- Table of Contents
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 01-DPI overview | 56.70 KB |
DPI overview
About DPI
Deep packet inspection (DPI) inspects application layer payloads to protect the network against application layer malicious activities, such as worms, viruses, spams, breaches, and information leakage.
Firewalls operate at the network layer and transport layer. DPI further enhances network security.
DPI functions
DPI provides the following functions:
· Service identification—The DPI engine identifies the service of a data flow by analyzing the application layer payload and matching the payload against signatures. DPI engine informs the DPI service modules of the identification results for service control.
· Service control—DPI service modules control services flexibly by using DPI service policies. Actions that DPI service policies use for data flows include permit, drop, block source, reset, capture, and log.
· Service statistics—DPI provides service statistics about service types, protocol parsing, signature inspection, and packet processing. Service statistics visually display the distribution of data flows and the use of different services. You can find factors that might promote service development or affect network operation.
DPI signature libraries
A DPI signature library is a collection of common signatures that DPI uses for service identification. H3C releases up-to-date signatures in the form of DPI signature library files. You can manually download the files or configure the device to automatically download the files to update the DPI signature libraries. You can also define signatures of your own as required.
DPI signature libraries include the IPS signature library, URL filtering signature library, and APR signature library.
DPI services
Table 1 lists the supported DPI services.
Table 1 DPI services
|
DPI service |
Function |
|
IPS |
Monitors network traffic for malicious activities and proactively takes actions to protect the network against attacks. |
|
URL filtering |
Controls access to the Web resources by filtering the URLs that the users visit. |
|
NBAR |
Identifies the application layer protocols of packets by comparing packet content against signatures. For more information about NBAR, see Security Configuration Guide. |
DPI mechanism
DPI is implemented based on object policies.
Object policy-based DPI mechanism
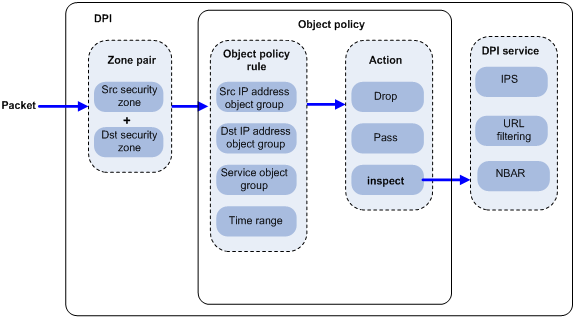
Figure 1 illustrates how object policy-based DPI works.
After receiving a packet in a zone pair, the device compares the packet against the object policy rules contained in the object policy applied to the zone pair.
An object policy rule can contain a set of match criteria, including source IP address, destination IP address, and service type. A packet matches a rule if the packet matches all the criteria in the rule. For information about security zones and zone pairs, see security zone configuration in Security Configuration Guide.
· If no matching object policy rule is found, the device drops the packet.
· If a matching object policy rule is found, the device processes the packet according to the configured rule action:
¡ If the rule action is drop, the device drops the packet.
¡ If the rule action is pass, the device permits the packet to pass.
¡ If the rule action is inspect, the device uses the specified DPI application profile to perform DPI on the packet. If the specified DPI application profile does not exist, the device permits the packet to pass.
Figure 1 Object policy-based DPI mechanism
Restrictions: Hardware compatibility with DPI
|
Hardware |
DPI compatibility |
|
MSR810, MSR810-W, MSR810-W-DB, MSR810-LM, MSR810-W-LM, MSR810-10-PoE, MSR810-LM-HK, MSR810-W-LM-HK, MSR810-LMS-EA |
Yes |
|
MSR810-LMS, MSR810-LUS |
No |
|
MSR2600-6-X1, MSR2600-10-X1 |
Yes |
|
MSR 2630 |
Yes |
|
MSR3600-28, MSR3600-51 |
Yes |
|
MSR3600-28-SI, MSR3600-51-SI |
No |
|
MSR3600-28-X1, MSR3600-28-X1-DP, MSR3600-51-X1, MSR3600-51-X1-DP |
Yes |
|
MSR3610-I-DP, MSR3610-IE-DP |
Yes |
|
MSR3610-X1, MSR3610-X1-DP, MSR3610-X1-DC, MSR3610-X1-DP-DC |
Yes |
|
MSR 3610, MSR 3620, MSR 3620-DP, MSR 3640, MSR 3660 |
Yes |
|
MSR3610-G, MSR3620-G |
Yes |
DPI configuration workflow
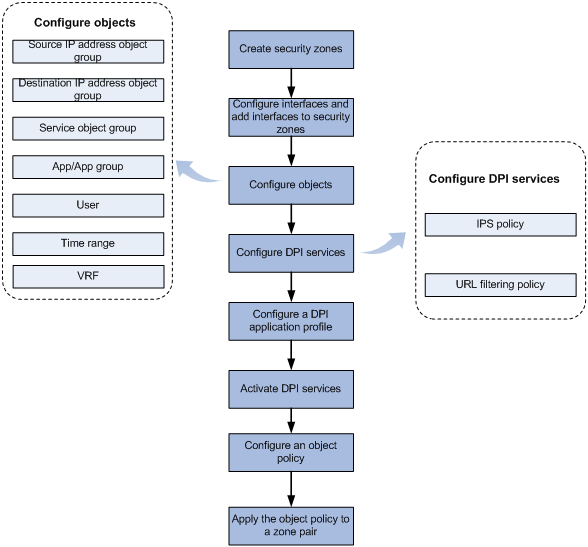
Figure 2 shows the basic configuration workflow for security policy-based DPI.
Figure 2 DPI configuration flow