Anti-tamper Solution for Government Website
I. Background
With the increasing number of government portal websites, Web attacks are commonplace, among which the tampering on the home page affects the government the most. In particular, attacks and tampering with political overtones will cause serious negative effects on the government's image. At present, the vast majority of government portal websites have independent web servers, and use content management systems to complete the editing and publishing of web content. With the advancement of e-government projects in recent years, interactive applications such as declaration and approval of administrative matters have been added to the portal sites. Therefore, the web anti-tamper solution applied to government websites should protect not only web files, but also dynamic data.
II. Solution overview
The H3C SecPath Web Guard is a web page tamper-proof system focused on website content, which features advanced technologies, comprehensive functions, wide application, and simple implementation. It is developed by a professional security team with robust R&D experience accumulated from their years of technical experience and hard work. This system can be widely applied to portals of the following industries such as government, finance, operator, energy, taxation, industry and commerce, social security, transportation, and education, and other Internet-based e-commerce portals. The deployment of H3C SecPath Web Guard can provide uninterrupted monitoring and protection for a website, effectively guaranteeing its integrity and authenticity.
Solution features
Key advantages
![]() Uses the 3rd generation anti-tamper technology, which is a mature, stable, and reliable file protection technology.
Uses the 3rd generation anti-tamper technology, which is a mature, stable, and reliable file protection technology.
![]() Enables simple operation and easy deployment to improve deployment efficiency.
Enables simple operation and easy deployment to improve deployment efficiency.
![]() Supports continuous anti-tamper protection and dynamic web page protection.
Supports continuous anti-tamper protection and dynamic web page protection.
![]() Poses no impact on the original network structure.
Poses no impact on the original network structure.
![]() Provides fully-compatible and secure automatic incremental updates.
Provides fully-compatible and secure automatic incremental updates.
Key technologies
![]() Based on the kernel-driven file protection technology, it supports various web page formats, including various scripts on dynamic web pages.
Based on the kernel-driven file protection technology, it supports various web page formats, including various scripts on dynamic web pages.
![]() Kernel-level event trigger technology, which greatly reduces additional expenses of the systems.
Kernel-level event trigger technology, which greatly reduces additional expenses of the systems.
![]() The system runs automatically in the background and supports tamper prevention in a disconnected state.
The system runs automatically in the background and supports tamper prevention in a disconnected state.
![]() The kernel outbound verification technology completely prevents the tampered content from being viewed by external users.
The kernel outbound verification technology completely prevents the tampered content from being viewed by external users.
Applicable website environments
Item | Description |
OS | Windows (server 2003/2008/2012/2016 Windows XP/7/8/10) Linux (such as CentOS, Red Hat, and SUSE) Unix (such as AIX, HP Unix, and Solaris) |
Web server software | IIS, Apache, Weblogic, Tomcat, WebSphere, and Nginx |
Database system | SQL Server, Oracle, MySQL, Access, and Informix |
CMS | No limitation |
III. Common deployment mode of the solution
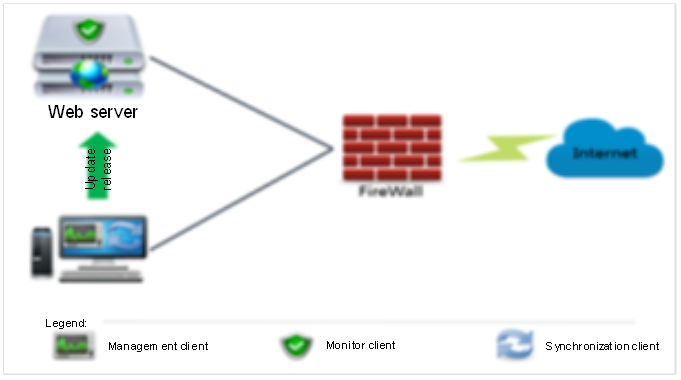
This preceding figure shows the common deployment of the solution. It is typically deployed for government websites and large enterprises or institutions with an intranet web server.
Step 1: Install a management client (Center Server, with an IP address of 172.16.1.100 in the example) on any server in the DMZ, and set the external management port (5366 by default).
Step 2: Install a monitor client (Monitor Client) on the web server (172.16.1.X), and specify the IP address of the management server (such as 172.16.1.100).
Step 3: Install a synchronization client (Monitor Client)[M帐1] in any area that is accessible to the web server, and specify the IP address of the central management server (such as 172.16.1.100).
Step 4: In the internal management area, use any PC to open a browser to log in to the website security protection system.
Remarks: The installation packages of the monitor client (Monitor Client) and the synchronization client (Monitor Client) are the same, which can be configured in the management center. The user can specify the synchronization client or the monitoring client as needed.
Notes:
![]() The monitor client (Monitor Client) is installed on a web server. After installation, it runs automatically in the background. It is mainly used to monitor the attack status of the website, execute the policies configured by the management center, and effectively prevent all kinds of tampering attacks.
The monitor client (Monitor Client) is installed on a web server. After installation, it runs automatically in the background. It is mainly used to monitor the attack status of the website, execute the policies configured by the management center, and effectively prevent all kinds of tampering attacks.
![]() The management client (Center Server) is recommended to be deployed on an independent PC server. It is mainly used for user management, policy distribution, log monitoring, and publishing the security policies of each monitoring client. It runs in the background with no program interface.
The management client (Center Server) is recommended to be deployed on an independent PC server. It is mainly used for user management, policy distribution, log monitoring, and publishing the security policies of each monitoring client. It runs in the background with no program interface.
![]() The synchronization client (Monitor Client) is installed on a web server. After installation, it runs automatically in the background. It is mainly used to release website content and serves as a backup of the website content of the monitor client.
The synchronization client (Monitor Client) is installed on a web server. After installation, it runs automatically in the background. It is mainly used to release website content and serves as a backup of the website content of the monitor client.
[M帐1]同步端是否也成为monitor center?答疑回复信息:待确认


