Water Resource Network Security Situation Awareness Solutions
I. Background
The Ministry of Water Resources (MWR) issued the 2019 Water Resources Network Information Work Key Points, emphasizing the importance of adhering to the guideline of building a "practical and secure" network. It requires working on water resource network security situation awareness, monitoring the Internet security threats to MWR departments and river basin institutes, collecting Internet security vulnerabilities and risk monitoring data from all MWR departments, providing timely warning and information notification, and improving water resource network security monitoring and early-warning capabilities by conducting a deep analysis on water resource business needs, implementing the schemes for refining and actualizing water resource network security tasks, promoting intelligent water resources, and implementing Water Resource Network Information Improvement Action Plan (2019 to 2021). Moreover, in consideration of the deteriorating security environment, H3C follows the trend and introduces water resource network security situation awareness solutions with water resources security situation awareness as the primary solution.
II. Solution overview
To achieve unified monitoring and in-depth analysis of network-wide risks, we deploy detection devices (including full traffic probes, traditional security devices, advanced threat detection engines, and log collection) at the key nodes of each network, and connect the devices with the situation awareness platform in O&M management areas.
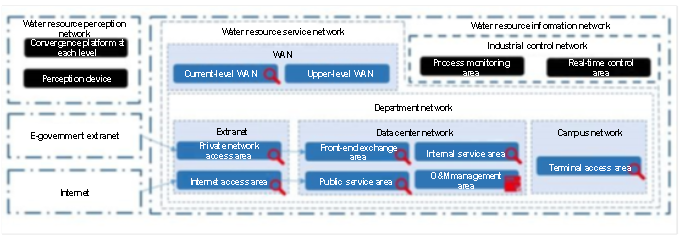
III. Features of water resources network security situation awareness solutions
H3C water resource security situation awareness solution covers a process of obtaining, interpreting, assessing, and presenting the factors that can cause changes in a network situation and predicting the future trend, based on security big data. From a global viewpoint, it can improve the detection and identification, understanding and analysis, reaction, and disposal of security threats. Moreover, the solution can also implement the closed-loop decision of the "security brain" and the practice of security capabilities through intelligent analysis and collaborative response with machine learning and artificial intelligence, thus truly achieving "proactive discovery, foreseeing the future, collaborative defense, and intelligent evolution" of security risks and threats.
H3C water resource security situation awareness solution covers the entire process of security risk monitoring, analysis, response, and prediction. By taking threats, risks, assets, services, and users as objects, it achieves the "evaluability of situations" through global status evaluation, external attack rating, and system compliance self-inspection, implements the “predictability of trends” through attack trend analysis, abnormal traffic assessment, and terminal behavior detection, realizes the "awareness of risks" through the intelligent detection and identification of unknown threats, traffic/behavior/asset status monitoring, and multi-dimensional risk analysis, and obtains the "control of knowledge and behavior" through attack tracing and forensics, cloud-network-terminal collaboration, closed-loop processing of work orders, and adaptive adjustment of device strategies based on security logs, network traffic, user behavior, terminal logs, business data, asset status, and other multi-source data, as well as external information.
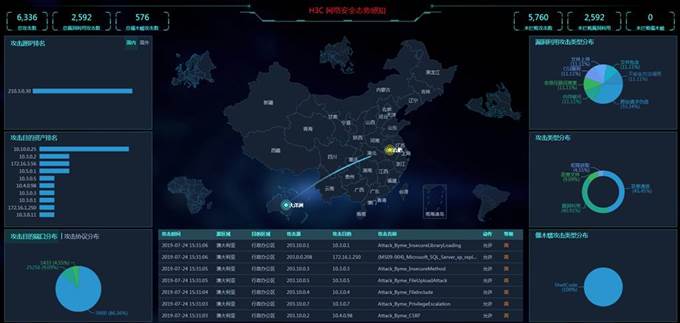
H3C water resource security situation awareness solution dashboard
Diverse data collection
![]() Supports the log collection of various network devices, security devices, vulnerability scanners, web crawlers, hosts and applications, and can access external threat intelligence.
Supports the log collection of various network devices, security devices, vulnerability scanners, web crawlers, hosts and applications, and can access external threat intelligence.
![]() Adopts active and passive data collection technologies to collect heterogeneous and massive logs in the network in real time. It supports multiple log access methods, such as passive log collection via Syslog and HTTP/HTTPS, active log collection via FTP and database, and log collection via deployed agents.
Adopts active and passive data collection technologies to collect heterogeneous and massive logs in the network in real time. It supports multiple log access methods, such as passive log collection via Syslog and HTTP/HTTPS, active log collection via FTP and database, and log collection via deployed agents.
![]() Supports centralized/distributed storage of massive logs and full life-cycle management.
Supports centralized/distributed storage of massive logs and full life-cycle management.
![]() Supports rapid adaptation of logs from different manufacturers to the system through log normalization and log classification.
Supports rapid adaptation of logs from different manufacturers to the system through log normalization and log classification.
Multi-engine cooperative perception
![]() Security analysis engine: performs functions such as threat detection, anomaly discovery, attack tracing, situation presentation, and collaborative response.
Security analysis engine: performs functions such as threat detection, anomaly discovery, attack tracing, situation presentation, and collaborative response.
![]() Intelligent learning engine: builds discriminative models, predictive models, associative models, and learnable evolution models.
Intelligent learning engine: builds discriminative models, predictive models, associative models, and learnable evolution models.
![]() Web security engine: performs functions such as vulnerability detection, Trojan detection, web page tampering detection, and availability detection.
Web security engine: performs functions such as vulnerability detection, Trojan detection, web page tampering detection, and availability detection.
![]() Cloud-enabled O&M engine: performs baseline configuration, assessment of the classified protection compliance, asset risk monitoring, and operational status monitoring.
Cloud-enabled O&M engine: performs baseline configuration, assessment of the classified protection compliance, asset risk monitoring, and operational status monitoring.
![]() Cloud sandbox engine: performs the static and dynamic analysis of samples and virtual environment execution.
Cloud sandbox engine: performs the static and dynamic analysis of samples and virtual environment execution.
Intelligent threat analysis
![]() Discover potential security issues through data correlation analysis in multiple dimensions (including assets, vulnerabilities, statistics, and rules).
Discover potential security issues through data correlation analysis in multiple dimensions (including assets, vulnerabilities, statistics, and rules).
![]() Discover attack behavior and access violations through multi-dimensional data correlation analysis based on multiple embedded analysis rules.
Discover attack behavior and access violations through multi-dimensional data correlation analysis based on multiple embedded analysis rules.
![]() Discover threats and predict trends through security analysis of wide-range sample data based on machine learning and expert systems.
Discover threats and predict trends through security analysis of wide-range sample data based on machine learning and expert systems.
![]() Build trend prediction models based on behavioral models through user behavior baselines, abnormal traffic baselines, and threat attack baselines.
Build trend prediction models based on behavioral models through user behavior baselines, abnormal traffic baselines, and threat attack baselines.
![]() Establish knowledge bases and continuously optimize models through machine learning and expert systems to achieve the self-healing immunity of the system.
Establish knowledge bases and continuously optimize models through machine learning and expert systems to achieve the self-healing immunity of the system.
Multi-dimensional risk alarms
![]() Uses the visualization technology to make fragmented data such as threat alarms, alarms of abnormal behaviors, and asset management data into structured data and forms a high-dimensional visualization view.
Uses the visualization technology to make fragmented data such as threat alarms, alarms of abnormal behaviors, and asset management data into structured data and forms a high-dimensional visualization view.
![]() Detects intrusion events in real time through network-wide threat intelligence and big data analysis, and displays data in various forms, including 3D charts, radar charts, topology maps, and heatmaps.
Detects intrusion events in real time through network-wide threat intelligence and big data analysis, and displays data in various forms, including 3D charts, radar charts, topology maps, and heatmaps.
![]() Displays risks from different perspectives and dimensions based on big data about security, realizing real-time monitoring and early warning of security events.
Displays risks from different perspectives and dimensions based on big data about security, realizing real-time monitoring and early warning of security events.
Traceability and forensics in whole process
![]() Visualize the complete attack chain through the multi-dimensional expansion of any clue left by the attacker.
Visualize the complete attack chain through the multi-dimensional expansion of any clue left by the attacker.
![]() Trace and investigate the security events, and customize the investigation of the effect and system defense effect of attacks with the full original log retrieval function.
Trace and investigate the security events, and customize the investigation of the effect and system defense effect of attacks with the full original log retrieval function.
![]() Present users with the complete process of an attack, covering the source, means, target, scope, and other relevant information of the attack, and allows for rapid tracing and characterization of the unknown threats by using rich real-time threat information on the cloud, as well as local network behavior, terminal behavior, and file information.
Present users with the complete process of an attack, covering the source, means, target, scope, and other relevant information of the attack, and allows for rapid tracing and characterization of the unknown threats by using rich real-time threat information on the cloud, as well as local network behavior, terminal behavior, and file information.
Cloud-network-terminal collaboration
![]() Builds a repository for policy management and quickly generates emergency response plans for early warning, response, and dispose of security incidents.
Builds a repository for policy management and quickly generates emergency response plans for early warning, response, and dispose of security incidents.
![]() Detects attacks in the cloud and forms an active defense system featuring cloud-network synergy, to implement closed-loop feedback control.
Detects attacks in the cloud and forms an active defense system featuring cloud-network synergy, to implement closed-loop feedback control.
![]() Adopts cloud-network-terminal collaboration, makes decisions and responses automatically based on real-time scenarios, and pushes security policies to network-wide key devices.
Adopts cloud-network-terminal collaboration, makes decisions and responses automatically based on real-time scenarios, and pushes security policies to network-wide key devices.
Automatic O&M response
![]() Monitors the status of key objects in real time, conducts risk analysis of important assets, and dynamically manages assets by classification and hierarchy.
Monitors the status of key objects in real time, conducts risk analysis of important assets, and dynamically manages assets by classification and hierarchy.
![]() Quickly generates configuration policies and task orders in case of a system state change, enabling quick response and disposal of O&M.
Quickly generates configuration policies and task orders in case of a system state change, enabling quick response and disposal of O&M.
![]() Supports the operational management of work orders, enabling automatic triggering, dispatching, tracking, reminding, and closing of work orders.
Supports the operational management of work orders, enabling automatic triggering, dispatching, tracking, reminding, and closing of work orders.
![]() Provides simple and easy deployment, modular design, and flexible expansion.
Provides simple and easy deployment, modular design, and flexible expansion.
Standardized compliance check
![]() Act as a security compliance self-inspection platform with a built-in professional classified protection work box to provide references for users to check the security compliance.
Act as a security compliance self-inspection platform with a built-in professional classified protection work box to provide references for users to check the security compliance.
![]() Comply with the information security standards including ISO 27001 and meet national classified protection and graded protection regulations as well as industry security requirements in terms of the architecture.
Comply with the information security standards including ISO 27001 and meet national classified protection and graded protection regulations as well as industry security requirements in terms of the architecture.
![]() Regularly conduct system security self-inspection and assessment in compliance with the requirements of internal control management regulations, classified protection, and graded protection.
Regularly conduct system security self-inspection and assessment in compliance with the requirements of internal control management regulations, classified protection, and graded protection.
![]() Equipped with professional staff and evaluation systems to conduct safety planning assessments and effectiveness checks before and after the construction and renovation.
Equipped with professional staff and evaluation systems to conduct safety planning assessments and effectiveness checks before and after the construction and renovation.
Product features
By collecting raw traffic data from the entire network and integrating it with threat information on the cloud to process and correlate the vast security data, H3C water resource security situation awareness solution detects the five primary aspects of attack, threat, traffic, behavior, and compliance, and creates a comprehensive security panoramic view to help users master the current security situation of the network and use it as the foundation for collaborative response.

Item | Feature |
Temperature | Operating: 5°C to 35°C Non-operating: -40°C to +65°C |
Humidity | Operating: 10% to 80% Non-operating: 5% to 95%, non-condensing |
Security situation display | Support network attack situation display, threat situation display, and vulnerability situation display. |
Association rules | Real-time association analysis: associates logs within a certain period and reports relevant alarms in real time. |
Historical association analysis: detects and analyzes multiple associated events over a long period. | |
Support custom association rules. | |
Threat alarms | Send alarms to users by SMS, email, and other means after network attacks occur. |
Threat analysis | Restore the attack process in response to threat events. |
Log audit | Audit the received logs. |
Behavior profiling | Support user behavior profiling and provide a timeline of the user's behavior. |
Traffic statistics | Support network application traffic analysis, intranet asset traffic analysis, and user traffic analysis. |
O&M monitoring | Support assets and asset groups: Assets include host devices, network devices, security devices, middleware, databases, and application systems. |
Asset management: Supports the manual addition, import, and automatic discovery of assets. | |
Compliance check | Support classified protection compliance check. |
Reports | Provide embedded predefined reports and support custom reports, which can be exported to a variety of formats, including PDF, HTML, DOCX, and XLS. |
Permission management | System administrator, security administrator, and audit administrator permissions are separated, and users can be authenticated locally and externally when they log in. |
System management | Support system status monitoring, including service node monitoring and service process status monitoring. Support sending alarms by SMS, WeChat, email, and other methods. |
Order information
H3C water resource security situation awareness solution can be purchased by part based on actual needs, including host, log collector, traffic detection engine, software license, and accessories.

