| Title | Size | Downloads |
|---|---|---|
| 51-Antivirus Software Check for Access Users-Antivirus Software Check for Access Users.rar | 3.81 MB |
- Table of Contents
- Related Documents
-
1 Antivirus Software Check for Access Users
To view this video, click the download link.
Software Version Used
This video was recorded based on the following versions:
l iMC: iMC PLAT 3.20-E2501, iMC UAM 3.60-E6101, iMC EAD 3.60-E6101
l iNode: iNode 3.60-E6101
Web interfaces of different versions may vary.
Application Scenario
With the popularity of the Internet, more and more computer viruses emerge, threatening the security of computers and networks. To confront such threats, enterprises usually require deployment of anti-virus software on each computer in their networks. However, it proves to be a head-aching task to make sure that every computer is installed with and running the required anti-virus software and keeps upgrading the anti-virus engine and virus definitions in time.
The EAD solution supports managing anti-virus software. To access a network with this solution deployed, a user must pass EAD authentication after passing identity authentication. If the anti-virus engine or virus definitions of the computer are too old, the user will fail EAD authentication and can only access the isolated area, where servers providing the up-to-date anti-virus engine and virus definitions reside. Only after upgrading the anti-virus engine and virus definitions, can the user pass EAD authentication and access the network normally. This not only prevents individual computers from being infected, but also prevents them from becoming infection sources, thus protecting the security of the whole network.
Recommended Configuration Flow
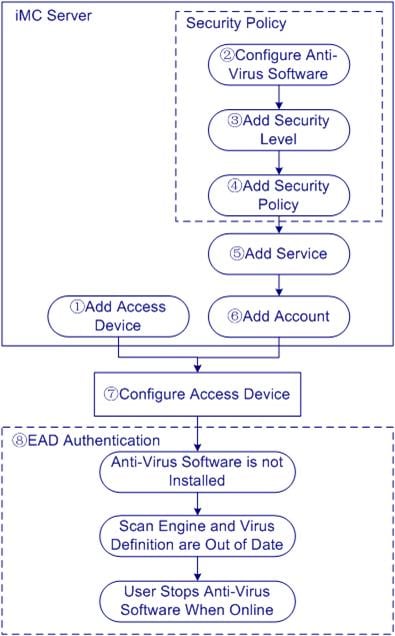
Step1 Add Access Device
Add an access device that supports AAA to the iMC system, so that the access device acts as the AAA client to cooperate with the iMC system.
Step2 Configure Anti-Virus Software
iMC supports various main-stream anti-virus software. This step shows how to specify the lowest requirements of anti-virus software as needed.
Step3 Add Security Level
In a security level, you can define the actions to be taken in response to anti-virus software violations and abnormities such as too old virus definitions and abnormal anti-virus client. Four types of actions are available: kick out, isolate, inform, and monitor, where isolate is the most commonly used one.
Step4 Add Security Policy
In a security policy, you can define the violations and abnormities to be processed and specify the actions to be taken in response by referencing the security level defined at step 3. You can also enable the real-time monitoring function so that the system monitors online users and processes violations and abnormities in real time.
Step5 Add Service
A service is a set of policies for user authentication and authorization. The service added in this step includes the security policy defined at step 4.
Step6 Add Account
Each user accessing the network must have an account configured in the iMC. An account includes information such as the account name and password. This step illustrates how to add an account and apply for the service configured at step 5 for the account.
Step7 Configure Access Device
An access device is used to control access of users. It may isolate users failing EAD authentication within the isolated area, where servers such as the patch server reside. This step illustrates how to configure a RADIUS scheme, a domain, the 802.1X feature, and security and isolation ACLs.
Step8 EAD Authentication(Verify Configuration)
1) On a PC with no anti-virus software installed, create an iNode authentication connection and initiate EAD authentication by using the account created at step 6. You should be isolated.
2) After installing an old version of anti-virus software, initiate EAD authentication again. You should still be isolated. After upgrading the virus definitions, you should be able to pass EAD authentication.
3) Stop the anti-virus software after passing EAD authentication. iMC should detect the abnormality and isolate you. Start the anti-virus software and initiate EAD authentication again. You should pass the authentication.

