- Released At: 18-12-2024
- Page Views:
- Downloads:
- Table of Contents
- Related Documents
-
IPoE Transparent Web Authentication Technology White Paper
Copyright © 2024 New H3C Technologies Co., Ltd. All rights reserved.
No part of this manual may be reproduced or transmitted in any form or by any means without prior written consent of New H3C Technologies Co., Ltd.
Except for the trademarks of New H3C Technologies Co., Ltd., any trademarks that may be mentioned in this document are the property of their respective owners.
The content in this article is general technical information, some of which may not apply to the product you purchased.
Contents
Implementation of Layer 2/3 transparent authentication technology
Transparent MAC-trigger authentication technology implementation
User online operation mechanism
Authentication process for user's first access
User authentication process for 2nd to nth access times
Transparent MAC authentication
Transparent MAC authentication types
Common transparent MAC authentication
Re-DHCP transparent MAC authentication
Mechanism of user going offline
Overview
Technical background
In a typical IPoE Web authentication scenario, users need to manually enter their username and password information for identity authentication every time they come online, which is quite inconvenient. This is particularly relevant now that the number of smart endpoints using Wi-Fi network is increasing, and such endpoints, restricted by screen and browser resources, find it challenging to enter their username and password on the authentication page, which significantly reduces the user's online experience. To address this issue, an IPoE transparent Web authentication solution has been proposed, which significantly simplifies the user's network access procedure and enhances the user's experience.
IPoE Web transparent authentication is a kind of quick authentication process based on MAC address, allowing users to automatically complete the authentication without manually entering the authentication information each time they access the network. Users only need to enter their username and password for the first online access. Subsequent online access doesn't require the input of user information and the IPoE Web authentication process is automatically completed.
Benefits
The IPoE transparent Web authentication delivers the following benefits:
· Reduces the complexity of users' online operations, thereby enhancing the efficiency of accessing network resources and realizing a minimalist user experience.
· Compatible with a variety of endpoint types, greatly meeting the endpoint access requirement.
· Supports both wired and wireless connections, allowing users to flexibly select the access method based as needed.
· Supports Layer 2/3 transparent authentication, and compatible with various networking types.
Concepts
· Access device: A device that provides access services.
· AAA server: Interacts with the access device to complete user authentication, authorization, and accounting.
· Portal server: It is responsible for providing the authentication interface to the clients, interacting with the access device to verify the client's authentication information, and completing the client's identity authentication.
· MAC binding server: A server used to record the binding relationship between client authentication information and client MAC addresses. In the scenario of MAC transparent authentication, the AAA server also serves as the MAC binding server.
· MAC binding entry: An entry on the server that stores the client's MAC address and authentication information.
· Re-DHCP: The user's online process involves two instances of IP address allocation.
Fundamentals
The principle of IPoE transparent Web authentication is as follows: it is completed in cooperation with the common IPoE Web authentication and MAC binding server.
1. When users first access the Internet, they must manually enter their usernames/passwords on the authentication page pushed by the access device to complete IPoE Web authentication.
2. After a user passes authentication, the binding server automatically sets up the binding of the user MAC address and the authentication information.
3. When the user accesses the network subsequently, the binding server directly completes authentication for the user according to the recorded binding. In this case, the device does not push an authentication page to the user and the user does not sense the authentication process. The user can quickly access the network without any operations.
Based on whether a Layer 3 device exists between the user and the access device, IPoE transparent Web authentication includes two types of authentication methods: Layer 2 and Layer 3 transparent .
Based on whether the server with MAC binding supports the MAC trigger protocol, IPoE transparent Web authentication includes transparent MAC-trigger authentication and transparent MAC authentication. These two types of IPoE transparent Web authentication technologies mainly have the following differences:
· Transparent MAC-trigger authentication requires additional deployment of a MAC-trigger server, while transparent MAC authentication does not require extra deployment of a MAC-trigger server.
· MAC-trigger transparent authentication requires interaction with Portal protocol messages and RADIUS protocol messages, while MAC transparent authentication requires interaction with RADIUS protocol messages.
Implementation of Layer 2/3 transparent authentication technology
In a transparent authentication network configuration, the access device must obtain the user's MAC address and submit this MAC address information to the authentication server. Only then can the authentication server determine whether the user meets the condition for transparent authentication based on that MAC address information.
· For Layer 2 transparent authentication, the access device can directly obtain the user's MAC address from the user message.
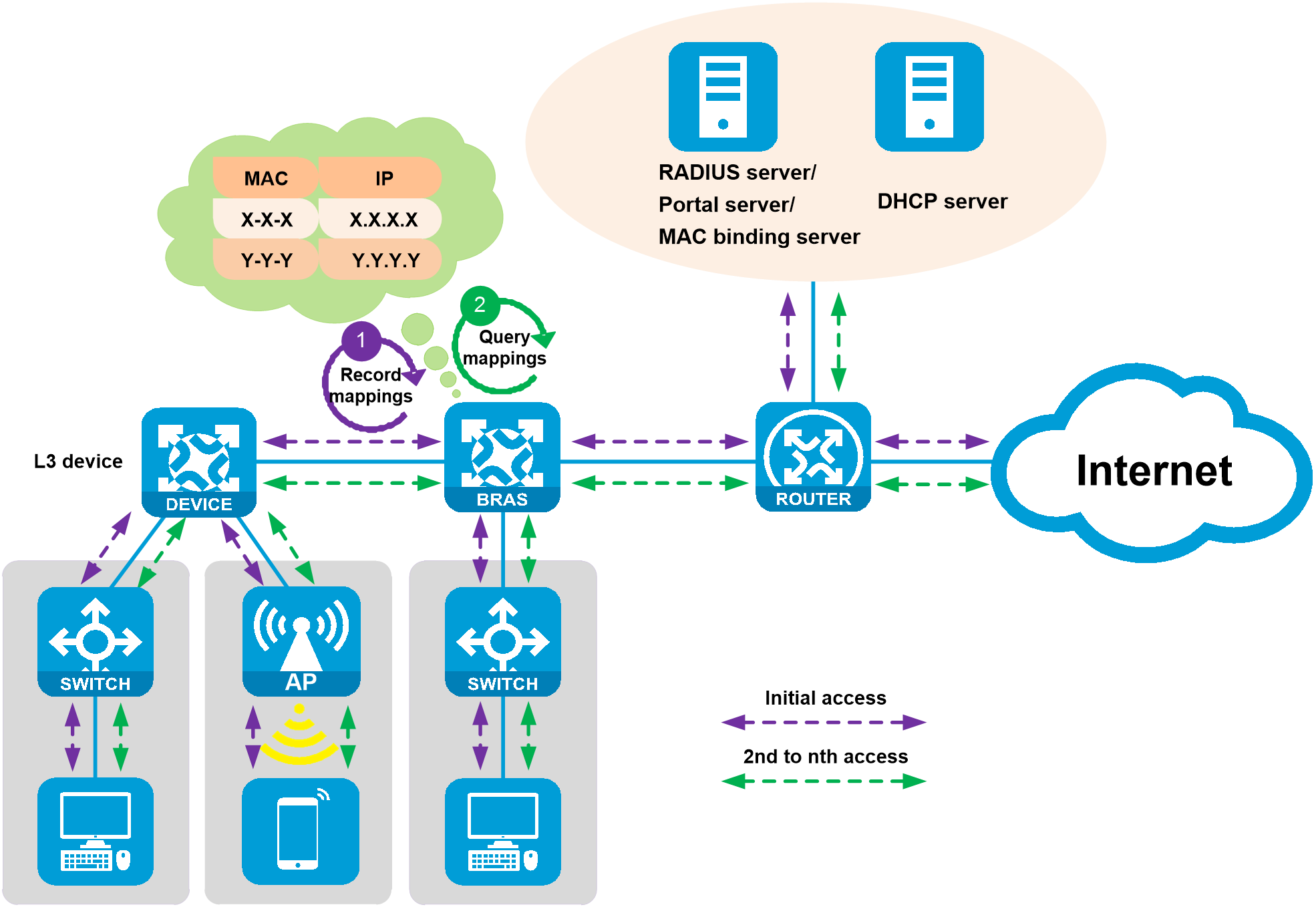
· For Layer 3 transparent authentication, since a Layer 3 device exists between the user and the access device, the access device cannot directly obtain the user's MAC address from the user message. As shown in Figure 1 at this time, the access device needs to obtain the user's MAC address based on the following principles:
¡ When a user connects for the first time, the access device retrieves the user's MAC address and IP address from the DHCP message that allocates the IP address for the user. It then records the mapping between the user's MAC address and IP address.
¡ When the user goes online for the second time and subsequently, the access device uses the recorded mappings of MAC addresses and IP addresses. It uses the IP address to look up the corresponding MAC address of the user's IP address.
Figure 1 Layer 2/3 transparent authentication
Transparent MAC-trigger authentication technology implementation
User online operation mechanism
Authentication process for user's first access
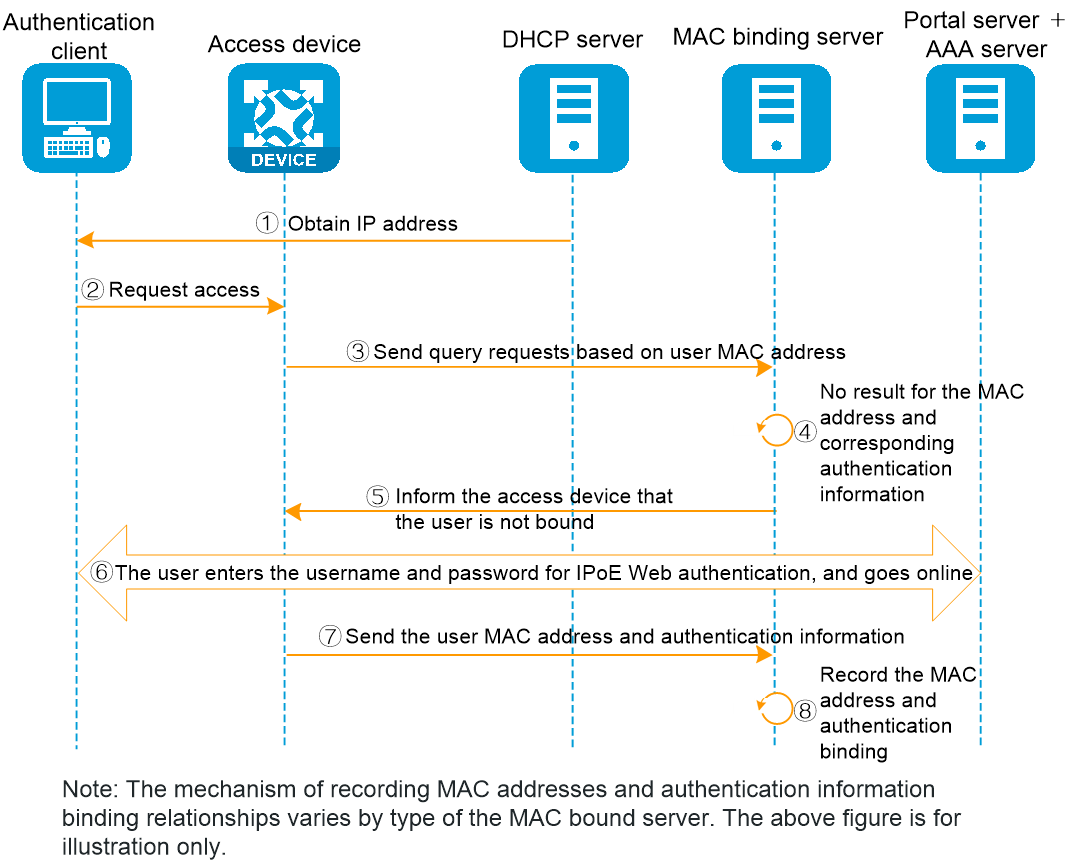
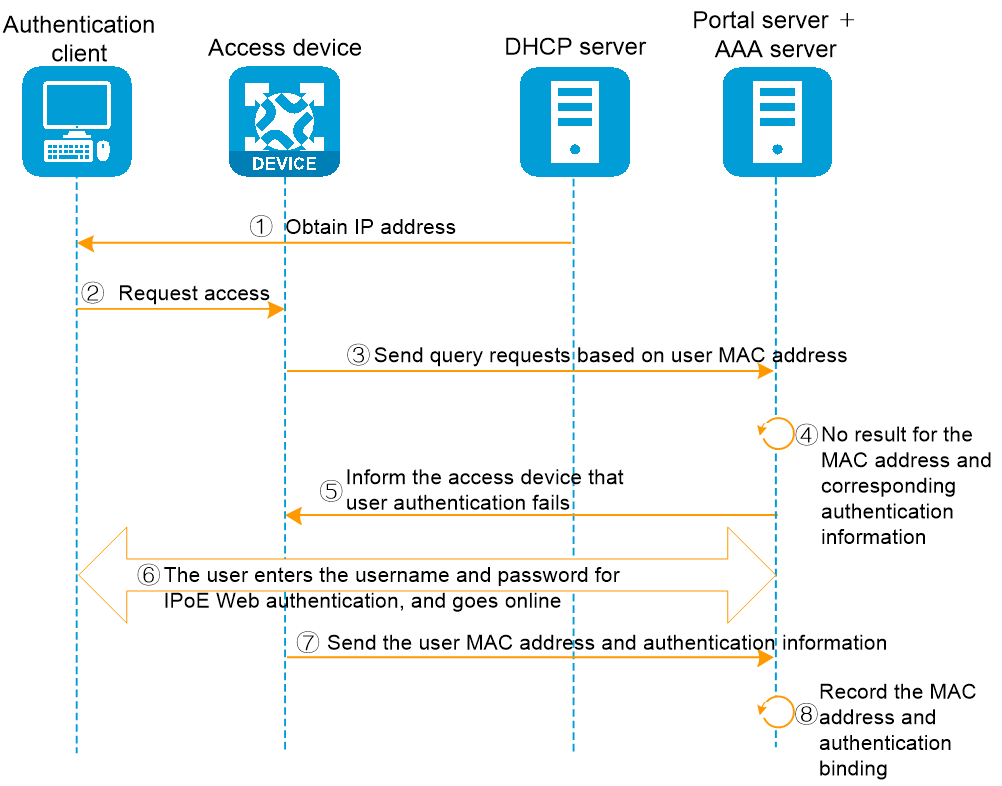
In the transparent MAC-trigger authentication method, the user's initial authentication process for accessing the network is shown as in Figure 2. The detailed authentication process is as follows:
1. The authentication client connects to the network and retrieves the IP address information through the DHCP server.
2. The user transmits a request to access the Internet.
3. The access device will transmit a binding query request to the MAC bound server and wait for the return of the query result.
4. The server did not find MAC address binding and authentication information binding in the MAC binding query.
5. The MAC binding server returns the query result to the access device: Not bound.
6. The access device redirects subsequent HTTP/HTTPS requests to the portal authentication page according to the standard IPoE Web process, where the user enters the username/password to complete the authentication.
7. The access device transmits the user's MAC address and authentication information to the MAC binding server.
8. The server completes the binding of the user's MAC address information and authentication information.
Figure 2 Flow chart of user's initial access authentication
User authentication process for 2nd to nth access times
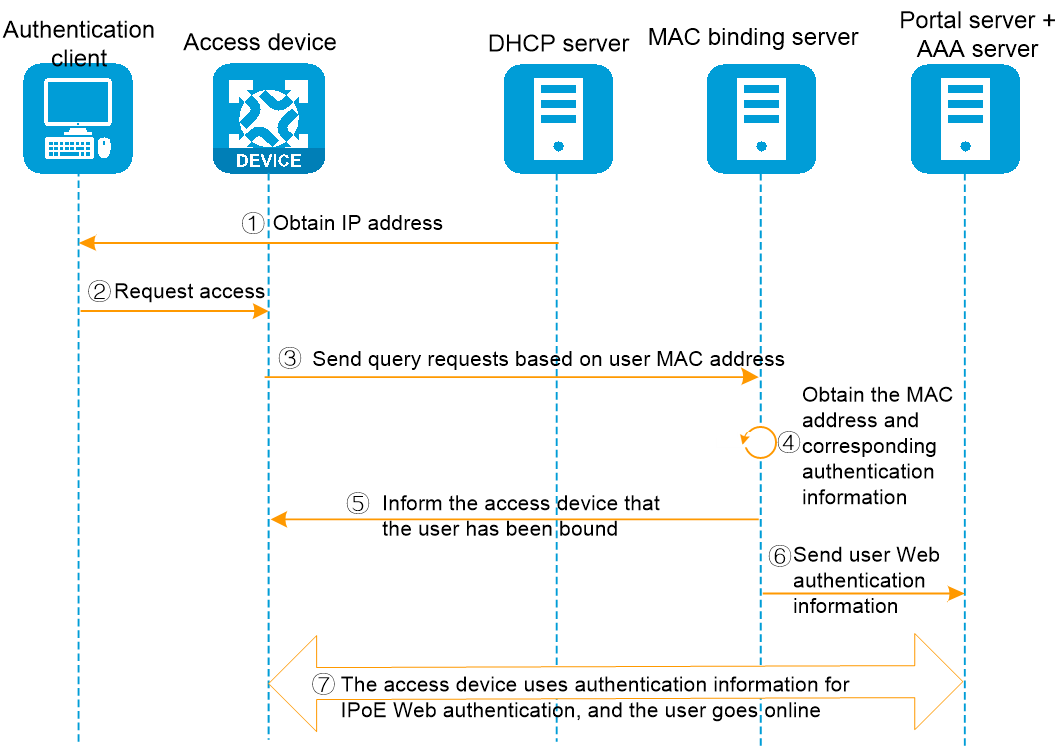
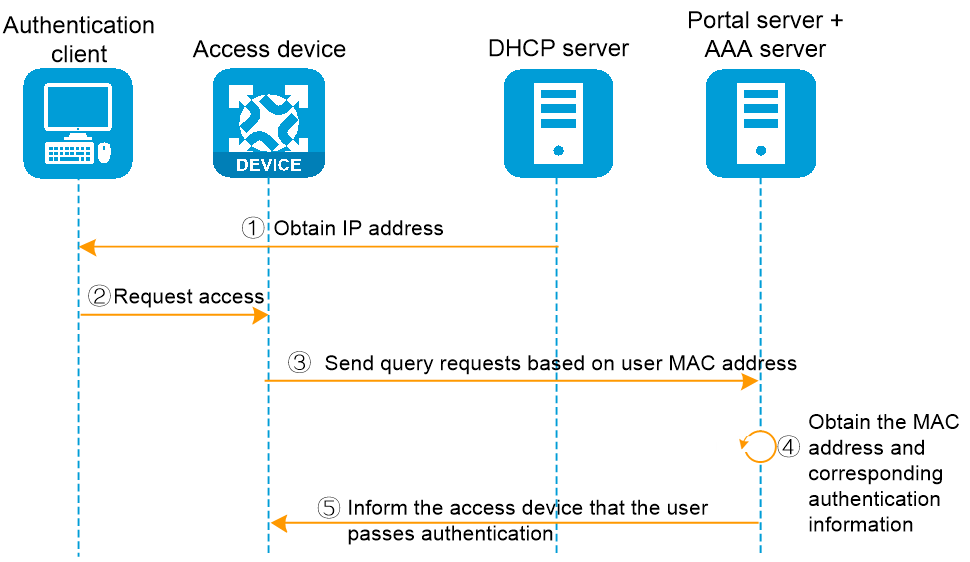
In the MAC-trigger transparent authentication method, the user's 2nd to nth access network authentication process is shown as in Figure 3. The specific authentication process is as follows:
1. The authentication client connects to the network and obtains the IP address information through the DHCP server.
2. The user transmits a request for Internet access.
3. The access device will transmit a binding query request to the MAC binding server and wait for the return of the query result.
4. The server queries and finds the Web authentication information bound to the MAC address.
5. The MAC binding server returns the query result to the access device: already bound.
6. The server with MAC binding forwards the user's Web authentication information to the portal server.
7. The portal server transmits user authentication information to the access device, and the access device utilizes this information to complete the subsequent authentication process.
Figure 3 User access authentication flowchart for the 2nd to nth time
User offline mechanism
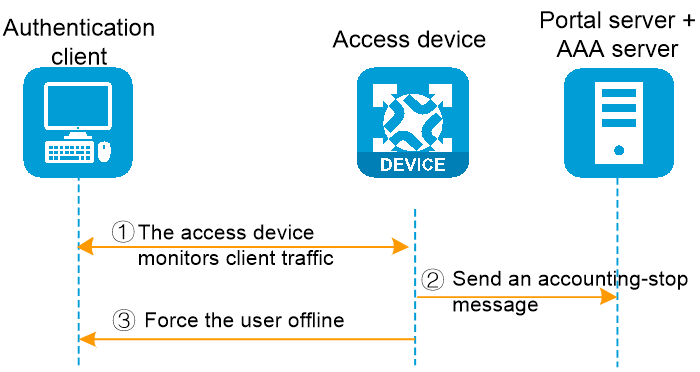
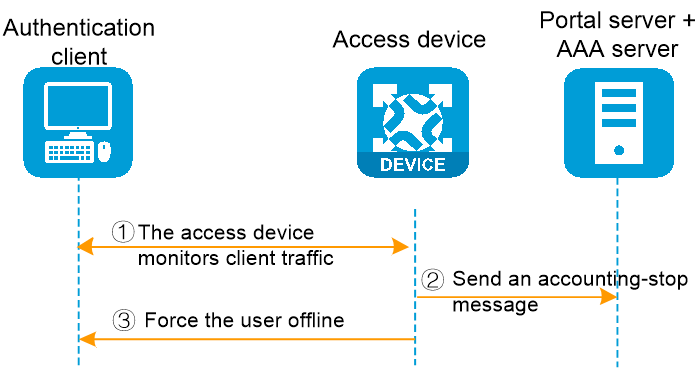
Users can disconnect by an idle cut mechanism, where if user traffic detected by the access device falls below a set threshold for a configurable period (idle cut time), the device will forcibly log the user out. The specific process is as follows:
1. The access device monitors the data flow of the authentication client.
2. During the user's idle cut time, if the user's traffic is below the set detection threshold, the access device transmits a charging end message to the AAA server.
3. The access device forcibly takes the user offline.
Figure 4 User offline process
Transparent MAC authentication
Transparent MAC authentication types
Based on the different IP address allocation methods, two types of transparent MAC authentication are included:
· Common transparent MAC authentication: The user's entire authentication online process carries out only one IP address allocation, and it triggers the transparent MAC authentication process during the Web authentication. After the completion of the transparent MAC authentication, the user goes online.
· Re-DHCP transparent MAC authentication: The user's entire authentication process involves two IP address allocations. The MAC transparent process is triggered during the preauthentication. Once the transparent MAC authentication is completed, the user comes online.
User online mechanism
Common transparent MAC authentication
Authentication process for a user's first access
In the transparent MAC authentication method, the user's initial network access authentication process is shown in Figure 5. The specific authentication process is as follows:
1. The authentication client connects to the network and obtains the IP address information through the DHCP server.
2. The user sends a request to access the Internet.
3. The access device transmits an access-request to the AAA server and waits for the authentication result to return.
4. The AAA server does not find any Web authentication information bound to the MAC address.
5. The AAA server returns authentication result to the access device: Authentication failed.
6. The access device redirects subsequent HTTP/HTTPS requests to the portal authentication page according to the normal IPoE Web process. The user will enter the username/password information to complete the subsequent authentication process.
7. The access device transmits the user's MAC address and authentication information to the AAA server.
8. The AAA server completes the binding of the user's MAC address information and authentication information.
Figure 5 Flow chart of the user's first access authentication process
Authentication process for the user's 2nd to nth access attempts
In the transparent MAC authentication method, the authentication process for user's 2nd to nth times of accessing the network is shown in Figure 6. The specific authentication process is as follows:
1. The authentication client connects to the network and obtains IP address information through the DHCP server.
2. The user sends a request to access the Internet.
3. The access device transmits an access-request to the AAA server and waits for the authentication result to return.
4. The AAA server queries the Web authentication information bound to the MAC address.
5. The AAA server's query result indicates that it is already bound. The access device is notified that the user authentication has passed.
Figure 6 Flow chart of the user's 2nd to nth access authentication process
Re-DHCP transparent MAC authentication
|
|
NOTE: · The primary scenario for the re-DHCP transparent MAC authentication method is when users first come online. Initially, a temporary IP address is allocated. Once the user is successfully authenticated via Web, a public network IP address is subsequently assigned. This approach helps conserve the allocation of public network IP addresses. · Currently, only DHCP users (including IPv4 and IPv6) support re-DHCP transparent MAC authentication. |
Process of user's first authentication
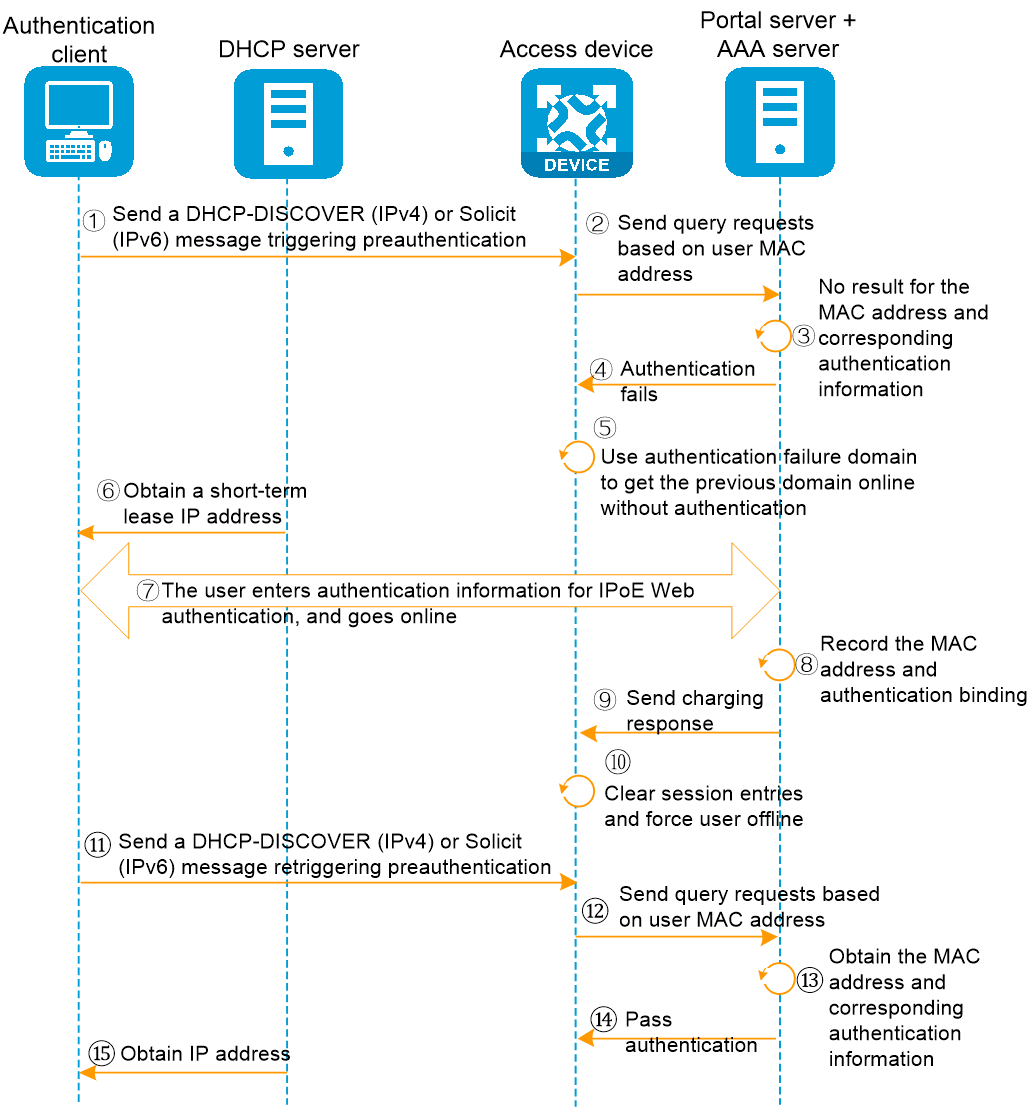
In the re-DHCP MAC authentication mode, the user's initial network access authentication process is as shown in Figure 7. The detailed authentication process is as follows:
1. When the authentication client transmits a DHCP-DISCOVER (IPv4) or Solicit (IPv6) message, it triggers preauthentication.
2. The access device initiates authentication to the AAA server based on the client's MAC address.
3. The AAA server does not find the MAC address binding and authentication information binding.
4. The AAA server returns the authentication result to the access device: Authentication fails.
5. Upon receiving the authentication failure information, the access device uses the configured authentication failure domain to retrigger the previous domain authentication, with the authentication failure domain configured for no authentication.
6. After coming online in the preauthentication domain, the user obtains a short-term lease IP address.
7. The access device redirects subsequent HTTP/HTTPS requests to the portal authentication page according to the normal IPoE Web process. The user enters username/password information to complete the following authentication process.
8. The AAA server completes the binding of the user's MAC address information and authentication information.
9. The AAA server transmits a charging response message to the access device.
10. After the device receives the accounting response message from the AAA server, it clears the DHCP user's session information and forces the user offline. If the user needs to come online, they need to re-trigger preauthentication. Afterwards, if a DHCP renewal message is received from the user, a direct NAK response is sent to enable the user to quickly re-initiate the transparent MAC preauthentication process for coming online.
11. When the authentication client sends the DHCP-DISCOVER (IPv4) or Solicit (IPv6) message again, it triggers preauthentication.
12. The access device initiates authentication to the AAA server based on the user's MAC address.
13. The AAA server queries the Web authentication information bound to the MAC address.
14. The AAA server returns the authentication result to the access device: authentication passed.
15. The user obtains the IP address and successfully comes online.
Figure 7 First user authentication flowchart
Authentication process for the user's 2nd to nth access
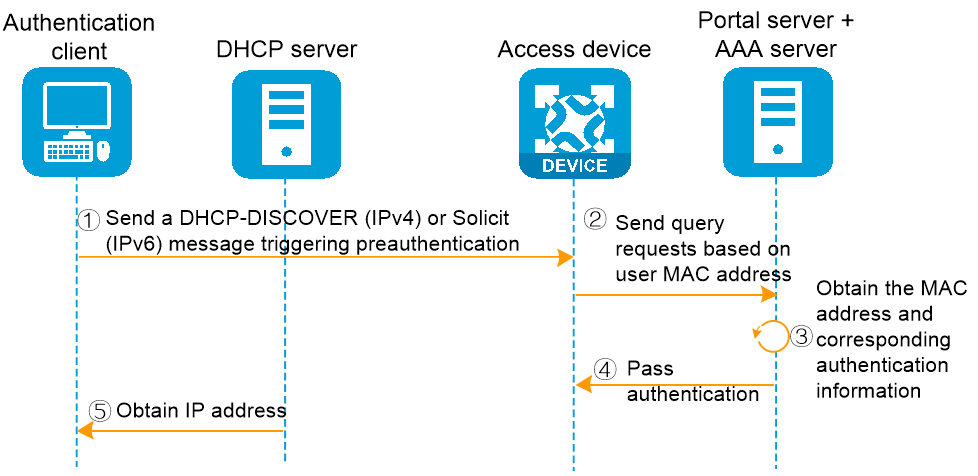
In the method of re-DHCP transparent MAC authentication, the authentication process of 2nd to nth user access to the network is as shown in Figure 8. The specific authentication process is as follows:
1. When the authentication client transmits a DHCP-DISCOVER (IPv4) or Solicit (IPv6) message, it triggers preauthentication.
2. The access device initiates authentication to the AAA server based on the user's MAC address.
3. The AAA server queries the Web authentication information bound to the MAC address.
4. The AAA server returns authentication results to the access device: authentication successful.
5. The user has successfully obtained the IP address and gone online.
Figure 8 Flow chart of user authentication process for the 2nd to nth times
Mechanism of user going offline
Users can complete the offline procedure through the idle cut mechanism. In this mechanism, the access device forces the user to go offline after detecting that the user's traffic is below a specified threshold within a period of time (configurable idle cut time). The specific procedure is as follows:
1. The access device monitors the data flow of the authentication client.
2. During the user's idle cut time, if the user traffic is below the set detection threshold, the access device transmits an accounting-stop message to the AAA server.
3. The access device forces the user offline.
Figure 9 User offline process
Typical network applications
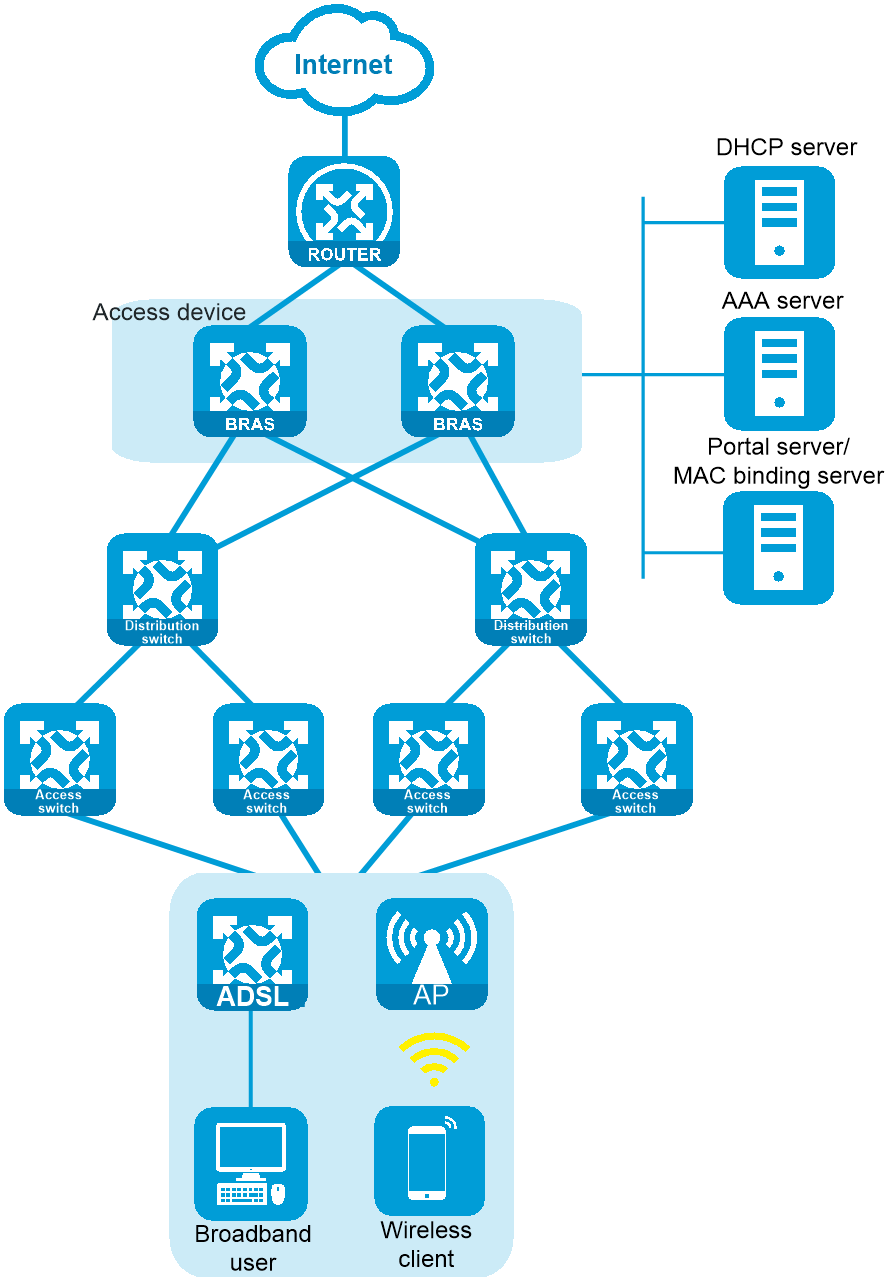
As shown in Figure 10, wired users and wireless users connect to the access device through a Layer 2 network by using IPoE. The specific requirements are as follows:
· When first accessing the Internet through IPoE Web, the user enters the username and password to access network resources.
· After the user disconnects and comes online again, the user can directly access the Internet without having to enter the username and password.
Figure 10 Typical network diagram for transparent authentication