H3C Vulnerability Response Process
A security vulnerability is a specific flaw that compromises the confidentiality, integrity, or availability of a device or software. In order to minimize the impact and harm of security vulnerabilities on users and to reduce the risks associated with them, H3C has established a comprehensive vulnerability management system from the perspectives of strategy, process, organization, management, standards, and technology. H3C encourages vulnerability researchers, industry organizations, customers, and suppliers to report any vulnerabilities to H3C Product Security Incident Response Team (PSIRT) so as to jointly address the challenges posed by vulnerabilities. H3C PSIRT follows industry standards such as ISO/IEC 30111 and ISO/IEC 29147 to handle suspected vulnerabilities in products.
1 Vulnerability Handling Process
H3C attaches great importance to vulnerability management in product development and maintenance. It develops a complete vulnerability handling process to ensure prompt response upon discovering vulnerabilities and enhance product security.
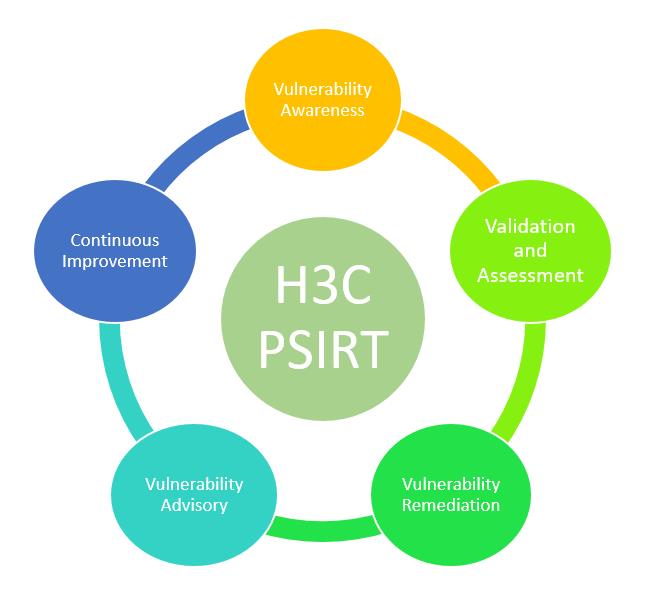
A. Vulnerability Awareness:Receive and collect suspected vulnerabilities in products
H3C encourages vulnerability researchers, industry organizations, customers, and suppliers to report suspected vulnerabilities to H3C PSIRT. You can submit them via email (email address: [email protected]) following the template. H3C PSIRT will confirm any suspected vulnerabilities received as soon as possible and will contact you within 48 hours of receiving the report.
Due to the sensitivity of vulnerability information, we suggest that you encrypt the information sent to [email protected] using PGP. Our PGP public key can be obtained by clicking here.
In addition, we actively monitor well-known public vulnerability databases, open-source communities, security websites, and other information sources to promptly obtain updated vulnerability information and determine if the products are affected.
B. Validation & assessment: Confirm the validity and impact scope of suspected vulnerabilities.
For any suspected vulnerability reported to PSIRT, PSIRT will work with the product team to analyze and confirm the vulnerability and evaluate its severity level based on the actual impact.
C. Vulnerability remediation: Develop and implement vulnerability remediation solutions.
Vulnerabilities will be remediated as soon as possible through version updates or patch releases.
D. Vulnerability Advisory: Release vulnerability remediation information to customers.
To minimize vulnerability risks and damages, security advisories will be released as soon as possible to inform customers of remediation methods, workarounds, and other related information.
E. Continuous Improvement: Accumulate technologies and experience for continuous optimization.
Based on the principle of continuous optimization, we will continuously enhance product security and optimize the vulnerability handling process.
During the vulnerability handling process, PSIRT only shares vulnerability information among relevant personnel involved in the process, and strictly controls the scope of information disclosure. Meanwhile, we also kindly ask the reporter to keep the vulnerability information confidential until our customers have obtained a complete solution.
2 Vulnerability Severity Rating
H3C adopts the industry standard Common Vulnerability Scoring System (CVSS) to evaluate the severity levels of suspected vulnerabilities in our products, and classifies vulnerabilities into four levels: critical, high, medium, and low.
3 Third-Party Software Vulnerability
H3C will provide risk decision-making, remediation or mitigation support to affected customers through Security Advisories for third-party software vulnerabilities meeting the following conditions:
· The CVSS score is 7.0 or above.
· The vulnerability has aroused wide public attention.
· The vulnerability is likely to be exploited or has already been exploited, or may be exploited in the wild.
4 Release vulnerability remediation information
H3C publishes vulnerability information and remediation solutions to the public in the following forms:
· Security Advisory (SA)
link:https://www.h3c.com/en/Support/Online_Help/psirt/
· Release Note (RN)
The version/patch release notes include information on the vulnerabilities that have been fixed. They are part of the delivery package that accompanies the product version/patch release.
5 Product lifecycle-based vulnerability management
Vulnerability management is based on the lifecycle milestones of the product/software versions. For discontinued products, H3C still accepts vulnerability reports, and will repair and disclose the vulnerabilities. For products that H3C has stopped providing services for, H3C will no longer accept, repair, or disclose related vulnerabilities.
H3C Product Life Cycle Management Strategy:https://www.h3c.com/en/Support/Policy_Dynamics/Management_Strategy/
6 Disclaimer & Rights Reserved
The policy described in this document does not constitute warranties, commitments, or contract parts. H3C may adjust it as appropriate.
We reserve the right to change or update this document at any time as necessary to increase transparency or respond more actively.
As changes to this policy are posted, we will revise the "Update Date" at the bottom of this policy.
Updated at 2023.5.23

