- Table of Contents
-
- 11-NAT Configuration
- 01-ER G3 Routers Port Mapping Configuration Examples (Web)
- 02-MSR Routers Port Mapping Configuration Examples (Web)
- 03-MSR Routers Configure Internal Users to Access Internal Servers by Using Public Addresses
- 04-MSR Routers Configure Internal and External Users to Access Internal Servers
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 03-MSR Routers Configure Internal Users to Access Internal Servers by Using Public Addresses | 76.28 KB |
|
|
|
MSR Routers |
|
Configure Internal Users to Access Internal Servers by Using Public Addresses |
|
|
Copyright © 2024 New H3C Technologies Co., Ltd. All rights reserved.
No part of this manual may be reproduced or transmitted in any form or by any means without prior written consent of New H3C Technologies Co., Ltd.
Except for the trademarks of New H3C Technologies Co., Ltd., any trademarks that may be mentioned in this document are the property of their respective owners.
The information in this document is subject to change without notice.
Introduction
The following information provides examples for configuring internal users to access internal servers by using public addresses on MSR routers.
Prerequisites
This document applies to Comware 7-based MSR router series. Procedures and information in the examples might be slightly different depending on the software or hardware version of the router.
The configuration examples in this document were created and verified in a lab environment, and all the devices were started with the factory default configuration. When you are working on a live network, make sure you understand the potential impact of every command on your network.
This document assumes that you have basic knowledge of NAT.
Example: Configuring internal users to access internal servers by using public addresses
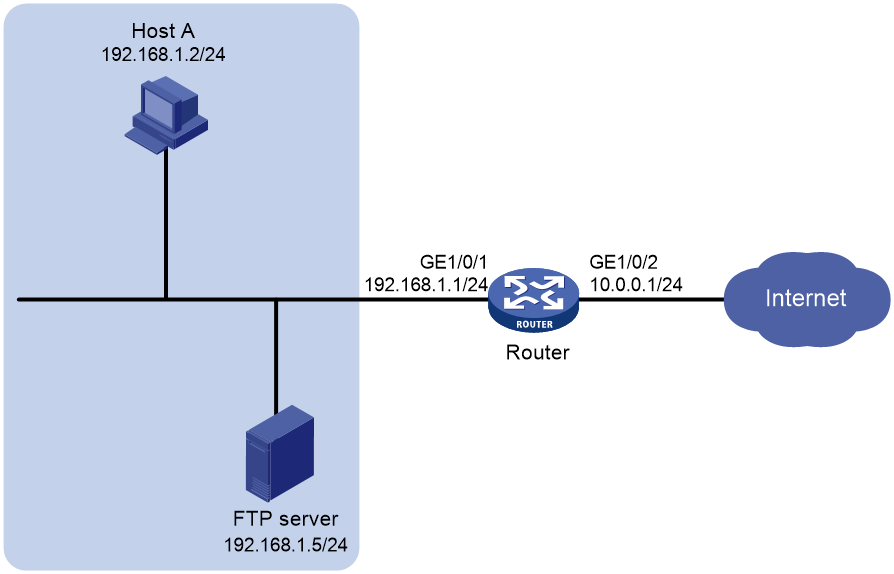
Network configuration
As shown in Figure 1, Host A and the FTP server reside in the same LAN and the router acts as the gateway in the LAN. Configure NAT hairpin to meet the following requirements:
· External hosts can access the internal FTP server through the router.
· Host A accesses the FTP server by using a public address to protect the server from internal network attacks.
Analysis
· Configure an ACL rule and associate it with NAT configuration. Only packets from subnet 192.168.1.0/24 that match the ACL rule are processed by NAT.
· To allow external hosts to access the internal FTP server by using a public IP address, configure NAT Server on the interface connected to the external network.
· To allow Host A to access the internal FTP server by using a public IP address, enable NAT hairpin on the interface connected to the internal network.
Software versions used
This configuration example was created and verified on R6749P14 of the H3C MSR3610-X1 router.
Procedures
# Specify IP addresses for GigabitEthernet 1/0/1 and GigabitEthernet 1/0/2.
<Router> system-view
[Router] interface gigabitethernet 1/0/1
[Router-GigabitEthernet1/0/1] ip address 192.168.1.1 24
[Router-GigabitEthernet1/0/1] quit
[Router] interface gigabitethernet 1/0/2
[Router-GigabitEthernet1/0/2] ip address 10.0.0.1 24
[Router-GigabitEthernet1/0/2] quit
# Configure ACL 2000 to identify packets from subnet 192.168.1.0/24.
[Router] acl number 2000
[Router-acl-ipv4-basic-2000] rule permit source 192.168.1.0 0.0.0.255
[Router-acl-ipv4-basic-2000] quit
# Configure a NAT server mapping on GigabitEthernet 1/0/2 to map the IP address of the FTP server to a public address, allowing external users to access the internal FTP server.
[Router] interface gigabitethernet 1/0/2
[Router-GigabitEthernet1/0/2] nat server protocol tcp global 10.0.0.1 inside 192.168.1.5 ftp
# Enable outbound NAT with Easy IP on GigabitEthernet 1/0/2 so that NAT translates the source addresses of the packets from Host A into the IP address of GigabitEthernet 1/0/2.
[Router-GigabitEthernet1/0/2] nat outbound 2000
[Router-GigabitEthernet1/0/2] quit
# Enable NAT hairpin on GigabitEthernet 1/0/1.
[Router] interface gigabitethernet 1/0/1
[Router-GigabitEthernet1/0/1] nat hairpin enable
[Router-GigabitEthernet1/0/1] quit
Verifying the configuration
# Execute the display nat all command to display all NAT configuration and statistics and verify that GigabitEthernet 1/0/1 is enabled with NAT hairpin.
[Router] display nat all
NAT outbound information:
Totally 1 NAT outbound rules.
Interface: GigabitEthernet1/0/2
ACL: 2000
Address group ID: ---
Port-preserved: N NO-PAT: N Reversible: N
NAT counting: 0
Config status: Active
NAT internal server information:
Totally 1 internal servers.
Interface: GigabitEthernet1/0/2
Protocol: 6(TCP)
Global IP/port: 10.0.0.1/21
Local IP/port: 192.168.1.5/21
NAT counting : 0
Config status : Active
NAT logging:
Log enable : Disabled
Flow-begin : Disabled
Flow-end : Disabled
Flow-active : Disabled
Port-block-assign : Disabled
Port-block-withdraw : Disabled
Alarm : Disabled
NO-PAT IP usage : Disabled
NAT hairpinning:
Totally 1 interfaces enabled with NAT hairpinning.
Interface: GigabitEthernet1/0/1
Config status: Active
NAT mapping behavior:
Mapping mode: Address and Port-Dependent
ACL : ---
Config status: Active
NAT ALG:
DNS : Enabled
FTP : Enabled
H323 : Enabled
ICMP-ERROR : Enabled
ILS : Enabled
MGCP : Enabled
NBT : Enabled
PPTP : Enabled
RTSP : Enabled
RSH : Enabled
SCCP : Enabled
SCTP : Enabled
SIP : Enabled
SQLNET : Enabled
TFTP : Enabled
XDMCP : Enabled
Static NAT load balancing: Disabled
NAT link-switch recreate-session: Disabled
NAT configuration-for-new-connection: Disabled
NAT global-policy compatible-previous-version rule-type ipv4-snat-and-dnat trans
late-before-secp : Disabled
# Execute the display nat session verbose command to display NAT sessions that are generated when Host A accesses the FTP server.
[Router] display nat session verbose
Slot 1:
Initiator:
Source IP/port: 192.168.1.2/1694
Destination IP/port: 10.0.0.1/21
DS-Lite tunnel peer: -
VPN instance/VLAN ID/VLL ID: -/-/-
Protocol: TCP(6)
Inbound interface: GigabitEthernet1/0/1
Responder:
Source IP/port: 192.168.1.5/21
Destination IP/port: 10.0.0.1/1025
DS-Lite tunnel peer: -
VPN instance/VLAN ID/VLL ID: -/-/-
Protocol: TCP(6)
Inbound interface: GigabitEthernet1/0/1
State: TCP_ESTABLISHED
Application: HTTP
Rule ID: -/-/-
Rule name:
Start time: 2013-08-15 14:53:29 TTL: 3597s
Initiator->Responder: 7 packets 308 bytes
Responder->Initiator: 5 packets 312 bytes
Total sessions found: 1
Configuration files
interface GigabitEthernet1/0/1
port link-mode route
ip address 192.168.1.1 255.255.255.0
nat hairpin enable
#
interface GigabitEthernet1/0/2
port link-mode route
ip address 10.0.0.1 255.255.255.0
nat outbound 2000
nat server protocol tcp global 10.0.0.1 21 inside 192.168.1.5 21
#
acl number 2000
rule 0 permit source 192.168.1.0 0.0.0.255
#
Related documentation
· Layer 3—IP Services Configuration Guide in H3C MSR Router Series Comware 7 Configuration Guides
· Layer 3—IP Services Command Reference in H3C MSR Router Series Comware 7 Command References