- Released At: 12-05-2025
- Page Views:
- Downloads:
- Table of Contents
- Related Documents
-
MACsec Technology White Paper
Copyright © 2024 New H3C Technologies Co., Ltd. All rights reserved.
No part of this manual may be reproduced or transmitted in any form or by any means without prior written consent of New H3C Technologies Co., Ltd.
Except for the trademarks of New H3C Technologies Co., Ltd., any trademarks that may be mentioned in this document are the property of their respective owners.
The content in this article is general technical information, and some information may not be applicable to the product you purchased.
Contents
MACsec technology implementation
Format of MACsec encryption message
Operating mechanism of MACsec in client-oriented mode
Operating mechanism of MACsec in device-oriented mode
Cipher suite for MACsec encryption
Typical MACsec application in a campus network
Typical application of MACsec between data centers
Overview
Technical background
At the birth of Ethernet, it was a network with no access control measures, which resulted in poor security. The emergence of the 802.1X protocol resolved controlled access issues within the network and became a significant milestone in Ethernet's development history. However, since the data plane (DP) of 802.1X still uses plaintext transmission, it introduces the following security risks:
· Typically, the links that transcend the Internet or wide area network (WAN) are insecure, and we encrypt such links to enhance transmission security. However, with the rise of Bring Your Own Device (BYOD) solutions and the diversification of access roles within campus networks, the traditional boundaries of campus networks have been broken, thus gradually increasing the security risk of data transmission.
· Furthermore, for a campus network, the network wiring in certain scenarios inevitably pass through uncontrolled public zones. For example, in the case of a business office park where two buildings at a certain distance are interconnected with fiber optic, the area traversed by the fiber optic is a public zone, posing a significant data exposure risk. Currently, low-cost and easy-to-use fiber optic eavesdropping devices have emerged, which can completely restore and eavesdrop on the fiber optic transmission content.
· Even more worrisome is that there are already relevant technologies capable of exploiting the changes in the electromagnetic field during the transmission of data streams in network cables. This allows for the recovery of transmitted content through the principle of electromagnetic induction without the need for corruption of the existing wiring.
For the above security risks, the 802.1X protocol is powerless as it only controls user access, and once accessed, the user messages transmitted in the network are in plaintext, theoretically posing a risk of eavesdropping on any link. Although we can use traditional Layer 3 encryption technologies like IPsec to solve this issue, these techniques cannot achieve line rate forwarding and cannot protect all data after the start-of-frame (SOF). They are not suitable for a campus network. If we use an external dedicated encryption device for data encryption, firstly, it would be too costly and secondly, campus network devices can achieve single-port throughput of up to 10 Gbps, a performance level that encryption devices often cannot match in terms of forwarding capability. Under such pressing circumstances, Media Access Control Security (MACsec) was developed.
MACsec defines a secure communication method for data based on IEEE 802 local area network (LAN), providing users with secure MAC layer transmission and reception services, including data encryption, frame integrity check, and data source authenticity verification. MACsec is commonly used in conjunction with the 802.1X authentication framework, using the key pair generated through the MACsec Key Agreement (MKA) protocol to encrypt and verify the integrity of authenticated user data, preventing ports from processing messages from unauthenticated devices or tampered messages.
Benefits
MACsec employs Layer 2 encryption technology to provide secure data transmission on a hop-by-hop basis for devices. By safeguarding Ethernet data frames, it reduces the risk of data leaks and malicious network attacks. It's suitable for sectors like government and finance, where there's a high requirement for data confidentiality.
The advantages of MACsec include:
· The MACsec on the device is hardware-based, enabling line rate forwarding of messages.
· It can be deployed in combination with 802.1X, which is particularly suited for campus networks.
· After a packet is received from the port that has deployed MACsec, it is decrypted into plaintext. The device can then continue to execute other policy controls, seamlessly compatible with existing policy deployments.
MACsec technology implementation
MACsec application modes
MACsec includes two typical networking modes: client-oriented mode and device-oriented mode.
Client-oriented mode
As shown in Figure 1, the client-oriented mode is used to protect the data frames between the client and the device.
Figure 1 Client-oriented network diagram
Client-oriented MACsec includes the following entities:
· Client: It can be a user terminal that requests access to the local area network (LAN), or a device that supports 802.1X Client function. It is authenticated by the access device in the LAN and executes the MACsec cipher key negotiation and message encryption functions.
· Access device: Controls the access of the client, interacts with the authentication server, conducts 802.1X authentication for the connected client, and executes MACsec encryption key negotiation and message encryption functions.
· Authentication server: It performs authentication, authorization, and accounting for the client, typically a Remote Authentication Dial-In User Service (RADIUS) server. Once the client is authenticated, the authentication server distributes encryption keys to the client and the access device.
|
|
NOTE: When using a device that supports the 802.1X Client function as a client, the port enabling the MKA protocol on the access device must adopt the port-based 802.1X authentication method, and the 802.1X authentication method used must be the EAP trunking method. |
Device-oriented mode
As shown in Figure 2, the device-oriented mode is used to protect data frames between devices.
Figure 2 Device-oriented network diagram
In this mode, the two interconnecting devices use the pre-shared key (PSK) configured through the command line to negotiate the MACsec key and implement the message encryption function. There is no need for 802.1X authentication between the two devices.
MACsec security mechanisms
Data encryption
When a port with the MACsec function enabled and MACsec protection activated transmits a data frame, it requires encryption. When a port with the MACsec function enabled receives a MACsec-encapsulated data frame, it needs to decrypt it. The cryptographic key used for encryption and decryption is negotiated through the MKA protocol.
Integrity check
The transmitting end calculates a checksum for the MACsec encapsulated message using a certain algorithm and appends it to the end of the MACsec encrypted message. When the receiving device gets the MACsec encrypted message, it uses the same algorithm to calculate an integrity check value, then compares this result with the checksum in the message. If the comparison results are the same, it verifies the message as legal; if not, the message might be discarded based on the configured validation mode.
MACsec supports the following validation modes:
· Validation: MACsec only performs validation, but does not discard illegal data frames.
· No validation: MACsec does not perform validation on the received data frames.
· Strict validation: MACsec validates the received data frames and discards illegal data frames.
Replay protection
When data frames encapsulated by MACsec are transmitted over the network, they may become out of sequence. The MACsec replay protection mechanism allows for some degree of disordered frames. If the sequence number of an out-of-order message falls within the user-specified window, the message can be legally received; otherwise, the message will be discarded.
Basic concepts
The MKA protocol is responsible for the establishment and management of MACsec security channels, as well as the negotiation of cryptographic keys used by MACsec. The basic concepts involved in the operation of the MKA protocol are as follows:
· Connectivity Association (CA): A CA is a collection of two or more members who use the same encryption key and key algorithm suite. The members of CA are referred to as the participants of the CA.
· Secure Connectivity Association Key (CAK): A key used by CA participants. In client-oriented mode, the CAK used by both devices is generated during the 802.1X authentication process. In device-oriented mode, the CAK used by both devices is configured directly with a pre-shared key (PSK).
CAK is divided into the following two types:
¡ Pairwise CAK, known as the CAK belonging to a pair of member groups.
¡ Group CAK, also known as a Certificate Authority group with three or more members, possesses a CAK known as the Group CAK.
Currently, MACsec is mainly used in point-to-point (P2P) networking environments, thus primarily utilizing pairwise CAKs.
· Secure Channel (SC): A security transmission channel for unidirectional receive or transmit messages from one point to multipoint.
· Security Association (SA): A collection of security parameters used to establish a secure channel between CA participants, including an algorithm suite for encrypting data, encryption keys for integrity checks, and so on.
· Security Association Key (SAK): An SAK is derived from the CAK using an algorithm and is used to encrypt the data transmitted between secure channels. Each Security Association (SA) has a distinct SAK. The MKA limits the number of messages that can be encrypted by each SAK. When the number of messages encrypted by a specific SAK exceeds the limit, the SAK is refreshed. For example, on a 10Gbps link, the SAK is refreshed at least every 300 seconds.
· Integrity Check Value (ICV): At the transmit (Tx) end of a message, a check value is calculated for the MAC protocol data unit (MPDU) using a specific algorithm and attached to the end of the message. It is then recalculated and compared at the receive (Rx) end to ensure the data integrity of the message.
· MKA Session: It is a secure connection between CA members who hold the same SAK. Under each SC channel, multiple MKA sessions will be created continuously.
· MKA Session Timeout: After establishing each MKA session, both devices confirm the existence of the current session via exchanging MKA protocol messages. Once the device receives an MKA protocol message from the opposite end, the MKA session timeout timer is initiated. If the device does not receive another MKA protocol message from the opposite end within the timeout period set by the timer (default is 6 seconds), the session is deemed insecure and needs to be cleared immediately.
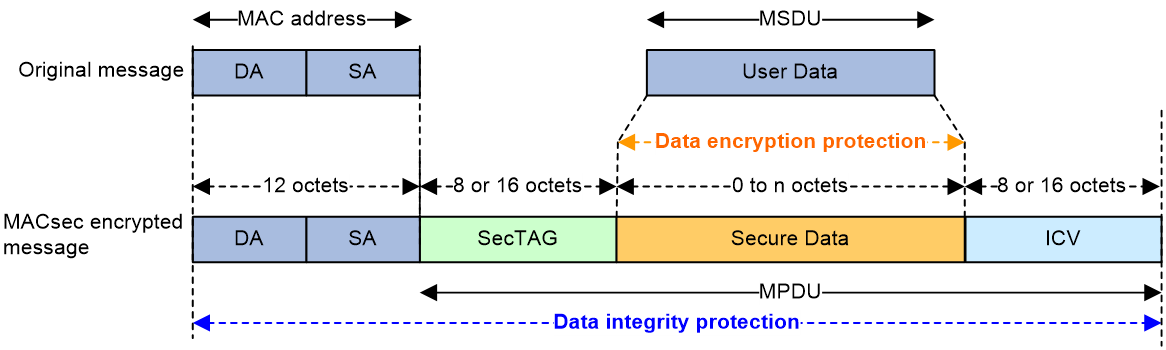
Format of MACsec encryption message
Upon completion of SAK key negotiation and installation among CA members, the negotiated key will be used for the forwarding of data packets.
· At the sender of a data packet, the raw data part, MAC Service Data Unit (MSDU), is encrypted using SAK and the encryption algorithm to form encrypted text (Secure Data). Using SAK and the verification algorithm, the source/destination MAC, SecTAG, and the encrypted part are calculated to output an ICV, which is placed at the end of the data packet. This is then assembled into a complete MACsec encrypted data packet transmitted to the peer.
· At the receiver of the data packet, the encrypted text is decrypted into plaintext using the SAK and decryption algorithm. Simultaneously, the verification algorithm calculates the ICV and compares it with the ICV carried by the data packet. If they match, it indicates that the data packet has not been modified.
Figure 3 MACsec Message Encryption Diagram
The key fields in a MACsec packet have the following meanings:
· DA/SA: The destination/source MAC (SMAC) addresses in the packet, each consisting of 6 bytes.
· SecTAG: A security tag, with a length of either 8 or 16 bytes. Further explanation can be found below.
· Secure Data: The payload after MACsec encryption. According to the protocol, the encryption starting point can be offset by 0, 30, or 50 bytes after the ET field.
· ICV: Integrity Check Value, 8-16 bytes. If a message is tampered with, the ICV value will change, thus protecting the message from malicious modification.
Figure 4 Schematic Diagram of the SecTAG Field
· EtherType (Ethertype): 2 bytes, indicating the Ethernet type of the MACsec protocol, with a value of 0x88E5.
· The TCI (TAG Control Information): 6 bit, provides state information such as the MACsec version number, whether the message has been encrypted, whether it has undergone integrity calculations, and whether it carries the ICV field at the end.
· Association Number (AN): 2-bit identifier that indicates the Security Association (SA) ID within the secure channel transmitting the package. A secure channel can include up to 4 SAs.
· SL (Short Length): 1 byte, the value is the length of SecureData if it is less than 48 bytes; otherwise, it is zero.
· Packet Number (PN): This 4-byte field signifies the packet's identification number. The transmitting end increments this field by 1 every time it transmits a packet, to prevent replay attacks.
· SCI (Secure Channel Identifier): An 8-byte identifier for the security channel, composed of a 6-byte MAC address and a 2-byte port number.
Operating mechanism of MACsec
Operating mechanism of MACsec in client-oriented mode
As illustrated in Figure 5, before establishing a secure session between the client and the access device, the client first needs to perform 802.1X authentication on the port of the access device. After authentication, the client will begin to negotiate with the access device for session establishment and maintenance. The interaction process of MACsec protocol is mainly divided into four stages: identity authentication, session negotiation, secure communication, and session termination.
Figure 5 MACsec operating mechanism in client-oriented mode
1. Identity Verification
The access device performs 802.1X authentication on the client. After the client passes the authentication, the RADIUS server will distribute the generated CAK to both the client and the access device.
2. Session negotiation
The client and access device have an available CAK and use EAPOL-MKA messages to initiate a session negotiation. During the session negotiation, the client and access device announce their capabilities and required parameters (such as privilege level, whether an encrypted session is desired) to each other using the MKA protocol. When negotiating the session, the access device is automatically elected as the key server. The key server derives a SAK from the CAK for encrypting data packets and distributes it to the client.
3. Secure Communication
After the session negotiation is complete, the client and access device have an available SAK. They use the SAK to encrypt the data packet, and begin encrypted communication.
4. Session termination
When the access device receives an offline request message from the 802.1X client, it immediately clears the corresponding security session of that user to prevent an unauthenticated client from using the security session established by a previously authenticated client to access the network. If the MKA session timeout timer (default time is 6 seconds) expires and this end has not received the MKA protocol document from the opposite end, the corresponding security session of that user is cleared.
Operating mechanism of MACsec in device-oriented mode
As shown in Figure 6, devices use the configured pre-shared key (PSK) to negotiate a session and begin secure communication once negotiation is completed. The interaction process of the MACsec protocol mainly consists of three stages: session negotiation, secure communication, and session termination.
Figure 6 MACsec operating mechanism in device-oriented mode
1. Session negotiation.
The configured pre-shared key (PSK) is used as the CAK between devices, negotiating sessions through EAPOL-MKA protocol messages. The port with the higher privilege level between devices is elected as the Key Server and is responsible for generating and distributing SAK. Devices announce their capabilities and various parameters needed to establish a session (such as privilege level, whether encryption session is expected, etc.) to each other through the MKA protocol.
2. Secure communication
Once the session negotiation is completed, each device has an available SAK, and it begins to encrypt communication using the SAK to encrypt data packets.
3. Session termination
Upon receiving the offline request message from the other party, the device instantly clears the security session corresponding to this user. If the MKA session timeout timer (default to 6 seconds, but configurable) expires and this end has yet not received the MKA protocol message from the other end, the security session corresponding to this user is cleared.
Cipher suite for MACsec encryption
The cipher suite used by MACsec is a group of algorithms for encrypting, checksumming, and decrypting protected data frames. The currently supported cipher suites are GCM-AES-128 and GCM-AES-256. GCM-AES (Galois Counter Mode-Advanced Encryption Standard) is a widely recognized secure and fast symmetric encryption algorithm.
The cipher suite GCM-AES-128 and GCM-AES-256 mainly have the following differences:
· The length of the cryptographic key varies: GCM-AES-128 has a key length of 128 bits, while GCM-AES-256 has a key length of 256 bits.
· The number of encryption rounds differs: GCM-AES-128 has 10 encryption rounds, while GCM-AES-256 has 14.
The longer the GCM-AES cryptographic key and the more encryption rounds, the higher the security. Therefore, GCM-AES-256 has a higher security strength than GCM-AES-128.
Restrictions and guidelines
· Not all types of interfaces have MACsec capability. The MACsec capability of an interface is related to the actual situation of the product. Please refer to the actual situation of the device.
· On an interface without MACsec capability, starting the MKA protocol is not supported.
· In devices that support MACsec cipher suite function, only some daughtercards can be configured with the MACsec cipher suite. Please refer to the actual situation of the device. The MACsec cipher suite should be configured on devices only in device-oriented mode, and the 802.1X function cannot be enabled on the port where this function is configured.
Typical Network Applications
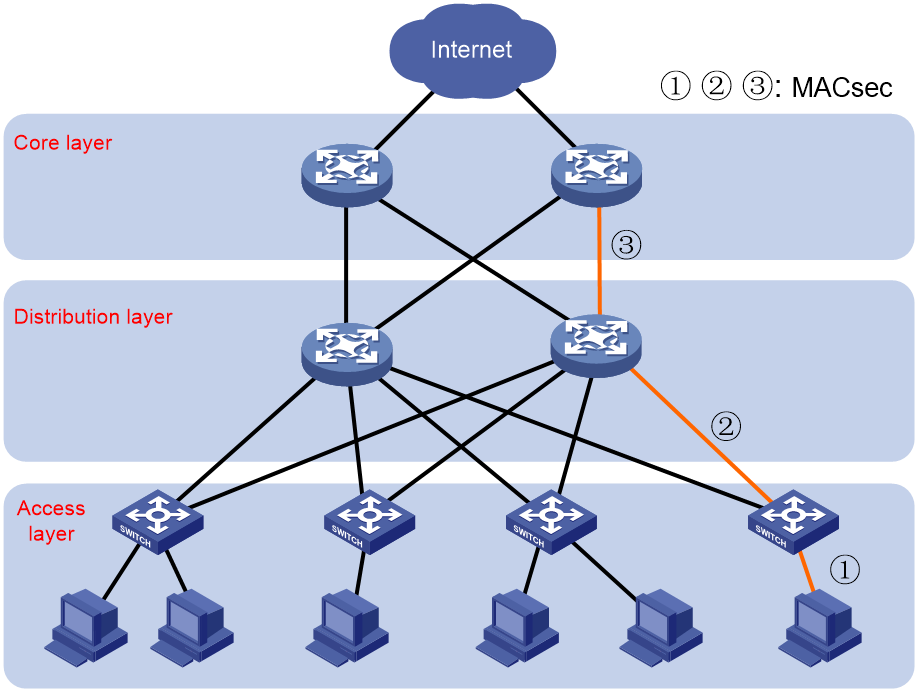
Typical MACsec application in a campus network
As shown in Figure 7, in a campus network with a large number of network access devices, dispersed distribution, and significant security management risks, end-to-end security protection is required for the network. These devices can adopt end-to-end MACsec security protection and use authentication methods such as 802.1X for secure access control for users.
Figure 7 MACsec in a campus network
Typical application of MACsec between data centers
As illustrated in Figure 8, fiber optic interconnection is used between two long reach (LR) data center networks, and the place where the fiber optic passes is a public zone. There's a significant risk of data exposure within this zone. To prevent data from being stolen or modified during the transmission, MACsec can be used to secure the data transmission on the output port of the two network edge devices.
Figure 8 Application of MACsec between data centers
Related documentation
· IEEE 802.1X-2010: Port-Based Network Access Control
· IEEE 802.1AE-2006: Media Access Control (MAC) Security