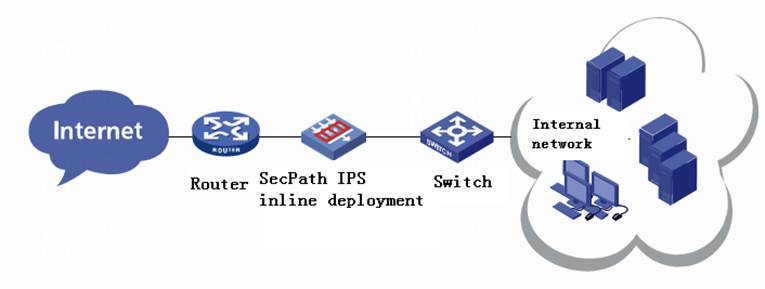
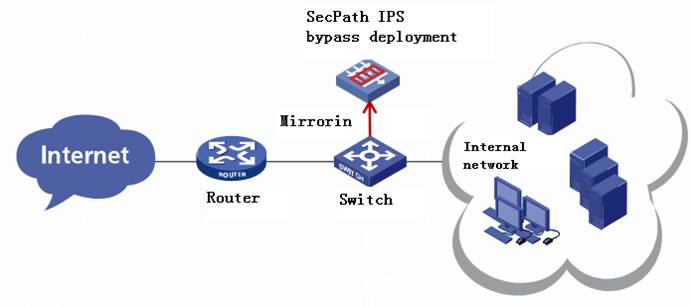
The SecPath T1000-AI delivers high system performance with advanced architecture and components:
 64-bit multi-core high-performance processor and high-speed cache—Provides high-performance security processing capability.
64-bit multi-core high-performance processor and high-speed cache—Provides high-performance security processing capability.
 CPU+switch structure—Uses the CPU to process security services and the switch to implement service port extension.
CPU+switch structure—Uses the CPU to process security services and the switch to implement service port extension.
 Hardware scalability—The interface module slots allow flexible interface expansion and the two drive slots can accommodate growing storage needs.
Hardware scalability—The interface module slots allow flexible interface expansion and the two drive slots can accommodate growing storage needs.
Industry-leading virtualization solution
N:1, 1:N, and N:1:M virtualization solutions allow resource pooling for cloud computing.
Powerful security protection features
 Intrusion prevention and detection—Integrates IPS, antivirus, bandwidth management, and URL filtering features. By inspecting and analyzing Layer 7 application information of the traffic, the system can identify and block attacks and malicious behaviors in the network in real-time to secure the network applications, infrastructure, and performance.
Intrusion prevention and detection—Integrates IPS, antivirus, bandwidth management, and URL filtering features. By inspecting and analyzing Layer 7 application information of the traffic, the system can identify and block attacks and malicious behaviors in the network in real-time to secure the network applications, infrastructure, and performance.
 Attack prevention technologies—Supported in both IPv4 and IPv6 network. In addition to the stateful firewall technology. The system detects and prevents various attacks, including:
Attack prevention technologies—Supported in both IPv4 and IPv6 network. In addition to the stateful firewall technology. The system detects and prevents various attacks, including:
● Single packet attacks, such as Land, Smurf, Fraggle, WinNuke, ping of death, Teardrop, and invalid TCP flag.
● IP spoofing attacks.
● IP scanning attacks and port scanning attacks.
● Flood attacks, such as Ack flood, DNS flood, Fin flood, HTTP flood, ICMP flood, ICMPv6 flood, Reset flood, SYNACK flood, SYN flood, and UDP flood.
Complete and updated security signature database
 H3C has a professional team to track the security bulletins of global security organizations and enterprises. The team provides an up-to-date security signature database based on the threat analysis results.
H3C has a professional team to track the security bulletins of global security organizations and enterprises. The team provides an up-to-date security signature database based on the threat analysis results.
 The signature database not only provides all vulnerability signatures for the mainstream operation systems, network devices, database systems, and application software systems, but also includes signatures for attacks such as hackers, worms, viruses, Trojans, DoS/DDoS attacks, scanning attacks, spyware, Web fishing, and traffic of P2P, IM, and network games.
The signature database not only provides all vulnerability signatures for the mainstream operation systems, network devices, database systems, and application software systems, but also includes signatures for attacks such as hackers, worms, viruses, Trojans, DoS/DDoS attacks, scanning attacks, spyware, Web fishing, and traffic of P2P, IM, and network games.
 As a partner of Microsoft Active Protections Program, H3C has early access to the vulnerability information so that H3C can provide updated protections to customers faster.
As a partner of Microsoft Active Protections Program, H3C has early access to the vulnerability information so that H3C can provide updated protections to customers faster.
 With certificate of Common Vulnerabilities & Exposures (CVE) compatibility, H3C provides industry-leading vulnerability research and attack prevention technologies. At the same time, H3C pays close attention to the domestic network security events and provides real-time prevention methods.
With certificate of Common Vulnerabilities & Exposures (CVE) compatibility, H3C provides industry-leading vulnerability research and attack prevention technologies. At the same time, H3C pays close attention to the domestic network security events and provides real-time prevention methods.
 With a global honeypot system deployed, H3C understands the latest attack technologies and trends, and use the following releasing methods:
With a global honeypot system deployed, H3C understands the latest attack technologies and trends, and use the following releasing methods:
● Weekly and emergency (for critical security vulnerability) security update publishing.
● Automatic or manual deployment to the IPS devices for real-time attack prevention.
Flexible and extensible, integrated and advanced DPI security
 Integrated security service processing platform—Highly integrates the basic and advanced security protection measures to a security platform.
Integrated security service processing platform—Highly integrates the basic and advanced security protection measures to a security platform.
 Highly precise and effective intrusion inspection engine—Uses the H3C-proprietary Full Inspection with Rigorous State Test (FIRST) engine and various intrusion inspection technologies to implement highly precise inspection of intrusions based on application states. The FIRST engine also supports software and hardware concurrent inspections to improve the inspection efficiency.
Highly precise and effective intrusion inspection engine—Uses the H3C-proprietary Full Inspection with Rigorous State Test (FIRST) engine and various intrusion inspection technologies to implement highly precise inspection of intrusions based on application states. The FIRST engine also supports software and hardware concurrent inspections to improve the inspection efficiency.
 Real-time virus protection—Uses the Kaspersky stream-based antivirus engine to prevent, detect, and remove malicious code from network traffic.
Real-time virus protection—Uses the Kaspersky stream-based antivirus engine to prevent, detect, and remove malicious code from network traffic.
 Fast URL category filtering—Provides basic URL filtering blacklist and whitelist and allows you to query the URL category filtering server on line.
Fast URL category filtering—Provides basic URL filtering blacklist and whitelist and allows you to query the URL category filtering server on line.
 Complete and updated security signature database—H3C has a senior signature database team and professional attack protection labs that can provide a precise and up-to-date signature database.
Complete and updated security signature database—H3C has a senior signature database team and professional attack protection labs that can provide a precise and up-to-date signature database.
 Abundant protection actions for packet inspection results, including blocking, dropping, permit, TCP Reset, raw packet capture, redirection, logging, and sending alarms.
Abundant protection actions for packet inspection results, including blocking, dropping, permit, TCP Reset, raw packet capture, redirection, logging, and sending alarms.
 Flexible combination of actions for detected threats. Common combinations of actions are defined in the factory default settings.
Flexible combination of actions for detected threats. Common combinations of actions are defined in the factory default settings.
Industry-leading IPv6 features
 All features are supported in IPv6 networks.
All features are supported in IPv6 networks.
 Support for deployment in the IPv6 networks, IPv6 feature management, and IPv6 logs and auditing.
Support for deployment in the IPv6 networks, IPv6 feature management, and IPv6 logs and auditing.
Carrier-level high availability
 1:1 active/active and active/standby stateful failover for load balancing and service backup.
1:1 active/active and active/standby stateful failover for load balancing and service backup.
 IRF for flexible management and extension.
IRF for flexible management and extension.
 Fault isolation. Modular design-based Comware 7 ensures one process fault does not affect the running of other processes, the kernel, and the hardware.
Fault isolation. Modular design-based Comware 7 ensures one process fault does not affect the running of other processes, the kernel, and the hardware.
 Configuration and management through Web, CLI, and SSH.
Configuration and management through Web, CLI, and SSH.
 RBAC for controlling user access to functions, command lines, and menus based on user roles.
RBAC for controlling user access to functions, command lines, and menus based on user roles.
 SSM unified management platform for configuration management, performance monitoring, and log auditing.
SSM unified management platform for configuration management, performance monitoring, and log auditing.
 MIB nodes to manage and monitor performance.
MIB nodes to manage and monitor performance.
Publicly available system interfaces
 Programming interfaces—The Linux-based Comware 7 provides open standard programming interfaces for users to define dedicated features. Currently, the system provides NETCONF interfaces.
Programming interfaces—The Linux-based Comware 7 provides open standard programming interfaces for users to define dedicated features. Currently, the system provides NETCONF interfaces.
 Tcl scripts—Comware 7 provides a built-in tool command language (Tcl) interpreter. You can use the Tcl language to execute the Tcl command and the Comware commands, the SNMP GET and SET operations, and the programming interfaces to implement specific features.
Tcl scripts—Comware 7 provides a built-in tool command language (Tcl) interpreter. You can use the Tcl language to execute the Tcl command and the Comware commands, the SNMP GET and SET operations, and the programming interfaces to implement specific features.
 Embedded Automation Architecture—EAA allows you to self-define monitored events and actions to take in response to an event. EAA not only ensures HA, but also meets specific user requirements.
Embedded Automation Architecture—EAA allows you to self-define monitored events and actions to take in response to an event. EAA not only ensures HA, but also meets specific user requirements.
![]() Prevention against common attacks such as hackers, worms, viruses, Trojans, DoS/DDoS attacks, scanning attacks, spyware, protocol anomalies, and Web phishing.
Prevention against common attacks such as hackers, worms, viruses, Trojans, DoS/DDoS attacks, scanning attacks, spyware, protocol anomalies, and Web phishing.![]() P2P and IM traffic identification and control.
P2P and IM traffic identification and control.![]() Powerful bandwidth management and URL filtering.
Powerful bandwidth management and URL filtering.![]() Security protection and access control based on users, applications, time, and security status. Security protection features include IPS, antivirus, app control, URL category, WAF, and user-defined filtering.
Security protection and access control based on users, applications, time, and security status. Security protection features include IPS, antivirus, app control, URL category, WAF, and user-defined filtering.![]() Comware 7-based virtualization and HA features, including IRF and 1:N virtualization, which satisfies the flexible extension requirements of cloud computing.
Comware 7-based virtualization and HA features, including IRF and 1:N virtualization, which satisfies the flexible extension requirements of cloud computing.

 Products and Solutions
Products and Solutions