- Table of Contents
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 01-Text | 3.29 MB |
Introduction to system information
Introduction to fast configuration
Configure LAN interface settings
Configure a time range group with only one type of time ranges
Configure a time range group that contains both periodic and absolute time ranges
Introduction to the firewall feature
Introduction to attack defense
Introduction to connection limit
Configure network connection limits
Configure VLAN-based network connection limits
Introduction to MAC address filter
Configure a MAC address filter
Add a whitelist or blacklist entry
Introduction to ARP attack protection
Configure dynamic ARP learning
Configure dynamic ARP management
Configure attack protection management
Introduction to portal authentication
Configure the authentication page for Web page authentication
Add an authentication-free MAC address
Add an authentication-free IP address or host name
Configure the device as a branch node
Configure the device as a center node
Introduction to application services
Introduction to basic settings
Configure basic device information
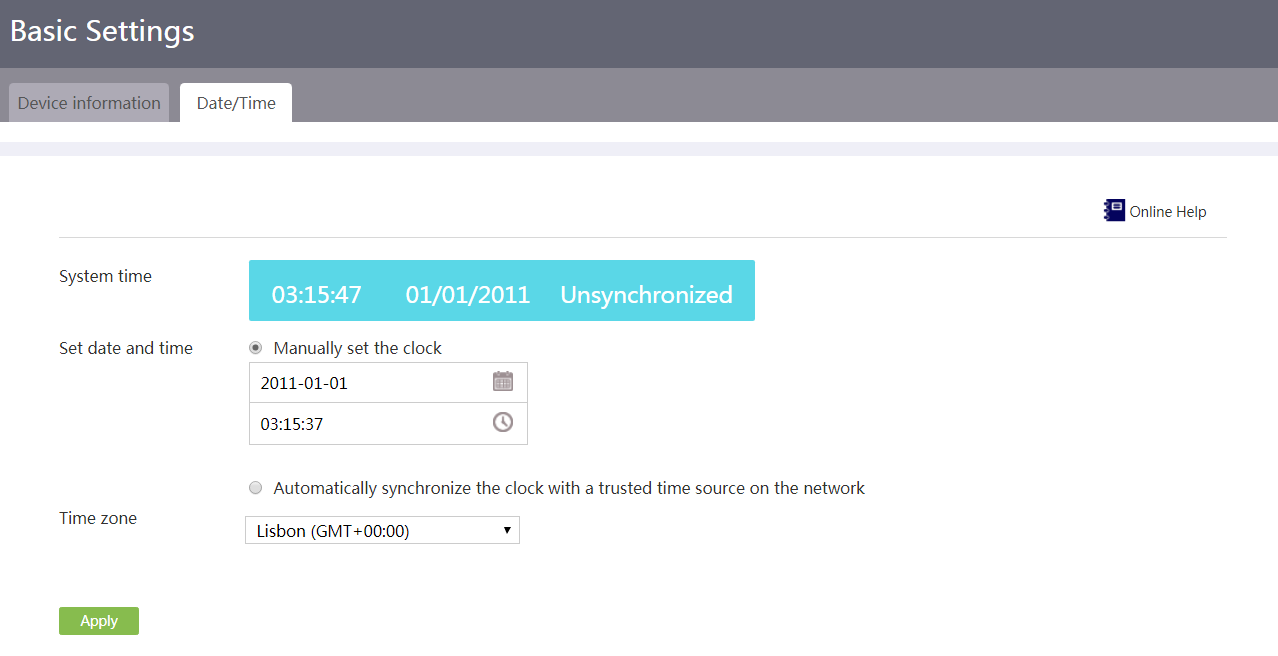
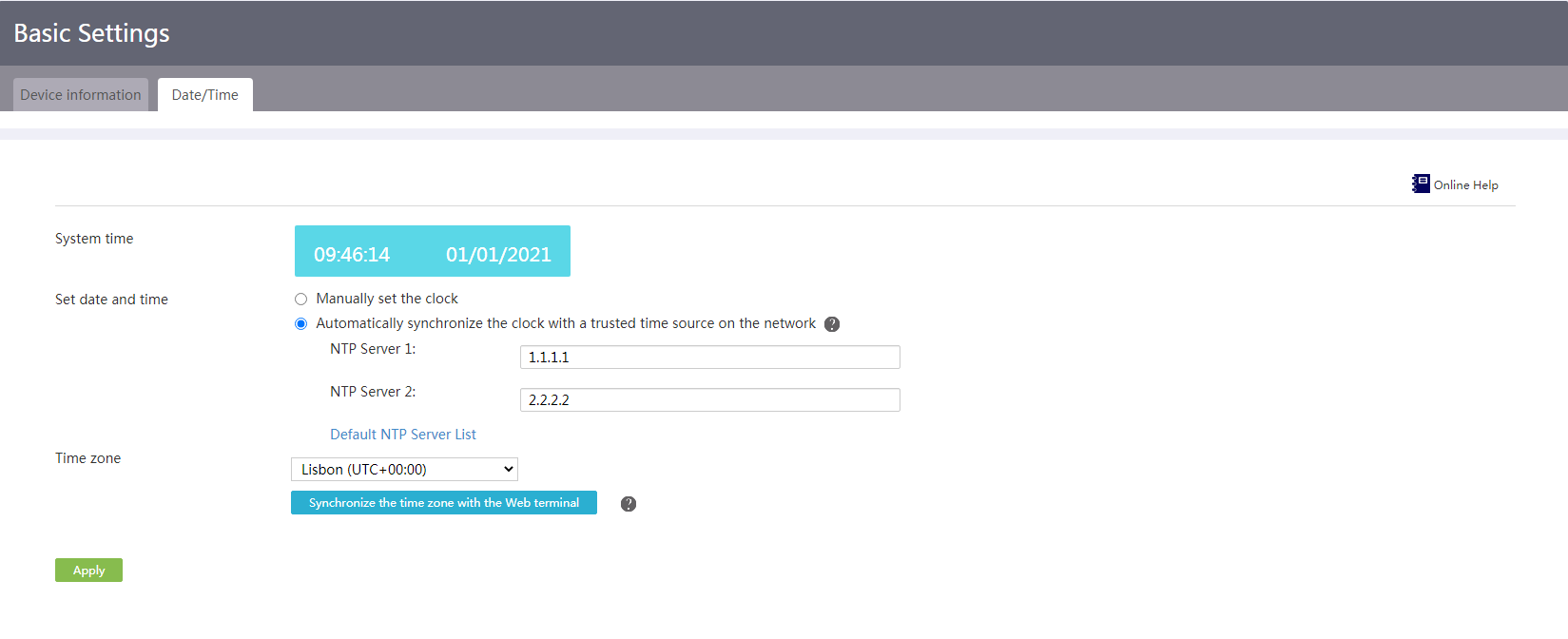
Manually configure the system time
Automatically synchronize the UTC time
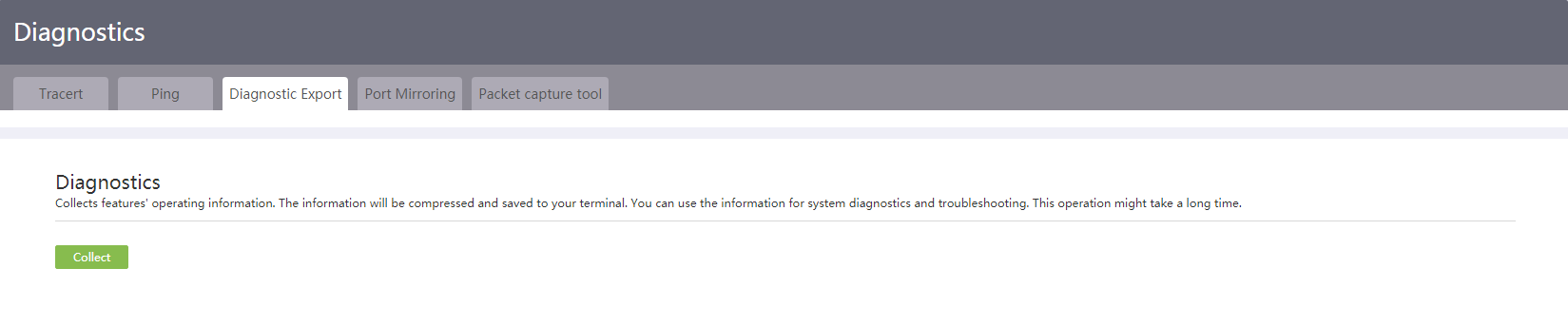
Collect diagnostic information
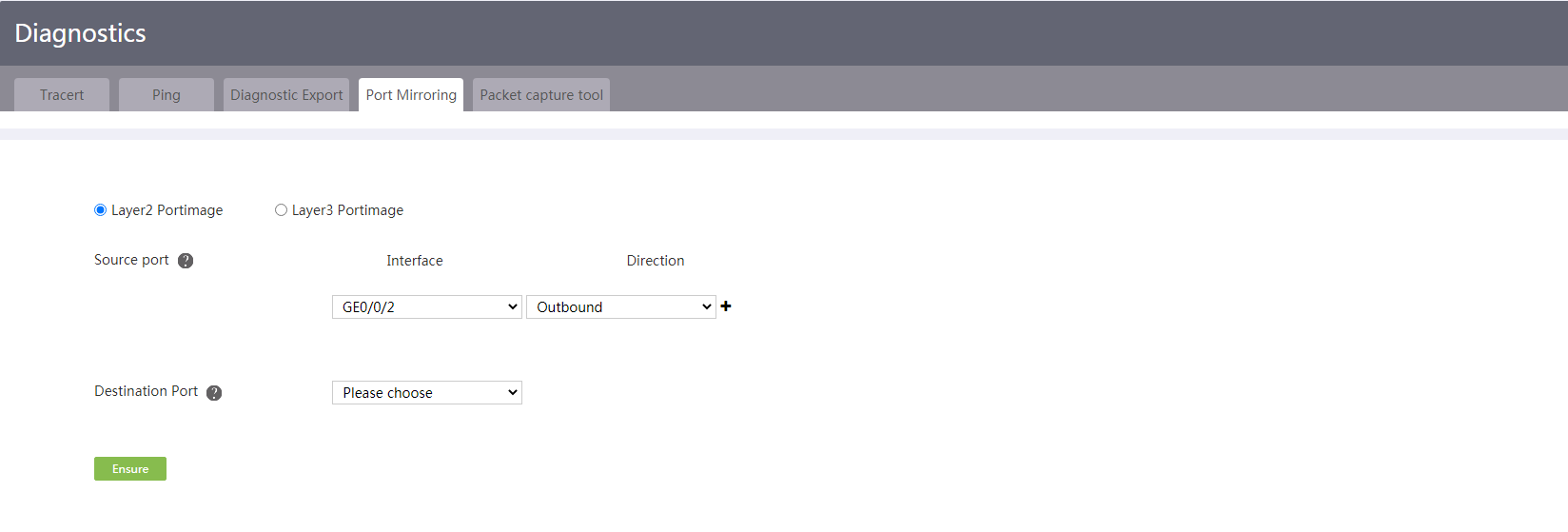
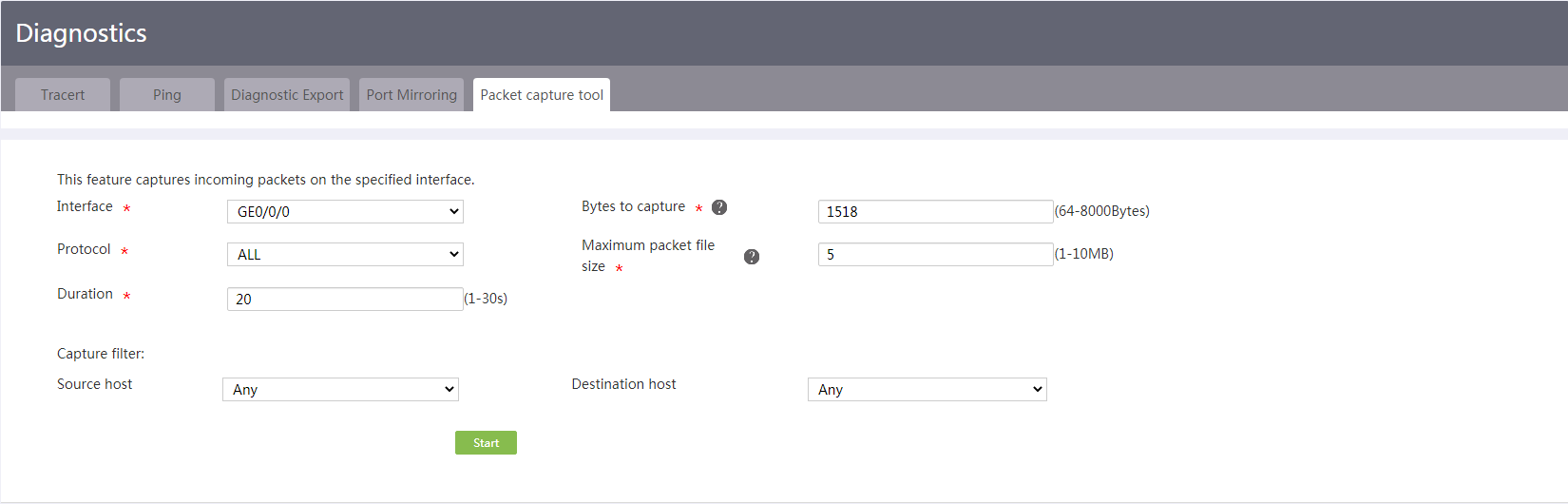
Configure the packet capture tool
About admin account management
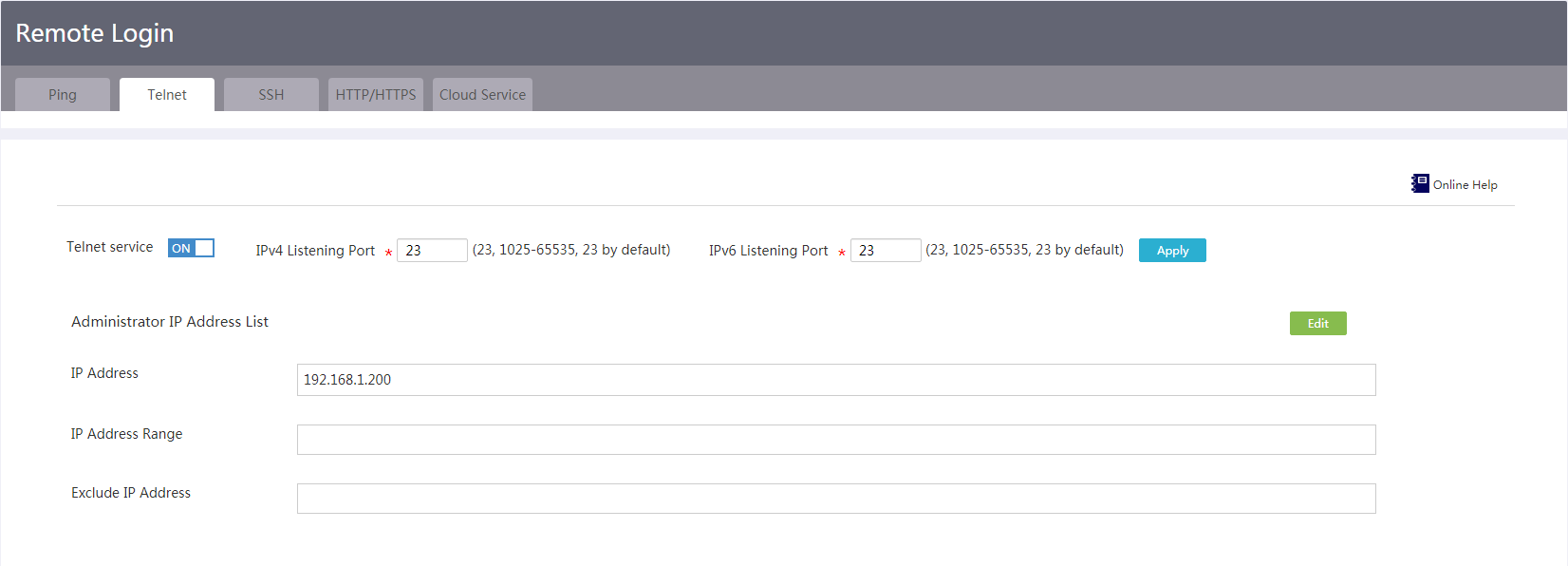
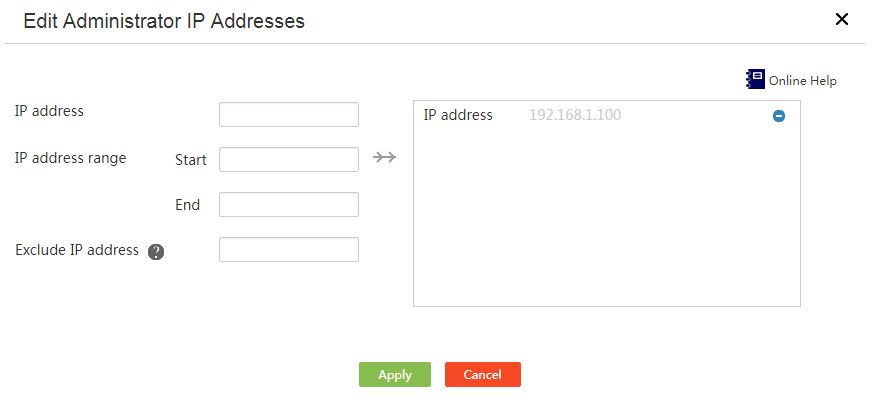
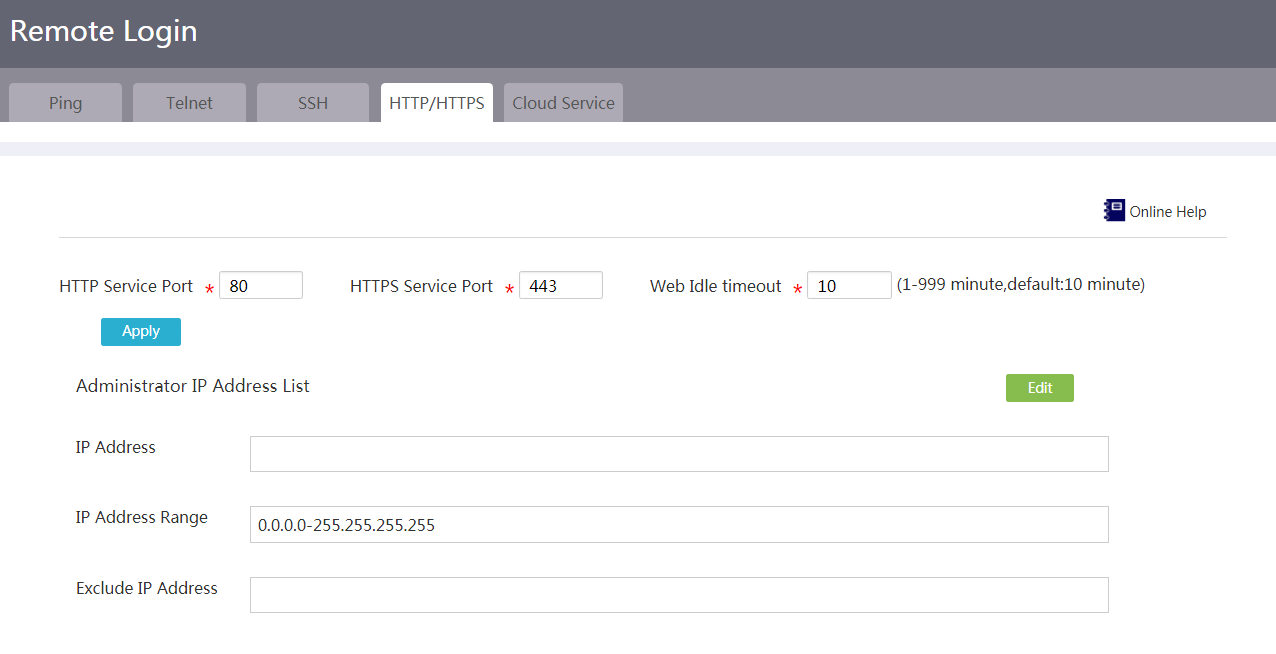
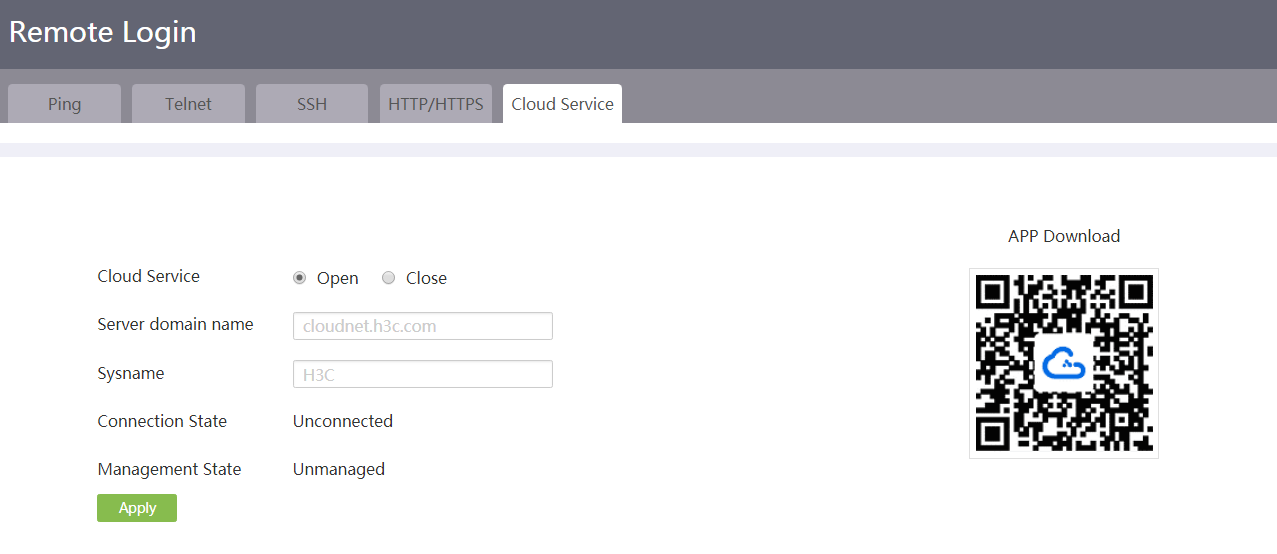
Introduction to remote management
Configure HTTP login and HTTPS login
Introduction to configuration management
Save the running configuration
Restore configuration from a backup file
Export the running configuration
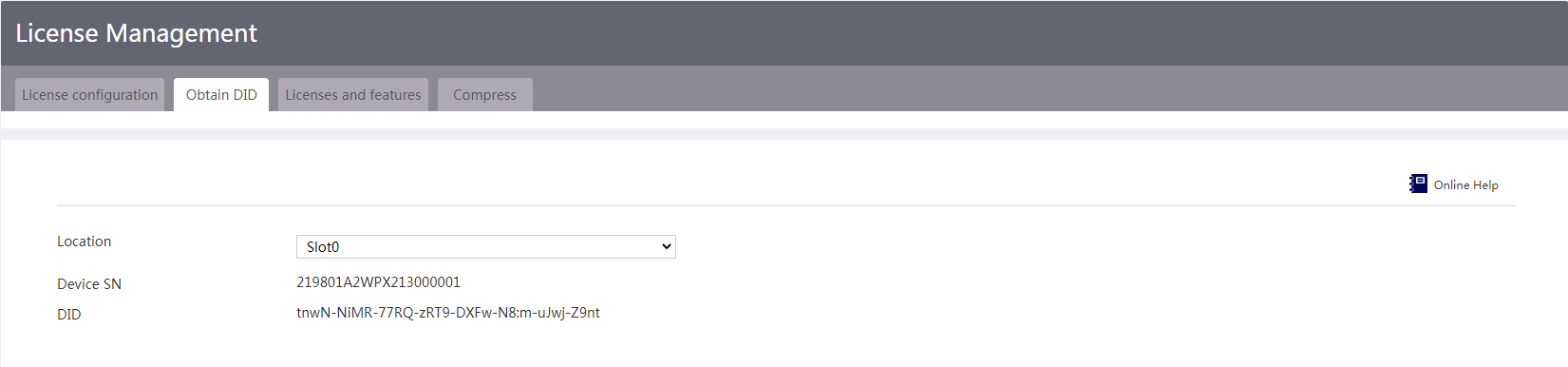
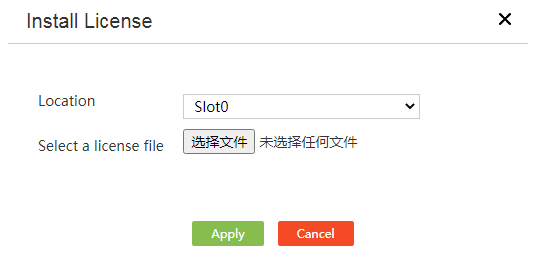
Restrictions and guidelines for license management
View features that require licenses
Send system log to a log server
View system log on the webpage
Products
H3C SR router series includes the following series:
· H3C SR6602-I routers
· H3C SR6602-IE routers
System information
Introduction to system information
System information allows you to obtain device operation information, use the wizard to configure basic settings, and obtain technology support.
View system information
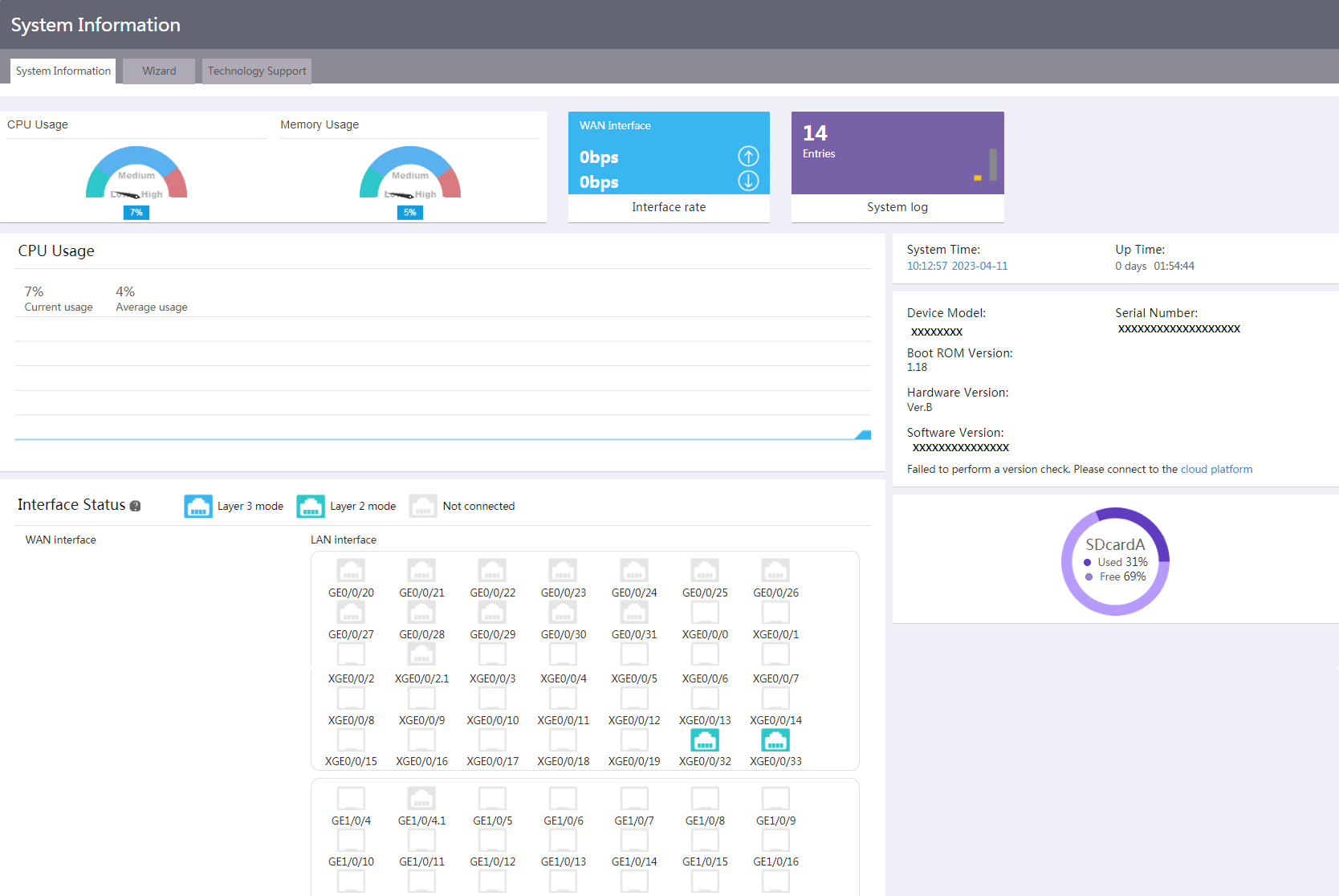
CPU usage and memory usage
Network configuration
Perform this task to view information about CPU usage and memory usage, including:
· Current and average CPU usage.
· Current and average memory usage.
Procedure
1. From the navigation pane, select System Information.
2. To view the current and average CPU usage or the current and average memory usage, click the CPU Usage or Memory Usage area, respectively.
Figure 1 Viewing CPU usage and memory usage
Interface rate
Network configuration
Perform this task to view interface rate information, including uplink traffic, uplink rate, downlink traffic, downlink rate, WAN interface status, and network access parameters. You can also re-connect an interface or disconnect an interface, or refresh interface information.
Procedure
1. From the navigation pane, select System Information.
2. Click the Interface rate area.
3. To reconnect to an interface, click reconnect.
4. To disconnect an interface, click release.
Figure 2 Viewing interface rate information
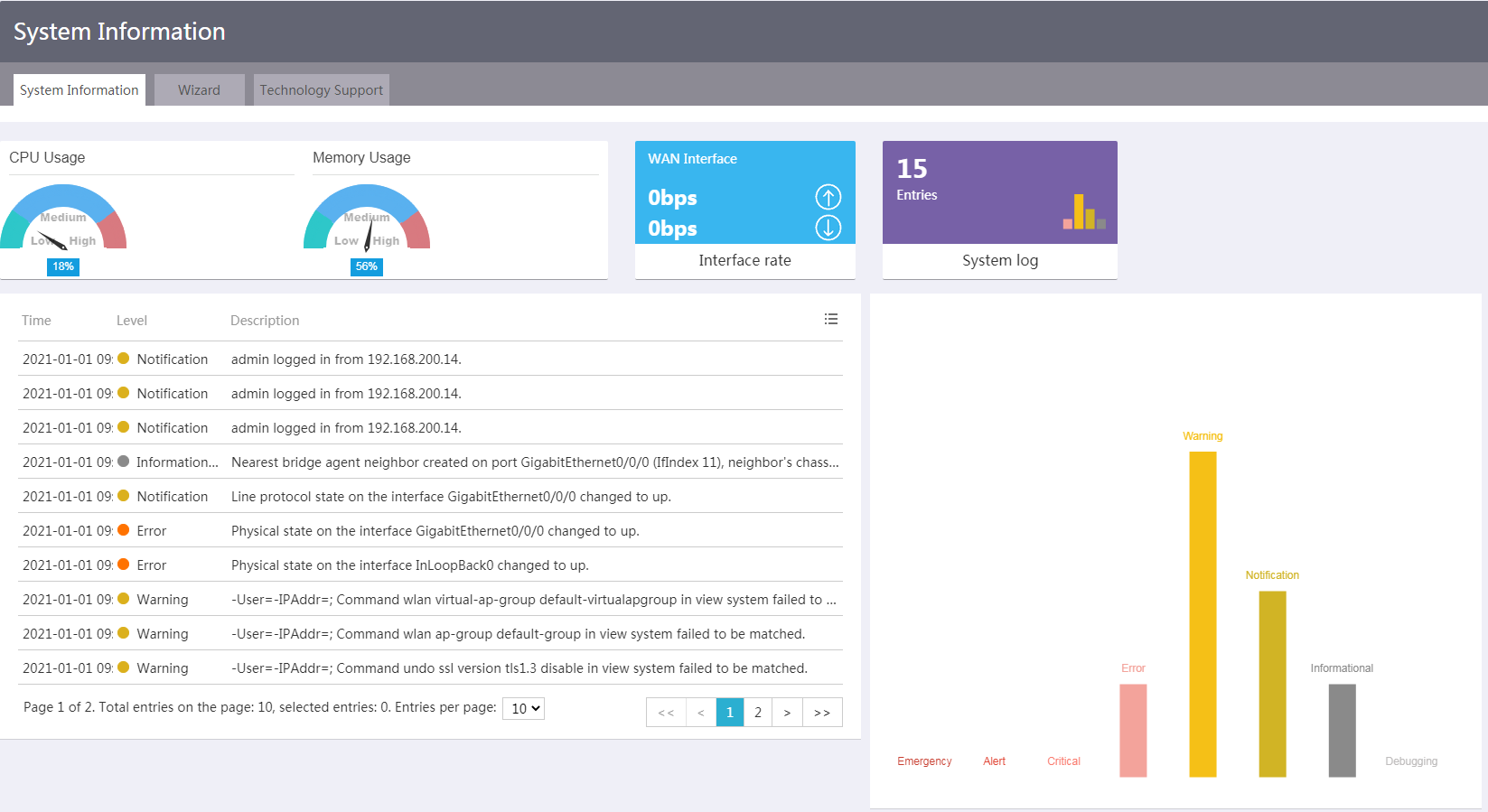
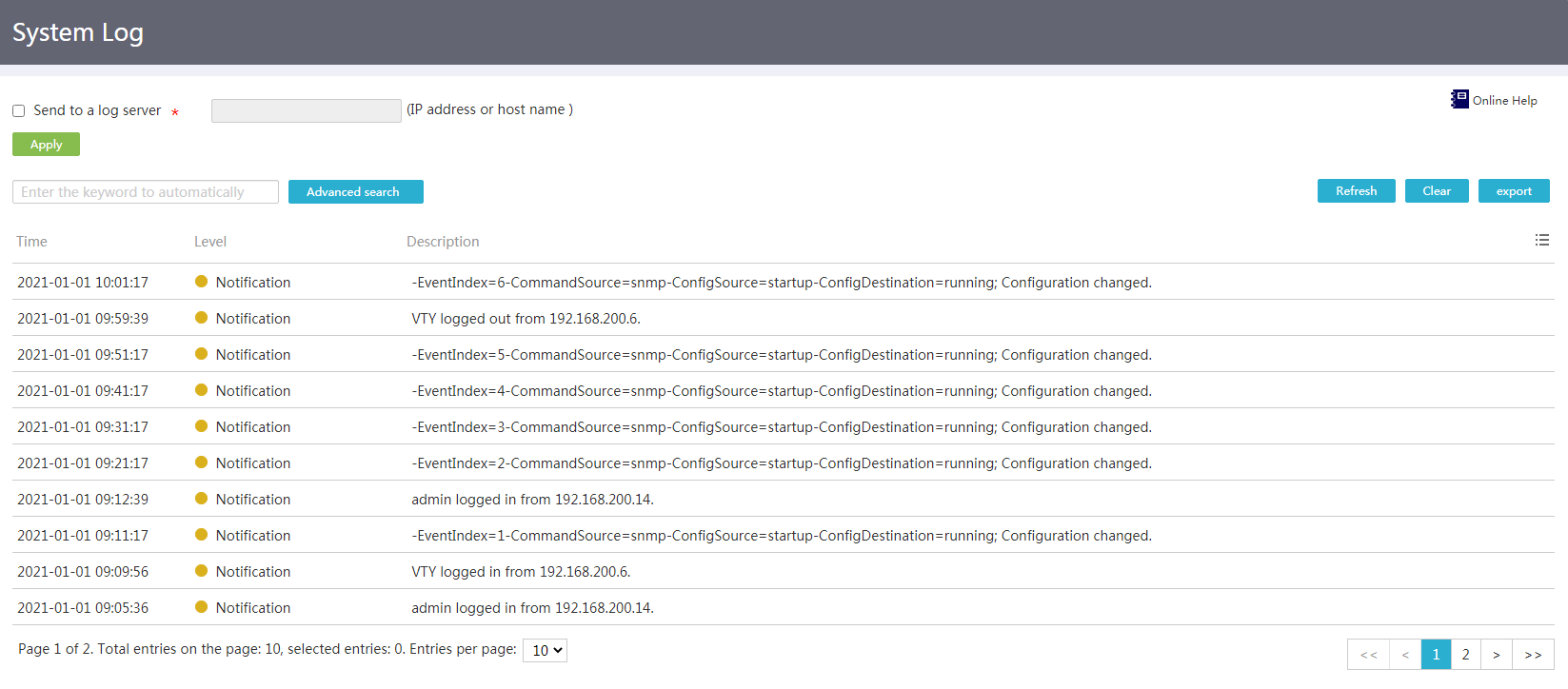
System log
Network configuration
Perform this task to view system log information of the device, including:
· Log information of the device.
· Log statistics.
Procedure
1. From the navigation pane, select System Information.
2. Click the System log area.
Figure 3 Viewing system log
Device information
Network configuration
Perform this task to view device information, including the system time and device model.
Procedure
1. From the navigation pane, select System Information.
2. In the System Time area, you can view the system time and up time of the device. In the Device Model area, you can view the device model, serial number, Boot RoM version, hardware version, and software version.
Interface status
Network configuration
Perform this task to view WAN interface status and LAN interface status.
Procedure
1. From the navigation pane, select System Information.
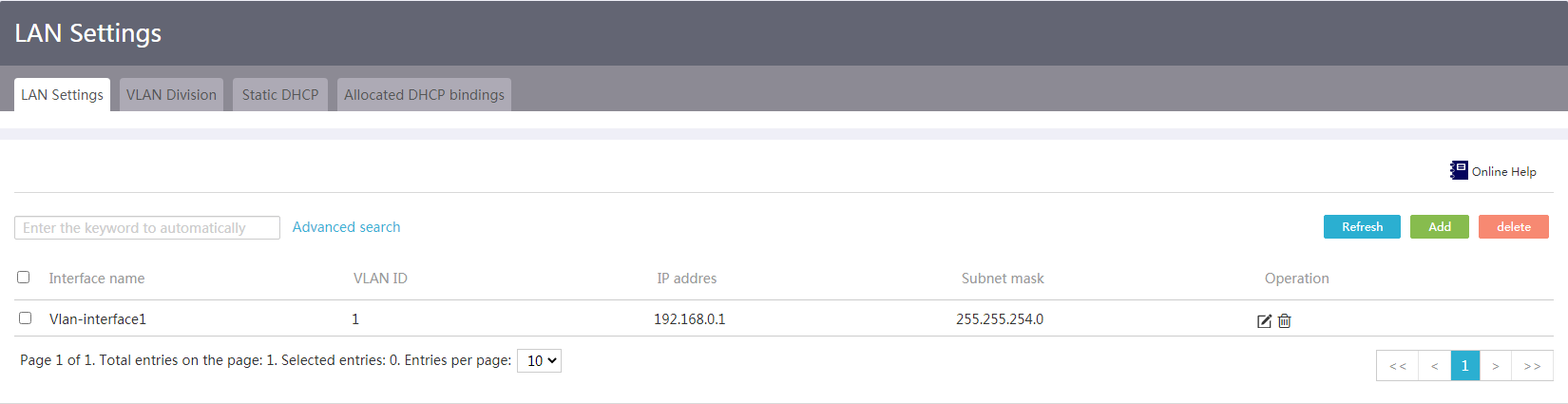
2. To view information about a WAN interface or LAN interface, click the interface icon in the Interface Status area to enter the WAN settings page or LAN settings page.
Figure 4 LAN Settings page
Storage medium
Network configuration
Perform this task to view the storage space usage of the storage medium.
Procedure
1. From the navigation pane, select System Information.
2. In the lower right corner of the page, you can view the storage space usage of the storage medium.
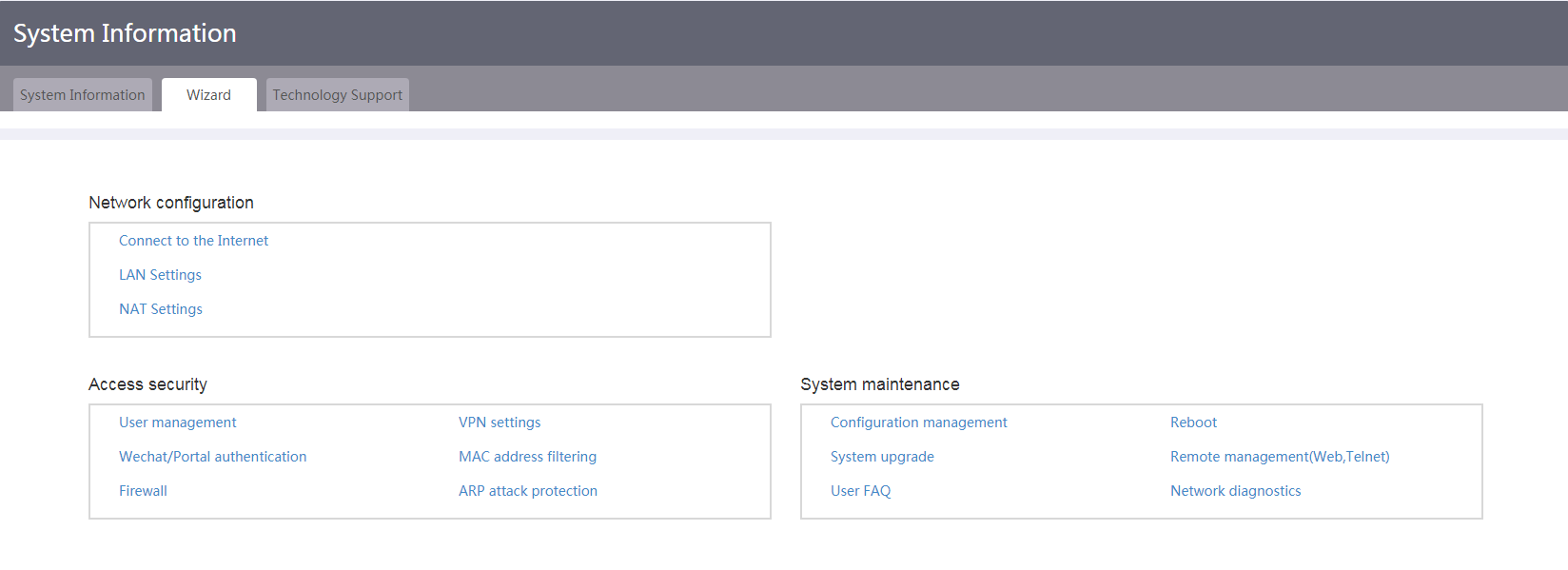
Use the wizard
To configure network settings quickly from the wizard:
1. From the navigation pane, select System Information.
2. Click the Wizard tab.
3. Click links to configure the following settings as needed:
¡ Network configuration:
- Connect to the Internet—Click the Connect to the Internet link to go to the WAN Settings page.
- LAN Settings—Click the LAN Settings link to go to the LAN Settings page.
- NAT Settings—Click the NAT Settings link to go to the NAT Settings page.
¡ Access security:
- User management—Click the User management link to go to the User Management > User Settings page.
- VPN settings—Click the VPN settings link to go to the IPsec VPN > IPsec policy page.
- Wechat/Portal authentication—Click the Wechat/Portal authentication link to go to the Portal Authentication > Authentication Settings page.
- MAC address filtering—Click the MAC address filtering link to go to the MAC Address Filter > MAC Filter Setting page.
- Firewall—Click the Firewall link to go to the Firewall page.
- ARP attack protection—Click the ARP attack protection link to the dynamic ARP learning settings page.
¡ System maintenance:
- Configuration management—Click the Configuration management link to go to the View Config page
- Reboot—Click the Reboot link to go to the Reboot now page.
- System upgrade—Click the System upgrade link to go to the Upgrade page.
- Remote management(Web,Telnet)—Click the Remote management(Web,Telnet) link to go to the Remote Login > Ping page.
- User FAQ—Click the User FAQ link to go to the User FAQ page.
- Network diagnostics—Click the Network diagnostics link to go to the Diagnostics > Tracert page.
Figure 5 Using the wizard
Obtain technology support
If you experience an issue using the product, you can obtain technology support in any of the following ways, as shown in Figure 6:
· Hotline: 400-810-0504.
· Email: [email protected].
· Website: zhiliao.h3c.com.
· WeChat official account.
Fast configuration
Introduction to fast configuration
Through fast configuration, you can fast complete basic WAN settings and LAN settings. Then, users in the LANs can access the WANs.
Configure WAN settings
Network configuration
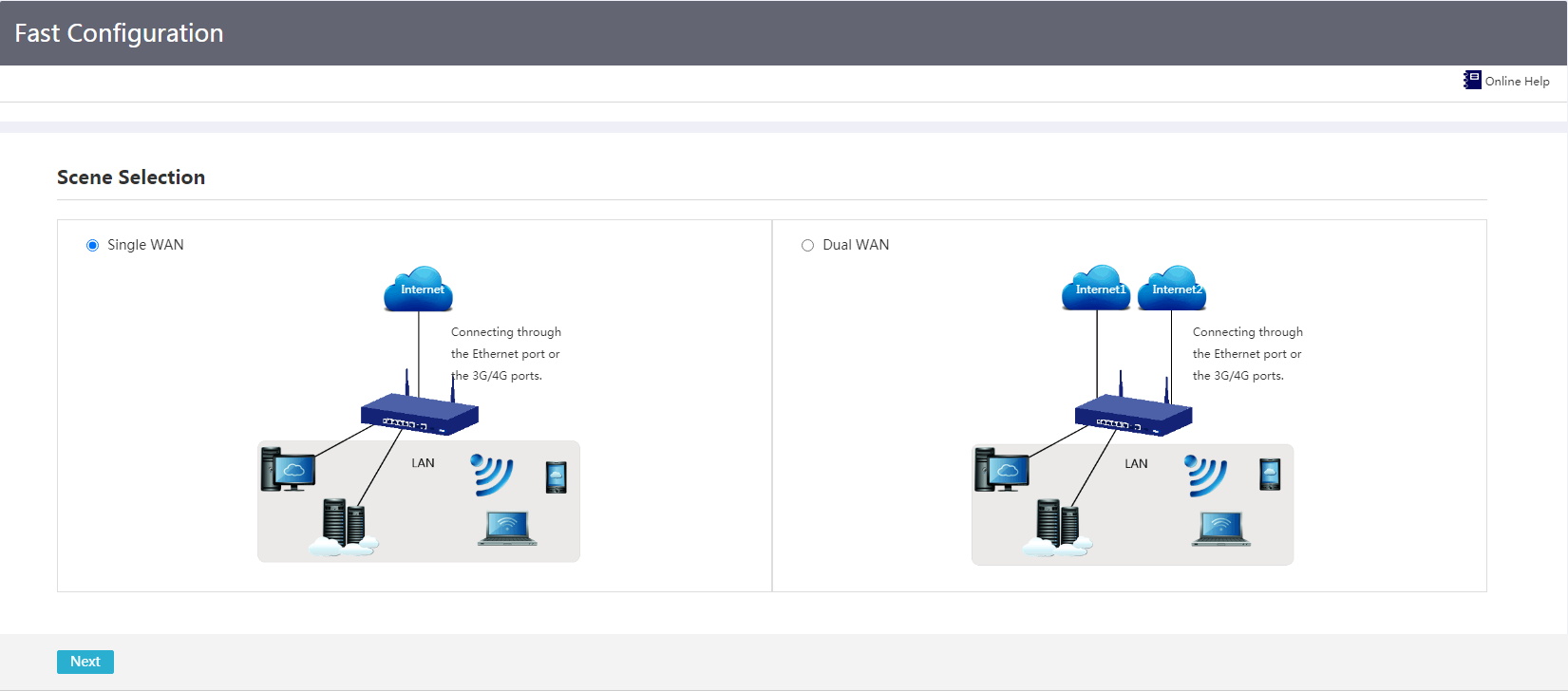
The device supports the following WAN access scenarios:
· Single-WAN—If the user leases only one operator network, select the single-WAN scenario.
· Dual-WAN—If the user leases two operator networks, select the dual-WAN scenario.
The configuration procedure is the same for both scenarios.
Connect to a WAN through a physical interface
1. From the navigation pane, select Fast Configuration.
2. Select the single-WAN and dual-WAN scenario as needed, and set the WAN access parameters.
Figure 7 Fast configuration: Selecting a scenario
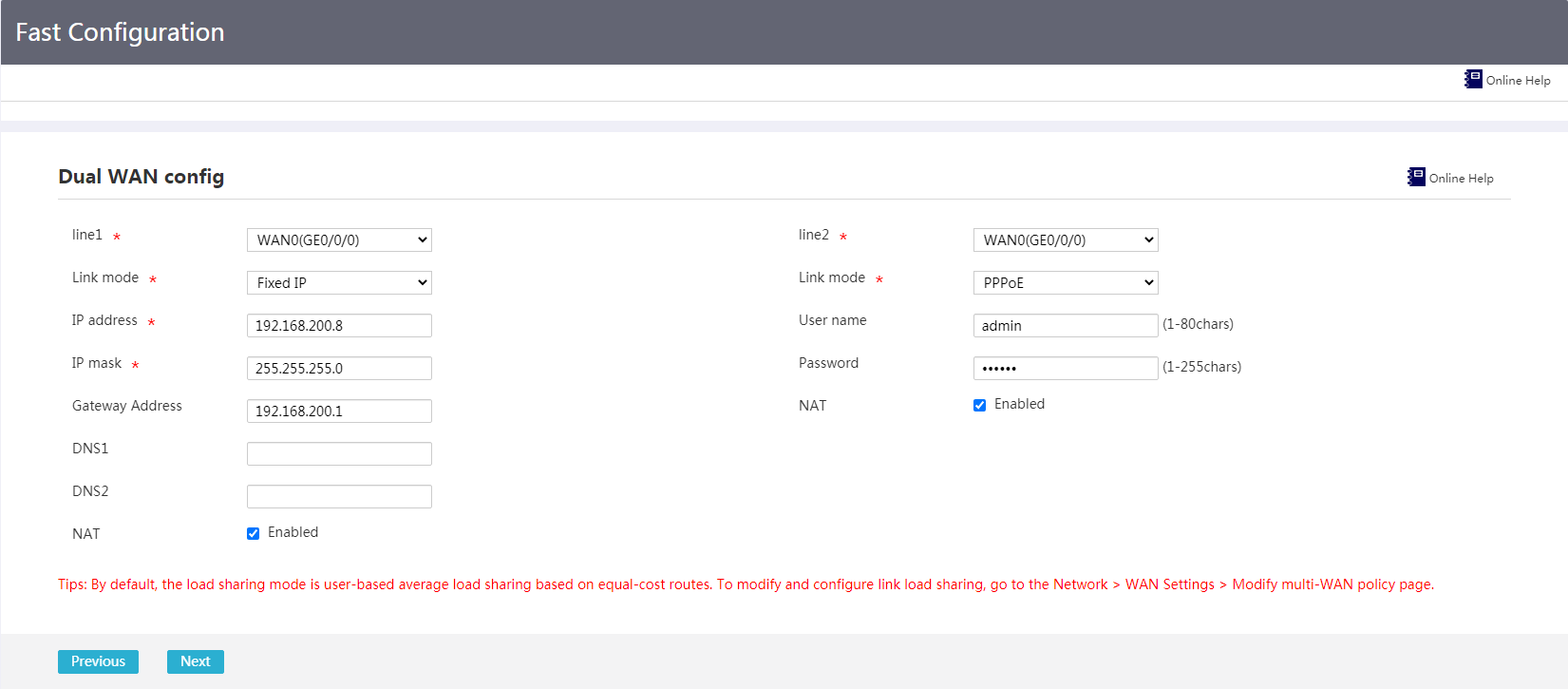
3. From the Line 1 or Line 2 list, select the physical interface WANx for accessing the WAN.
4. From the Link mode list, select a link mode as needed.
¡ If you select the PPPoE link mode, perform the following tasks:
- In the Username field, enter the PPPoE access username provided by the operator.
- In the Password field, enter the PPPoE access password provided by the operator.
¡ If you select the DHCP link mode, the DHCP server automatically assigns the public IP addresses for accessing the WAN.
¡ If you select the fixed IP link mode, perform the following tasks:
- In the IP address field, enter the fixed IP address for accessing the WAN.
- In the IP mask field, enter the mask or mask length for the IP address, for example, 255.255.255.0 or 24.
- In the Gateway address field, enter the gateway address for accessing the WAN.
- In the DNS1 and DNS2 fields, enter the IP addresses for DNS servers for accessing the WAN. The device preferentially uses DNS server DNS1 for domain name translation. If DNS server DNS1 fails to translate a domain name, DNS server DNS2 is used.
5. For the NAT field, select whether to enable NAT.
Enable NAT when multiple devices in the LAN share one public IP.
6. Click Next to complete WAN settings.
Figure 8 Fast configuration: Dual-WAN configuration
Configure LAN settings
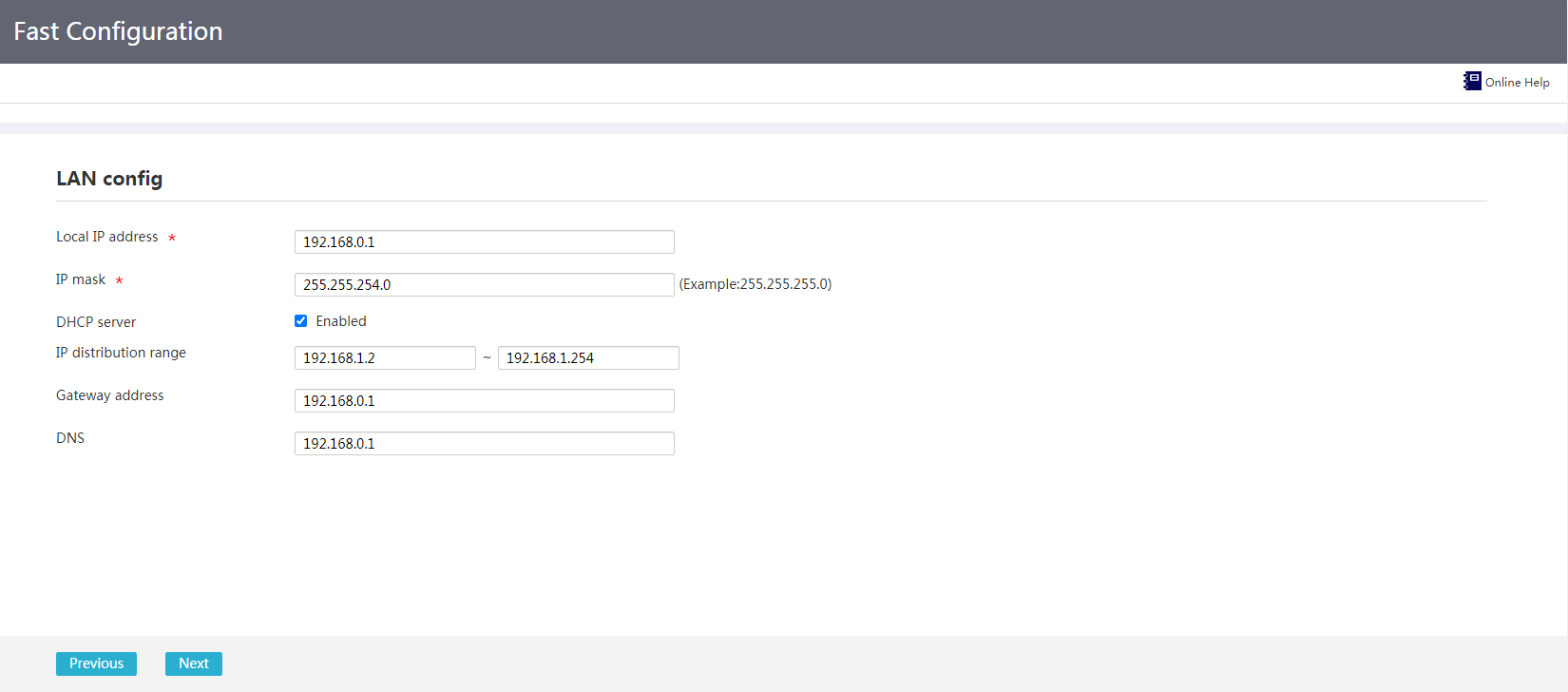
After WAN settings are completed, the LAN settings page opens.
1. In the Local IP address field, enter the IP address used by the device in the LAN.
2. In the IP mask field, enter the mask or mask length for the IP address, for example, 255.255.255.0 or 24.
3. For the DHCP server field, select Enabled as needed. For the device to act as the DHCP server and allocate IP addresses to hosts in the LAN, select Enabled.
¡ After selecting Enabled, perform the following tasks:
- In the IP distribution range field, enter the start IP address and end IP address of the IP addresses to be allocated.
- In the Gateway address field, enter the gateway address that the device allocates to DHCP clients.
- In the DNS field, enter the DNS server IP address that the device allocates to clients.
¡ If you do not select Enabled, DHCP will not be enabled on the device.
4. Click Next to complete LAN settings.
Figure 9 Fast configuration: LAN configuration
Network
WAN settings
Introduction to WAN settings
A wide area network (WAN) provides telecommunication services over a large geographical area. The Internet is a huge WAN network.
Generally, a device provides multiple WAN interfaces for WAN network access.
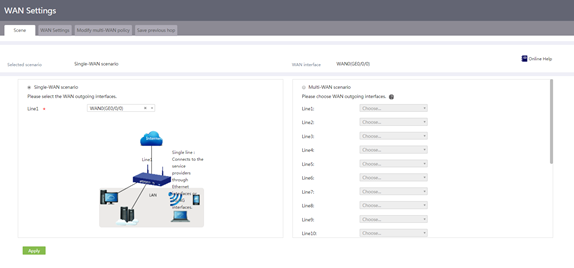
Select a scenario
About this task
The device supports the following WAN access scenarios:
· Single-WAN scenario—Select this scenario if your network service is provided by only one Internet service provider.
· Multi-WAN scenario—Select this scenario if your network service is provided by two Internet service providers.
The configuration procedures for both scenarios are the same.
Procedure
1. From the navigation pane, select Network > WAN Settings.
The Scene tab is displayed by default.
2. Select Single-WAN scenario or Multi-WAN scenario as needed.
3. Click Apply.
Figure 10 Selecting a scenario
Configure WAN settings
About this task
You can use a physical interface to access the WAN network.
Procedure
1. From the navigation pane, select Network > WAN Settings.
2. Click the WAN Settings tab.
Figure 11 WAN settings
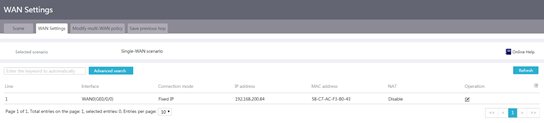
3. Click the edit icon for a line.
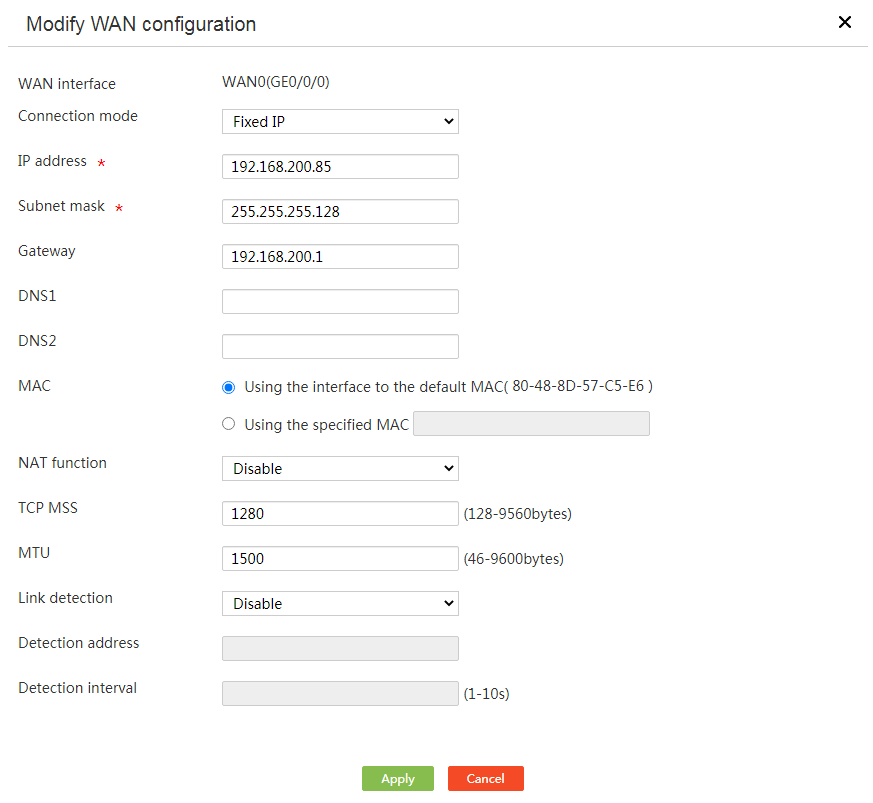
4. Select a connection mode. Options include PPPoE, DHCP, and Fixed IP.
¡ If you select PPPoE, configure the following parameters:
- In the User ID field, enter the username provided by the service provider.
- In the User password field, enter the password provided by the service provider.
- Select Always online for Online mode.
¡ If you select DHCP, the device will obtain a public IP address from the DHCP server for WAN access.
¡ If you select Fixed IP, configure the following parameters:
- In the IP address field, enter the fixed IP address.
- In the Subnet mask field, enter the subnet mask or subnet mask length, for example, 255.255.255.0 or 24.
- In the Gateway field, enter the gateway IP address.
- In the DNS1 and DNS2 fields, enter IP addresses of the primary DNS server and secondary DNS server, respectively. If the primary DNS server fails domain name resolution, the secondary DNS server is used.
5. Select Using the interface to the default MAC (XX-XX-XX-XX-XX-XX) or Using the specified MAC for MAC.
If you select Using the specified MAC, enter a MAC address. If you use an IP address assigned by the Internet service provider for WAN network access, configure a static MAC address.
6. Select whether to enable NAT.
Enable this feature if multiple devices on the LAN network share the same public IP address.
7. In the TCP MSS field, enter a MSS value.
8. In the MTU field, enter an MTU value.
9. Select whether to enable link detection.
This feature improves the link availability by detecting the link status to the specified IP address. If you enable this feature, configure the following parameters:
¡ In the Detection address field, enter an IP address for link detection.
¡ In the Detection interval field, enter the link detection interval.
10. Click Apply.
Figure 12 Modifying WAN configuration
Modify multi-WAN policy
Restrictions and guidelines
This task is supported only in a multi-WAN scenario.
Procedure
1. From the navigation pane, select Network > WAN Settings.
2. Click the Modify Multi-WAN policy tab.
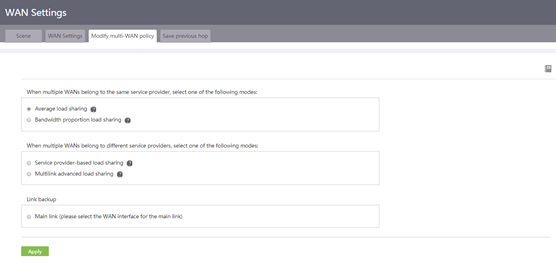
3. Modify the multiple-WAN policy as follows:
¡ If multiple WANs belong to the same service provider, select Average load sharing or Bandwidth proportion load sharing.
- If the service provider provides the same bandwidth for all links, select Average load sharing.
- If link bandwidths are different, select Bandwidth proportion load sharing.
¡ If multiple WANs belong to different service providers, select Service provider-based load sharing or Multilink advanced load sharing.
- If each service provider provides the same link bandwidth, select Service provider-based load sharing.
- If link bandwidths are different, select Multilink advanced load sharing.
You must select a service provider for each link no matter which load sharing mode is used.
¡ To ensure network stability, back up links as follows:
- Select Main link (please select the WAN interface for the main link), and then select a line.
- Select Backup link (please select the WAN interface for the backup link), and then select a line.
Make sure the lines for the main and backup links are different.
4. Click Apply.
Figure 13 Modifying multi-WAN policy
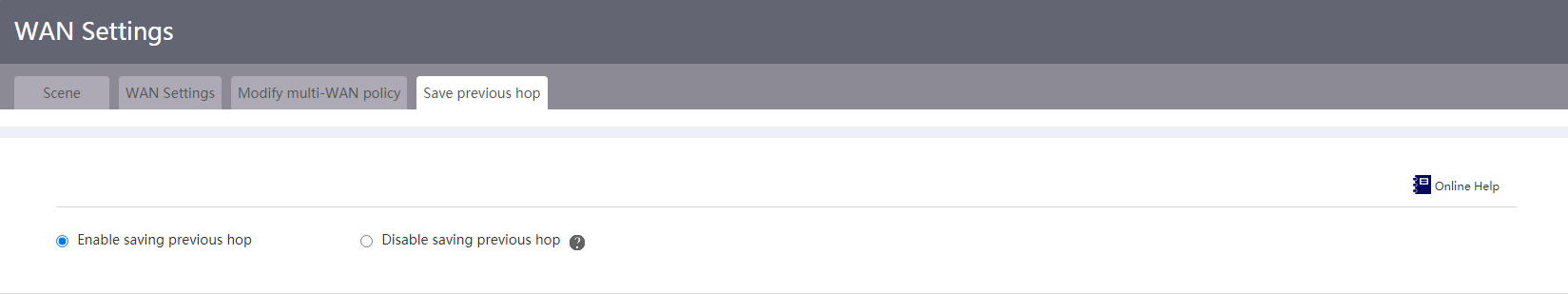
Save previous hop
1. From the navigation pane, select Network > WAN Settings.
2. Click the Save previous hop tab.
3. Select whether to enable saving the previous hop.
In a multi-WAN scenario, enable this feature to ensure that the packets originated from or destined for the LAN network is forwarded through the same WAN interface.
Figure 14 Saving previous hop
LAN settings
Introduction to LAN settings
Perform this task to configure a LAN interface for connecting to the internal network, enable DHCP, and assign the interface to VLANs.
DHCP is a LAN protocol mainly used for allocating IP addresses to hosts in a LAN. DHCP supports the following allocation mechanisms:
· Dynamic allocation—Configure this feature on an interface. This feature dynamically assigns IP addresses to hosts. After the lease of an IP address expires or an IP address is explicitly rejected by a host, the IP address can be used by another host. This allocation mechanism applies if you want to assign an IP address to a host for a limited period of time.
· Static allocation—Static IP addresses are not bound to interfaces, and they are bound to the host NIC MAC addresses. A static IP address can be used permanently. This allocation mechanism applies if you want to assign an IP address to a host permanently.
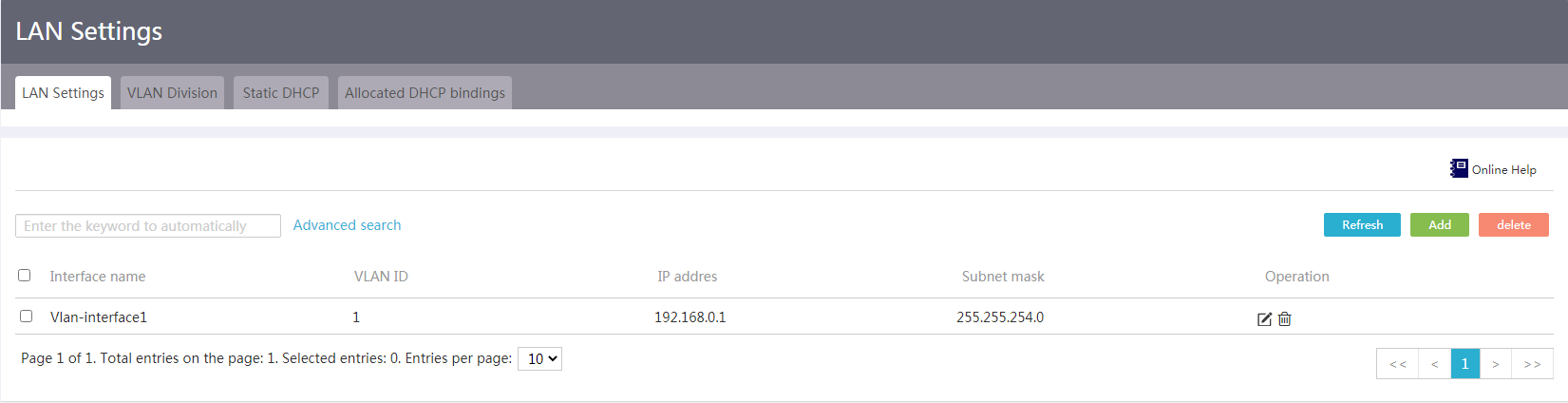
Configure LAN interface settings
Network configuration
Perform this task to configure an IP address for a GE interface connecting to the internal network or create a VLAN and its VLAN interface.
Procedure
1. From the navigation pane, select Network > LAN Settings.
2. Click the LAN Settings tab.
Figure 15 LAN settings
3. Click Add.
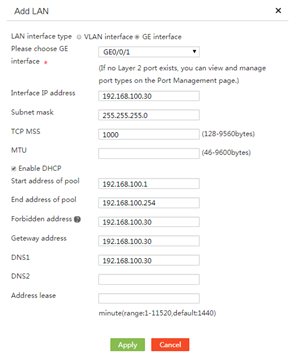
4. In the LAN interface type field, select an interface type.
¡ If you select VLAN interface, enter a VLAN ID to create a VLAN and its VLAN interface.
¡ If you select GE interface, select a GE interface.
5. In the Interface IP address field, enter an IP address for the interface.
6. In the Subnet mask field, enter the mask or mask length for the IP address, for example, 255.255.255.0 or 24.
7. In the TCP MSS field, configure the maximum segment size (MSS) of TCP packets for the interface.
8. In the MTU field, enter the MTU for the interface.
9. For the device to dynamically allocate IP addresses to connected clients (for example, computers), select Enable DHCP to enable DHCP on the device.
10. Click Apply.
Figure 16 Adding a LAN interface
Configure VLANs
Network configuration
Assign the LAN interfaces on the device to the specified VLAN, so that hosts in the same VLAN can communicate and hosts in different VLANs cannot directly communicate.
Restrictions and guidelines
When you configure a VLAN as the PVID for an interface on the detailed port configuration page, make sure the VLAN has already been created.
|
|
NOTE: The PVID identifies the default VLAN of a port. Untagged packets received on a port are considered as the packets from the PVID. |
Prerequisites
Plan the VLANs to which each LAN interface belongs on the device, and create the corresponding VLAN interface on the LAN interface configuration page.
Procedure
1. From the navigation pane, select Network > LAN Settings.
2. Click the VLAN Division tab.
Figure 17 VLAN division
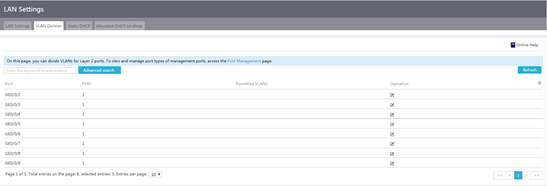
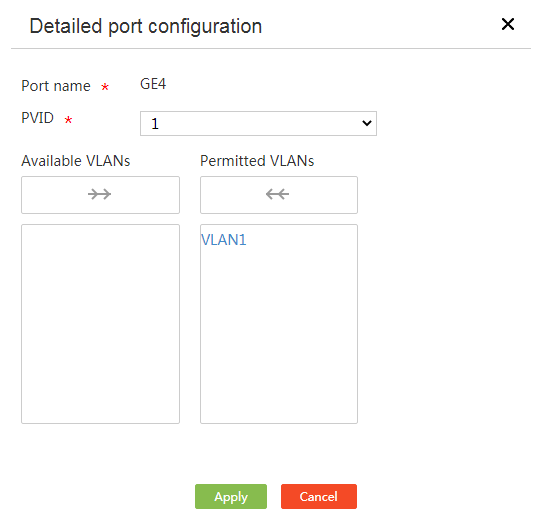
3. In the interface list, click the Edit icon for an interface. The detailed port configuration page opens.
4. In the PVID field, enter a PVID for the interface.
5. To assign an interface to or remove an interface from a VLAN:
¡ Click a VLAN ID in the available VLAN list to assign the interface to the VLAN, or click the rightward arrow icon above the available VLAN list to assign the interface to all available VLANs.
¡ Click a VLAN ID in the permitted VLAN list to remove the interface from the VLAN, or click the leftward arrow icon above the permitted VLAN list to remove the interface form all selected VLANs.
6. Click Apply.
Figure 18 Detailed port configuration
Enable DHCP on an interface
Network configuration
For the device to dynamically allocate IP addresses to clients (for example, computers) connected to the interface, enable DHCP on the interface.
Restrictions and guidelines
Make sure the address pool specified on the interface does not overlap with the WAN interface IP address range specified on the device.
Procedure
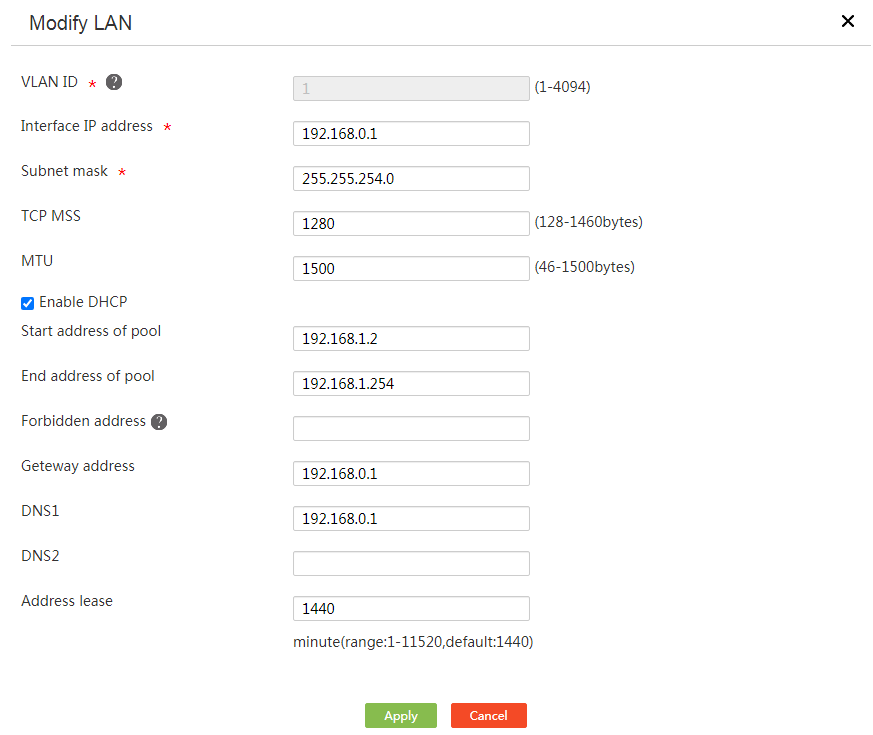
1. From the navigation pane, select Network > LAN Settings.
2. Click the LAN Settings tab.
3. Click the Edit icon for an interface.
4. Select the Enable DHCP option.
5. In the Start address of pool and End address of pool fields, specify the range of IP addresses that DHCP can allocate to clients.
6. In the Forbidden address field, specify the IP addresses that cannot be allocated to clients.
If some IP addresses in the address range (for example, the gateway address) cannot be allocated to clients, specify these addresses as forbidden addresses.
7. In the Gateway address, DNS1, and DNS2 fields, enter the IP addresses of the gateway, primary DNS server, and secondary DNS server, respectively.
8. In the Address lease field, enter the lease (in minutes) of IP addresses to be allocated. For example, to specify the lease of IP addresses as five days, enter 7200.
9. Click Apply.
Figure 19 Editing a LAN interface
Configure static DHCP
Network configuration
To assign fixed IP addresses to some clients, configure static DHCP to bind client MAC addresses to IP addresses.
Restrictions and guidelines
Make sure static client IP addresses are not contained in the WAN interface IP address range specified on the device.
Prerequisites
Enable DHCP on any interface. To use only static DHCP to allocate IP addresses, you also need to delete DHCP settings on the interface.
Procedure
1. From the navigation pane, select Network > LAN Settings.
2. Click the Static DHCP tab.
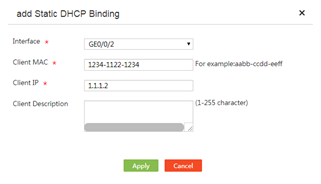
3. Click Add.
4. From the Interface list, select a DHCP-enabled interface.
5. In the Client MAC field, enter a client MAC address.
For a PC-type client, you can check the NIC information for its MAC address.
For a device-type client, execute the display interface command to obtain the MAC address of the interface.
6. In the Client IP field, enter the IP address to be allocated to the device.
7. Click Apply.
Figure 20 Creating a static DHCP binding
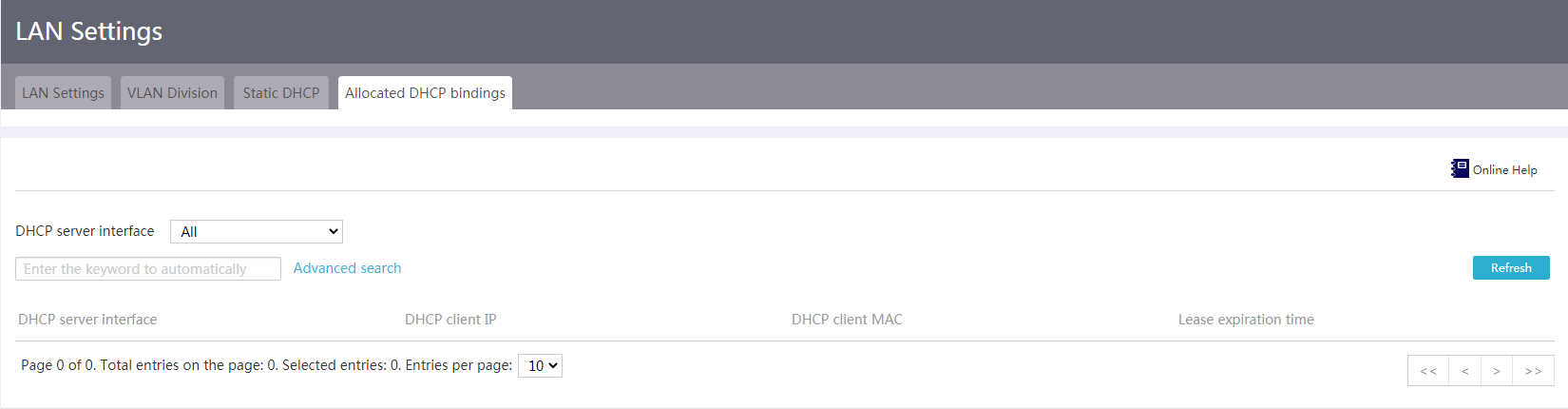
View allocated DHCP bindings
Prerequisites
After static or dynamic DHCP is configured on interfaces, you can view the IP addresses allocated to DHCP clients.
Procedure
1. From the navigation pane, select Network > LAN Settings.
2. Click the Allocated DHCP bindings tab.
3. Select an interface with DHCP server enabled from the DHCP server interface list to view the IP addresses assigned by the interface.
Figure 21 Allocated DHCP bindings
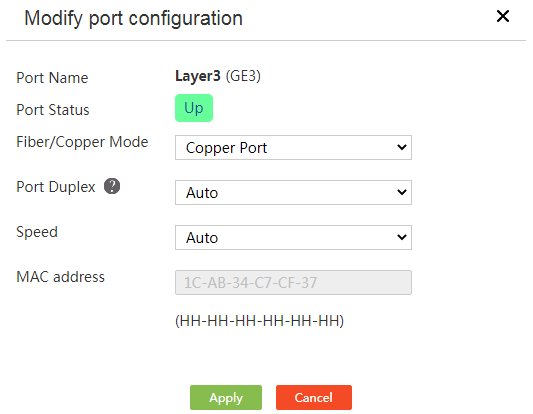
Port management
Introduction to port management
Port management allows you to view information about each physical port, including the port type, duplex mode, speed, and MAC address, change the physical status of ports, and modify the duplex mode and speed of ports.
Procedure
1. From the navigation pane, select Network > Port Management.
2. Click the toggle button in the Physical Status column to enable or disable a port.
Figure 22 Port management
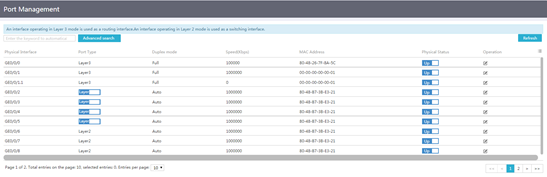
3. Click the Edit icon for a port.
4. Select a port mode from the Fiber/Copper Mode list.
5. Select a speed option from the Speed list.
6. View the MAC address of the port.
7. Click Apply.
Figure 23 Editing a port
NAT settings
Introduction to NAT
Network Address Translation (NAT) translates an IP address in the IP packet header to another IP address. It enables private hosts to access external networks and external hosts to access private network resources.
NAT supports the following address translation methods:
· Port mapping—Allows multiple internal servers (for example Web, mail, and FTP servers) to provide services to external hosts by using one public IP address and different port numbers. This method saves public IP address resources.
· One-to-one mapping—Creates a fixed mapping between a private address and a public address. Use this method for fixed network access requirements. This method is preferred if you need to use a fixed public IP address to access an internal server.
NAT provides the following advanced features:
· NAT hairpin—Allows internal users to access internal servers through NAT addresses. This feature is applicable if you want the gateway to control the internal user traffic destined for the internal server that provides services to external users through a public IP address.
· NAT ALG—If an application layer service (for example, FTP or DNS) exists between the internal and external networks, enable NAT ALG for this application layer protocol. It ensures that the data connection of this protocol can be correctly established after address translation.
Configure port mapping
1. From the navigation pane, select Network > NAT Settings.
Figure 24 NAT settings
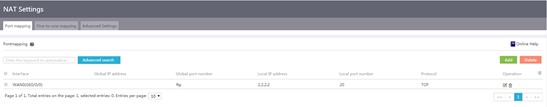
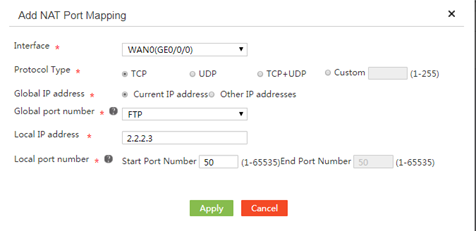
2. On the Port mapping tab, click Add.
3. Select the interface that connects to the Internet from the Interface list.
4. Select TCP, UDP, TCP+UDP, or Custom for Protocol Type.
Select the transport layer protocol that the internal server uses or enter a number that represents a transport layer protocol after selecting Custom. FTP servers use TCP and TFTP servers use UDP.
5. Select Current IP address or Other IP addresses for Global IP address.
6. Select FTP, Telnet, or User-defined ports from the Global port number list.
If the service provided by the internal server is not FTP or Telnet, enter the port number of the service, for example, port 80 for the HTTP server. If you have selected Custom for Protocol Type, this field cannot be configured.
7. In the Local IP address field, enter the private IP address of the internal server.
8. In the Local port number field, enter the port number of the internal server. If you have selected Custom for Protocol Type, this field cannot be configured.
9. Click Apply.
Figure 25 Adding a NAT port mapping
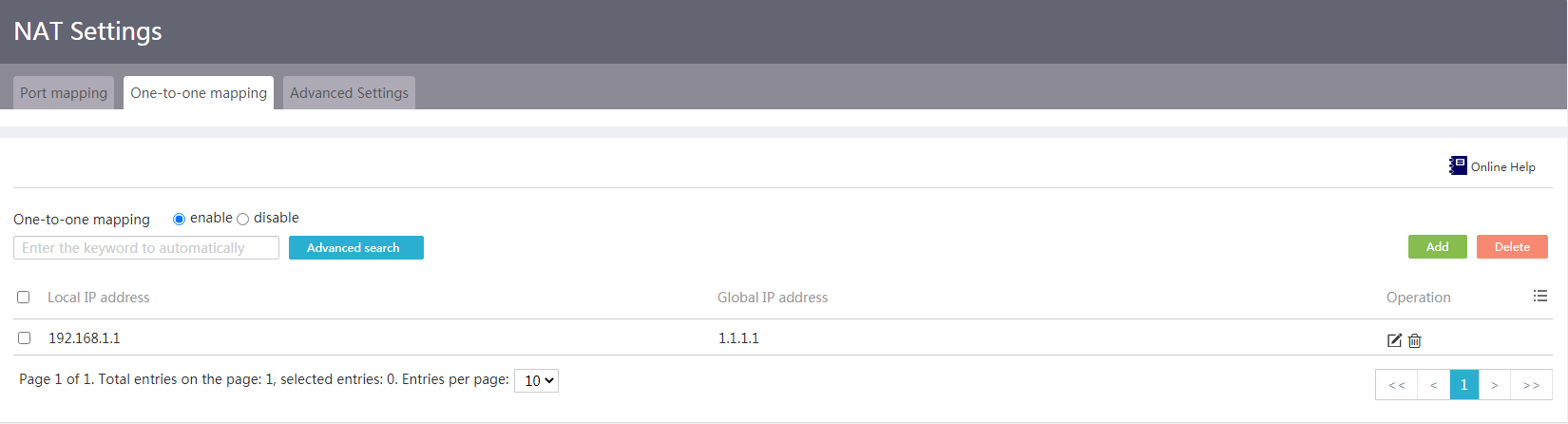
Configure one-to-one mapping
Prerequisites
Before you configure one-to-one mappings, select a WAN outgoing interface on the Network > WAN Settings > Scene page.
Restrictions and guidelines
As a best practice, do not configure a one-to-one mapping if the device has only one public IP address.
Procedure
1. From the navigation pane, select Network > NAT Settings.
2. Click the One-to-one mapping tab.
Figure 26 One-to-one mapping tab
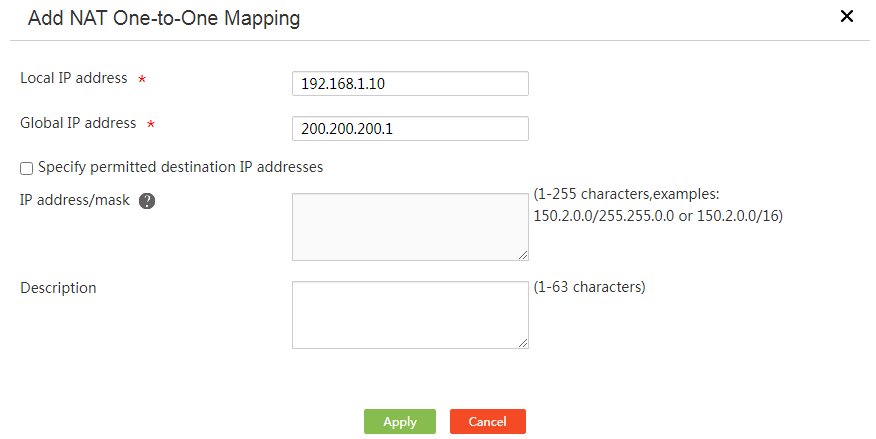
3. Click Add.
4. In the Local IP address field, enter an internal IP address.
5. In the Global IP address field, enter an external IP address.
6. Select Specify permitted destination IP addresses as required.
¡ If you select this option, enter destination IP addresses that can be accessed by internal users in the IP address/mask field. Address translation is performed on packets with the specified destination addresses.
¡ If you do not select this option, address translation is performed on all packets sent from the internal network to the external network.
7. Click Apply.
8. On the One-to-one mapping tab, select enable following OnetoOne mapping.
Figure 27 Adding a NAT one-to-one mapping
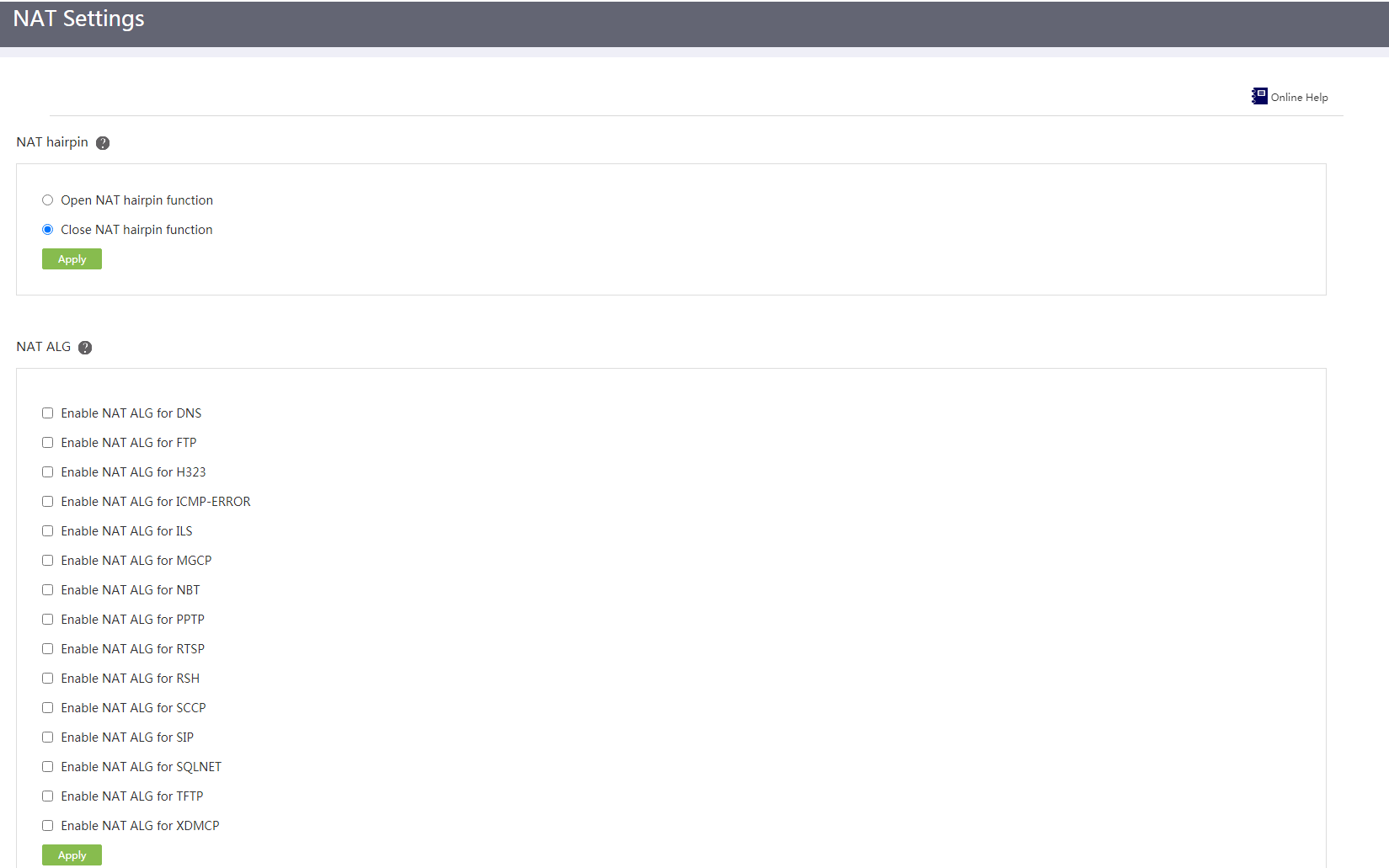
Configure NAT hairpin
Prerequisites
Before you configure NAT hairpin, configure a port mapping or one-to-one mapping.
Procedure
1. From the navigation pane, select Network > NAT Settings.
2. Click the Advanced Settings tab.
3. Select Open NAT hairpin function in the NAT hairpin area.
4. Click Apply.
Figure 28 Advanced settings-NAT hairpin
Configure NAT ALG
1. From the navigation pane, select Network > NAT Settings.
2. Click the Advanced Settings tab.
3. Enable NAT ALG for protocols.
4. Click Apply.
Figure 29 Advanced settings-NAT ALG
Network behavior management
User group
Introduction
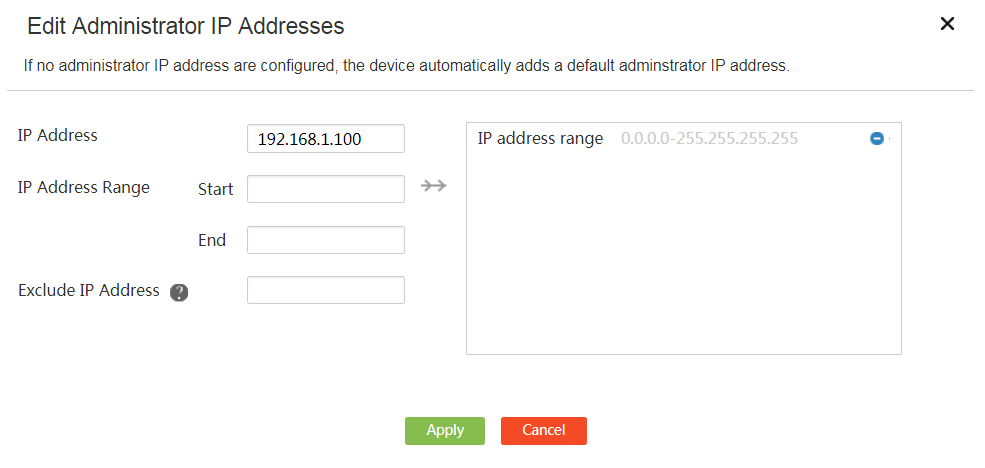
A user group is a group of host names or IP addresses. A user group can contain multiple members, and a member can be a host name, IP address, or IP address range. You can configure a user group to identify user packets for some services, such as bandwidth management.
Restrictions and guidelines
· The IP address member can only be an IPv4 address. IPv6 addresses are not supported.
· The start address in an IP address range must be lower than the end address.
Procedure
1. From the left navigation tree, select Network Behaviors> User Groups.
Figure 30 User groups
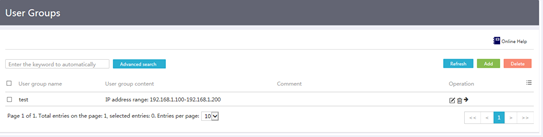
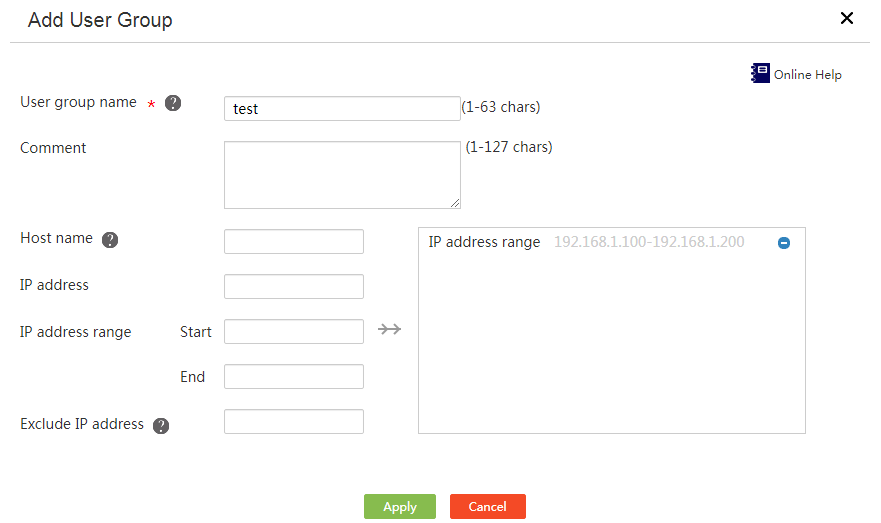
2. Click Add.
3. Enter a user group name in the User group name field.
4. Enter a user group description in the Comment field.
5. Configure members for the user group:
¡ Enter a host name to add to the user group.
¡ Enter an IP address to add to the user group.
¡ Enter a start address and an end address to specify an IP address range to add to the user group.
¡ Specify an IP address to exclude from the IP address range.
6. Click →→ to commit the configured members.
7. Repeat steps 5 and 6 to add multiple members of the same type.
8. Click Apply.
Figure 31 Adding a user group
Time range group
Introduction
If you want same features (for example, bandwidth management and network behavior management) to be effective only during a specific time period, you can configure a time range group and reference it for the related feature.
A time range group can contain multiple time ranges. The following types of time ranges are available:
· Periodic—Recurs periodically on a day or days of the week, for example, 8:00 to 12:00 every Monday.
· Absolute—Represents only a period of time and does not recur, for example, 8:00 on January 1, 2015 to 18:00 on January 3, 2015.
The active period of a time range group is calculated as follows:
· Combining all periodic statements.
· Combining all absolute statements.
· Taking the intersection of the two statement sets as the active period of the time range group.
Suppose you configure the following time ranges:
· Periodic time range: 08:30 to 12:00 and 13:30 to 18:00 on Monday through Friday.
· Absolute time range: 10:00 to 12:00 and 14:00 to 16:00 on April 1, 2015 through April 30, 2015.
The active period is 10:00 to 12:00 and 14:00 to 16:00 on Monday through Friday during April 1, 2015 through April 30, 2015.
Restrictions and guidelines
· You can create a maximum of 1024 time ranges, each with a maximum of 32 periodic time ranges and 12 absolute time ranges.
· You cannot configure the same time range group from both the CLI and the Web interface.
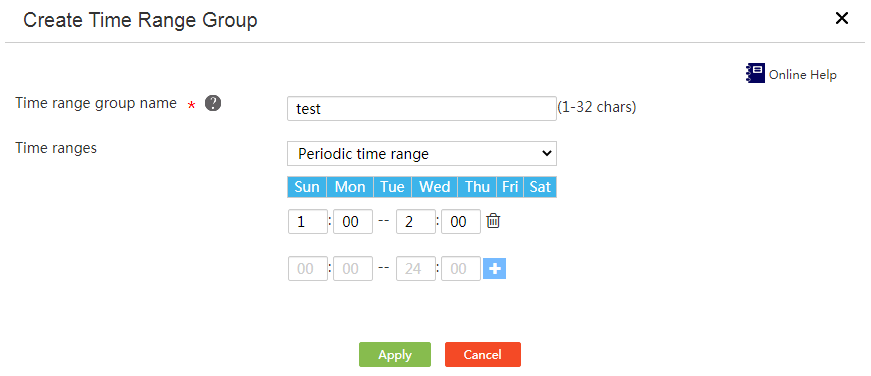
Configure a time range group with only one type of time ranges
Restrictions and guidelines
Perform this task to configure a time range group that contains only periodic or absolute time ranges.
Procedure
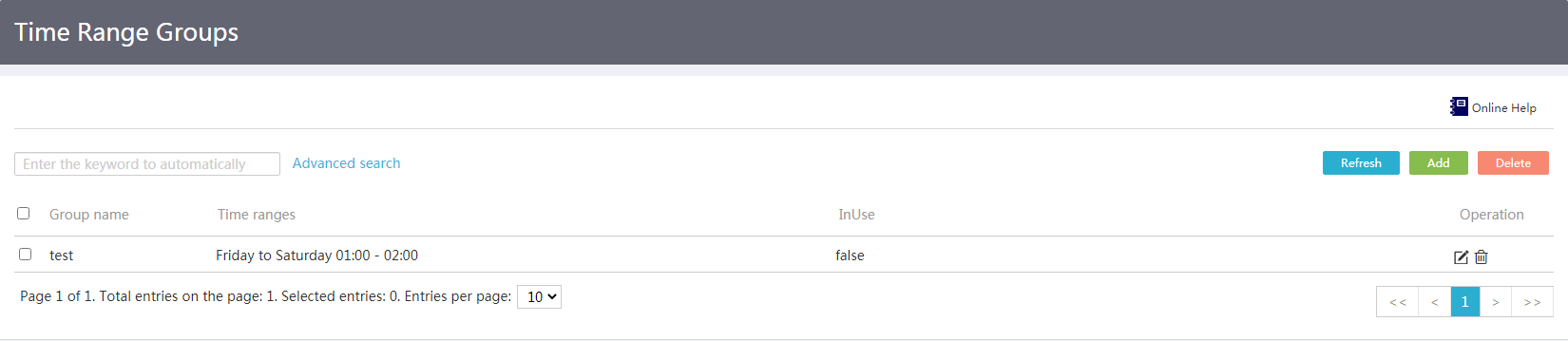
1. From the left navigation tree, select Network Behaviors> Time Range Groups.
Figure 32 Time range groups
2. Click Add.
3. Enter a time range group name in the Time range group name field.
4. From the Time ranges list, select Periodic time range or Absolute time range, and configure a periodic time range or absolute time range.
¡ To configure a periodic time range, select the days of the week, enter the start time and end time, and click the plus sign.
¡ To configure an absolute time range, select the start date and end date, enter the start time and end time, and click the plus sign.
5. Click Apply.
Figure 33 Configuring a time range group with only one type of time ranges
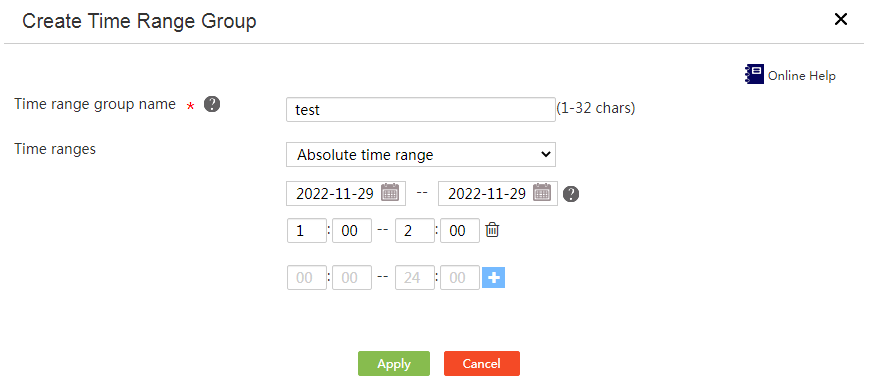
Configure a time range group that contains both periodic and absolute time ranges
Restrictions and guidelines
Perform this task to configure a time range group that contains both periodic and absolute time ranges.
Procedure
1. From the left navigation tree, select Network Behaviors> Time Range Groups.
2. Click Add.
3. Enter a time range group name in the Time range group name field.
4. Configure time ranges.
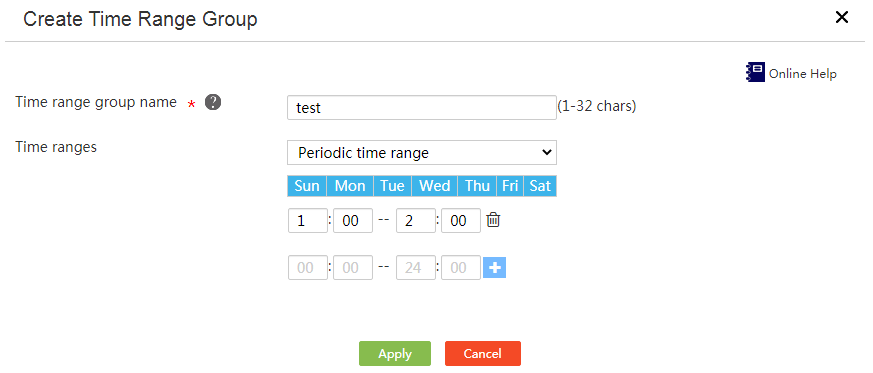
¡ Select Periodic time range from the Time ranges list. Select the days of the week, enter the start time and end time, and click the plus sign.
Figure 34 Configuring a periodic time range
¡ Select Absolute time range from the Time ranges list. Select the start date and end date, enter the start time and end time, and click the plus sign.
Figure 35 Configuring an absolute time range
5. Click Apply.
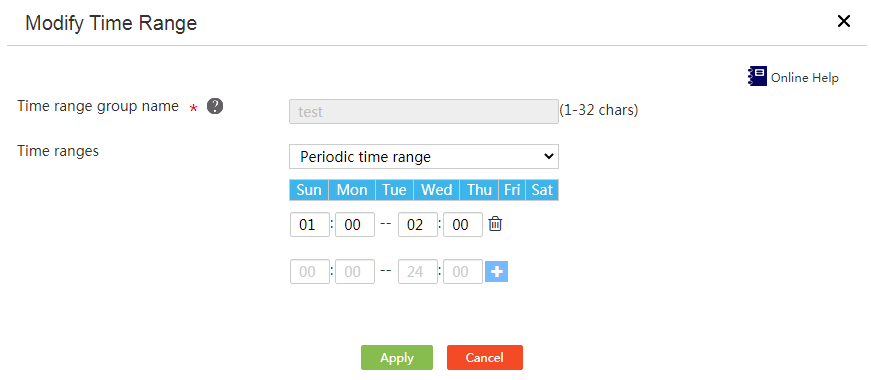
Edit a time range group
Restrictions and guidelines
Perform this task to remove periodic or absolute time ranges from a time range group that contains both periodic and absolute time ranges.
Procedure
1. From the left navigation tree, select Network Behaviors> Time Range Groups.
2. Click Edit in the Operation column for a time range group.
3. From the Time ranges list, select Periodic time range or Absolute time range.
4. Click the delete icon after each time range.
5. Click Apply.
Figure 36 Editing a time range group
Network security
Firewall
Introduction to the firewall feature
The firewall feature identifies packets based on security rules and takes actions to prevent illegal packets from entering the network.
Restrictions and guidelines
Specify priorities for security rules carefully. Security rules are matched in priority order. Once a matching security rule is found, the firewall takes the action specified by the rule.
Firewall settings take effect only on incoming traffic.
Prerequisites
Before configuring security rules, complete the following tasks:
· Configure WAN settings.
· Configure the time ranges to be used for the security rules.
Add a security rule
1. From the navigation pane, select Network Security > Firewall.
Figure 37 Security rules
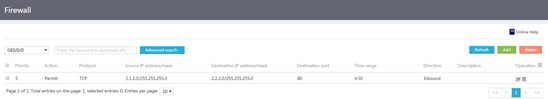
2. Click Add.
3. In the Interface field, select the interface to which you want to apply the security rule. The firewall will use the rule to match packets that arrive at the interface.
4. In the Protocol field, select the protocol that the target packets use.
¡ To match transport layer packets, select TCP or UDP.
¡ To match ping or tracert packets, select ICMP.
¡ To match packets of all protocols, select All protocols.
5. In the Source IP address/mask field, enter the IP address and mask of the packet sender. To match packets from all senders, enter any.
6. In the Destination IP address/mask field, enter the IP address and mask of the intended packet receiver. To match packets destined for all receivers, enter any.
7. In the Destination port field, enter the destination port number of the target packets, for example, 80 for HTTP packets.
8. In the Time range field, select the time range during which you want the rule to take effect.
9. In the Action field, select the action to be taken on target packets.
10. In the Priority field, perform one of the following tasks:
¡ For the system to assign the rule a priority, select Auto. The system assigns priorities to rules according to the rule configuration order. The priority numbering step is 5.
¡ To enter a priority value, select User-defined. A smaller value represents a higher priority.
11. In the Description field, enter a description for the rule.
12. Click Apply.
Figure 38 Adding a security rule

Attack defense
Introduction to attack defense
DDoS attacks are common on the Internet and can cause greater harm than traditional DoS attacks. This feature can protect your devices and network against the following types of attacks:
· Single-packet attacks—An attacker uses malformed packets to paralyze the target system. For example, in a LAND attack, the IP address of the target system is used as both the source IP address and destination IP address of TCP packets. The attacker sends those packets to exhaust connection resources of the target system and make the target system unable to process normal services.
· Abnormal flow attacks—Include the following types of attacks:
¡ Scanning attacks—In order to find a way to intrude into the target network, an attacker scans host addresses and ports to probe the target network topology and open ports.
¡ Flood attacks—An attacker sends a large number of forged requests to the target system. The system is too busy responding to these forged requests to provide services for legitimate users.
The device supports preventing the following DDoS attacks:
· Single-packet attacks—Fraggle attacks, LAND attacks, WinNuke attacks, TCP flag attacks, ICMP unreachable packet attacks, ICMP redirect packet attacks, Smurf attacks, IP source route attacks, IP record route attacks, and large ICMP packet attacks.
· Abnormal flow attacks—Scanning attacks, SYN flood attacks, UDP flood attacks, and ICMP flood attacks.
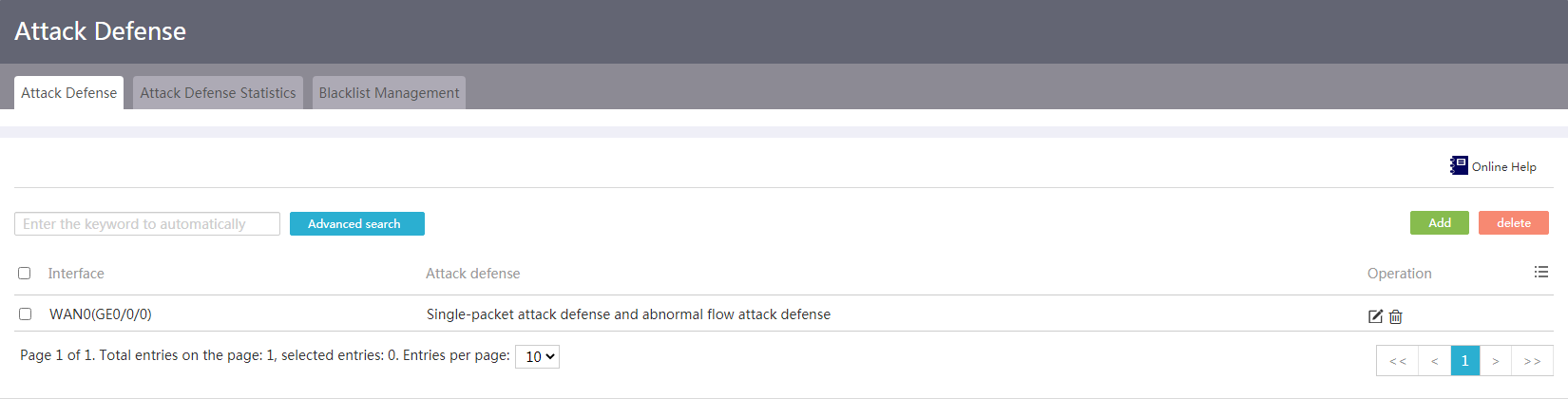
Configure attack defense
1. From the navigation pane, select Network Security > Attack Defense.
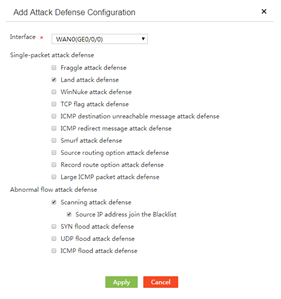
2. On the Attack Defense tab, click Add.
Figure 39 Attack defense
3. On the page that opens, configure attack defense as follows:
¡ From the Interface list, select an interface to which the attack defense configuration applies.
¡ Enable attack defense for single-packet attacks.
As a best practice, enable attack defense for all types of single-packet attacks.
¡ Enable attack defense for abnormal flow attacks.
After enabling scanning attack defense, you can select to add packet source IP addresses to the blacklist. The device drops packets with the matching source IP address. To view IP addresses added to the blacklist, access the Blacklist Management page.
As a best practice, enable flood attack defense based on the network traffic type.
4. Click Apply.
Figure 40 Adding an attack defense configuration entry
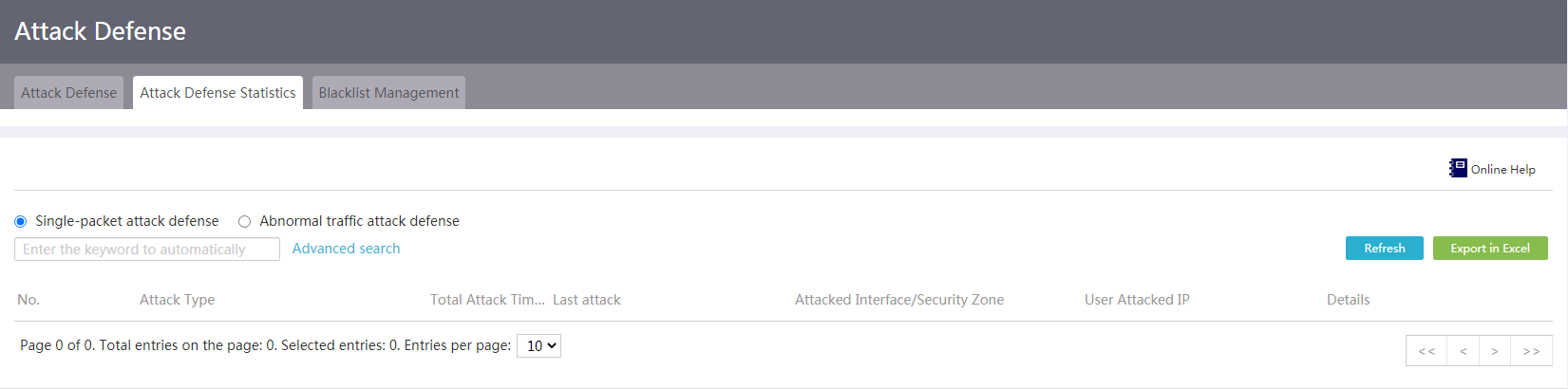
Attack defense statistics
Introduction
Use this feature to view details about DDoS attacks on the device, including the attack type, total attack times, time when the last attack occurred, attacked interface/security zone, and user attacked IP.
Procedure
1. From the navigation pane, select Network Security > Attack Defense.
2. Click the Attack Defense Statistics tab.
3. To view statistics about single-packet attacks, select Single-packet attack defense.
4. To view statistics about abnormal flow attacks, click Abnormal traffic attack defense.
5. To export the statistics, click Export in Excel.
Figure 41 Attack defense statistics
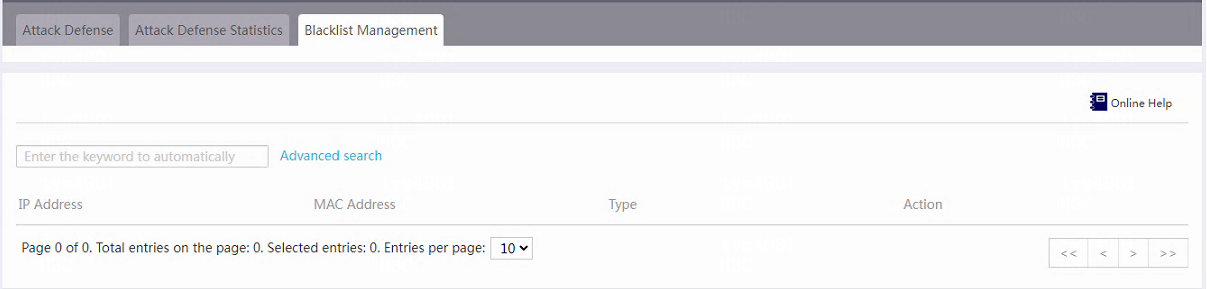
Blacklist management
Introduction
After enabling scanning attack defense, you can add source IP addresses to the blacklist. The device drops packets with the matching source IP address.
To view IP addresses added to the blacklist, navigate to the Blacklist Management page. This page records information about the blacklist, including the IP address added to the blacklist, MAC address, type, and action.
Procedure
1. From the navigation pane, select Network Security > Attack Defense.
2. Click the Blacklist Management tab.
3. To remove an IP address from the blacklist, click the delete icon in the Action column for the IP address.
Figure 42 Blacklist management
Connection limit
Introduction to connection limit
Use connection limit to limit per-IP connections for better resource allocation and attack prevention.
When the number of TCP or UDP connections from an IP address exceeds the connection limit, no connections from the IP address are permitted until the connection count falls below the connection limit.
You can configure the following connection limits:
· Network connection limits—Limit the number of connections from each IP address in an IP address range. This limit method is used to limit the total number of connections received on all interfaces from one IP address.
· VLAN-based network connection limits—Limit the number of connections from each IP address on a VLAN interface. This limit method is used to limit the number of connections received on one VLAN interface from one IP address.
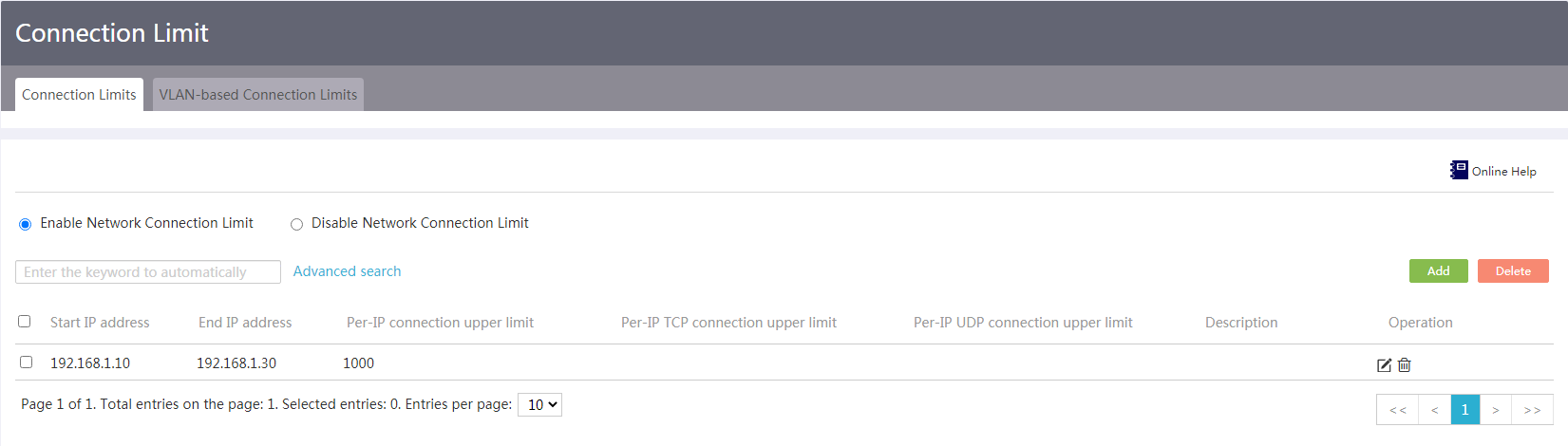
Configure network connection limits
1. From the navigation pane, select Network Security > Connection Limit.
2. On the Connection Limits tab, select Enable Network Connection Limit.
Figure 43 Network connection limit rules
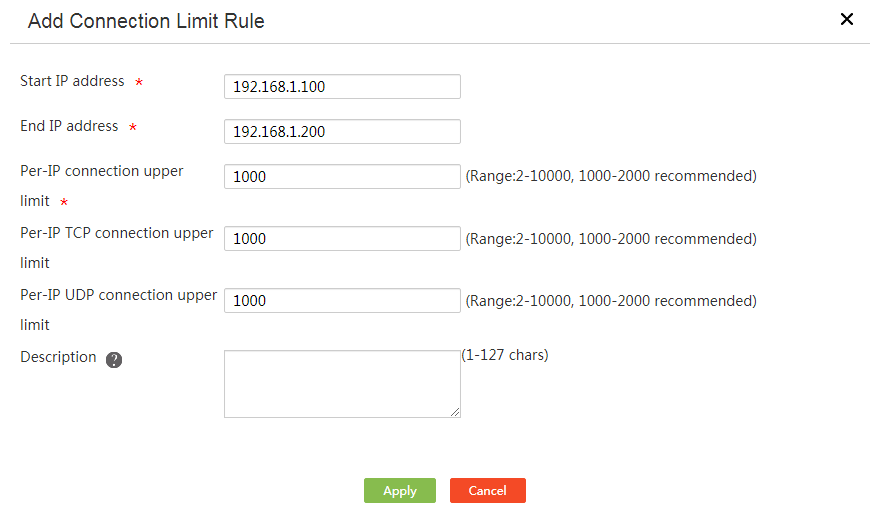
3. Click Add. The Add Connection Limit Rule page opens.
4. Enter a start IP address in the Start IP address field.
5. Enter an end IP address in the End IP address field.
6. Enter the total maximum number of TCP connections and UDP connections sourced from each IP address in the Per-IP connection upper limit field.
Connections with the same source IP address but a different source port number, destination IP address, destination port number, or protocol type are considered as different connections.
7. To limit TCP connections per IP address, enter the maximum number of TCP connections in the Per-IP TCP connection upper limit field.
The maximum number of TCP connections must be smaller than or equal to the total maximum number of TCP connections and UDP connections.
8. To limit UDP connections per IP address, enter the maximum number of UDP connections in the Per-IP UDP connection upper limit field.
The maximum number of UDP connections must be smaller than or equal to the total maximum number of TCP connections and UDP connections.
9. Enter a rule description in the Description field.
10. Click Apply.
Figure 44 Add/edit network connection limit rule
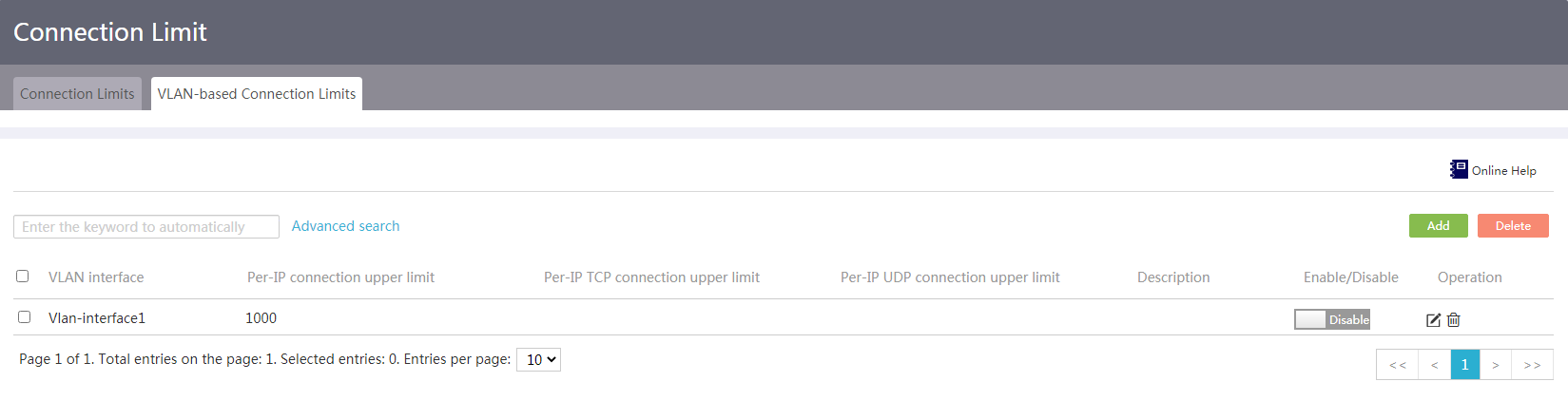
Configure VLAN-based network connection limits
1. From the navigation pane, select Network Security > Connection Limit.
2. Click the VLAN-based Network Connection Limits tab.
Figure 45 VLAN-based network connection limits
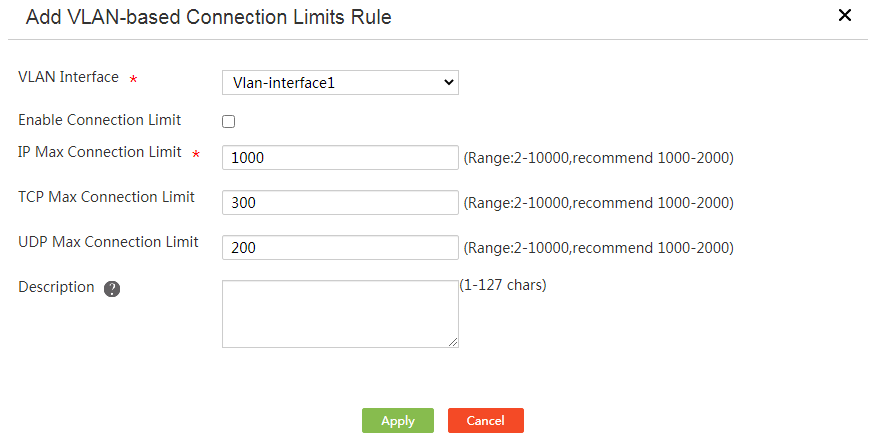
3. Click Add. The Add VLAN-based Connection Limits Rule page opens.
4. Select a VLAN interface from the VLAN Interface list.
5. Select Enable Connection Limit.
6. Enter the total maximum number of TCP and UDP connections sourced from each IP address in the IP Max Connection Limit field.
Connections with the same source IP address but a different source port number, destination IP address, destination port number, or protocol type are considered as different connections.
7. To limit TCP connections per IP address, enter the maximum number of TCP connections in the TCP Max Connection Limit field.
The maximum number of TCP connections must be smaller than or equal to the total maximum number of TCP connections and UDP connections.
8. To limit UDP connections per IP address, enter the maximum number of UDP connections in the UDP Max Connection Limit field.
The maximum number of UDP connections must be smaller than or equal to the total maximum number of TCP connections and UDP connections.
9. Enter a rule description in the Description field.
10. Click Apply.
Figure 46 Add VLAN-based network connection limits rule
MAC address filter
Introduction to MAC address filter
If you want to permit or deny packets sent by specific devices, you can configure MAC address filter on Layer 3 interfaces that connect to the devices.
MAC address filter filters packets that are sourced from specific MAC addresses.
· If whitelist is enabled, the device permits only packets that are sourced from the MAC addresses on the whitelist.
· If blacklist is enabled, the device drops only packets that are sourced from the blacklisted MAC addresses.
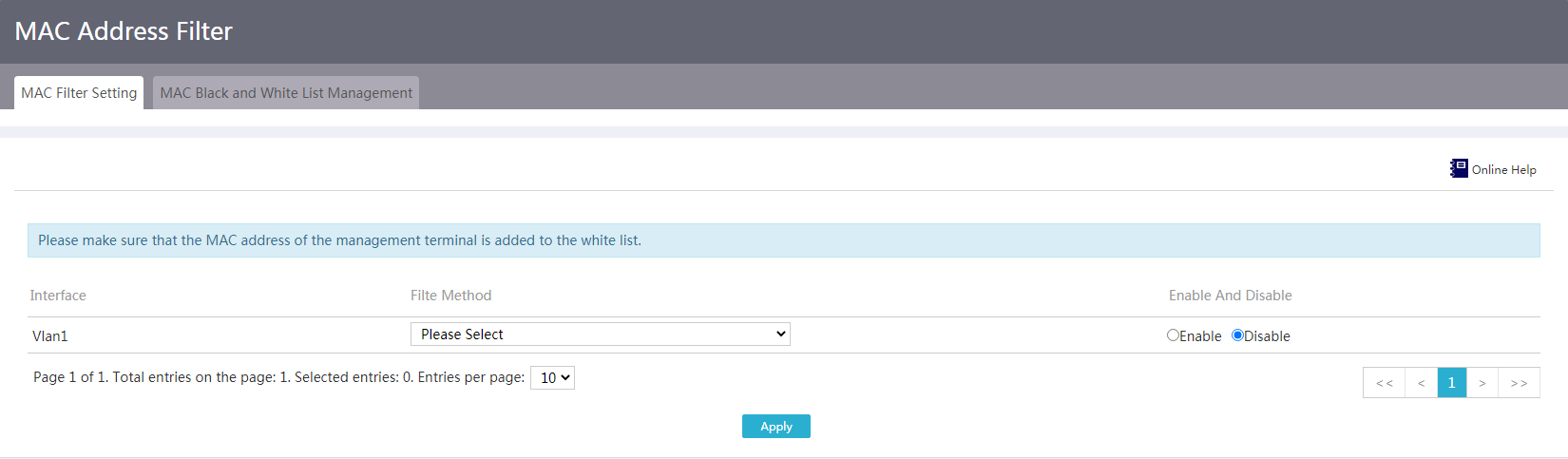
Configure a MAC address filter
Restrictions and guidelines
If you want to enable whitelist MAC address filter on the interface that connects to the management endpoint, make sure the MAC address of the management endpoint has already been added to the whitelist.
Procedure
1. From the navigation pane, select Network Security > MAC Address Filter.
2. Select Whitelist or Blacklist as the filtering method for the interface where you want to enable this feature, and click Enable.
3. Click Apply.
Figure 47 MAC filter settings
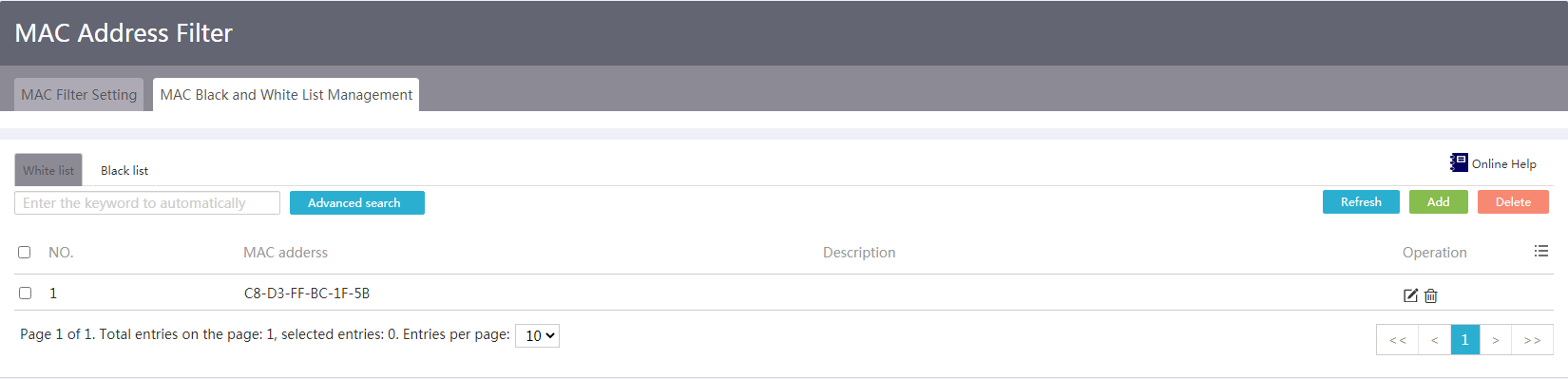
Add a whitelist or blacklist entry
Restrictions and guidelines
The MAC address whitelist and blacklist configuration steps are similar. The following procedure describes the MAC address whitelist configuration as an example.
Procedure
1. From the navigation pane, select Network Security > MAC Address Filter.
2. Click the MAC Black and White List Management tab.
3. On the White list tab, you can add MAC addresses to the whitelist.
Figure 48 MAC blacklist and whitelist
4. Click Add.
5. On the page that opens, enter the MAC address that you want to add to the whitelist.
6. Click Apply.
Figure 49 Add a MAC address to the whitelist
Edit whitelist or blacklist
Restrictions and guidelines
The MAC address whitelist and blacklist configuration steps are similar. The following procedure describes the MAC address whitelist configuration as an example.
Procedure
1. From the navigation pane, select Network Security > MAC Address Filter.
2. Click the MAC Black and White List Management tab.
3. On the White list tab, you can add MAC addresses to the whitelist.
4. Click the Edit icon for a MAC address entry.
5. On the page that opens, specify a new MAC address, and then click Apply.
Figure 50 Edit source MAC address
ARP attack protection
Introduction to ARP attack protection
ARP is inherently vulnerable. An attacker can exploit ARP vulnerabilities to attack network devices. The device provides multiple ARP attack protection features to detect and prevent ARP attacks and viruses in the LAN.
ARP attack protection includes the following features:
· Dynamic ARP learning—Controls the enabling status of dynamic ARP learning on a per-interface basis. When dynamic ARP learning is disabled on an interface, the interface cannot learn dynamic ARP entries. To improve security, you can disable dynamic ARP learning on an interface if the interface has already learnt ARP entries for all valid hosts.
· Dynamic ARP management—Includes dynamic ARP entry management, ARP scanning, and fixed ARP.
¡ Dynamic ARP entry management—You can refresh, add, or delete dynamic ARP entries.
¡ ARP scanning—This feature creates dynamic ARP entries for valid hosts in the LAN.
¡ Fixed ARP—This feature converts the dynamic ARP entries to static ARP entries.
ARP scanning is typically used together with fixed ARP on a small-scale and stable network. To prevent the device from learning incorrect ARP entries, you can disable dynamic ARP learning after both ARP scanning and fixed ARP are performed.
· Attack protection management—Includes static ARP entry management and control of user access to the external network.
¡ Static ARP entry management—You can refresh, add, delete, batch import, or batch export static ARP entries.
¡ Control of user access to the external network—To prevent illegal internal users from attacking the external network, you can select to allow only users for which the device has static ARP entries to access the external network. Before you configure this setting, first perform ARP scanning and fixed ARP.
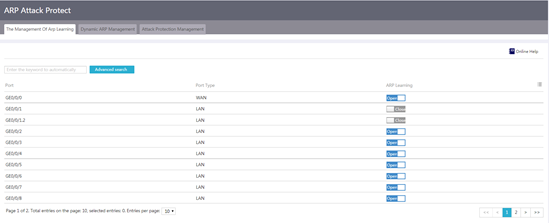
Configure dynamic ARP learning
1. From the navigation pane, select Network Security > ARP Attack Protect.
2. On the The Management Of Arp Learning tab, set the enabling status of dynamic ARP learning.
¡ To enable dynamic ARP learning, click Open.
¡ To disable dynamic ARP learning, click Close.
Figure 51 Dynamic ARP learning
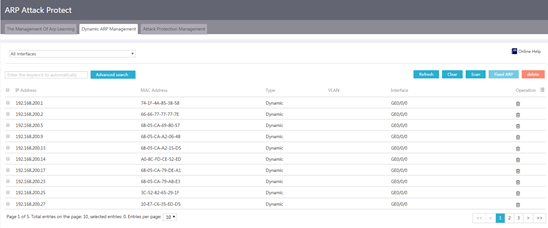
Configure dynamic ARP management
1. From the navigation pane, select Network Security > ARP Attack Protect.
2. Click the Dynamic ARP Management tab.
3. Perform one of the following tasks on existing dynamic ARP entries.
¡ To refresh existing ARP entries, click Refresh.
¡ To delete all existing ARP entries, click Clear.
¡ To delete specific dynamic ARP entries, select dynamic ARP entries, click delete, and then click Yes.
Figure 52 Dynamic ARP management
4. Perform ARP scanning and fixed ARP:
a. Click Scan.
b. Select an interface from the Interface list.
c. On the page that opens, enter the start IPv4 address and the end IPv4 address in the Start Ipv4Address and End Ipv4Address fields, respectively. Make sure the IP address range is on the same network segment as the interface.
d. Select IP addresses already in existing ARP entries are also scanned.
e. Select dynamic ARP entries and click Fixed ARP to convert the dynamic ARP entries to static ARP entries.
Configure attack protection management
Restrictions and guidelines
Make sure the ARP entry for the host from which you log in to the device is a static ARP entry.
Prerequisites
To add static ARP entries in bulk, you need to save the static ARP entries in a file and then bulk import them from the local file to the device.
To correctly import static ARP entries in bulk, you can first export existing static ARP entries to a file. This file can be used as a template file, in which you can edit static ARP entries as needed.
Procedure
1. From the navigation pane, select Network Security > ARP Attack Protect.
2. Click the Attack Protection Management tab.
Figure 53 Attack protection management
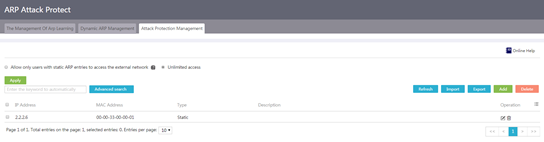
3. Control the user access to the external network.
¡ To allow only users for which the device has static ARP entries to access the external network, select Allow only users with static ARP entries to access the external network.
¡ To allow all users to access the external network, select Unlimited access.
4. Perform one of the following tasks on static ARP entries:
¡ To refresh static ARP entries, click Refresh.
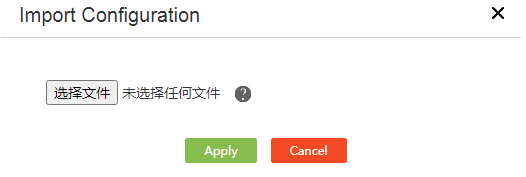
¡ To import static ARP entries in bulk, click Import.
Figure 54 Importing ARP entries
¡ To export static ARP entries in bulk, click Export.
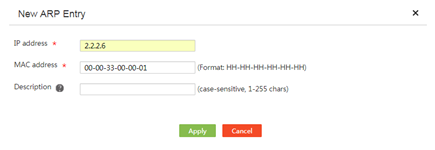
¡ To add a static ARP entry, click Add. On the page that opens, enter the IP address and MAC address for the static ARP entry, and then click Apply.
Figure 55 Adding an ARP entry
¡ To delete specific static ARP entries, select the static ARP entries, click Delete, and then click Yes.
Authentication management
Portal authentication
Introduction to portal authentication
Portal authenticates the identity of users to control user access to networks. The users can access network resources after they pass portal authentication. The device supports Web page authentication. Users initiate portal authentication through a Web browser. The device authenticates a user by the username and password that the user enters on the authentication page.
Both portal authentication types do not require the installation of authentication client software.
To allow specific users to access specified network resources without portal authentication, you can configure portal-free rules. The matching items for a portal-free rule include the MAC address, IP address, or host name of a user.
Configure the authentication page for Web page authentication
Prerequisites
Configure an IP address for the interface connected to portal users.
Save the image to be used as the background image on the portal authentication page as a local file named background-logon.jpg on the client through which you log in to the device. Make sure the resolution of the image is 1440 × 900 and the size is 255 K.
Procedure
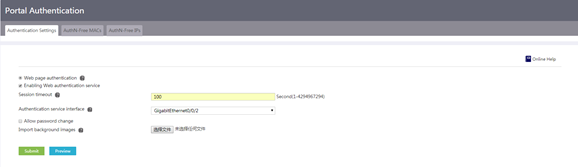
1. From the navigation pane, select Authentication > Portal Authentication.
2. Select Enabling Web authentication service. To configure portal authentication, you must enable the Web authentication service.
¡ Set the session timeout time in the Session timeout field. The device logs out a user if the online duration of the user exceeds the value.
¡ Select an interface to be enabled with portal authentication from the Authentication service interface list. The selected interface must be configured with an IP address.
3. Determine whether to allow password change. To allow portal users to change their login passwords, select the Allow password change option.
4. Click Choose File next to the Import background images field and then select the image file to be used as the background image on the authentication page.
5. Click Submit.
6. Click Preview. The configured authentication page is displayed.
Figure 56 Authentication settings
Add an authentication-free MAC address
1. From the navigation pane, select Authentication > Portal Authentication.
2. Click the AuthN-Free MACs tab.
Figure 57 Authentication-free MAC address configuration page
3. Click Add.
4. On the page that opens, enter a MAC address in the MAC address field.
5. Enter a description for the authentication-free MAC address in the Description field.
6. Click Apply.
Figure 58 Add an authentication-free MAC address
Add an authentication-free IP address or host name
1. From the navigation pane, select Authentication > Portal Authentication.
2. Click the AuthN-Free IPs tab.
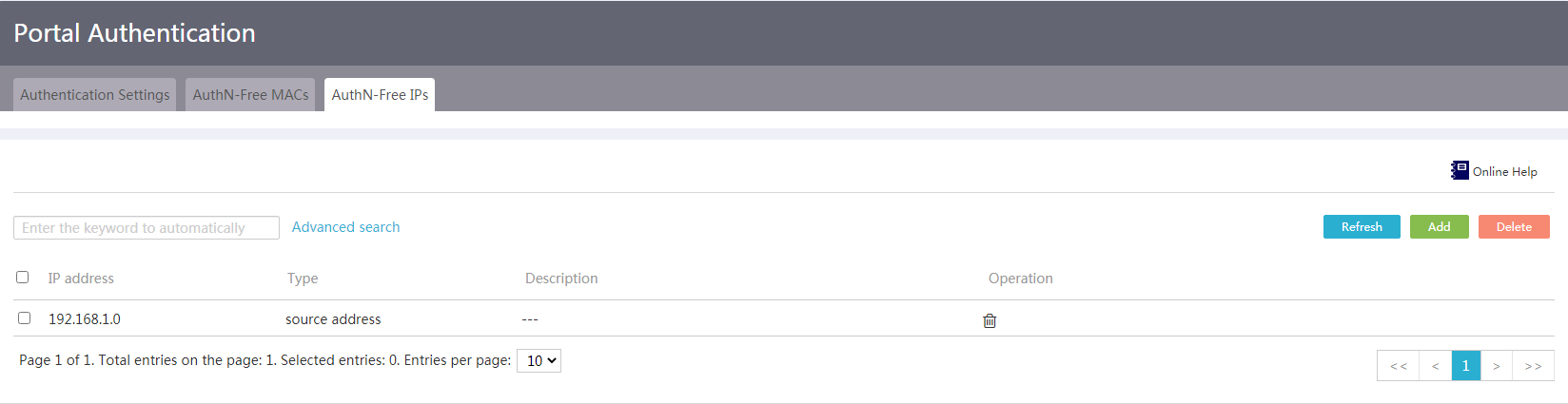
Figure 59 Authentication-free IP address or host name configuration page
3. Click Add.
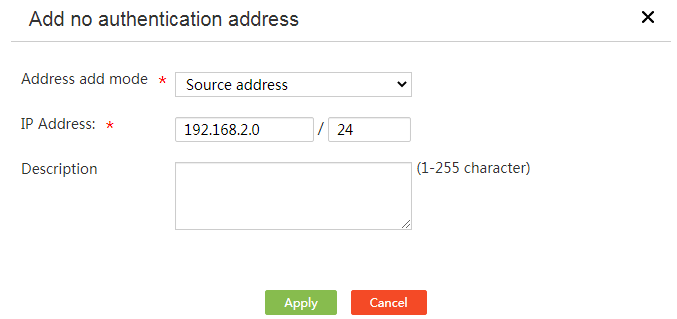
4. On the page that opens, select an address type from the Address add mode list. Supported options include Source address, Destination address, and Hostname.
¡ If you select Source address or Destination address, enter an IP address and mask in the IP Address field.
¡ If you select Hostname, enter the host name in the Hostname field.
5. Enter a description for the authentication-free IP address or host name in the Description field.
6. Click Apply.
Figure 60 Add an authentication-free IP address
PPPoE server
About this task
To provide the PPPoE broadband dialup service that can allocate IP addresses and perform authentication for dialup users, configure the PPPoE server.
Restrictions and guidelines
After you complete the configuration in this section, the device acts as the PPPoE server to allocate IP addresses and perform authentication for dialup users. To provide the Internet access service for dialup users, you must configure the WAN settings in addition to the PPPoE server settings. To configure the WAN settings, access the Fast Configuration or Network > WAN Settings page.
Procedure
1. From the navigation pane, select Authentication > PPPoE Server.
Figure 61 PPPoE server
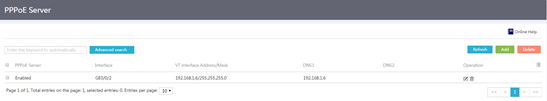
2. Click Add. The page for adding a PPPoE server opens.
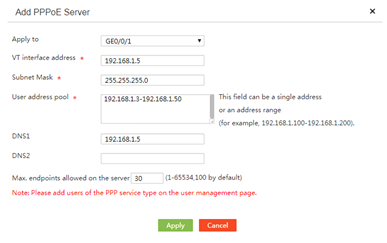
3. In the Apply to field, select a device interface used for providing the PPPoE dialup service.
4. In the VT interface address field, enter the VT interface IP address to enable the PPPoE server to allocate IP addresses.
5. In the Subnet Mask field, enter the subnet mask for the VT interface IP address.
6. In the User address pool field, enter the IP addresses to be allocated to PPPoE dialup users.
7. In the DNS1 field, enter the IPv4 address of the primary DNS server for PPPoE dialup users.
8. In the DNS2 field, specify the IPv4 address for the secondary DNS server for PPPoE dialup users.
9. In the Max. endpoints allowed on the server field, enter the maximum number of users that are allowed to dial up for Internet access.
10. Click Apply to enable the PPPoE service.
Figure 62 Adding a PPPoE server
User management
About this task
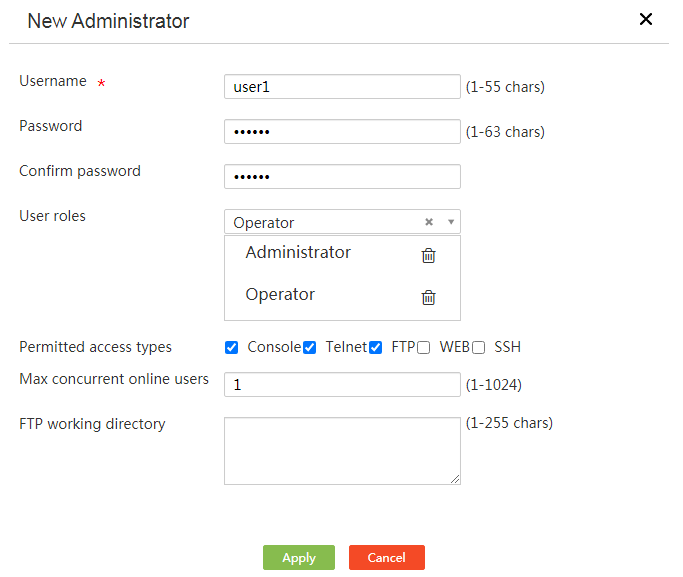
Use user management to manage user accounts for users that access the external network through the device. The user account information includes user credentials (the username and password) and network service information (including the available services and validity period). During identity authentication (such as portal authentication and PPPoE authentication), the device will use user account information to authenticate users. Only users of which the user account information matches that in the user management module can pass identity authentication to access the external network.
Add a user account
Prerequisites
To bind this user account to a specific host by user account-MAC binding, you must first obtain the MAC address of the NIC on the host.
Procedure
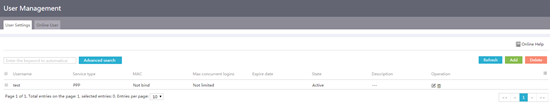
1. From the navigation pane, select Authentication > User Management.
2. On the User Settings tab, click Add.
Figure 63 User settings
3. In the dialog box that opens, enter a username in the Username field.
4. In the State field, set the status of the user account.
¡ To allow the users that use this account to request network services, select Active.
¡ To prevent users from using this account to request network services, select Blocked. Select this status if you temporarily do not want this user account to take effect.
5. In the Password field, enter a password.
If you do not configure a password, no password is required by the system for user identity authentication. As a best practice to enhance security, configure a password for the user account.
6. In the Service type field, select services for the user account.
7. In the MAC field, select whether to bind the user account to a MAC address.
¡ To bind the user account to a MAC address, select Bind and enter a MAC address in the format of xx-xx-xx-xx-xx-xx.
During authentication, the device will match the specified MAC address with the actual MAC address of the user that uses this account. The user fails authentication if the two MAC addresses do not match.
¡ To not bind the user account to a MAC address, select Not bind.
Users can use this user account to access the external network through this device from any endpoint.
8. In the Max concurrent logins field, set the maximum number of concurrent users that can use this account.
If you do not set a limit, the device does not limit the number of concurrent users that use this account.
9. In the ExpireDate field, configure a validity period for the user account as needed.
¡ If you configure a validity period, users that use this user account can pass authentication only within the validity period.
¡ If you do not configure a validity period, users that use this user account can always pass authentication.
10. In the Description field, configure a description for the user account.
For easy to remember and manage user accounts, configure a description for each user account.
11. Click Apply.
Figure 64 Adding a user
Delete a user account
Restrictions and guidelines
Deleting of a user account will not log out online users that use this account. The deletion operation only forbids new users to use this account to come online.
Procedure
1. From the navigation pane, select Authentication > User Management.
2. Click the Delete icon in the Operation column for a user account.
3. In the dialog box that opens, click Yes.
Figure 65 Deleting a user
View online users
1. From the navigation pane, select Authentication > User Management.
2. On the Online User tab, you can view online users.
3. To refresh online users, click Refresh.
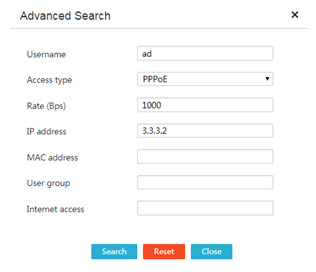
4. Click Advanced search. In the dialog box that opens, configure the filter criteria, and then click Search.
Figure 66 Advanced search
Virtual network
IPsec VPN
Introduction to IPsec VPN
IPsec VPN is a virtual private network established by using the IPsec technology. IPsec transmits data in a secure channel established between two endpoints. Such a secure channel is usually called an IPsec tunnel.
IPsec is a security framework that has the following protocols and algorithms:
· Authentication Header (AH).
· Encapsulating Security Payload (ESP).
· Internet Key Exchange (IKE).
· Algorithms for authentication and encryption.
AH and ESP are security protocols that provide security services. IKE performs automatic key exchange.
The device supports the following networking modes:
· Center-branch mode—Each branch gateway of an enterprise establishes an IPsec tunnel to the gateway of the enterprise center. Branches can securely communicate with the enterprise center through IPsec.
· Branch-branch mode—A branch gateway establishes an IPsec tunnel to another branch gateway of the enterprise. Data communications between branches are protected by IPsec.
Configure the device as a branch node
About this task
In a center-branch network, a branch node needs to establish an IPsec tunnel with the center node.
In a branch-branch network, a branch node needs to establish an IPsec tunnel with another branch node.
Configure basic IPsec settings
1. From the navigation pane, select Virtual Network > IPsec VPN.
2. Click the IPsec policy tab.
Figure 67 IPsec policy configuration page
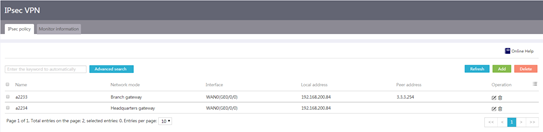
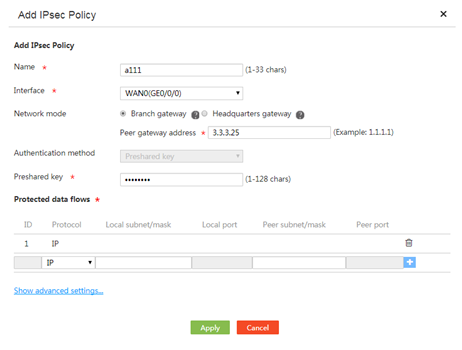
3. Click Add.
4. Enter an IPsec policy name in the Name field.
5. From the Interface field, select an interface to which the IPsec policy applies.
Make sure the selected interface can reach the peer.
6. Select the Branch gateway mode.
7. Enter the remote IP address of the IPsec tunnel in the Peer gateway address field.
The IP address is often the WAN interface address of the headquarters gateway or branch gateway.
8. Use the default and only authentication method Preshared key.
9. Enter the preshared key used with the peer in the Preshared key field.
The preshared key is negotiated and advertised in advance.
10. In the IPsec protected flows area, configure the following settings:
a. Select a protocol to be protected by the IPsec tunnel from the Protocol list.
b. Enter the local protected IP address/mask in the Local subnet/mask field.
c. Enter the local protected port in the Local port field.
This field is configurable only when the protected protocol is TCP or UDP.
The device performs IPsec encapsulation for packets sent by the source protected port and IP address.
d. Enter the peer protected IP address/mask in the Peer subnet/mask field.er
e. Enter the peer protected port in the Peer port field.
This field is configurable only when the protected protocol is TCP or UDP.
The device decapsulates only the IPsec packets received from the destination protected port and IP address.
f. Click the Add icon.
g. Repeat the previous steps to add more IPsec protected flow entries.
Figure 68 Add an IPsec policy
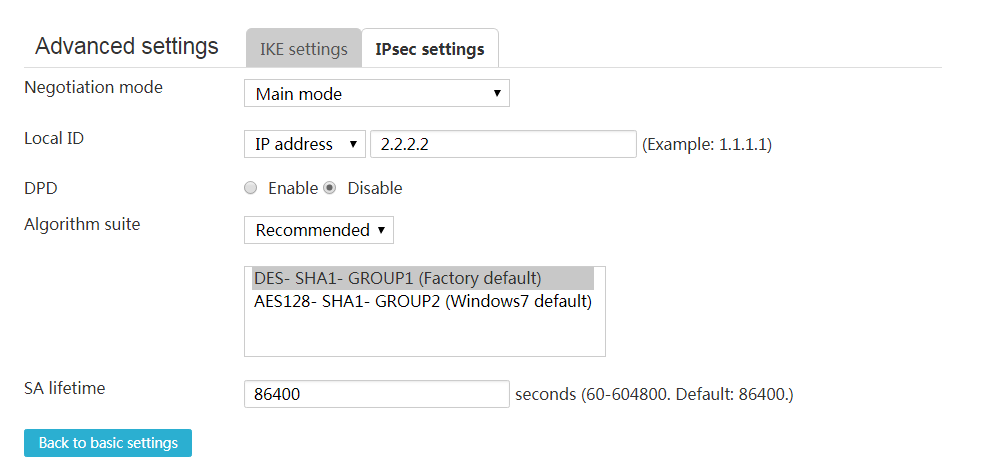
Configure IKE settings
Perform this task to change the default IKE settings.
1. Click the Show advanced settings link on the Add IPsec Policy page.
2. On the IKE settings tab, select a negotiation mode. Options include Main mode and Aggressive mode.
The aggressive mode is faster than the main mode but it does not provide identity information protection. The main mode provides identity information protection but is slower. Choose the appropriate negotiation mode according to your requirements.
If the device's public IP address is dynamically assigned, select the aggressive mode as a best practice.
3. Select an ID type and enter the local ID in the Local ID field for the IKE authentication. ID types include IP address, FQDN, and User-FQDN.
Make sure the ID type and the local ID are the same as the remote ID configuration for the peer.
If the IKE negotiation mode is the main mode, you must select IP address.
4. Select an ID type and enter the remote ID in the Remote ID field for the IKE authentication. ID types include IP address, FQDN, and User-FQDN.
Make sure the ID type and the remote ID are the same as the local ID configuration for the peer.
5. Select whether to enable DPD. DPD detects dead peers and the device will delete the IPsec tunnels established with dead peers.
As a best practice, enable DPD for the device to quickly detect availability problems of IPsec tunnels.
6. Select Recommended to use the recommended algorithm combination, or select Customize to customize the combination of encryption, authentication, and PFS algorithms for IKE negotiation process.
Make sure two peers of an IPsec tunnel are configured with the same encryption, authentication, and PFS algorithms.
7. Enter the IKE SA lifetime in the SA lifetime field. After the lifetime expires, the IKE parameters will be renegotiated.
Figure 69 Configure advanced IKE settings
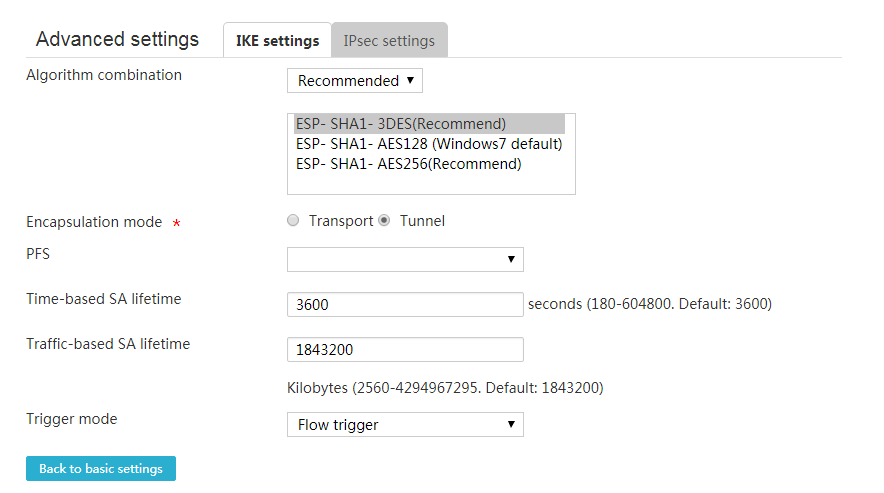
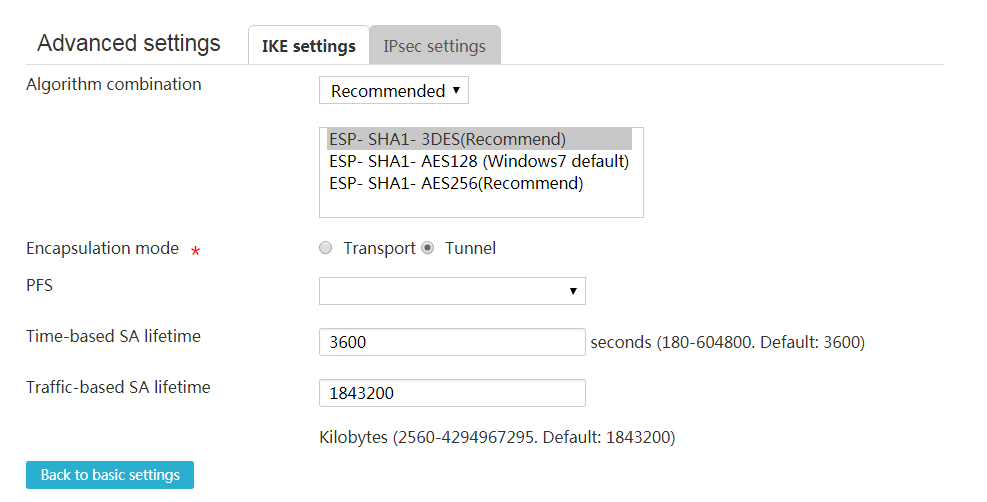
Configure advanced IPsec settings
Perform this task to change the default advanced IPsec settings
1. Configure basic IPsec settings, and then click Show advanced settings link.
2. On the page that opens, click the IPsec settings tab.
3. Select Recommended to use the recommended security protocols, encryption algorithms, and authentication algorithms, or select Customize to customize security protocols, authentication algorithms, encryption algorithms, encapsulation modes, and PFS algorithms.
If both the local IPsec-protected network segment and the peer protected network segment belong to private networks, select the tunnel encapsulation mode as a best practice.
Make sure two peers of an IPsec tunnel are configured with the same security protocol, authentication algorithms, encryption algorithms, encapsulation mode, and PFS algorithm.
4. Enter an interval that triggers IPsec renegotiation in the Time-based SA lifetime field. If the interval expires, the IPsec parameters will be renegotiated.
5. Enter the amount of the traffic that triggers IPsec renegotiation in the Traffic-based SA lifetime field. If the traffic exceeds the configured traffic limit, the IPsec parameters will be renegotiated.
6. Select an IPsec SA negotiation triggering mode in the Trigger mode field. Options include Flow trigger and Long connection trigger.
¡ Flow trigger—Triggers IPsec SA negotiation when the traffic to be sent meets the IPsec protection requirements.
¡ Long connection trigger—Triggers IPsec SA negotiation when required IPsec configuration is complete.
7. Click Back to basic settings to go back to the Add IPsec Policy page.
8. Click Apply.
Figure 70 Configure advanced IPsec settings
Configure the device as a center node
About this task
In a center-branch network, the center node needs to establish an IPsec tunnel with a branch node.
Configure basic IPsec settings
1. From the navigation pane, select Virtual Network > IPsec VPN.
2. Click the IPsec policy tab.
Figure 71 IPsec policy configuration page
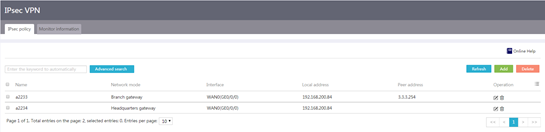
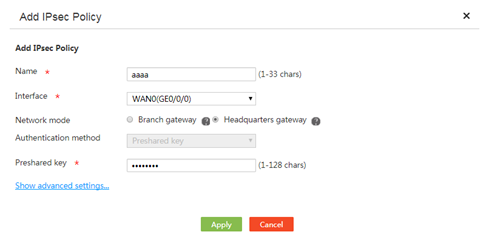
3. Click Add.
4. Enter an IPsec policy name in the Name field.
5. From the Interface field, select an interface to which the IPsec policy applies.
Make sure the selected interface can reach the branch.
6. Select the Headquarters gateway mode.
7. Use the Preshared key authentication method.
The device supports only the preshared key authentication method.
8. Enter the preshared key used with the peer in the Preshared key field.
The preshared key is negotiated and advertised in advance.
Figure 72 Add an IPsec policy
Configure IKE settings
Perform this task to change the default IKE settings.
1. Click the Show advanced settings link on the Add IPsec Policy page.
2. On the IKE settings tab, select a negotiation mode. Options include Main mode and Aggressive mode.
The aggressive mode is faster than the main mode but it does not provide identity information protection. The main mode provides identity information protection but is slower. Choose the appropriate negotiation mode according to your requirements.
If the device's public IP address is dynamically assigned, select the aggressive mode as a best practice.
3. Select an ID type and enter the local ID in the Local ID field for the IKE authentication. ID types include IP address, FQDN, and User-FQDN.
Make sure the ID type and the local ID are the same as the remote ID type and remote ID configured on the branches.
If the IKE negotiation mode is the main mode, you must select IP address.
4. Select whether to enable DPD. DPD detects dead peers and the device will delete the IPsec tunnels with dead peers.
As a best practice, enabling DPD for the device to obtain the availability of IPsec tunnels in time.
5. Select Recommended to use the recommended algorithm combination, or select Customize to customize the combination of encryption, authentication, and PFS algorithms for IKE negotiation process.
Make sure two peers of an IPsec tunnel are configured with the same encryption, authentication, and PFS algorithms.
6. Enter the IKE SA lifetime in the SA lifetime field. After the lifetime expires, the IKE parameters will be renegotiated.
Figure 73 Configure advanced IKE settings
Configure advanced IPsec settings
Perform this task to change the default advanced IPsec settings
1. Configure basic IPsec settings, and then click Show advanced settings link.
2. On the page that opens, click the IPsec settings tab.
3. Select Recommended to use the recommended security protocols, encryption algorithms, and authentication algorithms, or select Customize to customize security protocols, authentication algorithms, encryption algorithms, encapsulation modes, and PFS algorithms.
If both the local IPsec-protected network segment and the peer protected network segment belong to private networks, select the tunnel encapsulation mode as a best practice.
Make sure two peers of an IPsec tunnel are configured with the same security protocol, authentication algorithms, encryption algorithms, encapsulation mode, and PFS algorithm.
4. Enter an interval that triggers IPsec renegotiation in the Time-based SA lifetime field. If the interval expires, the IPsec parameters will be renegotiated.
5. Enter the amount of the traffic that triggers IPsec renegotiation in the Traffic-based SA lifetime field. If the traffic exceeds the configured traffic limit, the IPsec parameters will be renegotiated.
6. Click Back to basic settings to go back to the Add IPsec Policy page.
7. Click Apply.
Figure 74 Configure advanced IPsec settings
Monitor information
1. From the navigation pane, select Virtual Network > IPsec VPN.
2. Click the Monitor information tab.
Figure 75 Monitor information
L2TP server
Introduction to L2TP servers
Perform this task to configure basic L2TP server parameters and enable L2TP.
To provide a secure, cost-effective solution for remote users (such as branches and travelers) of an enterprise to access resources in the internal network of the enterprise, configure an L2TP server.
An L2TP server is a device that can process PPP and L2TP protocol packets. Typically, an L2TP server is deployed on the border of the internal network of an enterprise.
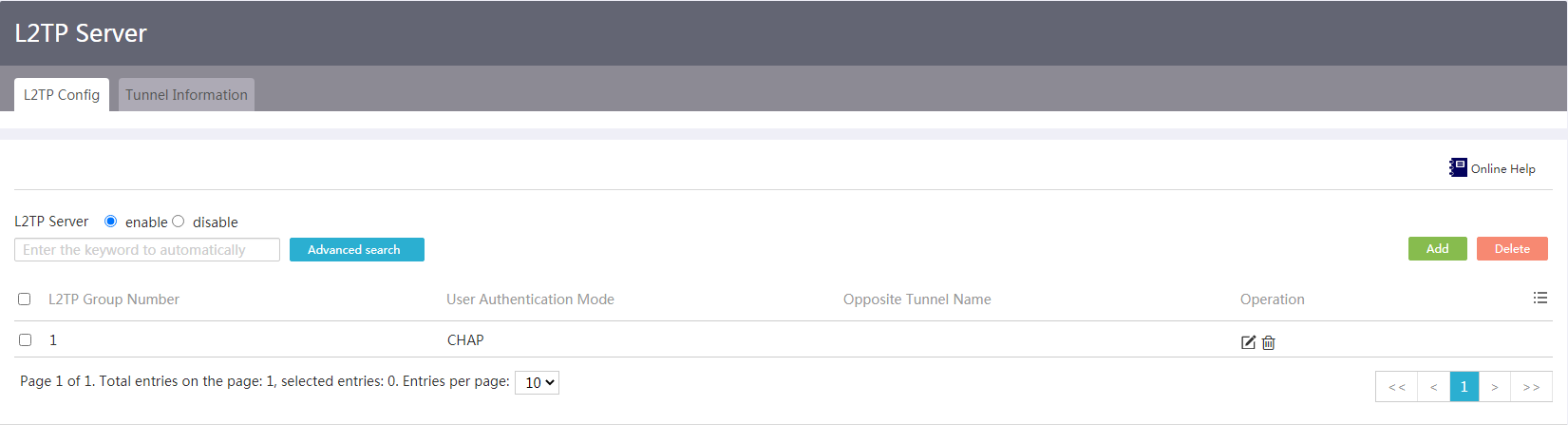
Configure an L2TP server
Procedure
1. From the navigation pane, select Virtual Network > L2TP Server.
2. Click the L2TP Config tab.
3. Select enable for the L2TP Server field.
Figure 76 L2TP server configuration
4. Click Add.
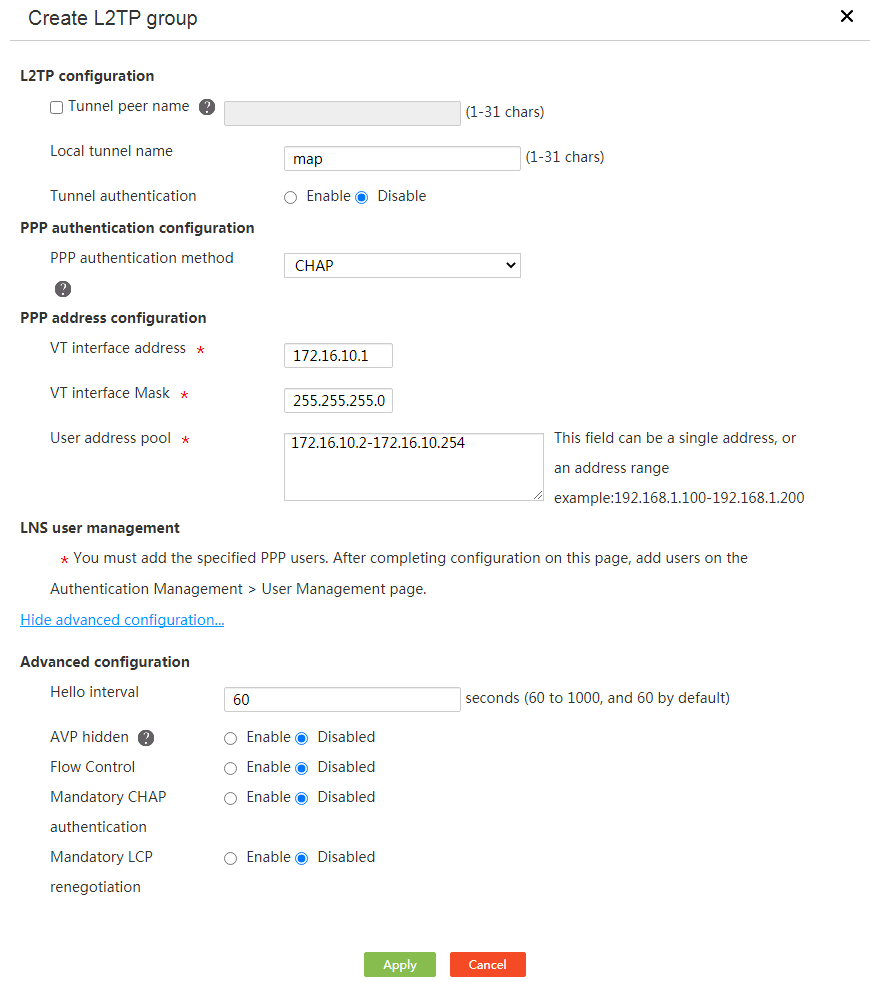
5. In the L2TP configuration area, configure L2TP tunnel parameters as follows:
¡ Select the Tunnel peer name option as needed. If you select this option, enter the tunnel name of the L2TP client.
¡ In the Local tunnel name field, enter the tunnel name for the L2TP server.
¡ For the Tunnel authentication parameter, select Enable or Disable as needed.
- If you select Enable, enter the tunnel password in the Tunnel password field. The tunnel authentication feature enhances security. To use this feature, you must enable tunnel authentication on both the L2TP server and L2TP client and make sure their passwords are the same. Tunnel establishment will fail if the L2TP server and L2TP client have different configuration.
- If you select Disable, authentication will not be performed for establishing a tunnel between the L2TP server and L2TP client.
6. From the PPP authentication method list, select None, PAP, or CHAP as needed.
¡ If you select None, authentication will not be performed on users. Use this authentication method with caution because it is of the lowest security.
¡ If you select PAP, a two-way handshake authentication will be performed on users. This authentication method is of medium security.
¡ If you select CHAP, a three-way handshake authentication will be performed on users. This authentication method is of the highest security.
7. In the PPP address configuration area, configure PPP address parameters:
¡ In the VT interface address field, enter the VT interface IP address to enable the L2TP server to allocate IP addresses to L2TP clients or users.
¡ In the VT interface Mask field, enter the subnet mask for the VT interface IP address.
¡ In the User address pool field, enter the IP addresses to be allocated to L2TP clients or users.
8. In the LNS user management area, add PPP users as prompted.
9. Click Display advanced configuration to display the advanced configuration area.
10. In the Advanced configuration area, configure advanced parameters as follows:
¡ In the Hello interval field, enter the Hello interval.
¡ For the AVP hidden field, select Enable or Disable as needed.
- If you select Enable, the tunnel password is used to transfer the AVP data (including tunnel negotiation parameters, session negotiation parameters, and user authentication information) in hidden mode. This feature enhances the data transmission security. This feature takes effect only when tunnel authentication is enabled.
- If you select Disable, AVP data will not be transferred in hidden mode.
¡ For the Flow control field, select Enable or Disable as needed.
- If you select Enable, when L2TP data packets are transmitted and received, the sequence numbers carried in packets are used to identify whether packets are lost and reorder packets. This feature improves the correctness and reliability of L2TP data packet transmission. For this feature to take effect, enable flow control on either of the L2TP server and L2TP client.
- If you select Disable, packets will not be detected or reordered.
¡ For the Mandatory CHAP authentication field, select Enable or Disable as needed.
- If you select Enable, the L2TP server will use CHAP to perform authentication again for a user after the L2TP client authenticates the user. This feature enhances the security. To enable mandatory CHAP authentication, make sure the PPP authentication method is set to CHAP.
- If you select Disable, the L2TP server will not perform mandatory CHAP authentication for users. For users that do not support second CHAP authentication, disable this feature as a best practice.
¡ For the Mandatory LCP renegotiation field, select Enable or Disable as needed.
- If you select Enable, the L2TP server will use LCP renegotiation to perform LCP negotiation and authentication again for a user after the L2TP client authenticates the user. This feature enhances the security. If you enable both mandatory LCP renegotiation and mandatory CHAP authentication, only mandatory LCP renegotiation takes effect.
- If you select Disable, the L2TP server will not perform mandatory LCP renegotiation for users. For users that do not support LCP negotiation, disable this feature as a best practice.
11. Click Apply.
Figure 77 Creating an L2TP group
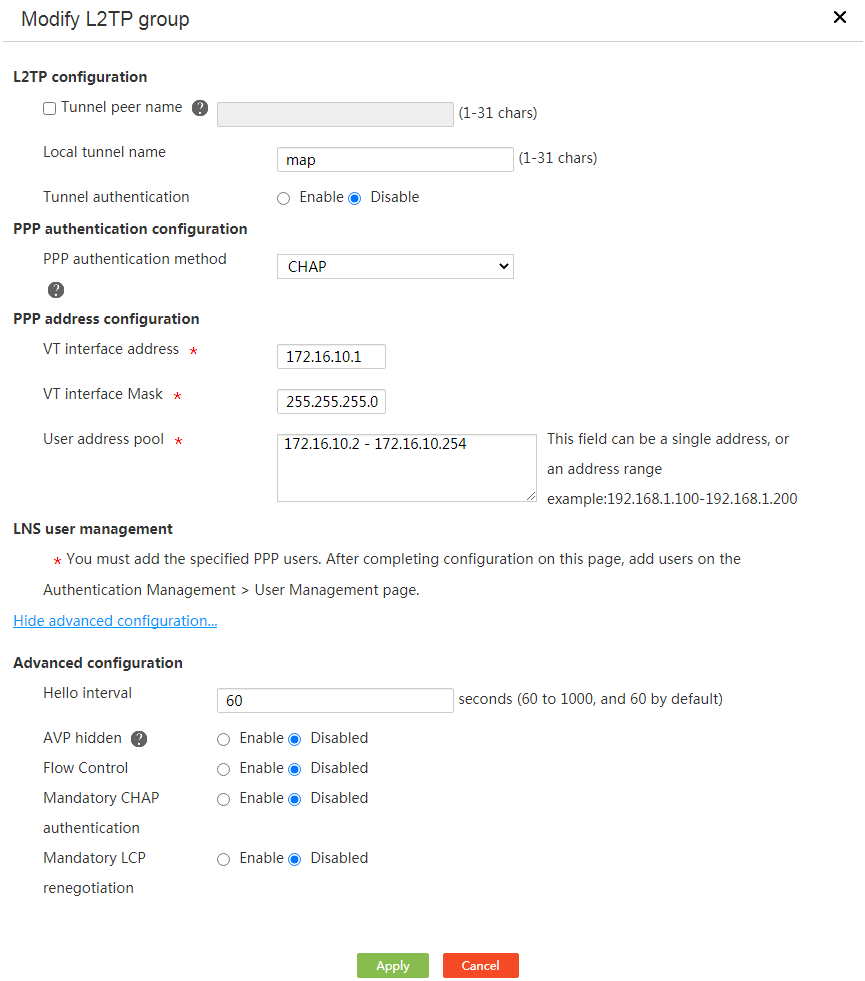
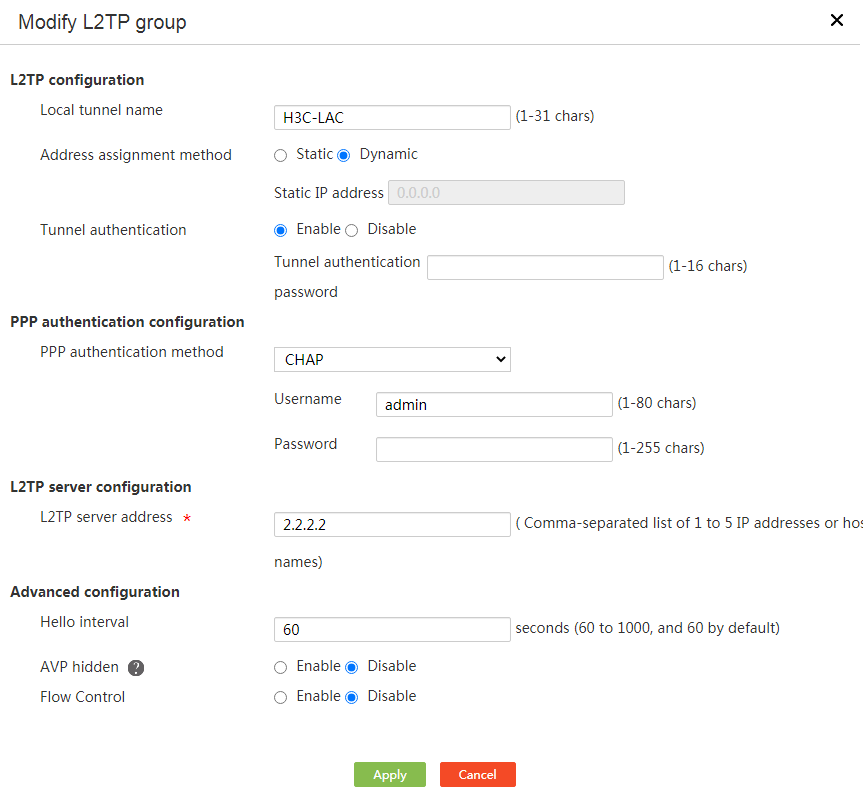
Edit an L2TP group
Procedure
1. From the navigation pane, select Virtual Network > L2TP Server.
2. Click the L2TP Config tab.
3. Click Edit for an L2TP group.
4. Edit the parameters as needed, and then click Apply.
Figure 78 L2TP server-editing an L2TP group
Delete L2TP groups
Procedure
1. From the navigation pane, select Virtual Network > L2TP Server.
2. Click the L2TP Config tab.
3. Perform one of the following tasks:
¡ Click Delete for an L2TP group.
¡ Select multiple L2TP groups, and then click Delete.
4. Click Yes.
Figure 79 L2TP server-confirming the deletion
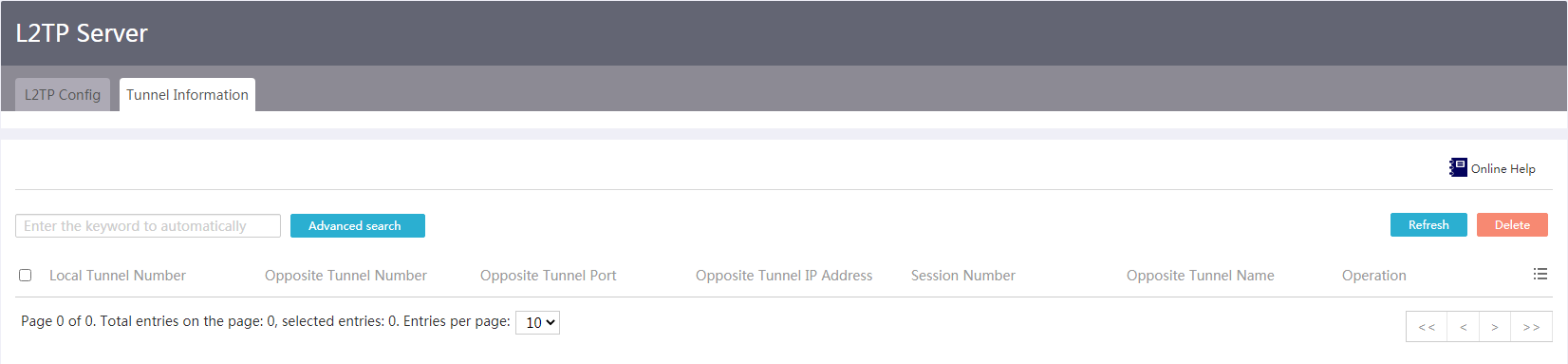
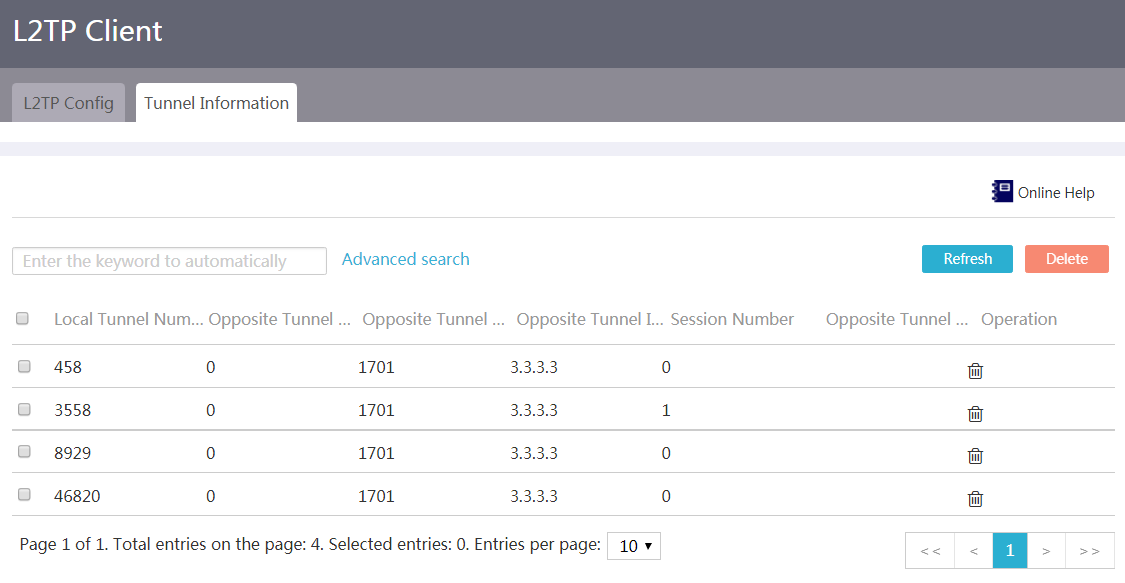
View L2TP tunnels
Procedure
1. From the navigation pane, select Virtual Network > L2TP Server.
2. Click the Tunnel Information tab.
Figure 80 L2TP tunnels
Delete L2TP tunnels
Procedure
1. From the navigation pane, select Virtual Network > L2TP Server.
2. Click the Tunnel Information tab.
3. Perform one of the following tasks:
¡ Click Delete for an L2TP tunnel.
¡ Select multiple L2TP tunnels, and then click Delete.
4. Click Yes.
Figure 81 L2TP server-confirming the deletion
L2TP client
Introduction to L2TP clients
Perform this task to configure basic L2TP client parameters and enable L2TP.
To provide a secure, cost-effective solution for branches of an enterprise to access resources in the internal network of the enterprise, configure an L2TP server.
An L2TP client is a device that can process PPP and L2TP protocol packets. Typically, an L2TP client is deployed on the egress of an enterprise branch.
Configure an L2TP client
Procedure
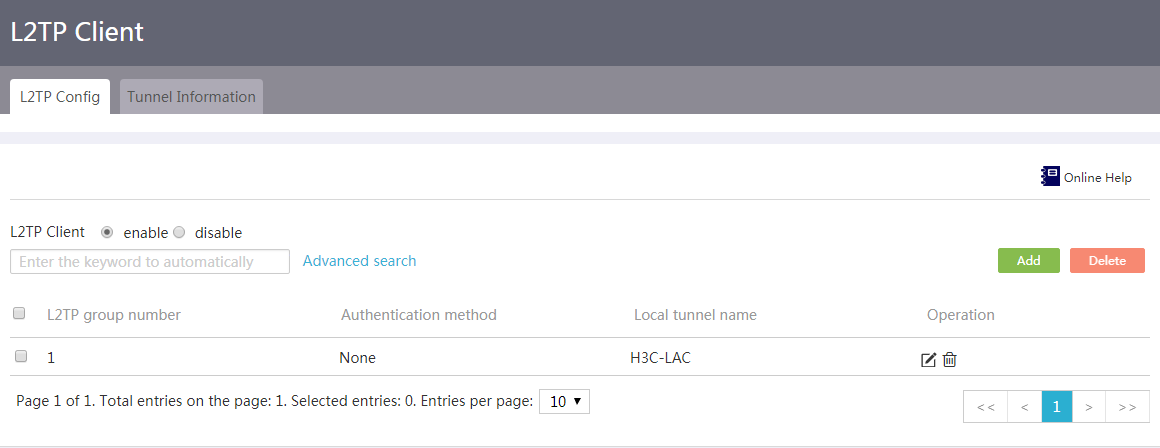
1. From the navigation pane, select Virtual Network > L2TP Client.
2. Click the L2TP Config tab.
3. Select enable for the L2TP Client field to enable L2TP.
Figure 82 L2TP client configuration
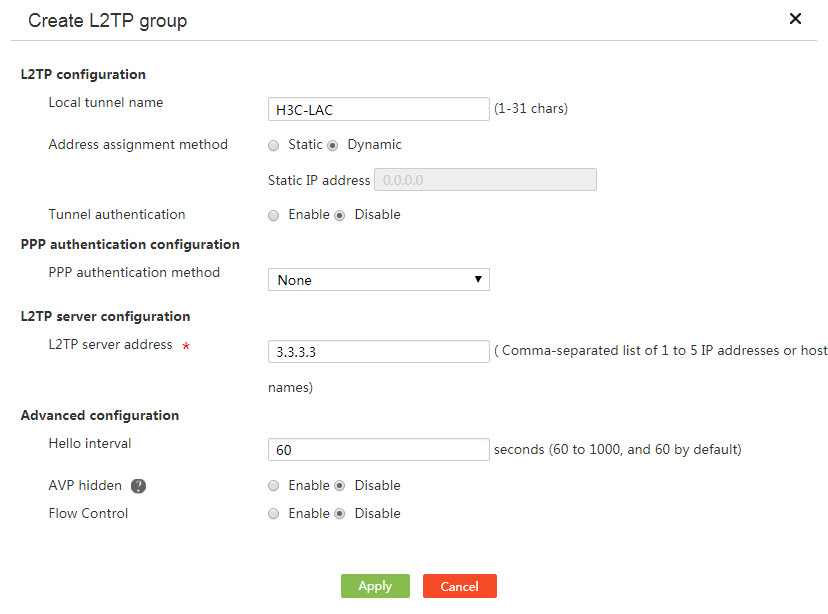
4. Click Add.
5. In the L2TP configuration area, configure L2TP tunnel parameters as follows:
¡ In the Local tunnel name field, enter the tunnel name for the L2TP client.
¡ For the Address assignment method field, select Static or Dynamic as needed.
- If you select Static, you must manually configure an IP address for the virtual PPP interface in the Static IP address field.
- If you select Dynamic, the LNS dynamically allocates an IP address to the virtual PPP interface.
¡ For the Tunnel authentication parameter, select Enable or Disable as needed.
- If you select Enable, enter the authentication password in the Tunnel password field. The tunnel authentication feature enhances security. To use this feature, you must enable tunnel authentication on both the L2TP server and L2TP client and make sure their passwords are the same. Tunnel establishment will fail if the L2TP server and L2TP client have different configuration.
- If you select Disable, authentication will not be performed for establishing a tunnel between the L2TP server and L2TP client.
6. From the PPP authentication method list, select None, PAP, or CHAP as needed.
¡ If you select None, authentication will not be performed on users. Use this authentication method with caution because it is of the lowest security.
¡ If you select PAP, a two-way handshake authentication will be performed on users. This authentication method is of medium security.
¡ If you select CHAP, a three-way handshake authentication will be performed on users. This authentication method is of the highest security.
7. In the L2TP server address field in the L2TP server configuration area, enter the IP address of the L2TP server.
8. In the Advanced configuration area, configure advanced parameters as follows:
¡ In the Hello interval field, enter the Hello interval.
¡ For the AVP hidden field, select Enable or Disable as needed.
- If you select Enable, the tunnel authentication password is used to transfer the AVP data (including tunnel negotiation parameters, session negotiation parameters, and user authentication information) in hidden mode. This feature enhances the data transmission security.
- If you select Disable, AVP data will not be transferred in hidden mode.
¡ For the Flow control field, select Enable or Disable as needed.
- If you select Enable, when L2TP data packets are transmitted and received, the sequence numbers carried in packets are used to identify whether packets are lost and reorder packets. This feature improves the correctness and reliability of L2TP data packet transmission. For this feature to take effect, enable flow control on either of the L2TP server and L2TP client.
- If you select Disable, packets will not be detected or reordered.
9. Click Apply.
Figure 83 Creating an L2TP group
Edit an L2TP group
Procedure
1. From the navigation pane, select Virtual Network > L2TP Client.
2. Click the L2TP Config tab.
3. Click Edit for an L2TP group.
4. Edit the parameters as needed, and then click Apply.
Figure 84 L2TP client-editing an L2TP group
Delete L2TP groups
Procedure
1. From the navigation pane, select Virtual Network > L2TP Client.
2. Click the L2TP Config tab.
3. Perform one of the following tasks:
¡ Click Delete for an L2TP group.
¡ Select multiple L2TP groups, and then click Delete.
4. Click Yes.
Figure 85 L2TP client-confirming the deletion
View L2TP tunnels
Procedure
1. From the navigation pane, select Virtual Network > L2TP Client.
2. Click the Tunnel Information tab.
Figure 86 L2TP tunnels
Delete L2TP tunnels
Procedure
1. From the navigation pane, select Virtual Network > L2TP Client.
2. Click the Tunnel Information tab.
3. Perform one of the following tasks:
¡ Click Delete for an L2TP tunnel.
¡ Select multiple L2TP tunnels, and then click Delete.
4. Click Yes.
Figure 87 L2TP client-confirming the deletion
Advanced settings
Application services
Introduction to application services
Application services allow you to configure Domain Name System (DNS). DNS is a distributed database used by TCP/IP applications to translate domain names into IP addresses. The domain name-to-IP address mapping is called a DNS entry. DNS can be static or dynamic.
Static DNS
Static DNS (SDNS) allows you to manually create mappings between domain names and IP addresses. When you use a domain name to access a service (for example, a Web, mail, or FTP service), the system will look up the DNS cache for the IP address mapped to the domain name.
Dynamic DNS
Dynamic DNS (DDNS) can dynamically update the mappings between domain names and IP addresses for DNS servers.
In some scenarios, for example, the dial-up access scenario, a WAN interface is used to provide Web, mail, or FTP service, and the interface IP address changes. To allow users to access the service through a fixed domain name, you can configure DDNS on the WAN interface. When the IP address of the WAN interface changes, the device automatically sends packets to the DDNS server to update the domain name-IP address mapping.
Configure static DNS
1. From the navigation pane, select Advanced Settings > Application Services.
2. On the SDNS tab, click Add. The New SDNS Entry page opens.
Figure 88 SDNS
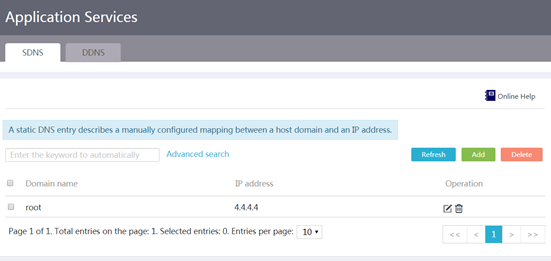
3. In the Domain name field, enter the domain name of the network device.
4. In the IP address field, enter the IP address of the network device.
5. Click Apply.
Figure 89 Adding an SDNS entry
Configure dynamic DNS
Restrictions and guidelines
Make sure the WAN interface uses a public IP address when the device applies for a domain name from the DDNS server.
Prerequisites
Before configuring DDNS, go to the website of a DDNS service provider (for example, PeanutHull), and register an account.
Procedure
1. From the navigation pane, select Advanced Settings > Application Services.
2. Click the DDNS tab.
Figure 90 DDNS

3. Click Add. The New DDNS Policy page opens.
4. On the page that opens, select the WAN interface that provides Web, mail, or FTP service from the WAN interface list.
5. In the Domain name field, enter the domain name of the device.
6. Configure the following DDNS server parameters:
¡ Select a service provider (for example, PeanutHull) from the Service provider list.
¡ In the Server address filed, enter the DDNS server address. If the server address is different from the default setting, select Modify server address to modify the IP address.
¡ Set the interval for the device to send DDNS update requests. If you set the interval to 0, the device sends update requests only when the WAN interface address changes or the WAN interface comes up from the down state.
7. In the Username and Password fields, enter the username and password that have been registered with the DDNS server, respectively.
8. Click Apply.
Figure 91 Adding a DDNS policy
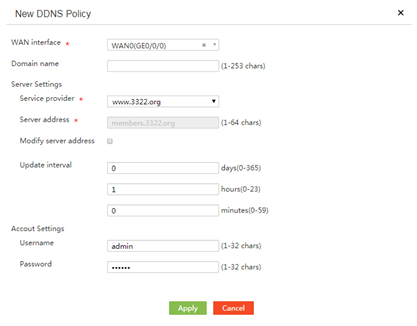
Static routing
Introduction
Static routes are manually configured. If a network's topology is simple and stable, you only need to configure static routes for the network to work correctly. For example, you can configure a static route based on the network egress interface and the gateway IP address for correct communication.
If multiple static routes are available to reach the same destination, you can assign different preference values to the static routes. The lower the preference value of a static route, the higher the priority of the route.
Restrictions and guidelines
If the interface associated with the next hop in a static route becomes invalid, the static route will not be deleted from the local device. To resolve this issue, you need to check your network environment and edit the static route settings.
Procedure
1. From the navigation pane, select Advanced Settings > Static Routing.
Figure 92 Static route list
2. Click Add.
3. In the Destination IP address field, enter the destination network IP address of the static route.
4. In the Mask length field, enter the mask length of the destination network.
5. In the Next hop field, select an output interface and enter the next hop IP address of the static route.
¡ Select an output interface. Supported interface types include WAN, cellular, and VLAN interfaces.
¡ Enter a next hop IP address.
6. In the Preference field, enter a preference for the static route.
7. In the Description field, enter a description for the static route.
8. Click Apply.
Figure 93 Adding an IPv4 static route
Policy-based routing
Introduction
Policy-based routing (PBR) enables you to forward packets flexibly based on packet characteristics by configuring a policy that contains a set of packet matching criteria and actions. For example, you can configure a PBR policy to forward packets with the specified source or destination IP address to the specified next hop or out of the specified interface.
Procedure
1. From the navigation pane, select Advanced Settings > PBR.
2. Select an interface to apply the PBR policy.
Figure 94 PBR policy list
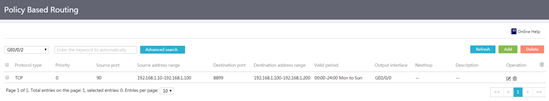
3. Click Add.
4. In the Match rule area, configure the matching criteria as needed:
¡ Select a protocol type in the Protocol type field.
- If you select Protocol number, you must enter the protocol number, for example, 80 (for HTTP).
- If you select TCP or UDP, you must enter the source and destination port numbers of the packets to match.
¡ In the Source address range and Destination address range fields, enter the source and destination IP address ranges. To specify an address range, separate the start and end IP addresses with a hyphen (-), for example, 1.1.1.1-1.1.1.2. To specify only one IP address, enter that IP address as both start and end IP addresses, for example, 1.1.1.1-1.1.1.1.
¡ In the Source port and Destination port fields, enter the source and destination ports. The Source port and Destination port fields are required only when the protocol type is TCP or UDP.
¡ In the Valid period section, specify the period of time in which the PBR policy takes effect. To specify a whole day, set the period to 00:00-23:59.
5. In the Output interface or Next hop field, set the output interface or next hop for the matching packets.
6. To facilitate management, enter a description for the PBR policy in the Description field.
7. Click Apply.
Figure 95 Configuring PBR policy settings
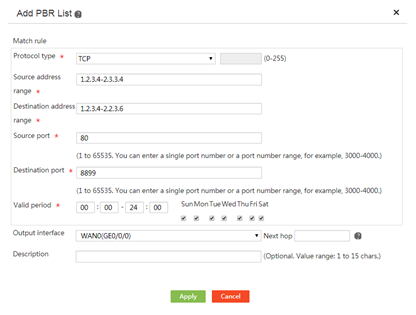
SNMP
Introduction to SNMP
Simple Network Management Protocol (SNMP) allows you to use a network management system (NMS), such as MIB Browser, to access and manage devices. With SNMP configured, devices automatically send traps or informs to the NMS when a critical event (such as interface going up or coming down, high CPU utilization, and memory exhaustion) occurs.
The device supports SNMPv1, SNMPv2c, and SNMPv3. SNMPv3 offers greater security than SNMPv1 and SNMPv2c.
· SNMPv1 and SNMPv2c use passwords for authentication.
· SNMPv3 uses a username for authentication and you must configure an authentication key and a privacy key to ensure communication security.
¡ The username and authentication key are used to authenticate the NMSs to prevent invalid NMSs from accessing the device.
¡ The privacy key is used to encrypt the messages transmitted between the NMS and the device to prevent the messages from being eavesdropped.
Prerequisites
Determine the SNMP version to use. The NMS and device must use the same SNMP version.
Configure SNMPv1 or SNMPv2c
Restrictions and guidelines
The NMS and device must use the same SNMP passwords. SNMP passwords include read-only password and read-write password. A minimum of one must be configured.
· To obtain parameter values from the device, configure only a read-only password.
· To obtain and set parameter values on the device, configure a read and write password.
Procedure
1. From the navigation pane, select Advanced Settings > SNMP.
2. Enable SNMP.
3. Select the SNMPv1 and SNMPv2c version.
4. Specify the SNMP password.
5. Enter the IP address of an NMS in the Trust Host IPv4 Address field.
Only the specified NMS can manage the device. If you do not configure this parameter, all NMSs that use correct SNMP passwords can manage the device.
6. Enter the IP address or domain name of the host to receive the notifications in the Trap Target Host IPv4 Address/Domain field.
7. Enter the contact information of the device administrator in the Contact Information field.
8. Enter the physical location of the device in the Device Location field.
9. Click Apply.
Figure 96 Configuring SNMPv1 and SNMPv2c
Configure SNMPv3
Restrictions and guidelines
The NMS and device must use the same username, authentication key, and privacy key.
Procedure
1. From the navigation pane, select Advanced Settings > SNMP.
2. Enable SNMP.
3. Select the SNMPv3 version.
4. Specify the username.
5. Specify the authentication key.
6. Specify the privacy key.
7. Enter the IP address of an NMS in the Trust Host IPv4 Address field.
Only the specified NMS can manage the device. If you do not configure this parameter, all NMSs that use the correct SNMP username, authentication key, and privacy key can manage the device.
8. Enter the IP address or domain name of the host to receive notifications in the Trap Target Host IPv4 Address/Domain field.
9. Enter the contact information of the device administrator in the Contact Information field.
10. Enter the physical location of the device in the Device Location field.
11. Click Apply.
Figure 97 Configuring SNMPv3
System tool
Basic settings
Introduction to basic settings
Perform this task to configure device information and system time.
The device information includes device name, device location, and contact information. The device name is editable, but the device location and contact information cannot be edited.
The system time includes date, time, and time zone. Correct system time is essential to network management and communication. Configure the system time correctly before you run the device on the network.
The device can use one of the following methods to obtain the system time:
· Manually set the system time.
The device uses the locally set system time, and then uses the clock signals generated by its built-in crystal oscillator to maintain the system time.
If the device restarts, the system time will restore to the factory default.
· Automatically synchronize date and time with an NTP server.
The device uses the time obtained from the NTP server as the current system time, and synchronizes time with the NTP server periodically. The device will quickly resynchronize the system time with the NTP server even if the device restarts. If you have an NTP server on the network, this method is recommended.
The system time calculated by using the time from a time source is more precise.
|
|
NOTE: As a best practice, use one of the following browsers to access the Web interface: · Internet Explorer 10 or later. · Chrome 57 or later. · Firefox 35 or later. |
Configure basic device information
1. From the navigation pane, select System Tool > Basic Settings.
2. On the Device information tab, enter a device name.
3. Click Apply.
Figure 98 Device information
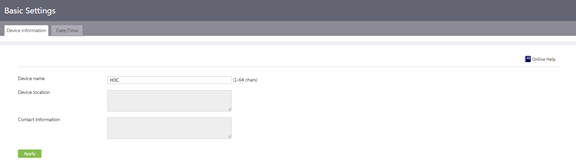
Manually configure the system time
Restrictions and guidelines
A device reboot restores the factory default system time settings.
Prerequisites
Identify the time zone of the place where the device resides.
Procedure
1. From the navigation pane, select System Tool > Basic Settings.
2. Click the Date/Time tab.
3. Select Manually set the clock.
4. Set the system time to the current time in the geographic area where the device is located:
a. Select the date.
b. Select the time. The minute and second values available on the Web interface are multiples of 3 (00, 03, 06, 09, ..., 57). You can use the up or down arrows to fine tune the values. For example, to set the minute value to 20, select 18 first, and then click the up arrow twice to get 20.
5. Select the time zone of the place where the device resides.
6. Click Apply.
Figure 99 Configuring the system time manually
Automatically synchronize the UTC time
Restrictions and guidelines
Make sure the device uses the same time zone as the NTP server.
Prerequisites
Identify the time zone of the place where the device resides.
Procedure
1. From the navigation pane, select System Tool > Basic Settings.
2. Click the Date/Time tab.
3. Select Automatically synchronize the clock with a trusted time source on the network.
4. Configure the IP addresses of NTP server 1 and NTP server 2.
5. Click Default NTP Server List to identify the default NTP servers.
6. Select the time zone.
7. Click Apply.
Figure 100 Synchronizing the UTC time automatically
|
|
NOTE: · Whether default NTP servers are configured for the device depends on the device model. · You can use default NTP servers or specify NTP servers as needed. The device automatically obtains the UTC time from an available NTP server that provides highest time precision. If none of NTP servers is available, the device uses its internal clock signal. After an NTP server recovers, the device will synchronize time with the NTP server again. |
Diagnostics
Introduction to diagnostics
Use this feature to diagnose network faults. With diagnostics, you can perform the following tasks:
· Tracert—Traces the path that packets traverse from the device to the destination host.
· Ping—Tests the reachability of another device or host.
· Diagnostic export—Collects the operating information of feature modules for system diagnostics and troubleshooting. The device will automatically store collected information in a compressed file and save the file on your Web login terminal.
· Port mirroring—Automatically copies packets passing through a monitored port to the monitor port and provides transmission information on each port in real time. The network administrator can use the information to perform traffic monitoring, performance analysis, and fault diagnosis.
· Packet capture tool—Captures network data packets to more effectively analyze network faults. The tool uses tcpdump to run at the backend and automatically stores the captured packets to a file named flash--packetCapture.pcap on your Web login terminal.
Configure tracert
1. From the navigation pane, select System Tool > Diagnostics.
2. Click the Tracert tab.
3. Enter the destination IP address or host name.
4. Click Start.
5. In the Result area, view the tracert result.
Figure 101 Configuring Tracert
Configure ping
1. From the navigation pane, select System Tool > Diagnostics.
2. Click the Ping tab.
3. Enter the destination IP address or host name.
4. Click Start.
5. In the Result area, view the ping result.
Figure 102 Configuring ping
Collect diagnostic information
1. From the navigation pane, select System Tool > Diagnostics.
2. Click the Diagnostic Export tab.
3. Click Collect.
Figure 103 Collecting diagnostic information
Configure port mirroring
1. From the navigation pane, select System Tool > Diagnostics.
2. Click the Port Mirroring tab.
3. Select to configure port mirroring for Layer 2 or Layer 3 interfaces.
4. Configure source ports.
Select a source port. Then select a direction for the source port. The following options are available:
¡ Inbound: Mirror only packets received on the source port.
¡ Outbound: Mirror only packets sent from the source port.
¡ Both: Mirror both packets received on the source port and packets sent from the source port.
To add more source ports, click the + icon.
5. Select a destination port.
6. Click Ensure.
Figure 104 Configuring port mirroring
Configure the packet capture tool
Restrictions and guidelines
Before using this feature, make sure the storage medium has sufficient space to store the packet capture file. If the storage space is insufficient, the packet capture task will be stopped before it is completed.
Procedure
1. From the navigation pane, select System Tool > Diagnostics.
2. Click the Packet capture tool tab.
3. Select the interface on which packets are to be captured.
Any WAN interface on the router can be selected.
4. Configure the size of packets to be captured, in bytes. The capture length parameter represents the maximum length that the device can capture from a packet. If the length of a packet is longer than the specified length, the device captures only contents of the specified length from that packet.
A long capture length increases the packet processing time and reduces the number of packets that tcpdump can cache, which might result in packet loss. On the premise that the required packets can be captured, specify a smaller capture length.
5. Specify protocol types for capturing packets as needed. If you select all, all packets on the interface will be captured.
6. Set the maximum size of the file that stores captured packets, in MB.
7. Set the packet capture duration, in seconds.
8. Filter packets to be captured by source host parameters. The following options are available:
¡ Any: Capture packets for all source hosts.
¡ Filter by IP address: Capture packets sourced from a host with a specific IP address.
¡ Filter by MAC address: Capture packets sourced from a host with a specific MAC address.
9. Filter packets to be captured by destination host parameters. The following options are available:
¡ Any: Capture packets for all destination hosts.
¡ Filter by IP address: Capture packets received by a host with a specific IP address.
¡ Filter by MAC address: Capture packets received by a host with a specific MAC address.
10. Click Start.
The packet capture process and the number of packets currently captured are displayed on the current page. You can click Cancel to terminate packet capture and export the capture file flash -- packetCapture.pcap.
Figure 105 Configuring the packet capture tool
Admin account management
About admin account management
Use this page to manage and maintain the admin accounts used by users to log in to the device. You can add, edit, or delete admin accounts.
Add an admin account
1. From the navigation pane, select System Tool > Admin Accounts.
Figure 106 Admin accounts
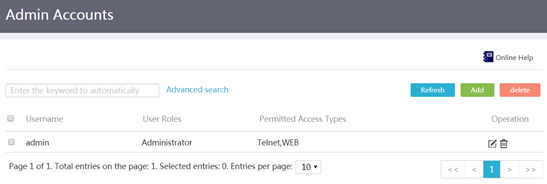
2. Click Add.
3. In the dialog box that opens, enter an account name in the Username field.
4. Enter a password in the Password field and confirm it in the Confirm password field.
If you do not configure a password, no password is required by the system when a user uses this account to log in to the device. To improve security, configure a password for the admin account.
5. In the User roles field, select user roles.
¡ To assign the highest administrative privilege to this admin account, select Administrator.
¡ To assign only the view privilege to this admin account, select Operator.
6. In the Permitted access types field, select access services.
¡ To assign the console service to this admin account, select Console.
The console service allows users to log in to the device through the console port.
¡ To assign the Telnet service to this admin account, select Telnet.
The Telnet service allows users to Telnet to the device from a Telnet client when the device acts as a Telnet server.
¡ To assign the FTP service to this admin account, select FTP.
The FTP service allows users to access the file system resources on the device from an FTP client when the device acts as an FTP server.
¡ To assign the Web service to this admin account, select WEB.
The Web service allows users to log in to the device through Web.
¡ To assign the SSH service to this admin account, select SSH.
The SSH service allows users to log in to the device from an SSH client when the device acts as an SSH server. SSH login is safer than Telnet login.
7. In the Max concurrent online users field, set the maximum number of concurrent users that can use this admin account.
If you do not set a limit, the device does not limit the number of concurrent users that use this admin account.
This setting does not limit the number of concurrent users that use this admin account to log in to the device through FTP.
8. In the FTP working directory field, enter a working directory. You must configure this parameter if the admin account is assigned the FTP service.
As a best practice to enter a valid working directory, first access the System Tool > Upgrade > File Management page to view existing file paths.
9. Click Apply.
Figure 107 Adding an admin account
Edit an admin account
1. From the navigation pane, select System Tool > Admin Accounts.
2. Click the Edit icon in the Operation column for an admin account.
3. In the dialog box that opens, enter a new password in the Change password field and confirm it in the Confirm password field.
After you change the password of an admin account, users that use this admin account must change the password again at the next login.
4. In the User roles list, select a new role.
¡ To assign the highest administrative privilege to this admin account, select Administrator.
¡ To assign only the view privilege to this admin account, select Operator.
5. In the Permitted access types field, select new access services.
¡ To assign the console service to this admin account, select Console.
The console service allows users to log in to the device through the console port.
¡ To assign the Telnet service to this admin account, select Telnet.
The Telnet service allows users to Telnet to the device from a Telnet client when the device acts as a Telnet server.
¡ To assign the FTP service to this admin account, select FTP.
The FTP service allows users to access the file system resources on the device from an FTP client when the device acts as an FTP server.
¡ To assign the Web service to this admin account, select WEB.
The Web service allows users to log in to the device through Web.
¡ To assign the SSH service to this admin account, select SSH.
The SSH service allows users to log in to the device from an SSH client when the device acts as an SSH server. SSH login is safer than Telnet login.
6. In the Max concurrent online users field, set a new value to change the maximum number of concurrent users that can use this admin account.
If you do not set a limit, the device does not limit the number of concurrent users that use this admin account.
This setting does not limit the number of concurrent users that use this admin account to log in to the device through FTP.
7. In the FTP working directory field, enter a new working directory. You must configure this parameter if the admin account is assigned the FTP service.
As a best practice to enter a valid working directory, first access the System Tool > Upgrade > File Management page to view existing file paths.
8. Click Apply.
Figure 108 Editing an admin account
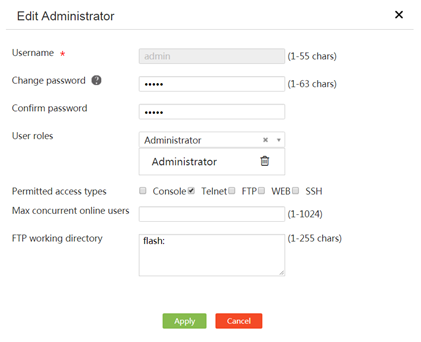
Delete an admin account
1. From the navigation pane, select System Tool > Admin Accounts.
2. Click the Delete icon in the Operation column for an admin account.
3. In the dialog box that opens, click Yes.
Figure 109 Deleting an admin account
Remote management
Introduction to remote management
Use remote management to configure parameters for network connectivity detection or device remote login and management.
With remote management, you can perform the following tasks:
· Permit ping on interfaces—Perform this task to permit interfaces to send ping packets. Ping is a utility for detecting network connectivity and obtaining the running status of the network.
· Permit Telnet login on interfaces—Perform this task to allow users to Telnet to the device through specific interfaces. Telnet is a remote login protocol. Users can Telnet to the device from a PC to remotely manage the device.
· Permit SSH login—To secure device access, perform this task to enable the Secure Shell (SSH) services. SSH is a network security protocol. Using encryption and authentication, SSH can implement secure remote access and file transfer over an insecure network. Acting as an SSH server, the device supports the following SSH services:
¡ Stelnet—The implementation of Secure Telnet (Stelnet) is the same as that of Telnet, but Stelnet is more secure.
¡ SFTP—Secure FTP (SFTP) uses SSH connections to provide secure file transfer. The device allows a remote user to log in to it for secure file management and transfer.
¡ SCP—Secure Copy (SCP) offers a secure method to copy files.
· Permit HTTP/HTTPS login on interfaces—Perform this task to allow users to use HTTP or HTTPS to log in to the device through specific interfaces. Web login can use HTTP or HTTPS. HTTPS login is more secure than HTTP login. Users can use HTTP or HTTPS to log in to the Web interface of the device from a PC for remote device configuration and management.
· Use the cloud service—Perform this task to establish a remote management tunnel with an H3C Cloud server through the Internet. The network administrator can remotely manage and maintain the device through the Cloud server.
Permit ping on an interface
1. From the navigation pane, select System Tool > Remote Login.
2. On the Ping tab, select Permit ping for an interface to permit the interface to send ping packets.
3. Click Apply.
Figure 110 Configure ping service
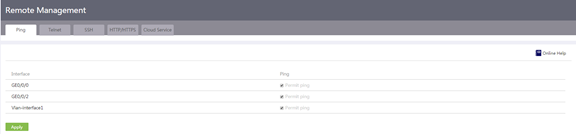
Configure Telnet login
1. From the navigation pane, select System Tool > Remote Login.
2. Click the Telnet tab.
3. Click the button next to the Telnet service field to enable the Telnet service. When the Telnet service is in ON state, the service is enabled.
4. In the IPv4 Listening Port or IPv6 Listening Port field, enter a port number for the Telnet service.
Enter the IPv4 listening port number or IPv6 listening port number depending on the network requirements.
¡ If users Telnet to the device in an IPv4 network, the port number used by the users must be the same as that specified in the IPv4 Listening Port field.
¡ If users Telnet to the device in an IPv6 network, the port number used by the users must be the same as that specified in the IPv6 Listening Port field.
5. Click Apply.
Figure 111 Configure Telnet service
6. Click Edit on the right side of Administrator IP Address List.
7. On the page that opens, specify one or multiple IPv4 addresses of the interface for remote login:
¡ To add an individual administrator IP address, enter the IP address in the IP address field.
¡ To add a range of administrator IP addresses, specify the IP address range in the IP address range field.
The start address must be lower than the end address. The IP address specified individually can be out of the specified IP address range.
¡ To exclude an IP address from the IP address range, enter the excluded IP address in the Exclude IP address field.
The excluded IP address must be in the specified IP address range. An excluded IP address cannot access the device through Telnet.
8. Click the ![]() icon to add the specified IP address, address range, or/and
excluded IP address to the administrator IP address list at
right.
icon to add the specified IP address, address range, or/and
excluded IP address to the administrator IP address list at
right.
9. Repeat steps 7 to 8 to add more administrator IP addresses.
10. Click Apply.
Figure 112 Configure administrator IP addresses
Configure SSH login
1. From the navigation pane, select System Tool > Remote Login.
2. Click the SSH tab.
3. Enable one or multiple SSH services according to the network requirements:
¡ To enable the Stelnet service, click the button next to the Stelnet service field to set the service state to ON.
¡ To enable the SFTP service, click the button next to the SFTP service field to set the service state to ON.
¡ To enable the SCP service, click the button next to the SCP service field to set the service state to ON.
Figure 113 Configure SSH service
Configure HTTP login and HTTPS login
1. From the navigation pane, select System Tool > Remote Login.
2. Click the HTTP/HTTPS tab.
3. In the HTTP Service Port field, enter a port number for HTTP login. As a best practice, use a port number greater than 10000 for HTTP login.
4. In the HTTPS Service Port field, enter a port number for HTTPS login. As a best practice, use a port number greater than 10000 for HTTPS login.
5. Enter a timeout time in the Web Idle timeout field.
6. Click Apply.
Figure 114 Configure HTTP/HTTPS service
7. Click Edit on the right side of Administrator IP Address List.
8. On the page that opens, add administrator IP addresses:
¡ To add an individual administrator IP address, enter the IP address in the IP address field.
¡ To add a range of administrator IP addresses, specify the IP address range in the IP address range field.
The start address must be lower than the end address. The IP address specified individually can be out of the specified IP address range.
By default, the device allows Web access from IP address range 1.1.1.1–255.255.255.255. You can edit the address range as needed. Make sure the administrators can still access Web pages after IP address modification.
As a best practice, configure the administrator IP address list to contain the network segment where the VLAN interface connecting the user client resides.
¡ To exclude an IP address from the IP address range, enter the excluded IP address in the Exclude IP address field.
The excluded IP address must be in the specified IP address range. The device does not allow Web access from the excluded IP address.
9. Click the ![]() icon to add the specified IP address, address range, or/and
excluded IP address to the administrator IP address list at
right.
icon to add the specified IP address, address range, or/and
excluded IP address to the administrator IP address list at
right.
10. Repeat steps 8 to 9 to add more administrator IP addresses.
11. Click Apply.
Figure 115 Configure administrator IP addresses
Configure the cloud service
1. From the navigation pane, select System Tool > Remote Login.
2. Click the Cloud Service tab.
3. Select Open from the Cloud Service field to enable the cloud service.
4. In the Server domain name field, enter the Cloud server domain name.
5. In the Sysname field, enter the system name of the device.
6. Click Apply.
7. Use a mobile phone to scan the QR code on the page to download and install the Cloudnet app. Then, open the app on the mobile phone to log in to the Cloud server to remotely manage and maintain the device.
Figure 116 Configure the cloud service
Configuration management
Introduction to configuration management
Use configuration management to manage the configuration files on the device.
With configuration management, you can perform the following tasks:
· View the running configuration—To view the running configuration on the device, for example, the software version and interface IP addresses, select System Tool > Config Management from the navigation pane and click the View Config tab.
· Restore the factory defaults—This task restores the configuration to the factory defaults. If the device does not have a startup configuration file or the startup configuration file is corrupt, perform this task so the device can start up at the next startup.
· Save the running configuration—This task saves the running configuration to the main next-startup configuration file, which is the primary next-startup configuration file. Perform this task after you complete one or multiple configuration tasks so the new settings you have made can survive a device reboot.
· Restore the configuration from a backup file—This task replaces the running configuration with the configuration from a backup file. Perform this task if the running configuration contains incorrect or undesirable settings.
· Export the running configuration—This task exports the running configuration to a configuration file. Perform this task to back up the running configuration for future use.
Restore the factory defaults
1. From the navigation pane, select System Tool > Config Management.
2. Click the Restore Config tab.
3. Click Reset.
Figure 117 Restoring the factory defaults
4. In the dialog box that opens, click Yes to confirm that you are sure to restore the factory default configuration and forcibly reboot the system.
Then, the device automatically reboots and restores the factory default configuration.
Figure 118 Confirming the configuration
Save the running configuration
1. From the navigation pane, select System Tool > Config Management.
2. Click the Save Config tab.
3. Click Save Running Configuration.
Figure 119 Save Config page

4. On the page that opens, use one of the following methods to save the running configuration to the main next-startup configuration file:
¡ to the next-startup configuration file—If you select this option, the system does not allow you to select a file. The system directly saves the running configuration to a file in the root directory of the storage medium and specifies the file as the main next-startup configuration file.
¡ to file—If you select this option, the system allows you to select a file to save the running configuration and specifies the file as the main next-startup configuration file.
Figure 120 Saving the running configuration
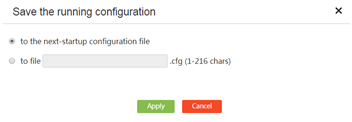
5. Click Apply.
Restore configuration from a backup file
1. From the navigation pane, select System Tool > Config Management.
2. Click the Save Config tab.
3. Click Import Configuration.
4. On the page that opens, click Choose File to select a backup configuration file.
Figure 121 Choosing a backup file
5. Click Apply.
6. Reboot the device.
Export the running configuration
1. From the navigation pane, select System Tool > Config Management.
2. Click the Save Config tab.
3. Click Export Running Configuration to export the running configuration to the local PC.
Software upgrade
Introduction
Use software upgrade to upgrade device software and manage the files on the device. You can add new feature or fix bugs by upgrading device software.
You can upgrade device software by using the following methods:
· Manual upgrade: Upgrade device software by using a local IPE file uploaded to the device.
· Auto upgrade: Upgrade device software by downloading the latest software image file from the cloud platform.
File management supports the following operations:
· Upload—Upload a file to the device. For example, you can upload an .ipe file to the device before using the file to upgrade the software on the device.
· Delete—Delete unimportant files from the device to release the storage space used by the files.
· Download—Download a file from the device to your PC for data backup or analysis.
Upgrade device software
Manually upgrade device software
1. From the navigation tree, select System Tool > Upgrade.
2. On the Upgrade tab, click Manual upgrade.
Figure 122 Upgrade
3. Click Select File, and select the target IPE file.
4. To load the device with the new software immediately, select Reboot Now.
5. Click OK.
Figure 123 Manually upgrading system software
Automatically upgrade device software
· Restrictions and guidelines
Before an automatic upgrade, make sure the cloud connection is connected state. You can view the connection state from the System Tool > Remote Management > Cloud Services page.
· Procedure
1. From the navigation tree, select System Tool > Upgrade.
2. On the Upgrade tab, click Auto upgrade to download the latest software version from the cloud platform for automatic upgrade.
Figure 124 Automatically upgrading system software
Manage files
Upload a file
1. From the navigation tree, select System Tool > Upgrade.
2. Click the File System tab.
Figure 125 File management
3. Click Upload.
4. Click Select File, and select the file to be uploaded.
5. Click Apply.
Figure 126 Uploading a file
Delete files
Restrictions and guidelines
Do not delete the image files being used by the device. If you delete the files, the device cannot operate correctly.
Procedure
1. From the navigation tree, select System Tool > Upgrade.
2. Click the File System tab.
3. Select the file or files to be deleted.
4. Click Delete.
Figure 127 Deleting files
Download files
1. From the navigation tree, select System Tool > Upgrade.
2. Click the File System tab.
3. Select the file or files to be downloaded.
4. Click Download and select the destination path.
License management
About license management
To use a license-based feature on the device, you need to purchase a license key, use it to request an activation file, and install the activation file on the device. To view features that must be licensed, click the Licenses and features tab.
|
|
NOTE: Activation file is also called license file on the Web interface of the device. |
Restrictions and guidelines for license management
Make sure no one else is performing license management tasks while you are managing licenses on the device.
View features that require licenses
1. From the navigation pane, select System Tool > License Management.
2. Click the Licenses and features tab.
3. View the license-based features, licensing status, and license type.
¡ Feature name—Displays the features that must be licensed before being used.
¡ Licensed or Not—Displays the licensing state of the feature.
- N—Not licensed.
- Y—Licensed.
¡ Status—Displays the license type.
- Formal—Purchased license. This state indicates that a valid formal license has been installed.
- Trial—Trial license. This state indicates that a valid trial license has been installed.
- Pre-licensed—Preinstalled license. This state indicates that a valid preinstalled license has been installed.
If the feature is not licensed, this field displays a hyphen (-). To use the feature, you must install a valid license.
Figure 128 Licenses and features
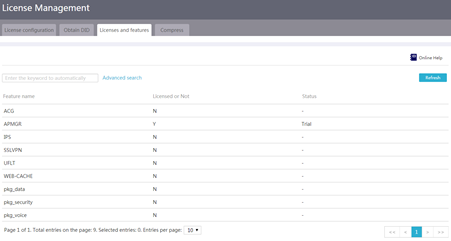
Compress the license storage
About this task
Compress the license storage to delete expired license information. This operation ensures sufficient storage space for installing new licenses.
Restrictions and guidelines
If expired licenses exist on the device, the compression operation will make the DID change. Before performing a compression, make sure all licenses registered with the old DID have been installed. You will be unable to install such licenses after the compression.
Procedure
1. From the navigation pane, select System Tool > License Management.
2. Click the Compress tab.
3. On the page that opens, you can click Compress if the remaining number of allowed activation files is smaller than the number of activation files to be installed.
Remaining number of allowed activation files = Total number of allowed activation files – Number of installed activation files.
4. Click Apply.
Figure 129 Compressing the license storage
Request an activation file
Restrictions and guidelines
Save the activation file properly and back it up to avoid accidental loss or deletion.
Do not modify the name or content of the activation file to avoid licensing failures.
If you cannot obtain the activation file after filling in the correct information on H3C License Management Platform, contact H3C Support.
Prerequisites
Obtain a license key by purchasing a software license certificate.
Procedure
1. From the navigation pane, select System Tool > License Management.
2. Click the Obtain DID tab.
3. Obtain the device SN and DID.
4. Log in to H3C License Management Platform at https://new-licensing.h3c.com/website/anonymous/navIndex/en-US/activate/input-license to obtain the activation file. For more information about requesting an activation file, see H3C Switches and Routers Licensing Guide.
Figure 130 Obtaining the DID
Install a license
1. From the navigation pane, select System Tool > License Management.
2. On the License configuration tab, click Add.
Figure 131 License configuration
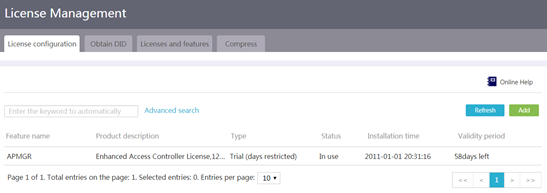
3. In the dialog box that opens, select an activation file, and then click Apply.
Figure 132 Installing a license
Reboot
Introduction to reboot
Perform this task to reboot the device immediately or at a scheduled time.
Reboot now
Restrictions and guidelines
Rebooting the device will cause service interruption. Perform this operation with caution.
Procedure
1. From the navigation pane, select System Tool > Reboot.
Figure 133 Rebooting the device immediately
2. On the Reboot now tab, click Reboot Device.
3. In the dialog box that opens, select one of the following options:
¡ Save running configuration before the reboot.
¡ Force reboot the device immediately without performing any software check.
4. Click Apply.
Figure 134 Rebooting the device
Scheduled reboot
1. From the navigation pane, select System Tool > Reboot.
2. Click the Scheduled reboot tab.
3. In the Scheduled reboot field, select Enable.
4. In the Reboot at field, specify the device reboot time every week.
5. Click Submit. The device will reboot at the scheduled time.
Figure 135 Scheduling the reboot
System log
Introduction to system log
During operation, the device generates system log to record the settings configured by the administrator, device state changes, and important events on the device. Based on the system log, you can monitor device performance and troubleshoot network issues.
You can send the system log to a log server for centralized management or view log entries directly on the webpage.
Logs are classified into eight severity levels from 0 through 7 in descending order of severity, as shown in Table 1.
|
Severity value |
Level |
Description |
|
0 |
Emergency |
The system is unusable. For example, the system authorization has expired. |
|
1 |
Alert |
Action must be taken immediately. For example, traffic on an interface exceeds the upper limit. |
|
2 |
Critical |
Critical condition. For example, the device temperature exceeds the upper limit, the power module fails, or the fan tray fails. |
|
3 |
Error |
Error condition. For example, the link state changes. |
|
4 |
Warning |
Warning condition. For example, an interface is disconnected, or the memory resources are used up. |
|
5 |
Notification |
Normal but significant condition. For example, a terminal logs in to the device, or the device reboots. |
|
6 |
Informational |
Informational message. For example, a command or a ping operation is executed. |
|
7 |
Debugging |
Debugging message. |
Send system log to a log server
Prerequisites
Make sure the device and the log server can reach each other.
Procedure
1. From the navigation pane, select System Tool > System Log.
2. On the System Log tab, select Send to a log server, and then enter the IP address or host name of a log server.
3. Click Apply.
Figure 136 Sending system log to a log server
View system log on the webpage
1. From the navigation pane, select System Tool > System Log.
2. On the System Log tab, log entries are listed with time, level, and description information. You can view specific log entries by specifying the search conditions.
3. Click Export to export the log entries to the PC that you have logged in.
Figure 137 Viewing system log