- Table of Contents
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 01-Basic VXLAN configuration | 376.58 KB |
Generic VXLAN network establishment and forwarding process
VXLAN tunnel establishment and assignment
Assignment of traffic to VXLANs
Configuring basic VXLAN features
Restrictions and guidelines: VXLAN configuration
Setting the forwarding mode for VXLANs
Manually creating a VXLAN tunnel
Manually assigning VXLAN tunnels to a VXLAN
Assigning customer frames to a VSI
Mapping an Ethernet service instance to a VSI
About MAC address entry management
Configuring static MAC address entries
Disabling remote-MAC address learning
Setting the destination UDP port number of VXLAN packets
Enabling default VXLAN decapsulation
Enabling ARP flood suppression
Verifying and maintaining VXLANs
Verifying VXLAN tunnel configuration and running status
Displaying information about Ethernet service instances
Verifying and maintaining VSIs
VXLAN overview
Virtual eXtensible LAN (VXLAN) is a MAC-in-UDP technology that provides Layer 2 connectivity between distant network sites across an IP network. VXLAN is typically used in data centers and the access layer of campus networks for multitenant services.
VXLAN benefits
VXLAN provides the following benefits:
· Support for more virtual switched domains than VLANs—Each VXLAN is uniquely identified by a 24-bit VXLAN ID. The total number of VXLANs can reach 16777216 (224). This specification makes VXLAN a better choice than 802.1Q VLAN to isolate traffic for user terminals.
· Easy deployment and maintenance—VXLAN requires deployment only on the edge devices of the transport network. Devices in the transport network perform typical Layer 3 forwarding.
VXLAN network model
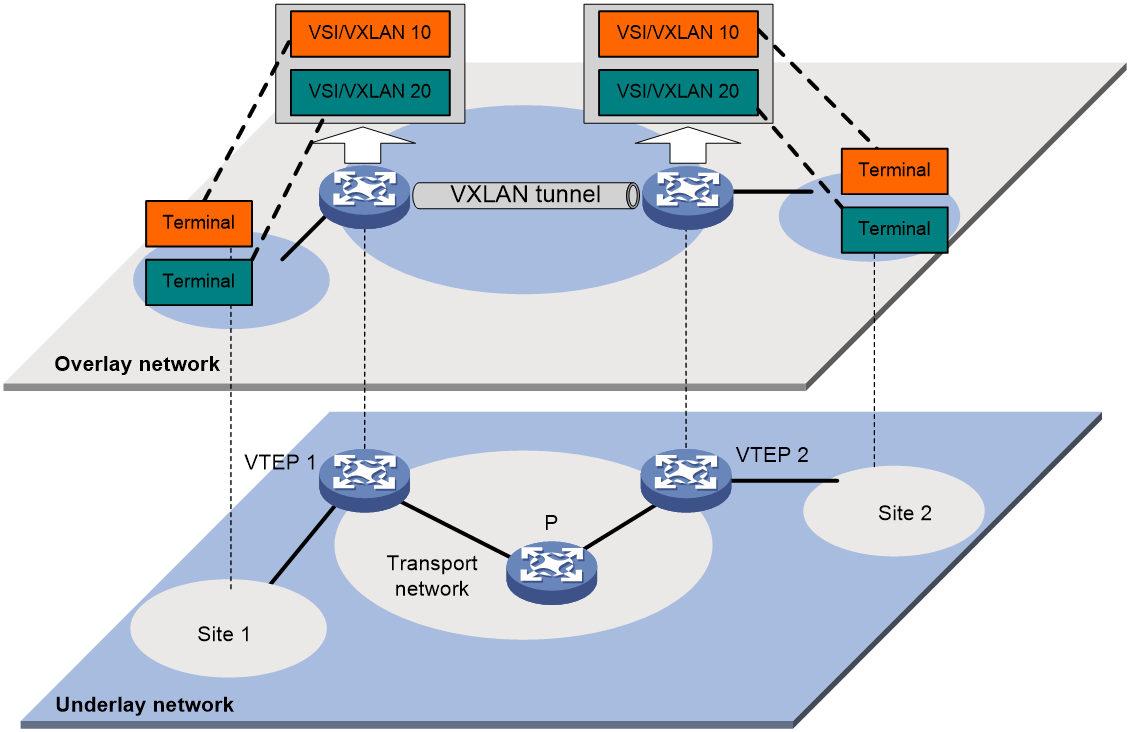
As shown in Figure 1, a VXLAN is a virtual Layer 2 network (known as the overlay network) built on top of an existing physical Layer 3 network (known as the underlay network). The overlay network encapsulates inter-site Layer 2 frames into VXLAN packets and forwards the packets to the destination along the Layer 3 forwarding paths provided by the underlay network. The underlay network is transparent to tenants, and geographically dispersed sites of a tenant are merged into a Layer 2 network.
The transport edge devices assign user terminals to different VXLANs, and then forward traffic between sites for user terminals by using VXLAN tunnels. Supported user terminals include PCs, wireless terminals, and VMs on servers.
|
|
NOTE: This document uses VMs as examples to describe the mechanisms of VXLAN. The mechanisms do not differ between different kinds of user terminals. |
The transport edge devices are VXLAN tunnel endpoints (VTEP). The VTEP implementation of the device uses ACs, VSIs, and VXLAN tunnels to provide VXLAN services.
· VSI—A virtual switch instance is a virtual Layer 2 switched domain. Each VSI provides switching services only for one VXLAN. VSIs learn MAC addresses and forward frames independently of one another. VMs in different sites have Layer 2 connectivity if they are in the same VXLAN.
· Attachment circuit (AC)—An AC is a physical or virtual link that connects a VTEP to a local site. Typically, ACs are Ethernet service instances that are associated with the VSI of a VXLAN. Traffic received from an AC is assigned to the VSI associated with the AC. Ethernet service instances are created on site-facing Layer 2 interfaces. An Ethernet service instance matches a list of custom VLANs by using a frame match criterion.
· VXLAN tunnel—Logical point-to-point tunnels between VTEPs over the transport network. Each VXLAN tunnel can trunk multiple VXLANs.
VTEPs encapsulate VXLAN traffic in the VXLAN, outer UDP, and outer IP headers. The devices in the transport network forward VXLAN traffic only based on the outer IP header.
Figure 1 VXLAN network model
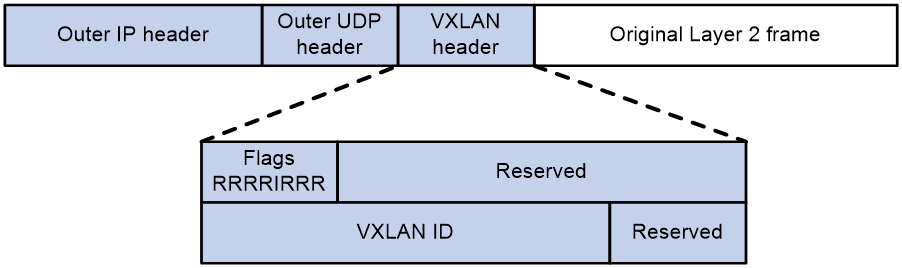
VXLAN packet format
As shown in Figure 2, a VTEP encapsulates a frame in the following headers:
· 8-byte VXLAN header—VXLAN information for the frame.
¡ Flags—If the I bit is 1, the VXLAN ID is valid. If the I bit is 0, the VXLAN ID is invalid. All other bits are reserved and set to 0.
¡ 24-bit VXLAN ID—Identifies the VXLAN of the frame. It is also called the virtual network identifier (VNI).
· 8-byte outer UDP header for VXLAN—The default VXLAN destination UDP port number is 4789.
· 20-byte outer IP header—Valid addresses of VTEPs or VXLAN multicast groups on the transport network. Devices in the transport network forward VXLAN packets based on the outer IP header.
Figure 2 VXLAN packet format
VXLAN working mechanisms
Generic VXLAN network establishment and forwarding process
The VTEP uses the following process to establish the VXLAN network and forward an inter-site frame:
1. Discovers remote VTEPs, establishes VXLAN tunnels, and assigns the VXLAN tunnels to VXLANs.
2. Assigns the frame to its matching VXLAN if the frame is sent between sites.
3. Performs MAC learning on the VXLAN's VSI.
4. Forwards the frame through VXLAN tunnels.
This section describes this process in detail. For intra-site frames in a VSI, the system performs typical Layer 2 forwarding, and it processes 802.1Q VLAN tags as described in "Access modes of VSIs."
VXLAN tunnel establishment and assignment
To provide Layer 2 connectivity for a VXLAN between two sites, you must create a VXLAN tunnel between the sites and assign the tunnel to the VXLAN.
VXLAN tunnel establishment
VXLAN supports manual and automatic VXLAN tunnel establishment.
· Manual creation—Manually create a VXLAN tunnel interface, and specify the tunnel source and destination IP addresses on the peer VTEPs.
· Automatic creation—Configure Ethernet Virtual Private Network (EVPN) to automatically discover VTEPs and set up VXLAN tunnels. For more information about EVPN, see EVPN Configuration Guide.
VXLAN tunnel assignment
VXLAN supports manual and automatic VXLAN tunnel assignment.
· Manual assignment—Manually assign VXLAN tunnels to VXLANs.
· Automatic assignment—Run EVPN to automatically assign VXLAN tunnels to VXLANs. For more information about EVPN, see EVPN Configuration Guide.
Assignment of traffic to VXLANs
Traffic from the local site to a remote site
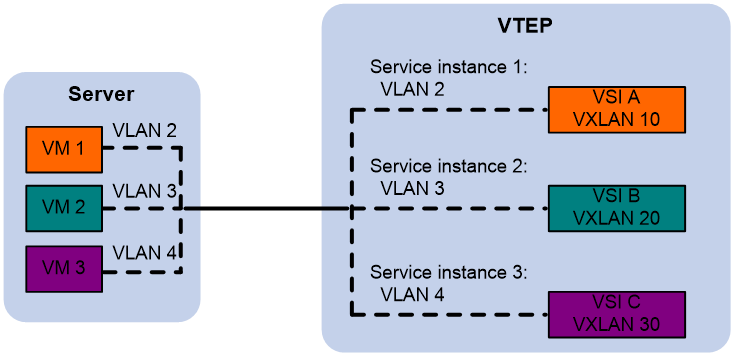
The VTEP uses Ethernet service instance-to-VSI mapping to assign customer frames to a VXLAN. This method uses the frame match criterion of an Ethernet service instance to match a list of VLANs on a site-facing Layer 2 interface. The frame match criterion specifies the characteristics of traffic from the VLANs, such as tagging status and VLAN IDs. The VTEP assigns customer traffic to a VXLAN by mapping the Ethernet service instance to a VSI.
As shown in Figure 3, Ethernet service instance 1 matches VLAN 2 and is mapped to VSI A (VXLAN 10). When a frame from VLAN 2 arrives, the VTEP assigns the frame to VXLAN 10, and looks up VSI A's MAC address table for the outgoing interface.
Figure 3 Identifying traffic from the local site
Traffic from a remote site to the local site
When a frame arrives at a VXLAN tunnel, the VTEP uses the VXLAN ID in the frame to identify its VXLAN.
MAC learning
The VTEP performs source MAC learning on the VSI as a Layer 2 switch.
· For traffic from the local site to the remote site, the VTEP learns the source MAC address before VXLAN encapsulation.
· For traffic from the remote site to the local site, the VTEP learns the source MAC address after removing the VXLAN header.
A VSI's MAC address table includes the following types of MAC address entries:
· Local MAC—MAC entries learned from the local site. The outgoing interfaces for the MAC address entries are site-facing interfaces.
¡ Static—Manually added MAC entries.
¡ Dynamic—Dynamically learned MAC entries.
· Remote MAC—MAC entries learned from a remote site, including static and dynamic MAC entries. The outgoing interfaces for the MAC addresses are VXLAN tunnel interfaces.
¡ Static—Manually added MAC entries.
¡ Dynamic—MAC entries learned in the data plane from incoming traffic on VXLAN tunnels. The learned MAC addresses are contained in the inner Ethernet header.
¡ BGP EVPN—MAC entries advertised through BGP EVPN. For more information, see EVPN Configuration Guide.
The following shows the priority order of different types of remote MAC address entries:
a. Static MAC address entries.
b. MAC address entries advertised through BGP EVPN.
c. Dynamic MAC address entries.
Unicast forwarding
Intra-site unicast forwarding
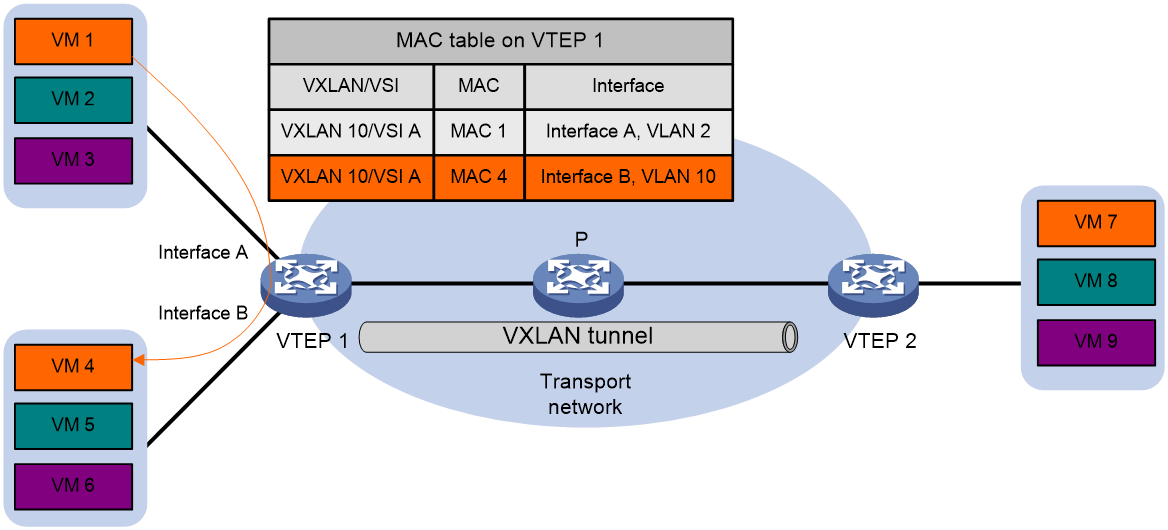
The VTEP uses the following process to forward a known unicast frame within a site:
1. Identifies the VSI of the frame.
2. Looks up the destination MAC address in the VSI's MAC address table for the outgoing interface.
3. Sends the frame out of the matching outgoing interface.
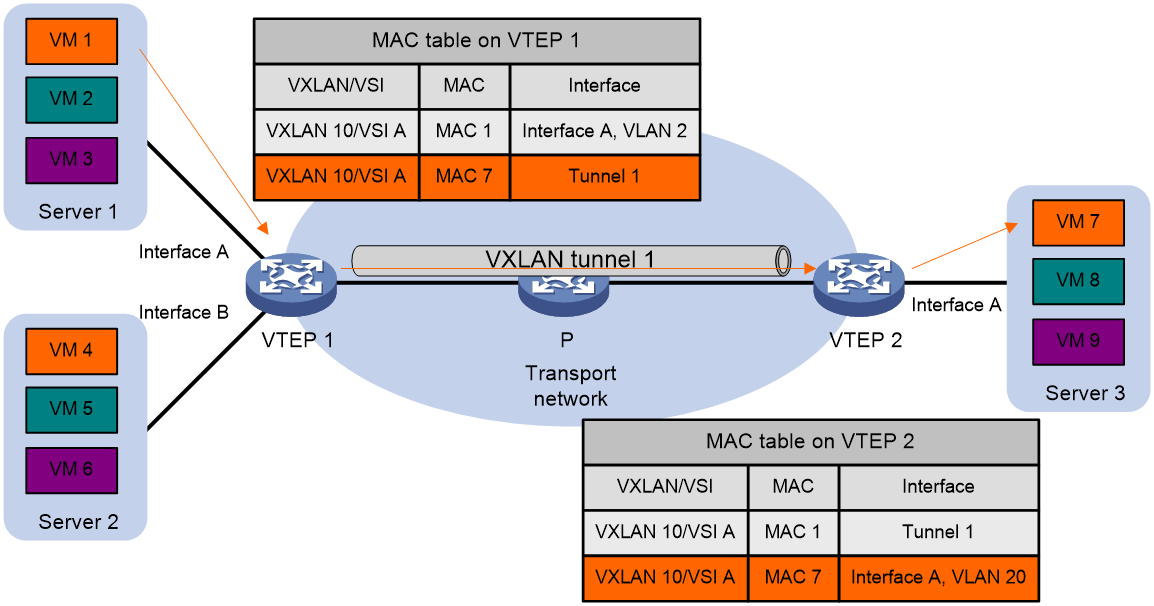
As shown in Figure 4, VTEP 1 forwards a frame from VM 1 to VM 4 within the local site in VLAN 10 as follows:
4. Identifies that the frame belongs to VSI A when the frame arrives at Interface A.
5. Looks up the destination MAC address (MAC 4) in the MAC address table of VSI A for the outgoing interface.
6. Sends the frame out of the matching outgoing interface (Interface B) to VM 4 in VLAN 10.
Inter-site unicast forwarding
The following process (see Figure 5) applies to a known unicast frame between sites:
1. The source VTEP encapsulates the Ethernet frame in the VXLAN/UDP/IP header.
In the outer IP header, the source IP address is the source VTEP's VXLAN tunnel source IP address. The destination IP address is the VXLAN tunnel destination IP address.
2. The source VTEP forwards the encapsulated packet out of the outgoing VXLAN tunnel interface found in the VSI's MAC address table.
3. The intermediate transport devices (P devices) forward the frame to the destination VTEP by using the outer IP header.
4. The destination VTEP removes the headers on top of the inner Ethernet frame. It then performs MAC address table lookup in the VXLAN's VSI to forward the frame out of the matching outgoing interface.
Flood
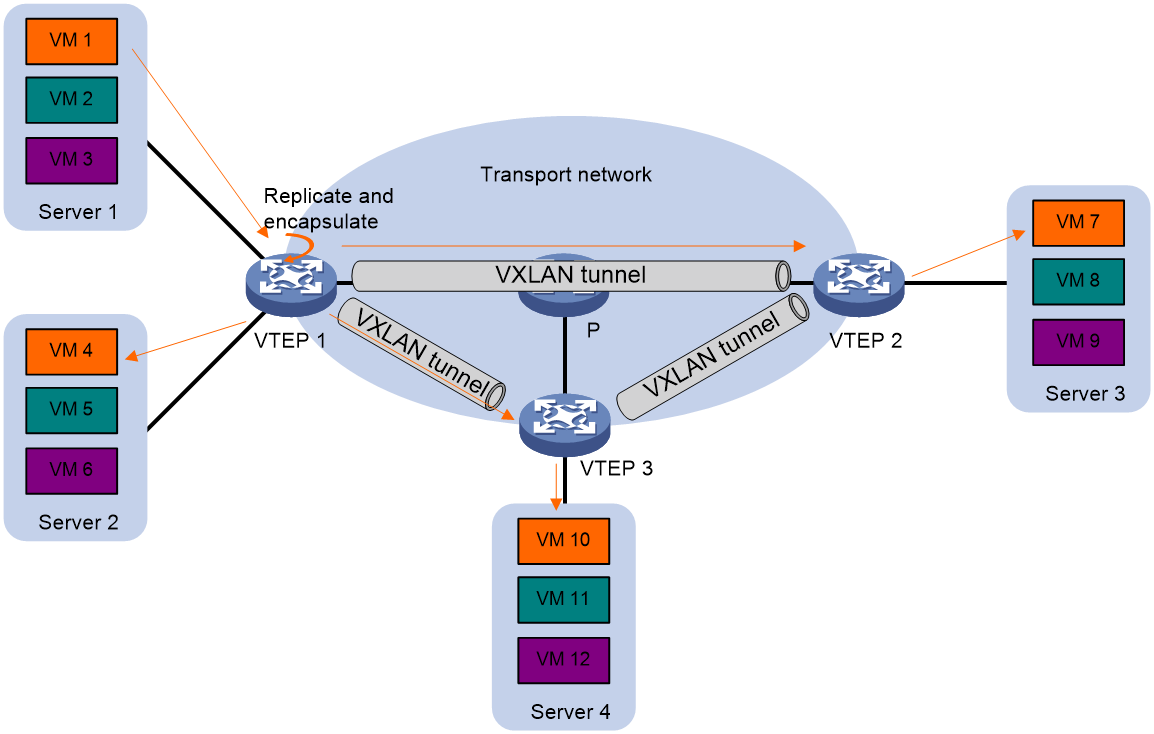
The source VTEP floods a broadcast, multicast, or unknown unicast frame to all site-facing interfaces and VXLAN tunnels in the VXLAN, except for the incoming interface. Each destination VTEP floods the inner Ethernet frame to all site-facing interfaces in the VXLAN. To avoid loops, the destination VTEPs do not flood the frame back to VXLAN tunnels.
VXLAN supports unicast mode (also called head-end replication) for flood traffic.
Unicast mode (head-end replication)
As shown in Figure 6, the source VTEP replicates the flood frame, and then sends one replica to the destination IP address of each VXLAN tunnel in the VXLAN.
Access modes of VSIs
The access mode of a VSI determines how the VTEP processes the 802.1Q VLAN tags in the Ethernet frames. The S9825 switch series does not support the Ethernet access mode.
VLAN access mode
In this mode, Ethernet frames received from or sent to the local site must contain 802.1Q VLAN tags.
· For an Ethernet frame received from the local site, the VTEP removes all its 802.1Q VLAN tags before forwarding the frame.
· For an Ethernet frame destined for the local site, the VTEP adds 802.1Q VLAN tags to the frame before forwarding the frame.
In VLAN access mode, VXLAN packets sent between sites do not contain 802.1Q VLAN tags. You can use different 802.1Q VLANs to provide the same service in different sites.
Ethernet access mode
The VTEP does not process the 802.1Q VLAN tags of Ethernet frames received from or sent to the local site.
· For an Ethernet frame received from the local site, the VTEP forwards the frame with the 802.1Q VLAN tags intact.
· For an Ethernet frame destined for the local site, the VTEP forwards the frame without adding 802.1Q VLAN tags.
In Ethernet access mode, VXLAN packets sent between VXLAN sites contain 802.1Q VLAN tags. You must use the same VLAN to provide the same service between sites.
ARP and ND flood suppression
ARP or ND flood suppression reduces ARP request broadcasts or ND request multicasts by enabling the VTEP to reply to ARP or ND requests on behalf of VMs.
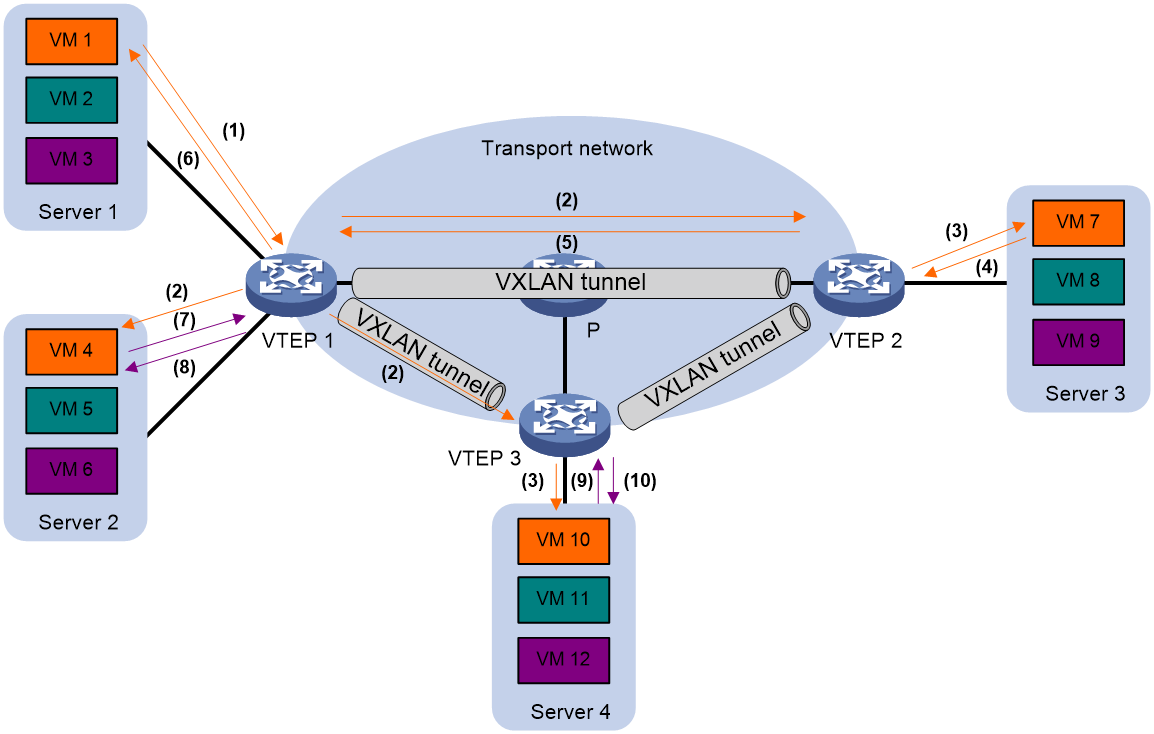
As shown in Figure 7, this feature snoops ARP or ND packets to populate the ARP or ND flood suppression table with local and remote MAC addresses. If an ARP or ND request has a matching entry, the VTEP replies to the request on behalf of the VM. If no match is found, the VTEP floods the request to both local and remote sites.
Figure 7 ARP and ND flood suppression
The following uses ARP flood suppression as an example to explain the flood suppression workflow:
1. VM 1 sends an ARP request to obtain the MAC address of VM 7.
2. VTEP 1 creates a suppression entry for VM 1, and floods the ARP request in the VXLAN.
3. VTEP 2 and VTEP 3 de-encapsulate the ARP request. The VTEPs create a suppression entry for VM 1, and broadcast the request in the local site.
4. VM 7 sends an ARP reply.
5. VTEP 2 creates a suppression entry for VM 7 and forwards the ARP reply to VTEP 1.
6. VTEP 1 de-encapsulates the ARP reply, creates a suppression entry for VM 7, and forwards the ARP reply to VM 1.
7. VM 4 sends an ARP request to obtain the MAC address of VM 1 or VM 7.
8. VTEP 1 creates a suppression entry for VM 4 and replies to the ARP request.
9. VM 10 sends an ARP request to obtain the MAC address of VM 1.
10. VTEP 3 creates a suppression entry for VM 10 and replies to the ARP request.
VXLAN IP gateways
A VXLAN IP gateway provides Layer 3 forwarding services for VMs in VXLANs. A VXLAN IP gateway can be an independent device or be collocated with a VTEP. For more information about VXLAN IP gateway placement, see "Configuring VXLAN IP gateways."
VXLAN M-LAG
|
IMPORTANT: VXLAN M-LAG supports only IPv4 sites and IPv4 underlay networks. |
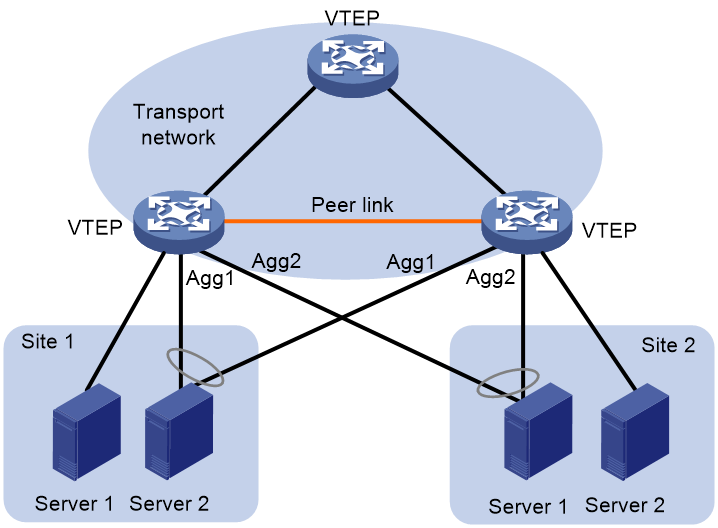
About VXLAN M-LAG
As shown in Figure 8, VXLAN M-LAG virtualizes two VTEPs or VXLAN IP gateways into one M-LAG system through Multichassis Link Aggregation (M-LAG) to avoid single points of failure. The VTEPs or VXLAN IP gateways are called M-LAG member devices. For more information about M-LAG, see Layer 2—LAN Switching Configuration Guide.
Figure 8 VXLAN M-LAG
VM reachability information synchronization
To ensure VM reachability information consistency in the M-LAG system, the M-LAG member devices synchronize MAC address entries and ARP information with each other through a peer link. A peer link can only be an Ethernet aggregate link.
|
IMPORTANT: The VXLAN tunnel that acts as the peer link is automatically associated with all VXLANs on each M-LAG member device. |
Virtual VTEP address
The M-LAG member devices use the same IP address to set up VXLAN tunnels with remote VTEPs or VXLAN IP gateways.
Dual-homed ACs
As shown in Figure 8, a VM is dual-homed to the VTEPs in an M-LAG system through Ethernet links. The Ethernet links connected to the same VM are aggregated into one Layer 2 aggregation group across VTEPs. On the corresponding Layer 2 aggregate interface, Ethernet service instances are configured as ACs of VXLANs to match customer traffic. These ACs are dual-homed ACs.
· The site-facing link backup mechanism is as follows:
When a site-facing AC is configured on a VTEP, the VTEP automatically creates an AC on the peer link with the same traffic match criterion as the site-facing AC. Then, it maps the automatically created AC to the VSI of the site-facing AC. When the site-facing AC is down, traffic sent to the AC is forwarded to the other VTEP through the peer link. This mechanism ensures service continuity in case of AC failure.
Communication between single-homed ACs
An AC that is attached to only one of the VTEPs in an M-LAG system is called a single-homed AC. Two single-homed ACs attached to different VTEPs communicate through the peer link.
· The traffic forwarding mechanism is as follows:
When a single-homed AC is configured on a VTEP, the VTEP automatically creates an AC on the peer link with the same traffic match criterion as the single-homed AC. Then, it maps the automatically created AC to the VSI of the single-homed AC. When receiving traffic from the single-homed AC, the VTEP sends the traffic to the other VTEP through the peer link. Then, the other VTEP identifies the VSI of the traffic and forwards it.
Protocols and standards
RFC 7348, Virtual eXtensible Local Area Network (VXLAN): A Framework for Overlaying Virtualized Layer 2 Networks over Layer 3 Networks
Configuring basic VXLAN features
Restrictions and guidelines: VXLAN configuration
When the hardware resource mode is set to MAC mode, the device does not support VXLAN. For more information about hardware resource modes, see hardware resource management configuration in System Management Configuration Guide.
Ethernet service instances do not support the spanning tree feature. With the spanning tree feature enabled on an interface where an Ethernet service instance resides, the Ethernet service instance cannot change its state (for example, change to blocking state or keep the forwarding state) based on the spanning tree calculation result.
The S9825 switch series has the following restrictions:
· On a device without VXLAN configured, any packets with VXLAN encapsulation received from a Layer 3 Ethernet/aggregate interface/subinterface will be dropped and cannot be forwarded based on the outer encapsulation of VXLAN.
· When a VXLAN tunnel decapsulates packets, the inner priority information might be lost. To avoid this issue, execute the qos trust dscp or qos trust dot1p command on the VXLAN tunnel source interface. For more information about the qos trust command, see ACL and QoS Command Reference.
· Do not configure the following features in a VXLAN network:
¡ QoS features in MQC method on VSIs. For more information about QoS, see ACL and QoS Configuration Guide.
¡ Mirroring packets to a VXLAN tunnel. For more information about mirroring, see Network Management and Monitoring Configuration Guide.
¡ INT. For more information about INT, see Telemetry Configuration Guide.
¡ Loop detection. For more information about loop detection, see loop detection configuration in Layer 2—LAN Switching Configuration Guide.
¡ Setting the next hop for policy-based routing to the address of a VXLAN tunnel interface. For more information about policy-based routing, see policy-based routing configuration and IPv6 policy-based routing configuration in Layer 3—IP Routing Configuration Guide.
VXLAN tasks at a glance
To configure basic VXLAN settings, perform the following tasks on VTEPs:
1. Setting the forwarding mode for VXLANs
4. Manually assigning VXLAN tunnels to a VXLAN
5. Assigning customer frames to a VSI
6. (Optional.) Managing MAC address entries
¡ Configuring static MAC address entries
¡ Disabling remote-MAC address learning
7. Setting the destination UDP port number of VXLAN packets
8. (Optional.) Reducing flood traffic in the transport network
¡ Disabling flooding for a VSI
¡ Enabling ARP flood suppression
¡ Enabling ND flood suppression
9. (Optional.) Configuring VXLAN M-LAG
Prerequisites for VXLAN
Configure a routing protocol on the devices in the transport network to make sure the VTEPs can reach one another.
Setting the forwarding mode for VXLANs
About this task
A VXLAN tunnel supports the following modes:
· Layer 3 forwarding mode—The device uses the ARP table (IPv4 network) or ND table (IPv6 network) to forward traffic for VXLANs.
· Layer 2 forwarding mode—The device uses the MAC address table to forward traffic for VXLANs.
If the device is a VTEP, enable Layer 2 forwarding for VXLANs. If the device is a VXLAN IP gateway, enable Layer 3 forwarding for VXLANs. For more information about VXLAN IP gateways, see "Configuring VXLAN IP gateways."
If you enable Layer 3 forwarding for VXLANs, the tagging status of VXLAN packets is not determined by the link type of the outgoing interface. You must use this command to set the tagging mode of VXLAN packets.
· Set the tagging mode to untagged if the following requirements are met:
¡ The link type of the outgoing interface is access, trunk, or hybrid.
¡ VXLAN packets are transmitted to the next hop through the PVID of the outgoing interface.
· Set the tagging mode to tagged if the following requirements are met:
¡ The link type of the outgoing interface is trunk or hybrid.
¡ VXLAN packets are transmitted to the next hop through a VLAN other than the PVID of the outgoing interface.
Restrictions and guidelines
You must delete all VSIs, VSI interfaces, and VXLAN tunnel interfaces before you can change the forwarding mode. As a best practice, finish VXLAN network planning and determine the VXLAN forwarding mode of each device before your configuration, and set the VXLAN forwarding mode before other VXLAN settings.
You must delete all VXLAN tunnel interfaces before you can change the tagging mode of VXLAN packets.
Procedure
1. Enter system view.
system-view
2. Set the forwarding mode of VXLANs.
¡ Enable Layer 2 forwarding.
undo vxlan ip-forwarding
¡ Enable Layer 3 forwarding.
vxlan ip-forwarding [ tagged | untagged ]
By default, Layer 3 forwarding is enabled for VXLANs.
Creating a VXLAN on a VSI
1. Enter system view.
system-view
2. Enable L2VPN.
l2vpn enable
By default, L2VPN is disabled.
3. Create a VSI and enter VSI view.
vsi vsi-name
4. Enable the VSI.
undo shutdown
By default, a VSI is enabled.
5. Create a VXLAN and enter VXLAN view.
vxlan vxlan-id
You can create only one VXLAN on a VSI.
The VXLAN ID must be unique for each VSI.
6. (Optional.) Configure VSI parameters:
a. Return to VSI view.
quit
b. Configure a VSI description.
description text
By default, a VSI does not have a description.
c. Set the MTU for the VSI.
mtu size
The default MTU for a VSI is 1500 bytes.
d. Enable MAC address learning for the VSI.
mac-learning enable
By default, MAC address learning is enabled for a VSI.
Configuring a VXLAN tunnel
Manually creating a VXLAN tunnel
About this task
When you manually create a VXLAN tunnel, specify addresses on the local VTEP and the remote VTEP as the tunnel source and destination addresses, respectively.
Restrictions and guidelines
As a best practice, do not configure multiple VXLAN tunnels to use the same source and destination IP addresses.
Make sure the following VXLAN tunnels are not associated with the same VXLAN when they have the same tunnel destination IP address:
· A VXLAN tunnel automatically created by EVPN.
· A manually created VXLAN tunnel.
For more information about EVPN, see EVPN Configuration Guide.
This task provides basic VXLAN tunnel configuration. For more information about tunnel interface configuration and commands, see Interface Configuration Guide and Interface Command Reference.
Procedure
1. Enter system view.
system-view
2. (Optional.) Specify a global source IP address for VXLAN tunnels.
tunnel global source-address { ipv4-address | ipv6 ipv6-address }
By default, no global source IP address is specified for VXLAN tunnels.
A VXLAN tunnel uses the global source address if you do not specify a source interface or source address for the tunnel.
3. Create a VXLAN tunnel interface and enter tunnel interface view.
interface tunnel tunnel-number mode vxlan [ ipv6 ]
The endpoints of a tunnel must use the same tunnel mode.
4. Specify a source address for the tunnel. Choose one of the following methods:
¡ Specify a source IP address for the tunnel.
source { ipv4-address | ipv6-address }
The specified IP address is used in the outer IP header of tunneled VXLAN packets.
¡ Specify a source interface for the tunnel.
source interface-type interface-number
The primary IP address of the specified interface is used in the outer IP header of tunneled VXLAN packets.
By default, no source IP address or source interface is specified for a tunnel.
5. Specify a destination IP address for the tunnel.
destination { ipv4-address | ipv6-address }
By default, no destination IP address is specified for a tunnel.
Specify the remote VTEP's IP address. This IP address will be the destination IP address in the outer IP header of tunneled VXLAN packets.
Manually assigning VXLAN tunnels to a VXLAN
About this task
To provide Layer 2 connectivity for a VXLAN between two sites, you must assign the VXLAN tunnel between the sites to the VXLAN.
You can assign multiple VXLAN tunnels to a VXLAN, and configure a VXLAN tunnel to trunk multiple VXLANs. For a unicast-mode VXLAN, the system floods unknown unicast, multicast, and broadcast traffic to each tunnel associated with the VXLAN. If a flood proxy server is used, the VTEP sends flood traffic to the server through the flood proxy tunnel. The flood proxy server replicates and forwards flood traffic to remote VTEPs.
Restrictions and guidelines
For full Layer 2 connectivity in the VXLAN, make sure the VXLAN contains the VXLAN tunnel between each pair of sites in the VXLAN.
Procedure
1. Enter system view.
system-view
2. Enter VSI view.
vsi vsi-name
3. Enter VXLAN view.
vxlan vxlan-id
4. Assign VXLAN tunnels to the VXLAN.
tunnel { tunnel-number [ backup-tunnel tunnel-number ] | all }
By default, a VXLAN does not contain any VXLAN tunnels.
|
Parameter |
Description |
|
backup-tunnel tunnel-number |
Specifies a backup tunnel. When the primary VXLAN tunnel is operating correctly, the backup VXLAN tunnel does not forward traffic. When the primary VXLAN tunnel goes down, traffic is switched to the backup VXLAN tunnel. |
Assigning customer frames to a VSI
Mapping an Ethernet service instance to a VSI
About this task
An Ethernet service instance matches a list of VLANs on a site-facing interface. The VTEP assigns customer traffic from the VLANs to a VXLAN by mapping the Ethernet service instance to a VSI.
Restrictions and guidelines
Link aggregation group membership is mutually exclusive with Ethernet service instance-to-VSI mappings on a Layer 2 interface. Do not map a VSI to an Ethernet service instance on a Layer 2 interface if the interface is in a Layer 2 aggregation group.
When using an Ethernet service instance for CPU forwarding on the S9825 switch series, make sure the PVID of the port associated with the Ethernet service instance does not match the S-VID configured in the frame match criteria of the Ethernet service instance.
When multiple ACs are associated with the same physical interface through Ethernet service instances, these ACs can forward packets to each other. On the S9825 switch series, you can configure the split horizon feature in system view to prevent packets from being forwarded between multiple ACs on the same physical interface.
Procedure
1. Enter system view.
system-view
2. Enter interface view.
¡ Enter Layer 2 Ethernet interface view.
interface interface-type interface-number
¡ Enter Layer 2 aggregate interface view.
interface bridge-aggregation interface-number
3. Create an Ethernet service instance and enter Ethernet service instance view.
service-instance instance-id
4. Configure a frame match criterion. Choose one of the following options:
¡ Match frames tagged with the specified inner 802.1Q VLAN ID.
encapsulation c-vid vlan-id
¡ Match frames tagged with the specified outer 802.1Q VLAN ID.
encapsulation s-vid vlan-id [ only-tagged ]
¡ Match frames tagged with the specified outer and inner 802.1Q VLAN IDs.
encapsulation s-vid vlan-id c-vid vlan-id
¡ Match any 802.1Q tagged or untagged frames.
encapsulation { tagged | untagged }
By default, an Ethernet service instance does not contain a frame match criterion.
The S9825 switch series does not support the c-vid keyword. If you execute the encapsulation command with the only-tagged keyword on the S9825 switch series, an Ethernet service instance can still match untagged packets.
5. Map the Ethernet service instance to a VSI.
xconnect vsi vsi-name [ access-mode { ethernet | vlan } ]
By default, an Ethernet service instance is not mapped to any VSI.
The S9825 switch series does not support the ethernet keyword.
Managing MAC address entries
About MAC address entry management
Local-MAC address entries can be manually added or dynamically learned. You can log local MAC addresses and local-MAC changes.
Remote-MAC address entries have a variety of types, including manually added entries and dynamically learned entries.
Configuring static MAC address entries
Restrictions and guidelines
Do not configure static remote-MAC entries for VXLAN tunnels that are automatically established by using EVPN.
· EVPN re-establishes VXLAN tunnels if the transport-facing interface goes down and then comes up. If you have configured static remote-MAC entries, the entries are deleted when the tunnels are re-established.
· EVPN re-establishes VXLAN tunnels if you perform configuration rollback. If the tunnel IDs change during tunnel re-establishment, configuration rollback fails, and static remote-MAC entries on the tunnels cannot be restored.
For more information about EVPN, see EVPN Configuration Guide.
Procedure
1. Enter system view.
system-view
2. Add a static local-MAC address entry.
mac-address static mac-address interface interface-type interface-number service-instance instance-id vsi vsi-name
For successful configuration, make sure the Ethernet service instance has been mapped to the VSI.
3. Add a static remote-MAC address entry.
mac-address static mac-address interface tunnel tunnel-number vsi vsi-name
For the setting to take effect, make sure the VSI's VXLAN has been specified on the VXLAN tunnel.
Disabling remote-MAC address learning
About this task
When network attacks occur, disable remote-MAC address learning to prevent the device from learning incorrect remote MAC addresses. You can manually add static remote-MAC address entries.
Procedure
1. Enter system view.
system-view
2. Disable remote-MAC address learning.
vxlan tunnel mac-learning disable
By default, remote-MAC address learning is enabled.
Enabling local-MAC logging
About this task
When the local-MAC logging feature is enabled, the VXLAN module immediately sends a log message with its local MAC addresses to the information center. When a local MAC address is added or removed, a log message is also sent to the information center to notify the local-MAC change.
With the information center, you can set log message filtering and output rules, including output destinations. For more information about configuring the information center, see System Management Configuration Guide.
Procedure
1. Enter system view.
system-view
2. Enable local-MAC logging.
vxlan local-mac report
By default, local-MAC logging is disabled.
Setting the destination UDP port number of VXLAN packets
1. Enter system view.
system-view
2. Set a destination UDP port for VXLAN packets.
vxlan udp-port port-number
By default, the destination UDP port number is 4789 for VXLAN packets.
You must configure the same destination UDP port number on all VTEPs in a VXLAN.
Enabling default VXLAN decapsulation
About this task
If a VXLAN tunnel is configured on only one VTEP of a pair of VTEPs, the VXLAN tunnel is a unidirectional tunnel to the VTEP not configured with the tunnel. In this situation, that VTEP drops the VXLAN packets received from the unidirectional VXLAN tunnel. For a VTEP to receive VXLAN packets from a unidirectional VXLAN tunnel, enable default VXLAN decapsulation on the interface whose IP address is the tunnel destination address. The VTEP will decapsulate all the VXLAN packets destined for the IP address of that interface.
Restrictions and guidelines
This feature takes effect only when the specified interface has an IP address.
Default VXLAN decapsulation does not take effect on bidirectional VXLAN tunnels. If you remove the one-way communication issue for a VXLAN tunnel by configuring the tunnel on both the local and remote VTEPs, this feature no longer takes effect on that tunnel.
Enabling default IPv4 VXLAN decapsulation
1. Enter system view.
system-view
2. Enable default IPv4 VXLAN decapsulation.
vxlan default-decapsulation source interface interface-type interface-number
By default, default IPv4 VXLAN decapsulation is disabled.
Enabling default IPv6 VXLAN decapsulation
1. Enter system view.
system-view
2. Enable default IPv6 VXLAN decapsulation.
vxlan ipv6 default-decapsulation source interface interface-type interface-number
By default, default IPv6 VXLAN decapsulation is disabled.
Disabling flooding for a VSI
About this task
By default, the VTEP floods broadcast, unknown unicast, and unknown multicast frames received from the local site to the following interfaces in the frame's VXLAN:
· All site-facing interfaces except for the incoming interface.
· All VXLAN tunnel interfaces.
When receiving broadcast, unknown unicast, and unknown multicast frames on VXLAN tunnel interfaces, the device floods the frames to all site-facing interfaces in the frames' VXLAN.
To confine a kind of flood traffic, disable flooding for that kind of flood traffic on the VSI bound to the VXLAN.
Procedure
1. Enter system view.
system-view
2. Enter VSI view.
vsi vsi-name
3. Disable flooding for the VSI.
flooding disable { all | { broadcast | unknown-multicast | unknown-unicast } * } [ all-direction | dci ]
By default, flooding is enabled for a VSI.
If VXLAN-DCI is configured, flood traffic is also sent out of VXLAN-DCI tunnel interfaces. To confine flood traffic to the site-facing interfaces and VXLAN tunnels within a data center, you can specify the dci keyword to disable flooding only to VXLAN-DCI tunnel interfaces.
The all-direction keyword disables flooding traffic received from an AC or VXLAN tunnel interface to any other ACs and VXLAN tunnel interfaces of the same VSI. If VXLAN-DCI is configured, this keyword also disables flooding between VXLAN tunnel interfaces and VXLAN-DCI tunnel interfaces.
Enabling ARP flood suppression
Restrictions and guidelines
The aging timer is fixed at 25 minutes for ARP flood suppression entries. If the suppression table is full, the VTEP stops learning new entries. For the VTEP to learn new entries, you must wait for old entries to age out, or use the reset arp suppression vsi command to clear the table.
If the flooding disable command is configured, set the MAC aging timer to a higher value than the aging timer for ARP flood suppression entries on all VTEPs. This setting prevents the traffic blackhole that occurs when a MAC address entry ages out before its ARP flood suppression entry ages out. To set the MAC aging timer, use the mac-address timer command.
When remote ARP learning is disabled for VXLANs, the device does not use ARP flood suppression entries to respond to ARP requests received on VXLAN tunnels.
Procedure
1. Enter system view.
system-view
2. Enter VSI view.
vsi vsi-name
3. Enable ARP flood suppression.
arp suppression enable
By default, ARP flood suppression is disabled.
Enabling ND flood suppression
1. Enter system view.
system-view
2. Enter VSI view.
vsi vsi-name
3. Enable ND flood suppression.
ipv6 nd suppression enable
By default, ND flood suppression is disabled.
Configuring VXLAN M-LAG
About this task
VXLAN M-LAG virtualizes two VTEPs or VXLAN IP gateways into one M-LAG system to avoid single points of failure.
Hardware and feature compatibility
The S9825 switch series does not support VXLAN M-LAG.
Restrictions and guidelines
When you configure VXLAN M-LAG, follow these restrictions and guidelines:
· An M-LAG system does not support Layer 2 multicast.
· M-LAG member devices must use the same tunnel source address to establish VXLAN tunnels to remote devices.
If an Ethernet aggregate link is used as the peer link, follow these restrictions:
· If the frame match criteria of dynamic ACs on the peer link are created based on site-facing Ethernet service instances, you can configure only the following criteria for site-facing Ethernet service instances:
¡ encapsulation s-vid { vlan-id | vlan-id-list }
¡ encapsulation untagged
In addition, you must set the access mode to VLAN for site-facing Ethernet service instances.
The above restrictions are not applicable when the frame match criteria of dynamic ACs on the peer link are created based on VXLAN IDs.
· Make sure the Ethernet service instances that use the same match criterion are mapped to the same VSI.
· Make sure the following settings are consistent on the M-LAG member devices:
¡ Ethernet service instances and their match criterion on the M-LAG interfaces in the same M-LAG group or single-homed site-facing interfaces.
¡ VXLAN IDs of VSIs.
In addition, the Ethernet service instances must be created manually.
If a VXLAN tunnel is used as the peer link, follow these restrictions:
· As a best practice, use different physical interfaces as the traffic outgoing interfaces of the peer link VXLAN tunnel and non-peer link VXLAN tunnels.
· To prioritize transmission of M-LAG protocol packets on the peer link, use the tunnel tos command on the VXLAN tunnel interface to set a high ToS value for tunneled packets.
· You must disable spanning tree on the Layer 2 Ethernet interface that acts as the physical traffic outgoing interface of the peer link VXLAN tunnel. If you enable spanning tree on that interface, the upstream device will block the interfaces connected to the M-LAG member devices.
· Make sure the following settings are consistent on the M-LAG member devices:
¡ Ethernet service instances and their match criterion on the M-LAG interfaces in the same M-LAG group.
¡ VXLAN IDs of VSIs.
In addition, the Ethernet service instances must be created manually.
The VTEPs in a M-LAG system synchronize local MAC address entries with each other over the peer link. However, they do not synchronize MAC address entry deletions. When you delete a MAC address entry from one VTEP, the other VTEP retains the entry that contains the same MAC address until the entry ages out.
In the VXLAN M-LAG network, you must configure the l2vpn m-lag peer-link ac-match-rule vxlan-mapping command.
Prerequisites
Configure basic VXLAN settings before you configure M-LAG.
Procedure
1. Configure M-LAG as described in Layer 2—LAN Switching Configuration Guide.
2. Exclude interfaces from the shutdown action by M-LAG MAD.
m-lag mad exclude interface interface-type interface-number
By default, M-LAG MAD shuts down all network interfaces when detecting a multi-active collision, except for the network interfaces set by the system to not shut down.
Exclude all interfaces used by VXLAN from the MAD shutdown action by M-LAG. The interfaces include VSI interfaces, interfaces used for setting up the keepalive link, and transport-facing outgoing interfaces of VXLAN tunnels. Also exclude peer-link interfaces from the shutdown action by M-LAG MAD if the peer link is a VXLAN tunnel.
For more information about this command, see M-LAG commands in Layer 2—LAN Switching Command Reference.
3. Set the data restoration interval.
m-lag restore-delay value
By default, the data restoration interval is 30 seconds.
Set the data restoration interval to a value equal to or larger than 180 seconds on a VXLAN M-LAG system.
For more information about this command, see M-LAG commands in Layer 2—LAN Switching Command Reference.
4. (Optional.) Enable the device to create frame match criteria based on VXLAN IDs for the dynamic ACs on the Ethernet aggregate link peer link.
l2vpn m-lag peer-link ac-match-rule vxlan-mapping
By default, on an M-LAG system that uses an Ethernet aggregate link as the peer link, dynamic ACs on the peer link use frame match criteria that are identical to those of site-facing ACs.
If you do not execute this command, do not configure overlapping outer VLAN IDs for Ethernet service instances of different VSIs.
If you execute this command, do not create VXLANs with IDs larger than 16000000.
For more information about this command, see EVPN Command Reference.
Verifying and maintaining VXLANs
Verifying VXLAN tunnel configuration and running status
Perform display tasks in any view.
· Display information about tunnel interfaces.
display interface [ tunnel [ number ] ] [ brief [ description | down ] ]
For more information about this command, see tunnel interface commands in Interface Command Reference.
· Display VXLAN tunnel information for VXLANs.
display vxlan tunnel [ vxlan vxlan-id ]
Displaying information about Ethernet service instances
To display information about Ethernet service instances, execute the following command in any view:
display l2vpn service-instance [ interface interface-type interface-number [ service-instance instance-id ] ] [ verbose ]
Verifying and maintaining VSIs
Verifying VSI configuration
Display information about VSIs in any view.
display l2vpn vsi [ name vsi-name ] [ verbose ]
Displaying and clearing MAC address entries on VSIs
To display MAC address entries for VSIs, execute the following command in any view:
display l2vpn mac-address [ vsi vsi-name ] [ dynamic ] [ count | verbose ]
To clear dynamic MAC address entries on VSIs, execute the following command in user view:
reset l2vpn mac-address [ vsi vsi-name ]
Displaying and clearing ARP flood suppression entries on VSIs
To display ARP flood suppression entries on VSIs, execute the following command in any view:
display arp suppression vsi [ name vsi-name ] [ slot slot-number [ cpu cpu-number ] ] [ count ]
To clear ARP flood suppression entries on VSIs, execute the following command in user view:
reset arp suppression vsi [ name vsi-name ]
Displaying and clearing ND flood suppression entries on VSIs
To display ND flood suppression entries on VSIs, execute the following command in any view:
display ipv6 nd suppression vsi [ name vsi-name ] [ slot slot-number ] [ count ]
To clear ND flood suppression entries on VSIs, execute the following command in user view:
reset ipv6 nd suppression vsi [ name vsi-name ]
Verifying and maintaining ACs
Displaying L2VPN AC forwarding information
To display L2VPN AC forwarding information, execute the following command in any view:
display l2vpn forwarding ac [ vsi vsi-name ] [ slot slot-number [ cpu cpu-number ] ] [ verbose ]
Displaying L2VPN entries for M-LAG
|
|
NOTE: The S9825 switch series does not support displaying or maintaining L2VPN entries on M-LAG member devices. |
Displaying L2VPN MAC address entries for M-LAG
To display L2VPN MAC address entries for M-LAG, execute the following command in any view:
display l2vpn m-lag mac-address [ local | remote ] [ count | vsi vsi-name [ count | mac-address ] ]
Displaying L2VPN ARP entries and L2VPN ARP flood suppression entries for M-LAG
Perform display tasks in any view.
· Display L2VPN ARP entries for M-LAG.
display l2vpn m-lag arp [ local | remote ] [ count | { public-instance | vpn-instance vpn-instance-name } [ count | ip-address ] ]
· Display L2VPN ARP flood suppression entries for M-LAG.
display l2vpn m-lag arp suppression [ local | remote ] [ count | vsi vsi-name [ count | ip-address ] ]
Displaying L2VPN ND entries and L2VPN ND flood suppression entries for M-LAG
Perform display tasks in any view.
· Display L2VPN ND entries for M-LAG.
display l2vpn m-lag nd [ local | remote ] [ count | { public-instance | vpn-instance vpn-instance-name } [ ipv6-address | count ] ]
· Display L2VPN ND flood suppression entries for M-LAG.
display l2vpn m-lag nd suppression [ local | remote ] [ count | vsi vsi-name [ ipv6-address | count ] ]
VXLAN configuration examples
Example: Configuring a unicast-mode VXLAN
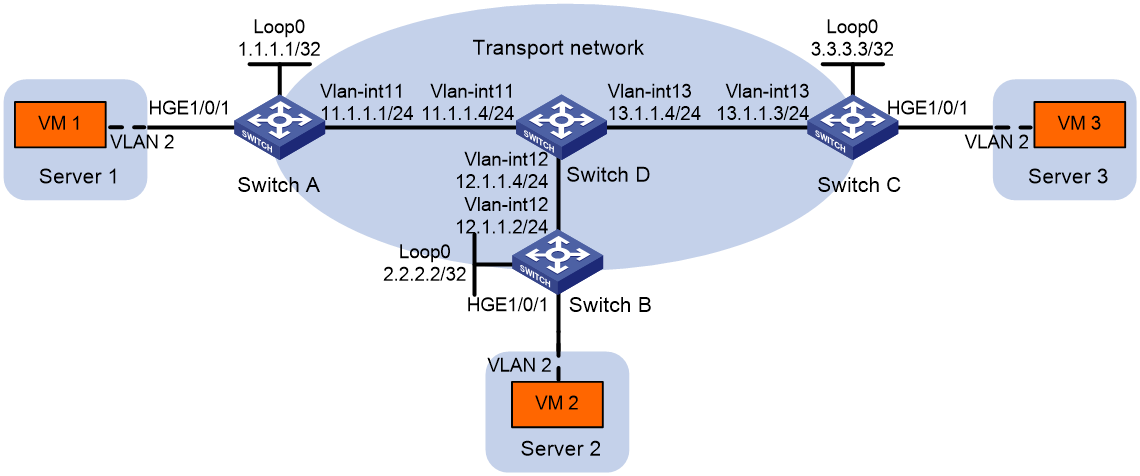
Network configuration
As shown in Figure 9:
· Configure VXLAN 10 as a unicast-mode VXLAN on Switch A, Switch B, and Switch C to provide Layer 2 connectivity for the VMs across the network sites.
· Manually establish VXLAN tunnels and assign the tunnels to VXLAN 10.
· Enable remote-MAC address learning.
Procedure
1. Configure IP addresses and unicast routing settings:
# Assign IP addresses to interfaces, as shown in Figure 9. (Details not shown.)
# Configure OSPF on all transport network switches (Switches A through D). (Details not shown.)
2. Configure Switch A:
# Enable L2VPN.
<SwitchA> system-view
[SwitchA] l2vpn enable
# Enable Layer 2 forwarding for VXLANs.
[SwitchA] undo vxlan ip-forwarding
# Create VSI vpna and VXLAN 10.
[SwitchA] vsi vpna
[SwitchA-vsi-vpna] vxlan 10
[SwitchA-vsi-vpna-vxlan-10] quit
[SwitchA-vsi-vpna] quit
# Assign an IP address to Loopback 0. The IP address will be used as the source IP address of the VXLAN tunnels to Switch B and Switch C.
[SwitchA] interface loopback 0
[SwitchA-Loopback0] ip address 1.1.1.1 255.255.255.255
[SwitchA-Loopback0] quit
# Create a VXLAN tunnel to Switch B. The tunnel interface name is Tunnel 1.
[SwitchA] interface tunnel 1 mode vxlan
[SwitchA-Tunnel1] source 1.1.1.1
[SwitchA-Tunnel1] destination 2.2.2.2
[SwitchA-Tunnel1] quit
# Create a VXLAN tunnel to Switch C. The tunnel interface name is Tunnel 2.
[SwitchA] interface tunnel 2 mode vxlan
[SwitchA-Tunnel2] source 1.1.1.1
[SwitchA-Tunnel2] destination 3.3.3.3
[SwitchA-Tunnel2] quit
# Assign Tunnel 1 and Tunnel 2 to VXLAN 10.
[SwitchA] vsi vpna
[SwitchA-vsi-vpna] vxlan 10
[SwitchA-vsi-vpna-vxlan-10] tunnel 1
[SwitchA-vsi-vpna-vxlan-10] tunnel 2
[SwitchA-vsi-vpna-vxlan-10] quit
[SwitchA-vsi-vpna] quit
# On HundredGigE 1/0/1, create Ethernet service instance 1000 to match VLAN 2.
[SwitchA] interface hundredgige 1/0/1
[SwitchA-HundredGigE1/0/1] service-instance 1000
[SwitchA-HundredGigE1/0/1-srv1000] encapsulation s-vid 2
# Map Ethernet service instance 1000 to VSI vpna.
[SwitchA-HundredGigE1/0/1-srv1000] xconnect vsi vpna
[SwitchA-HundredGigE1/0/1-srv1000] quit
[SwitchA-HundredGigE1/0/1] quit
3. Configure Switch B:
# Enable L2VPN.
<SwitchB> system-view
[SwitchB] l2vpn enable
# Enable Layer 2 forwarding for VXLANs.
[SwitchB] undo vxlan ip-forwarding
# Create VSI vpna and VXLAN 10.
[SwitchB] vsi vpna
[SwitchB-vsi-vpna] vxlan 10
[SwitchB-vsi-vpna-vxlan-10] quit
[SwitchB-vsi-vpna] quit
# Assign an IP address to Loopback 0. The IP address will be used as the source IP address of the VXLAN tunnels to Switch A and Switch C.
[SwitchB] interface loopback 0
[SwitchB-Loopback0] ip address 2.2.2.2 255.255.255.255
[SwitchB-Loopback0] quit
# Create a VXLAN tunnel to Switch A. The tunnel interface name is Tunnel 2.
[SwitchB] interface tunnel 2 mode vxlan
[SwitchB-Tunnel2] source 2.2.2.2
[SwitchB-Tunnel2] destination 1.1.1.1
[SwitchB-Tunnel2] quit
# Create a VXLAN tunnel to Switch C. The tunnel interface name is Tunnel 3.
[SwitchB] interface tunnel 3 mode vxlan
[SwitchB-Tunnel3] source 2.2.2.2
[SwitchB-Tunnel3] destination 3.3.3.3
[SwitchB-Tunnel3] quit
# Assign Tunnel 2 and Tunnel 3 to VXLAN 10.
[SwitchB] vsi vpna
[SwitchB-vsi-vpna] vxlan 10
[SwitchB-vsi-vpna-vxlan-10] tunnel 2
[SwitchB-vsi-vpna-vxlan-10] tunnel 3
[SwitchB-vsi-vpna-vxlan-10] quit
[SwitchB-vsi-vpna] quit
# On HundredGigE 1/0/1, create Ethernet service instance 1000 to match VLAN 2.
[SwitchB] interface hundredgige 1/0/1
[SwitchB-HundredGigE1/0/1] service-instance 1000
[SwitchB-HundredGigE1/0/1-srv1000] encapsulation s-vid 2
# Map Ethernet service instance 1000 to VSI vpna.
[SwitchB-HundredGigE1/0/1-srv1000] xconnect vsi vpna
[SwitchB-HundredGigE1/0/1-srv1000] quit
[SwitchB-HundredGigE1/0/1] quit
4. Configure Switch C:
# Enable L2VPN.
<SwitchC> system-view
[SwitchC] l2vpn enable
# Enable Layer 2 forwarding for VXLANs.
[SwitchC] undo vxlan ip-forwarding
# Create VSI vpna and VXLAN 10.
[SwitchC] vsi vpna
[SwitchC-vsi-vpna] vxlan 10
[SwitchC-vsi-vpna-vxlan-10] quit
[SwitchC-vsi-vpna] quit
# Assign an IP address to Loopback 0. The IP address will be used as the source IP address of the VXLAN tunnels to Switch A and Switch B.
[SwitchC] interface loopback 0
[SwitchC-Loopback0] ip address 3.3.3.3 255.255.255.255
[SwitchC-Loopback0] quit
# Create a VXLAN tunnel to Switch A. The tunnel interface name is Tunnel 1.
[SwitchC] interface tunnel 1 mode vxlan
[SwitchC-Tunnel1] source 3.3.3.3
[SwitchC-Tunnel1] destination 1.1.1.1
[SwitchC-Tunnel1] quit
# Create a VXLAN tunnel to Switch B. The tunnel interface name is Tunnel 3.
[SwitchC] interface tunnel 3 mode vxlan
[SwitchC-Tunnel3] source 3.3.3.3
[SwitchC-Tunnel3] destination 2.2.2.2
[SwitchC-Tunnel3] quit
# Assign Tunnel 1 and Tunnel 3 to VXLAN 10.
[SwitchC] vsi vpna
[SwitchC-vsi-vpna] vxlan 10
[SwitchC-vsi-vpna-vxlan-10] tunnel 1
[SwitchC-vsi-vpna-vxlan-10] tunnel 3
[SwitchC-vsi-vpna-vxlan-10] quit
[SwitchC-vsi-vpna] quit
# On HundredGigE 1/0/1, create Ethernet service instance 1000 to match VLAN 2.
[SwitchC] interface hundredgige 1/0/1
[SwitchC-HundredGigE1/0/1] service-instance 1000
[SwitchC-HundredGigE1/0/1-srv1000] encapsulation s-vid 2
# Map Ethernet service instance 1000 to VSI vpna.
[SwitchC-HundredGigE1/0/1-srv1000] xconnect vsi vpna
[SwitchC-HundredGigE1/0/1-srv1000] quit
[SwitchC-HundredGigE1/0/1] quit
Verifying the configuration
1. Verify the VXLAN settings on the VTEPs. This example uses Switch A.
# Verify that the VXLAN tunnel interfaces on the VTEP are up.
[SwitchA] display interface tunnel 1
Tunnel1
Current state: UP
Line protocol state: UP
Description: Tunnel1 Interface
Bandwidth: 64 kbps
Maximum transmission unit: 64000
Internet protocol processing: Disabled
Last clearing of counters: Never
Tunnel source 1.1.1.1, destination 2.2.2.2
Tunnel protocol/transport UDP_VXLAN/IP
Last 300 seconds input rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Last 300 seconds output rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Input: 0 packets, 0 bytes, 0 drops
Output: 0 packets, 0 bytes, 0 drops
# Verify that the VXLAN tunnels have been assigned to the VXLAN.
[SwitchA] display l2vpn vsi verbose
VSI Name: vpna
VSI Index : 0
VSI State : Up
MTU : 1500
Bandwidth : -
Broadcast Restrain : -
Multicast Restrain : -
Unknown Unicast Restrain: -
MAC Learning : Enabled
MAC Table Limit : -
MAC Learning rate : -
Drop Unknown : -
PW Redundancy Mode : Slave
Flooding : Enabled
Statistics : Disabled
VXLAN ID : 10
Tunnels:
Tunnel Name Link ID State Type Flood proxy
Tunnel1 0x5000001 Up Manual Disabled
Tunnel2 0x5000002 Up Manual Disabled
ACs:
AC Link ID State
HGE1/0/1 srv1000 0 Up
Statistics: Disabled
# Verify that the VTEP has learned the MAC addresses of remote VMs.
<SwitchA> display l2vpn mac-address
MAC Address State VSI Name Link ID/Name Aging
cc3e-5f9c-6cdb Dynamic vpna Tunnel1 Aging
cc3e-5f9c-23dc Dynamic vpna Tunnel2 Aging
--- 2 mac address(es) found ---
2. Verify that VM 1, VM 2, and VM 3 can ping each other. (Details not shown.)