- Table of Contents
-
- 03-Security Configuration Guide
- 00-Preface
- 01-Security zone configuration
- 02-Security policy configuration
- 03-ASPF configuration
- 04-Session management
- 05-Object group configuration
- 06-IP source guard configuration
- 07-AAA configuration
- 08-User identification configuration
- 09-Password control configuration
- 10-Portal configuration
- 11-MAC authentication configuration
- 12-SMS configuration
- 13-802.1X configuration
- 14-Public key management
- 15-PKI configuration
- 16-SSH configuration
- 17-SSL configuration
- 18-Connection limit configuration
- 19-Attack detection and prevention configuration
- 20-Deception configuration
- 21-Server connection detection configuration
- 22-ARP attack protection configuration
- 23-ND attack defense configuration
- 24-uRPF configuration
- 25-IP-MAC binding configuration
- 26-Keychain configuration
- 27-MAC learning through a Layer 3 device configuration
- 28-APR configuration
- 29-IPoE configuration
- 30-Crypto engine configuration
- 31-Location identification configuration
- 32-Terminal identification configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 20-Deception configuration | 290.92 KB |
Contents
Deception device and decoy server
Restrictions: Hardware compatibility with deception
Configuring the decoy server IP address
Configuring offline IP deception
Configuring the IP scanning rate
Configure the deception allowlist
Display and maintenance commands for deception
Deception configuration examples
Example: Configuring the basic deception feature
Configuring deception
About deception
Deception is a cybersecurity defense practice that aims to detect and prevent attacks targeting the internal network. Intruders typically scan the internal network infrastructure and host ports for vulnerabilities to launch further attacks. Deception technology detects scanning behaviors on the intranet to find out intrusion threats. Besides, it forges the responses of the victims to entice the attackers into deep interactions with the decoy server. In this way, it can misdirect the attackers from their true targets, analyze and traceback the attacks, so as to protect the intranet security.
Deception device and decoy server
A deception device and a decoy server cooperate to implement deception.
· Deception device—Device enabled with the deception capability. The deception device monitors the intranet scanning behaviors and lures suspicious traffic to the decoy server.
· Decoy server—Third-party threat perception and traceability system deployed with various sandboxes and analytics tools. The decoy server imitates real network devices, systems, and applications and deceives the attackers to interact with it continuously so as to protect the real assets from attacks.
Deception types
Offline IP deception
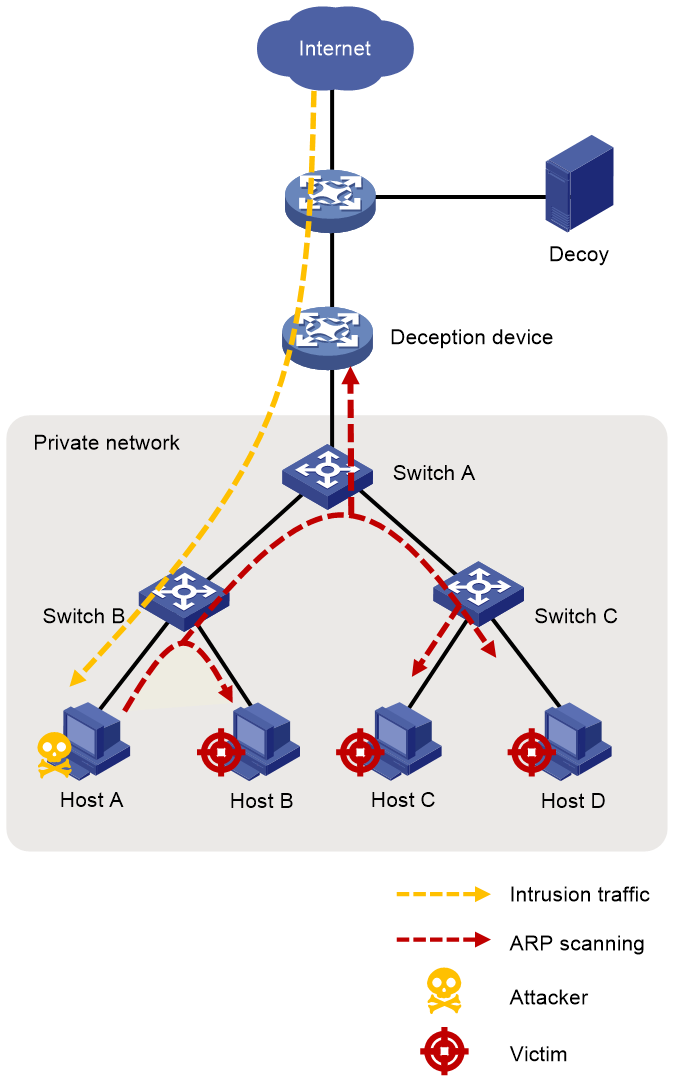
As shown in Figure 1, after the attackers intrude the network through viruses or Trojans, they first scan the intranet infrastructure, typically by sending continuous ARP requests from the infected hosts or servers. The offline IP deception feature can monitor the ARP requests for offline IP addresses. By forging the ARP responses, it lures the subsequent traffic of the attackers to the decoy server for in-depth interactions and analysis.
Offline IP deception supports two modes, which require different triggers.
· In strict mode, once the deception device detects an ARP request for an offline IP address on a specific network, it immediately lures the attacker's subsequent traffic destined for the IP address to the decoy server.
· In non-strict mode, the deception device periodically detects the rate of ARP requests sent by attackers to the specified networks. When the rate reaches the deception threshold, the subsequent traffic sent from the attackers to the offline IP addresses in the specified networks will be lured to the decoy server.
Figure 1 Offline IP deception diagram
|
|
NOTE: The deception device processes the ARP requests sent from attackers and sends ARP responses to the attackers. Make sure the deception device has an up Layer 3 Ethernet interface, Layer 3 Ethernet subinterface, or VLAN interface on the detection networks. |
Static deception
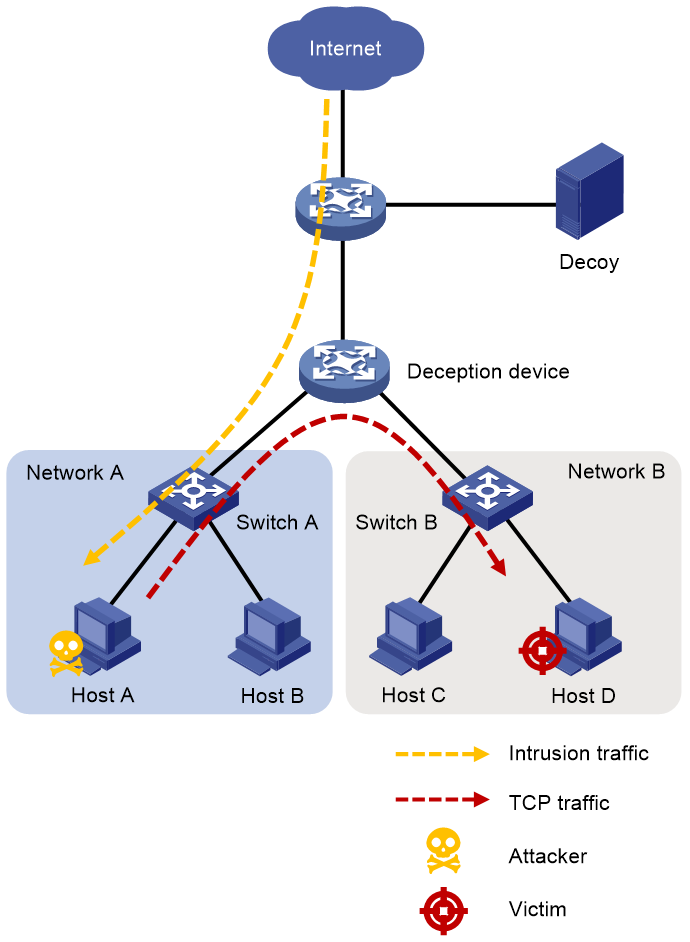
As shown in Figure 2, after attackers intrude the internal network through viruses or Trojans, they might perform port scanning or other TCP-based access to some fixed IP addresses. Static deception regards all the traffic that accesses the specified IP addresses as suspicious attack traffic and lures the traffic to the decoy server for in-depth analysis.
A static deception is triggered if the deception device detects ARP or TCP scanning aiming at the IP addresses in the specified network segment. It immediately lures the attacker's subsequent traffic destined for the IP addresses to the decoy server, regardless of the online status of the IP addresses.
Figure 2 Static deception network diagram
|
|
NOTE: To perform static deception, the deception device must reside on the only path for the intrusion traffic to reach the victim. |
Deception workflow
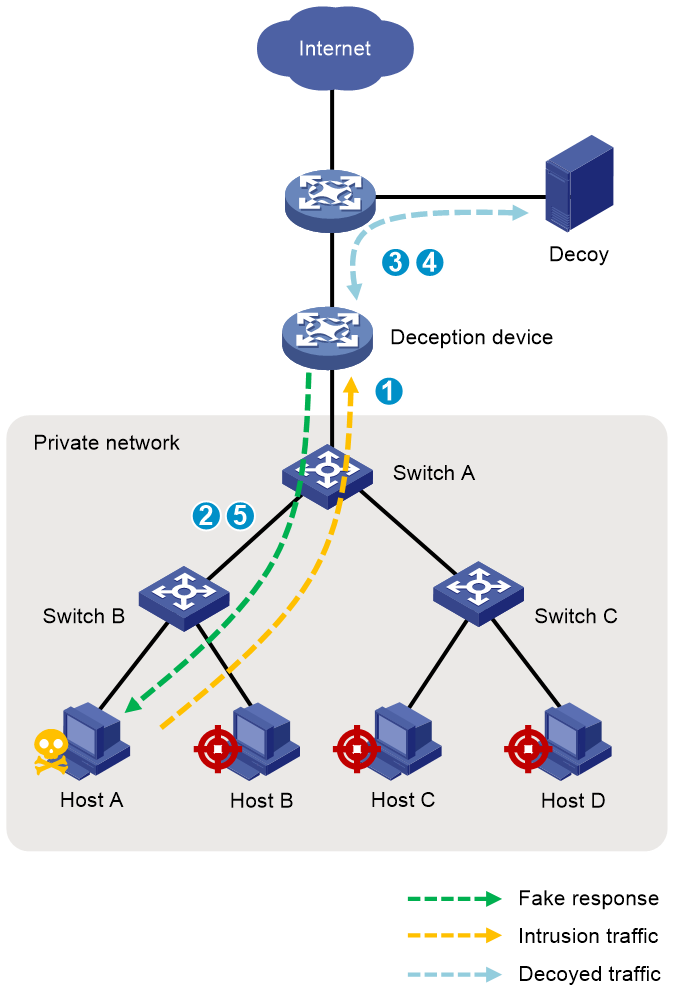
As shown in Figure 3, deception works as follows:
1. The deception device constantly monitors scanning behaviors in the intranet. Once it detects a scanning behavior that triggers the deception threshold, it enters deception state.
2. The deception device forges the ARP response for the ARP request that is regarded as intrusion traffic, sends the response to the attacker, so as to direct the subsequent traffic of the attacker to the deception device.
3. When the deception device receives subsequent traffic, it creates a deception redirect entry to record the packet source and destination IP addresses, source and destination port numbers, deception type, and the entry aging time, and then forwards the traffic to the decoy server for further analysis.
4. The decoy server uses the built-in sandbox to construct the response packet and sends the packet back to the deception device.
5. The deception device forwards the response packet to the attacker, completing a round of interaction with the attacker.
Before the deception redirect entry ages, traffic matching the entry will be lured to the decoy server for processing. After the deception entry ages, the corresponding traffic will not be directed to the decoy server any longer until the deception device detects and decoys the traffic again using the previous procedure.
Figure 3 Deception workflow (offline IP deception)
Restrictions: Hardware compatibility with deception
|
Series |
Models |
Deception compatibility |
|
F5000 series |
F5000-AI360, F5000-AI160, F5000-AI120, F5000-AI-40, F5000-AI-20, F5000-AI-15, F5000-CN-G85, F5000-CN-G65, F5000-CN60, F5000-CN-G55, F5000-CN30 |
Yes |
|
F5000-CN160 |
No |
|
|
F1000 series |
F1000-AI-90, F1000-AI-80, F1000-AI-75, F1000-AI-70, F1000-AI-65, F1000-AI-60, F1000-AI-25, F1000-CN-G35 |
Yes |
Deception tasks at a glance
To configure deception, perform the following tasks:
1. Configuring the decoy server IP address
2. Configuring offline IP deception
4. (Optional.) Configuring the IP scanning rate
5. (Optional.) Configure the deception allowlist
Configuring the decoy server IP address
About this feature
A decoy server is a threat perception and traceability system deployed with sandboxes and analysis tools, which can decoy attackers to interact with it deeply in the well-constructed simulation environment, analyze and trace the attack behaviors, and protect the real network from attacks.
Restrictions and guidelines
Make sure the deception device and decoy server can reach each other.
Do not configure the virtual IP address of a VRRP group as the source IP address used by the deception device to connect to the decoy server. For more information about VRRP group, see the VRRP configuration in High Availability Configuration Guide.
Procedure
1. Enter system view.
system-view
2. Enter deception view.
deception
3. Configure the decoy server IP address.
decoy destination destination-ip [ source source-ip ] [ dest-port destination-port ] [ vpn-instance vpn-instance-name ]
By default, no decoy server IP address is configured.
Configuring offline IP deception
About this feature
Offline IP deception detects ARP scans on the specified detection networks, and decoys the subsequent intrusion traffic destined for the offline IP addresses in the detection networks.
Restrictions and guidelines
Make sure the deception device has an up Layer 3 Ethernet interface, Layer 3 Ethernet subinterface, or VLAN interface on the detection networks.
On a network where devices use static ARP entries instead of sending ARP requests, enable the strict mode for deception.
The total number of IP addresses in all detection networks cannot exceed 10240.
A detection network cannot contain IP address 0.0.0.0 or 255.255.255.255.
Procedure
1. Enter system view.
system-view
2. Enter deception view.
deception
3. Configure a detection network.
detect-network [ id id-number ] ip-address [ mask | mask-length ] [ vpn-instance vpn-instance-name ]
By default, no detection network is configured.
4. Set the ARP request sending rate that triggers deception (the deception threshold).
arp-scan threshold threshold-value
By default, the ARP request sending rate that triggers deception is 10 ARP requests per 10 seconds.
5. (Optional.) Enable the strict mode for deception.
deception mode strict
By default, the strict deception mode is disabled.
Configure static deception
About this feature
Static deception decoys all the traffic that accesses the decoy networks.
Restrictions and guidelines
|
CAUTION: Do not configure a decoy network that contains the device management address. Otherwise, you cannot manage the device through the address. |
If a detection network overlaps with a decoy network, the device will treat the overlapping IP addresses as the IP addresses in the decoy network.
A decoy network cannot contain IP address 0.0.0.0 or 255.255.255.255.
Procedure
1. Enter system view.
system-view
2. Enter deception view.
deception
3. Configure a decoy network.
decoy-network [ id id-number ] destination ip-address [ mask | mask-length ] [ vpn-instance vpn-instance-name ]
By default, no decoy network is configured.
Configuring the IP scanning rate
About this feature
The deception device needs to maintain the online status of all the IP addresses in the detection networks for offline IP deception.
After deception is enabled, the deception device initiates IP address scanning on the detection networks at intervals of 30 minutes. Within an interval, the deception device sends ARP requests to the IP addresses on the detection networks at the specified rate, and then updates the IP address online status according to the responses.
Restrictions and guidelines
If the IP scanning rate is too big, the scanning might affect the internal network operating. If the IP scanning rate is too small, it might take a long time to obtain the online status of the IP addresses.
Procedure
1. Enter system view.
system-view
deception
3. Configure the IP scanning rate.
ip-state detect rate rate-number
By default, the deception device performs IP scanning at a rate of 30 ARP requests per second.
Configure the deception allowlist
About this feature
The deception allowlist specifies the deception exceptions. It can contain source address allowlist entries and destination address allowlist entries.
The deception device will not decoy the traffic accessing the destination addresses or the traffic initiated by the source addresses in the allowlist.
Restrictions and guidelines
· For devices that do not respond to ARP requests (some legacy printers for example), you can add their IP addresses to the destination address allowlist to prevent normal access traffic from being decoyed. For devices that will periodically send probe packets (some NMS devices for example), you can add their IP addresses to the source address allowlist to prevent their traffic from being decoyed as intrusion traffic.
· If the deception allowlist overlaps with a decoy network or detection network, the device will treat the overlapping IP addresses as the IP addresses in the allowlist.
· A deception allowlist cannot contain IP address 0.0.0.0 or 255.255.255.255.
Procedure
1. Enter system view.
system-view
2. Enter deception view.
deception
3. Configure a deception allowlist entry.
allowlist [ id id-number ] { destination | source } ip-address [ mask | mask-length ] [ vpn-instance vpn-instance-name ]
By default, no deception allowlist entry is configured.
Enabling deception
About this feature
After deception is enabled, the device monitors the intranet scanning behaviors and lures suspicious traffic to the decoy server for in-depth analysis.
Restrictions and guidelines
|
CAUTION: Incorrect deception settings might misdirect normal network traffic to the decoy server. Before enabling deception, use the display this command in deception view to verify the deception settings. |
For the deception function to take effect, you must configure a minimum of one decoy network (by using the decoy-network command) or detection network (by using the detect-network command).
Procedure
1. Enter system view.
system-view
2. Enter deception view.
deception
3. Enable deception.
deception enable
By default, deception is disabled.
Display and maintenance commands for deception
Execute display commands in any view and reset commands in user view.
|
Command |
|
|
Display ARP scanning statistics |
display deception arp-scan [ source ip-address ] statistics [ slot slot-number ] |
|
Display the decoy server status |
display deception decoy status |
|
Display the online status of the IP addresses in detection networks |
display deception ip-state [ ip-address ] [ slot slot-number ] |
|
Display deception redirect entries. |
display deception redirect [ source-ip ip-address ] [ destination-ip ip-address ] [ destination-port port ] [ slot slot-number ] |
|
Clear the online status records for the IP addresses in detection networks |
reset deception ip-state |
|
Clear the specified deception redirect entries. |
reset deception redirect [ source-ip ip-address ] [ destination-ip ip-address ] [ destination-port port ] |
Deception configuration examples
Example: Configuring the basic deception feature
Network configuration
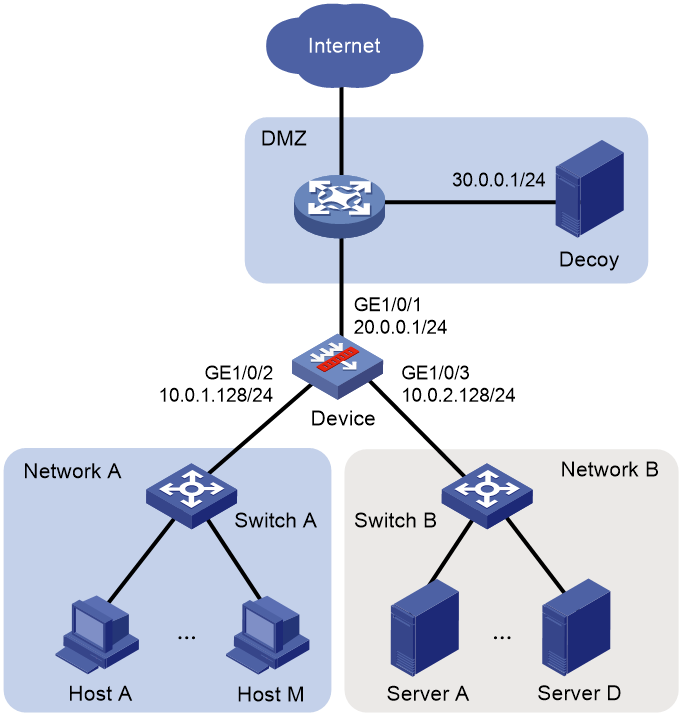
Internal network A (10.0.1.0/24) is for the office. Internal network B (10.0.2.0/24) is for business. A legacy printer with IP address 10.0.1.38 works in network A. To detect and prevent attacks targeting the internal networks, deploy a deception system, as follows:
· Use the internal gateway as the deception device. Deploy a separate server with IP address 30.0.0.1 as the decoy server.
· Configure offline IP deception for network A and network B to detect abnormal ARP scanning on the networks.
· Configure static deception for the idle network segment 10.0.2.0/28 of network A to decoy all the traffic accessing the idle network segment.
· Add the printer's IP address to the destination address deception allowlist, as the printer does not response to ARP requests.
Figure 4 Network diagram
Prerequisites
Complete the decoy server configuration. For more information, see the manual for the decoy server.
Procedure
1. Assign IP addresses to interfaces:
# Assign an IP address to interface to interface GigabitEthernet 1/0/1.
<Device> system-view
[Device] interface gigabitethernet 1/0/1
[Device-GigabitEthernet1/0/1] ip address 20.0.0.1 24
[Device-GigabitEthernet1/0/1] quit
# Assign IP addresses to other interfaces in the same way. (Details not shown.)
2. Add interfaces to security zones.
[Device] security-zone name DMZ
[Device-security-zone-DMZ] import interface gigabitethernet 1/0/1
[Device-security-zone-DMZ] quit
[Device] security-zone name networkA
[Device-security-zone-networkA] import interface gigabitethernet 1/0/2
[Device-security-zone-networkA] quit
[Device] security-zone name networkB
[Device-security-zone-networkB] import interface gigabitethernet 1/0/3
[Device-security-zone-networkB] quit
3. Configure a security policy to ensure network connectivity.
[Device] security-policy ip
[Device-security-policy-ip] rule name neta-netb
[Device-security-policy-ip-0-neta-netb] action pass
[Device-security-policy-ip-0-neta-netb] source-zone networkA
[Device-security-policy-ip-0-neta-netb] destination-zone networkB
[Device-security-policy-ip-0-neta-netb] quit
[Device-security-policy-ip] rule name neta-dmz
[Device-security-policy-ip-1-neta-dmz] action pass
[Device-security-policy-ip-1-neta-dmz] source-zone networkA
[Device-security-policy-ip-1-neta-dmz] destination-zone DMZ
[Device-security-policy-ip-1-neta-dmz] quit
[Device-security-policy-ip] rule name dmz-neta
[Device-security-policy-ip-2-dmz-neta] action pass
[Device-security-policy-ip-2-dmz-neta] source-zone DMZ
[Device-security-policy-ip-2-dmz-neta] destination-zone networkA
[Device-security-policy-ip-2-dmz-neta] quit
[Device-security-policy-ip] rule name dmz-netb
[Device-security-policy-ip-3-dmz-netb] action pass
[Device-security-policy-ip-3-dmz-netb] source-zone DMZ
[Device-security-policy-ip-3-dmz-netb] destination-zone networkB
[Device-security-policy-ip-3-dmz-netb] quit
[Device-security-policy-ip] rule name local-dmz
[Device-security-policy-ip-4-local-dmz] action pass
[Device-security-policy-ip-4-local-dmz] source-zone Local
[Device-security-policy-ip-4-local-dmz] destination-zone DMZ
[Device-security-policy-ip-4-local-dmz] source-ip-host 20.0.0.1
[Device-security-policy-ip-4-local-dmz] destination-ip-host 30.0.0.1
[Device-security-policy-ip-4-local-dmz] quit
[Device-security-policy-ip] rule name dmz-local
[Device-security-policy-ip-5-dmz-local] action pass
[Device-security-policy-ip-5-dmz-local] source-zone DMZ
[Device-security-policy-ip-5-dmz-local] destination-zone Local
[Device-security-policy-ip-5-dmz-local] source-ip-host 30.0.0.1
[Device-security-policy-ip-5-dmz-local] destination-ip-host 20.0.0.1
[Device-security-policy-ip-5-dmz-local] quit
[Device-security-policy-ip] rule name local-neta
[Device-security-policy-ip-6-local-neta] action pass
[Device-security-policy-ip-6-local-neta] source-zone Local
[Device-security-policy-ip-6-local-neta] destination-zone networkA
[Device-security-policy-ip-6-local-neta] quit
[Device-security-policy-ip] rule name local-netb
[Device-security-policy-ip-7-local-netb] action pass
[Device-security-policy-ip-7-local-netb] source-zone Local
[Device-security-policy-ip-7-local-netb] destination-zone networkB
[Device-security-policy-ip-7-local-netb] quit
[Device-security-policy-ip] quit
4. Configure settings for routing:
This example configures a static routes, and the next hop in the route is 2.2.2.2.
# Configure a static route for the device to reach the decoy server.
[Device] ip route-static 30.0.0.1 24 gigabitethernet 1/0/1 20.0.0.2
5. Configure the deception function:
# Configure the IP address of the decoy server as 30.0.0.1, and the source IP address used by the deception device to connect the decoy server as 20.0.0.1.
[Device] deception
[Device-deception] decoy destination 30.0.0.1 source 20.0.0.1
# Configure offline IP deception settings: configure detection networks as 10.0.1.0/24 and 10.0.2.0/24, configure the deception threshold as 500 ARP requests per 10 seconds, and the IP scanning rate as 100 ARP requests per second.
[Device-deception] detect-network id 1 10.0.1.0 255.255.255.0
[Device-deception] detect-network id 2 10.0.2.0 255.255.255.0
[Device-deception] arp-scan threshold 500
[Device-deception] ip-state detect rate 100
# Configure decoy network 1 for static deception as 10.0.1.0/28.
[Device-deception] decoy-network id 1 destination 10.0.1.0 255.255.255.240
# Add the printer's IP address 10.0.1.38 to the destination address deception allowlist.
[Device-deception] allowlist destination 10.0.1.38
# Verify the correctness of the deception configuration.
[Device-deception] display this
# Enable deception.
[Device-deception] deception enable
Verifying the configuration
1. Display the deception settings.
[Device-deception] display this
deception enable
decoy destination 30.0.0.1 source 20.0.0.1
allowlist destination 10.0.1.38
arp-scan threshold 500
decoy-network id 1 destination 10.0.1.0 255.255.255.240
detect-network id 1 10.0.1.0 255.255.255.0
detect-network id 2 10.0.2.0 255.255.255.0
ip-state detect rate 100
[Device-deception] quit
[Device] quit
2. Verify that the registration status of the deception device on the decoy server is alive.
<Device> display deception decoy status
Decoy register status information:
Register status : alive
Online duration : 25510(s)
Available decoy service ports:
21 22 80 443 3306
4855 15554
3. After the deception device detects a threat and enters deception state, display the generated deception redirect entry.
<Device> display deception redirect
slot 1:
SrcIP SrcPort DstIP DstPort VPN instance Type Aging Count
10.0.1.1 1123 10.0.2.1 80 -- Decoy 12 100