence
Solution
The official patch
VMware has provided the latest version to fix the vulnerabilities. It is recommended to upgrade to the latest security version:
https://www.vmware.com/security/advisories/VMSA-2020-0023.html
The temporary solution
If you cannot upgrade, you can temporarily solve the impact of the ESXi OpenSLP remote code execution vulnerability (CVE-2020-3992) through the following steps (only if the SLP service is not used):
1. Stop the SLP service on the EXSi host:
/etc/init.d/slpd stop
2. Turn off the SLP service:
esxcli network firewall ruleset set -r CIMSLP -e 0
3. Make the changes take effect after restarting:
chkconfig slpd off
4. Check whether the changes take effect after restarting (slpd off should be displayed):
chkconfig --list | grep slpd
H3C security emergency response external service
H3C advocates that every effort be made to safeguard the ultimate interests of product users, to abide by principles of responsible disclosure of security incidents, and to handle product security issues in accordance with security issues mechanisms. For information on H3C's security emergency response service and H3C product vulnerabilities, please visit https://www.h3c.com/en/Support/Online_Help/psirt/.
