- Table of Contents
-
- 05-Layer 3 - IP Services Configuration Guide
- 00-Preface
- 01-ARP Configuration
- 02-IP Addressing Configuration
- 03-DHCP Configuration
- 04-DNS Configuration
- 05-NAT Configuration
- 06-IP Performance Optimization Configuration
- 07-Adjacency Table Configuration
- 08-UDP Helper Configuration
- 09-IPv6 Basics Configuration
- 10-DHCPv6 Configuration
- 11-IPv6 DNS Configuration
- 12-NAT-PT Configuration
- 13-Tunneling Configuration
- 14-GRE Configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 01-ARP Configuration | 236.01 KB |
Contents
ARP address resolution process
Configuring a static ARP entry
Configuring the maximum number of dynamic ARP entries for an interface
Setting aging time for dynamic ARP entries
Enabling dynamic ARP entry check
Enabling natural network support for ARP requests
Displaying and maintaining ARP
Static ARP configuration example
Introduction to gratuitous ARP
Displaying and maintaining proxy ARP
Proxy ARP configuration examples
Proxy ARP configuration example
Local proxy ARP configuration example in case of port isolation
ARP overview
ARP function
The Address Resolution Protocol (ARP) is used to resolve an IP address into a physical address (Ethernet MAC address, for example).
In an Ethernet LAN, a router uses ARP to translate the IP address of the next hop to the corresponding MAC address.
ARP message format
ARP messages are classified into ARP requests and ARP replies. Figure 1 shows the format of the ARP request/reply.
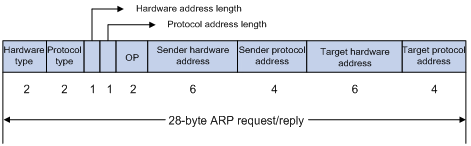
The following explains the fields in Figure 1.
· Hardware type—The hardware address type. The value 1 represents Ethernet.
· Protocol type—The type of the protocol address to be mapped. The hexadecimal value “0x0800” represents IP.
· Hardware address length and protocol address length—Length, in bytes, of a hardware address and a protocol address. For an Ethernet address, the value of the hardware address length field is 6. For an IP(v4) address, the value of the protocol address length field is 4.
· OP—Operation code. The type of ARP message. The value 1 represents an ARP request and 2 represents an ARP reply.
· Sender hardware address—Hardware address of the router sending the message.
· Sender protocol address—Protocol address of the router sending the message.
· Target hardware address—Hardware address of the router the message is being sent to.
· Target protocol address—Protocol address of the router the message is being sent to.
ARP address resolution process
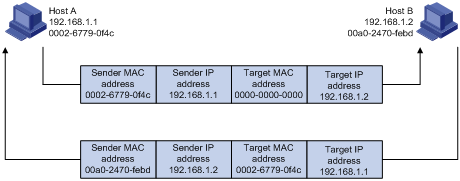
If Host A and Host B are on the same subnet and Host A sends a message to Host B, as show in Figure 2. The resolution process is as follows:
1. Host A looks in its ARP mapping table to see whether there is an ARP entry for Host B. If yes, Host A uses the MAC address in the entry to encapsulate the IP packet into a data link layer frame and sends the frame to Host B.
2. If Host A finds no entry for Host B, Host A buffers the packet and broadcasts an ARP request using the following information:
¡ Source IP address and source MAC address—Host A’s own IP address and MAC address
¡ Target IP address—Host B’s IP address
¡ Target MAC address—An all-zero MAC address
Because the ARP request is sent in broadcast mode, all hosts on this subnet can receive the request, but only the requested host (namely, Host B) will process the request.
3. Host B compares its own IP address with the target IP address in the ARP request. If they are the same, Host B
¡ Adds the sender IP address and sender MAC address to its ARP table.
¡ Encapsulates its MAC address into an ARP reply.
¡ Unicasts the reply to Host A.
4. After receiving the ARP reply, Host A:
¡ Adds the MAC address of Host B to its ARP table.
¡ Encapsulates the MAC address into the IP packet and sends it to Host B.
Figure 2 ARP address resolution process
If Host A and Host B are not on the same subnet:
1. Host A sends an ARP request to the gateway. The target IP address in the ARP request is the IP address of the gateway.
2. After obtaining the MAC address of the gateway from an ARP reply, Host A sends the packet to the gateway.
3. If the gateway maintains the ARP entry of Host B, it forwards the packet to Host B directly; if not, it broadcasts an ARP request, in which the target IP address is the IP address of Host B.
4. After obtaining the MAC address of Host B, the gateway sends the packet to Host B.
ARP table
After obtaining a host’s MAC address, the router adds the IP-to-MAC mapping into its own ARP mapping table. This mapping is used for forwarding packets with the same destination in future.
An ARP table contains dynamic and static ARP entries.
Dynamic ARP entry
A dynamic entry is automatically created and maintained by ARP. It can age out, be updated by a new ARP packet, or be overwritten by a static ARP entry. A dynamic ARP entry is removed when its age timer expires or the interface goes down.
Static ARP entry
A static ARP entry is manually configured and maintained. It does not age out and cannot be overwritten by any dynamic ARP entry.
Static ARP entries protect communication between devices, because attack packets cannot modify the IP-to-MAC mapping in a static ARP entry.
Static ARP entries can be classified into long and short ARP entries.
· A long static ARP entry can be directly used to forward packets. When you configure a long static ARP entry, you must configure a VLAN and outbound interface for the entry besides the IP address and MAC address.
· A short static ARP entry has only an IP address and MAC address configured. If the outbound interface is a Layer 3 Ethernet interface, the short ARP entry can be directly used for forwarding data; if the outbound interface is a VLAN interface, it cannot be directly used for forwarding data. If a short static ARP entry matches an IP packet to be forwarded, the router sends an ARP request. If the source IP and MAC addresses in the received ARP reply are the same as those in the short static ARP entry, the router adds the interface receiving the ARP reply into the short static ARP entry. Then, the entry can be used for forwarding IP packets.
|
|
NOTE: · Usually ARP dynamically generates APR entries without manual intervention. · To allow communication with a host by using a fixed IP-to-MAC mapping, configure a short static ARP entry for it. To allow communication with a host through a specific interface in a specific VLAN by using a fixed IP-to-MAC mapping, configure a long static ARP entry for it. |
Configuring ARP
Configuring a static ARP entry
A static ARP entry is effective when the router works normally. However, when a VLAN or VLAN interface to which a static ARP entry corresponds is deleted, the entry, if long, will be deleted, and if short and resolved, will become unresolved.
To configure a static ARP entry:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Configure a static ARP entry. |
·
Configure a long static ARP entry: ·
Configure a short static ARP entry: |
Use either command. By default, no long or short static ARP entry is configured. |
|
CAUTION: · The vlan-id argument must be the ID of an existing VLAN where the ARP entry resides; the specified Ethernet interface must belong to that VLAN. The VLAN interface of the VLAN must be created. · The IP address of the VLAN interface of the VLAN specified by the vlan-id argument must belong to the same subnet as the IP address specified by the ip-address argument. |
Configuring the maximum number of dynamic ARP entries for an interface
An interface can dynamically learn ARP entries, so it may hold too many ARP entries. To solve this problem, you can set the maximum number of dynamic ARP entries that an interface can learn. When the maximum number is reached, the interface stops learning ARP entries.
To set the maximum number of dynamic ARP entries that an interface can learn:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter Layer 3 Ethernet interface view or VLAN interface view. |
interface interface-type interface-number |
N/A |
|
3. Set the maximum number of dynamic ARP entries that the interface can learn. |
arp max-learning-num number |
The value defaults to 65533 when the system works in SPE or SPC mode and defaults to 16381 when the system works in hybrid mode. For more information about system working modes, see Fundamentals Configuration Guide. If the number argument is set to 0, the interface is disabled from learning dynamic ARP entries. |
Setting aging time for dynamic ARP entries
Each dynamic ARP entry in the ARP table has a limited lifetime, called age timer. The age timer of a dynamic ARP entry is reset each time the dynamic ARP entry is used. Dynamic ARP entries that are not used before expiration are deleted from the ARP table. You can adjust the age timer for dynamic ARP entries according to the actual network condition.
To set aging time for dynamic ARP entries:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Set the aging time for dynamic ARP entries. |
arp timer aging aging-time |
20 minutes by default |
Enabling dynamic ARP entry check
The dynamic ARP entry check function controls whether the router supports dynamic ARP entries with multicast MAC addresses.
When dynamic ARP entry check is enabled, the router cannot learn dynamic ARP entries containing multicast MAC addresses.
When dynamic ARP entry check is disabled, the router can learn dynamic ARP entries containing multicast MAC addresses.
To enable dynamic ARP entry check:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable dynamic ARP entry check. |
arp check enable |
Optional Enabled by default |
Enabling natural network support for ARP requests
This feature enables the router to learn the sender IP and MAC addresses in a received ARP request whose sender IP address is on the same classful network as but a different subnet from the IP address of the receiving interface. A classful network refers to a class A, B, or C network.
For example, VLAN-interface 10 with IP address 10.10.10.5/24 receives an ARP request from 10.11.11.1/8. Because the subnet address calculated by the AND operation of 10.11.11.1 and the receiving interface’s 24-bit subnet mask is not in the subnet 10.10.10.5/24, VLAN-interface 10 cannot process the ARP packet.
With this feature enabled, the router calculates the subnet address by using the default mask of the class A network where 10.10.10.5/24 resides. Because 10.10.10.5/24 is on the same class A network as 10.11.11.1/8, VLAN-interface 10 can learn the sender IP and MAC addresses in the request.
To enable natural mask support for ARP requests:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable the support for ARP requests from a natural network. |
naturemask-arp enable |
Disabled by default |
Displaying and maintaining ARP
|
Task |
Command |
Remarks |
|
Display the ARP entries in the ARP mapping table. |
display arp [ [ all | dynamic | static ] [ slot slot-number ] | vlan vlan-id | interface interface-type interface-number ] [ count | verbose ] [ | { begin | exclude | include } regular-expression ] |
Available in any view |
|
Display the ARP entry for a specified IP address. |
display arp ip-address [ slot slot-number ] [ verbose ] [ | { begin | exclude | include } regular-expression ] |
Available in any view |
|
Display the ARP entries for a specified VPN instance. |
display arp vpn-instance vpn-instance-name [ count ] [ | { begin | exclude | include } regular-expression ] |
Available in any view |
|
Display the aging time for dynamic ARP entries. |
display arp timer aging [ | { begin | exclude | include } regular-expression ] |
Available in any view |
|
Clear ARP entries from the ARP mapping table. |
eset arp { all | dynamic | static | slot slot-number | interface interface-type interface-number } |
Available in user view |
|
|
NOTE: Clearing ARP entries from the ARP table may cause communication failures. |
Static ARP configuration example
Network requirements
As shown in Figure 3, hosts are connected to the device that connects to the router through interface GigabitEthernet 4/1/1. The IP address of the router is 192.168.1.1/24. The MAC address of the router is 00e0-fc01-0000.
To enhance communication security for the device and the router, static ARP entries are configured on the device.
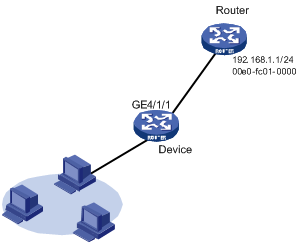
Configuration procedure
# Specify an IP address for interface GigabitEthernet 4/1/1.
<Device> system-view
[Device] interface gigabitethernet 4/1/1
[Device-GigabitEthernet4/1/1] ip address 192.168.1.2 24
# Configure a static ARP entry with IP address 192.168.1.1 and MAC address 00e0-fc01-0000. The outgoing interface corresponding to the static ARP entry is GigabitEthernet 4/1/1.
[Device] arp static 192.168.1.1 00e0-fc01-0000
# View information about static ARP entries.
[Device] display arp static
Type: S-Static D-Dynamic A-Authorized
IP Address MAC Address VLAN ID Interface Aging Type
192.168.1.1 00e0-fc01-0000 N/A N/A N/A S
Introduction to gratuitous ARP
In a gratuitous ARP packet, the sender IP address and the target IP address are both the IP address of the router issuing the packet, the sender MAC address is the MAC address of the router, and the target MAC address is the broadcast address ff:ff:ff:ff:ff:ff.
A router implements the following functions by sending gratuitous ARP packets:
· Determining whether its IP address is already used by another router. If the IP address is already used, the router issuing the gratuitous ARP packet will be informed by an ARP reply of the conflict.
· Informing other routers about the change of its MAC address so that they can update their ARP entries.
Enabling learning of gratuitous ARP packets
With this feature enabled, a router receiving a gratuitous ARP packet adds the sender IP and MAC addresses carried in the packet to its ARP table if no corresponding ARP entry exists. If a corresponding ARP entry is found, the router updates the ARP entry.
After this feature is disabled, the router will use the address information in the received gratuitous ARP packets to update the existing ARP entries only, but not to create new ARP entries.
Configuring periodic sending of gratuitous ARP packets
Enabling a router to periodically send gratuitous ARP packets helps downstream routers update their corresponding ARP entries or MAC entries in time. This feature can be used to:
· Prevent gateway spoofing
If an attacker sends forged gratuitous ARP packets to the hosts on a network, the traffic destined for the gateway from the hosts is sent to the attacker instead. As a result, the hosts cannot access the external network.
To prevent such gateway spoofing attacks, you can enable the gateway to send gratuitous ARP packets containing its primary IP address or one of its manually configured secondary IP addresses at a specific interval. In this way, each host can learn correct gateway address information.
· Prevent ARP entries from being aged out
If network traffic is heavy or the CPU utility is high on a host, ARP packets received may be discarded or cannot be processed in time. Eventually, the dynamic ARP entries on the receiving host will be aged out, and the traffic between the host and the corresponding routers will be interrupted until the host creates the ARP entries again.
To prevent such a problem, you can enable the gateway to send gratuitous ARP packets periodically. The gratuitous ARP packets contain the gateway's primary IP address or one of its manually configured secondary IP addresses. In this way, the receiving host can update ARP entries in time and thus ensure traffic continuity.
· Prevent the virtual IP address of a VRRP group from being used by a host
The master router of a VRRP group can periodically send gratuitous ARP packets to the hosts on the local network, so that the hosts can update local ARP entries and avoid using the virtual IP address of the VRRP group.
If the virtual IP address of the VRRP group is associated with a virtual MAC address, the sender MAC address in the gratuitous ARP packet takes the virtual MAC address of the virtual router. If the virtual IP address of the VRRP group is associated with the real MAC address of an interface, the sender MAC address in the gratuitous ARP packet takes the MAC address of the interface on the master router in the VRRP group.
· Update MAC entries of routers in the VLANs having ambiguous VLAN termination configured
In VRRP configuration, if ambiguous VLAN termination is configured for many VLANs and VRRP groups, interfaces configured with VLAN termination need to be disabled from transmitting broadcast/multicast packets and a VRRP control VLAN needs to be configured so that VRRP advertisements can be transmitted within the control VLAN only. In such cases, you can enable periodic sending of gratuitous ARP packets containing the VRRP virtual IP address, and the primary IP address or a manually configured secondary IP address of the sending interface on the subinterfaces. In this way, when a VRRP failover occurs, routers in the VLANs having ambiguous VLAN termination configured can use the gratuitous ARP packets to update their corresponding MAC entries in time.
|
|
NOTE: For more information about VRRP, see High Availability Configuration Guide. |
Configuring gratuitous ARP
To configure gratuitous ARP:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable learning of gratuitous ARP packets. |
gratuitous-arp-learning enable |
Optional Enabled by default. |
|
3. Enable the router to send gratuitous ARP packets upon receiving ARP requests from another network segment. |
gratuitous-arp-sending enable |
Optional By default, a router does not send gratuitous ARP packets upon receiving ARP requests from another network segment. |
|
4. Enter interface view. |
interface interface-type interface-number |
N/A |
|
5. Enable periodic sending of gratuitous ARP packets and set the sending interval. |
arp send-gratuitous-arp [ interval milliseconds ] |
Disabled by default. |
|
|
NOTE: · You can enable periodic sending of gratuitous ARP packets on a maximum of 1024 interfaces. · Periodic sending of gratuitous ARP packets takes effect only when the link of the enabled interface goes up and an IP address has been assigned to the interface. · If you change the interval for sending gratuitous ARP packets, the configuration is effective at the next sending interval. · The frequency of sending gratuitous ARP packets may be much lower than is expected if this function is enabled on multiple interfaces, or each interface is configured with multiple secondary IP addresses, or a small sending interval is configured in the preceding cases. |
Proxy ARP overview
If a host sends an ARP request for the MAC address of another host that actually resides on another network (but the sending host considers the requested host is on the same network) or that is isolated from the sending host at Layer 2, the router in between must be able to respond to the request with the MAC address of the receiving interface to allow Layer 3 communication between the two hosts. This is achieved by proxy ARP. Proxy ARP hides the physical details of the network.
Proxy ARP involves common proxy ARP and local proxy ARP, which are described in the following sections.
|
|
NOTE: The term proxy ARP in the following sections of this chapter refers to common proxy ARP unless otherwise specified. |
Proxy ARP
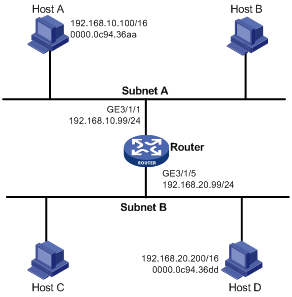
A proxy ARP enabled router allows hosts that reside on different subnets to communicate.
As shown in Figure 4, Router connects to two subnets through GigabitEthernet 4/1/1 and GigabitEthernet 4/1/2. The IP addresses of the two interfaces are 192.168.10.99/24 and 192.168.20.99/24. Host A and Host B have the same prefix 192.168.0.0 assigned and connect to GigabitEthernet 4/1/1 and GigabitEthernet 4/1/2, respectively.
Figure 4 Application environment of proxy ARP
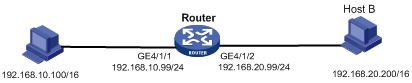
Because Host A considers that Host B is on the same network, it broadcasts an ARP request for the MAC address of Host B. Host B, however, cannot receive this request because it is in a different broadcast domain.
You can enable proxy ARP on Router so that Router can reply to the ARP request from Host A with the MAC address of GigabitEthernet 4/1/1, and forward packets sent from Host A to Host B. In this case, Router seems like a proxy of Host B.
A main advantage of proxy ARP is that you can enable it on a single router without disturbing routing tables of other routers in the network. Proxy ARP acts as the gateway for IP hosts that are not configured with a default gateway or do not have routing capability.
Local proxy ARP
As shown in Figure 5, Host A and Host B belong to VLAN 2, but are isolated at Layer 2. Host A connects to GigabitEthernet 3/1/3 while Host B connects to GigabitEthernet 3/1/1. Enable local proxy ARP on Router to allow Layer 3 communication between the two hosts.
Figure 5 Application environment of local proxy ARP
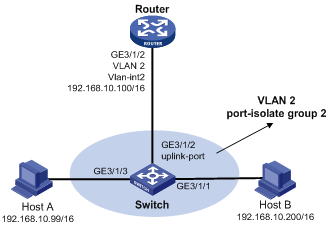
In one of the following cases, you need to enable local proxy ARP:
· Hosts connecting to different isolated Layer 2 ports in the same VLAN need to communicate at Layer 3.
· If a super VLAN is configured, hosts in different sub VLANs of the super VLAN need to communicate at Layer 3.
· If an isolate-user-VLAN is configured, hosts in different secondary VLANs of the isolate-user-VLAN need to communicate at Layer 3.
Enabling proxy ARP
To enable proxy ARP in VLAN interface view/Layer 3 Ethernet interface view/Layer 3 Ethernet subinterface view/Layer 3 aggregate interface view/Layer 3 aggregate subinterface view:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter interface view. |
interface interface-type interface-number |
N/A |
|
3. Enable proxy ARP. |
proxy-arp enable |
Disabled by default |
To enable local proxy ARP in VLAN interface view/Layer 3 Ethernet interface view/Layer 3 aggregate interface view:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter interface view. |
interface interface-type interface-number |
N/A |
|
3. Enable local proxy ARP. |
local-proxy-arp enable [ ip-range startIP to endIP ] |
Disabled by default |
Displaying and maintaining proxy ARP
|
Task |
Command |
Remarks |
|
Display whether proxy ARP is enabled. |
display proxy-arp [ interface interface-type interface-number ] [ | { begin | exclude | include } regular-expression ] |
Available in any view |
|
Display whether local proxy ARP is enabled. |
display local-proxy-arp [ interface interface-type interface-number ] [ | { begin | exclude | include } regular-expression ] |
Available in any view |
Proxy ARP configuration examples
Proxy ARP configuration example
Network requirements
As shown in Figure 6, Host A and Host D have the same prefix and mask (the IP addresses of Host A and Host D are 192.168.10.100/16 and 192.168.20.200/16 respectively, and the two IP addresses belong to the same network 192.168.0.0/16), but they are located on different subnets separated through the router. As a result, Host D cannot receive or respond to any ARP request from Host A.
You need to configure proxy ARP on the router to enable communication between Host A and Host D.
Configuration procedure
# Specify an IP address for interface GigabitEthernet 3/1/1.
<Router> system-view
[Router] interface gigabitethernet 3/1/1
[Router-GigabitEthernet3/1/1] ip address 192.168.10.99 255.255.255.0
# Enable proxy ARP on interface GigabitEthernet 3/1/1.
[Router-GigabitEthernet3/1/1] proxy-arp enable
[Router-GigabitEthernet3/1/1] quit
# Specify an IP address for interface GigabitEthernet 3/1/5.
[Router] interface gigabitethernet 3/1/5
[Router-GigabitEthernet3/1/5] ip address 192.168.20.99 255.255.255.0
# Enable proxy ARP on interface GigabitEthernet 3/1/5.
[Router-GigabitEthernet3/1/5] proxy-arp enable
[Router-GigabitEthernet3/1/5] quit
After the configuration, use the ping command to verify that Host A and Host D can ping each other.
Local proxy ARP configuration example in case of port isolation
Network requirements
As shown in Figure 7, Host A and Host B belong to the same VLAN, and are connected to GigabitEthernet 3/1/1 and GigabitEthernet 3/1/2 of Switch respectively. The switch is connected to Router via GigabitEthernet 3/1/3.
Configure port isolation on GigabitEthernet 3/1/1 and GigabitEthernet 3/1/2 to isolate Host A from Host B at Layer 2. Enable local proxy ARP on the router to allow communication between Host A and Host B at Layer 3.
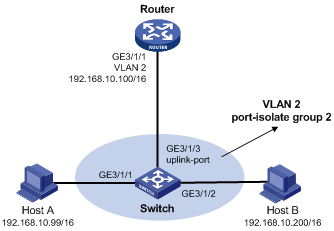
|
|
NOTE: In this configuration example, the switch blocks all traffic between hosts. Therefore, you need to configure local proxy ARP on interface GigabitEthernet 3/1/1 of the router to allow communication between Host A and Host B. If the two interfaces (GigabitEthernet 3/1/1 and GigabitEthernet 3//1/2) on the switch are isolated only at Layer 2, you can enable communication between the two hosts by configuring local proxy ARP on VLAN-interface 2 of the switch. |
Configuration procedure
1. Configure the Switch:
# Add GigabitEthernet 3/1/1, GigabitEthernet 3/1/2 and GigabitEthernet 3/1/3 to VLAN 2. Host A and Host B are isolated and unable to exchange Layer 2 packets.
<Switch> system-view
[Switch] port-isolate group 2
[Switch] vlan 2
[Switch-vlan2] port gigabitethernet 3/1/1
[Switch-vlan2] port gigabitethernet 3/1/2
[Switch-vlan2] port gigabitethernet 3/1/3
[Switch-vlan2] quit
[Switch] interface gigabitethernet 3/1/1
[Switch-GigabitEthernet3/1/1] port-isolate enable group 2
[Switch-GigabitEthernet3/1/1] quit
[Switch] interface gigabitethernet 3/1/2
[Switch-GigabitEthernet3/1/2] port-isolate enable group 2
[Switch-GigabitEthernet3/1/2] quit
[Switch] interface gigabitethernet 3/1/3
[Switch-GigabitEthernet3/1/3] port-isolate uplink-port group 2
2. Configure the Router:
# Specify an IP address for GigabitEthernet 3/1/1.
<Router> system-view
[Router] interface GigabitEthernet 3/1/1
[Router-GigabitEthernet3/1/1] ip address 192.168.10.100 255.255.255.0
Ping Host B on Host A to verify that the two hosts cannot be pinged through, which indicates they are isolated at Layer 2.
# Configure local proxy ARP to let Host A and Host B communicate at Layer 3.
[Router-GigabitEthernet3/1/1] local-proxy-arp enable
[Router-GigabitEthernet3/1/1] quit
The ping operation from Host A to Host B is successful after the configuration.
