Video Security Gateway Solution for Customs Supervision Areas
I. Background
The special customs supervision areas are classified into the following six types: bonded zones, export processing zones, bonded logistics parks, cross-border industrial parks, bonded port areas, and comprehensive bonded zones. Since 2012, the newly established special customs supervision areas have been uniformly named comprehensive bonded zones (CBZ). CBZs are designed to promote the foreign trade economy and mainly focus on businesses such as international transit, distribution, procurement, entrepot trade, and export processing.
In 2020, the global spreading of the epidemic caused a sharp drop in demands in international markets, which greatly affected China's foreign trade industry. The CPC Central Committee, the State Council, and other relevant departments have issued many policies to boost the foreign trade industry, including policies for tax cuts, domestic sales of commodities originally produced for exports, and the development of cross-border e-commerce. By implementing high-level trade and trade liberalization, China intends to build CBZs into a new highland for comprehensively deepening reform and opening up in the new era.
II. Solution overview
Taking the status of the video security industry and the above issues into consideration, H3C has developed the video security gateway solution and products for video security scenarios. In addition to the security features of traditional gateways, this solution also supports access authentication of video terminals, fingerprint recognition of video cameras, video asset management, and vulnerability detection. This solution is compatible with H3C iMC Endpoints Profiling System (EPS) and can control the access of the endpoints in the video private network and visually monitor network security, providing the video private network with reliable protection measures.
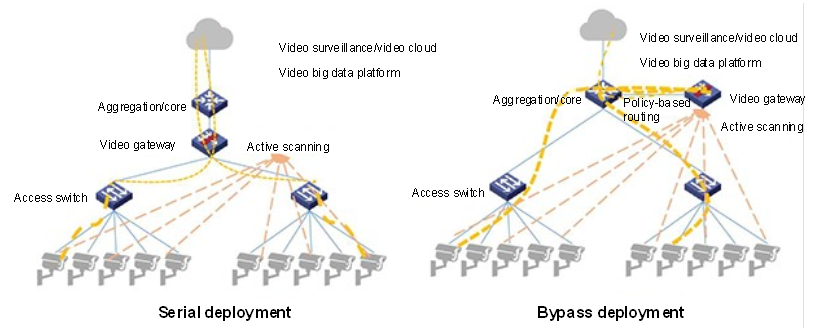
As shown in the following figure, video gateways can be deployed at the access layer, aggregation layer, or core layer according to network scale and deployment requirements.
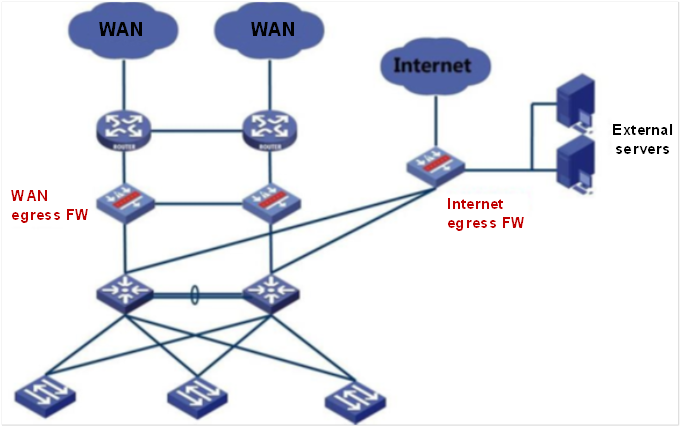
Firewall
The video gateway can also be used as a firewall, which is deployed at the WAN egress and Internet egress to provide security control and network address translation (NAT) for external access. Meanwhile, it protects the servers in the demilitarized zone (DMZ) through the attack defense of the firewall and in-depth defense functions.
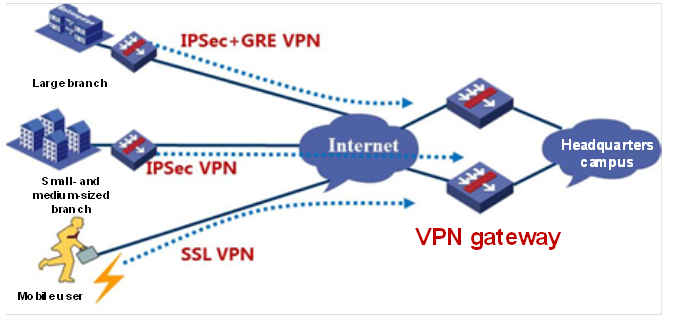
VPN
The device integrates abundant VPN features, including IPsec VPN, SSL VPN, and L2TP VPN. It can serve as an egress gateway device for small and medium-sized enterprises to provide SSL VPN access for mobile users, and can also be used as a branch of WAN networking or a secondary/tertiary core device to provide site-to-site IPsec VPN access. IP SEC services and SSL VPN services support the national encryption algorithm (NEAT).
III. Solution features
High-performance software and hardware processing platform
![]() The H3C SecPath gateways used in the solution adopt high-performance 64-bit multi-core processors, providing processing performance of 1 Gbps to 10 Gbps. The product uses a CPU+Switch architecture in which the CPU processes security services, and the switch implements the expansion of multi-service interfaces.
The H3C SecPath gateways used in the solution adopt high-performance 64-bit multi-core processors, providing processing performance of 1 Gbps to 10 Gbps. The product uses a CPU+Switch architecture in which the CPU processes security services, and the switch implements the expansion of multi-service interfaces.
Carrier-level high availability
![]() Uses H3C-proprietary software and hardware platforms that have been proven by Telecom carriers and small- to medium-sized enterprises.
Uses H3C-proprietary software and hardware platforms that have been proven by Telecom carriers and small- to medium-sized enterprises.
![]() Supports H3C SCF, which can virtualize multiple devices into one logical device (acting as one network node) for unified resource management, service backup, and system performance improvement.
Supports H3C SCF, which can virtualize multiple devices into one logical device (acting as one network node) for unified resource management, service backup, and system performance improvement.
Comprehensive security protection features
![]() Supports authentication via allowlists to control the access of endpoints based on the MAC address allowlist or IP address allowlist.
Supports authentication via allowlists to control the access of endpoints based on the MAC address allowlist or IP address allowlist.
![]() Recognizes the information about the endpoints, including its IP addresses, MAC addresses, physical interfaces, manufacturers (such as Dahua, Hikvision, and Unisinsight), types, and models.
Recognizes the information about the endpoints, including its IP addresses, MAC addresses, physical interfaces, manufacturers (such as Dahua, Hikvision, and Unisinsight), types, and models.
![]() Reports information about the endpoint if the device finds a change in the endpoint, including its IP address, MAC address, physical interfaces, original manufacturer, original type, original model, original SN, new manufacturer, new type, new model, and new SN.
Reports information about the endpoint if the device finds a change in the endpoint, including its IP address, MAC address, physical interfaces, original manufacturer, original type, original model, original SN, new manufacturer, new type, new model, and new SN.
![]() Locates the information of the device that is illegally connected to the video private network, including information such as its region, IP address, access interface, endpoint MAC address, and endpoint IP address.
Locates the information of the device that is illegally connected to the video private network, including information such as its region, IP address, access interface, endpoint MAC address, and endpoint IP address.
![]() Conducts attack analysis of the video traffic based on the database for video attack behaviors, enabling effective recognition and blocking of attack behaviors in the video traffic.
Conducts attack analysis of the video traffic based on the database for video attack behaviors, enabling effective recognition and blocking of attack behaviors in the video traffic.
![]() Detects the device connecting to the video private network. If it is connected to an external network, alarms will be triggered in a timely manner.
Detects the device connecting to the video private network. If it is connected to an external network, alarms will be triggered in a timely manner.
![]() Supports portal access function to authenticate the PC endpoints in the video network.
Supports portal access function to authenticate the PC endpoints in the video network.
![]() Works with the H3CEPS products to provide perfect asset management and security management features.
Works with the H3CEPS products to provide perfect asset management and security management features.
Powerful security protection features
![]() Supports abundant attack protection features to detect and prevent various attacks, including Land, Smurf, Fraggle, ping of death, teardrop, IP spoofing, IP fragment, ARP spoofing, reverse ARP lookup, invalid TCP flag, large ICMP packet, IP scanning, port scanning, and common DDoS attacks such as SYN flood, UDP flood, ICMP flood, and DNS flood. In addition, it also supports traffic self-learning to set the self-learning time and automatically generate DDoS prevention policies, greatly reducing the workload of policy configuration.
Supports abundant attack protection features to detect and prevent various attacks, including Land, Smurf, Fraggle, ping of death, teardrop, IP spoofing, IP fragment, ARP spoofing, reverse ARP lookup, invalid TCP flag, large ICMP packet, IP scanning, port scanning, and common DDoS attacks such as SYN flood, UDP flood, ICMP flood, and DNS flood. In addition, it also supports traffic self-learning to set the self-learning time and automatically generate DDoS prevention policies, greatly reducing the workload of policy configuration.
![]() Supports SOP 1:N virtualization. An H3C SecPath Series F1000 firewall can be virtualized into multiple logical firewalls, which have the same features as the physical firewall based on the container-based virtualization technology. The virtual firewalls can be allocated based on the virtual system in terms of their performances such as throughput, concurrency, feature, and policy.
Supports SOP 1:N virtualization. An H3C SecPath Series F1000 firewall can be virtualized into multiple logical firewalls, which have the same features as the physical firewall based on the container-based virtualization technology. The virtual firewalls can be allocated based on the virtual system in terms of their performances such as throughput, concurrency, feature, and policy.
![]() Supports the management of security zones, which can be configured based on interfaces and VLANs.
Supports the management of security zones, which can be configured based on interfaces and VLANs.
![]() Supports packet filtering. The standard or advanced ACLs can be applied between security zones to filter packets based on information contained in the packets, such as UDP and TCP port numbers. Packet filtering can be also configured to execute in specific time ranges.
Supports packet filtering. The standard or advanced ACLs can be applied between security zones to filter packets based on information contained in the packets, such as UDP and TCP port numbers. Packet filtering can be also configured to execute in specific time ranges.
![]() Supports access control based on users and applications and integrates deep intrusion prevention of the next-generation device with access control.
Supports access control based on users and applications and integrates deep intrusion prevention of the next-generation device with access control.
![]() Supports application specific packet filter (ASPF) to dynamically determine whether to forward or drop a packet by checking its application layer protocol information and state. ASPF supports inspecting FTP, HTTP, SMTP, RTSP, and other TCP/UDP-based application layer protocols.
Supports application specific packet filter (ASPF) to dynamically determine whether to forward or drop a packet by checking its application layer protocol information and state. ASPF supports inspecting FTP, HTTP, SMTP, RTSP, and other TCP/UDP-based application layer protocols.
![]() Supports authentication, authorization, and accounting (AAA) services, including authentication based on RADIUS/HWTACACS+, CHAP, and PAP.
Supports authentication, authorization, and accounting (AAA) services, including authentication based on RADIUS/HWTACACS+, CHAP, and PAP.
![]() Supports static denylist and dynamic denylist.
Supports static denylist and dynamic denylist.
![]() Supports NAT and NAT multi-instance.
Supports NAT and NAT multi-instance.
![]() Supports VPNs, including L2TP, IPsec/IKE, GRE, and SSL VPNs, and allows smart devices to connect to the VPNs.
Supports VPNs, including L2TP, IPsec/IKE, GRE, and SSL VPNs, and allows smart devices to connect to the VPNs.
![]() Supports multiple routing protocols, including static routing, policy-based routing, and dynamic routing such as RIP and OSPF.
Supports multiple routing protocols, including static routing, policy-based routing, and dynamic routing such as RIP and OSPF.
![]() Supports security logs.
Supports security logs.
![]() Supports traffic monitoring, statistics, and management.
Supports traffic monitoring, statistics, and management.
Flexible, extensible, and integrated DPI security
![]() Highly integrates the basic security protection measures to an integrated security service processing platform.
Highly integrates the basic security protection measures to an integrated security service processing platform.
![]() Application-layer traffic identification and management: The solution uses the state machine and traffic exchange inspection technologies to detect the traffic of P2P, IM, online game, stock, Internet video, and Internet multi-media applications, such as Thunder, Web Thunder, BitTorrent, eMule, eDonkey, WeChat, Weibo, QQ, MSN, and PPLive. Besides, the solution uses deep inspection technology to identify P2P traffic precisely and provides multiple policies to control and manage the P2P traffic flexibly.
Application-layer traffic identification and management: The solution uses the state machine and traffic exchange inspection technologies to detect the traffic of P2P, IM, online game, stock, Internet video, and Internet multi-media applications, such as Thunder, Web Thunder, BitTorrent, eMule, eDonkey, WeChat, Weibo, QQ, MSN, and PPLive. Besides, the solution uses deep inspection technology to identify P2P traffic precisely and provides multiple policies to control and manage the P2P traffic flexibly.
![]() Highly precise and effective intrusion inspection engine. The solution uses the H3C-proprietary Full Inspection with Rigorous State Test (FIRST) engine that is integrated with various intrusion inspection technologies, to implement highly precise inspection of intrusions based on application states. The FIRST engine also supports software and hardware concurrent inspections to improve inspection efficiency.
Highly precise and effective intrusion inspection engine. The solution uses the H3C-proprietary Full Inspection with Rigorous State Test (FIRST) engine that is integrated with various intrusion inspection technologies, to implement highly precise inspection of intrusions based on application states. The FIRST engine also supports software and hardware concurrent inspections to improve inspection efficiency.
![]() Real-time anti-virus protection: The solution uses the stream-based anti-virus engine to prevent, detect, and remove malicious code from network traffic.
Real-time anti-virus protection: The solution uses the stream-based anti-virus engine to prevent, detect, and remove malicious code from network traffic.
![]() Massive URL category filtering: The solution supports local + cloud mode, 139 category libraries, and over 20 million URL rules.
Massive URL category filtering: The solution supports local + cloud mode, 139 category libraries, and over 20 million URL rules.
![]() Complete and timely security signature databases: H3C has a senior attack signature database team and professional attack defense labs, so the signature database is always precise and up to date.
Complete and timely security signature databases: H3C has a senior attack signature database team and professional attack defense labs, so the signature database is always precise and up to date.
Industry-leading IPv6 features
![]() Supports the IPv6 stateful firewall to implement the firewall feature of the IPv6 service and prevent IPv6 related attacks.
Supports the IPv6 stateful firewall to implement the firewall feature of the IPv6 service and prevent IPv6 related attacks.
![]() Supports IPv4 and IPv6 dual stack and supports IPv6 data forwarding, IPv6 static routing and dynamic routing, and IPv6 multicast.
Supports IPv4 and IPv6 dual stack and supports IPv6 data forwarding, IPv6 static routing and dynamic routing, and IPv6 multicast.
![]() Supports IPv6 transition technologies, including NAT-PT, IPv6 over IPv4 GRE tunnel, manual tunnel, 6to4 tunnel, automatic IPv4-compatible IPv6 tunnel, ISATAP tunnel, NAT444, and DS-Lite.
Supports IPv6 transition technologies, including NAT-PT, IPv6 over IPv4 GRE tunnel, manual tunnel, 6to4 tunnel, automatic IPv4-compatible IPv6 tunnel, ISATAP tunnel, NAT444, and DS-Lite.
![]() Supports security technologies such as IPv6 ACL and RADIUS.
Supports security technologies such as IPv6 ACL and RADIUS.
Next-generation multi-service features
![]() Integrated link load balancing feature: includes smart DNS proxy and transparent DNS proxy. This feature uses the link state inspection and link busy detection technologies to implement automatic balancing and switching of traffic among links for an enterprise network egress.
Integrated link load balancing feature: includes smart DNS proxy and transparent DNS proxy. This feature uses the link state inspection and link busy detection technologies to implement automatic balancing and switching of traffic among links for an enterprise network egress.
![]() Integrated SSL VPN feature: This feature can use USB-Key, SMSs, and the enterprise's existing authentication system to authenticate users, providing secure access for mobile users to the enterprise network in case of mobile working and business trips.
Integrated SSL VPN feature: This feature can use USB-Key, SMSs, and the enterprise's existing authentication system to authenticate users, providing secure access for mobile users to the enterprise network in case of mobile working and business trips.
![]() Data leakage prevention (DLP): This solution supports email filtering by SMTP email address, subject, attachment, and content, HTTP URL and content filtering, FTP file filtering, and application layer filtering (including Java/ActiveX blocking and SQL injection attack prevention).
Data leakage prevention (DLP): This solution supports email filtering by SMTP email address, subject, attachment, and content, HTTP URL and content filtering, FTP file filtering, and application layer filtering (including Java/ActiveX blocking and SQL injection attack prevention).
![]() Intrusion prevention system (IPS): The solution supports Web attack identification and protection, such as cross-site scripting attacks and SQL injection attacks.
Intrusion prevention system (IPS): The solution supports Web attack identification and protection, such as cross-site scripting attacks and SQL injection attacks.
![]() Antivirus (AV): The solution uses a high-performance anti-virus engine that can protect against more than 5 million viruses and Trojan horses. The virus signature database is updated every day.
Antivirus (AV): The solution uses a high-performance anti-virus engine that can protect against more than 5 million viruses and Trojan horses. The virus signature database is updated every day.
![]() Unknown threat defense: By cooperating with the situation awareness platform, H3C SecBlade NGFW can quickly detect attacks and locate problems. Once a single node is attacked, the firewall can upgrade policies, trigger security warnings, and take fast responses in the whole network.
Unknown threat defense: By cooperating with the situation awareness platform, H3C SecBlade NGFW can quickly detect attacks and locate problems. Once a single node is attacked, the firewall can upgrade policies, trigger security warnings, and take fast responses in the whole network.
Professional intelligent management
![]() Supports intelligent and unified security policy management to detect duplicate policies, optimize policy matching rules, and detect and propose security policies dynamically generated in the internal network.
Supports intelligent and unified security policy management to detect duplicate policies, optimize policy matching rules, and detect and propose security policies dynamically generated in the internal network.
![]() Supports SNMPv3, compatible with SNMPv1 and SNMPv2.
Supports SNMPv3, compatible with SNMPv1 and SNMPv2.
![]() Provides web-based management with a simple and user-friendly GUI.
Provides web-based management with a simple and user-friendly GUI.
![]() Performs CLI-based management and firewall configuration to meet the needs of professional management and batch configuration.
Performs CLI-based management and firewall configuration to meet the needs of professional management and batch configuration.
![]() Implements unified security management with the H3C iMC SSM, which can collect, analyze, and respond to security information and security events, and offer an intuitive view into network and security conditions, saving management efforts and improving management efficiency.
Implements unified security management with the H3C iMC SSM, which can collect, analyze, and respond to security information and security events, and offer an intuitive view into network and security conditions, saving management efforts and improving management efficiency.
![]() Supports centralized log management based on advanced data drill-down and analysis technology. It can request and receive information to generate logs and compile different types of logs (such as syslogs and binary stream logs) in the same format. Moreover, it uses the aggregation and compression technology to compress large amounts of events for storage and can automatically compress, encrypt, and store logs in external storage devices such as DAS, NAS, and SAN, avoid losing important security logs.
Supports centralized log management based on advanced data drill-down and analysis technology. It can request and receive information to generate logs and compile different types of logs (such as syslogs and binary stream logs) in the same format. Moreover, it uses the aggregation and compression technology to compress large amounts of events for storage and can automatically compress, encrypt, and store logs in external storage devices such as DAS, NAS, and SAN, avoid losing important security logs.
![]() Provides abundant reports, including application-based reports and stream-based analysis reports.
Provides abundant reports, including application-based reports and stream-based analysis reports.
![]() Supports export of reports in different formats, such as PDF, HTML, word, and txt.
Supports export of reports in different formats, such as PDF, HTML, word, and txt.
![]() Supports custom reports through the Web interface. The customizable contents include the time range, data source device, generation period, and export format.
Supports custom reports through the Web interface. The customizable contents include the time range, data source device, generation period, and export format.

