- Table of Contents
- Related Documents
-
01-Text
Download Book (2.96 MB)Contents
Information transmission techniques
Multicast benefits and applications
Multicast packet forwarding mechanism
IGMP snooping configuration task list
IGMP snooping configuration task list for VLANs
IGMP configuration task list for VSIs
Configuring basic IGMP snooping features
Specifying an IGMP snooping version
Setting the maximum number of IGMP snooping forwarding entries
Configuring static multicast MAC address entries
Setting the IGMP last member query interval
Configuring IGMP snooping port features
Setting aging timers for dynamic ports
Configuring a port as a simulated member host
Enabling fast-leave processing
Disabling a port from becoming a dynamic router port
Enabling inner VLAN ID-based forwarding
Configuring the IGMP snooping querier
Enabling the IGMP snooping querier
Configuring parameters for IGMP general queries and responses
Enabling IGMP snooping proxying
Configuring parameters for IGMP messages
Configuring source IP addresses for IGMP messages
Setting the 802.1p priority for IGMP messages
Configuring IGMP snooping policies
Configuring a multicast group policy
Enabling multicast source port filtering
Enabling dropping unknown multicast data
Enabling IGMP report suppression
Setting the maximum number of multicast groups on a port
Enabling multicast group replacement
Displaying and maintaining IGMP snooping
IGMP snooping configuration examples
Group policy and simulated joining configuration example(for VLANs)
Static port configuration example (for VLANs)
IGMP snooping querier configuration example (for VLANs)
IGMP snooping proxying configuration example (for VLANs)
Layer 2 multicast forwarding cannot function
Multicast group policy does not work
Displaying and maintaining PIM snooping
PIM snooping configuration example (for VLANs)
PIM snooping does not work on a Layer 2 device
Multicast VLAN configuration task list
Configuring a sub-VLAN-based multicast VLAN
Configuration restrictions and guidelines
Configuring a port-based multicast VLAN
Configuring user port attributes
Assigning user ports to a multicast VLAN
Setting the maximum number of multicast VLAN forwarding entries
Displaying and maintaining multicast VLANs
Multicast VLAN configuration examples
Sub-VLAN-based multicast VLAN configuration example
Port-based multicast VLAN configuration example
Configuring multicast routing and forwarding
Multicast forwarding across unicast subnets
Configuring multicast routing and forwarding
Configuring static multicast routes
Specifying the longest prefix match principle
Configuring multicast load splitting
Configuring a multicast forwarding boundary
Setting the multicast hardware resource mode
Displaying and maintaining multicast routing and forwarding
Multicast routing and forwarding configuration examples
Troubleshooting multicast routing and forwarding
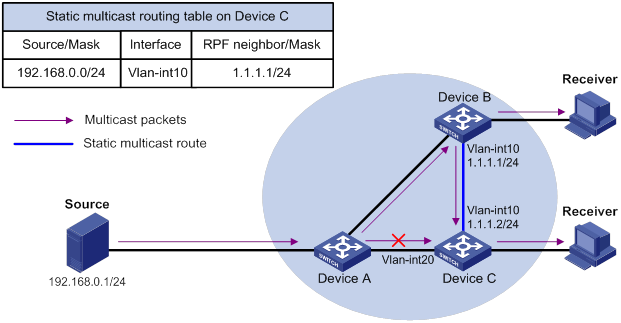
Static multicast route failure
Configuring basic IGMP features
Configuring a static group member
Configuring a multicast group policy
Configuring IGMP query and response parameters
Enabling fast-leave processing
Enabling multicast forwarding on a non-querier interface
Configuring multicast load splitting on an IGMP proxy
Displaying and maintaining IGMP
Basic IGMP features configuration example
IGMP SSM mapping configuration example
IGMP proxying configuration example
No membership information on the receiver-side router
Inconsistent membership information on the routers on the same subnet
Administrative scoping overview
Relationship among PIM protocols
PIM-DM configuration task list
Enabling the state refresh feature
Configuring state refresh parameters
Configuring the PIM-DM graft retry timer
PIM-SM configuration task list
Configuring multicast source registration
PIM-SSM configuration task list
Configuring the SSM group range
Configuring common PIM features
Configuring a multicast source policy
Configuring a PIM hello policy
Configuring PIM hello message options
Setting the maximum size of a join or prune message
Enabling SNMP notifications for PIM
Setting a DSCP value for outgoing PIM messages
Displaying and maintaining PIM
PIM-SM non-scoped zone configuration example
PIM-SM admin-scoped zone configuration example
A multicast distribution tree cannot be correctly built
Multicast data is abnormally terminated on an intermediate router
An RP cannot join an SPT in PIM-SM
An RPT cannot be built or multicast source registration fails in PIM-SM
Configuring basic MSDP features
Configuring an MSDP peering connection
Configuring a description for an MSDP peer
Configuring an MSDP mesh group
Controlling MSDP peering connections
Configuring SA message-related parameters
Enabling multicast data encapsulation in SA messages
Configuring the originating RP of SA messages
Configuring SA request messages
Configuring SA message policies
Configuring the SA cache mechanism
Displaying and maintaining MSDP
PIM-SM inter-domain multicast configuration
Inter-AS multicast configuration by leveraging static RPF peers
SA message filtering configuration
MSDP peers stay in disabled state
No SA entries exist in the router's SA message cache
No exchange of locally registered (S, G) entries between RPs
MLD snooping configuration task list
MLD snooping configuration task list for VLANs
MLD snooping configuration task list for VSIs
Configuring basic MLD snooping features
Setting the maximum number of MLD snooping forwarding entries
Configuring static IPv6 multicast MAC address entries
Setting the MLD last listener query interval
Configuring MLD snooping port features
Setting aging timers for dynamic ports
Configuring a port as a simulated member host
Enabling fast-leave processing
Disabling a port from becoming a dynamic router port
Enabling inner VLAN ID-based forwarding
Configuring the MLD snooping querier
Enabling the MLD snooping querier
Configuring parameters for MLD general queries and responses
Enabling MLD snooping proxying
Configuring parameters for MLD messages
Configuring source IPv6 addresses for MLD messages
Setting the 802.1p priority for MLD messages
Configuring MLD snooping policies
Configuring an IPv6 multicast group policy
Enabling IPv6 multicast source port filtering
Enabling dropping unknown IPv6 multicast data
Enabling MLD report suppression
Setting the maximum number of IPv6 multicast groups on a port
Enabling IPv6 multicast group replacement
Displaying and maintaining MLD snooping
MLD snooping configuration examples
IPv6 group policy and simulated joining configuration example (for VLANs)
Static port configuration example (for VLANs)
MLD snooping querier configuration example (for VLANs)
MLD snooping proxying configuration example (for VLANs)
Layer 2 multicast forwarding cannot function
IPv6 multicast group policy does not work
Multicast overview
Introduction to multicast
As a technique that coexists with unicast and broadcast, the multicast technique effectively addresses the issue of point-to-multipoint data transmission. By enabling high-efficiency point-to-multipoint data transmission over a network, multicast greatly saves network bandwidth and reduces network load.
By using multicast technology, a network operator can easily provide bandwidth-critical and time-critical information services. These services include live webcasting, Web TV, distance learning, telemedicine, Web radio, and real-time video conferencing.
Information transmission techniques
The information transmission techniques include unicast, broadcast, and multicast.
Unicast
In unicast transmission, the information source must send a separate copy of information to each host that needs the information.
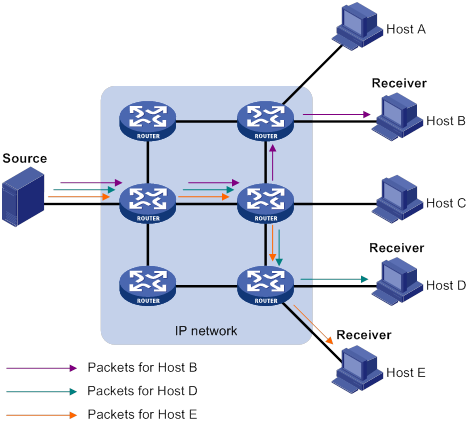
In Figure 1, Host B, Host D, and Host E need the information. A separate transmission channel must be established from the information source to each of these hosts.
In unicast transmission, the traffic transmitted over the network is proportional to the number of hosts that need the information. If a large number of hosts need the information, the information source must send a separate copy of the same information to each of these hosts. Sending many copies can place a tremendous pressure on the information source and the network bandwidth.
Unicast is not suitable for batch transmission of information.
Broadcast
In broadcast transmission, the information source sends information to all hosts on the subnet, even if some hosts do not need the information.
Figure 2 Broadcast transmission
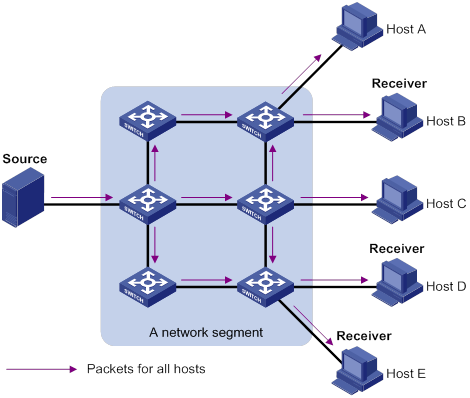
In Figure 2, only Host B, Host D, and Host E need the information. If the information is broadcast to the subnet, Host A and Host C also receive it. In addition to information security issues, broadcasting to hosts that do not need the information also causes traffic flooding on the same subnet.
Broadcast is disadvantageous in transmitting data to specific hosts. Moreover, broadcast transmission is a significant waste of network resources.
Multicast
Multicast provides point-to-multipoint data transmissions with the minimum network consumption. When some hosts on the network need multicast information, the information sender, or multicast source, sends only one copy of the information. Multicast distribution trees are built through multicast routing protocols, and the packets are replicated only on nodes where the trees branch.
Figure 3 Multicast transmission
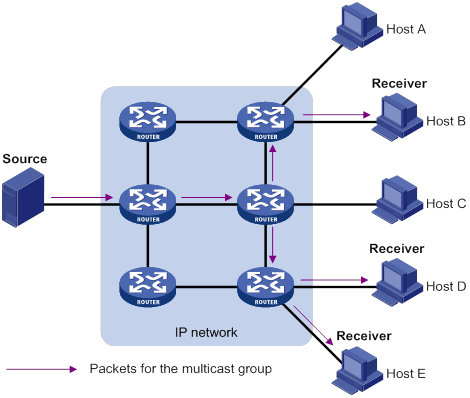
In Figure 3, the multicast source sends only one copy of the information to a multicast group. Host B, Host D, and Host E, which are information receivers, must join the multicast group. The routers on the network duplicate and forward the information based on the distribution of the group members. Finally, the information is correctly delivered to Host B, Host D, and Host E.
To summarize, multicast has the following advantages:
· Advantages over unicast—Multicast data is replicated and distributed until it flows to the farthest-possible node from the source. The increase of receiver hosts will not remarkably increase the load of the source or the usage of network resources.
· Advantages over broadcast—Multicast data is sent only to the receivers that need it. This saves network bandwidth and enhances network security. In addition, multicast data is not confined to the same subnet.
Multicast features
· A multicast group is a multicast receiver set identified by an IP multicast address. Hosts must join a multicast group to become members of the multicast group before they receive the multicast data addressed to that multicast group. Typically, a multicast source does not need to join a multicast group.
· A multicast source is an information sender. It can send data to multiple multicast groups at the same time. Multiple multicast sources can send data to the same multicast group at the same time.
· The group memberships are dynamic. Hosts can join or leave multicast groups at any time. Multicast groups are not subject to geographic restrictions.
· Multicast routers or Layer 3 multicast devices are routers or Layer 3 switches that support Layer 3 multicast. They provide multicast routing and manage multicast group memberships on stub subnets with attached group members. A multicast router itself can be a multicast group member.
For a better understanding of the multicast concept, you can compare multicast transmission to the transmission of TV programs.
Table 1 Comparing TV program transmission and multicast transmission
|
TV program transmission |
Multicast transmission |
|
A TV station transmits a TV program through a channel. |
A multicast source sends multicast data to a multicast group. |
|
A user tunes the TV set to the channel. |
A receiver joins the multicast group. |
|
The user starts to watch the TV program transmitted by the TV station on the channel. |
The receiver starts to receive the multicast data sent by the source to the multicast group. |
|
The user turns off the TV set or tunes to another channel. |
The receiver leaves the multicast group or joins another group. |
Common notations in multicast
The following notations are commonly used in multicast transmission:
· (*, G)—Rendezvous point tree (RPT), or a multicast packet that any multicast source sends to multicast group G. The asterisk (*) represents any multicast source, and "G" represents a specific multicast group.
· (S, G)—Shortest path tree (SPT), or a multicast packet that multicast source "S" sends to multicast group "G." "S" represents a specific multicast source, and "G" represents a specific multicast group.
For more information about the concepts RPT and SPT, see "Configuring PIM."
Multicast benefits and applications
Multicast benefits
· Enhanced efficiency—Reduces the processor load of information source servers and network devices.
· Optimal performance—Reduces redundant traffic.
· Distributed application—Enables point-to-multipoint applications at the price of minimum network resources.
Multicast applications
· Multimedia and streaming applications, such as Web TV, Web radio, and real-time video/audio conferencing
· Communication for training and cooperative operations, such as distance learning and telemedicine
· Data warehouse and financial applications (stock quotes)
· Any other point-to-multipoint application for data distribution
Multicast models
Based on how the receivers treat the multicast sources, the multicast models include any-source multicast (ASM), source-filtered multicast (SFM), and source-specific multicast (SSM).
ASM model
In the ASM model, any multicast sources can send information to a multicast group. Receivers can join a multicast group and get multicast information addressed to that multicast group from any multicast sources. In this model, receivers do not know the positions of the multicast sources in advance.
SFM model
The SFM model is derived from the ASM model. To a multicast source, the two models appear to have the same multicast membership architecture.
The SFM model functionally extends the ASM model. The upper-layer software checks the source address of received multicast packets and permits or denies multicast traffic from specific sources. The receivers obtain the multicast data from only part of the multicast sources. To a receiver, multicast sources are not all valid, but are filtered.
SSM model
The SSM model provides a transmission service that enables multicast receivers to specify the multicast sources in which they are interested.
In the SSM model, receivers have already determined the locations of the multicast sources. This is the main difference between the SSM model and the ASM model. In addition, the SSM model uses a different multicast address range than the ASM/SFM model. Dedicated multicast forwarding paths are established between receivers and the specified multicast sources.
IP multicast architecture
IP multicast addresses the following issues:
· Where should the multicast source transmit information to? (Multicast addressing.)
· What receivers exist on the network? (Host registration.)
· Where is the multicast source that will provide data to the receivers? (Multicast source discovery.)
· How is the information transmitted to the receivers? (Multicast routing.)
IP multicast is an end-to-end service. The multicast architecture involves the following parts:
· Addressing mechanism—A multicast source sends information to a group of receivers through a multicast address.
· Host registration—Receiver hosts can join and leave multicast groups dynamically. This mechanism is the basis for management of group memberships.
· Multicast routing—A multicast distribution tree (a forwarding path tree for multicast data on the network) is constructed for delivering multicast data from a multicast source to receivers.
· Multicast applications—A software system that supports multicast applications, such as video conferencing, must be installed on multicast sources and receiver hosts. The TCP/IP stack must support reception and transmission of multicast data.
Multicast addresses
IP multicast addresses
· IPv4 multicast addresses:
IANA assigned the Class D address block (224.0.0.0 to 239.255.255.255) to IPv4 multicast.
Table 2 Class D IP address blocks and description
|
Address block |
Description |
|
224.0.0.0 to 224.0.0.255 |
Reserved permanent group addresses. The IP address 224.0.0.0 is reserved. Other IP addresses can be used by routing protocols and for topology searching, protocol maintenance, and so on. Table 3 lists common permanent group addresses. A packet destined for an address in this block will not be forwarded beyond the local subnet regardless of the TTL value in the IP header. |
|
224.0.1.0 to 238.255.255.255 |
Globally scoped group addresses. This block includes the following types of designated group addresses: · 232.0.0.0/8—SSM group addresses. · 233.0.0.0/8—Glop group addresses. |
|
239.0.0.0 to 239.255.255.255 |
Administratively scoped multicast addresses. These addresses are considered locally unique rather than globally unique. You can reuse them in domains administered by different organizations without causing conflicts. For more information, see RFC 2365. |
|
|
NOTE: Glop is a mechanism for assigning multicast addresses between different ASs. By filling an AS number into the middle two bytes of 233.0.0.0, you get 255 multicast addresses for that AS. For more information, see RFC 2770. |
Table 3 Common permanent multicast group addresses
|
Address |
Description |
|
224.0.0.1 |
All systems on this subnet, including hosts and routers. |
|
224.0.0.2 |
All multicast routers on this subnet. |
|
224.0.0.3 |
Unassigned. |
|
224.0.0.4 |
DVMRP routers. |
|
224.0.0.5 |
OSPF routers. |
|
224.0.0.6 |
OSPF designated routers and backup designated routers. |
|
224.0.0.7 |
Shared Tree (ST) routers. |
|
224.0.0.8 |
ST hosts. |
|
224.0.0.9 |
RIPv2 routers. |
|
224.0.0.11 |
Mobile agents. |
|
224.0.0.12 |
DHCP server/relay agent. |
|
224.0.0.13 |
All Protocol Independent Multicast (PIM) routers. |
|
224.0.0.14 |
RSVP encapsulation. |
|
224.0.0.15 |
All Core-Based Tree (CBT) routers. |
|
224.0.0.16 |
Designated SBM. |
|
224.0.0.17 |
All SBMs. |
|
224.0.0.18 |
VRRP. |
· IPv6 multicast addresses:
Figure 4 IPv6 multicast format
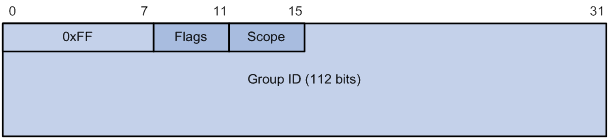
The following describes the fields of an IPv6 multicast address:
? 0xFF—The most significant eight bits are 11111111.
? Flags—The Flags field contains four bits.
Figure 5 Flags field format
![]()
Table 4 Flags field description
|
Bit |
Description |
|
0 |
Reserved, set to 0. |
|
R |
· When set to 0, this address is an IPv6 multicast address without an embedded RP address. · When set to 1, this address is an IPv6 multicast address with an embedded RP address. (The P and T bits must also be set to 1.) |
|
P |
· When set to 0, this address is an IPv6 multicast address not based on a unicast prefix. · When set to 1, this address is an IPv6 multicast address based on a unicast prefix. (The T bit must also be set to 1.) |
|
T |
· When set to 0, this address is an IPv6 multicast address permanently-assigned by IANA. · When set to 1, this address is a transient or dynamically assigned IPv6 multicast address. |
? Scope—The Scope field contains four bits, which represent the scope of the IPv6 internetwork for which the multicast traffic is intended.
Table 5 Values of the Scope field
|
Meaning |
|
|
0, F |
Reserved. |
|
1 |
Interface-local scope. |
|
2 |
Link-local scope. |
|
3 |
Subnet-local scope. |
|
4 |
Admin-local scope. |
|
5 |
Site-local scope. |
|
6, 7, 9 through D |
Unassigned. |
|
8 |
Organization-local scope. |
|
E |
Global scope. |
? Group ID—The Group ID field contains 112 bits. It uniquely identifies an IPv6 multicast group in the scope that the Scope field defines.
Ethernet multicast MAC addresses
· IPv4 multicast MAC addresses:
As defined by IANA, the most significant 24 bits of an IPv4 multicast MAC address are 0x01005E. Bit 25 is 0, and the other 23 bits are the least significant 23 bits of an IPv4 multicast address.
Figure 6 IPv4-to-MAC address mapping
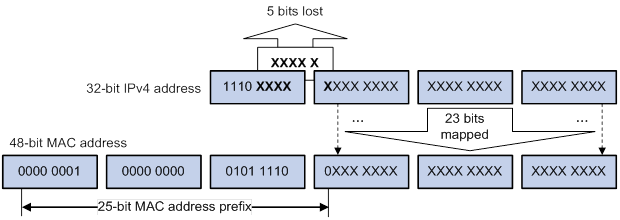
The most significant four bits of an IPv4 multicast address are fixed at 1110. In an IPv4-to-MAC address mapping, five bits of the IPv4 multicast address are lost. As a result, 32 IPv4 multicast addresses are mapped to the same IPv4 multicast MAC address. A device might receive unwanted multicast data at Layer 2 processing, which needs to be filtered by the upper layer.
· IPv6 multicast MAC addresses:
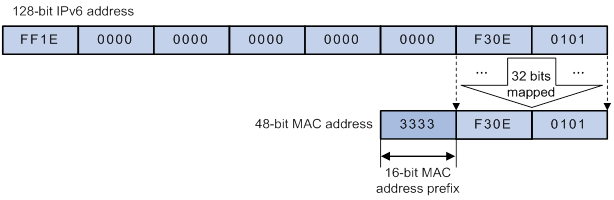
As defined by IANA, the most significant 16 bits of an IPv6 multicast MAC address are 0x3333. The least significant 32 bits are mapped from the least significant 32 bits of an IPv6 multicast address. Therefore, the problem of duplicate IPv6-to-MAC address mapping also arises like IPv4-to-MAC address mapping.
Figure 7 IPv6-to-MAC address mapping
|
|
IMPORTANT: Because of the duplicate mapping from multicast IP address to multicast MAC address, the device might inadvertently send multicast protocol packets as multicast data in Layer 2 forwarding. To avoid this, do not use the IP multicast addresses that are mapped to multicast MAC addresses 0100-5E00-00xx and 3333-0000-00xx (where "x" represents any hexadecimal number from 0 to F). |
Multicast protocols
Multicast protocols include the following categories:
· Layer 3 and Layer 2 multicast protocols:
? Layer 3 multicast refers to IP multicast operating at the network layer.
Layer 3 multicast protocols—IGMP, MLD, PIM, IPv6 PIM, MSDP, MBGP, and IPv6 MBGP.
? Layer 2 multicast refers to IP multicast operating at the data link layer.
Layer 2 multicast protocols—IGMP snooping, MLD snooping, PIM snooping, IPv6 PIM snooping, multicast VLAN, and IPv6 multicast VLAN.
· IPv4 and IPv6 multicast protocols:
? For IPv4 networks—IGMP snooping, PIM snooping, multicast VLAN, IGMP, PIM, MSDP, and MBGP.
? For IPv6 networks—MLD snooping, IPv6 PIM snooping, IPv6 multicast VLAN, MLD, IPv6 PIM, and IPv6 MBGP.
This section provides only general descriptions about applications and functions of the Layer 2 and Layer 3 multicast protocols in a network. For more information about these protocols, see the related chapters.
Layer 3 multicast protocols
In Figure 8, Layer 3 multicast protocols include multicast group management protocols and multicast routing protocols.
Figure 8 Positions of Layer 3 multicast protocols
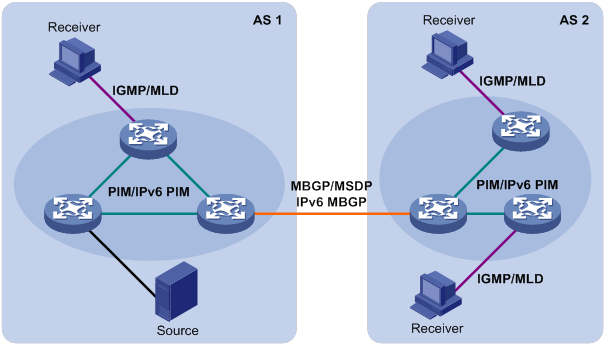
· Multicast group management protocols:
Internet Group Management Protocol (IGMP) and Multicast Listener Discovery (MLD) protocol are multicast group management protocols. Typically, they run between hosts and Layer 3 multicast devices that directly connect to the hosts to establish and maintain multicast group memberships.
· Multicast routing protocols:
A multicast routing protocol runs on Layer 3 multicast devices to establish and maintain multicast routes and correctly and efficiently forward multicast packets. Multicast routes constitute loop-free data transmission paths (also known as multicast distribution trees) from a data source to multiple receivers.
In the ASM model, multicast routes include intra-domain routes and inter-domain routes.
? An intra-domain multicast routing protocol discovers multicast sources and builds multicast distribution trees within an AS to deliver multicast data to receivers. Among a variety of mature intra-domain multicast routing protocols, PIM is most widely used. Based on the forwarding mechanism, PIM has dense mode (often referred to as PIM-DM) and sparse mode (often referred to as PIM-SM).
? An inter-domain multicast routing protocol is used for delivering multicast information between two ASs. So far, mature solutions include Multicast Source Discovery Protocol (MSDP) and MBGP. MSDP propagates multicast source information among different ASs. MBGP is an extension of the MP-BGP for exchanging multicast routing information among different ASs.
For the SSM model, multicast routes are not divided into intra-domain routes and inter-domain routes. Because receivers know the positions of the multicast sources, channels established through PIM-SM are sufficient for the transport of multicast information.
Layer 2 multicast protocols
In Figure 9, Layer 2 multicast protocols include IGMP snooping, MLD snooping, PIM snooping, IPv6 PIM snooping, multicast VLAN, and IPv6 multicast VLAN.
Figure 9 Positions of Layer 2 multicast protocols
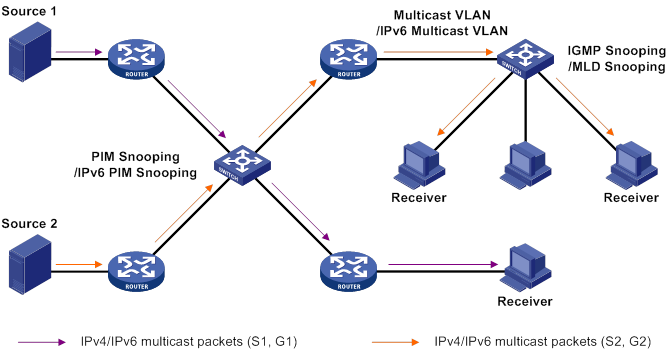
· IGMP snooping and MLD snooping:
IGMP snooping and MLD snooping are multicast constraining mechanisms that run on Layer 2 devices. They manage and control multicast groups by monitoring and analyzing IGMP or MLD messages exchanged between the hosts and Layer 3 multicast devices. This effectively controls the flooding of multicast data in Layer 2 networks.
· PIM snooping and IPv6 PIM snooping:
PIM snooping and IPv6 PIM snooping run on Layer 2 devices. They work with IGMP snooping or MLD snooping to analyze received PIM messages. Then, they add the ports that are interested in specific multicast data to a PIM snooping routing entry or IPv6 PIM snooping routing entry. In this way, multicast data can be forwarded to only the ports that are interested in the data.
· Multicast VLAN and IPv6 multicast VLAN:
Multicast VLAN or IPv6 multicast VLAN runs on a Layer 2 device in a multicast network where multicast receivers for the same group exist in different VLANs. With these protocols, the Layer 3 multicast device sends only one copy of multicast to the multicast VLAN or IPv6 multicast VLAN on the Layer 2 device. This method avoids waste of network bandwidth and extra burden on the Layer 3 device.
Multicast packet forwarding mechanism
In a multicast model, receiver hosts of a multicast group are usually located at different areas on the network. They are identified by the same multicast group address. To deliver multicast packets to these receivers, a multicast source encapsulates the multicast data in an IP packet with the multicast group address as the destination address. Multicast routers on the forwarding paths forward multicast packets that an incoming interface receives through multiple outgoing interfaces. Compared to a unicast model, a multicast model is more complex in the following aspects:
· To ensure multicast packet transmission on the network, different routing tables are used to guide multicast forwarding. These routing tables include unicast routing tables, routing tables for multicast (for example, the MBGP routing table), and static multicast routing tables.
· To process the same multicast information from different peers received on different interfaces, the multicast device performs an RPF check on each multicast packet. The RPF check result determines whether the packet will be forwarded or discarded. The RPF check mechanism is the basis for most multicast routing protocols to implement multicast forwarding.
For more information about the RPF mechanism, see "Configuring multicast routing and forwarding."
Configuring IGMP snooping
Overview
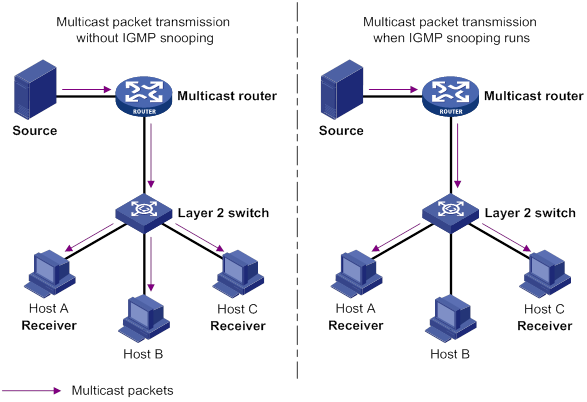
IGMP snooping runs on a Layer 2 device as a multicast constraining mechanism to improve multicast forwarding efficiency. It creates Layer 2 multicast forwarding entries from IGMP packets that are exchanged between the hosts and the router.
As shown in Figure 10, when IGMP snooping is not enabled, the Layer 2 switch floods multicast packets to all hosts in a VLAN or VSI. When IGMP snooping is enabled, the Layer 2 switch forwards multicast packets of known multicast groups to only the receivers.
Figure 10 Multicast packet transmission without and with IGMP snooping
IGMP snooping ports
As shown in Figure 11, IGMP snooping runs on Switch A and Switch B, and Host A and Host C are receivers in a multicast group. IGMP snooping ports are divided into member ports and router ports.
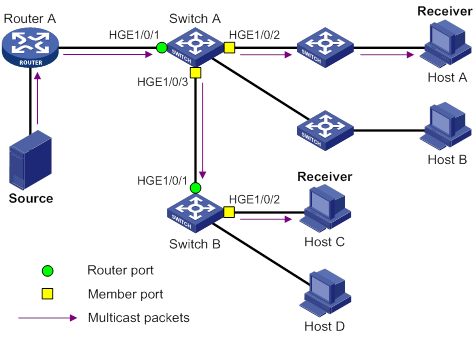
Router ports
On an IGMP snooping Layer 2 device, the ports toward Layer 3 multicast devices are called router ports. In Figure 11, HundredGigE 1/0/1 of Switch A and HundredGigE 1/0/1 of Switch B are router ports.
Router ports contain the following types:
· Dynamic router port—When a port receives an IGMP general query whose source address is not 0.0.0.0 or receives a PIM hello message, the port is added into the dynamic router port list. At the same time, an aging timer is started for the port. If the port receives either of the messages before the timer expires, the timer is reset. If the port does not receive either of the messages when the timer expires, the port is removed from the dynamic router port list.
· Static router port—When a port is statically configured as a router port, it is added into the static router port list. The static router port does not age out, and it can be deleted only manually.
Do not confuse the "router port" in IGMP snooping with the "routed interface" commonly known as the "Layer 3 interface." The router port in IGMP snooping is a Layer 2 interface.
Member ports
On an IGMP snooping Layer 2 device, the ports toward receiver hosts are called member ports. In Figure 11, HundredGigE 1/0/2 and HundredGigE 1/0/3 of Switch A and HundredGigE 1/0/2 of Switch B are member ports.
Member ports contain the following types:
· Dynamic member port—When a port receives an IGMP report, it is added to the associated dynamic IGMP snooping forwarding entry as an outgoing interface. At the same time, an aging timer is started for the port. If the port receives an IGMP report before the timer expires, the timer is reset. If the port does not receive an IGMP report when the timer expires, the port is removed from the associated dynamic forwarding entry.
· Static member port—When a port is statically configured as a member port, it is added to the associated static IGMP snooping forwarding entry as an outgoing interface. The static member port does not age out, and it can be deleted only manually.
Unless otherwise specified, router ports and member ports in this document include both static and dynamic router ports and member ports.
How IGMP snooping works
The ports in this section are dynamic ports. For information about how to configure and remove static ports, see "Configuring static ports."
IGMP messages types include general query, IGMP report, and leave message. An IGMP snooping-enabled Layer 2 device performs differently depending on the message types.
General query
The IGMP querier periodically sends IGMP general queries to all hosts and routers on the local subnet to check for the existence of multicast group members.
After receiving an IGMP general query, the Layer 2 device forwards the query to all ports in the VLAN or VSI except the receiving port. The Layer 2 device also performs one of the following actions:
· If the receiving port is a dynamic router port in the dynamic router port list, the Layer 2 device restarts the aging timer for the port.
· If the receiving port does not exist in the dynamic router port list, the Layer 2 device adds the port to the dynamic router port list. It also starts an aging timer for the port.
IGMP report
A host sends an IGMP report to the IGMP querier for the following purposes:
· Responds to queries if the host is a multicast group member.
· Applies for a multicast group membership.
After receiving an IGMP report from a host, the Layer 2 device forwards the report through all the router ports in the VLAN or VSI. It also resolves the address of the reported multicast group, and looks up the forwarding table for a matching entry as follows:
· If no match is found, the Layer 2 device creates a forwarding entry with the receiving port as an outgoing interface. It also marks the receiving port as a dynamic member port and starts an aging timer for the port.
· If a match is found but the matching forwarding entry does not contain the receiving port, the Layer 2 device adds the receiving port to the outgoing interface list. It also marks the receiving port as a dynamic member port and starts an aging timer for the port.
· If a match is found and the matching forwarding entry contains the receiving port, the Layer 2 device restarts the aging timer for the port.
In an application with a group policy configured on an IGMP snooping-enabled Layer 2 device, when a user requests a multicast program, the user's host initiates an IGMP report. After receiving this report, the Layer 2 device resolves the multicast group address in the report and performs ACL filtering on the report. If the report passes ACL filtering, the Layer 2 device creates an IGMP snooping forwarding entry for the multicast group with the receiving port as an outgoing interface. If the report does not pass ACL filtering, the Layer 2 device drops this report. The multicast data for the multicast group is not sent to this port, and the user cannot retrieve the program.
A Layer 2 device does not forward an IGMP report through a non-router port because of the host IGMP report suppression mechanism. For more information about the IGMP report suppression mechanism, see "Configuring IGMP."
Leave message
An IGMPv1 receiver host does not send any leave messages when it leaves a multicast group. The Layer 2 device cannot immediately update the status of the port that connects to the receiver host. The Layer 2 device does not remove the port from the outgoing interface list in the associated forwarding entry until the aging time for the group expires.
An IGMPv2 or IGMPv3 host sends an IGMP leave message when it leaves a multicast group.
When the Layer 2 device receives an IGMP leave message on a dynamic member port, the Layer 2 device first examines whether a forwarding entry matches the group address in the message.
· If no match is found, the Layer 2 device discards the IGMP leave message.
· If a match is found but the receiving port is not an outgoing interface in the forwarding entry, the Layer 2 device discards the IGMP leave message.
· If a match is found and the receiving port is not the only outgoing interface in the forwarding entry, the Layer 2 device performs the following actions:
? Discards the IGMP leave message.
? Sends an IGMP group-specific query to identify whether the group has active receivers attached to the receiving port.
? Sets the aging timer for the receiving port to twice the IGMP last member query interval.
· If a match is found and the receiving port is the only outgoing interface in the forwarding entry, the Layer 2 device performs the following actions:
? Forwards the IGMP leave message to all router ports in the VLAN or VSI.
? Sends an IGMP group-specific query to identify whether the group has active receivers attached to the receiving port.
? Sets the aging timer for the receiving port to twice the IGMP last member query interval.
After receiving the IGMP leave message on a port, the IGMP querier resolves the multicast group address in the message. Then, it sends an IGMP group-specific query to the multicast group through the receiving port.
After receiving the IGMP group-specific query, the Layer 2 device forwards the query through all router ports and member ports of the group in the VLAN or VSI. Then, it waits for the responding IGMP report from the directly connected hosts. For the dynamic member port that received the leave message, the Layer 2 device also performs one of the following actions:
· If the port receives an IGMP report before the aging timer expires, the Layer 2 device resets the aging timer.
· If the port does not receive an IGMP report when the aging timer expires, the Layer 2 device removes the port from the forwarding entry for the multicast group.
IGMP snooping proxying
As shown in Figure 12, to reduce the number of IGMP report and leave messages received by the upstream device, you can enable IGMP snooping proxying on the edge device. With IGMP snooping proxying enabled, the edge device acts as a host for the upstream IGMP snooping querier to send IGMP report and leave messages to Router A. The host IGMP report suppression mechanism on the edge device does not take effect. For more information about the IGMP report suppression mechanism, see "Configuring IGMP."
Figure 12 IGMP snooping proxying
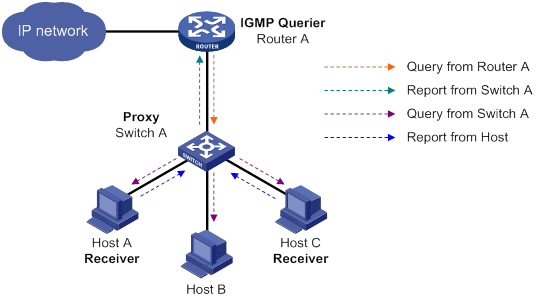
The IGMP snooping proxy device processes different IGMP messages as follows:
· General query.
After receiving an IGMP general query, the device forwards the query to all ports in the VLAN except the receiving port. The device also generates an IGMP report based on the local membership information and sends the report to all router ports.
· Group-specific query or group-and-source-specific query.
After receiving an IGMP group-specific query or group-and-source-specific query, the device forwards the query to all ports in the VLAN except the receiving port. If the forwarding entry has a member port, the device sends a report to all router ports in the VLAN.
· Report.
After receiving an IGMP report from a host, the device looks up the forwarding table for a matching entry as follows:
? If a match is found and the matching forwarding entry contains the receiving port, the device resets the aging timer for the port.
? If a match is found but the matching forwarding entry does not contain the receiving port, the device adds the receiving port to the outgoing interface list. It also marks the receiving port as a dynamic member port and starts an aging timer for the port.
? If no match is found, the device creates a forwarding entry with the receiving port as an outgoing interface. It also marks the receiving port as a dynamic member port and starts an aging timer for the port. Then it sends the report to all router ports.
· Leave message.
After receiving the IGMP leave message on a port, the device sends an IGMP group-specific query through the receiving port. The device sends the IGMP leave message to all router ports only when the last member port is removed from the forwarding entry.
Protocols and standards
RFC 4541, Considerations for Internet Group Management Protocol (IGMP) and Multicast Listener Discovery (MLD) Snooping Switches
IGMP snooping configuration task list
You can configure IGMP snooping for VLANs or VSIs.
IGMP snooping configuration task list for VLANs
IGMP configuration task list for VSIs
|
Tasks at a glance |
|
Configuring basic IGMP snooping features: · (Required.) Enabling IGMP snooping · (Optional.) Specifying an IGMP snooping version · (Optional.) Setting the maximum number of IGMP snooping forwarding entries · (Optional.) Setting the IGMP last member query interval |
|
Configuring IGMP snooping port features: (Optional.) Setting aging timers for dynamic ports |
|
Configuring the IGMP snooping querier: · (Optional.) Enabling the IGMP snooping querier · (Optional.) Configuring parameters for IGMP general queries and responses |
|
Configuring parameters for IGMP messages: · (Optional.) Configuring source IP addresses for IGMP messages · (Optional.) Setting the 802.1p priority for IGMP messages |
|
Configuring IGMP snooping policies: · (Optional.) Enabling dropping unknown multicast data · (Optional.) Enabling IGMP report suppression |
The IGMP snooping configurations made on Layer 2 aggregate interfaces do not interfere with the configurations made on member ports. In addition, the configurations made on Layer 2 aggregate interfaces do not take part in aggregation calculations. The configuration made on a member port of the aggregate group takes effect after the port leaves the aggregate group.
Configuring basic IGMP snooping features
Before you configure basic IGMP snooping features, complete the following tasks:
· Configure VLANs or VSIs.
· Determine the IGMP snooping version.
· Determine the maximum number of IGMP snooping forwarding entries.
· Determine the IGMP last member query interval.
Enabling IGMP snooping
When you enable IGMP snooping, follow these restrictions and guidelines:
· You must enable IGMP snooping globally before you enable it for a VLAN or VSI.
· IGMP snooping configuration made in VLAN view or VSI view takes effect only on the member ports in that VLAN or VSI.
· You can enable IGMP snooping for the specified VLANs in IGMP-snooping view, for a VSI in VSI view, or for a VLAN in VLAN view. For a VLAN, the configuration in VLAN view has the same priority as the configuration in IGMP-snooping view, and the most recent configuration takes effect.
Enabling IGMP snooping in IGMP-snooping view
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable IGMP snooping globally and enter IGMP-snooping view. |
igmp-snooping |
By default, IGMP snooping is globally disabled. |
|
3. Enable IGMP snooping for the specified VLANs. |
enable vlan vlan-list |
By default, IGMP snooping is disabled for a VLAN. |
Enabling IGMP snooping in VLAN or VSI view
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable IGMP snooping globally and enter IGMP-snooping view. |
igmp-snooping |
By default, IGMP snooping is globally disabled. |
|
3. Return to system view. |
quit |
N/A |
|
4. Enter VLAN or VSI view. |
·
Enter VLAN view: ·
Enter VSI view: |
N/A |
|
5. Enable IGMP snooping for the VLAN or VSI. |
igmp-snooping enable |
By default, IGMP snooping is disabled in a VLAN or VSI. |
Specifying an IGMP snooping version
Different IGMP snooping versions process different versions of IGMP messages.
· IGMPv2 snooping processes IGMPv1 and IGMPv2 messages, but it floods IGMPv3 messages in the VLAN instead of processing them.
· IGMPv3 snooping processes IGMPv1, IGMPv2, and IGMPv3 messages.
If you change IGMPv3 snooping to IGMPv2 snooping, the device performs the following actions:
· Clears all IGMP snooping forwarding entries that are dynamically added.
· Keeps static IGMPv3 snooping forwarding entries (*, G).
· Clears static IGMPv3 snooping forwarding entries (S, G), which will be restored when IGMP snooping is switched back to IGMPv3 snooping.
For more information about static IGMP snooping forwarding entries, see "Configuring static ports."
You can specify the version for the specified VLANs in IGMP-snooping view, for a VSI in VSI view, or for a VLAN in VLAN view. For a VLAN, the configuration in VLAN view has the same priority as the configuration in IGMP-snooping view, and the most recent configuration takes effect.
Specifying an IGMP snooping version in IGMP-snooping view
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable IGMP snooping globally and enter IGMP-snooping view. |
igmp-snooping |
N/A |
|
3. Specify an IGMP snooping version for the specified VLANs. |
version version-number vlan vlan-list |
The default setting is 2. |
Specifying an IGMP snooping version in VLAN or VSI view
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter VLAN view or VSI view. |
·
Enter VLAN view: ·
Enter VSI view: |
N/A |
|
3. Specify an IGMP snooping version for the VLAN or VSI. |
igmp-snooping version version-number |
The default setting is 2. |
Setting the maximum number of IGMP snooping forwarding entries
You can modify the maximum number of IGMP snooping forwarding entries, including dynamic entries and static entries. When the number of forwarding entries on the device reaches the upper limit, the device does not automatically remove any existing entries. To allow new entries to be created, remove some entries manually.
To set the maximum number of IGMP snooping forwarding entries:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter IGMP-snooping view. |
igmp-snooping |
N/A |
|
3. Set the maximum number of IGMP snooping forwarding entries. |
entry-limit limit |
The default setting is 4294967295. |
Configuring static multicast MAC address entries
In Layer 2 multicast, multicast MAC address entries can be dynamically created through Layer 2 multicast protocols (such as IGMP snooping). You can also manually configure static multicast MAC address entries by binding multicast MAC addresses and ports to control the destination ports of the multicast data.
Configuration restrictions and guidelines
When you configure static multicast MAC address entries, follow these restrictions and guidelines:
· You do not need to enable IP multicast routing before this configuration.
· You must specify an unused multicast MAC address when configuring a static multicast MAC address entry. A multicast MAC address is a MAC address in which the least significant bit of the most significant octet is 1.
· You can configure static multicast MAC address entries on the specified interfaces in system view or on the current interface in interface view.
Configuring a static multicast MAC address entry in system view
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Configure a static multicast MAC address entry. |
mac-address multicast mac-address interface interface-list vlan vlan-id |
By default, no static multicast MAC address entries exist. |
Configuring a static multicast MAC address entry in interface view
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter Layer 2 Ethernet interface or Layer 2 aggregate interface view. |
interface interface-type interface-number |
N/A |
|
3. Configure a static multicast MAC address entry. |
mac-address multicast mac-address vlan vlan-id |
By default, no static multicast MAC address entries exist. |
Setting the IGMP last member query interval
A receiver host starts a report delay timer for a multicast group when it receives an IGMP group-specific query for the group. This timer is set to a random value in the range of 0 to the maximum response time advertised in the query. When the timer value decreases to 0, the host sends an IGMP report to the group.
The IGMP last member query interval defines the maximum response time advertised in IGMP group-specific queries. Set an appropriate value for the IGMP last member query interval to speed up hosts' responses to IGMP group-specific queries and avoid IGMP report traffic bursts.
Configuration restrictions and guidelines
When you set the IGMP last member query interval, follow these restrictions and guidelines:
· The Layer 2 device does not send an IGMP group-specific query if it receives an IGMP leave message from a port enabled with fast-leave processing.
· You can set the IGMP last member query interval globally for all VLANs and VSIs in IGMP-snooping view, for a VSI in VSI view, or for a VLAN in VLAN view. For a VSI, the VSI-specific configuration takes priority over the global configuration. For a VLAN, the VLAN-specific configuration takes priority over the global configuration.
Setting the IGMP last member query interval globally
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter IGMP-snooping view. |
igmp-snooping |
N/A |
|
3. Set the IGMP last member query interval globally. |
last-member-query-interval interval |
The default setting is 1 second. |
Setting the IGMP last member query interval in a VLAN or VSI
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter VLAN view or VSI view. |
·
Enter VLAN view: ·
Enter VSI view: |
N/A |
|
3. Set the IGMP last member query interval for the VLAN or VSI. |
igmp-snooping last-member-query-interval interval |
The default setting is 1 second. |
Configuring IGMP snooping port features
Before you configure IGMP snooping port features, complete the following tasks:
· Enable IGMP snooping for the VLAN or VSI.
· Determine the aging timer for dynamic router ports.
· Determine the aging timer for dynamic member ports.
· Determine the addresses of the multicast group and multicast source.
Setting aging timers for dynamic ports
When you set aging timers for dynamic ports, follow these restrictions and guidelines:
· If the memberships of multicast groups frequently change, you can set a relatively small value for the aging timer of the dynamic member ports. If the memberships of multicast groups rarely change, you can set a relatively large value.
· If a dynamic router port receives a PIMv2 hello message, the aging timer for the port is specified by the hello message. In this case, the router-aging-time or igmp-snooping router-aging-time command does not take effect on the port.
· IGMP group-specific queries originated by the Layer 2 device trigger the adjustment of aging timers for dynamic member ports. If a dynamic member port receives such a query, its aging timer is set to twice the IGMP last member query interval. For more information about setting the IGMP last member query interval on the Layer 2 device, see "Setting the IGMP last member query interval."
· You can set the timers globally for all VLANs and VSIs in IGMP-snooping view, for a VSI in VSI view, or for a VLAN in VLAN view. For a VLAN, the VLAN-specific configuration takes priority over the global configuration. For a VSI, the VSI-specific configuration takes priority over the global configuration.
Setting the aging timers for dynamic ports globally
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter IGMP-snooping view. |
igmp-snooping |
N/A |
|
3. Set the aging timer for dynamic router ports globally. |
router-aging-time seconds |
The default setting is 260 seconds. |
|
4. Set the global aging timer for dynamic member ports globally. |
host-aging-time seconds |
The default setting is 260 seconds. |
Setting the aging timers for dynamic ports in a VLAN or VSI
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter VLAN view or VSI view. |
·
Enter VLAN view: ·
Enter VSI view: |
N/A |
|
3. Set the aging timer for dynamic router ports in the VLAN or VSI. |
igmp-snooping router-aging-time seconds |
The default setting is 260 seconds. |
|
4. Set the aging timer for dynamic member ports in the VLAN or VSI. |
igmp-snooping host-aging-time seconds |
The default setting is 260 seconds. |
Configuring static ports
You can configure the following types of static ports:
· Static member port—When you configure a port as a static member port for a multicast group, all hosts attached to the port will receive multicast data for the group.
The static member port does not respond to IGMP queries. When you complete or cancel this configuration on a port, the port does not send an unsolicited IGMP report or leave message.
· Static router port—When you configure a port as a static router port for a multicast group, all multicast data for the group received on the port will be forwarded.
To configure a port as a static port:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter Layer 2 Ethernet interface view or Layer 2 aggregate interface view. |
interface interface-type interface-number |
N/A |
|
3. Configure the port as a static port. |
·
Configure the port as a static member port: ·
Configure the port as a static router port: |
By default, a port is not a static member port or a static router port. |
Configuring a port as a simulated member host
When a port is configured as a simulated member host, it is equivalent to an independent host in the following ways:
· It sends an unsolicited IGMP report when you complete the configuration.
· It responds to IGMP general queries with IGMP reports.
· It sends an IGMP leave message when you cancel the configuration.
The version of IGMP running on the simulated member host is the same as the version of IGMP snooping running on the port. The port ages out in the same way as a dynamic member port.
To configure a port as a simulated member host:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter Layer 2 Ethernet interface view or Layer 2 aggregate interface view. |
interface interface-type interface-number |
N/A |
|
3. Configure the port as a simulated member host. |
igmp-snooping host-join group-address [ source-ip source-address ] vlan vlan-id |
By default, the port is not a simulated member host. |
Enabling fast-leave processing
This feature enables the device to immediately remove a port from the forwarding entry for a multicast group when the port receives a leave massage.
Configuration restrictions and guidelines
When you enable fast-leave processing, follow these restrictions and guidelines:
· Do not enable fast-leave processing on a port that has multiple receiver hosts in a VLAN. If fast-leave processing is enabled, the remaining receivers cannot receive multicast data for a group after a receiver leaves that group.
Enabling fast-leave processing globally
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter IGMP-snooping view. |
igmp-snooping |
N/A |
|
3. Enable fast-leave processing globally. |
fast-leave [ vlan vlan-list ] |
By default, fast-leave processing is disabled globally. |
Enabling fast-leave processing on a port
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter Layer 2 Ethernet interface view or Layer 2 aggregate interface view. |
interface interface-type interface-number |
N/A |
|
3. Enable fast-leave processing on the port. |
igmp-snooping fast-leave [ vlan vlan-list ] |
By default, fast-leave processing is disabled on a port. |
Disabling a port from becoming a dynamic router port
A receiver host might send IGMP general queries or PIM hello messages for testing purposes. On the Layer 2 device, the port that receives either of the messages becomes a dynamic router port. Before the aging timer for the port expires, the following problems might occur:
· All multicast data for the VLAN to which the port belongs flows to the port. Then, the port forwards the data to attached receiver hosts. The receiver hosts will receive multicast data that it does not want to receive.
· The port forwards the IGMP general queries or PIM hello messages to its upstream multicast routers. These messages might affect the multicast routing protocol state (such as the IGMP querier or DR election) on the multicast routers. This might further cause network interruption.
To solve these problems, you can disable a port from becoming a dynamic router port. This also improves network security and the control over receiver hosts.
To disable a port from becoming a dynamic router port:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter Layer 2 Ethernet interface view or Layer 2 aggregate interface view. |
interface interface-type interface-number |
N/A |
|
3. Disable the port from becoming a dynamic router port. |
igmp-snooping router-port-deny [ vlan vlan-list ] |
By default, a port is allowed to become a dynamic router port. This configuration does not affect the static router port configuration. |
Enabling inner VLAN ID-based forwarding
Use this feature to enable a port to create and maintain IGMP snooping entries based on the inner VLAN IDs of the received double-tagged IGMP packets.
To enable inner VLAN ID-based forwarding:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter Layer 2 Ethernet interface view or Layer 2 aggregate interface view. |
interface interface-type interface-number |
N/A |
|
3. Enable inner VLAN ID-based forwarding. |
igmp-snooping cvid-forward |
By default, inner VLAN ID-based forwarding is disabled on a port. The port performs outer VLAN ID-based forwarding. |
Configuring the IGMP snooping querier
This section describes how to configure an IGMP snooping querier.
Configuration prerequisites
Before you configure the IGMP snooping querier, complete the following tasks:
· Enable IGMP snooping for the VLAN or VSI.
· Determine the IGMP general query interval.
· Determine the maximum response time for IGMP general queries.
Enabling the IGMP snooping querier
Configuration restrictions and guidelines
When you enable the IGMP snooping querier, follow these restrictions and guidelines:
· Do not enable the IGMP snooping querier on a multicast network that runs IGMP. An IGMP snooping querier does not take part in IGMP querier elections. However, it might affect IGMP querier elections if it sends IGMP general queries with a low source IP address.
· On a VXLAN network, the IGMP snooping querier in a VSI does not include VLAN tags in IGMP general queries. As a best practice, do not enable the IGMP snooping querier in a VSI if the VSI uses the Ethernet access mode. For more information about the Ethernet access mode, see VXLAN Configuration Guide.
Configuration procedure
To enable the IGMP snooping querier for a VLAN or VSI:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter VLAN view or VSI view. |
·
Enter VLAN view: ·
Enter VSI view: |
N/A |
|
3. Enable the IGMP snooping querier. |
igmp-snooping querier |
By default, the IGMP snooping querier is disabled. |
Configuring parameters for IGMP general queries and responses
|
|
CAUTION: To avoid mistakenly deleting multicast group members, make sure the IGMP general query interval is greater than the maximum response time for IGMP general queries. |
You can modify the IGMP general query interval for a VLAN or VSI based on the actual condition of the network.
A receiver host starts a report delay timer for each multicast group that it has joined when it receives an IGMP general query. This timer is set to a random value in the range of 0 to the maximum response time advertised in the query. When the timer value decreases to 0, the host sends an IGMP report to the corresponding multicast group.
Set an appropriate value for the maximum response time for IGMP general queries to speed up hosts' responses to IGMP general queries and avoid IGMP report traffic bursts.
You can set the maximum response time for IGMP general queries globally for all VLANs and VSIs in IGMP-snooping view, for a VSI in VSI view, or for a VLAN in VLAN view. For a VSI, the VSI-specific configuration takes priority over the global configuration. For a VLAN, the VLAN-specific configuration takes priority over the global configuration.
Configuring parameters for IGMP general queries and responses globally
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter IGMP-snooping view. |
igmp-snooping |
N/A |
|
3. Set the maximum response time for IGMP general queries. |
max-response-time seconds |
The default setting is 10 seconds. |
Configuring parameters for IGMP general queries and responses in a VLAN or VSI
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter VLAN view or VSI view. |
·
Enter VLAN view: ·
Enter VSI view: |
N/A |
|
3. Set the IGMP general query interval in the VLAN or VSI. |
igmp-snooping query-interval interval |
The default setting is 125 seconds. |
|
4. Set the maximum response time for IGMP general queries in the VLAN or VSI. |
igmp-snooping max-response-time seconds |
The default setting is 10 seconds. |
Enabling IGMP snooping proxying
Before you enable IGMP snooping proxying for a VLAN, enable IGMP snooping for the VLAN.
To enable IGMP snooping proxying:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter VLAN view. |
vlan vlan-id |
N/A |
|
3. Enable IGMP snooping proxying for the VLAN. |
igmp-snooping proxy enable |
By default, IGMP snooping proxying is disabled for a VLAN. |
Configuring parameters for IGMP messages
This section describes how to configure parameters for IGMP messages.
Configuration prerequisites
Before you configure parameters for IGMP messages, complete the following tasks:
· Enable IGMP snooping for the VLAN or VSI.
· Determine the source IP address of IGMP general queries.
· Determine the source IP address of IGMP group-specific queries.
· Determine the source IP address of IGMP reports.
· Determine the source IP address of IGMP leave messages.
· Determine the 802.1p priority of IGMP messages.
Configuring source IP addresses for IGMP messages
The IGMP snooping querier might send IGMP general queries with the source IP address 0.0.0.0. The port that receives such queries will not be maintained as a dynamic router port. This might prevent the associated dynamic IGMP snooping forwarding entry from being correctly created at the data link layer and eventually cause multicast traffic forwarding failures.
To avoid this problem, you can configure a non-all-zero IP address as the source IP address of the IGMP queries on the IGMP snooping querier. This configuration might affect the IGMP querier election within the subnet.
You can also change the source IP address of IGMP reports or leave messages sent by a simulated member host or an IGMP snooping proxy.
Configuring the source IP address for IGMP messages in a VLAN
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter VLAN view. |
vlan vlan-id |
N/A |
|
3. Configure the source IP address for IGMP general queries. |
igmp-snooping general-query source-ip ip-address |
By default, the source IP address of IGMP general queries is the IP address of the current VLAN interface. If the current VLAN interface does not have an IP address, the source IP address is 0.0.0.0. |
|
4. Configure the source IP address for IGMP group-specific queries. |
igmp-snooping special-query source-ip ip-address |
By default, the source IP address of IGMP group-specific queries is one of the following: · The source address of IGMP group-specific queries if the IGMP snooping querier of the VLAN has received IGMP general queries. · The IP address of the current VLAN interface if the IGMP snooping querier does not receive an IGMP general query. · 0.0.0.0 if the IGMP snooping querier does not receive an IGMP general query and the current VLAN interface does not have an IP address. |
|
5. Configure the source IP address for IGMP reports. |
igmp-snooping report source-ip ip-address |
By default, the source IP address of IGMP reports is the IP address of the current VLAN interface. If the current VLAN interface does not have an IP address, the source IP address is 0.0.0.0. |
|
6. Configure the source IP address for IGMP leave messages. |
igmp-snooping leave source-ip ip-address |
By default, the source IP address of IGMP leave messages is the IP address of the current VLAN interface. If the current VLAN interface does not have an IP address, the source IP address is 0.0.0.0. |
Configuring the source IP address for IGMP messages in a VSI
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter VSI view. |
vsi vsi-name |
N/A |
|
3. Configure the source IP address for IGMP general queries. |
igmp-snooping general-query source-ip ip-address |
By default, the source IP address of IGMP general queries is the IP address of the gateway interface for a VSI. If the gateway interface does not have an IP address, the source IP address is 0.0.0.0. |
|
4. Configure the source IP address for IGMP group-specific queries. |
igmp-snooping special-query source-ip ip-address |
By default, the source IP address of IGMP group-specific queries is one of the following: · The source IP address of IGMP general queries if the IGMP snooping querier of a VSI has received IGMP general queries. · The IP address of the gateway interface for the VSI if the IGMP snooping querier does not receive an IGMP general query. · 0.0.0.0 if the gateway interface of the VSI does not have an IP address. |
|
5. Configure the source IP address for IGMP reports. |
igmp-snooping report source-ip ip-address |
By default, the source IP address of IGMP reports is the IP address of the gateway interface for a VSI. If the gateway interface does not have an IP address, the source IP address is 0.0.0.0. |
|
6. Configure the source IP address for IGMP leave messages. |
igmp-snooping leave source-ip ip-address |
By default, the source IP address of IGMP leave messages is the IP address of the gateway interface for a VSI. If the gateway interface does not have an IP address, the source IP address is 0.0.0.0. |
Setting the 802.1p priority for IGMP messages
When congestion occurs on outgoing ports of the Layer 2 device, it forwards IGMP messages in their 802.1p priority order, from highest to lowest. You can assign a higher 802.1p priority to IGMP messages that are created or forwarded by the device.
You can set the 802.1p priority globally for all VLANs and VSIs in IGMP-snooping view or for a VLAN in VLAN view. For a VLAN, the VLAN-specific configuration takes priority over the global configuration.
Setting the 802.1p priority for IGMP messages globally
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter IGMP-snooping view. |
igmp-snooping |
N/A |
|
3. Set the 802.1p priority for IGMP messages. |
dot1p-priority priority |
By default, the 802.1p priority for IGMP packets is not configured. For IGMP packets created by the device, the 802.1p priority is 0. For IGMP packets to be forwarded, the device does not change the 802.1p priority. |
Setting the 802.1p priority for IGMP messages in a VLAN
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter VLAN view. |
vlan vlan-id |
N/A |
|
3. Set the 802.1p priority for IGMP messages in the VLAN. |
igmp-snooping dot1p-priority priority |
By default, the 802.1p priority for IGMP packets is not configured. For IGMP packets created by the device, the 802.1p priority is 0. For IGMP packets to be forwarded, the device does not change the 802.1p priority. |
Configuring IGMP snooping policies
Before you configure IGMP snooping policies, complete the following tasks:
· Enable IGMP snooping for the VLAN or VSI.
· Determine the ACL used by the multicast group policy.
· Determine the maximum number of multicast groups that a port can join.
Configuring a multicast group policy
This feature enables the device to filter IGMP reports by using an ACL that specifies the multicast groups and the optional sources. It is used to control the multicast groups that hosts can join.
Configuration restrictions and guidelines
When you configure a multicast group policy, follow these restrictions and guidelines:
· This configuration takes effect only on the multicast groups that ports join dynamically.
· You can configure a multicast group policy globally for all ports in IGMP-snooping view or for a port in interface view. For a port, the port-specific configuration takes priority over the global configuration.
Configuring a multicast group policy globally
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter IGMP-snooping view. |
igmp-snooping |
N/A |
|
3. Configure a multicast group policy globally. |
group-policy ipv4-acl-number [ vlan vlan-list ] |
By default, no multicast group policies exist, and hosts can join any multicast groups. |
Configuring a multicast group policy on a port
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter Layer 2 Ethernet interface view or Layer 2 aggregate interface view. |
interface interface-type interface-number |
N/A |
|
3. Configure a multicast group policy on the port. |
igmp-snooping group-policy ipv4-acl-number [ vlan vlan-list ] |
By default, no multicast group policies exist on a port, and hosts attached to the port can join any multicast groups. |
Enabling multicast source port filtering
This feature enables the device to discard all multicast data packets and to accept multicast protocol packets. You can enable this feature on ports that connect only to multicast receivers.
You can enable this feature for the specified ports in IGMP-snooping view or for a port in interface view. For a port, the configuration in interface view has the same priority as the configuration in IGMP-snooping view, and the most recent configuration takes effect.
Enabling multicast source port filtering in IGMP-snooping view
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter IGMP-snooping view. |
igmp-snooping |
N/A |
|
3. Enable multicast source port filtering. |
source-deny port interface-list |
By default, multicast source port filtering is disabled. |
Enabling multicast source port filtering in interface view
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter Layer 2 Ethernet interface view. |
interface interface-type interface-number |
N/A |
|
3. Enable multicast source port filtering. |
igmp-snooping source-deny |
By default, multicast source port filtering is disabled. |
Enabling dropping unknown multicast data
Unknown multicast data refers to multicast data for which no forwarding entries exist in the IGMP snooping forwarding table. This feature enables the device only to forward unknown multicast data to the router port. If the device does not have a router port, unknown multicast data will be dropped.
If you do not enable this feature, the unknown multicast data is flooded in the VLAN to which the data belongs.
To enable dropping unknown multicast data in a VLAN or VSI:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter VLAN view or VSI view. |
·
Enter VLAN view: ·
Enter VSI view: |
N/A |
|
3. Enable dropping unknown multicast data for the VLAN or VSI. |
igmp-snooping drop-unknown |
By default, dropping unknown multicast data is disabled, and unknown multicast data is flooded. |
Enabling IGMP report suppression
This feature enables the device to forward only the first IGMP report for a multicast group to its directly connected Layer 3 device. Other reports for the same group in the same query interval are discarded. Use this feature to reduce multicast traffic.
To enable IGMP report suppression:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter IGMP-snooping view. |
igmp-snooping |
N/A |
|
3. Enable IGMP report suppression. |
report-aggregation |
By default, IGMP report suppression is enabled. |
Setting the maximum number of multicast groups on a port
You can set the maximum number of multicast groups on a port to regulate the port traffic.
Configuration restrictions and guidelines
When you set the maximum number of multicast groups on a port, follow these restrictions and guidelines:
· This configuration takes effect only on the multicast groups that a port joins dynamically.
· If the number of multicast groups on a port exceeds the limit, the system removes all the forwarding entries related to that port. The receiver hosts attached to that port can join multicast groups again before the number of multicast groups on the port reaches the limit.
Configuration procedure
To set the maximum number of multicast groups on a port:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter Layer 2 Ethernet interface view or Layer 2 aggregate interface view. |
interface interface-type interface-number |
N/A |
|
3. Set the maximum number of multicast groups on a port. |
igmp-snooping group-limit limit [ vlan vlan-list ] |
By default, no limit is placed on the maximum number of multicast groups on a port. |
Enabling multicast group replacement
This feature enables the device to replace an existing group with a newly joined group when the number of groups exceeds the upper limit. This feature is typically used in the channel switching application. Without this feature, the device discards IGMP reports for new groups, and the user cannot change to the new channel.
Configuration restrictions and guidelines
When you enable multicast group replacement, follow these restrictions and guidelines:
· This configuration takes effect only on the multicast groups that a port joins dynamically.
· You can enable this feature globally for all ports in IGMP-snooping view or for a port in interface view. For a port, the port-specific configuration takes priority over the global configuration.
Enabling multicast group replacement globally
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter IGMP-snooping view. |
igmp-snooping |
N/A |
|
3. Enable multicast group replacement globally. |
overflow-replace [ vlan vlan-list ] |
By default, multicast group replacement is disabled globally. |
Enabling multicast group replacement on a port
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter Layer 2 Ethernet interface view or Layer 2 aggregate interface view. |
interface interface-type interface-number |
N/A |
|
3. Enable multicast group replacement on a port. |
igmp-snooping overflow-replace [ vlan vlan-list ] |
By default, multicast group replacement is disabled on a port. |
Enabling host tracking
This feature enables the device to record information about member hosts that are receiving multicast data. The information includes IP addresses of the hosts, length of time elapsed since the hosts joined multicast groups, and remaining timeout time for the hosts. This feature facilitates monitoring and managing member hosts.
Enabling host tracking globally
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter IGMP-snooping view. |
igmp-snooping |
N/A |
|
3. Enable host tracking globally. |
host-tracking |
By default, host tracking is disabled. |
Enabling host tracking in a VLAN
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter VLAN view. |
vlan vlan-id |
N/A |
|
3. Enable host tracking for the VLAN. |
igmp-snooping host-tracking |
By default, host tracking is disabled for a VLAN. |
Displaying and maintaining IGMP snooping
Execute display commands in any view and reset commands in user view.
|
Command |
|
|
Display IGMP snooping status. |
display igmp-snooping [ global | vlan vlan-id | vsi vsi-name ] |
|
(In standalone mode.) Display dynamic IGMP snooping group entries. |
display igmp-snooping group [ group-address | source-address ] * [ vlan vlan-id | vsi vsi-name ] [ verbose ] [ slot slot-number ] |
|
(In IRF mode.) Display dynamic IGMP snooping group entries. |
display igmp-snooping group [ group-address | source-address ] * [ vlan vlan-id | vsi vsi-name ] [ verbose ] [ chassis chassis-number slot slot-number ] |
|
(In standalone mode.) Display host tracking information. |
display igmp-snooping host-tracking vlan vlan-id group group-address [ source source-address ] [ slot slot-number ] |
|
(In IRF mode.) Display host tracking information. |
display igmp-snooping host-tracking vlan vlan-id group group-address [ source source-address ] [ chassis chassis-number slot slot-number ] |
|
(In standalone mode.) Display dynamic router port information. |
display igmp-snooping router-port [ vlan vlan-id | vsi vsi-name ] [ verbose ] [ slot slot-number ] |
|
(In IRF mode.) Display dynamic router port information. |
display igmp-snooping router-port [ vlan vlan-id | vsi vsi-name ] [ verbose ] [ chassis chassis-number slot slot-number ] |
|
(In standalone mode.) Display static IGMP snooping group entries. |
display igmp-snooping static-group [ group-address | source-address ] * [ vlan vlan-id ] [ verbose ] [ slot slot-number ] |
|
(In IRF mode.) Display static IGMP snooping group entries. |
display igmp-snooping static-group [ group-address | source-address ] * [ vlan vlan-id ] [ verbose ] [ chassis chassis-number slot slot-number ] |
|
(In standalone mode.) Display static router port information. |
display igmp-snooping static-router-port [ vlan vlan-id ] [ verbose ] [ slot slot-number ] |
|
(In IRF mode.) Display static router port information. |
display igmp-snooping static-router-port [ vlan vlan-id ] [ verbose ] [ chassis chassis-number slot slot-number ] |
|
Display statistics for the IGMP messages and PIMv2 hello messages learned by IGMP snooping. |
display igmp-snooping statistics |
|
(In standalone mode.) Display Layer 2 multicast fast forwarding entries. |
display l2-multicast fast-forwarding cache [ vlan vlan-id ] [ source-address | group-address ] * [ slot slot-number ] |
|
(In IRF mode.) Display Layer 2 multicast fast forwarding entries. |
display l2-multicast fast-forwarding cache [ vlan vlan-id ] [ source-address | group-address ] * [ chassis chassis-number slot slot-number ] |
|
(In standalone mode.) Display information about Layer 2 IP multicast groups. |
display l2-multicast ip [ group group-address | source source-address ] * [ vlan vlan-id | vsi vsi-name ] [ slot slot-number ] |
|
(In IRF mode.) Display information about Layer 2 IP multicast groups. |
display l2-multicast ip [ group group-address | source source-address ] * [ vlan vlan-id | vsi vsi-name ] [ chassis chassis-number slot slot-number ] |
|
(In standalone mode.) Display Layer 2 IP multicast group entries. |
display l2-multicast ip forwarding [ group group-address | source source-address ] * [ vlan vlan-id | vsi vsi-name ] [ slot slot-number ] |
|
(In IRF mode.) Display Layer 2 IP multicast group entries. |
display l2-multicast ip forwarding [ group group-address | source source-address ] * [ vlan vlan-id | vsi vsi-name ] [ chassis chassis-number slot slot-number ] |
|
(In standalone mode.) Display information about Layer 2 MAC multicast groups. |
display l2-multicast mac [ mac-address ] [ vlan vlan-id | vsi vsi-name ] [ slot slot-number ] |
|
(In IRF mode.) Display information about Layer 2 MAC multicast groups. |
display l2-multicast mac [ mac-address ] [ vlan vlan-id | vsi vsi-name ] [ chassis chassis-number slot slot-number ] |
|
(In standalone mode.) Display Layer 2 MAC multicast group entries. |
display l2-multicast mac forwarding [ mac-address ] [ vlan vlan-id | vsi vsi-name ] [ slot slot-number ] |
|
(In IRF mode.) Display Layer 2 MAC multicast group entries. |
display l2-multicast mac forwarding [ mac-address ] [ vlan vlan-id | vsi vsi-name ] [ chassis chassis-number slot slot-number ] |
|
Display static multicast MAC address entries. |
display mac-address [ mac-address [ vlan vlan-id ] | [ multicast ] [ vlan vlan-id ] [ count ] ] |
|
Clear dynamic IGMP snooping group entries. |
reset igmp-snooping group { group-address [ source-address ] | all } [ vlan vlan-id | vsi vsi-name ] |
|
(In standalone mode.) Clear Layer 2 multicast fast forwarding entries. |
reset l2-multicast fast-forwarding cache [ vlan vlan-id ] { { source-address | group-address } * | all } [ slot slot-number ] |
|
(In IRF mode.) Clear Layer 2 multicast fast forwarding entries. |
reset l2-multicast fast-forwarding cache [ vlan vlan-id ] { { source-address | group-address } * | all } [ chassis chassis-number slot slot-number ] |
|
Clear dynamic router port information. |
reset igmp-snooping router-port { all | vlan vlan-id | vsi vsi-name } |
|
Clear statistics for IGMP messages and PIMv2 hello messages learned through IGMP snooping. |
reset igmp-snooping statistics |
IGMP snooping configuration examples
Group policy and simulated joining configuration example(for VLANs)
Network requirements
As shown in Figure 13, Router A runs IGMPv2 and acts as the IGMP querier. Switch A runs IGMPv2 snooping.
Configure a multicast group policy and simulated joining to meet the following requirements:
· Host A and Host B receive only the multicast data addressed to multicast group 224.1.1.1. Multicast data can be forwarded through HundredGigE 1/0/3 and HundredGigE 1/0/4 of Switch A uninterruptedly, even though Host A and Host B fail to receive the multicast data.
· Switch A will drop unknown multicast data instead of flooding it in VLAN 100.
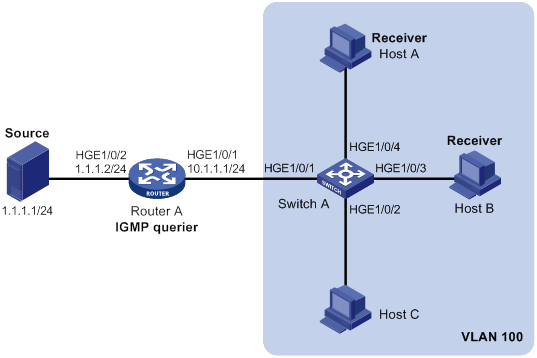
Configuration procedure
1. Assign an IP address and subnet mask to each interface, as shown in Figure 13. (Details not shown.)
2. Configure Router A:
# Enable IP multicast routing.
<RouterA> system-view
[RouterA] multicast routing
[RouterA-mrib] quit
# Enable IGMP on HundredGigE 1/0/1.
[RouterA] interface hundredgige 1/0/1
[RouterA-HundredGigE1/0/1] igmp enable
[RouterA-HundredGigE1/0/1] quit
# Enable PIM-DM on HundredGigE 1/0/2.
[RouterA] interface hundredgige 1/0/2
[RouterA-HundredGigE1/0/2] pim dm
[RouterA-HundredGigE1/0/2] quit
3. Configure Switch A:
# Enable IGMP snooping globally.
<SwitchA> system-view
[SwitchA] igmp-snooping
[SwitchA-igmp-snooping] quit
# Create VLAN 100, and assign HundredGigE 1/0/1 through HundredGigE 1/0/4 to the VLAN.
[SwitchA] vlan 100
[SwitchA-vlan100] port hundredgige 1/0/1 to hundredgige 1/0/4
# Enable IGMP snooping, and enable dropping unknown multicast data for VLAN 100.
[SwitchA-vlan100] igmp-snooping enable
[SwitchA-vlan100] igmp-snooping drop-unknown
[SwitchA-vlan100] quit
# Configure a multicast group policy so that hosts in VLAN 100 can join only multicast group 224.1.1.1.
[SwitchA] acl basic 2001
[SwitchA-acl-ipv4-basic-2001] rule permit source 224.1.1.1 0
[SwitchA-acl-ipv4-basic-2001] quit
[SwitchA] igmp-snooping
[SwitchA-igmp-snooping] group-policy 2001 vlan 100
[SwitchA-igmp-snooping] quit
# Configure HundredGigE 1/0/3 and HundredGigE 1/0/4 as simulated member hosts of multicast group 224.1.1.1.
[SwitchA] interface hundredgige 1/0/3
[SwitchA-HundredGigE1/0/3] igmp-snooping host-join 224.1.1.1 vlan 100
[SwitchA-HundredGigE1/0/3] quit
[SwitchA] interface hundredgige 1/0/4
[SwitchA-HundredGigE1/0/4] igmp-snooping host-join 224.1.1.1 vlan 100
[SwitchA-HundredGigE1/0/4] quit
Verifying the configuration
# Send IGMP reports from Host A and Host B to join multicast groups 224.1.1.1 and 224.2.2.2. (Details not shown.)
# Display brief information about dynamic IGMP snooping group entries for VLAN 100 on Switch A.
[SwitchA] display igmp-snooping group vlan 100
Total 1 entries.
VLAN 100: Total 1 entries.
(0.0.0.0, 224.1.1.1)
Host ports (2 in total):
HGE1/0/3 (00:03:23)
HGE1/0/4 (00:04:10)
The output shows the following information:
· Host A and Host B have joined multicast group 224.1.1.1 through the member ports HundredGigE 1/0/4 and HundredGigE 1/0/3 on Switch A, respectively.
· Host A and Host B have failed to join multicast group 224.2.2.2.
Static port configuration example (for VLANs)
Network requirements
As shown in Figure 14:
· Router A runs IGMPv2 and acts as the IGMP querier. Switch A, Switch B, and Switch C run IGMPv2 snooping.
· Host A and host C are permanent receivers of multicast group 224.1.1.1.
Configure static ports to meet the following requirements:
· To enhance the reliability of multicast traffic transmission, configure HundredGigE 1/0/3 and HundredGigE 1/0/5 on Switch C as static member ports for multicast group 224.1.1.1.
· Suppose the STP runs on the network. To avoid data loops, the forwarding path from Switch A to Switch C is blocked. Multicast data flows to the receivers attached to Switch C only along the path of Switch A—Switch B—Switch C. When this path is blocked, a minimum of one IGMP query-response cycle must be completed before multicast data flows to the receivers along the path of Switch A—Switch C. In this case, the multicast delivery is interrupted during the process. For more information about the STP, see Layer 2—LAN Switching Configuration Guide.
Configure HundredGigE 1/0/3 on Switch A as a static router port. Then, multicast data can flow to the receivers nearly uninterruptedly along the path of Switch A—Switch C when the path of Switch A—Switch B—Switch C is blocked.
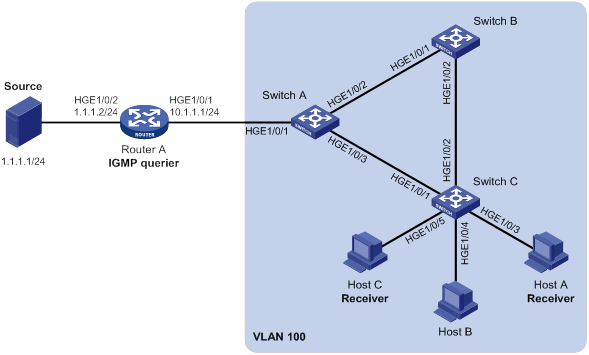
Configuration procedure
1. Assign an IP address and subnet mask to each interface, as shown in Figure 14. (Details not shown.)
2. Configure Router A:
# Enable IP multicast routing.
<RouterA> system-view
[RouterA] multicast routing
[RouterA-mrib] quit
# Enable IGMP on HundredGigE 1/0/1.
[RouterA] interface hundredgige 1/0/1
[RouterA-HundredGigE1/0/1] igmp enable
[RouterA-HundredGigE1/0/1] quit
# Enable PIM-DM on HundredGigE 1/0/2.
[RouterA] interface hundredgige 1/0/2
[RouterA-HundredGigE1/0/2] pim dm
[RouterA-HundredGigE1/0/2] quit
3. Configure Switch A:
# Enable IGMP snooping globally.
<SwitchA> system-view
[SwitchA] igmp-snooping
[SwitchA-igmp-snooping] quit
# Create VLAN 100, and assign HundredGigE 1/0/1 through HundredGigE 1/0/3 to the VLAN.
[SwitchA] vlan 100
[SwitchA-vlan100] port hundredgige 1/0/1 to hundredgige 1/0/3
# Enable IGMP snooping for VLAN 100.
[SwitchA-vlan100] igmp-snooping enable
[SwitchA-vlan100] quit
# Configure HundredGigE 1/0/3 as a static router port.
[SwitchA] interface hundredgige 1/0/3
[SwitchA-HundredGigE1/0/3] igmp-snooping static-router-port vlan 100
[SwitchA-HundredGigE1/0/3] quit
4. Configure Switch B:
# Enable IGMP snooping globally.
<SwitchB> system-view
[SwitchB] igmp-snooping
[SwitchB-igmp-snooping] quit
# Create VLAN 100, and assign HundredGigE 1/0/1 and HundredGigE 1/0/2 to the VLAN.
[SwitchB] vlan 100
[SwitchB-vlan100] port hundredgige 1/0/1 hundredgige 1/0/2
# Enable IGMP snooping for VLAN 100.
[SwitchB-vlan100] igmp-snooping enable
[SwitchB-vlan100] quit
5. Configure Switch C:
# Enable IGMP snooping globally.
<SwitchC> system-view
[SwitchC] igmp-snooping
[SwitchC-igmp-snooping] quit
# Create VLAN 100, and assign HundredGigE 1/0/1 through HundredGigE 1/0/5 to the VLAN.
[SwitchC] vlan 100
[SwitchC-vlan100] port hundredgige 1/0/1 to hundredgige 1/0/5
# Enable IGMP snooping for VLAN 100.
[SwitchC-vlan100] igmp-snooping enable
[SwitchC-vlan100] quit
# Configure HundredGigE 1/0/3 and HundredGigE 1/0/5 as static member ports for multicast group 224.1.1.1.
[SwitchC] interface hundredgige 1/0/3
[SwitchC-HundredGigE1/0/3] igmp-snooping static-group 224.1.1.1 vlan 100
[SwitchC-HundredGigE1/0/3] quit
[SwitchC] interface hundredgige 1/0/5
[SwitchC-HundredGigE1/0/5] igmp-snooping static-group 224.1.1.1 vlan 100
[SwitchC-HundredGigE1/0/5] quit
Verifying the configuration
# Display brief information about static router ports for VLAN 100 on Switch A.
[SwitchA] display igmp-snooping static-router-port vlan 100
VLAN 100:
Router ports (1 in total):
HGE1/0/3
The output shows that HundredGigE 1/0/3 on Switch A has become a static router port.
# Display brief information about static IGMP snooping group entries for VLAN 100 on Switch C.
[SwitchC] display igmp-snooping static-group vlan 100
Total 1 entries.
VLAN 100: Total 1 entries.
(0.0.0.0, 224.1.1.1)
Host ports (2 in total):
HGE1/0/3
HGE1/0/5
The output shows that HundredGigE 1/0/3 and HundredGigE 1/0/5 on Switch C have become static member ports of multicast group 224.1.1.1.
IGMP snooping querier configuration example (for VLANs)
Network requirements
As shown in Figure 15:
· The network is a Layer 2-only network.
· Source 1 and Source 2 send multicast data to multicast groups 224.1.1.1 and 225.1.1.1, respectively.
· Host A and Host C are receivers of multicast group 224.1.1.1, and Host B and Host D are receivers of multicast group 225.1.1.1.
· All host receivers run IGMPv2, and all switches run IGMPv2 snooping. Switch A (which is close to the multicast sources) acts as the IGMP snooping querier.
Configure the switches to meet the following requirements:
· To prevent the switches from flooding unknown data in the VLAN, enable all the switches to drop unknown multicast data.
· A switch does not mark a port that receives an IGMP query with source IP address 0.0.0.0 as a dynamic router port. This adversely affects the establishment of Layer 2 forwarding entries and multicast traffic forwarding. To avoid this, configure the source IP address of IGMP queries as a non-zero IP address.
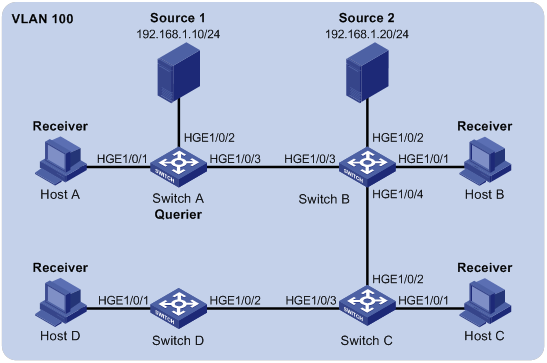
Configuration procedure
1. Configure Switch A:
# Enable IGMP snooping globally.
<SwitchA> system-view
[SwitchA] igmp-snooping
[SwitchA-igmp-snooping] quit
# Create VLAN 100, and assign HundredGigE 1/0/1 through HundredGigE 1/0/3 to the VLAN.
[SwitchA] vlan 100
[SwitchA-vlan100] port hundredgige 1/0/1 to hundredgige 1/0/3
# Enable IGMP snooping, and enable dropping unknown multicast data for VLAN 100.
[SwitchA-vlan100] igmp-snooping enable
[SwitchA-vlan100] igmp-snooping drop-unknown
# Configure Switch A as the IGMP snooping querier.
[SwitchA-vlan100] igmp-snooping querier
[SwitchA-vlan100] quit
# In VLAN 100, specify 192.168.1.1 as the source IP address of IGMP general queries.
[SwitchA-vlan100] igmp-snooping general-query source-ip 192.168.1.1
# In VLAN 100, specify 192.168.1.1 as the source IP address of IGMP group-specific queries.
[SwitchA-vlan100] igmp-snooping special-query source-ip 192.168.1.1
[SwitchA-vlan100] quit
2. Configure Switch B:
# Enable IGMP snooping globally.
<SwitchB> system-view
[SwitchB] igmp-snooping
[SwitchB-igmp-snooping] quit
# Create VLAN 100, and assign HundredGigE 1/0/1 through HundredGigE 1/0/4 to the VLAN.
[SwitchB] vlan 100
[SwitchB-vlan100] port hundredgige 1/0/1 to hundredgige 1/0/4
# Enable IGMP snooping, and enable dropping unknown multicast data for VLAN 100.
[SwitchB-vlan100] igmp-snooping enable
[SwitchB-vlan100] igmp-snooping drop-unknown
[SwitchB-vlan100] quit
3. Configure Switch C:
# Enable IGMP snooping globally.
<SwitchC> system-view
[SwitchC] igmp-snooping
[SwitchC-igmp-snooping] quit
# Create VLAN 100, and assign HundredGigE 1/0/1 through HundredGigE 1/0/3 to the VLAN.
[SwitchC] vlan 100
[SwitchC-vlan100] port hundredgige 1/0/1 to hundredgige 1/0/3
# Enable IGMP snooping, and enable dropping unknown multicast data for VLAN 100.
[SwitchC-vlan100] igmp-snooping enable
[SwitchC-vlan100] igmp-snooping drop-unknown
[SwitchC-vlan100] quit
4. Configure Switch D:
# Enable IGMP snooping globally.
<SwitchD> system-view
[SwitchD] igmp-snooping
[SwitchD-igmp-snooping] quit
# Create VLAN 100, and assign HundredGigE 1/0/1 and HundredGigE 1/0/2 to the VLAN.
[SwitchD] vlan 100
[SwitchD-vlan100] port hundredgige 1/0/1 to hundredgige 1/0/2
# Enable IGMP snooping, and enable dropping unknown multicast data for VLAN 100.
[SwitchD-vlan100] igmp-snooping enable
[SwitchD-vlan100] igmp-snooping drop-unknown
[SwitchD-vlan100] quit
Verifying the configuration
# Display statistics for IGMP messages and PIMv2 hello messages learned through IGMP snooping on Switch B.
[SwitchB] display igmp-snooping statistics
Received IGMP general queries: 3
Received IGMPv1 reports: 0
Received IGMPv2 reports: 12
Received IGMP leaves: 0
Received IGMPv2 specific queries: 0
Sent IGMPv2 specific queries: 0
Received IGMPv3 reports: 0
Received IGMPv3 reports with right and wrong records: 0
Received IGMPv3 specific queries: 0
Received IGMPv3 specific sg queries: 0
Sent IGMPv3 specific queries: 0
Sent IGMPv3 specific sg queries: 0
Received PIMv2 hello: 0
Received error IGMP messages: 0
The output shows that all switches except Switch A can receive the IGMP general queries after Switch A acts as the IGMP snooping querier.
IGMP snooping proxying configuration example (for VLANs)
Network requirements
As shown in Figure 16, Router A runs IGMPv2 and acts as the IGMP querier. Switch A runs IGMPv2 snooping. Configure IGMP snooping proxying so that Switch A can perform the following actions:
· Forward IGMP report and leave messages to Router A.
· Respond to IGMP queries sent by Router A and forward the queries to downstream hosts.
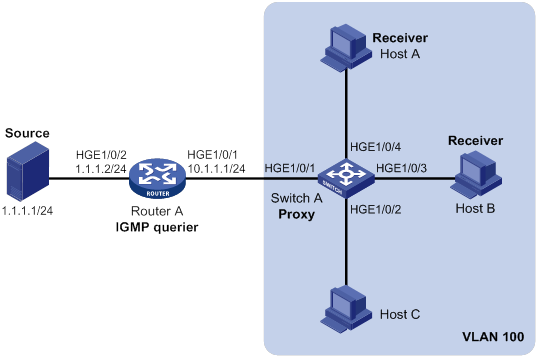
Configuration procedure
1. Assign an IP address and subnet mask to each interface, as shown in Figure 16. (Details not shown.)
2. Configure Router A:
# Enable IP multicast routing.
<RouterA> system-view
[RouterA] multicast routing
[RouterA-mrib] quit
# Enable IGMP and PIM-DM on HundredGigE 1/0/1.
[RouterA] interface hundredgige 1/0/1
[RouterA-HundredGigE1/0/1] igmp enable
[RouterA-HundredGigE1/0/1] pim dm
[RouterA-HundredGigE1/0/1] quit
# Enable PIM-DM on HundredGigE 1/0/2.
[RouterA] interface hundredgige 1/0/2
[RouterA-HundredGigE1/0/2] pim dm
[RouterA-HundredGigE1/0/2] quit
3. Configure Switch A:
# Enable IGMP snooping globally.
<SwitchA> system-view
[SwitchA] igmp-snooping
[SwitchA-igmp-snooping] quit
# Create VLAN 100, and assign HundredGigE 1/0/1 through HundredGigE 1/0/4 to the VLAN.
[SwitchA] vlan 100
[SwitchA-vlan100] port hundredgige 1/0/1 to hundredgige 1/0/4
# Enable IGMP snooping and IGMP snooping proxying for the VLAN.
[SwitchA-vlan100] igmp-snooping enable
[SwitchA-vlan100] igmp-snooping proxy enable
[SwitchA-vlan100] quit
Verifying the configuration
# Send IGMP reports from Host A and Host B to multicast group 224.1.1.1. (Details not shown.)
# Display brief information about IGMP snooping group entries on Switch A.
[SwitchA] display igmp-snooping group
Total 1 entries.
VLAN 100: Total 1 entries.
(0.0.0.0, 224.1.1.1)
Host ports (2 in total):
HGE1/0/3 (00:04:00)
HGE1/0/4 (00:04:04)
The output shows that HundredGigE1/0/3 and HundredGigE1/0/4 have become member ports of multicast group 224.1.1.1.
# Display IGMP group membership information on Router A.
[RouterA] display igmp group
IGMP groups in total: 1
HundredGigE1/0/1(10.1.1.1):
IGMP groups reported in total: 1
Group address Last reporter Uptime Expires
224.1.1.1 0.0.0.0 00:00:31 00:02:03
The output shows that HundredGigE1/0/1 has become the router port of multicast group 224.1.1.1.
# Display IGMP snooping group entries on Switch A.
[SwitchA] display igmp-snooping group
Total 1 entries.
VLAN 100: Total 1 entries.
(0.0.0.0, 224.1.1.1)
Host ports (1 in total):
HGE1/0/3 ( 00:01:23 )
The output shows that HundredGigE1/0/3 is the only member port of multicast group 224.1.1.1.
Troubleshooting IGMP snooping
Layer 2 multicast forwarding cannot function
Symptom
Layer 2 multicast forwarding cannot function on the Layer 2 device.
Solution
To resolve the problem:
1. Use the display igmp-snooping command to display IGMP snooping status.
2. If IGMP snooping is not enabled, use the igmp-snooping command in system view to enable IGMP snooping globally. Then, use the igmp-snooping enable command in VLAN view or VSI view to enable IGMP snooping for the VLAN or VSI.
3. If IGMP snooping is enabled globally but not enabled for the VLAN or VSI, use the igmp-snooping enable command in VLAN view or VSI view to enable IGMP snooping for the VLAN or VSI.
4. If the problem persists, contact H3C Support.
Multicast group policy does not work
Symptom
Hosts can receive multicast data for multicast groups that are not permitted by the multicast group policy.
Solution
To resolve the problem:
1. Use the display acl command to verify that the configured ACL meets the multicast group policy requirements.
2. Use the display this command in IGMP-snooping view or in a corresponding interface view to verify that the correct multicast group policy has been applied. If the applied policy is not correct, use the group-policy or igmp-snooping group-policy command to apply the correct multicast group policy.
3. Use the display igmp-snooping command to verify that dropping unknown multicast data is enabled. If it is not, use the igmp-snooping drop-unknown command to enable dropping unknown multicast data.
4. If the problem persists, contact H3C Support.
Configuring PIM snooping
Overview
PIM snooping runs on Layer 2 devices. It works with IGMP snooping to analyze received PIM messages, and adds the ports that are interested in specific multicast data to a PIM snooping routing entry. In this way, the multicast data can be forwarded to only the ports that are interested in the data.
Figure 17 Multicast packet transmission without or with PIM snooping
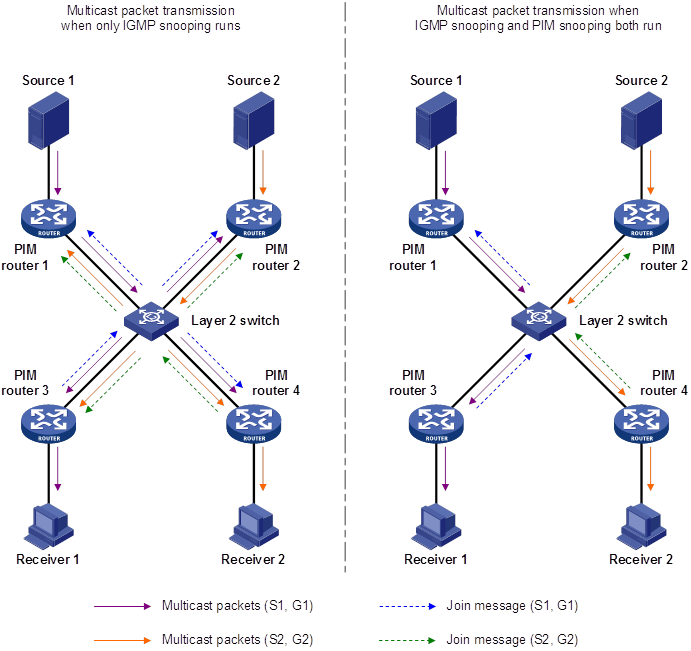
As shown in Figure 17, Source 1 sends multicast data to multicast group G1, and Source 2 sends multicast data to multicast group G2. Receiver 1 belongs to G1, and Receiver 2 belongs to G2. The Layer 2 switch's interfaces that connect to the PIM routers are in the same VLAN or VSI.
· When the Layer 2 switch runs only IGMP snooping, it performs the following actions:
a. Maintains the router ports according to the received PIM hello messages that PIM routers send.
b. Floods all other types of received PIM messages except PIM hello messages in the VLAN or VSI.
c. Forwards all multicast data to all router ports in the VLAN or VSI.
Each PIM router in the VLAN, whether interested in the multicast data or not, can receive all multicast data and all PIM messages except PIM hello messages.
· When the Layer 2 switch runs both IGMP snooping and PIM snooping, it performs the following actions:
d. Examines whether a PIM router is interested in the multicast data addressed to a multicast group according to the received PIM messages that the router sends.
e. Adds only the ports that connect to the router and are interested in the data to a PIM snooping routing entry.
f. Forwards PIM messages and multicast data to only the routers that are interested in the data, which saves network bandwidth.
For more information about IGMP snooping and the router port, see "Configuring IGMP snooping."
PIM snooping can run in PIM-SM and PIM-SSM networks. Do not configure PIM snooping in PIM-DM networks. For more information about PIM, see "Configuring PIM."
Configuring PIM snooping
|
|
IMPORTANT: Make sure the maximum size of a PIM join or prune message is smaller than the path MTU of devices connected to PIM snooping devices. Otherwise, fragmented PIM join or prune messages prevent PIM snooping from correctly forwarding multicast data. For more information about setting the maximum size of a join or prune message, see "Configuring PIM." |
To configure PIM snooping for a VLAN or VSI, you must enable IGMP snooping globally on the Layer 2 device, and then enable IGMP snooping and PIM snooping for the VLAN or VSI.
To configure PIM snooping:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable IGMP snooping globally and enter IGMP-snooping view. |
igmp-snooping |
By default, IGMP snooping is disabled. |
|
3. Return to system view. |
quit |
N/A |
|
4. Enter VLAN view or VSI view. |
·
Enter VLAN view: ·
Enter VSI view: |
N/A |
|
5. Enable IGMP snooping for the VLAN or VSI. |
igmp-snooping enable |
By default, IGMP snooping is disabled in a VLAN or VSI. |
|
6. Enable PIM snooping for the VLAN or VSI. |
pim-snooping enable |
By default, PIM snooping is disabled in a VLAN or VSI. |
|
7. (Optional.) Set the aging time for global neighbor ports on the new active MPU after an active/standby switchover. |
pim-snooping graceful-restart neighbor-aging-time seconds |
The default setting is 105 seconds. A global neighbor port is a Layer 2 aggregate interface, AC interface, N-PW interface, or U-PW interface that acts as a neighbor port. |
|
8. (Optional.) Set the aging time for global downstream ports and global router ports on the new active MPU after an active/standby switchover. |
pim-snooping graceful-restart join-aging-time seconds |
The default setting is 210 seconds. A global downstream port or a global router port is a Layer 2 aggregate interface, AC interface, N-PW interface, or U-PW interface that acts as a downstream port or router port. |
Displaying and maintaining PIM snooping
Execute display commands in any view and reset commands in user view.
|
Task |
Command |
|
(In standalone mode.) Display PIM snooping neighbor information. |
display pim-snooping neighbor [ vlan vlan-id | vsi vsi-name ] [ slot slot-number ] [ verbose ] |
|
(In IRF mode.) Display PIM snooping neighbor information. |
display pim-snooping neighbor [ vlan vlan-id | vsi vsi-name ] [ chassis chassis-number slot slot-number ] [ verbose ] |
|
(In standalone mode.) Display PIM snooping router port information. |
display pim-snooping router-port [ vlan vlan-id | vsi vsi-name ] [ slot slot-number ] [ verbose ] |
|
(In IRF mode.) Display PIM snooping router port information. |
display pim-snooping router-port [ vlan vlan-id | vsi vsi-name ] [ chassis chassis-number slot slot-number ] [ verbose ] |
|
(In standalone mode.) Display PIM snooping routing entries. |
display pim-snooping routing-table [ vlan vlan-id | vsi vsi-name ] [ slot slot-number ] [ verbose ] |
|
(In IRF mode.) Display PIM snooping routing entries. |
display pim-snooping routing-table [ vlan vlan-id | vsi vsi-name ] [ chassis chassis-number slot slot-number ] [ verbose ] |
|
Display statistics for the PIM messages learned through PIM snooping. |
display pim-snooping statistics |
|
Clear statistics for the PIM messages learned through PIM snooping. |
reset pim-snooping statistics |
PIM snooping configuration example (for VLANs)
Network requirements
As shown in Figure 18:
· OSPF runs on the network.
· Source 1 and Source 2 send multicast data to multicast groups 224.1.1.1 and 225.1.1.1, respectively.
· Receiver 1 and Receiver 2 belong to multicast groups 224.1.1.1 and 225.1.1.1, respectively.
· Router C and Router D run IGMP on HundredGigE 1/0/1. Router A, Router B, Router C, and Router D run PIM-SM.
· HundredGigE 1/0/2 on Router A acts as a C-BSR and a C-RP.
To make sure Switch A forwards PIM protocol packets and multicast data packets only to the routers that are connected to receivers, perform the following tasks:
· On Switch A, configure IGMP snooping and PIM snooping.
· On all PIM routers connected to Switch A, set the maximum size of a join or prune message to 1400 bytes, which is less than the path MTU.
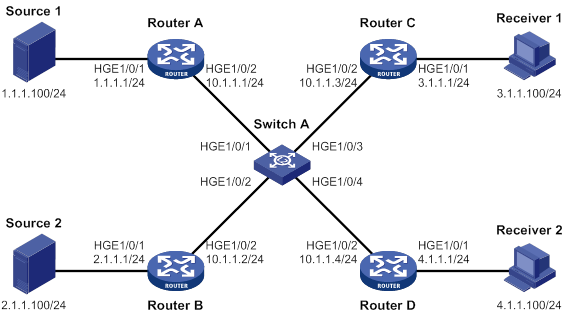
Configuration procedure
1. Assign an IP address and subnet mask to each interface, as shown in Figure 18. (Details not shown.)
2. Configure OSPF on the routers. (Details not shown.)
3. Configure Router A:
# Enable IP multicast routing.
<RouterA> system-view
[RouterA] multicast routing
[RouterA-mrib] quit
# Enable PIM-SM on each interface.
[RouterA] interface hundredgige 1/0/1
[RouterA-HundredGigE1/0/1] pim sm
[RouterA-HundredGigE1/0/1] quit
[RouterA] interface hundredgige 1/0/2
[RouterA-HundredGigE1/0/2] pim sm
[RouterA-HundredGigE1/0/2] quit
# Set the maximum size of a join or prune message to 1400 bytes.
[RouterA] pim
[RouterA-pim] jp-pkt-size 1400
# Configure HundredGigE 1/0/2 as a C-BSR and a C-RP.
[RouterA-pim] c-bsr 10.1.1.1
[RouterA-pim] c-rp 10.1.1.1
[RouterA-pim] quit
4. Configure Router B:
# Enable IP multicast routing.
<RouterB> system-view
[RouterB] multicast routing
[RouterB-mrib] quit
# Enable PIM-SM on each interface.
[RouterB] interface hundredgige 1/0/1
[RouterB-HundredGigE1/0/1] pim sm
[RouterB-HundredGigE1/0/1] quit
[RouterB] interface hundredgige 1/0/2
[RouterB-HundredGigE1/0/2] pim sm
[RouterB-HundredGigE1/0/2] quit
# Set the maximum size of a join or prune message to 1400 bytes.
[RouterB] pim
[RouterB-pim] jp-pkt-size 1400
5. Configure Router C:
# Enable IP multicast routing.
<RouterC> system-view
[RouterC] multicast routing
[RouterC-mrib] quit
# Enable IGMP on HundredGigE 1/0/1.
[RouterC] interface hundredgige 1/0/1
[RouterC-HundredGigE1/0/1] igmp enable
[RouterC-HundredGigE1/0/1] quit
# Enable PIM-SM on HundredGigE 1/0/2.
[RouterC] interface hundredgige 1/0/2
[RouterC-HundredGigE1/0/2] pim sm
[RouterC-HundredGigE1/0/2] quit
# Set the maximum size of a join or prune message to 1400 bytes.
[RouterC] pim
[RouterC-pim] jp-pkt-size 1400
6. Configure Router D:
# Enable IP multicast routing.
<RouterD> system-view
[RouterD] multicast routing
[RouterD-mrib] quit
# Enable IGMP on HundredGigE 1/0/1.
[RouterD] interface hundredgige 1/0/1
[RouterD-HundredGigE1/0/1] igmp enable
[RouterD-HundredGigE1/0/1] quit
# Enable PIM-SM on HundredGigE 1/0/2.
[RouterD] interface hundredgige 1/0/2
[RouterD-HundredGigE1/0/2] pim sm
[RouterD-HundredGigE1/0/2] quit
# Set the maximum size of a join or prune message to 1400 bytes.
[RouterD] pim
[RouterD-pim] jp-pkt-size 1400
7. Configure Switch A:
# Enable IGMP snooping globally.
<SwitchA> system-view
[SwitchA] igmp-snooping
[SwitchA-igmp-snooping] quit
# Create VLAN 100, and assign HundredGigE 1/0/1 through HundredGigE 1/0/4 to the VLAN.
[SwitchA] vlan 100
[SwitchA-vlan100] port hundredgige 1/0/1 to hundredgige 1/0/4
# Enable IGMP snooping and PIM snooping for VLAN 100.
[SwitchA-vlan100] igmp-snooping enable
[SwitchA-vlan100] pim-snooping enable
[SwitchA-vlan100] quit
Verifying the configuration
# On Switch A, display brief information about PIM snooping neighbors for VLAN 100.
[SwitchA] display pim-snooping neighbor vlan 100
Total 4 neighbors.
VLAN 100: Total 4 neighbors.
10.1.1.1
Ports (1 in total):
HGE1/0/1 (00:32:43)
10.1.1.2
Ports (1 in total):
HGE1/0/2 (00:32:43)
10.1.1.3
Ports (1 in total):
HGE1/0/3 (00:32:43)
10.1.1.4
Ports (1 in total):
HGE1/0/4 (00:32:43)
The output shows that Router A, Router B, Router C, and Router D are PIM snooping neighbors.
# On Switch A, display brief information about PIM snooping routing entries for VLAN 100.
[SwitchA] display pim-snooping routing-table vlan 100
Total 2 entries.
FSM Flag: NI-no info, J-join, PP-prune pending
VLAN 100: Total 2 entries.
(*, 224.1.1.1)
Upstream neighbor: 10.1.1.1
Upstream Ports (1 in total):
HGE1/0/1
Downstream Ports (1 in total):
HGE1/0/3
Expires: 00:03:01, FSM: J
(*, 225.1.1.1)
Upstream neighbor: 10.1.1.2
Upstream Ports (1 in total):
HGE1/0/2
Downstream Ports (1 in total):
HGE1/0/4
Expires: 00:03:11, FSM: J
The output shows the following information:
· Switch A will forward the multicast data intended for multicast group 224.1.1.1 only to Router C.
· Switch A will forward the multicast data intended for multicast group 225.1.1.1 only to Router D.
Troubleshooting PIM snooping
PIM snooping does not work on a Layer 2 device
Symptom
PIM snooping does not work on a Layer 2 device.
Solution
To resolve the problem:
1. Use the display current-configuration command to display information about IGMP snooping and PIM snooping.
2. If IGMP snooping is not enabled, enable IGMP snooping globally, and then enable IGMP snooping and PIM snooping for the VLAN or VSI.
3. If PIM snooping is not enabled, enable PIM snooping for the VLAN or VSI.
4. If the problem persists, contact H3C Support.
Configuring multicast VLANs
Overview
As shown in Figure 19, Host A, Host B, and Host C are in three different VLANs and the same multicast group. When Switch A (Layer 3 device) receives multicast data for that group, it sends three copies of the multicast data to Switch B (Layer 2 device). This occupies a large amount of bandwidth and increases the burden on the Layer 3 device.
Figure 19 Multicast transmission without the multicast VLAN feature
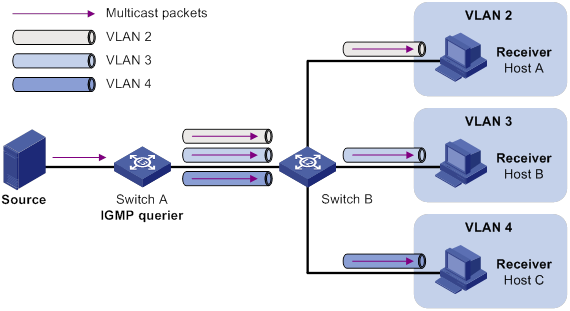
After a multicast VLAN is configured on Switch B, Switch A sends only one copy of the multicast data to the multicast VLAN on Switch B. This method saves network bandwidth and lessens the burden on the Layer 3 device.
Multicast VLANs include sub-VLAN-based multicast VLANs and port-based multicast VLANs.
|
|
NOTE: Support for the sub-VLAN-based multicast VLAN feature or the port-based multicast VLAN feature depends on the device model. |
Sub-VLAN-based multicast VLAN
As shown in Figure 20:
· Host A, Host B, and Host C are in VLAN 2 through VLAN 4, respectively.
· On Switch B, VLAN 10 is a multicast VLAN. VLAN 2 through VLAN 4 are sub-VLANs of VLAN 10.
· IGMP snooping is enabled for the multicast VLAN and its sub-VLANs.
Figure 20 Sub-VLAN-based multicast VLAN
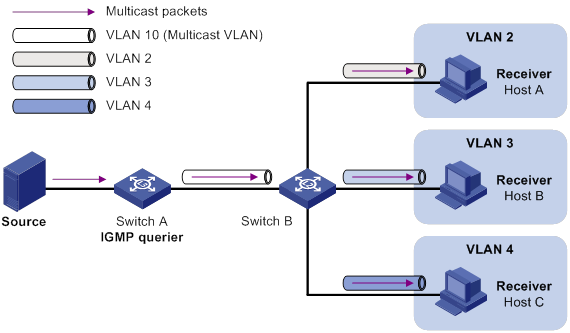
IGMP snooping manages router ports in the multicast VLAN and member ports in each sub-VLAN. When Switch A receives multicast data from the multicast source, it sends only one copy of the multicast data to the multicast VLAN on Switch B. Then, Switch B sends a separate copy to each sub-VLAN in the multicast VLAN.
Port-based multicast VLAN
As shown in Figure 21:
· Host A, Host B, and Host C are in VLAN 2 through VLAN 4, respectively.
· On Switch B, VLAN 10 is a multicast VLAN. All the user ports are hybrid ports and are assigned to VLAN 10.
· IGMP snooping is enabled for the multicast VLAN and VLAN 2 through VLAN 4.
Figure 21 Port-based multicast VLAN
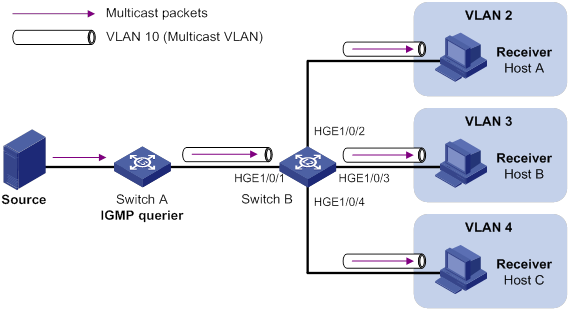
IGMP snooping manages the router ports and member ports in the multicast VLAN. When Switch A receives multicast data from the multicast source, it sends only one copy of the multicast data to the multicast VLAN on Switch B. Switch B sends a separate copy to each user port in the multicast VLAN.
Multicast VLAN configuration task list
|
Tasks at a glance |
|
(Required.) Perform one of the following tasks: · Configuring a sub-VLAN-based multicast VLAN · Configuring a port-based multicast VLAN: |
|
(Optional.) Setting the maximum number of multicast VLAN forwarding entries |
If you have configured both a sub-VLAN-based multicast VLAN and a port-based multicast VLAN on a device, the port-based multicast VLAN configuration takes effect.
Configuring a sub-VLAN-based multicast VLAN
To configure a sub-VLAN-based multicast VLAN, configure a VLAN as a multicast VLAN, and assign the VLANs that contain multicast receivers to the multicast VLAN as sub-VLANs.
Configuration prerequisites
Before you configure a sub-VLAN-based multicast VLAN, complete the following tasks:
· Create VLANs as required.
Configuration restrictions and guidelines
When you configure a sub-VLAN-based multicast VLAN, follow these restrictions and guidelines:
· The VLAN to be configured as the multicast VLAN must exist.
· The VLANs to be configured as sub-VLANs of the multicast VLAN must exist and cannot be multicast VLANs or sub-VLANs of any other multicast VLAN.
· The total number of multicast VLANs on a device cannot exceed the upper limit.
Configuration procedure
To configure a sub-VLAN-based multicast VLAN:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Configure a VLAN as a multicast VLAN and enter its view. |
multicast-vlan vlan-id |
By default, a VLAN is not a multicast VLAN. |
|
3. Assign the specified VLANs to the multicast VLAN as sub-VLANs. |
subvlan vlan-list |
By default, a multicast VLAN does not have any sub-VLANs. |
Configuring a port-based multicast VLAN
You can assign only Layer 2 Ethernet interfaces or Layer 2 aggregate interfaces to a multicast VLAN.
Configuration prerequisites
Before you configure a port-based multicast VLAN, complete the following tasks:
· Create VLANs as required.
· Enable IGMP snooping for the VLAN to be configured as the multicast VLAN.
· Enable IGMP snooping for all the VLANs that contain the multicast receivers.
Configuring user port attributes
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter interface view. |
interface interface-type interface-number |
N/A |
|
3. Configure the link type of the user port as hybrid. |
port link-type hybrid |
The default setting is access. For more information about this command, see Layer 2—LAN Switching Command Reference. |
|
4. Specify the PVID of the current user port as the VLAN to which the user port belongs. |
port hybrid pvid vlan vlan-id |
By default, the PVID for a hybrid port is VLAN 1. For more information about this command, see Layer 2—LAN Switching Command Reference. |
|
5. Configure the current user port to permit multicast VLAN and to untag the packets. |
port hybrid vlan vlan-id-list untagged |
By default, a hybrid port permits only VLAN 1. For more information about this command, see Layer 2—LAN Switching Command Reference. |
Assigning user ports to a multicast VLAN
You can assign user ports to a multicast VLAN in multicast VLAN view or assign a user port to a multicast VLAN in interface view. These configurations have the same priority.
Configuration restrictions and guidelines
When you assign user ports to a multicast VLAN, follow these restrictions and guidelines:
· The VLAN to be configured as a multicast VLAN must exist.
· A port can belong to only one multicast VLAN.
Configuration procedure
To assign user ports to a multicast VLAN in multicast VLAN view:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Configure a VLAN as a multicast VLAN and enter its view. |
multicast-vlan vlan-id |
By default, a VLAN is not a multicast VLAN. |
|
3. Assign ports to the multicast VLAN. |
port interface-list |
By default, a multicast VLAN does not have any user ports. |
To assign a user port to a multicast VLAN in interface view:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Configure a VLAN as a multicast VLAN and enter its view. |
multicast-vlan vlan-id |
By default, a VLAN is not a multicast VLAN. |
|
3. Return to system view. |
quit |
N/A |
|
4. Enter interface view. |
interface interface-type interface-number |
N/A |
|
5. Assign the current port to the multicast VLAN. |
port multicast-vlan vlan-id |
By default, a user port does not belong to any multicast VLAN. |
Setting the maximum number of multicast VLAN forwarding entries
You can set the maximum number of multicast VLAN forwarding entries on the device. When the upper limit is reached, the device does not create multicast VLAN forwarding entries until some entries age out or are manually removed.
If the total number of the entries exceeds the upper limit value that you are setting, the system does not automatically remove existing entries or create new entries. In this case, remove excess entries manually.
To set the maximum number of multicast VLAN forwarding entries:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Set the maximum number of multicast VLAN forwarding entries. |
multicast-vlan entry-limit limit |
By default, the maximum number of multicast VLAN forwarding entries is 8000. |
Displaying and maintaining multicast VLANs
Execute display commands in any view and reset commands in user view.
|
Task |
Command |
|
Display information about multicast VLANs. |
display multicast-vlan [ vlan-id ] |
|
(In standalone mode.) Display information about multicast groups in multicast VLANs. |
display multicast-vlan group [ source-address | group-address | slot slot-number | verbose | vlan vlan-id ] * |
|
(In IRF mode.) Display information about multicast groups in multicast VLANs. |
display multicast-vlan group [ source-address | group-address | chassis chassis-number slot slot-number | verbose | vlan vlan-id ] * |
|
(In standalone mode.) Display information about multicast VLAN forwarding entries. |
display multicast-vlan forwarding-table [ group-address [ mask { mask-length | mask } ] | source-address [ mask { mask-length | mask } ] | slot slot-number | subvlan vlan-id | vlan vlan-id ] * |
|
(In IRF mode.) Display information about multicast VLAN forwarding entries. |
display multicast-vlan forwarding-table [ group-address [ mask { mask-length | mask } ] | source-address [ mask { mask-length | mask } ] | chassis chassis-number slot slot-number | subvlan vlan-id | vlan vlan-id ] * |
|
Clear multicast groups in multicast VLANs. |
reset multicast-vlan group [ source-address [ mask { mask-length | mask } ] | group-address [ mask { mask-length | mask } ] | vlan vlan-id ] * |
Multicast VLAN configuration examples
Sub-VLAN-based multicast VLAN configuration example
Network requirements
As shown in Figure 22:
· Layer 3 device Switch A runs IGMPv2 and acts as the IGMP querier. Layer 2 device Switch B runs IGMPv2 snooping.
· The multicast source sends multicast data to multicast group 224.1.1.1. Receivers Host A, Host B, and Host C belong to VLAN 2, VLAN 3, and VLAN 4, respectively.
Configure a sub-VLAN-based multicast VLAN on Switch B to meet the following requirements:
· Switch A sends the multicast data to Switch B through the multicast VLAN.
· Switch B forwards the multicast data to the receivers in different user VLANs.
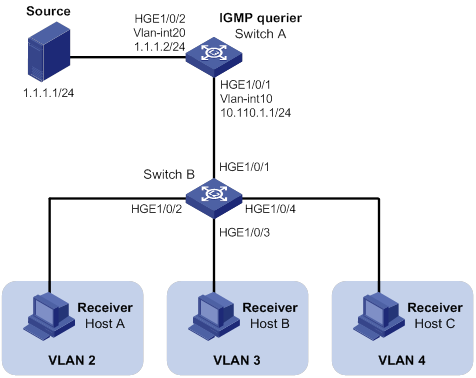
Configuration procedure
1. Configure Switch A:
# Enable IP multicast routing.
<SwitchA> system-view
[SwitchA] multicast routing
[SwitchA-mrib] quit
# Create VLAN 20, and assign HundredGigE 1/0/2 to the VLAN.
[SwitchA] vlan 20
[SwitchA-vlan20] port hundredgige 1/0/2
[SwitchA-vlan20] quit
# Assign an IP address to VLAN-interface 20, and enable PIM-DM on the interface.
[SwitchA] interface vlan-interface 20
[SwitchA-Vlan-interface20] ip address 1.1.1.2 24
[SwitchA-Vlan-interface20] pim dm
[SwitchA-Vlan-interface20] quit
# Create VLAN 10.
[SwitchA] vlan 10
[SwitchA-vlan10] quit
# Configure HundredGigE 1/0/1 as a hybrid port, and assign the port to VLAN 10 as a tagged VLAN member.
[SwitchA] interface hundredgige 1/0/1
[SwitchA-HundredGigE1/0/1] port link-type hybrid
[SwitchA-HundredGigE1/0/1] port hybrid vlan 10 tagged
[SwitchA-HundredGigE1/0/1] quit
# Assign an IP address to VLAN-interface 10, and enable IGMP on the interface.
[SwitchA] interface vlan-interface 10
[SwitchA-Vlan-interface10] ip address 10.110.1.1 24
[SwitchA-Vlan-interface10] igmp enable
[SwitchA-Vlan-interface10] quit
2. Configure Switch B:
# Enable IGMP snooping globally.
<SwitchB> system-view
[SwitchB] igmp-snooping
[SwitchB-igmp-snooping] quit
# Create VLAN 2, assign HundredGigE 1/0/2 to the VLAN, and enable IGMP snooping for the VLAN.
[SwitchB] vlan 2
[SwitchB-vlan2] port hundredgige 1/0/2
[SwitchB-vlan2] igmp-snooping enable
[SwitchB-vlan2] quit
# Create VLAN 3, assign HundredGigE 1/0/3 to the VLAN, and enable IGMP snooping in the VLAN.
[SwitchB] vlan 3
[SwitchB-vlan3] port hundredgige 1/0/3
[SwitchB-vlan3] igmp-snooping enable
[SwitchB-vlan3] quit
# Create VLAN 4, assign HundredGigE 1/0/4 to the VLAN, and enable IGMP snooping in the VLAN.
[SwitchB] vlan 4
[SwitchB-vlan4] port hundredgige 1/0/4
[SwitchB-vlan4] igmp-snooping enable
[SwitchB-vlan4] quit
# Create VLAN 10, and enable IGMP snooping for the VLAN.
[SwitchB] vlan 10
[SwitchB-vlan10] igmp-snooping enable
[SwitchB-vlan10] quit
# Configure HundredGigE 1/0/1 as a hybrid port, and assign the port to VLAN 10 as a tagged VLAN member.
[SwitchB] interface hundredgige 1/0/1
[SwitchB-HundredGigE1/0/1] port link-type hybrid
[SwitchB-HundredGigE1/0/1] port hybrid vlan 10 tagged
[SwitchB-HundredGigE1/0/1] quit
# Configure VLAN 10 as a multicast VLAN, and assign VLAN 2 through VLAN 4 as sub-VLANs to multicast VLAN 10.
[SwitchB] multicast-vlan 10
[SwitchB-mvlan-10] subvlan 2 to 4
[SwitchB-mvlan-10] quit
Verifying the configuration
# Display information about all multicast VLANs on Switch B.
[SwitchB] display multicast-vlan
Total 1 multicast VLANs.
Multicast VLAN 10:
Sub-VLAN list(3 in total):
2-4
Port list(0 in total):
# Display information about multicast groups in multicast VLANs on Switch B.
[SwitchB] display multicast-vlan group
Total 1 entries.
Multicast VLAN 10: Total 1 entries.
(0.0.0.0, 224.1.1.1)
Sub-VLANs (3 in total):
VLAN 2
VLAN 3
VLAN 4
The output shows that multicast group 224.1.1.1 belongs to multicast VLAN 10. Multicast VLAN 10 contains sub-VLANs VLAN 2 through VLAN 4. Switch B will replicate the multicast data of VLAN 10 to VLAN 2 through VLAN 4.
Port-based multicast VLAN configuration example
Network requirements
As shown in Figure 23:
· Layer 3 device Switch A runs IGMPv2 and acts as the IGMP querier. Layer 2 device Switch B runs IGMPv2 snooping.
· The multicast source sends multicast data to multicast group 224.1.1.1. Receivers Host A, Host B, and Host C belong to VLAN 2, VLAN 3, and VLAN 4, respectively.
Configure a port-based multicast VLAN on Switch B to meet the following requirements:
· Switch A sends multicast data to Switch B through the multicast VLAN.
· Switch B forwards the multicast data to the receivers in different user VLANs.
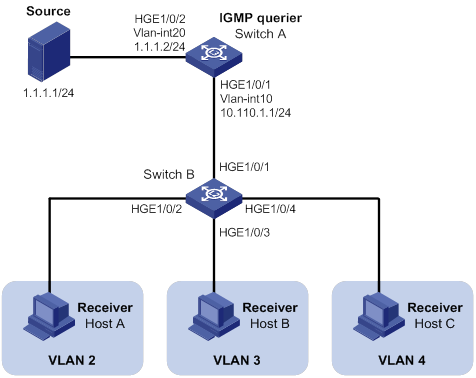
Configuration procedure
1. Configure Switch A:
# Enable IP multicast routing.
<SwitchA> system-view
[SwitchA] multicast routing
[SwitchA-mrib] quit
# Create VLAN 20, and assign HundredGigE 1/0/2 to the VLAN.
[SwitchA] vlan 20
[SwitchA-vlan20] port hundredgige 1/0/2
[SwitchA-vlan20] quit
# Assign an IP address to VLAN-interface 20, and enable PIM-DM on the interface.
[SwitchA] interface vlan-interface 20
[SwitchA-Vlan-interface20] ip address 1.1.1.2 24
[SwitchA-Vlan-interface20] pim dm
[SwitchA-Vlan-interface20] quit
# Create VLAN 10, and assign HundredGigE 1/0/1 to the VLAN.
[SwitchA] vlan 10
[SwitchA-vlan10] port hundredgige 1/0/1
[SwitchA-vlan10] quit
# Assign an IP address to VLAN-interface 10, and enable IGMP on the interface.
[SwitchA] interface vlan-interface 10
[SwitchA-Vlan-interface10] ip address 10.110.1.1 24
[SwitchA-Vlan-interface10] igmp enable
[SwitchA-Vlan-interface10] quit
2. Configure Switch B:
# Enable IGMP snooping globally.
<SwitchB> system-view
[SwitchB] igmp-snooping
[SwitchB-igmp-snooping] quit
# Create VLAN 10, assign HundredGigE 1/0/1 to the VLAN, and enable IGMP snooping for the VLAN.
[SwitchB] vlan 10
[SwitchB-vlan10] port hundredgige 1/0/1
[SwitchB-vlan10] igmp-snooping enable
[SwitchB-vlan10] quit
# Create VLAN 2, and enable IGMP snooping for the VLAN.
[SwitchB] vlan 2
[SwitchB-vlan2] igmp-snooping enable
[SwitchB-vlan2] quit
# Create VLAN 3, and enable IGMP snooping for the VLAN.
[SwitchB] vlan 3
[SwitchB-vlan3] igmp-snooping enable
[SwitchB-vlan3] quit
# Create VLAN 4, and enable IGMP snooping for the VLAN.
[SwitchB] vlan 4
[SwitchB-vlan4] igmp-snooping enable
[SwitchB-vlan4] quit
# Configure HundredGigE 1/0/2 as a hybrid port, and configure VLAN 2 as the PVID of the hybrid port.
[SwitchB] interface hundredgige 1/0/2
[SwitchB-HundredGigE1/0/2] port link-type hybrid
[SwitchB-HundredGigE1/0/2] port hybrid pvid vlan 2
# Assign HundredGigE 1/0/2 to VLAN 2 and VLAN 10 as an untagged VLAN member.
[SwitchB-HundredGigE1/0/2] port hybrid vlan 2 untagged
[SwitchB-HundredGigE1/0/2] port hybrid vlan 10 untagged
[SwitchB-HundredGigE1/0/2] quit
# Configure HundredGigE 1/0/3 as a hybrid port, and configure VLAN 3 as the PVID of the hybrid port.
[SwitchB] interface hundredgige 1/0/3
[SwitchB-HundredGigE1/0/3] port link-type hybrid
[SwitchB-HundredGigE1/0/3] port hybrid pvid vlan 3
# Assign HundredGigE 1/0/3 to VLAN 3 and VLAN 10 as an untagged VLAN member.
[SwitchB-HundredGigE1/0/3] port hybrid vlan 3 untagged
[SwitchB-HundredGigE1/0/3] port hybrid vlan 10 untagged
[SwitchB-HundredGigE1/0/3] quit
# Configure HundredGigE 1/0/4 as a hybrid port, and configure VLAN 4 as the PVID of the hybrid port.
[SwitchB] interface hundredgige 1/0/4
[SwitchB-HundredGigE1/0/4] port link-type hybrid
[SwitchB-HundredGigE1/0/4] port hybrid pvid vlan 4
# Assign HundredGigE 1/0/4 to VLAN 4 and VLAN 10 as an untagged VLAN member.
[SwitchB-HundredGigE1/0/4] port hybrid vlan 4 untagged
[SwitchB-HundredGigE1/0/4] port hybrid vlan 10 untagged
[SwitchB-HundredGigE1/0/4] quit
# Configure VLAN 10 as a multicast VLAN.
[SwitchB] multicast-vlan 10
# Assign HundredGigE 1/0/2 and HundredGigE 1/0/3 to VLAN 10.
[SwitchB-mvlan-10] port hundredgige 1/0/2 to hundredgige 1/0/3
[SwitchB-mvlan-10] quit
# Assign HundredGigE 1/0/4 to VLAN 10.
[SwitchB] interface hundredgige 1/0/4
[SwitchB-HundredGigE1/0/4] port multicast-vlan 10
[SwitchB-HundredGigE1/0/4] quit
Verifying the configuration
# Display information about multicast VLANs on Switch B.
[SwitchB] display multicast-vlan
Total 1 multicast VLANs.
Multicast VLAN 10:
Sub-VLAN list(0 in total):
Port list(0 in total):
HGE1/0/2
HGE1/0/3
HGE1/0/4
# Display dynamic IGMP snooping forwarding entries on Switch B.
[SwitchB] display igmp-snooping group
Total 1 entries.
VLAN 10: Total 1 entries.
(0.0.0.0, 224.1.1.1)
Host slots (0 in total):
Host ports (3 in total):
HGE1/0/2 (00:03:23)
HGE1/0/3 (00:04:07)
HGE1/0/4 (00:04:16)
The output shows that IGMP snooping maintains the user ports in the multicast VLAN (VLAN 10). Switch B will forward the multicast data of VLAN 10 through these user ports.
Configuring multicast routing and forwarding
Overview
The following tables are involved in multicast routing and forwarding:
· Multicast routing table of each multicast routing protocol, such as the PIM routing table.
· General multicast routing table that summarizes multicast routing information generated by different multicast routing protocols. The multicast routing information from multicast sources to multicast groups are stored in a set of (S, G) routing entries.
· Multicast forwarding table that guides multicast forwarding. The optimal routing entries in the multicast routing table are added to the multicast forwarding table.
RPF check mechanism
A multicast routing protocol uses reverse path forwarding (RPF) check to ensure the multicast data delivery along the correct path and to avoid data loops.
RPF check process
A multicast router performs the RPF check on a multicast packet as follows:
1. The router chooses an optimal route back to the packet source separately from the unicast, MBGP, and static multicast routing tables.
The term "packet source" means different things in different situations:
? For a packet that travels along the SPT, the packet source is the multicast source.
? For a packet that travels along the RPT, the packet source is the RP.
? For a bootstrap message originated from the BSR, the packet source is the BSR.
For more information about the concepts of SPT, RPT, source-side RPT, RP, and BSR, see "Configuring PIM."
2. The router selects one of the three optimal routes as the RPF route as follows:
? If the router uses the longest prefix match principle, the route with the highest subnet mask becomes the RPF route. If the routes have the same mask, the route with the highest route preference becomes the RPF route. If the routes have the same route preference, the unicast route becomes the RPF route.
For more information about the route preference, see Layer 3—IP Routing Configuration Guide.
? If the router does not use the longest prefix match principle, the route with the highest route preference becomes the RPF route. If the routes have the same preference, the unicast route becomes the RPF route.
The RPF route contains the RPF interface and RPF neighbor information.
? If the RPF route is a unicast route or MBGP route, the outgoing interface is the RPF interface and the next hop is the RPF neighbor.
? If the RPF route is a static multicast route, the RPF interface and RPF neighbor are specified in the route.
3. The router checks whether the packet arrived at the RPF interface. If yes, the RPF check succeeds and the packet is forwarded. If not, the RPF check fails and the packet is discarded.
RPF check implementation in multicast
Implementing an RPF check on each received multicast packet brings a big burden to the router. The use of a multicast forwarding table is the solution to this issue. When the router creates a multicast forwarding entry for an (S, G) packet, it sets the RPF interface of the packet as the incoming interface of the (S, G) entry. After the router receives another (S, G) packet, it looks up the multicast forwarding table for a matching (S, G) entry.
· If no match is found, the router first determines the RPF route back to the packet source and the RPF interface. Then, it creates a forwarding entry with the RPF interface as the incoming interface and makes the following judgments:
? If the receiving interface is the RPF interface, the RPF check succeeds and the router forwards the packet out of all the outgoing interfaces.
? If the receiving interface is not the RPF interface, the RPF check fails and the router discards the packet.
· If a match is found and the matching forwarding entry contains the receiving interface, the router forwards the packet out of all the outgoing interfaces.
· If a match is found but the matching forwarding entry does not contain the receiving interface, the router determines the RPF route back to the packet source. Then, the router performs one of the following actions:
? If the RPF interface is the incoming interface, it means that the forwarding entry is correct but the packet traveled along a wrong path. The packet fails the RPF check, and the router discards the packet.
? If the RPF interface is not the incoming interface, it means that the forwarding entry has expired. The router replaces the incoming interface with the RPF interface and matches the receiving interface against the RPF interface. If the receiving interface is the RPF interface, the router forwards the packet out of all outgoing interfaces. Otherwise, it discards the packet.
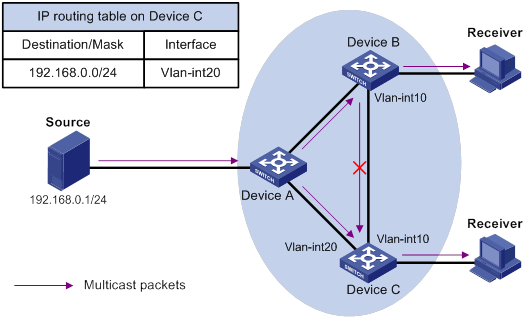
As shown in Figure 24, assume that unicast routes are available on the network, MBGP is not configured, and no static multicast routes have been configured on Device C. Multicast packets travel along the SPT from the multicast source to the receivers. The multicast forwarding table on Device C contains the (S, G) entry, with VLAN-interface 20 as the incoming interface.
· If a multicast packet arrives at Device C on VLAN-interface 20, the receiving interface is the incoming interface of the (S, G) entry. Device C forwards the packet out of all outgoing interfaces.
· If a multicast packet arrives at Device C on VLAN-interface 10, the receiving interface is not the incoming interface of the (S, G) entry. Device C searches its unicast routing table and finds that the outgoing interface to the source (the RPF interface) is VLAN-interface 20. In this case, the (S, G) entry is correct, but the packet traveled along a wrong path. The packet fails the RPF check and Device C discards the packet.
Static multicast routes
Depending on the application environment, a static multicast route can change an RPF route or create an RPF route.
Changing an RPF route
Typically, the topology structure of a multicast network is the same as that of a unicast network, and multicast traffic follows the same transmission path as unicast traffic does. You can configure a static multicast route for a multicast source to change the RPF route. As a result, the router creates a transmission path for multicast traffic that is different from the transmission path for unicast traffic.
Figure 25 Changing an RPF route
As shown in Figure 25, when no static multicast route is configured, Device C's RPF neighbor on the path back to the source is Device A. The multicast data from the source travels through Device A to Device C. You can configure a static multicast route on Device C and specify Device B as Device C's RPF neighbor on the path back to the source. The multicast data from the source travels along the path: Device A to Device B and then to Device C.
Creating an RPF route
When a unicast route is blocked, multicast forwarding might be stopped due to lack of an RPF route. You can configure a static multicast route to create an RPF route. In this way, a multicast routing entry is created to guide multicast forwarding.
Figure 26 Creating an RPF route
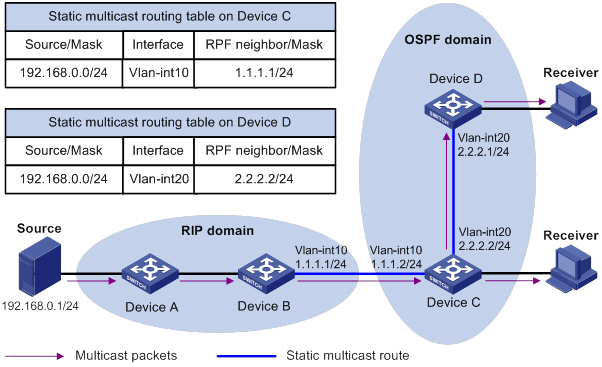
As shown in Figure 26, the RIP domain and the OSPF domain are unicast isolated from each other. For the receiver hosts in the OSPF domain to receive multicast packets from the multicast source in the RIP domain, you must configure Device C and Device D as follows:
· On Device C, configure a static multicast route for the multicast source and specify Device B as the RPF neighbor.
· On Device D, configure a static multicast route for the multicast source and specify Device C as the RPF neighbor.
|
|
NOTE: A static multicast route is effective only on the multicast router on which it is configured, and will not be advertised throughout the network or redistributed to other routers. |
Multicast forwarding across unicast subnets
Routers forward the multicast data from a multicast source hop by hop along the forwarding tree, but some routers might not support multicast protocols in a network. When the multicast data is forwarded to a router that does not support IP multicast, the forwarding path is blocked. In this case, you can enable multicast forwarding across two unicast subnets by establishing a tunnel between the routers at the edges of the two unicast subnets.
Figure 27 Multicast data transmission through a tunnel
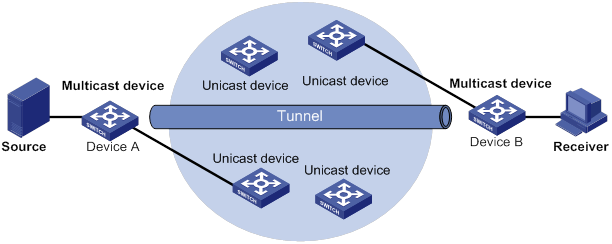
As shown in Figure 27, a tunnel is established between the multicast routers Device A and Device B. Device A encapsulates the multicast data in unicast IP packets, and forwards them to Device B across the tunnel through unicast routers. Then, Device B strips off the unicast IP header and continues to forward the multicast data to the receiver.
To use this tunnel only for multicast traffic, configure the tunnel as the outgoing interface only for multicast routes.
Configuration task list
|
Tasks at a glance |
|
(Required.) Enabling IP multicast routing |
|
(Optional.) Configuring multicast routing and forwarding: · (Optional.) Configuring static multicast routes · (Optional.) Specifying the longest prefix match principle · (Optional.) Configuring multicast load splitting · (Optional.) Configuring a multicast forwarding boundary · (Optional.) Setting the multicast hardware resource mode |
|
|
NOTE: The device can route and forward multicast data only through the primary IP addresses of interfaces, rather than their secondary addresses or unnumbered IP addresses. For more information about primary and secondary IP addresses, and IP unnumbered, see Layer 3—IP Services Configuration Guide. |
Enabling IP multicast routing
Enable IP multicast routing before you configure any Layer 3 multicast functionality on the public network or VPN instance.
To enable IP multicast routing:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable IP multicast routing and enter MRIB view. |
multicast routing [ vpn-instance vpn-instance-name ] |
By default, IP multicast routing is disabled. |
Configuring multicast routing and forwarding
Before you configure multicast routing and forwarding, complete the following tasks:
· Configure a unicast routing protocol so that all devices in the domain can interoperate at the network layer.
· Enable PIM-DM or PIM-SM.
Configuring static multicast routes
To configure a static multicast route for a given multicast source, you can specify an RPF interface or an RPF neighbor for the multicast traffic from that source.
To configure a static multicast route:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Configure a static multicast route. |
ip rpf-route-static [ vpn-instance vpn-instance-name ] source-address { mask-length | mask } { rpf-nbr-address | interface-type interface-number } [ preference preference ] |
By default, no static multicast routes exist. |
|
3. (Optional.) Delete static multicast routes. |
·
Delete a specific static multicast route: ·
Delete all static multicast routes: |
N/A |
Specifying the longest prefix match principle
You can enable the device to use the longest prefix match principle for RPF route selection. For more information about RPF route selection, see "RPF check process."
To specify the longest prefix match principle for RPF route selection:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter MRIB view. |
multicast routing [ vpn-instance vpn-instance-name ] |
N/A |
|
3. Specify the longest prefix match principle for RPF route selection. |
longest-match |
By default, the route preference principle is used. |
Configuring multicast load splitting
You can enable the device to split multiple data flows on a per-source basis or on a per-source-and-group basis. This optimizes the traffic delivery.
To configure multicast load splitting:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter MRIB view. |
multicast routing [ vpn-instance vpn-instance-name ] |
N/A |
|
3. Configure multicast load splitting. |
load-splitting { source | source-group } |
By default, multicast load splitting is disabled. |
Configuring a multicast forwarding boundary
You can configure an interface as a multicast forwarding boundary for a multicast group range. The interface cannot receive or forward multicast packets for the group range.
|
|
TIP: You do not need to enable IP multicast routing before this configuration. |
To configure a multicast forwarding boundary:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter interface view. |
interface interface-type interface-number |
N/A |
|
3. Configure the interface as a multicast forwarding boundary for a multicast group range. |
multicast boundary group-address { mask-length | mask } |
By default, an interface is not a multicast forwarding boundary. |
Setting the multicast hardware resource mode
Multicast hardware resource has the following modes:
· Normal—The switching fabric modules replicate multicast and broadcast traffic to all LPUs. This mode consumes a large amount of bandwidth.
· Enhance—The switching fabric modules replicate multicast traffic only to LPUs that have receivers.
This command is available only for the default MDC. If you set the multicast hardware resource mode to enhance on the default MDC, the multicast feature is not available on non-default MDCs.
For this feature to take effect, you must save the configuration and reboot the device.
To set the multicast hardware resource mode:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Set the multicast hardware resource mode. |
hardware-resource mcast { normal | enhance } |
By default, the multicast hardware resource mode is normal. |
Displaying and maintaining multicast routing and forwarding
|
|
CAUTION: The reset commands might cause multicast data transmission failures. |
Execute display commands in any view and reset commands in user view.
|
Task |
Command |
|
Display multicast replication mode information for switching fabrics. |
display hardware-resource [ mcast ] |
|
Display information about the interfaces maintained by the MRIB. |
display mrib [ vpn-instance vpn-instance-name ] interface [ interface-type interface-number ] |
|
Display multicast boundary information. |
display multicast [ vpn-instance vpn-instance-name ] boundary [ group-address [ mask-length | mask ] ] [ interface interface-type interface-number ] |
|
(In standalone mode.) Display multicast fast forwarding entries. |
display multicast [ vpn-instance vpn-instance-name ] fast-forwarding cache [ source-address | group-address ] * [ slot slot-number [ cpu cpu-number ] ] |
|
(In IRF mode.) Display multicast fast forwarding entries. |
display multicast [ vpn-instance vpn-instance-name ] fast-forwarding cache [ source-address | group-address ] * [ chassis chassis-number slot slot-number [ cpu cpu-number ] ] |
|
(In standalone mode.) Display statistics for multicast forwarding events. |
display multicast [ vpn-instance vpn-instance-name ] forwarding event [ slot slot-number [ cpu cpu-number ] ] |
|
(In IRF mode.) Display statistics for multicast forwarding events. |
display multicast [ vpn-instance vpn-instance-name ] forwarding event [ chassis chassis-number slot slot-number [ cpu cpu-number ] ] |
|
(In standalone mode.) Display multicast forwarding entries. |
display multicast [ vpn-instance vpn-instance-name ] forwarding-table [ source-address [ mask { mask-length | mask } ] | group-address [ mask { mask-length | mask } ] | incoming-interface interface-type interface-number | outgoing-interface { exclude | include | match } interface-type interface-number | slot slot-number [ cpu cpu-number ] | statistics ] * |
|
(In IRF mode.) Display multicast forwarding entries. |
display multicast [ vpn-instance vpn-instance-name ] forwarding-table [ source-address [ mask { mask-length | mask } ] | group-address [ mask { mask-length | mask } ] | chassis chassis-number slot slot-number [ cpu cpu-number ] | incoming-interface interface-type interface-number | outgoing-interface { exclude | include | match } interface-type interface-number | statistics ] * |
|
Display multicast routing entries. |
display multicast [ vpn-instance vpn-instance-name ] routing-table [ source-address [ mask { mask-length | mask } ] | group-address [ mask { mask-length | mask } ] | incoming-interface interface-type interface-number | outgoing-interface { exclude | include | match } interface-type interface-number ] * |
|
Display static multicast routing entries. |
display multicast [ vpn-instance vpn-instance-name ] routing-table static [ source-address { mask-length | mask } ] |
|
Display RPF information for a multicast source. |
display multicast [ vpn-instance vpn-instance-name ] rpf-info source-address [ group-address ] |
|
(In standalone mode.) Clear multicast fast forwarding entries. |
reset multicast [ vpn-instance vpn-instance-name ] fast-forwarding cache { { source-address | group-address } * | all } [ slot slot-number [ cpu cpu-number ] ] |
|
(In IRF mode.) Clear multicast fast forwarding entries. |
reset multicast [ vpn-instance vpn-instance-name ] fast-forwarding cache { { source-address | group-address } * | all } [ chassis chassis-number slot slot-number [ cpu cpu-number ] ] |
|
Clear statistics for multicast forwarding events. |
reset multicast [ vpn-instance vpn-instance-name ] forwarding event |
|
Clear multicast forwarding entries. |
reset multicast [ vpn-instance vpn-instance-name ] forwarding-table { { source-address [ mask { mask-length | mask } ] | group-address [ mask { mask-length | mask } ] | incoming-interface { interface-type interface-number } } * | all } |
|
Clear multicast routing entries. |
reset multicast [ vpn-instance vpn-instance-name ] routing-table { { source-address [ mask { mask-length | mask } ] | group-address [ mask { mask-length | mask } ] | incoming-interface interface-type interface-number } * | all } |
|
|
NOTE: · When you clear a multicast routing entry, the associated multicast forwarding entry is also cleared. · When you clear a multicast forwarding entry, the associated multicast routing entry is also cleared. |
Multicast routing and forwarding configuration examples
Changing an RPF route
Network requirements
As shown in Figure 28:
· PIM-DM runs on the network.
· All switches on the network support multicast.
· Switch A, Switch B and Switch C run OSPF.
· Typically, the receiver host can receive the multicast data from Source through the path: Switch A to Switch B, which is the same as the unicast route.
Configure the switches so that the multicast data from Source travels to the receiver through the path: Switch A to Switch C to Switch B. This is different from the unicast route.
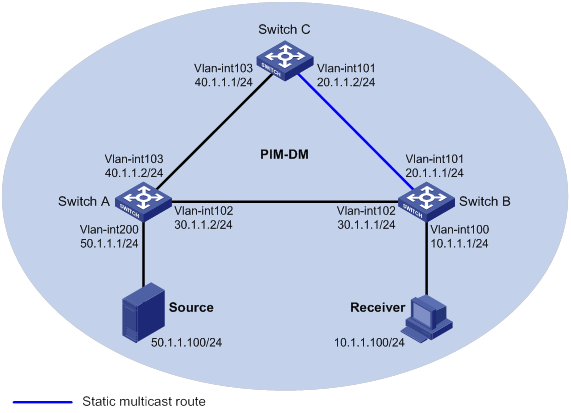
Configuration procedure
1. Assign an IP address and subnet mask for each interface, as shown in Figure 28. (Details not shown.)
2. Configure OSPF on the switches in the PIM-DM domain. (Details not shown.)
3. Enable IP multicast routing, and enable IGMP and PIM-DM:
# On Switch B, enable IP multicast routing.
<SwitchB> system-view
[SwitchB] multicast routing
[SwitchB-mrib] quit
# Enable IGMP on the receiver-side interface (VLAN-interface 100).
[SwitchB] interface vlan-interface 100
[SwitchB-Vlan-interface100] igmp enable
[SwitchB-Vlan-interface100] quit
# Enable PIM-DM on other interfaces.
[SwitchB] interface vlan-interface 101
[SwitchB-Vlan-interface101] pim dm
[SwitchB-Vlan-interface101] quit
[SwitchB] interface vlan-interface 102
[SwitchB-Vlan-interface102] pim dm
[SwitchB-Vlan-interface102] quit
# On Switch A, enable IP multicast routing.
<SwitchA> system-view
[SwitchA] multicast routing
[SwitchA-mrib] quit
# Enable PIM-DM on each interface.
[SwitchA] interface vlan-interface 200
[SwitchA-Vlan-interface200] pim dm
[SwitchA-Vlan-interface200] quit
[SwitchA] interface vlan-interface 102
[SwitchA-Vlan-interface102] pim dm
[SwitchA-Vlan-interface102] quit
[SwitchA] interface vlan-interface 103
[SwitchA-Vlan-interface103] pim dm
[SwitchA-Vlan-interface103] quit
# Enable IP multicast routing and PIM-DM on Switch C in the same way Switch A is configured. (Details not shown.)
4. Display RPF information for Source on Switch B.
[SwitchB] display multicast rpf-info 50.1.1.100
RPF information about source 50.1.1.100:
RPF interface: Vlan-interface102, RPF neighbor: 30.1.1.2
Referenced route/mask: 50.1.1.0/24
Referenced route type: igp
Route selection rule: preference-preferred
Load splitting rule: disable
The output shows that the current RPF route on Switch B is contributed by a unicast routing protocol and the RPF neighbor is Switch A.
5. Configure a static multicast route on Switch B and specify Switch C as its RPF neighbor on the route to Source.
[SwitchB] ip rpf-route-static 50.1.1.100 24 20.1.1.2
Verifying the configuration
# Display RPF information for Source on Switch B.
[SwitchB] display multicast rpf-info 50.1.1.100
RPF information about source 50.1.1.100:
RPF interface: Vlan-interface101, RPF neighbor: 20.1.1.2
Referenced route/mask: 50.1.1.0/24
Referenced route type: multicast static
Route selection rule: preference-preferred
Load splitting rule: disable
The output shows the following information:
· The RPF route on Switch B is the configured static multicast route.
· The RPF neighbor of Switch B is Switch C.
Creating an RPF route
Network requirements
As shown in Figure 29:
· PIM-DM runs on the network.
· All switches on the network support IP multicast.
· Switch B and Switch C run OSPF, and have no unicast routes to Switch A.
· Typically, the receiver host receives the multicast data from Source 1 in the OSPF domain.
Configure the switches so that the receiver host receives multicast data from Source 2, which is outside the OSPF domain.
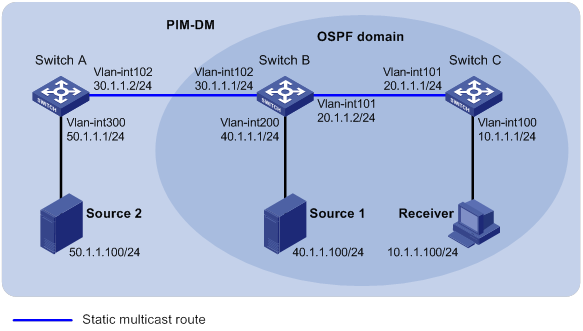
Configuration procedure
1. Assign an IP address and subnet mask for each interface, as shown in Figure 29. (Details not shown.)
2. Configure OSPF on Switch B and Switch C. (Details not shown.)
3. Enable IP multicast routing, and enable IGMP and PIM-DM:
# On Switch C, enable IP multicast routing.
<SwitchC> system-view
[SwitchC] multicast routing
[SwitchC-mrib] quit
# Enable IGMP on the receiver-side interface (VLAN-interface 100).
[SwitchC] interface vlan-interface 100
[SwitchC-Vlan-interface100] igmp enable
[SwitchC-Vlan-interface100] quit
# Enable PIM-DM on VLAN-interface 101.
[SwitchC] interface vlan-interface 101
[SwitchC-Vlan-interface101] pim dm
[SwitchC-Vlan-interface101] quit
# On Switch A, enable IP multicast routing.
<SwitchA> system-view
[SwitchA] multicast routing
[SwitchA-mrib] quit
# Enable PIM-DM on each interface.
[SwitchA] interface vlan-interface 300
[SwitchA-Vlan-interface300] pim dm
[SwitchA-Vlan-interface300] quit
[SwitchA] interface vlan-interface 102
[SwitchA-Vlan-interface102] pim dm
[SwitchA-Vlan-interface102] quit
# Enable IP multicast routing and PIM-DM on Switch B in the same way Switch A is configured. (Details not shown.)
4. Display RPF information for Source 2 on Switch B and Switch C.
[SwitchB] display multicast rpf-info 50.1.1.100
[SwitchC] display multicast rpf-info 50.1.1.100
No output is displayed because no RPF routes to Source 2 exist on Switch B or Switch C.
5. Configure a static multicast route:
# Configure a static multicast route on Switch B and specify Switch A as its RPF neighbor on the route to Source 2.
[SwitchB] ip rpf-route-static 50.1.1.100 24 30.1.1.2
# Configure a static multicast route on Switch C and specify Switch B as its RPF neighbor on the route to Source 2.
[SwitchC] ip rpf-route-static 10.1.1.100 24 20.1.1.2
Verifying the configuration
# Display RPF information for Source 2 on Switch B.
[SwitchB] display multicast rpf-info 50.1.1.100
RPF information about source 50.1.1.100:
RPF interface: Vlan-interface102, RPF neighbor: 30.1.1.2
Referenced route/mask: 50.1.1.0/24
Referenced route type: multicast static
Route selection rule: preference-preferred
Load splitting rule: disable
# Display RPF information for Source 2 on Switch C.
[SwitchC] display multicast rpf-info 50.1.1.100
RPF information about source 50.1.1.100:
RPF interface: Vlan-interface101, RPF neighbor: 20.1.1.2
Referenced route/mask: 50.1.1.0/24
Referenced route type: multicast static
Route selection rule: preference-preferred
Load splitting rule: disable
The output shows that the RPF routes to Source 2 exist on Switch B and Switch C. The routes are the configured static routes.
Troubleshooting multicast routing and forwarding
Static multicast route failure
Symptom
No dynamic routing protocol is enabled on the routers, and the physical status and link layer status of interfaces are both up, but the static multicast route fails.
Solution
To resolve the problem:
1. Use the display multicast routing-table static command to display information about static multicast routes. Verify that the static multicast route has been correctly configured and that the route entry exists in the static multicast routing table.
2. Check the type of interface that connects the static multicast route to the RPF neighbor. If the interface is not a point-to-point interface, be sure to specify the address for the RPF neighbor.
3. If the problem persists, contact H3C Support.
Configuring IGMP
Overview
Internet Group Management Protocol (IGMP) establishes and maintains the multicast group memberships between a Layer 3 multicast device and the hosts on the directly connected subnet.
IGMP has the following versions:
· IGMPv1 (defined by RFC 1112).
· IGMPv2 (defined by RFC 2236).
· IGMPv3 (defined by RFC 3376).
All IGMP versions support the ASM model. IGMPv3 can directly implement the SSM model. IGMPv1 and IGMPv2 must work with the IGMP SSM mapping feature to implement the SSM model. For more information about the ASM and SSM models, see "Multicast overview."
IGMPv1 overview
IGMPv1 manages multicast group memberships based on the query and response mechanism.
All routers that run IGMP on the same subnet can get IGMP membership report messages (called reports) from hosts. However, only one router can act as the IGMP querier to send IGMP query messages (called queries). The querier election mechanism determines which router acts as the IGMP querier on the subnet.
In IGMPv1, the DR elected by the multicast routing protocol (such as PIM) acts as the IGMP querier. For more information about DR, see "Configuring PIM."
Figure 30 IGMP queries and reports
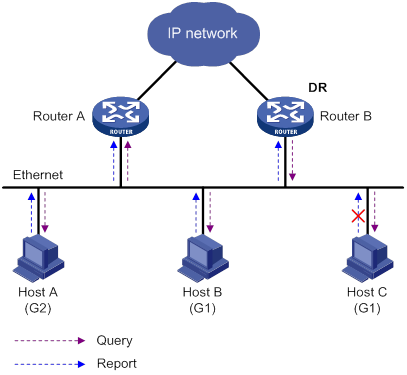
As shown in Figure 30, Host B and Host C are interested in the multicast data addressed to the multicast group G1. Host A is interested in the multicast data addressed to G2. The following process describes how the hosts join the multicast groups and how the IGMP querier (Router B in Figure 30) maintains the multicast group memberships:
1. The hosts send unsolicited IGMP reports to the multicast groups they want to join without having to wait for the IGMP queries.
2. The IGMP querier periodically multicasts IGMP queries (with the destination address of 224.0.0.1) to all hosts and routers on the local subnet.
3. After receiving a query message, the host whose report delay timer expires first sends an IGMP report to multicast group G1 to announce its membership for G1. In this example, Host B sends the report message. After receiving the report from Host B, Host C suppresses its own report for G1.
Because IGMP routers already know that G1 has a minimum of one member, other members do not need to report their memberships. This mechanism, known as the host IGMP report suppression, helps reduce traffic on the local subnet.
4. At the same time, Host A sends a report to the multicast group G2 after receiving a query.
5. Through the query and response process, the IGMP routers (Router A and Router B) determine that the local subnet has members of G1 and G2. The multicast routing protocol (PIM, for example) on the routers generates (*, G1) and (*, G2) multicast forwarding entries, where asterisk (*) represents any multicast source. These entries are the basis for subsequent multicast forwarding.
6. When the multicast data addressed to G1 or G2 reaches an IGMP router, the router looks up the multicast forwarding table. Based on the (*, G1) or (*, G2) entries, the router forwards the multicast data to the local subnet. Then, the receivers on the subnet can receive the data.
IGMPv1 does not define a leave group message (often called a leave message). When an IGMPv1 host is leaving a multicast group, it stops sending reports to that multicast group. If the subnet has no members for a multicast group, the IGMP routers will not receive any report addressed to that multicast group. In this case, the routers clear the information for that multicast group after a period of time.
IGMPv2 enhancements
Backwards-compatible with IGMPv1, IGMPv2 has introduced a querier election mechanism and a leave-group mechanism.
Querier election mechanism
In IGMPv1, the DR elected by the Layer 3 multicast routing protocol (such as PIM) acts as the querier.
IGMPv2 introduced an independent querier election mechanism. The querier election process is as follows:
1. Initially, every IGMPv2 router assumes itself to be the querier. Each router sends IGMP general query messages (called general queries) to all hosts and routers on the local subnet. The destination address is 224.0.0.1.
2. After receiving a general query, every IGMPv2 router compares the source IP address of the query with its own interface address. The router with the lowest IP address becomes the querier. All the other IGMPv2 routers become non-queriers.
3. All the non-queriers start the other querier present timer. If a router receives an IGMP query from the querier before the timer expires, it resets this timer. Otherwise, the router considers that the querier has timed out. In this case, the router initiates a new querier election process.
"Leave group" mechanism
In IGMPv1, when a host leaves a multicast group, it does not send any notification to the multicast routers. The multicast routers determine whether a group has members by using the maximum response time. This adds to the leave latency.
In IGMPv2, when a host is leaving a multicast group, the following process occurs:
1. The host sends a leave message to all routers on the local subnet. The destination address of leave messages is 224.0.0.2.
2. After receiving the leave message, the querier sends a configurable number of IGMP group-specific queries to the group that the host is leaving. Both the destination address field and the group address field of the message are the address of the multicast group that is being queried.
3. One of the remaining members (if any on the subnet) in the group should send a report within the maximum response time advertised in the group-specific queries.
4. If the querier receives a report for the group before the maximum response timer expires, it maintains the memberships for the group. Otherwise, the querier assumes that the local subnet has no member hosts for the group and stops maintaining the memberships for the group.
IGMPv3 enhancements
IGMPv3 is based on and is compatible with IGMPv1 and IGMPv2. It enhances the control capabilities of hosts and the query and report capabilities of IGMP routers.
Enhancements in control capability of hosts
IGMPv3 introduced two source filtering modes (Include and Exclude). These modes allow a host to receive or reject multicast data from the specified multicast sources. When a host joins a multicast group, one of the following occurs:
· If the host expects to receive multicast data from specific sources like S1, S2, …, it sends a report with the Filter-Mode denoted as "Include Sources (S1, S2, …)."
· If the host expects to reject multicast data from specific sources like S1, S2, …, it sends a report with the Filter-Mode denoted as "Exclude Sources (S1, S2, …)."
As shown in Figure 31, the network has two multicast sources: Source 1 (S1) and Source 2 (S2). Both of these sources can send multicast data to the multicast group G. Host B wants to receive the multicast data addressed to G from Source 1 but not from Source 2.
Figure 31 Flow paths of source-and-group-specific multicast traffic
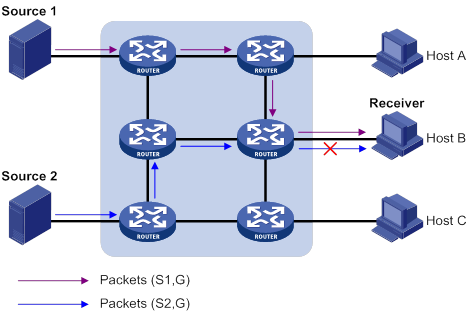
In IGMPv1 or IGMPv2, Host B cannot select multicast sources when it joins the multicast group G. The multicast streams from both Source 1 and Source 2 flow to Host B whether or not it needs them.
In IGMPv3, Host B can explicitly express that it needs to receive multicast data destined to the multicast group G from Source 1 but not from Source 2.
Enhancements in query and report capabilities
IGMPv3 introduces IGMP group-and-source queries and IGMP reports carrying group records.
· Query message carrying the source addresses
IGMPv3 is compatible with IGMPv1 and IGMPv2 and supports IGMP general queries and IGMP group-specific queries. It also introduces IGMP group-and-source-specific queries.
? A general query does not carry a group address or a source address.
? A group-specific query carries a group address, but no source address.
? A group-and-source-specific query carries a group address and one or more source addresses.
· Reports containing multiple group records
Unlike an IGMPv1 or IGMPv2 report, an IGMPv3 report is destined to 224.0.0.22 and contains one or more group records. Each group record contains a multicast group address and a multicast source address list.
Group records include the following categories:
? IS_IN—The current filtering mode is Include. The report sender requests the multicast data only from the sources specified in the Source Address field.
? IS_EX—The current filtering mode is Exclude. The report sender requests the multicast data from any sources except those specified in the Source Address field.
? TO_IN—The filtering mode has changed from Exclude to Include.
? TO_EX—The filtering mode has changed from Include to Exclude.
? ALLOW—The Source Address field contains a list of additional sources from which the receiver wants to obtain data. If the current filtering mode is Include, these sources are added to the multicast source list. If the current filtering mode is Exclude, these sources are deleted from the multicast source list.
? BLOCK—The Source Address field contains a list of the sources from which the receiver no longer wants to obtain data. If the current filtering mode is Include, these sources are deleted from the multicast source list. If the current filtering mode is Exclude, these sources are added to the multicast source list.
IGMP SSM mapping
An IGMPv3 host can explicitly specify multicast sources in its IGMPv3 reports. From the reports, the IGMP router can obtain the multicast source addresses and directly provide the SSM service. However, an IGMPv1 or IGMPv2 host cannot specify multicast sources in its IGMPv1 or IGMPv2 reports.
The IGMP SSM mapping feature enables the IGMP router to provide SSM support for IGMPv1 or IGMPv2 hosts. The router translates (*, G) in IGMPv1 or IGMPv2 reports into (G, INCLUDE, (S1, S2...)) based on the configured IGMP SSM mappings.
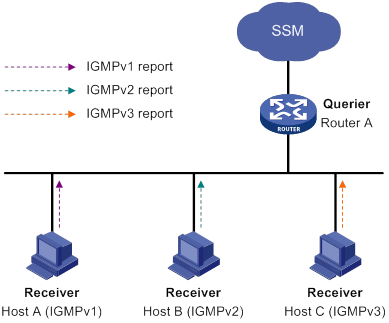
As shown in Figure 32, on an SSM network, Host A, Host B, and Host C run IGMPv1, IGMPv2, and IGMPv3, respectively. To provide the SSM service for Host A and Host B, you must configure the IGMP SSM mapping feature on Router A.
After IGMP SSM mappings are configured, Router A checks the multicast group address G in the received IGMPv1 or IGMPv2 report, and performs the following operations:
· If G is not in the SSM group range, Router A provides the ASM service.
· If G is in the SSM group range but does not match any IGMP SSM mapping, Router A drops the report.
· If G is in the SSM group range and matches IGMP SSM mappings, Router A translates (*, G) in the report into (G, INCLUDE, (S1, S2...)) to provide SSM services.
|
NOTE: The IGMP SSM mapping feature does not process IGMPv3 reports. |
For more information about SSM group ranges, see "Configuring PIM."
IGMP proxying
As shown in Figure 33, in a simple tree-shaped topology, it is not necessary to run multicast routing protocols, such as PIM, on edge devices. Instead, you can configure IGMP proxying on these devices. With IGMP proxying configured, the edge device acts as an IGMP proxy:
· For the upstream IGMP querier, the IGMP proxy device acts as a host.
· For the downstream receiver hosts, the IGMP proxy device acts as an IGMP querier.
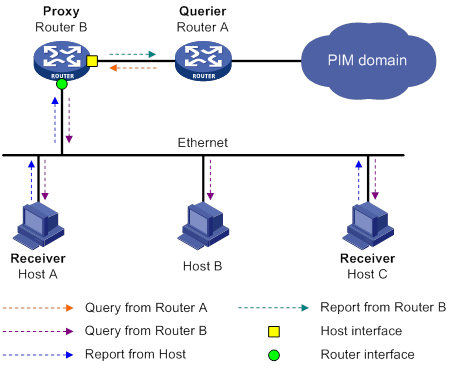
The following types of interfaces are defined in IGMP proxying:
· Host interface—An interface that is in the direction toward the root of the multicast forwarding tree. A host interface acts as a receiver host that is running IGMP. IGMP proxying must be enabled on this interface. This interface is also called the "proxy interface."
· Router interface—An interface that is in the direction toward the leaf of the multicast forwarding tree. A router interface acts as a router that is running IGMP. IGMP must be configured on this interface.
An IGMP proxy device maintains a group membership database, which stores the group memberships on all the router interfaces. The host interfaces and router interfaces perform actions based on this membership database.
· The host interfaces respond to queries according to the membership database or send join/leave messages when the database changes.
· The router interfaces participate in the querier election, send queries, and maintain memberships based on received IGMP reports.
IGMP support for VPNs
IGMP maintains group memberships on a per-interface basis. After receiving an IGMP message on an interface, IGMP processes the packet within the VPN to which the interface belongs. IGMP only communicates with other multicast protocols within the same VPN instance.
Protocols and standards
· RFC 1112, Host Extensions for IP Multicasting
· RFC 2236, Internet Group Management Protocol, Version 2
· RFC 3376, Internet Group Management Protocol, Version 3
IGMP configuration task list
|
Tasks at a glance |
|
Configuring basic IGMP features: · (Required.) Enabling IGMP · (Optional.) Specifying an IGMP version · (Optional.) Configuring a static group member · (Optional.) Configuring a multicast group policy |
|
· (Optional.) Configuring IGMP query and response parameters · (Optional.) Enabling fast-leave processing |
|
(Optional.) Configuring IGMP SSM mappin gs |
|
· (Optional.) Enabling IGMP proxying · (Optional.) Enabling multicast forwarding on a non-querier interface · (Optional.) Configuring multicast load splitting on an IGMP proxy |
|
(Optional.) Enabling IGMP NSR |
Configuring basic IGMP features
Before you configure basic IGMP features, complete the following tasks:
· Configure any unicast routing protocol so that all devices can interoperate at the network layer.
· Configure PIM.
· Determine the IGMP version.
· Determine the multicast group and multicast source addresses for static group member configuration.
· Determine the ACL to be used in the multicast group policy.
Enabling IGMP
Enable IGMP on the interface where the multicast group memberships are established and maintained.
To enable IGMP:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable IP multicast routing and enter MRIB view. |
multicast routing [ vpn-instance vpn-instance-name ] |
By default, IP multicast routing is disabled. |
|
3. Return to system view. |
quit |
N/A |
|
4. Enter interface view. |
interface interface-type interface-number |
N/A |
|
5. Enable IGMP. |
igmp enable |
By default, IGMP is disabled. |
Specifying an IGMP version
For IGMP to operate correctly, specify the same IGMP version for all routers on the same subnet.
To specify an IGMP version:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter interface view. |
interface interface-type interface-number |
N/A |
|
3. Specify an IGMP version on the interface. |
igmp version version-number |
The default setting is 2. |
Configuring a static group member
You can configure an interface as a static group member of a multicast group. Then, the interface can always receive multicast data addressed to the specified multicast group.
A static group member does not respond to IGMP queries. When you complete or cancel this configuration on an interface, the interface does not send an unsolicited IGMP report or leave message.
Configuration restrictions and guidelines
The interface to be configured as a static group member has the following restrictions:
· If the interface is IGMP and PIM-SM enabled, it must be a PIM-SM DR.
· If the interface is IGMP enabled but not PIM-SM enabled, it must be an IGMP querier.
For more information about PIM-SM and DR, see "Configuring PIM."
Configuration procedure
To configure a static group member:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter interface view. |
interface interface-type interface-number |
N/A |
|
3. Configure the interface as a static group member. |
igmp static-group group-address [ source source-address ] |
By default, an interface is not a static group member of any multicast groups. |
Configuring a multicast group policy
This feature enables an interface to filter IGMP reports by using an ACL that specifies multicast groups and the optional sources. It is used to control the multicast groups that the hosts attached to an interface can join.
This configuration does not take effect on static group members, because static group members do not send IGMP reports.
To configure a multicast group policy:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter interface view. |
interface interface-type interface-number |
N/A |
|
3. Configure a multicast group policy. |
igmp group-policy ipv4-acl-number [ version-number ] |
By default, no IGMP multicast group policy exists on an interface. Hosts attached to the interface can join any multicast groups. |
Adjusting IGMP performance
Before adjusting IGMP performance, complete the following tasks:
· Configure any unicast routing protocol so that all devices can interoperate at the network layer.
· Configure basic IGMP features.
Configuring IGMP query and response parameters
The following are IGMP query and response parameters:
· IGMP querier's robustness variable—Number of times for retransmitting IGMP queries in case of packet loss. A higher robustness variable makes the IGMP querier more robust, but increases the timeout time for multicast groups.
· IGMP startup query interval—Interval at which an IGMP querier sends IGMP general queries at startup.
· IGMP startup query count—Number of IGMP general queries that an IGMP querier sends at startup.
· IGMP general query interval—Interval at which an IGMP querier sends IGMP general queries to check for multicast group members on the network.
· IGMP last member query interval—In IGMPv2, it sets the interval at which a querier sends group-specific queries after receiving a leave message. In IGMPv3, it sets the interval at which a querier sends group-and-source-specific queries after receiving a report that changes multicast source and group mappings.
· IGMP last member query count—In IGMPv2, it sets the number of group-specific queries that a querier sends after receiving a leave message. In IGMPv3, it sets the number of group-and-source-specific queries that a querier sends after receiving a report that changes multicast source and group mappings.
· IGMP maximum response time—Maximum time before a receiver responds with a report to an IGMP general query. This per-group timer is initialized to a random value in the range of 0 to the maximum response time specified in the IGMP query. When the timer value for a group decreases to 0, the receiver sends an IGMP report to the group.
· IGMP other querier present timer—Lifetime for an IGMP querier after a non-querier receives an IGMP general query. If the non-querier does not receive a new query when this timer expires, the non-querier considers that the querier has failed and starts a new querier election.
Configuration restrictions and guidelines
When you configure the IGMP query and response parameters, follow these restrictions and guidelines:
· You can configure the IGMP query and response parameters globally for all interfaces in IGMP view or for an interface in interface view. For an interface, the interface-specific configuration takes priority over the global configuration.
· To avoid frequent IGMP querier changes, set the IGMP other querier present timer greater than the IGMP general query interval. In addition, configure the same IGMP other querier present timer for all IGMP routers on the same subnet.
· To avoid mistakenly deleting multicast receivers, set the IGMP general query interval greater than the maximum response time for IGMP general queries.
· To speed up the response to IGMP queries and avoid simultaneous timer expirations that cause IGMP report traffic bursts, set an appropriate maximum response time.
? For IGMP general queries, the maximum response time is set by the max-response-time command.
? For IGMP group-specific queries and IGMP group-and-source-specific queries, the maximum response time equals the IGMP last member query interval.
· The following configurations take effect only on the devices that run IGMPv2 and IGMPv3:
? Maximum response time for IGMP general queries.
? IGMP last member query interval.
? IGMP last member query count.
? IGMP other querier present interval.
Configuring the IGMP query and response parameters globally
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter IGMP view. |
igmp [ vpn-instance vpn-instance-name ] |
N/A |
|
3. Set the IGMP querier's robustness variable. |
robust-count count |
By default, the IGMP querier's robustness variable is 2. |
|
4. Set the IGMP startup query interval. |
startup-query-interval interval |
By default, the IGMP startup query interval equals one quarter of the IGMP general query interval. |
|
5. Set the IGMP startup query count. |
startup-query-count count |
By default, the IGMP startup query count equals the IGMP querier's robustness variable. |
|
6. Set the IGMP general query interval. |
query-interval interval |
By default, the IGMP general query interval is 125 seconds. |
|
7. Set the IGMP last member query interval. |
last-member-query-interval interval |
By default, the IGMP last member query interval is 1 second. |
|
8. Set the IGMP last member query count. |
last-member-query-count count |
By default, the IGMP last member query count equals the IGMP querier's robustness variable. |
|
9. Set the maximum response time for IGMP general queries. |
max-response-time time |
By default, the maximum response time for IGMP general queries is 10 seconds. |
|
10. Set the IGMP other querier present timer. |
other-querier-present-interval interval |
By default, the IGMP other querier present timer is calculated by
using the following formula: |
Configuring the IGMP query and response parameters on an interface
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter interface view. |
interface interface-type interface-number |
N/A |
|
3. Set the IGMP querier's robustness variable. |
igmp robust-count count |
By default, the IGMP querier's robustness variable is 2. |
|
4. Set the IGMP startup query interval. |
igmp startup-query-interval interval |
By default, the IGMP startup query interval equals one quarter of the IGMP general query interval. |
|
5. Set the IGMP startup query count. |
igmp startup-query-count count |
By default, the IGMP startup query count equals the IGMP querier's robustness variable. |
|
6. Set the IGMP general query interval. |
igmp query-interval interval |
By default, the IGMP general query interval is 125 seconds. |
|
7. Set the IGMP last member query interval. |
igmp last-member-query-interval interval |
By default, the IGMP last member query interval is 1 second. |
|
8. Set the IGMP last member query count. |
igmp last-member-query-count count |
By default, the IGMP last member query count equals the IGMP querier's robustness variable. |
|
9. Set the maximum response time for IGMP general queries. |
igmp max-response-time time |
By default, the maximum response time for IGMP general queries is 10 seconds. |
|
10. Set the IGMP other querier present timer. |
igmp other-querier-present-interval interval |
By default, the IGMP other querier present timer is calculated by
using the following formula: |
Enabling fast-leave processing
This feature enables an IGMP querier to send leave notifications to the upstream without sending group-specific or group-and-source-specific queries after receiving a leave message. Use this feature to reduce leave latency and to preserve the network bandwidth.
The fast-leave processing configuration takes effect only when the device runs IGMPv2 or IGMPv3.
To enable fast-leave processing:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter interface view. |
interface interface-type interface-number |
N/A |
|
3. Enable fast-leave processing. |
igmp fast-leave [ group-policy ipv4-acl-number ] |
By default, fast-leave processing is disabled. |
Configuring IGMP SSM mappings
This feature enables the device to provide SSM services for IGMPv1 or IGMPv2 hosts.
This feature does not process IGMPv3 messages. Enable IGMPv3 on the receiver-side interface to ensure that IGMPv3 reports can be processed.
Configuration prerequisites
Before you configure IGMP SSM mappings, complete the following tasks:
· Configure any unicast routing protocol so that all devices in the domain can interoperate at the network layer.
· Configure basic IGMP features.
Configuration procedure
To configure an IGMP SSM mapping:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter IGMP view. |
igmp [ vpn-instance vpn-instance-name ] |
N/A |
|
3. Configure an IGMP SSM mapping. |
ssm-mapping source-address ipv4-acl-number |
By default, no IGMP SSM mappings exist. |
Configuring IGMP proxying
This section describes how to configure IGMP proxying.
Configuration prerequisites
Before you configure the IGMP proxying feature, complete the following tasks:
1. Configure a unicast routing protocol so that all devices in the domain can interoperate at the network layer.
2. Determine the router interfaces and host interfaces based on the network topology.
3. Enable IGMP on the router interfaces.
Enabling IGMP proxying
When you enable IGMP proxying, follow these restrictions and guidelines:
· You must enable IGMP proxying on the receiver-side interfaces.
· On an interface enabled with IGMP proxying, only the igmp version command takes effect and other IGMP commands do not take effect.
· If you enable both IGMP proxying and a multicast routing protocol (such as PIM or MSDP) on the same device, the multicast routing protocol does not take effect.
In IGMPv1, the DR is elected by PIM and acts as the IGMP querier. Because PIM does not take effect on a proxy device, a router interface running IGMPv1 cannot be elected as the DR. To ensure that the downstream receiver hosts on the router interface can receive multicast data, you must enable multicast forwarding on the interface. For more information, see "Enabling multicast forwarding on a non-querier interface."
To enable IGMP proxying:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable IP multicast routing and enter MRIB view. |
multicast routing [ vpn-instance vpn-instance-name ] |
By default, IP multicast routing is disabled. |
|
3. Return to system view. |
quit |
N/A |
|
4. Enter interface view. |
interface interface-type interface-number |
N/A |
|
5. Enable IGMP proxying. |
igmp proxying enable |
By default, IGMP proxying is disabled. |
Enabling multicast forwarding on a non-querier interface
Typically, only IGMP queriers can forward multicast traffic and non-queriers cannot. This prevents multicast data from being repeatedly forwarded. If a router interface on an IGMP proxy device failed in the querier election, enable multicast forwarding on the interface to forward multicast data to attached receiver hosts.
Configuration restrictions and guidelines
A shared-media network might have multiple MLD proxies, including one proxy acting as a querier. To avoid duplicate multicast traffic, do not enable multicast forwarding on any of the non-querier MLD proxies for the network.
Configuration procedure
To enable multicast forwarding on a non-querier interface:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter interface view. |
interface interface-type interface-number |
N/A |
|
3. Enable multicast forwarding on the interface. |
igmp proxy forwarding |
By default, multicast forwarding is disabled on a non-querier interface. |
Configuring multicast load splitting on an IGMP proxy
This feature enables all proxy interfaces on an IGMP proxy device to share multicast traffic on a per-group basis.
To enable multicast load splitting on an IGMP proxy device:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter IGMP view. |
igmp [ vpn-instance vpn-instance-name ] |
N/A |
|
3. Enable multicast load splitting. |
proxy multipath |
By default, multicast load splitting is disabled, and only the proxy interface with the highest IP address on the IGMP proxy device forwards multicast data. |
Enabling IGMP NSR
This feature backs up information about IGMP interfaces and IGMP multicast groups to the standby process. The device recovers the information without cooperation of other devices when an active/standby switchover occurs. Use this feature to prevent an active/standby switchover from affecting the multicast service.
To enable IGMP NSR:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable IGMP NSR. |
igmp non-stop-routing |
By default, IGMP NSR is disabled. |
Displaying and maintaining IGMP
|
|
CAUTION: The reset igmp group command might cause multicast data transmission failures. |
Execute display commands in any view and reset commands in user view.
|
Task |
Command |
|
Display information about IGMP multicast groups. |
display igmp [ vpn-instance vpn-instance-name ] group [ group-address | interface interface-type interface-number ] [ static | verbose ] |
|
Display IGMP information for interfaces. |
display igmp [ vpn-instance vpn-instance-name ] interface [ interface-type interface-number ] [ host | proxy ] [ verbose ] |
|
Display multicast group membership information maintained by the IGMP proxy. |
display igmp [ vpn-instance vpn-instance-name ] proxy group [ group-address | interface interface-type interface-number ] [ verbose ] |
|
Display multicast routing entries maintained by the IGMP proxy. |
display igmp [ vpn-instance vpn-instance-name ] proxy routing-table [ source-address [ mask { mask-length | mask } ] | group-address [ mask { mask-length | mask } ] ] * [ verbose ] |
|
Display IGMP SSM mappings. |
display igmp [ vpn-instance vpn-instance-name ] ssm-mapping group-address |
|
Clear dynamic IGMP multicast group entries. |
reset igmp [ vpn-instance vpn-instance-name ] group { all | interface interface-type interface-number { all | group-address [ mask { mask | mask-length } ] [ source-address [ mask { mask | mask-length } ] ] } } |
IGMP configuration examples
This section provides examples of configuring IGMP on switches.
Basic IGMP features configuration example
Network requirements
As shown in Figure 34:
· OSPF and PIM-DM run on the network.
· VOD streams are sent to receiver hosts in multicast. Receiver hosts of different organizations form stub networks N1 and N2. Host A and Host C are receiver hosts in N1 and N2, respectively.
· IGMPv2 runs between Switch A and N1, and between the other two switches and N2. Switch A acts as the IGMP querier in N1. Switch B acts as the IGMP querier in N2 because it has a lower IP address.
Configure the routers to meet the following requirements:
· The hosts in N1 can join only multicast group 224.1.1.1.
· The hosts in N2 can join any multicast groups.
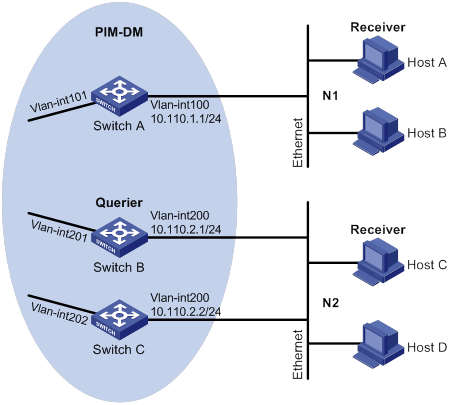
Configuration procedure
1. Assign an IP address and subnet mask to each interface, as shown in Figure 34. (Details not shown.)
2. Configure OSPF on the switches in the PIM-DM domain. (Details not shown.)
3. Enable IP multicast routing, IGMP, and PIM-DM:
# On Switch A, enable IP multicast routing.
<SwitchA> system-view
[SwitchA] multicast routing
[SwitchA-mrib] quit
# Enable IGMP on VLAN-interface 100.
[SwitchA] interface vlan-interface 100
[SwitchA-Vlan-interface100] igmp enable
[SwitchA-Vlan-interface100] quit
# Enable PIM-DM on VLAN-interface 101.
[SwitchA] interface vlan-interface 101
[SwitchA-Vlan-interface101] pim dm
[SwitchA-Vlan-interface101] quit
# On Switch B, enable IP multicast routing.
<SwitchB> system-view
[SwitchB] multicast routing
[SwitchB-mrib] quit
# Enable IGMP on VLAN-interface 200.
[SwitchB] interface vlan-interface 200
[SwitchB-Vlan-interface200] igmp enable
[SwitchB-Vlan-interface200] quit
# Enable PIM-DM on VLAN-interface 201.
[SwitchB] interface vlan-interface 201
[SwitchB-Vlan-interface201] pim dm
[SwitchB-Vlan-interface201] quit
# On Switch C, enable IP multicast routing.
<SwitchC> system-view
[SwitchC] multicast routing
[SwitchC-mrib] quit
# Enable IGMP on VLAN-interface 200.
[SwitchC] interface vlan-interface 200
[SwitchC-Vlan-interface200] igmp enable
[SwitchC-Vlan-interface200] quit
# Enable PIM-DM on VLAN-interface 202.
[SwitchC] interface vlan-interface 202
[SwitchC-Vlan-interface202] pim dm
[SwitchC-Vlan-interface202] quit
4. Configure a multicast group policy on Switch A so that hosts connected to VLAN-interface 100 can join only multicast group 224.1.1.1.
[SwitchA] acl basic 2001
[SwitchA-acl-ipv4-basic-2001] rule permit source 224.1.1.1 0
[SwitchA-acl-ipv4-basic-2001] quit
[SwitchA] interface vlan-interface 100
[SwitchA-Vlan-interface100] igmp group-policy 2001
[SwitchA-Vlan-interface100] quit
Verifying the configuration
# Display IGMP information for VLAN-interface 200 on Switch B.
[SwitchB] display igmp interface vlan-interface 200
Vlan-interface200(10.110.2.1):
IGMP is enabled.
IGMP version: 2
Query interval for IGMP: 125s
Other querier present time for IGMP: 255s
Maximum query response time for IGMP: 10s
Querier for IGMP: 10.110.2.1 (This router)
IGMP groups reported in total: 1
IGMP SSM mapping configuration example
Network requirements
As shown in Figure 35:
· OSPF runs on the network.
· The PIM-SM domain uses both the ASM model and SSM model for multicast delivery. VLAN-interface 104 on Switch D acts as the C-BSR and C-RP. The SSM group range is 232.1.1.0/24.
· IGMPv3 runs on VLAN-interface 400 of Switch D. The receiver host runs IGMPv2, and does not support IGMPv3. The receiver host cannot specify multicast sources in its membership reports.
· Source 1, Source 2, and Source 3 send multicast packets to multicast groups in the SSM group range 232.1.1.0/24.
Configure the IGMP SSM mapping feature on Switch D so that the receiver host can receive multicast data only from Source 1 and Source 3.
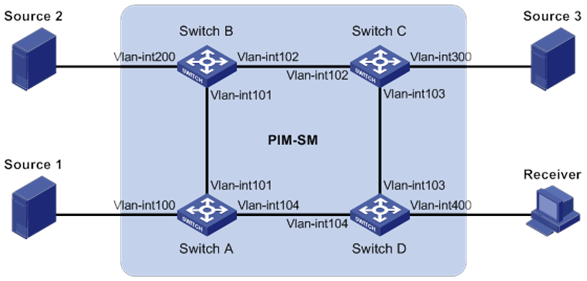
Table 6 Interface and IP address assignment
|
Device |
Interface |
IP address |
Device |
Interface |
IP address |
|
Source 1 |
— |
133.133.1.1/24 |
Source 3 |
— |
133.133.3.1/24 |
|
Source 2 |
— |
133.133.2.1/24 |
Receiver |
— |
133.133.4.1/24 |
|
Switch A |
Vlan-int100 |
133.133.1.2/24 |
Switch C |
Vlan-int300 |
133.133.3.2/24 |
|
Switch A |
Vlan-int101 |
192.168.1.1/24 |
Switch C |
Vlan-int103 |
192.168.3.1/24 |
|
Switch A |
Vlan-int104 |
192.168.4.2/24 |
Switch C |
Vlan-int102 |
192.168.2.2/24 |
|
Switch B |
Vlan-int200 |
133.133.2.2/24 |
Switch D |
Vlan-int400 |
133.133.4.2/24 |
|
Switch B |
Vlan-int101 |
192.168.1.2/24 |
Switch D |
Vlan-int103 |
192.168.3.2/24 |
|
Switch B |
Vlan-int102 |
192.168.2.1/24 |
Switch D |
Vlan-int104 |
192.168.4.1/24 |
Configuration procedure
1. Assign an IP address and subnet mask to each interface, as shown in Figure 35. (Details not shown.)
2. Configure OSPF on the switches in the PIM-SM domain. (Details not shown.)
3. Enable IP multicast routing, PIM-SM, and IGMP:
# On Switch D, enable IP multicast routing.
<SwitchD> system-view
[SwitchD] multicast routing
[SwitchD-mrib] quit
# Enable IGMPv3 on the receiver-side interface (VLAN-interface 400).
[SwitchD] interface vlan-interface 400
[SwitchD-Vlan-interface400] igmp enable
[SwitchD-Vlan-interface400] igmp version 3
[SwitchD-Vlan-interface400] quit
# Enable PIM-SM on the other interfaces.
[SwitchD] interface vlan-interface 103
[SwitchD-Vlan-interface103] pim sm
[SwitchD-Vlan-interface103] quit
[SwitchD] interface vlan-interface 104
[SwitchD-Vlan-interface104] pim sm
[SwitchD-Vlan-interface104] quit
# On Switch A, enable IP multicast routing.
<SwitchA> system-view
[SwitchA] multicast routing
[SwitchA-mrib] quit
# Enable PIM-SM on each interface.
[SwitchA] interface vlan-interface 100
[SwitchA-Vlan-interface100] pim sm
[SwitchA-Vlan-interface100] quit
[SwitchA] interface vlan-interface 101
[SwitchA-Vlan-interface101] pim sm
[SwitchA-Vlan-interface101] quit
[SwitchA] interface vlan-interface 104
[SwitchA-Vlan-interface104] pim sm
[SwitchA-Vlan-interface104] quit
# Configure Switch B and Switch C in the same way Switch A is configured. (Details not shown.)
4. On Switch D, configure VLAN-interface 104 as a C-BSR and a C-RP.
[SwitchD] pim
[SwitchD-pim] c-bsr 192.168.4.1
[SwitchD-pim] c-rp 192.168.4.1
[SwitchD-pim] quit
5. Configure the SSM group range:
# On Switch D, specify 232.1.1.0/24 as the SSM group range.
[SwitchD] acl basic 2000
[SwitchD-acl-ipv4-basic-2000] rule permit source 232.1.1.0 0.0.0.255
[SwitchD-acl-ipv4-basic-2000] quit
[SwitchD] pim
[SwitchD-pim] ssm-policy 2000
[SwitchD-pim] quit
# Configure the SSM group range on Switch A, Switch B, and Switch C in the same way Switch D is configured. (Details not shown.)
6. Configure IGMP SSM mappings on Switch D.
[SwitchD] igmp
[SwitchD-igmp] ssm-mapping 133.133.1.1 2000
[SwitchD-igmp] ssm-mapping 133.133.3.1 2000
[SwitchD-igmp] quit
Verifying the configuration
# Display IGMP SSM mappings for multicast group 232.1.1.1 on Switch D.
[SwitchD] display igmp ssm-mapping 232.1.1.1
Group: 232.1.1.1
Source list:
133.133.1.1
133.133.3.1
# On Switch D, display information about IGMP multicast groups that hosts have dynamically joined.
[SwitchD] display igmp group
IGMP groups in total: 1
Vlan-interface400(133.133.4.2):
IGMP groups reported in total: 1
Group address Last reporter Uptime Expires
232.1.1.1 133.133.4.1 00:02:04 off
# Display PIM routing entries on Switch D.
[SwitchD] display pim routing-table
Total 0 (*, G) entry; 2 (S, G) entry
(133.133.1.1, 232.1.1.1)
RP: 192.168.4.1
Protocol: pim-ssm, Flag:
UpTime: 00:13:25
Upstream interface: Vlan-interface104
Upstream neighbor: 192.168.4.2
RPF prime neighbor: 192.168.4.2
Downstream interface(s) information:
Total number of downstreams: 1
1: Vlan-interface400
Protocol: igmp, UpTime: 00:13:25, Expires: -
(133.133.3.1, 232.1.1.1)
RP: 192.168.4.1
Protocol: pim-ssm, Flag:
UpTime: 00:13:25
Upstream interface: Vlan-interface103
Upstream neighbor: 192.168.3.1
RPF prime neighbor: 192.168.3.1
Downstream interface(s) information:
Total number of downstreams: 1
1: Vlan-interface400
Protocol: igmp, UpTime: 00:13:25, Expires: -
IGMP proxying configuration example
Network requirements
As shown in Figure 36:
· PIM-DM runs on the core network.
· Host A and Host C on the stub network receive VOD information sent to multicast group 224.1.1.1.
Configure the IGMP proxying feature on Switch B so that Switch B can maintain group memberships and forward multicast traffic without running PIM-DM.
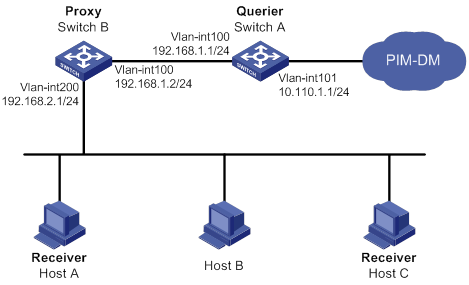
Configuration procedure
1. Assign an IP address and subnet mask to each interface, as shown in Figure 36. (Details not shown.)
2. Enable IP multicast routing, PIM-DM, IGMP, and IGMP proxying:
# On Switch A, enable IP multicast routing.
<SwitchA> system-view
[SwitchA] multicast routing
[SwitchA-mrib] quit
# Enable PIM-DM on VLAN-interface 101.
[SwitchA] interface vlan-interface 101
[SwitchA-Vlan-interface101] pim dm
[SwitchA-Vlan-interface101] quit
# Enable IGMP on VLAN-interface 100.
[SwitchA] interface vlan-interface 100
[SwitchA-Vlan-interface100] igmp enable
[SwitchA-Vlan-interface100] quit
# On Switch B, enable IP multicast routing.
<SwitchB> system-view
[SwitchB] multicast routing
[SwitchB-mrib] quit
# Enable IGMP proxying on VLAN-interface 100.
[SwitchB] interface vlan-interface 100
[SwitchB-Vlan-interface100] igmp proxy enable
[SwitchB-Vlan-interface100] quit
# Enable IGMP on VLAN-interface 200.
[SwitchB] interface vlan-interface 200
[SwitchB-Vlan-interface200] igmp enable
[SwitchB-Vlan-interface200] quit
Verifying the configuration
# Display multicast group membership information maintained by the IGMP proxy on Switch B.
[SwitchB] display igmp proxy group
IGMP proxy group records in total: 1
Vlan-interface100(192.168.1.2):
IGMP proxy group records in total: 1
Group address Member state Expires
224.1.1.1 Delay 00:00:02
Troubleshooting IGMP
No membership information on the receiver-side router
Symptom
When a host sends a report for joining multicast group G, no membership information of multicast group G exists on the router closest to that host.
Solution
To resolve the problem:
1. Use the display igmp interface command to verify that the networking, interface connection, and IP address configuration are correct.
2. Use the display current-configuration command to verify that multicast routing is enabled. If it is not enabled, use the multicast routing command in system view to enable IP multicast routing. In addition, verify that IGMP is enabled on the associated interfaces.
3. Use the display igmp interface command to verify that the IGMP version on the interface is lower than that on the host.
4. Use the display current-configuration interface command to verify that no multicast group policies have been configured to filter IGMP reports for multicast group G.
5. If the problem persists, contact H3C Support.
Inconsistent membership information on the routers on the same subnet
Symptom
Different memberships are maintained on different IGMP routers on the same subnet.
Solution
To resolve the problem:
1. Use the display current-configuration command to verify the IGMP information on the interfaces. Make sure the routers on the subnet have the same IGMP settings on their interfaces.
2. Use the display igmp interface command on all routers on the same subnet to verify the IGMP-related timer settings. Make sure the settings are consistent on all the routers.
3. Use the display igmp interface command to verify that all routers on the same subnet are running the same IGMP version.
4. If the problem persists, contact H3C Support.
Configuring PIM
Overview
Protocol Independent Multicast (PIM) provides IP multicast forwarding by leveraging unicast static routes or unicast routing tables generated by any unicast routing protocol, such as RIP, OSPF, IS-IS, or BGP. PIM uses the underlying unicast routing to generate a multicast routing table without relying on any particular unicast routing protocol.
PIM uses the RPF mechanism to implement multicast forwarding. When a multicast packet arrives on an interface of the device, it undergoes an RPF check. If the RPF check succeeds, the device creates a multicast routing entry and forwards the packet. If the RPF check fails, the device discards the packet. For more information about RPF, see "Configuring multicast routing and forwarding."
Based on the implementation mechanism, PIM includes the following categories:
· Protocol Independent Multicast–Dense Mode (PIM-DM)
· Protocol Independent Multicast–Sparse Mode (PIM-SM)
· Protocol Independent Multicast Source-Specific Multicast (PIM-SSM)
In this document, a PIM domain refers to a network composed of PIM routers.
PIM-DM overview
PIM-DM uses the push mode for multicast forwarding, and is suitable for small-sized networks with densely distributed multicast members.
PIM-DM assumes that all downstream nodes want to receive multicast data from a source, so multicast data is flooded to all downstream nodes on the network. Branches without downstream receivers are pruned from the forwarding trees. When a pruned branch has new receivers, the graft mechanism turns the pruned branch into a forwarding branch.
In PIM-DM, the multicast forwarding paths for a multicast group constitutes a forwarding tree. The forwarding tree is rooted at the multicast source and has multicast group members as its "leaves." Because the forwarding tree consists of the shortest paths from the multicast source to the receivers, it is also called a "shortest path tree (SPT)."
Neighbor discovery
In a PIM domain, each PIM interface on a router periodically multicasts PIM hello messages to all other PIM routers (identified by the address 224.0.0.13) on the local subnet. Through the exchanging of hello messages, all PIM routers on the subnet determine their PIM neighbors, maintain PIM neighboring relationship with other routers, and build and maintain SPTs.
SPT building
The process of building an SPT is the flood-and-prune process:
1. In a PIM-DM domain, the multicast data from the multicast source S to the multicast group G is flooded throughout the domain. A router performs an RPF check on the multicast data. If the RPF check succeeds, the router creates an (S, G) entry and forwards the data to all downstream nodes on the network. In the flooding process, all the routers in the PIM-DM domain create the (S, G) entry.
2. The nodes without downstream receivers are pruned. A router that has no downstream receivers multicasts a prune message to all PIM routers on the subnet. When an upstream node receives the prune message, it removes the receiving interface from the (S, G) entry. In this way, the upstream stream node stops forwarding subsequent packets addressed to that multicast group down to this node.
|
|
NOTE: An (S, G) entry contains a multicast source address S, a multicast group address G, an outgoing interface list, and an incoming interface. |
A prune process is initiated by a leaf router. As shown in Figure 37, the router interface that does not have any downstream receivers initiates a prune process by sending a prune message toward the multicast source. This prune process goes on until only necessary branches are left in the PIM-DM domain, and these necessary branches constitute an SPT.
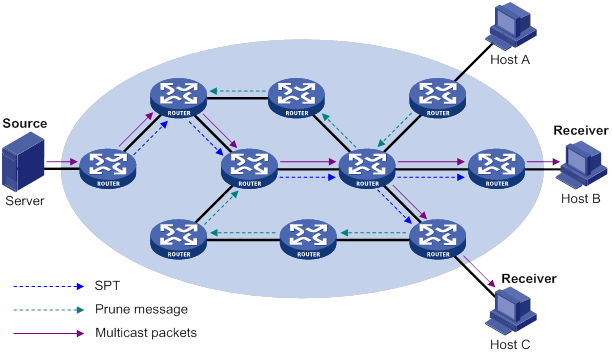
The pruned state of a branch has a finite holdtime timer. When the timer expires, multicast data is again forwarded to the pruned branch. The flood-and-prune cycle takes place periodically to maintain the forwarding branches.
Graft
A previously pruned branch might have new downstream receivers. To reduce the latency for resuming the forwarding capability of this branch, a graft mechanism is used as follows:
1. The node that needs to receive the multicast data sends a graft message to its upstream node, telling it to rejoin the SPT.
2. After receiving this graft message on an interface, the upstream node adds the receiving interface to the outgoing interface list of the (S, G) entry. It also sends a graft-ack message to the graft sender.
3. If the graft sender receives a graft-ack message, the graft process finishes. Otherwise, the graft sender continues to send graft messages at a graft retry interval until it receives an acknowledgment from its upstream node.
Assert
On a subnet with more than one multicast router, the assert mechanism shuts off duplicate multicast flows to the network. It does this by electing a unique multicast forwarder for the subnet.
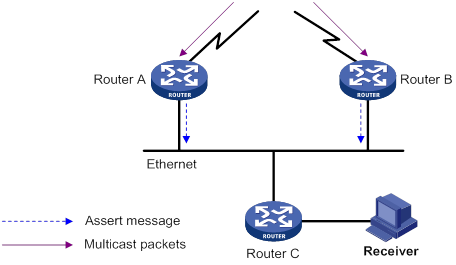
As shown in Figure 38, after Router A and Router B receive an (S, G) packet from the upstream node, they both forward the packet to the local subnet. As a result, the downstream node Router C receives two identical multicast packets. In addition, both Router A and Router B, on their downstream interfaces, receive a duplicate packet forwarded by the other. After detecting this condition, both routers send an assert message to all PIM routers (224.0.0.13) on the local subnet through the interface that received the packet. The assert message contains the multicast source address (S), the multicast group address (G), and the metric preference and metric of the unicast route/MBGP route/static multicast route to the multicast source. By comparing these parameters, either Router A or Router B becomes the unique forwarder of the subsequent (S, G) packets on the shared-media LAN. The comparison process is as follows:
1. The router with a higher metric preference to the multicast source wins.
2. If both routers have the same metric preference, the router with a smaller metric wins.
3. If both routers have the same metric, the router with a higher IP address on the downstream interface wins.
PIM-SM overview
PIM-DM uses the flood-and-prune cycles to build SPTs for multicast data forwarding. Although an SPT has the shortest paths from the multicast source to the receivers, it is built with a low efficiency. Therefore, PIM-DM is not suitable for large and medium-sized networks.
PIM-SM uses the pull mode for multicast forwarding, and it is suitable for large- and medium-sized networks with sparsely and widely distributed multicast group members.
PIM-SM assumes that no hosts need multicast data. A multicast receiver must express its interest in the multicast data for a multicast group before the data is forwarded to it. A rendezvous point (RP) is the core of a PIM-SM domain. Relying on the RP, SPTs and rendezvous point trees (RPTs) are established and maintained to implement multicast data forwarding. An SPT is rooted at the multicast source and has the RPs as its leaves. An RPT is rooted at the RP and has the receiver hosts as its leaves.
Neighbor discovery
PIM-SM uses the same neighbor discovery mechanism as PIM-DM does. For more information, see "Neighbor discovery."
DR election
A designated router (DR) is required on both the source-side network and receiver-side network. A source-side DR acts on behalf of the multicast source to send register messages to the RP. The receiver-side DR acts on behalf of the multicast receivers to send join messages to the RP.
PIM-DM does not require a DR. However, if IGMPv1 runs on any shared-media LAN in a PIM-DM domain, a DR must be elected to act as the IGMPv1 querier for the LAN. For more information about IGMP, see "Configuring IGMP."
|
|
IMPORTANT: IGMP must be enabled on the device that acts as the receiver-side DR. Otherwise, the receiver hosts attached to the DR cannot join any multicast groups. |
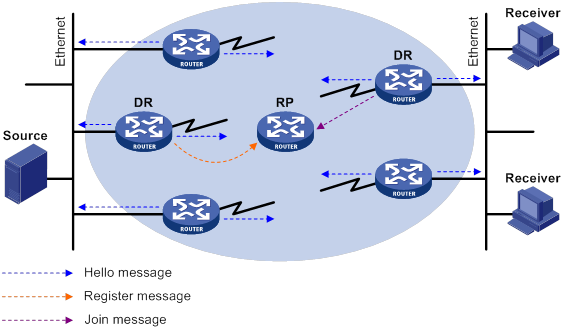
As shown in Figure 39, the DR election process is as follows:
1. The routers on the shared-media LAN send hello messages to one another. The hello messages contain the DR priority for DR election. The router with the highest DR priority is elected as the DR.
2. The router with the highest IP address wins the DR election under one of following conditions:
? All the routers have the same DR election priority.
? A router does not support carrying the DR priority in hello messages.
If the DR fails, its PIM neighbor lifetime expires and the other routers will initiate to elect a new DR.
RP discovery
An RP is the core of a PIM-SM domain. For a small-sized, simple network, one RP is enough for multicast forwarding throughout the network. In this case, you can specify a static RP on each router in the PIM-SM domain. However, in a PIM-SM network that covers a wide area, a huge amount of multicast data is forwarded by the RP. To lessen the RP burden and optimize the topological structure of the RPT, you can configure multiple candidate-RPs (C-RPs) in a PIM-SM domain. An RP is dynamically elected from the multiple C-RPs through the bootstrap mechanism. An elected RP provides services for a different multicast group. For this purpose, you must configure a bootstrap router (BSR). A BSR acts as the administrative core of a PIM-SM domain. A PIM-SM domain has only one BSR, but can have multiple candidate-BSRs (C-BSRs). If the BSR fails, a new BSR can be automatically elected from the C-BSRs and avoid service interruption.
|
|
NOTE: · An RP can provide services for multiple multicast groups, but a multicast group only uses one RP. · A device can act as a C-RP and a C-BSR at the same time. |
As shown in Figure 40, each C-RP periodically unicasts its advertisement messages (C-RP-Adv messages) to the BSR. An advertisement message contains the address of the advertising C-RP and the multicast group range to which it is designated. The BSR collects these advertisement messages and organizes the C-RP information into an RP-set, which is a database of mappings between multicast groups and RPs. The BSR encapsulates the RP-set information in the bootstrap messages (BSMs) and floods the BSMs to the entire PIM-SM domain.
Figure 40 Information exchange between C-RPs and BSR
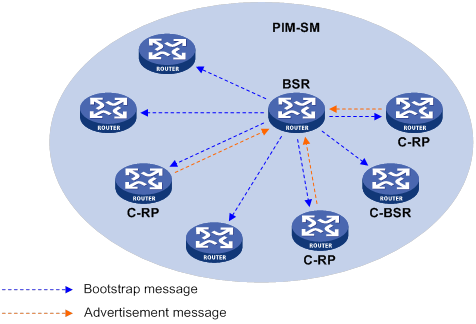
Based on the information in the RP-set, all routers on the network can select an RP for a specific multicast group based on the following rules:
1. The C-RP that is designated to the smallest group range wins.
2. If the C-RPs are designated to the same group ranges, the C-RP with the highest priority wins.
3. If the C-RPs have the same priority, the C-RP with the largest hash value wins. The hash value is calculated through the hash algorithm.
4. If the C-RPs have the same hash value, the C-RP with the highest IP address wins.
Anycast RP
PIM-SM requires only one active RP to serve each multicast group. If the active RP fails, the multicast traffic might be interrupted. The Anycast RP mechanism enables redundancy backup among RPs by configuring multiple RPs with the same IP address. A multicast source registers with the closest RP or a receiver joins the closest RP to implement source information synchronization.
Anycast RP has the following benefits:
· Optimal RP path—A multicast source registers with the closest RP to build an optimal SPT. A receiver joins the closest RP to build an optimal RPT.
· Redundancy backup among RPs—When an RP fails, the RP-related sources will register with the closest available RPs and the receiver-side DRs will join the closest available RPs. This provides redundancy backup among RPs.
Anycast RP is implemented in either of the following methods:
· Anycast RP through MSDP—In this method, you can configure multiple RPs with the same IP address for one multicast group and configure MSDP peering relationships between them. For more information about Anycast RP through MSDP, see "Configuring MSDP."
· Anycast RP through PIM-SM—In this method, you can configure multiple RPs for one multicast group and add them to an Anycast RP set. This method introduces the following concepts:
? Anycast RP set—A set of RPs that are designated to the same multicast group.
? Anycast RP member—Each RP in the Anycast RP set.
? Anycast RP member address—IP address of each Anycast RP member for communication among the RP members.
? Anycast RP address—IP address of the Anycast RP set for communication within the PIM-SM domain. It is also known as RPA.
As shown in Figure 41, RP 1, RP 2, and RP 3 are members of an Anycast RP set.
Figure 41 Anycast RP through PIM-SM
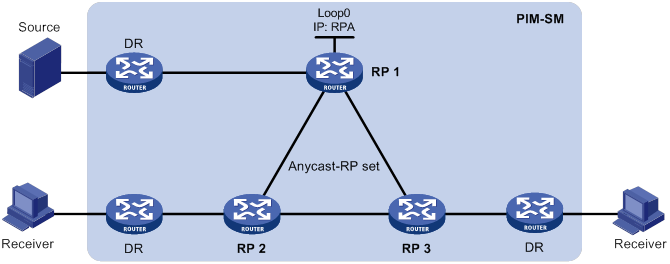
The following describes how Anycast RP through PIM-SM is implemented:
a. RP 1 receives a register message destined to RPA. Because the message is not from other Anycast RP members (RP 2 or RP 3), RP 1 considers that the register message is from the DR. RP 1 changes the source IP address of the register message to its own address and sends the message to the other members (RP 2 and RP 3).
If a router acts as both a DR and an RP, it creates a register message, and then forwards the message to the other RP members.
b. After receiving the register message, RP 2 and RP 3 find out that the source address of the register message is an Anycast RP member address. They stop forwarding the message to other routers.
In Anycast RP implementation, an RP must forward the register message from the DR to other Anycast RP members to synchronize multicast source information.
RPT building
Figure 42 RPT building in a PIM-SM domain
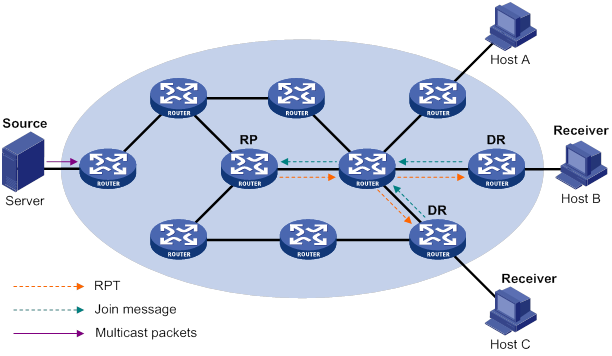
As shown in Figure 42, the process of building an RPT is as follows:
1. When a receiver wants to join the multicast group G, it uses an IGMP message to inform the receiver-side DR.
2. After getting the receiver information, the DR sends a join message, which travels hop by hop to the RP for the multicast group.
3. The routers along the path from the DR to the RP form an RPT branch. Each router on this branch adds to its forwarding table a (*, G) entry, where the asterisk (*) represents any multicast source. The RP is the root of the RPT, and the DR is a leaf of the RPT.
When the multicast data addressed to the multicast group G reaches the RP, the RP forwards the data to the DR along the established RPT, and finally to the receiver.
When a receiver is no longer interested in the multicast data addressed to the multicast group G, the receiver-side DR sends a prune message. The prune message goes hop by hop along the RPT to the RP. After receiving the prune message, the upstream node deletes the interface that connects to this downstream node from the outgoing interface list. At the same time, the upstream router checks for the existence of receivers for that multicast group. If no receivers for the multicast group exist, the router continues to forward the prune message to its upstream router.
Multicast source registration
The multicast source uses the registration process to inform an RP of its presence.
Figure 43 Multicast source registration
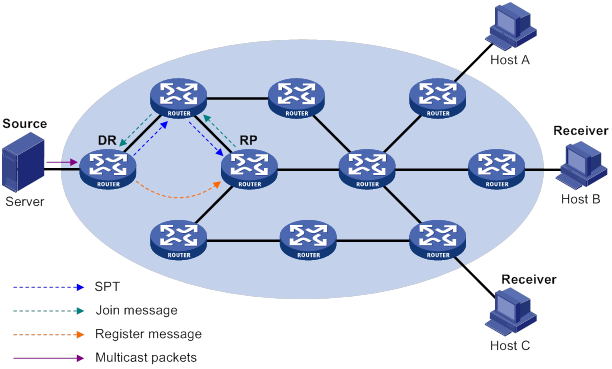
As shown in Figure 43, the multicast source registers with the RP as follows:
1. The multicast source S sends the first multicast packet to the multicast group G. When receiving the multicast packet, the source-side DR encapsulates the packet into a PIM register message and unicasts the message to the RP.
2. After the RP receives the register message, it decapsulates the register message and forwards the register message down to the RPT. Meanwhile, it sends an (S, G) source-specific join message toward the multicast source. The routers along the path from the RP to the multicast source constitute an SPT branch. Each router on this branch creates an (S, G) entry in its forwarding table.
3. The subsequent multicast data from the multicast source are forwarded to the RP along the established SPT. When the multicast data reaches the RP along the SPT, the RP forwards the data to the receivers along the RPT. Meanwhile, it unicasts a register-stop message to the source-side DR to prevent the DR from unnecessarily encapsulating the data.
Switchover to SPT
|
|
CAUTION: If the switch is an RP, disabling switchover to SPT might cause multicast traffic forwarding failures on the source-side DR. When disabling switchover to SPT, be sure you fully understand its impact on your network. |
In a PIM-SM domain, only one RP and one RPT provide services for a specific multicast group. Before the switchover to SPT occurs, the source-side DR encapsulates all multicast data in register messages and sends them to the RP. After receiving these register messages, the RP decapsulates them and forwards them to the receiver-side DR along the RPT.
Multicast forwarding along the RPT has the following weaknesses:
· Encapsulation and decapsulation are complex on the source-side DR and the RP.
· The path for a multicast packet might not be the shortest one.
· The RP might be overloaded by multicast traffic bursts.
To eliminate these weaknesses, PIM-SM allows an RP or the receiver-side DR to initiate the switchover to SPT when the RP or DR receives multicast traffic.
· The RP initiates the switchover to SPT:
When the RP receives multicast traffic, it sends an (S, G) source-specific join message toward the multicast source. The routers along the path from the RP to the multicast source constitute an SPT. The subsequent multicast data is forwarded to the RP along the SPT without being encapsulated into register messages.
For more information about the switchover to SPT initiated by the RP, see "Multicast source registration."
· The receiver-side DR initiates the switchover to SPT:
When the receiver-side DR receives multicast traffic, it initiates the switchover to SPT as follows:
a. The DR sends an (S, G) source-specific join message toward the multicast source. The routers along the path create an (S, G) entry in their forwarding table to constitute an SPT branch.
b. When the multicast packets reach the router where the RPT and the SPT branches, the router drops the multicast packets that travel along the RPT. It then sends a prune message with the RP bit toward the RP.
c. After receiving the prune message, the RP forwards it toward the multicast source (supposed only one receiver exists). Thus, the switchover to SPT is completed. The subsequent multicast packets travel along the SPT from the multicast source to the receiver hosts.
With the switchover to SPT, PIM-SM builds SPTs more economically than PIM-DM does.
Assert
PIM-SM uses a similar assert mechanism as PIM-DM does. For more information, see "Assert."
Administrative scoping overview
Typically, a PIM-SM domain contains only one BSR, which is responsible for advertising RP-set information within the entire domain. The information about all multicast groups is forwarded within the network that the BSR administers. This is called the "non-scoped BSR mechanism."
Administrative scoping mechanism
To implement refined management, you can divide a PIM-SM domain into a global-scoped zone and multiple administratively-scoped zones (admin-scoped zones). This is called the "administrative scoping mechanism."
The administrative scoping mechanism effectively releases stress on the management in a single-BSR domain and enables provision of zone-specific services through private group addresses.
Admin-scoped zones are divided for multicast groups. Zone border routers (ZBRs) form the boundary of an admin-scoped zone. Each admin-scoped zone maintains one BSR for multicast groups within a specific range. Multicast protocol packets, such as assert messages and BSMs, for a specific group range cannot cross the boundary of the admin-scoped zone for the group range. Multicast group ranges that are associated with different admin-scoped zones can have intersections. However, the multicast groups in an admin-scoped zone are valid only within the local zone, and theses multicast groups are regarded as private group addresses.
The global-scoped zone maintains a BSR for the multicast groups that do not belong to any admin-scoped zones.
Relationship between admin-scoped zones and the global-scoped zone
The global-scoped zone and each admin-scoped zone have their own C-RPs and BSRs. These devices are effective only on their respective zones, and the BSR election and the RP election are implemented independently. Each admin-scoped zone has its own boundary. The multicast information within a zone cannot cross this boundary in either direction. You can have a better understanding of the global-scoped zone and admin-scoped zones based on geographical locations and multicast group address ranges.
· In view of geographical locations:
An admin-scoped zone is a logical zone for particular multicast groups. The multicast packets for such multicast groups are confined within the local admin-scoped zone and cannot cross the boundary of the zone.
Figure 44 Relationship in view of geographical locations
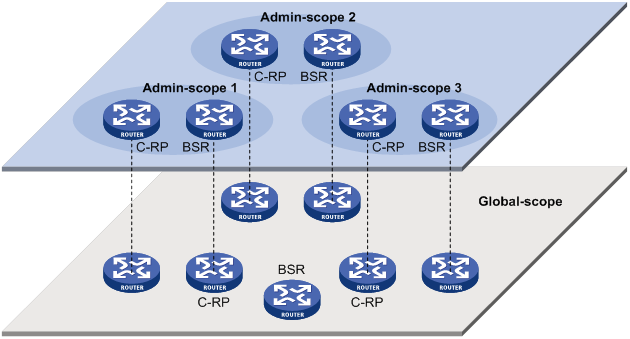
As shown in Figure 44, for the multicast groups in a specific group address range, the admin-scoped zones must be geographically separated and isolated. A router cannot belong to multiple admin-scoped zones. An admin-scoped zone cannot contain a router that belongs to any other admin-scoped zone. However, the global-scoped zone includes all routers in the PIM-SM domain. Multicast packets that do not belong to any admin-scoped zones are forwarded in the entire PIM-SM domain.
· In view of multicast group address ranges:
Each admin-scoped zone is designated to specific multicast groups, of which the multicast group addresses are valid only within the local zone. The multicast groups of different admin-scoped zones might have intersections. All the multicast groups other than those of the admin-scoped zones use the global-scoped zone.
Figure 45 Relationship in view of multicast group address ranges
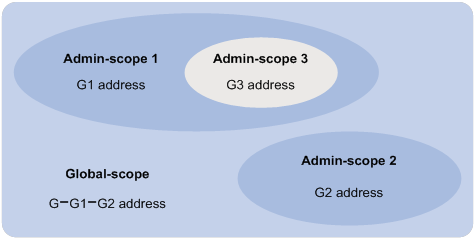
As shown in Figure 45, the admin-scoped zones 1 and 2 have no intersection, but the admin-scoped zone 3 is a subset of the admin-scoped zone 1. The global-scoped zone provides services for all the multicast groups that are not covered by the admin-scoped zones 1 and 2, G−G1−G2 in this case.
PIM-SSM overview
The ASM model includes PIM-DM and PIM-SM. The SSM model can be implemented by leveraging part of the PIM-SM technique. It is also called "PIM-SSM."
The SSM model provides a solution for source-specific multicast. It maintains the relationship between hosts and routers through IGMPv3.
In actual applications, part of IGMPv3 and PIM-SM techniques are adopted to implement the SSM model. In the SSM model, because receivers have located a multicast source, no RP or RPT is required. Multicast sources do not register with the RP, and the MSDP is not needed for discovering multicast sources in other PIM domains.
Neighbor discovery
PIM-SSM uses the same neighbor discovery mechanism as PIM-SM. For more information, see "Neighbor discovery."
DR election
PIM-SSM uses the same DR election mechanism as PIM-SM. For more information, see "DR election."
SPT building
The decision to build an RPT for PIM-SM or an SPT for PIM-SSM depends on whether the multicast group that the receiver joins is in the SSM group range. The SSM group range reserved by IANA is 232.0.0.0/8.
Figure 46 SPT building in PIM-SSM
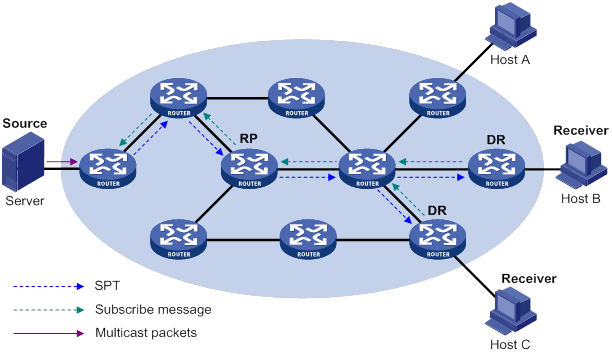
As shown in Figure 46, Host B and Host C are receivers. They send IGMPv3 report messages to their DRs to express their interest in the multicast information that the multicast source S sends to the multicast group G.
After receiving a report message, the DR first checks whether the group address in this message is in the SSM group range and does the following:
· If the group address is in the SSM group range, the DR sends a subscribe message hop by hop toward the multicast source S. All routers along the path from the DR to the source create an (S, G) entry to build an SPT. The SPT is rooted at the multicast source S and has the receivers as its leaves. This SPT is the transmission channel in PIM-SSM.
· If the group address is not in the SSM group range, the receiver-side DR sends a (*, G) join message to the RP. The multicast source registers with the source-side DR.
In PIM-SSM, the term "subscribe message" refers to a join message.
Relationship among PIM protocols
In a PIM network, PIM-DM cannot run together with PIM-SM, BIDIR-PIM, or PIM-SSM. However, PIM-SM, BIDIR-PIM, and PIM-SSM can run together. Figure 47 shows how the device selects one protocol from among them for a receiver trying to join a group. BIDIR-PIM is not supported in the current software version.
For more information about IGMP SSM mapping, see "Configuring IGMP."
Figure 47 Relationship among PIM protocols
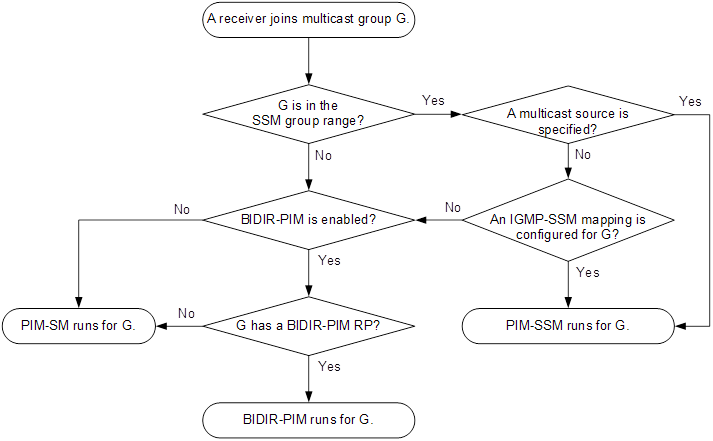
PIM support for VPNs
To support PIM for VPNs, a multicast router that runs PIM maintains an independent set of PIM neighbor table, multicast routing table, BSR information, and RP-set information for each VPN.
After receiving a multicast data packet, the multicast router checks which VPN the data packet belongs to. Then, the router forwards the packet according to the multicast routing table for that VPN or creates a multicast routing entry for that VPN.
Protocols and standards
· RFC 3973, Protocol Independent Multicast-Dense Mode (PIM-DM): Protocol Specification(Revised)
· RFC 4601, Protocol Independent Multicast-Sparse Mode (PIM-SM): Protocol Specification (Revised)
· RFC 4610, Anycast-RP Using Protocol Independent Multicast (PIM)
· RFC 5059, Bootstrap Router (BSR) Mechanism for Protocol Independent Multicast (PIM)
· RFC 4607, Source-Specific Multicast for IP
· Draft-ietf-ssm-overview-05, An Overview of Source-Specific Multicast (SSM)
Configuring PIM-DM
This section describes how to configure PIM-DM.
PIM-DM configuration task list
|
Tasks at a glance |
|
(Required.) Enabling PIM-DM |
|
(Optional.) Enabling the state refresh feature |
|
(Optional.) Configuring state refresh parameters |
|
(Optional.) Configuring the PIM-DM graft retry timer |
|
(Optional.) Configuring common PIM features |
Configuration prerequisites
Before you configure PIM-DM, configure a unicast routing protocol so that all devices in the domain can interoperate at the network layer.
Enabling PIM-DM
Enable IP multicast routing before you configure PIM.
With PIM-DM enabled on interfaces, routers can establish PIM neighbor relationship and process PIM messages from their PIM neighbors. As a best practice, enable PIM-DM on all non-border interfaces of the routers when you deploy a PIM-DM domain.
|
|
IMPORTANT: All the interfaces on a device must operate in the same PIM mode in the public network or the same VPN instance. |
To enable PIM-DM:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable IP multicast routing and enter MRIB view. |
multicast routing [ vpn-instance vpn-instance-name ] |
By default, IP multicast routing is disabled. |
|
3. Return to system view. |
quit |
N/A |
|
4. Enter interface view. |
interface interface-type interface-number |
N/A |
|
5. Enable PIM-DM. |
pim dm |
By default, PIM-DM is disabled. |
Enabling the state refresh feature
In a PIM-DM domain, the state refresh feature enables the PIM router that is directly connected to the source to periodically send state refresh messages. It also enables other PIM routers to refresh pruned state timers after receiving the state refresh messages. It prevents the pruned interfaces from resuming multicast forwarding. You must enable this feature on all PIM routers on a subnet.
To enable the state refresh feature:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter interface view. |
interface interface-type interface-number |
N/A |
|
3. Enable the state refresh feature. |
pim state-refresh-capable |
By default, the state refresh feature is enabled. |
Configuring state refresh parameters
The state refresh interval determines the interval at which a router sends state refresh messages. It is configurable.
A router might receive duplicate state refresh messages within a short time. To prevent this situation, you can configure the time that the router must wait to accept a new state refresh message. If the router receives a new state refresh message before the timer expires, it discards the message. If the router receives a new state refresh message after the timer expires, it accepts the message, refreshes its own PIM-DM state, and resets the waiting timer.
The TTL value of a state refresh message decrements by 1 whenever it passes a router before it is forwarded to the downstream node. The state refresh message stops being forwarded when the TTL value comes down to 0. A state refresh message with a large TTL value might cycle on a small network. To effectively control the propagation scope of state refresh messages, configure an appropriate TTL value based on the network size on the router directly connected with the multicast source.
To configure state refresh parameters:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter PIM view. |
pim [ vpn-instance vpn-instance-name ] |
N/A |
|
3. Configure the state refresh interval. |
state-refresh-interval interval |
The default setting is 60 seconds. |
|
4. Configure the amount of time to wait before accepting a new state refresh message. |
state-refresh-rate-limit time |
The default setting is 30 seconds. |
|
5. Configure the TTL value of state refresh messages. |
state-refresh-ttl ttl-value |
The default setting 255. |
Configuring the PIM-DM graft retry timer
To configure the PIM-DM graft retry timer:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter interface view. |
interface interface-type interface-number |
N/A |
|
3. Configure the PIM-DM graft retry timer. |
pim timer graft-retry interval |
The default setting is 3 seconds. |
For more information about the configuration of other timers in PIM-DM, see "Configuring common PIM timers."
Configuring PIM-SM
This section describes how to configure PIM-SM.
PIM-SM configuration task list
|
Tasks at a glance |
Remarks |
|
(Required.) Enabling PIM-SM |
N/A |
|
(Required.) Configuring an RP: · (Optional.) Enabling Auto-RP listening · (Optional.) Configuring Anycast RP |
You must configure a static RP, a C-RP, or both in a PIM-SM domain. |
|
· (Required.) Configuring a C-BSR · (Optional.) Configuring a PIM domain border · (Optional.) Disabling BSM semantic fragmentation · (Optional.) Disabling BSM forwarding out of incoming interfaces |
Skip the task of configuring a BSR on a network without C-RPs. |
|
(Optional.) Configuring multicast source registration |
N/A |
|
(Optional.) Configuring common PIM features |
N/A |
Configuration prerequisites
Before you configure PIM-SM, configure a unicast routing protocol so that all devices in the domain can interoperate at the network layer.
Enabling PIM-SM
Enable IP multicast routing before you configure PIM.
With PIM-SM enabled on interfaces, routers can establish PIM neighbor relationship and process PIM messages from their PIM neighbors. As a best practice, enable PIM-SM on all non-border interfaces of routers when you deploy a PIM-SM domain.
|
|
IMPORTANT: All the interfaces on the same router must operate in the same PIM mode in the public network or the same VPN instance. |
To enable PIM-SM:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable IP multicast routing and enter MRIB view. |
multicast routing [ vpn-instance vpn-instance-name ] |
By default, IP multicast routing is disabled. |
|
3. Return to system view. |
quit |
N/A |
|
4. Enter interface view. |
interface interface-type interface-number |
N/A |
|
5. Enable PIM-SM. |
pim sm |
By default, PIM-SM is disabled. |
Configuring an RP
An RP can provide services for multiple or all multicast groups. However, only one RP can forward multicast traffic for a multicast group at a time.
An RP can be manually configured or dynamically elected through the BSR mechanism. For a large-scaled PIM network, configuring static RPs is a tedious job. Generally, static RPs are backups for dynamic RPs to enhance the robustness and operational manageability on a multicast network.
Configuring a static RP
If only one dynamic RP exists on a network, you can configure a static RP to avoid communication interruption caused by single-point failures. The static RP can also avoid waste of bandwidth due to frequent message exchange between C-RPs and the BSR. You must configure the same static RP on all routers in the PIM-SM domain.
When you configure static RPs for PIM-SM, follow these restrictions and guidelines:
· You can configure the same static RP for different multicast groups by using the same RP address but different ACLs.
· You do not need to enable PIM for an interface to be configured as a static RP.
· If you configure multiple static RPs for a multicast group, only the static RP with the highest IP address takes effect.
To configure a static RP for PIM-SM:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter PIM view. |
pim [ vpn-instance vpn-instance-name ] |
N/A |
|
3. Configure a static RP for PIM-SM. |
static-rp rp-address [ ipv4-acl-number | preferred ] * |
By default, no static RPs exist. |
Configuring a C-RP
|
|
IMPORTANT: When you configure a C-RP, reserve a relatively large bandwidth between the C-RP and other devices in the PIM-SM domain. |
In a PIM-SM domain, if you want a router to become the RP, you can configure the router as a C-RP. As a best practice, configure C-RPs on backbone routers.
The C-RPs periodically send advertisement messages to the BSR, which collects RP-set information for RP election. You can configure the interval for sending the advertisement messages.
The holdtime option in C-RP advertisement messages defines the C-RP lifetime for the advertising C-RP. The BSR starts a holdtime timer for a C-RP after it receives an advertisement message. If the BSR does not receive any advertisement message when the timer expires, it considers the C-RP failed or unreachable.
A C-RP policy enables the BSR to filter C-RP advertisement messages by using an ACL that specifies the packet source address range and multicast groups. It is used to guard against C-RP spoofing. You must configure the same C-RP policy on all C-BSRs in the PIM-SM domain.
To configure a C-RP:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter PIM view. |
pim [ vpn-instance vpn-instance-name ] |
N/A |
|
3. Configure a C-RP. |
c-rp ip-address [ advertisement-interval adv-interval | group-policy ipv4-acl-number | holdtime hold-time | priority priority ] * |
By default, no C-RPs exist. |
|
4. (Optional.) Configure a C-RP policy. |
crp-policy ipv4-acl-number |
By default, no C-RP policy exists, and all C-RP advertisement messages are regarded as legal. |
Enabling Auto-RP listening
This feature enables the device to receive Auto-RP announcement and discovery messages and learn RP information. The destination IP addresses for Auto-RP announcement and discovery messages are 224.0.1.39 and 224.0.1.40, respectively.
To enable Auto-RP listening:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter PIM view. |
pim [ vpn-instance vpn-instance-name ] |
N/A |
|
3. Enable Auto-RP listening. |
auto-rp enable |
By default, Auto-RP listening is disabled. |
Configuring Anycast RP
|
|
IMPORTANT: The Anycast RP address must be different from the BSR address. Otherwise, the other Anycast RP member devices will discard the BSM sent by the BSR. |
You must configure a static RP or C-RPs in the PIM-SM domain before you configure the Anycast RP. Use the address of the static RP or the dynamically elected RP as the Anycast RP address.
When you configure Anycast RP, follow these restrictions and guidelines:
· You must add the device that the Anycast RP resides as an RP member to the Anycast RP set. The RP member address cannot be the same as the Anycast RP address.
· You must add all RP member addresses (including the local RP member address) to the Anycast RP set on each RP member device.
· As a best practice, configure no more than 16 Anycast RP members for an Anycast RP set.
· As a best practice, configure the loopback interface address of an RP member device as the RP member address. If you add multiple interface addresses of an RP member device to an Anycast RP set, the lowest IP address becomes the RP member address. The rest of the interface addresses become backup RP member addresses.
To configure Anycast RP:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter PIM view. |
pim [ vpn-instance vpn-instance-name ] |
N/A |
|
3. Configure Anycast RP. |
anycast-rp anycast-rp-address member-rp-address |
By default, Anycast RP is not configured. You can repeat this command to add multiple RP member addresses to the Anycast RP set. |
Configuring a BSR
You must configure a BSR if C-RPs are configured to dynamically select the RP. You do not need to configure a BSR when you have configured only a static RP but no C-RPs.
A PIM-SM domain can have only one BSR, but must have a minimum of one C-BSR. Any router can be configured as a C-BSR. Elected from C-BSRs, the BSR is responsible for collecting and advertising RP information in the PIM-SM domain.
Configuring a C-BSR
The BSR election process is summarized as follows:
1. Initially, each C-BSR regards itself as the BSR of the PIM-SM domain and sends a BSM to other routers in the domain.
2. When a C-BSR receives the BSM from another C-BSR, it compares its own priority with the priority carried in the message. The C-BSR with a higher priority wins the BSR election. If a tie exists in the priority, the C-BSR with a higher IP address wins. The loser uses the winner's BSR address to replace its own BSR address and no longer regards itself as the BSR. The winner retains its own BSR address and continues to regard itself as the BSR.
The elected BSR distributes the RP-set information collected from C-RPs to all routers in the PIM-SM domain. All routers use the same hash algorithm to select an RP for a specific multicast group.
A BSR policy enables a PIM-SM router to filter BSR messages by using an ACL that specifies the legal BSR addresses. It is used to guard against the following BSR spoofing cases:
· Some maliciously configured hosts can forge BSMs to fool routers and change RP mappings. Such attacks often occur on border routers.
· When an attacker controls a router on the network, the attacker can configure the router as a C-BSR to win the BSR election. Through this router, the attacker controls the advertising of RP information.
When you configure a C-BSR, follow these restrictions and guidelines:
· Configure C-BSRs on routers that are on the backbone network.
· Reserve a relatively large bandwidth between the C-BSR and the other devices in the PIM-SM domain.
· You must configure the same BSR policy on all routers in the PIM-SM domain. The BSR policy discards illegal BSR messages, but it partially guards against BSR attacks on the network. If an attacker controls a legal BSR, the problem still exists.
· When C-BSRs connect to other PIM routers through tunnels, static multicast routes must be configured to make sure the next hop to a C-BSR is a tunnel interface. Otherwise, RPF check is affected. For more information about static multicast routes, see "Configuring multicast routing and forwarding."
To configure a C-BSR:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter PIM view. |
pim [ vpn-instance vpn-instance-name ] |
N/A |
|
3. Configure a C-BSR. |
c-bsr ip-address [ scope group-address { mask-length | mask } ] [ hash-length hash-length | priority priority ] * |
By default, no C-BSRs exist. |
|
4. (Optional.) Configure a BSR policy. |
bsr-policy ipv4-acl-number |
By default, no BSR policy exists, and all bootstrap messages are regarded as legal. |
Configuring a PIM domain border
A PIM domain border determines the transmission boundary of bootstrap messages. Bootstrap messages cannot cross the domain border in either direction. A number of PIM domain border interfaces partition a network into different PIM-SM domains.
To configure a PIM domain border:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter interface view. |
interface interface-type interface-number |
N/A |
|
3. Configure a PIM domain border. |
pim bsr-boundary |
By default, an interface is not a PIM domain border. |
Disabling BSM semantic fragmentation
BSM semantic fragmentation enables a BSR to split a BSM into multiple BSM fragments (BSMFs) if the BSM exceeds the MTU. In this way, a non-BSR router can update the RP-set information for a group range after receiving all BSMFs for the range. The loss of one BSMF only affects the RP-set information of the group ranges that the fragment contains.
If the PIM-SM domain contains a device that does not support this feature, you must disable this feature on all C-BSRs. If you do not disable this feature, such a device regards a BSMF as a BSM and updates the RP-set information each time it receives a BSMF. It learns only part of the RP-set information, which further affects the RP election.
To disable BSM semantic fragmentation:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter PIM view. |
pim [ vpn-instance vpn-instance-name ] |
N/A |
|
3. Disable BSM semantic fragmentation. |
undo bsm-fragment enable |
By default, BSM semantic fragmentation is enabled. |
|
|
NOTE: Generally, a BSR performs BSM semantic fragmentation according to the MTU of its BSR interface. For BSMs originated due to learning of a new PIM neighbor, semantic fragmentation is performed according to the MTU of the interface that sends the BSMs. |
Disabling BSM forwarding out of incoming interfaces
By default, the device is enabled to forward BSMs out of incoming interfaces. This feature avoids devices in the PIM-SM domain might from failing to receive BSMs due to inconsistent routing information. To reduce traffic, you can disable this feature if all the devices have consistent routing information.
To disable the device to forward BSMs out of incoming interfaces:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter PIM view. |
pim [ vpn-instance vpn-instance-name ] |
N/A |
|
3. Disable the device to forward BSMs out of incoming interfaces. |
undo bsm-reflection enable |
By default, the device is enabled to forward BSMs out of incoming interfaces. |
Configuring multicast source registration
You can configure the device to calculate the checksum based on the entire register message to ensure information integrity of a register message in the transmission process. If a device that does not support this feature is present on the network, you can configure the device to calculate the checksum based on the register message header.
The RP sends a register-stop message to the source-side DR in either of the following conditions:
· The RP stops serving the receivers for a multicast group. The receivers do not receive multicast data addressed to the multicast group through the RP.
· The RP receives multicast data that travels along the SPT.
After receiving the register-stop message, the DR stops sending register messages encapsulated with multicast data and starts a register-stop timer. Before the register-stop timer expires, the DR sends a null register message (a register message without encapsulated multicast data) to the RP and starts a register probe timer. If the DR receives a register-stop message before the register probe timer expires, it resets its register-stop timer. Otherwise, the DR starts sending register messages with encapsulated data again.
The register-stop timer is set to a random value chosen uniformly from (0.5 × register_suppression_time minus register_probe_time) to (1.5 × register_suppression_time minus register_probe_time). The register_probe_time is fixed to 5 seconds.
On all C-RP routers, perform the following tasks:
· Configure a PIM register policy.
· Configure the routers to calculate the checksum based on the entire register messages or the register message header.
On all routers that might become the source-side DR, configure the register suppression time.
To configure multicast source registration:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter PIM view. |
pim [ vpn-instance vpn-instance-name ] |
N/A |
|
3. Configure a PIM register policy. |
register-policy ipv4-acl-number |
By default, no PIM register policy exists, and all PIM register messages are regarded as legal. |
|
4. Configure the device to calculate the checksum based on the entire register message. |
register-whole-checksum |
By default, the device calculates the checksum based on the header of a register message. |
|
5. Configure the register suppression time. |
register-suppression-timeout interval |
The default setting is 60 seconds. |
Configuring PIM-SSM
PIM-SSM requires IGMPv3 support. Enable IGMPv3 on PIM routers that connect to multicast receivers.
PIM-SSM configuration task list
|
Tasks at a glance |
|
(Required.) Enabling PIM-SM |
|
(Optional.) Configuring the SSM group range |
|
(Optional.) Configuring common PIM features |
Configuration prerequisites
Before you configure PIM-SSM, configure a unicast routing protocol so that all devices in the domain can interoperate at the network layer.
Enabling PIM-SM
Before you configure PIM-SSM, you must enable PIM-SM, because the implementation of the SSM model is based on subsets of PIM-SM.
When you deploy a PIM-SSM domain, enable PIM-SM on non-border interfaces of the routers.
|
|
IMPORTANT: All the interfaces on a device must be enabled with the same PIM mode. |
To enable PIM-SM:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable IP multicast routing, and enter MRIB view. |
multicast routing [ vpn-instance vpn-instance-name ] |
By default, IP multicast routing is disabled. |
|
3. Return to system view. |
quit |
N/A |
|
4. Enter interface view. |
interface interface-type interface-number |
N/A |
|
5. Enable PIM-SM. |
pim sm |
By default, PIM-SM is disabled. |
Configuring the SSM group range
When a PIM-SM enabled interface receives a multicast packet, it checks whether the multicast group address of the packet is in the SSM group range. If the multicast group address is in this range, the PIM mode for this packet is PIM-SSM. If the multicast group address is not in this range, the PIM mode is PIM-SM.
Configuration restrictions and guidelines
When you configure the SSM group range, follow these restrictions and guidelines:
· Configure the same SSM group range on all routers in the entire PIM-SSM domain. Otherwise, multicast information cannot be delivered through the SSM model.
· When a member of a multicast group in the SSM group range sends an IGMPv1 or IGMPv2 report message, the device does not trigger a (*, G) join.
Configuration procedure
To configure an SSM group range:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter PIM view. |
pim |
N/A |
|
3. Configure the SSM group range. |
ssm-policy ipv4-acl-number |
By default, the SSM group range is 232.0.0.0/8. |
Configuring common PIM features
Configuration task list
|
Tasks at a glance |
|
(Optional.) Configuring a multicast source policy |
|
(Optional.) Configuring a PIM hello policy |
|
(Optional.) Configuring PIM hello message options |
|
(Optional.) Configuring common PIM timers |
|
(Optional.) Setting the maximum size of a join or prune message |
|
(Optional.) Enabling BFD for PIM |
|
(Optional.) Enabling PIM passive mode |
|
(Optional.) Enabling PIM NSR |
|
(Optional.) Enabling SNMP notifications for PIM |
|
(Optional.) Setting a DSCP value for outgoing PIM messages |
Configuration prerequisites
Before you configure common PIM features, complete the following tasks:
· Configure a unicast routing protocol so that all devices in the domain can interoperate at the network layer.
· Configure PIM-DM or PIM-SM.
Configuring a multicast source policy
This feature enables the device to filter multicast data by using an ACL that specifies the multicast sources and the optional groups. It filters not only data packets but also register messages with multicast data encapsulated. It controls the information available to downstream receivers.
To configure a multicast source policy:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter PIM view. |
pim [ vpn-instance vpn-instance-name ] |
N/A |
|
3. Configure a multicast source policy. |
source-policy ipv4-acl-number |
By default, no multicast source policy exists. The device does not filter multicast data packets. |
Configuring a PIM hello policy
This feature enables the device to filter PIM hello messages by using an ACL that specifies the packet source addresses. It is used to guard against PIM message attacks and to establish correct PIM neighboring relationships.
If hello messages of an existing PIM neighbor are filtered out by the policy, the neighbor is automatically removed when its aging timer expires.
To configure a PIM hello policy:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter interface view. |
interface interface-type interface-number |
N/A |
|
3. Configure a PIM hello policy. |
pim neighbor-policy ipv4-acl-number |
By default, no PIM hello policy exists on an interface, and all PIM hello messages are regarded as legal. |
Configuring PIM hello message options
In either a PIM-DM domain or a PIM-SM domain, hello messages exchanged among routers contain the following configurable options:
· DR_Priority (for PIM-SM only)—Priority for DR election. The device with the highest priority wins the DR election. You can configure this option for all the routers in a shared-media LAN that directly connects to the multicast source or the receivers.
· Holdtime—PIM neighbor lifetime. If a router does not receive a hello message from a neighbor when the neighbor lifetime expires, it regards the neighbor failed or unreachable.
· LAN_Prune_Delay—Delay of pruning a downstream interface on a shared-media LAN. This option has LAN delay, override interval, and neighbor tracking support (the capability to disable join message suppression).
The LAN delay defines the PIM message propagation delay. The override interval defines a period for a router to override a prune message. If the propagation delay or override interval on different PIM routers on a shared-media LAN are different, the largest ones apply.
On the shared-media LAN, the propagation delay and override interval are used as follows:
? If a router receives a prune message on its upstream interface, it means that there are downstream routers on the shared-media LAN. If this router still needs to receive multicast data, it must send a join message to override the prune message within the override interval.
? When a router receives a prune message from its downstream interface, it does not immediately prune this interface. Instead, it starts a timer (the propagation delay plus the override interval). If interface receives a join message before the timer expires, the router does not prune the interface. Otherwise, the router prunes the interface.
If you enable neighbor tracking on an upstream router, this router can track the states of the downstream nodes for which the joined state holdtime timer has not expired. If you want to enable neighbor tracking, you must enable it on all PIM routers on a shared-media LAN. Otherwise, the upstream router cannot track join messages from every downstream routers.
· Generation ID—A router generates a generation ID for hello messages when an interface is enabled with PIM. The generation ID is a random value, but only changes when the status of the router changes. If a PIM router finds that the generation ID in a hello message from the upstream router has changed, it assumes that the status of the upstream router has changed. In this case, it sends a join message to the upstream router for status update. You can configure an interface to drop hello messages without the generation ID options to promptly know the status of an upstream router.
You can configure hello message options for all interfaces in PIM view or for the current interface in interface view. The configuration made in interface view takes priority over the configuration made in PIM view.
Configuring hello message options globally
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter PIM view. |
pim [ vpn-instance vpn-instance-name ] |
N/A |
|
3. Set the DR priority. |
hello-option dr-priority priority |
The default setting is 1. |
|
4. Set the neighbor lifetime. |
hello-option holdtime time |
The default setting is 105 seconds. |
|
5. Set the PIM message propagation delay for a shared-media LAN. |
hello-option lan-delay delay |
The default setting is 500 milliseconds. |
|
6. Set the override interval. |
hello-option override-interval interval |
The default setting is 2500 milliseconds. |
|
7. Enable neighbor tracking. |
hello-option neighbor-tracking |
By default, neighbor tracking is disabled. |
Configuring hello message options on an interface
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter interface view. |
interface interface-type interface-number |
N/A |
|
3. Set the DR priority. |
pim hello-option dr-priority priority |
The default setting is 1. |
|
4. Set the neighbor lifetime. |
pim hello-option holdtime time |
The default setting is 105 seconds. |
|
5. Set the PIM message propagation delay. |
pim hello-option lan-delay delay |
The default setting is 500 milliseconds. |
|
6. Set the override interval. |
pim hello-option override-interval interval |
The default setting is 2500 milliseconds. |
|
7. Enable neighbor tracking. |
pim hello-option neighbor-tracking |
By default, neighbor tracking is disabled. |
|
8. Enable dropping hello messages without the Generation ID option. |
pim require-genid |
By default, an interface accepts hello messages without the Generation ID option. |
Configuring common PIM timers
|
|
IMPORTANT: To prevent the upstream neighbors from aging out, you must configure the interval for sending join/prune messages to be less than the joined/pruned state holdtime timer. |
The following are common timers in PIM:
· Hello interval—Interval at which a PIM router sends hello messages to discover PIM neighbors, and maintain PIM neighbor relationship.
· Triggered hello delay—Maximum delay for sending a hello message to avoid collisions caused by simultaneous hello messages. After receiving a hello message, a PIM router waits for a random time before sending a hello message. This random time is in the range of 0 to the triggered hello delay.
· Join/Prune interval—Interval at which a PIM router sends join/prune messages to its upstream routers for state update.
· Joined/Pruned state holdtime—Time for which a PIM router keeps the joined/pruned state for the downstream interfaces. This joined/pruned state holdtime is specified in a join/prune message.
· Multicast source lifetime—Lifetime that a PIM router maintains for a multicast source. If a router does not receive subsequent multicast data from the multicast source S when the timer expires, it deletes the (S, G) entry for the multicast source.
You can configure common PIM timers for all interfaces in PIM view or for the current interface in interface view. The configuration made in interface view takes priority over the configuration made in PIM view.
|
|
TIP: As a best practice, use the defaults for a network without special requirements. |
Configuring common PIM timers globally
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter PIM view. |
pim [ vpn-instance vpn-instance-name ] |
N/A |
|
3. Set the hello interval. |
timer hello interval |
The default setting is 30 seconds. |
|
4. Set the join/prune interval. |
timer join-prune interval |
The default setting is 60 seconds. This configuration takes effect after the current interval ends. |
|
5. Set the joined/pruned state holdtime. |
holdtime join-prune time |
The default setting is 210 seconds. |
|
6. Set the multicast source lifetime. |
source-lifetime time |
The default setting is 210 seconds. |
Configuring common PIM timers on an interface
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter interface view. |
interface interface-type interface-number |
N/A |
|
3. Set the hello interval. |
pim timer hello interval |
The default setting is 30 seconds. |
|
4. Set the triggered hello delay. |
pim triggered-hello-delay delay |
The default setting is 5 seconds. |
|
5. Set the join/prune interval. |
pim timer join-prune interval |
The default setting is 60 seconds. This configuration takes effect after the current interval ends. |
|
6. Set the joined/pruned state holdtime. |
pim holdtime join-prune time |
The default setting is 210 seconds. |
Setting the maximum size of a join or prune message
The loss of an oversized join or prune message might result in loss of massive information. You can set a small value for the size of a join or prune message to reduce the impact.
To set the maximum size of a join or prune message:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter PIM view. |
pim [ vpn-instance vpn-instance-name ] |
N/A |
|
3. Set the maximum size of a join or prune message. |
jp-pkt-size size |
The default setting is 8100 bytes. |
Enabling BFD for PIM
If a DR on a shared-media network fails, a new DR election process does not start until the DR ages out. In addition, it might take a long period of time before other routers detect the link failures and trigger a new DR election. To start a new DR election process immediately after the original DR fails, enable BFD for PIM to detect link failures among PIM neighbors.
You must enable BFD for PIM on all PIM routers on a shared-media network. For more information about BFD, see High Availability Configuration Guide.
You must enable PIM-DM or PIM-SM on an interface before you configure this feature on the interface.
To enable BFD for PIM:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter interface view. |
interface interface-type interface-number |
N/A |
|
3. Enable BFD for PIM. |
pim bfd enable |
By default, BFD is disabled for PIM. |
Enabling PIM passive mode
To guard against PIM hello spoofing, you can enable PIM passive mode on a receiver-side interface. The PIM passive interface cannot receive or forward PIM protocol messages (excluding register, register-stop and C-RP-Adv messages), and it acts as the DR on the subnet.
Configuration restrictions and guidelines
When you enable PIM passive mode, follow these restrictions and guidelines:
· This feature takes effect only when PIM-DM or PIM-SM is enabled on the interface.
· To avoid duplicate multicast data transmission and flow loop, do not enable this feature on a shared-media LAN with multiple PIM routers.
Configuration procedure
To enable PIM passive mode on an interface:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter interface view. |
interface interface-type interface-number |
N/A |
|
3. Enable PIM passive mode on the interface. |
pim passive |
By default, PIM passive mode is disabled on an interface. |
Enabling PIM NSR
This feature enables PIM to back up protocol state information and data, including PIM neighbor information and routes, from the active process to the standby process. The standby process immediately takes over when the active process fails. Use this feature to avoid route flapping and forwarding interruption for PIM when an active/standby switchover occurs.
To enable PIM NSR:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable PIM NSR. |
pim non-stop-routing |
By default, PIM NSR is disabled. |
Enabling SNMP notifications for PIM
To report critical PIM events to an NMS, enable SNMP notifications for PIM. For PIM event notifications to be sent correctly, you must also configure SNMP as described in Network Management and Monitoring Configuration Guide.
To enable SNMP notifications for PIM:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable SNMP notifications for PIM. |
snmp-agent trap enable pim [ candidate-bsr-win-election | elected-bsr-lost-election | neighbor-loss ] * |
By default, SNMP notifications for PIM are enabled. |
Setting a DSCP value for outgoing PIM messages
To control the transmission preference of outgoing PIM messages, set a DSCP value for outgoing PIM messages.
To set a DSCP value for outgoing PIM messages:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter PIM view. |
pim [ vpn-instance vpn-instance-name ] |
N/A |
|
3. Set a DSCP value for outgoing PIM messages. |
dscp dscp-value |
By default, the DSCP value for outgoing PIM messages is 48. |
Displaying and maintaining PIM
Execute display commands in any view and reset commands in user view.
|
Task |
Command |
|
Display register-tunnel interface information. |
display interface [ register-tunnel [ interface-number ] ] [ brief [ description | down ] ] |
|
Display BSR information in the PIM-SM domain. |
display pim [ vpn-instance vpn-instance-name ] bsr-info |
|
Display information about the routes used by PIM. |
display pim [ vpn-instance vpn-instance-name ] claimed-route [ source-address ] |
|
Display C-RP information in the PIM-SM domain. |
display pim [ vpn-instance vpn-instance-name ] c-rp [ local ] |
|
Display PIM information on an interface. |
display pim [ vpn-instance vpn-instance-name ] interface [ interface-type interface-number ] [ verbose ] |
|
Display PIM neighbor information. |
display pim [ vpn-instance vpn-instance-name ] neighbor [ neighbor-address | interface interface-type interface-number | verbose ] * |
|
Display PIM routing entries. |
display pim [ vpn-instance vpn-instance-name ] routing-table [ group-address [ mask { mask-length | mask } ] | source-address [ mask { mask-length | mask } ] | flags flag-value | fsm | incoming-interface interface-type interface-number | mode mode-type | outgoing-interface { exclude | include | match } interface-type interface-number ] * |
|
Display RP information in the PIM-SM domain. |
display pim [ vpn-instance vpn-instance-name ] rp-info [ group-address ] |
|
Display statistics for PIM packets. |
display pim statistics |
PIM configuration examples
PIM-DM configuration example
Network requirements
As shown in Figure 48:
· OSPF runs on the network.
· VOD streams are sent to receiver hosts in multicast. The receiver groups of different organizations form stub networks, and one or more receiver hosts exist on each stub network.
· The entire PIM domain operates in the dense mode.
· Host A and Host C are multicast receivers on two stub networks.
· IGMPv2 runs between Switch A and N1, and between Switch B, Switch C, and N2.
Table 7 Interface and IP address assignment
|
Device |
Interface |
IP address |
Device |
Interface |
IP address |
|
Switch A |
Vlan-int100 |
10.110.1.1/24 |
Switch C |
Vlan-int102 |
192.168.3.1/24 |
|
Switch A |
Vlan-int103 |
192.168.1.1/24 |
Switch D |
Vlan-int300 |
10.110.5.1/24 |
|
Switch B |
Vlan-int200 |
10.110.2.1/24 |
Switch D |
Vlan-int103 |
192.168.1.2/24 |
|
Switch B |
Vlan-int101 |
192.168.2.1/24 |
Switch D |
Vlan-int101 |
192.168.2.2/24 |
|
Switch C |
Vlan-int200 |
10.110.2.2/24 |
Switch D |
Vlan-int102 |
192.168.3.2/24 |
Configuration procedure
1. Assign an IP address and subnet mask for each interface, as shown in Figure 48. (Details not shown.)
2. Configure OSPF on the switches in the PIM-DM domain. (Details not shown.)
3. Enable IP multicast routing, IGMP, and PIM-DM:
# On Switch A, enable IP multicast routing.
<SwitchA> system-view
[SwitchA] multicast routing
[SwitchA-mrib] quit
# Enable IGMP on VLAN-interface 100 (the interface that connects to the stub network).
[SwitchA] interface vlan-interface 100
[SwitchA-Vlan-interface100] igmp enable
[SwitchA-Vlan-interface100] quit
# Enable PIM-DM on VLAN-interface 103.
[SwitchA] interface vlan-interface 103
[SwitchA-Vlan-interface103] pim dm
[SwitchA-Vlan-interface103] quit
# Enable IP multicast routing, IGMP, and PIM-DM on Switch B and Switch C in the same way Switch A is configured. (Details not shown.)
# On Switch D, enable IP multicast routing, and enable PIM-DM on each interface.
<SwitchD> system-view
[SwitchD] multicast routing
[SwitchD-mrib] quit
[SwitchD] interface vlan-interface 300
[SwitchD-Vlan-interface300] pim dm
[SwitchD-Vlan-interface300] quit
[SwitchD] interface vlan-interface 103
[SwitchD-Vlan-interface103] pim dm
[SwitchD-Vlan-interface103] quit
[SwitchD] interface vlan-interface 101
[SwitchD-Vlan-interface101] pim dm
[SwitchD-Vlan-interface101] quit
[SwitchD] interface vlan-interface 102
[SwitchD-Vlan-interface102] pim dm
[SwitchD-Vlan-interface102] quit
Verifying the configuration
# Display PIM information on Switch D.
[SwitchD] display pim interface
Interface NbrCnt HelloInt DR-Pri DR-Address
Vlan300 0 30 1 10.110.5.1 (local)
Vlan103 1 30 1 192.168.1.2 (local)
Vlan101 1 30 1 192.168.2.2 (local)
Vlan102 1 30 1 192.168.3.2 (local)
# Display PIM neighboring relationships on Switch D.
[SwitchD] display pim neighbor
Total Number of Neighbors = 3
Neighbor Interface Uptime Expires Dr-Priority Mode
192.168.1.1 Vlan103 00:02:22 00:01:27 1
192.168.2.1 Vlan101 00:00:22 00:01:29 3
192.168.3.1 Vlan102 00:00:23 00:01:31 5
# Send an IGMP report from Host A to join multicast group 225.1.1.1. (Details not shown.)
# Send multicast data from multicast source 10.110.5.100/24 to multicast group 225.1.1.1. (Details not shown.)
# Display PIM routing entries on Switch A.
[SwitchA] display pim routing-table
Total 1 (*, G) entry; 1 (S, G) entry
(*, 225.1.1.1)
Protocol: pim-dm, Flag: WC
UpTime: 00:04:25
Upstream interface: NULL
Upstream neighbor: NULL
RPF prime neighbor: NULL
Downstream interface(s) information:
Total number of downstreams: 1
1: Vlan-interface100
Protocol: igmp, UpTime: 00:04:25, Expires: -
(10.110.5.100, 225.1.1.1)
Protocol: pim-dm, Flag: ACT
UpTime: 00:06:14
Upstream interface: Vlan-interface103
Upstream neighbor: 192.168.1.2
RPF prime neighbor: 192.168.1.2
Downstream interface(s) information:
Total number of downstreams: 1
1: Vlan-interface100
Protocol: pim-dm, UpTime: 00:04:25, Expires: -
# Display PIM routing entries on Switch D.
[SwitchD] display pim routing-table
Total 0 (*, G) entry; 1 (S, G) entry
(10.110.5.100, 225.1.1.1)
Protocol: pim-dm, Flag: LOC ACT
UpTime: 00:03:27
Upstream interface: Vlan-interface300
Upstream neighbor: NULL
RPF prime neighbor: NULL
Downstream interface(s) information:
Total number of downstreams: 2
1: Vlan-interface103
Protocol: pim-dm, UpTime: 00:03:27, Expires: -
2: Vlan-interface102
Protocol: pim-dm, UpTime: 00:03:27, Expires: -
The output shows the following information:
· Switches on the SPT path (Switch A and Switch D) have the correct (S, G) entries.
· Switch A has the correct (*, G) entry.
PIM-SM non-scoped zone configuration example
Network requirements
As shown in Figure 49:
· OSPF runs on the network.
· VOD streams are sent to receiver hosts in multicast. The receivers of different subnets form stub networks, and a minimum of one receiver host exist on each stub network.
· The entire PIM-SM domain contains only one BSR.
· Host A and Host C are multicast receivers on two stub networks N1 and N2.
· Specify VLAN-interface 102 on Switch E as a C-BSR and a C-RP. The C-RP is designated to multicast group range 225.1.1.0/24. Specify VLAN-interface 101 of Switch D as the static RP on all the switches to back up the dynamic RP.
· IGMPv2 runs between Switch A and N1, and between Switch B, Switch C, and N2.
Table 8 Interface and IP address assignment
|
Device |
Interface |
IP address |
Device |
Interface |
IP address |
|
Switch A |
Vlan-int100 |
10.110.1.1/24 |
Switch D |
Vlan-int300 |
10.110.5.1/24 |
|
Switch A |
Vlan-int101 |
192.168.1.1/24 |
Switch D |
Vlan-int101 |
192.168.1.2/24 |
|
Switch A |
Vlan-int102 |
192.168.9.1/24 |
Switch D |
Vlan-int105 |
192.168.4.2/24 |
|
Switch B |
Vlan-int200 |
10.110.2.1/24 |
Switch E |
Vlan-int104 |
192.168.3.2/24 |
|
Switch B |
Vlan-int103 |
192.168.2.1/24 |
Switch E |
Vlan-int103 |
192.168.2.2/24 |
|
Switch C |
Vlan-int200 |
10.110.2.2/24 |
Switch E |
Vlan-int102 |
192.168.9.2/24 |
|
Switch C |
Vlan-int104 |
192.168.3.1/24 |
Switch E |
Vlan-int105 |
192.168.4.1/24 |
Configuration procedure
1. Assign an IP address and subnet mask to each interface, as shown in Figure 49. (Details not shown.)
2. Configure OSPF on all switches in the PIM-SM domain. (Details not shown.)
3. Enable IP multicast routing, and enable IGMP and PIM-SM:
# On Switch A, enable IP multicast routing.
<SwitchA> system-view
[SwitchA] multicast routing
[SwitchA-mrib] quit
# Enable IGMP on VLAN-interface 100 (the interface that connects to the stub network).
[SwitchA] interface vlan-interface 100
[SwitchA-Vlan-interface100] igmp enable
[SwitchA-Vlan-interface100] quit
# Enable PIM-SM on the other interfaces.
[SwitchA] interface vlan-interface 101
[SwitchA-Vlan-interface101] pim sm
[SwitchA-Vlan-interface101] quit
[SwitchA] interface vlan-interface 102
[SwitchA-Vlan-interface102] pim sm
[SwitchA-Vlan-interface102] quit
# Enable IP multicast routing, IGMP, and PIM-SM on Switch B and Switch C in the same way Switch A is configured. (Details not shown.)
# Enable IP multicast routing and PIM-SM on Switch D and Switch E in the same way Switch A is configured. (Details not shown.)
4. Configure C-BSRs, C-RPs, and the static RP:
# On Switch E, configure the service scope of RP advertisements.
<SwitchE> system-view
[SwitchE] acl basic 2005
[SwitchE-acl-ipv4-basic-2005] rule permit source 225.1.1.0 0.0.0.255
[SwitchE-acl-ipv4-basic-2005] quit
# Configure VLAN-interface 102 as a C-BSR and a C-RP.
[SwitchE] pim
[SwitchE-pim] c-bsr 192.168.9.2
[SwitchE-pim] c-rp 192.168.9.2 group-policy 2005
# Configure VLAN-interface 101 of Switch D as the static RP.
[SwitchE-pim] static-rp 192.168.1.2
[SwitchE-pim] quit
# On Switch A, configure VLAN-interface 101 of Switch D as the static RP.
[SwitchA] pim
[SwitchA-pim] static-rp 192.168.1.2
[SwitchA-pim] quit
# Configure the static RP on Switch B, Switch C, and Switch D in the same way Switch A is configured. (Details not shown.)
Verifying the configuration
# Display PIM information on Switch A.
[SwitchA] display pim interface
Interface NbrCnt HelloInt DR-Pri DR-Address
Vlan100 0 30 1 10.110.1.1 (local)
Vlan101 1 30 1 192.168.1.2
Vlan102 1 30 1 192.168.9.2
# Display BSR information on Switch A.
[SwitchA] display pim bsr-info
Scope: non-scoped
State: Accept Preferred
Bootstrap timer: 00:01:44
Elected BSR address: 192.168.9.2
Priority: 64
Hash mask length: 30
Uptime: 00:11:18
# Display BSR information on Switch E.
[SwitchE] display pim bsr-info
Scope: non-scoped
State: Elected
Bootstrap timer: 00:01:44
Elected BSR address: 192.168.9.2
Priority: 64
Hash mask length: 30
Uptime: 00:11:18
Candidate BSR address: 192.168.9.2
Priority: 64
Hash mask length: 30
# Display RP information on Switch A.
[SwitchA] display pim rp-info
BSR RP information:
Scope: non-scoped
Group/MaskLen: 225.1.1.0/24
RP address Priority HoldTime Uptime Expires
192.168.9.2 192 180 00:51:45 00:02:22
Static RP information:
RP address ACL Mode Preferred
192.168.1.2 ---- pim-sm No
PIM-SM admin-scoped zone configuration example
Network requirements
As shown in Figure 50:
· OSPF runs on the network.
· VOD streams are sent to receiver hosts in multicast. The entire PIM-SM domain is divided into admin-scoped zone 1, admin-scoped zone 2, and the global-scoped zone. Switch B, Switch C, and Switch D are ZBRs of the three zones, respectively.
· Source 1 and Source 2 send different multicast data to the multicast group 239.1.1.1. Host A receives the multicast data only from Source 1, and Host B receives the multicast data only from Source 2. Source 3 sends multicast data to multicast group 224.1.1.1. Host C is a multicast receiver for the multicast group 224.1.1.1.
· VLAN-interface 101 of Switch B acts as a C-BSR and a C-RP for admin-scoped zone 1, and VLAN-interface 105 of Switch D acts as a C-BSR and a C-RP for admin-scoped zone 2. Both of the two interfaces are designated to multicast group range 239.0.0.0/8. VLAN-interface 109 of Switch F acts as a C-BSR and a C-RP for the global-scoped zone, and is designated to all the multicast groups that are not in the range 239.0.0.0/8.
· IGMPv2 runs between Switch A, Switch E, Switch I, and the receivers that directly connect to them, respectively.
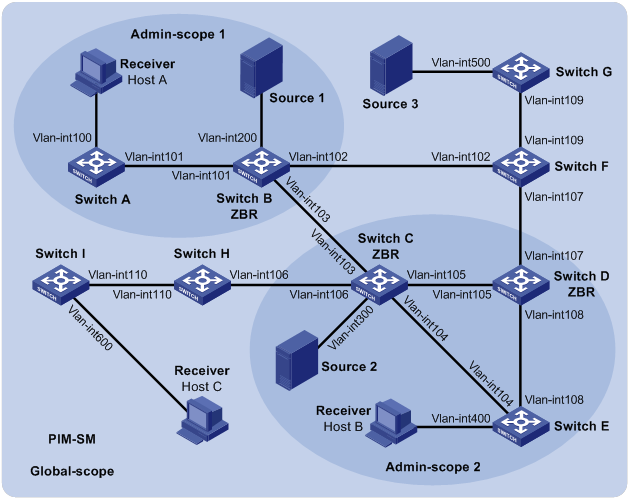
Table 9 Interface and IP address assignment
|
Device |
Interface |
IP address |
Device |
Interface |
IP address |
|
Switch A |
Vlan-int100 |
192.168.1.1/24 |
Switch D |
Vlan-int105 |
10.110.5.2/24 |
|
Switch A |
Vlan-int101 |
10.110.1.1/24 |
Switch D |
Vlan-int108 |
10.110.7.1/24 |
|
Switch B |
Vlan-int200 |
192.168.2.1/24 |
Switch D |
Vlan-int107 |
10.110.8.1/24 |
|
Switch B |
Vlan-int101 |
10.110.1.2/24 |
Switch E |
Vlan-int400 |
192.168.4.1/24 |
|
Switch B |
Vlan-int103 |
10.110.2.1/24 |
Switch E |
Vlan-int104 |
10.110.4.2/24 |
|
Switch B |
Vlan-int102 |
10.110.3.1/24 |
Switch E |
Vlan-int108 |
10.110.7.2/24 |
|
Switch C |
Vlan-int300 |
192.168.3.1/24 |
Switch F |
Vlan-int109 |
10.110.9.1/24 |
|
Switch C |
Vlan-int104 |
10.110.4.1/24 |
Switch F |
Vlan-int107 |
10.110.8.2/24 |
|
Switch C |
Vlan-int105 |
10.110.5.1/24 |
Switch F |
Vlan-int102 |
10.110.3.2/24 |
|
Switch C |
Vlan-int103 |
10.110.2.2/24 |
Switch G |
Vlan-int500 |
192.168.5.1/24 |
|
Switch C |
Vlan-int106 |
10.110.6.1/24 |
Switch G |
Vlan-int109 |
10.110.9.2/24 |
|
Switch H |
Vlan-int110 |
10.110.10.1/24 |
Source 1 |
— |
192.168.2.10/24 |
|
Switch H |
Vlan-int106 |
10.110.6.2/24 |
Source 2 |
— |
192.168.3.10/24 |
|
Switch I |
Vlan-int600 |
192.168.6.1/24 |
Source 3 |
— |
192.168.5.10/24 |
|
Switch I |
Vlan-int110 |
10.110.10.2/24 |
|
|
|
Configuration procedure
1. Assign an IP address and subnet mask to each interface, as shown in Figure 50. (Details not shown.)
2. Configure OSPF on all switches in the PIM-SM domain. (Details not shown.)
3. Enable IP multicast routing, and enable IGMP and PIM-SM:
# On Switch A, enable IP multicast routing.
<SwitchA> system-view
[SwitchA] multicast routing
[SwitchA-mrib] quit
# Enable IGMP on the receiver-side interface (VLAN-interface 100).
[SwitchA] interface vlan-interface 100
[SwitchA-Vlan-interface100] igmp enable
[SwitchA-Vlan-interface100] quit
# Enable PIM-SM on VLAN-interface 101.
[SwitchA] interface vlan-interface 101
[SwitchA-Vlan-interface101] pim sm
[SwitchA-Vlan-interface101] quit
# Enable IP multicast routing, IGMP, and PIM-SM on Switch E and Switch I in the same way Switch A is configured. (Details not shown.)
# On Switch B, enable IP multicast routing, and enable PIM-SM on each interface.
<SwitchB> system-view
[SwitchB] multicast routing
[SwitchB-mrib] quit
[SwitchB] interface vlan-interface 200
[SwitchB-Vlan-interface200] pim sm
[SwitchB-Vlan-interface200] quit
[SwitchB] interface vlan-interface 101
[SwitchB-Vlan-interface101] pim sm
[SwitchB-Vlan-interface101] quit
[SwitchB] interface vlan-interface 102
[SwitchB-Vlan-interface102] pim sm
[SwitchB-Vlan-interface102] quit
[SwitchB] interface vlan-interface 103
[SwitchB-Vlan-interface103] pim sm
[SwitchB-Vlan-interface103] quit
# Enable IP multicast routing and PIM-SM on Switch C, Switch D, Switch F, Switch G, and Switch H in the same way Switch B is configured. (Details not shown.)
4. Configure admin-scoped zone boundaries:
# On Switch B, configure VLAN-interface 102 and VLAN-interface 103 as the boundaries of admin-scoped zone 1.
[SwitchB] interface vlan-interface 102
[SwitchB-Vlan-interface102] multicast boundary 239.0.0.0 8
[SwitchB-Vlan-interface102] quit
[SwitchB] interface vlan-interface 103
[SwitchB-Vlan-interface103] multicast boundary 239.0.0.0 8
[SwitchB-Vlan-interface103] quit
# On Switch C, configure VLAN-interface 103 and VLAN-interface 106 as the boundaries of admin-scoped zone 2.
<SwitchC> system-view
[SwitchC] interface vlan-interface 103
[SwitchC-Vlan-interface103] multicast boundary 239.0.0.0 8
[SwitchC-Vlan-interface103] quit
[SwitchC] interface vlan-interface 106
[SwitchC-Vlan-interface106] multicast boundary 239.0.0.0 8
[SwitchC-Vlan-interface106] quit
# On Switch D, configure VLAN-interface 107 as the boundary of admin-scoped zone 2.
<SwitchD> system-view
[SwitchD] interface vlan-interface 107
[SwitchD-Vlan-interface107] multicast boundary 239.0.0.0 8
[SwitchD-Vlan-interface107] quit
5. Configure C-BSRs and C-RPs:
# On Switch B, configure the service scope of RP advertisements.
[SwitchB] acl basic 2001
[SwitchB-acl-ipv4-basic-2001] rule permit source 239.0.0.0 0.255.255.255
[SwitchB-acl-ipv4-basic-2001] quit
# Configure VLAN-interface 101 as a C-BSR and a C-RP for admin-scoped zone 1.
[SwitchB] pim
[SwitchB-pim] c-bsr 10.110.1.2 scope 239.0.0.0 8
[SwitchB-pim] c-rp 10.110.1.2 group-policy 2001
[SwitchB-pim] quit
# On Switch D, configure the service scope of RP advertisements.
[SwitchD] acl basic 2001
[SwitchD-acl-ipv4-basic-2001] rule permit source 239.0.0.0 0.255.255.255
[SwitchD-acl-ipv4-basic-2001] quit
# Configure VLAN-interface 105 as a C-BSR and a C-RP for admin-scoped zone 2.
[SwitchD] pim
[SwitchD-pim] c-bsr 10.110.5.2 scope 239.0.0.0 8
[SwitchD-pim] c-rp 10.110.5.2 group-policy 2001
[SwitchD-pim] quit
# On Switch F, configure VLAN-interface 109 as a C-BSR and a C-RP for the global-scoped zone.
<SwitchF> system-view
[SwitchF] pim
[SwitchF-pim] c-bsr 10.110.9.1
[SwitchF-pim] c-rp 10.110.9.1
[SwitchF-pim] quit
Verifying the configuration
# Display BSR information on Switch B.
[SwitchB] display pim bsr-info
Scope: non-scoped
State: Accept Preferred
Bootstrap timer: 00:01:44
Elected BSR address: 10.110.9.1
Priority: 64
Hash mask length: 30
Uptime: 00:01:45
Scope: 239.0.0.0/8
State: Elected
Bootstrap timer: 00:00:06
Elected BSR address: 10.110.1.2
Priority: 64
Hash mask length: 30
Uptime: 00:04:54
Candidate BSR address: 10.110.1.2
Priority: 64
Hash mask length: 30
# Display BSR information on Switch D.
[SwitchD] display pim bsr-info
Scope: non-scoped
State: Accept Preferred
Bootstrap timer: 00:01:44
Elected BSR address: 10.110.9.1
Priority: 64
Hash mask length: 30
Uptime: 00:01:45
Scope: 239.0.0.0/8
State: Elected
Bootstrap timer: 00:01:12
Elected BSR address: 10.110.5.2
Priority: 64
Hash mask length: 30
Uptime: 00:03:48
Candidate BSR address: 10.110.5.2
Priority: 64
Hash mask length: 30
# Display BSR information on Switch F.
[SwitchF] display pim bsr-info
Scope: non-scoped
State: Elected
Bootstrap timer: 00:00:49
Elected BSR address: 10.110.9.1
Priority: 64
Hash mask length: 30
Uptime: 00:11:11
Candidate BSR address: 10.110.9.1
Priority: 64
Hash mask length: 30
# Display RP information on Switch B.
[SwitchB] display pim rp-info
BSR RP information:
Scope: non-scoped
Group/MaskLen: 224.0.0.0/4
RP address Priority HoldTime Uptime Expires
10.110.9.1 192 180 00:03:39 00:01:51
Scope: 239.0.0.0/8
Group/MaskLen: 239.0.0.0/8
RP address Priority HoldTime Uptime Expires
10.110.1.2 (local) 192 180 00:07:44 00:01:51
# Display RP information on Switch D.
[SwitchD] display pim rp-info
BSR RP information:
Scope: non-scoped
Group/MaskLen: 224.0.0.0/4
RP address Priority HoldTime Uptime Expires
10.110.9.1 192 180 00:03:42 00:01:48
Scope: 239.0.0.0/8
Group/MaskLen: 239.0.0.0/8
RP address Priority HoldTime Uptime Expires
10.110.5.2 (local) 192 180 00:06:54 00:02:41
# Display RP information on Switch F.
[SwitchF] display pim rp-info
BSR RP information:
Scope: non-scoped
Group/MaskLen: 224.0.0.0/4
RP address Priority HoldTime Uptime Expires
10.110.9.1 (local) 192 180 00:00:32 00:01:58
PIM-SSM configuration example
Network requirements
As shown in Figure 51:
· OSPF runs on the network.
· The receivers receive VOD information through multicast. The receiver groups of different organizations form stub networks, and one or more receiver hosts exist on each stub network.
· The entire PIM domain operates in the SSM mode.
· Host A and Host C are multicast receivers on two stub networks.
· The SSM group range is 232.1.1.0/24.
· IGMPv3 runs between Switch A and N1, and between Switch B, Switch C, and N2.
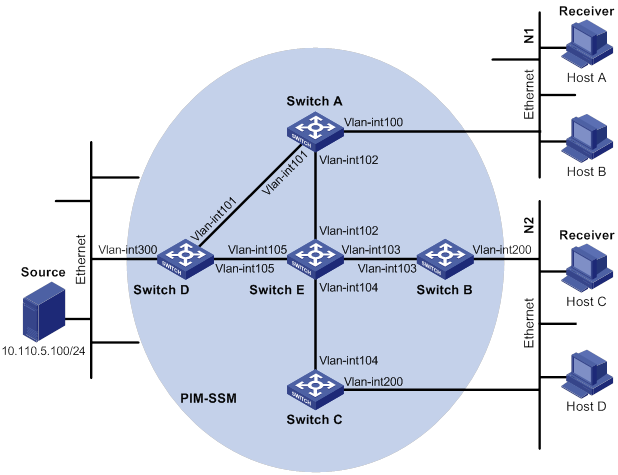
Table 10 Interface and IP address assignment
|
Device |
Interface |
IP address |
Device |
Interface |
IP address |
|
Switch A |
Vlan-int100 |
10.110.1.1/24 |
Switch D |
Vlan-int300 |
10.110.5.1/24 |
|
Switch A |
Vlan-int101 |
192.168.1.1/24 |
Switch D |
Vlan-int101 |
192.168.1.2/24 |
|
Switch A |
Vlan-int102 |
192.168.9.1/24 |
Switch D |
Vlan-int105 |
192.168.4.2/24 |
|
Switch B |
Vlan-int200 |
10.110.2.1/24 |
Switch E |
Vlan-int104 |
192.168.3.2/24 |
|
Switch B |
Vlan-int103 |
192.168.2.1/24 |
Switch E |
Vlan-int103 |
192.168.2.2/24 |
|
Switch C |
Vlan-int200 |
10.110.2.2/24 |
Switch E |
Vlan-int102 |
192.168.9.2/24 |
|
Switch C |
Vlan-int104 |
192.168.3.1/24 |
Switch E |
Vlan-int105 |
192.168.4.1/24 |
Configuration procedure
1. Assign an IP address and subnet mask to each interface, as shown in Figure 51. (Details not shown.)
2. Configure OSPF on the switches in the PIM-SSM domain. (Details not shown.)
3. Enable IP multicast routing, IGMP, and PIM-SM:
# On Switch A, enable IP multicast routing.
<SwitchA> system-view
[SwitchA] multicast routing
[SwitchA-mrib] quit
# Enable IGMPv3 on VLAN-interface 100 (the interface that connects to the stub network).
[SwitchA] interface vlan-interface 100
[SwitchA-Vlan-interface100] igmp enable
[SwitchA-Vlan-interface100] igmp version 3
[SwitchA-Vlan-interface100] quit
# Enable PIM-SM on the other interfaces.
[SwitchA] interface vlan-interface 101
[SwitchA-Vlan-interface101] pim sm
[SwitchA-Vlan-interface101] quit
[SwitchA] interface vlan-interface 102
[SwitchA-Vlan-interface102] pim sm
[SwitchA-Vlan-interface102] quit
# Enable IP multicast routing, IGMP, and PIM-SM on Switch B and Switch C in the same way Switch A is configured. (Details not shown.)
# Enable IP multicast routing and PIM-SM on Switch D and Switch E in the same way Switch A is configured. (Details not shown.)
4. Configure the SSM group range:
# Configure the SSM group range 232.1.1.0/24 on Switch A.
[SwitchA] acl basic 2000
[SwitchA-acl-ipv4-basic-2000] rule permit source 232.1.1.0 0.0.0.255
[SwitchA-acl-ipv4-basic-2000] quit
[SwitchA] pim
[SwitchA-pim] ssm-policy 2000
[SwitchA-pim] quit
# Configure the SSM group range on Switch B, Switch C, Switch D and Switch E in the same way Switch A is configured. (Details not shown.)
Verifying the configuration
# Display PIM information on Switch A.
[SwitchA] display pim interface
Interface NbrCnt HelloInt DR-Pri DR-Address
Vlan100 0 30 1 10.110.1.1 (local)
Vlan101 1 30 1 192.168.1.2
Vlan102 1 30 1 192.168.9.2
# Send an IGMPv3 report from Host A to join the multicast source and group (10.110.5.100/24, 232.1.1.1). (Details not shown.)
# Display the PIM routing table on Switch A.
[SwitchA] display pim routing-table
Total 0 (*, G) entry; 1 (S, G) entry
(10.110.5.100, 232.1.1.1)
Protocol: pim-ssm, Flag:
UpTime: 00:13:25
Upstream interface: Vlan-interface101
Upstream neighbor: 192.168.1.2
RPF prime neighbor: 192.168.1.2
Downstream interface(s) information:
Total number of downstreams: 1
1: Vlan-interface100
Protocol: igmp, UpTime: 00:13:25, Expires: 00:03:25
# Display the PIM routing table on Switch D.
[SwitchD] display pim routing-table
Total 0 (*, G) entry; 1 (S, G) entry
(10.110.5.100, 232.1.1.1)
Protocol: pim-ssm, Flag: LOC
UpTime: 00:12:05
Upstream interface: Vlan-interface300
Upstream neighbor: NULL
RPF prime neighbor: NULL
Downstream interface(s) information:
Total number of downstreams: 1
1: Vlan-interface105
Protocol: pim-ssm, UpTime: 00:12:05, Expires: 00:03:25
The output shows that switches on the SPT path (Switch A and Switch D) have generated the correct (S, G) entries.
Troubleshooting PIM
A multicast distribution tree cannot be correctly built
Symptom
No multicast forwarding entries are established on the routers (including routers directly connected with multicast sources or receivers) in a PIM network. This means that a multicast distribution tree cannot be built correctly.
Solution
To resolve the problem:
1. Use display ip routing-table to verify that a unicast route to the multicast source or the RP is available.
2. Use display pim interface to verify PIM information on each interface, especially on the RPF interface. If PIM is not enabled on the interfaces, use pim dm or pim sm to enable PIM-DM or PIM-SM for the interfaces.
3. Use display pim neighbor to verify that the RPF neighbor is a PIM neighbor.
4. Verify that PIM and IGMP are enabled on the interfaces that directly connect to the multicast sources or the receivers.
5. Use display pim interface verbose to verify that the same PIM mode is enabled on the RPF interface on a router and the connected interface of the router's RPF neighbor.
6. Use display current-configuration to verify that the same PIM mode is enabled on all routers. For PIM-SM, verify that the BSR and C-RPs are correctly configured.
7. If the problem persists, contact H3C Support.
Multicast data is abnormally terminated on an intermediate router
Symptom
An intermediate router can receive multicast data successfully, but the data cannot reach the last-hop router. An interface on the intermediate router receives multicast data but does not create an (S, G) entry in the PIM routing table.
Solution
To resolve the problem:
1. Use display current-configuration to verify the multicast forwarding boundary settings. Use multicast boundary to change the multicast forwarding boundary settings to make the multicast packet able to cross the boundary.
2. Use display current-configuration to verify the multicast source policy. Change the ACL rule defined in the source-policy command so that the source/group address of the multicast data can pass ACL filtering.
3. If the problem persists, contact H3C Support.
An RP cannot join an SPT in PIM-SM
Symptom
An RPT cannot be correctly built, or an RP cannot join the SPT toward the multicast source.
Solution
To resolve the problem:
1. Use display ip routing-table to verify that a unicast route to the RP is available on each router.
2. Use display pim rp-info to verify that the dynamic RP information is consistent on all routers.
3. Use display pim rp-info to verify that the same static RPs are configured on all routers on the network.
4. If the problem persists, contact H3C Support.
An RPT cannot be built or multicast source registration fails in PIM-SM
Symptom
The C-RPs cannot unicast advertisement messages to the BSR. The BSR does not advertise BSMs containing C-RP information and has no unicast route to any C-RP. An RPT cannot be correctly established, or the source-side DR cannot register the multicast source with the RP.
Solution
To resolve the problem:
1. Use display ip routing-table on each router to view routing table information. Verify that unicast routes to the C-RPs and the BSR are available on each router and that a route is available between each C-RP and the BSR.
2. Use display pim bsr-info to verify that the BSR information exists on each router.
3. Use display pim rp-info to verify that the RP information is correct on each router.
4. Use display pim neighbor to verify that PIM neighboring relationship has been correctly established among the routers.
5. If the problem persists, contact H3C Support.
Configuring MSDP
Overview
Multicast Source Discovery Protocol (MSDP) is an inter-domain multicast solution that addresses the interconnection of PIM-SM domains. It discovers multicast source information in other PIM-SM domains.
In the basic PIM-SM mode, a multicast source registers only with the RP in the local PIM-SM domain, and the multicast source information in each domain is isolated. As a result, both of the following occur:
· The RP obtains the source information only within the local domain.
· A multicast distribution tree is built only within the local domain to deliver multicast data locally.
MSDP enables the RPs of different PIM-SM domains to share their multicast source information. The local RP can then join the SPT rooted at the multicast source across the PIM-SM domains. This allows multicast data to be transmitted among different domains.
With MSDP peer relationships established between appropriate routers on the network, the RPs of different PIM-SM domains are interconnected with one another. These MSDP peers exchange source active (SA) messages, so that the multicast source information is shared among these domains.
MSDP is applicable only if the intra-domain multicast protocol is PIM-SM. MSDP takes effect only for the ASM model.
For more information about the concepts of DR, BSR, C-BSR, RP, C-RP, SPT, and RPT mentioned in this document, see "Configuring PIM."
How MSDP works
MSDP peers
One or more pairs of MSDP peers on the network form an MSDP interconnection map. In the map, the RPs of different PIM-SM domains interconnect in a series. An SA message from an RP is relayed to all other RPs by these MSDP peers.
Figure 52 MSDP peer locations on the network
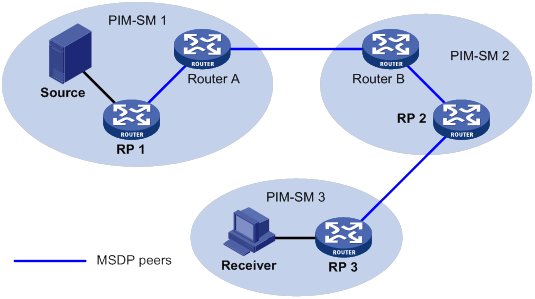
As shown in Figure 52, an MSDP peer can be created on any PIM-SM router. MSDP peers created on PIM-SM routers that assume different roles function differently.
· MSDP peers created on RPs:
? Source-side MSDP peer—MSDP peer closest to the multicast source, such as RP 1. The source-side RP creates and sends SA messages to its remote MSDP peer to notify the MSDP peer of the locally registered multicast source information.
A source-side MSDP peer must be created on the source-side RP. Otherwise, it cannot advertise the multicast source information out of the PIM-SM domain.
? Receiver-side MSDP peer—MSDP peer closest to the receivers, typically the receiver-side RP, such as RP 3. After receiving an SA message, the receiver-side MSDP peer resolves the multicast source information carried in the message. Then, it joins the SPT rooted at the multicast source across the PIM-SM domains. When multicast data from the multicast source arrives, the receiver-side MSDP peer forwards the data to the receivers along the RPT.
? Intermediate MSDP peer—MSDP peer with multiple remote MSDP peers, such as RP 2. An intermediate MSDP peer forwards SA messages received from one remote MSDP peer to other remote MSDP peers. It acts as a relay for forwarding multicast source information.
· MSDP peers created on PIM-SM routers that are not RPs:
Router A and Router B are MSDP peers on multicast routers that are not RPs. Such MSDP peers only forward SA messages.
In a PIM-SM network using the BSR mechanism, the RP is dynamically elected from C-RPs. A PIM-SM network typically has multiple C-RPs to ensure network robustness. Because the RP election result is unpredictable, MSDP peering relationships must be built between all C-RPs to always keep the winning C-RP on the MSDP interconnection map. Losing C-RPs assume the role of common PIM-SM routers on this map.
Inter-domain multicast delivery through MSDP
As shown in Figure 53, an active source (Source) exists in the domain PIM-SM 1, and RP 1 has learned the existence of Source through multicast source registration. RPs in PIM-SM 2 and PIM-SM 3 also seek the location of Source so that multicast traffic from Source can be sent to their receivers. MSDP peering relationships must be established between RP 1 and RP 3 and between RP 3 and RP 2.
Figure 53 Inter-domain multicast delivery through MSDP
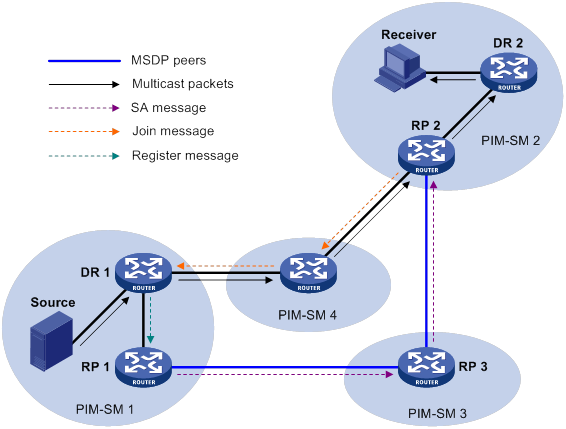
The process of implementing PIM-SM inter-domain multicast delivery by leveraging MSDP peers is as follows:
1. When the multicast source in PIM-SM 1 sends the first multicast packet to multicast group G, DR 1 encapsulates the data within a register message. It sends the register message to RP 1, and RP 1 obtains information about the multicast source.
2. As the source-side RP, RP 1 creates SA messages and periodically sends them to its MSDP peer.
An SA message contains the address of the multicast source (S), the multicast group address (G), and the address of the RP that has created this SA message (RP 1, in this example).
3. On MSDP peers, each SA message undergoes an RPF check and multicast policy-based filtering. Only SA messages that have arrived along the correct path and passed the filtering are received and forwarded. This avoids delivery loops of SA messages. In addition, you can configure MSDP peers into an MSDP mesh group to avoid SA message flooding between MSDP peers.
|
|
NOTE: An MSDP mesh group refers to a group of MSDP peers that establish MSDP peering relationships with each other and share the same group name. |
4. SA messages are forwarded from one MSDP peer to another. Finally, information about the multicast source traverses all PIM-SM domains with MSDP peers (PIM-SM 2 and PIM-SM 3, in this example).
5. After receiving the SA message that RP 1 created, RP 2 in PIM-SM 2 examines whether any receivers for the multicast group exist in the domain.
? If a receiver exists in the domain, the RPT for the multicast group G is maintained between RP 2 and the receivers. RP 2 creates an (S, G) entry and sends an (S, G) join message. The join message travels hop by hop toward the multicast source, and the SPT is established across the PIM-SM domains.
The subsequent multicast data flows to RP 2 along the SPT, and from RP 2 to the receiver-side DR along the RPT. After receiving the multicast data, the receiver-side DR determines whether to initiate an RPT-to-SPT switchover process based on its configuration.
? If no receivers exist in the domain, RP 2 neither creates an (S, G) entry nor sends a join message toward the multicast source.
In inter-domain multicasting using MSDP, once an RP gets information about a multicast source in another PIM-SM domain, it no longer relies on RPs in other PIM-SM domains. The receivers can override the RPs in other domains and directly join the multicast SPT rooted at the source.
Anycast RP through MSDP
PIM-SM requires only one active RP to serve each multicast group. If the active RP fails, the multicast traffic might be interrupted. The Anycast RP mechanism enables redundancy backup between two or more RPs by configuring multiple RPs with the same IP address for one multicast group. A multicast source registers with the closest RP or a receiver joins the closest RP to implement source information synchronization.
Anycast RP has the following benefits:
· Optimal RP path—A multicast source registers with the closest RP to build an optimal SPT. A receiver joins the closest RP to build an optimal RPT.
· Redundancy backup among RPs—When an RP fails, the RP-related sources and receiver-side DRs will register with or join their closest available RPs. This achieves redundancy backup among RPs.
Anycast RP is implemented by using either of the following methods:
· Anycast RP through PIM-SM—In this method, you can configure multiple RPs for one multicast group and add them to an Anycast RP set. For more information about Anycast RP through PIM-SM, see "Configuring PIM."
· Anycast RP through MSDP—In this method, you can configure multiple RPs with the same IP address for one multicast group and configure MSDP peering relationships between the RPs.
As shown in Figure 54, within a PIM-SM domain, a multicast source sends multicast data to multicast group G, and the receiver joins the multicast group.
To implement Anycast RP through MSDP:
a. Assign the same IP address (known as Anycast RP address, typically a private address) to an interface on Router A and Router B.
- An Anycast RP address is usually assigned to a logical interface, such as a loopback interface.
- Make sure the Anycast RP address is a host address (with the subnet mask 255.255.255.255).
b. Configure the interfaces as C-RPs.
c. Establish an MSDP peering relationship between Router A and Router B.
An MSDP peer address must be different from the Anycast RP address.
Figure 54 Anycast RP through MSDP
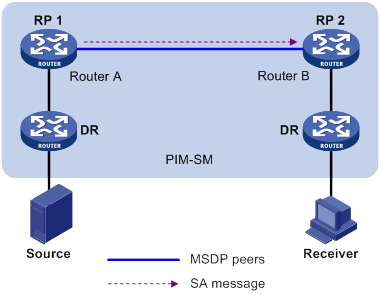
The following describes how Anycast RP through MSDP is implemented:
a. After receiving the multicast data from Source, the source-side DR registers with the closest RP (RP 1 in this example).
b. After receiving the IGMP report message from the receiver, the receiver-side DR sends a join message toward the closest RP (RP 2 in this example). An RPT rooted at this RP is established.
c. The RPs share the registered multicast source information through SA messages. After obtaining the multicast source information, RP 2 sends an (S, G) source-specific join message toward the source to create an SPT.
d. When the multicast data reaches RP 2 along the SPT, the RP forwards the data along the RPT to the receiver. After receiving the multicast data, the receiver-side DR determines whether to initiate an RPT-to-SPT switchover process based on its configuration.
MSDP peer-RPF forwarding
The MSDP peer-RPF check is used for forwarding SA messages on a network that runs MSDP. If the peer-RPF check succeeds, the SA message is accepted and forwarded. Otherwise, the SA message is discarded.
As shown in Figure 55:
· There are five ASs on the network. IGP runs within each AS, and BGP or MBGP runs between these ASs.
· Each AS contains a minimum of one PIM-SM domain, and each PIM-SM domain contains a minimum of one RP.
· MSDP peering relationship has been established among these RPs.
RP 3, RP 4, and RP 5 are in the same MSDP mesh group.
RP 6 is configured as the static RPF peer of RP 7.
Figure 55 MSDP peer-RPF forwarding
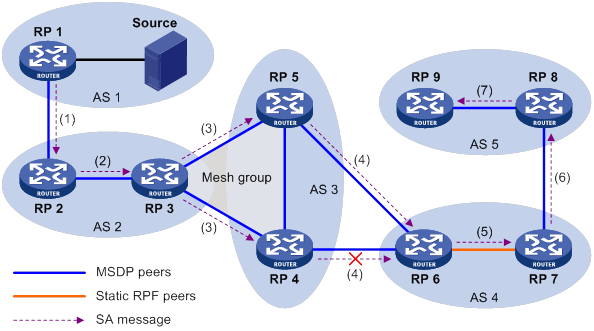
The process of peer-RPF forwarding is as follows:
1. RP 1 creates an SA message and forwards it to its peer RP 2.
2. RP 2 determines that RP 1 is the RP that creates the SA message because the RP address in the SA message is the same as that of RP 1. Then, RP 2 accepts and forwards the SA message.
3. RP 3 accepts and forwards the SA message, because RP 2 and RP 3 reside in the same AS and RP 2 is the next hop of RP 3 to RP 1.
4. RP 4 and RP 5 accept the SA message, because RP 3 is in the same mesh group with them. Then, RP 4 and RP 5 forward the SA message to their peer RP 6 rather than other members of the mesh group.
5. RP 4 and RP 5 reside in the closest AS in the route to RP 1. However, RP 6 accepts and forwards only the SA message from RP 5, because the IP address of RP 5 is higher than that of RP 4.
6. RP 7 accepts and forwards the SA message, because RP 6 is its static RPF peer.
7. RP 8 accepts and forwards the SA message, because RP 7 is the EBGP or MBGP next hop of the peer-RPF route to RP 1.
8. RP 9 accepts the SA message, because RP 8 is the only RP of RP 9.
MSDP support for VPNs
Interfaces on the multicast routers in a VPN can set up MSDP peering relationships with each other. With the SA messages exchanged between MSDP peers, the multi-instance VPN implements the forwarding of multicast data across different PIM-SM domains.
To support MSDP for VPNs, a multicast router that runs MSDP maintains an independent set of MSDP mechanism for each VPN that it supports. These mechanisms include SA message cache, peering connection, timers, sending cache, and cache for exchanging PIM messages.
One VPN is isolated from another, and MSDP and PIM-SM messages can be exchanged only within the same VPN.
Protocols and standards
· RFC 3618, Multicast Source Discovery Protocol (MSDP)
· RFC 3446, Anycast Rendezvous Point (RP) mechanism using Protocol Independent Multicast (PIM) and Multicast Source Discovery Protocol (MSDP)
MSDP configuration task list
|
Tasks at a glance |
|
Configuring basic MSDP features: · (Required.) Enabling MSDP · (Required.) Specifying an MSDP peer · (Optional.) Configuring a static RPF peer |
|
Configuring an MSDP peering connection: · (Optional.) Configuring a description for an MSDP peer · (Optional.) Configuring an MSDP mesh group · (Optional.) Controlling MSDP peering connections |
|
Configuring SA message-related parameters: · (Optional.) Enabling multicast data encapsulation in SA messages · (Optional.) Configuring the originating RP of SA messages · (Optional.) Configuring SA request messages · (Optional.) Configuring SA message policies · (Optional.) Configuring the SA cache mechanism |
|
(Optional.) Enabling MSDP NSR |
Configuring basic MSDP features
All the configuration tasks in this section should be performed on RPs in PIM-SM domains, and each of these RPs acts as an MSDP peer.
Configuration prerequisites
Before you configure basic MSDP features, complete the following tasks:
· Configure a unicast routing protocol so that all devices in the domain can interoperate at the network layer.
· Configure PIM-SM to enable intra-domain multicast.
Enabling MSDP
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable IP multicast routing and enter MRIB view. |
multicast routing [ vpn-instance vpn-instance-name ] |
By default, IP multicast routing is disabled. |
|
3. Return to system view. |
quit |
N/A |
|
4. Enable MSDP and enter MSDP view. |
msdp [ vpn-instance vpn-instance-name ] |
By default, MSDP is disabled. |
Specifying an MSDP peer
An MSDP peering relationship is identified by an address pair (the addresses of the local MSDP peer and the remote MSDP peer). To create an MSDP peering connection, you must perform the following operation on both devices that are a pair of MSDP peers.
If an MSDP peer and a BGP or MBGP peer share the same interface, specify the MSDP peer and the BGP or MBGP peer by using the same IP address.
To specify an MSDP peer:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter MSDP view. |
msdp [ vpn-instance vpn-instance-name ] |
N/A |
|
3. Specify an MSDP peer. |
peer peer-address connect-interface interface-type interface-number |
By default, no MSDP peers exist. |
Configuring a static RPF peer
This feature prevents SA messages forwarded by the static RPF peer from undertaking the RPF check. This simplifies the RPF check mechanism for SA messages.
You can configure an RP policy for the static RPF peer to filter SA messages based on the used IPv4 prefix list that specifies the RP addresses.
If only one MSDP peer is configured on a router, this MSDP peer is considered to be a static RPF peer.
To configure a static RPF peer:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter MSDP view. |
msdp [ vpn-instance vpn-instance-name ] |
N/A |
|
3. Configure a static RPF peer. |
static-rpf-peer peer-address [ rp-policy ip-prefix-name ] |
By default, no static RPF peers exist. |
Configuring an MSDP peering connection
This section describes how to configure an MSDP peering connection.
Configuration prerequisites
Before you configure an MSDP peering connection, complete the following tasks:
· Configure a unicast routing protocol so that all devices in the domain can interoperate at the network layer.
· Configure basic MSDP features.
Configuring a description for an MSDP peer
This feature helps administrators easily distinguish an MSDP peer from other MSDP peers.
To configure a description for an MSDP peer:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter MSDP view. |
msdp [ vpn-instance vpn-instance-name ] |
N/A |
|
3. Configure a description for an MSDP peer. |
peer peer-address description text |
By default, no description for an MSDP peer exists. |
Configuring an MSDP mesh group
This feature avoids SA message flooding among MSDP peers within an AS. It also simplifies the RPF check mechanism because you do not need to run BGP or MBGP between these MSDP peers.
When receiving an SA message from outside the mesh group, a member MSDP peer performs the RPF check on the SA message. If the SA message passes the RPF check, the member MSDP peer floods the message to the other members in the mesh group. When receiving an SA message from another member, the MSDP peer neither performs an RPF check on the message nor forwards the message to the other members.
To organize multiple MSDP peers in a mesh group, assign the same mesh group name to these MSDP peers. Before doing this, make sure the routers are interconnected with one another.
To configure an MSDP mesh group:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter MSDP view. |
msdp [ vpn-instance vpn-instance-name ] |
N/A |
|
3. Configure an MSDP mesh group. |
peer peer-address mesh-group name |
By default, an MSDP peer does not belong to any mesh group. If you assign an MSDP peer to multiple mesh groups, the most recent configuration takes effect. |
Controlling MSDP peering connections
MSDP peers are interconnected over TCP (port number 639). You can tear down or re-establish MSDP peering connections to control SA message exchange between the MSDP peers. When the connection between two MSDP peers is torn down, SA messages are no longer delivered between them. No attempt is made to re-establish the connection. The configuration information for the peer remains unchanged.
MSDP peers periodically send keepalive messages to each other to keep a session alive. When a session is established, an MSDP peer sends a keepalive message to its peer and starts a keepalive timer and a peer hold timer. When the keepalive timer expires, the MSDP peer sends a new keepalive message. If the MSDP peer receives an MSDP message from its peer before the peer hold timer expires, it resets the peer hold timer. Otherwise, the MSDP peer tears down the session.
A TCP connection is required when one of the following conditions exists:
· A new MSDP peer is created.
· A previously deactivated MSDP peering connection is reactivated.
· A previously failed MSDP peer attempts to resume operation.
You can change the MSDP connection retry interval to adjust the interval between MSDP peering connection attempts.
To enhance MSDP security, enable MD5 authentication for both MSDP peers to establish a TCP connection. If the MD5 authentication fails, the TCP connection cannot be established.
|
|
IMPORTANT: The MSDP peers involved in MD5 authentication must be configured with the same authentication method and key. Otherwise, the authentication fails and the TCP connection cannot be established. |
To control MSDP peering connections:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter MSDP view. |
msdp [ vpn-instance vpn-instance-name ] |
N/A |
|
3. Tear down an MSDP peering connection. |
shutdown peer-address |
By default, an MSDP peering connection is active. |
|
4. Set the keepalive timer and peer hold timer for MSDP sessions. |
timer keepalive keepalive holdtime |
By default, the keepalive timer and peer hold timer are 60 seconds and 75 seconds, respectively. This command immediately takes effect on an established session. |
|
5. Configure the MSDP connection retry interval. |
timer retry interval |
The default setting is 30 seconds. |
|
6. Configure the device to perform MD5 authentication when establishing a TCP connection with an MSDP peer. |
peer peer-address password { cipher | simple } password |
By default, the device does not perform MD5 authentication when establishing a TCP connection with an MSDP peer. |
Configuring SA message-related parameters
This section describes how to configure SA message-related parameters.
Configuration prerequisites
Before you configure SA message delivery, complete the following tasks:
· Configure a unicast routing protocol so that all devices in the domain can interoperate at the network layer.
· Configure basic MSDP features.
Enabling multicast data encapsulation in SA messages
Some multicast sources send multicast data at an interval longer than the aging time of (S, G) entries. In this case, the source-side DR must encapsulate multicast data packet-by-packet in register messages and send them to the source-side RP. The source-side RP transmits the (S, G) information to the remote RP through SA messages. Then, the remote RP sends join messages to the source-side DR and builds an SPT. Because the (S, G) entries have timed out, remote receivers can never receive the multicast data from the multicast source.
To avoid this problem, you can enable the source-side RP to encapsulate multicast data in SA messages. As a result, the source-side RP can forward the multicast data in SA messages to its remote MSDP peers. After receiving the SA messages, the remote RP decapsulates the SA messages and forwards the multicast data to the receivers in the local domain along the RPT.
To enable multicast data encapsulation in SA messages:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter MSDP view. |
msdp [ vpn-instance vpn-instance-name ] |
N/A |
|
3. Enable multicast data encapsulation in SA messages. |
encap-data-enable |
By default, an SA message contains only (S, G) entries, but not the multicast data. |
Configuring the originating RP of SA messages
This feature enables an interface to originate SA messages and to use its IP address as the RP address in SA messages. It is typically used in the Anycast-RP application.
By default, the RP address in SA messages originated by a member Anycast-RP is the Anycast-RP address. The SA messages will fail the RPF check on the other members because the RP address in SA messages is the same as the local RP address. In this case, source information cannot be exchanged within the Anycast-RP. To solve the problem, you must specify an interface other than the interface where the member Anycast-RP resides as the originating RP of SA messages.
To configure the originating RP of SA messages:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter MSDP view. |
msdp [ vpn-instance vpn-instance-name ] |
N/A |
|
3. Configure an interface as the originating RP of SA messages. |
originating-rp interface-type interface-number |
By default, SA messages are originated by the actual RPs. |
Configuring SA request messages
An SA request policy enables the device to filter SA request messages from an MSDP peer by using an ACL that specifies the multicast groups.
|
|
IMPORTANT: Before you enable the router to send SA requests, make sure you disable the SA message cache mechanism. |
To configure SA request messages:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter MSDP view. |
msdp [ vpn-instance vpn-instance-name ] |
N/A |
|
3. Enable the device to send SA request messages to an MSDP peer. |
peer peer-address request-sa-enable |
By default, after receiving a new join message, a device does not send an SA request message to any MSDP peer. Instead, it waits for the next SA message from its MSDP peer. |
|
4. Configure an SA request policy for an MSDP peer. |
peer peer-address sa-request-policy [ acl ipv4-acl-number ] |
By default, no SA request policy exists, and all SA request from an MSDP peer are permitted. |
Configuring SA message policies
To control the propagation of multicast source information, you can configure the following policies:
· SA creation policy—Limits the multicast source information advertised in SA messages. This policy enables the router to advertise (S, G) entries based on the used ACL that specifies the multicast sources and groups.
· SA incoming or outgoing policy—Limits the receipt or forwarding of SA messages. This policy enables the router to receive or forward SA messages based on the used ACL that specifies the multicast sources and groups.
By default, multicast data packets are encapsulated in SA messages and forwarded to MSDP peers only if the TTL values in the packets are larger than zero. You can set the lower TTL threshold for multicast data packets encapsulated in SA messages that are sent to an MSDP peer. Then, only multicast data packets whose TTL values are larger than or equal to the configured value are encapsulated in SA messages. Only SA messages whose TTL values are larger than or equal to the configured value are forwarded to the specified MSDP peer. This controls the multicast data packet encapsulation and limits the propagation range of the SA messages.
To configure SA message policies:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter MSDP view. |
msdp [ vpn-instance vpn-instance-name ] |
N/A |
|
3. Configure an SA creation policy. |
import-source [ acl ipv4-acl-number ] |
By default, no SA creation policies exist. |
|
4. Configure an SA incoming or outgoing policy. |
peer peer-address sa-policy { export | import } [ acl ipv4-acl-number ] |
By default, no SA incoming or outgoing policy exists. |
|
5. Set the lower TTL threshold for multicast data packets encapsulated in SA messages. |
peer peer-address minimum-ttl ttl-value |
The default setting is 0. |
Configuring the SA cache mechanism
The SA cache mechanism enables the router to locally cache (S, G) entries contained in SA messages. It reduces the time for obtaining multicast source information, but increases memory occupation.
With the SA cache mechanism enabled, when the router receives a new (*, G) join message, it searches its SA message cache first.
· If no matching (S, G) entry is found, the router waits for the SA message that its MSDP peer sends in the next cycle.
· If a matching (S, G) entry is found in the cache, the router joins the SPT rooted at S.
To protect the router against DoS attacks, you can set a limit on the number of (S, G) entries in the SA cache from an MSDP peer.
To configure the SA cache mechanism:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter MSDP view. |
msdp [ vpn-instance vpn-instance-name ] |
N/A |
|
3. Enable the SA cache mechanism. |
cache-sa-enable |
By default, the SA message cache mechanism is enabled. The device caches the (S, G) entries contained in the received SA messages. |
|
4. Set the maximum number of (S, G) entries in the SA cache from an MSDP peer. |
peer peer-address sa-cache-maximum sa-limit |
The default setting is 4294967295. |
Enabling MSDP NSR
This command enables MSDP to back up protocol state information and data, such as MSDP peer and remote multicast source information, from the active process to standby processes. A standby process seamlessly takes over when the active process fails. Use this feature to avoid forwarding interruption for MSDP when an active/standby switchover occurs.
To enable MSDP NSR:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable MSDP NSR. |
msdp non-stop-routing |
By default, MSDP NSR is disabled. |
Displaying and maintaining MSDP
Execute display commands in any view and reset commands in user view.
|
Task |
Command |
|
Display brief information about MSDP peers. |
display msdp [ vpn-instance vpn-instance-name ] brief [ state { connect | disabled | established | listen | shutdown } ] |
|
Display MSDP NSR status information. |
display msdp non-stop-routing status |
|
Display detailed status of MSDP peers. |
display msdp [ vpn-instance vpn-instance-name ] peer-status [ peer-address ] |
|
Display (S, G) entries in the SA cache. |
display msdp [ vpn-instance vpn-instance-name ] sa-cache [ group-address | source-address | as-number ] * |
|
Display the number of (S, G) entries in the SA cache. |
display msdp [ vpn-instance vpn-instance-name ] sa-count [ as-number ] |
|
Reset the TCP connection with an MSDP peer and clear statistics for the MSDP peer. |
reset msdp [ vpn-instance vpn-instance-name ] peer [ peer-address ] |
|
Delete (S, G) entries in the SA cache. |
reset msdp [ vpn-instance vpn-instance-name ] sa-cache [ group-address ] |
|
Clear statistics for an MSDP peer without resetting the TCP connection with the MSDP peer. |
reset msdp [ vpn-instance vpn-instance-name ] statistics [ peer-address ] |
MSDP configuration examples
This section provides examples of configuring MSDP on switches.
PIM-SM inter-domain multicast configuration
Network requirements
As shown in Figure 56:
· OSPF runs within AS 100 and AS 200 and BGP runs between them.
· Each PIM-SM domain has a minimum of one multicast source or receiver.
Set up MSDP peering relationships between the RPs in the PIM-SM domains to share multicast source information among the PIM-SM domains.
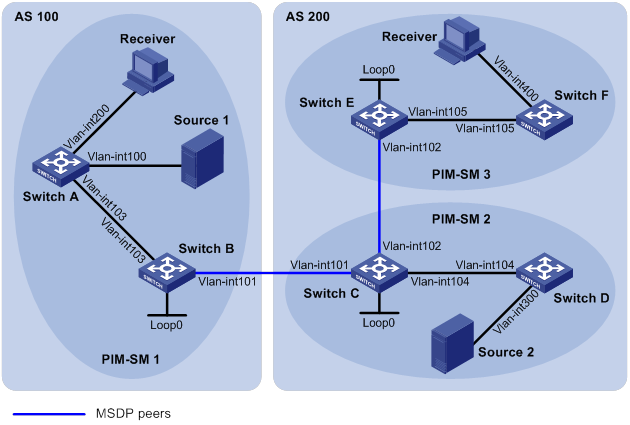
Table 11 Interface and IP address assignment
|
Interface |
IP address |
Device |
Interface |
IP address |
|
|
Switch A |
Vlan-int103 |
10.110.1.2/24 |
Switch D |
Vlan-int104 |
10.110.4.2/24 |
|
Switch A |
Vlan-int100 |
10.110.2.1/24 |
Switch D |
Vlan-int300 |
10.110.5.1/24 |
|
Switch A |
Vlan-int200 |
10.110.3.1/24 |
Switch E |
Vlan-int105 |
10.110.6.1/24 |
|
Switch B |
Vlan-int103 |
10.110.1.1/24 |
Switch E |
Vlan-int102 |
192.168.3.2/24 |
|
Switch B |
Vlan-int101 |
192.168.1.1/24 |
Switch E |
Loop0 |
3.3.3.3/32 |
|
Switch B |
Loop0 |
1.1.1.1/32 |
Switch F |
Vlan-int105 |
10.110.6.2/24 |
|
Switch C |
Vlan-int104 |
10.110.4.1/24 |
Switch F |
Vlan-int400 |
10.110.7.1/24 |
|
Switch C |
Vlan-int102 |
192.168.3.1/24 |
Source 1 |
— |
10.110.2.100/24 |
|
Switch C |
Vlan-int101 |
192.168.1.2/24 |
Source 2 |
— |
10.110.5.100/24 |
|
Switch C |
Loop0 |
2.2.2.2/32 |
Switch D |
Vlan-int104 |
10.110.4.2/24 |
Configuration procedure
1. Assign an IP address and subnet mask to each interface, as shown in Figure 56. (Details not shown.)
2. Configure OSPF on the switches in the ASs. (Details not shown.)
3. Enable IP multicast routing and PIM-SM, and configure PIM-SM domain borders:
# On Switch A, enable IP multicast routing.
<SwitchA> system-view
[SwitchA] multicast routing
[SwitchA-mrib] quit
# Enable PIM-SM on VLAN-interface 103 and VLAN-interface 100.
[SwitchA] interface vlan-interface 103
[SwitchA-Vlan-interface103] pim sm
[SwitchA-Vlan-interface103] quit
[SwitchA] interface vlan-interface 100
[SwitchA-Vlan-interface100] pim sm
[SwitchA-Vlan-interface100] quit
# Enable IGMP on the receiver-side interface (VLAN-interface 200).
[SwitchA] interface vlan-interface 200
[SwitchA-Vlan-interface200] igmp enable
[SwitchA-Vlan-interface200] quit
# Enable IP multicast routing and PIM-SM on Switch B, Switch C, Switch D, Switch E, and Switch F in the same way Switch A is configured. (Details not shown.)
# Configure a PIM domain border on Switch B.
[SwitchB] interface vlan-interface 101
[SwitchB-Vlan-interface101] pim bsr-boundary
[SwitchB-Vlan-interface101] quit
# Configure a PIM domain border on Switch C and Switch E in the same way Switch B is configured. (Details not shown.)
4. Configure C-BSRs and C-RPs:
# Configure Loopback 0 as a C-BSR and a C-RP on Switch B.
[SwitchB] pim
[SwitchB-pim] c-bsr 1.1.1.1
[SwitchB-pim] c-rp 1.1.1.1
[SwitchB-pim] quit
# Configure C-BSRs and C-RPs on Switch C and Switch E in the same way Switch B is configured. (Details not shown.)
5. Configure BGP for mutual route redistribution between BGP and OSPF:
# On Switch B, configure an EBGP peer, and redistribute OSPF routes.
[SwitchB] bgp 100
[SwitchB-bgp] router-id 1.1.1.1
[SwitchB-bgp] peer 192.168.1.2 as-number 200
[SwitchB-bgp] address-family ipv4 unicast
[SwitchB-bgp-ipv4] import-route ospf 1
[SwitchB-bgp-ipv4] peer 192.168.1.2 enable
[SwitchB-bgp-ipv4] quit
# On Switch C, configure an EBGP peer, and redistribute OSPF routes.
[SwitchC] bgp 200
[SwitchC-bgp] router-id 2.2.2.2
[SwitchC-bgp] peer 192.168.1.1 as-number 100
[SwitchC-bgp] address-family ipv4 unicast
[SwitchC-bgp-ipv4] import-route ospf 1
[SwitchC-bgp-ipv4] peer 192.168.1.1 enable
[SwitchC-bgp-ipv4] quit
# Redistribute BGP routes into OSPF on Switch B.
[SwitchB] ospf 1
[SwitchB-ospf-1] import-route bgp
[SwitchB-ospf-1] quit
# Redistribute BGP routes into OSPF on Switch C.
[SwitchB] ospf 1
[SwitchB-ospf-1] import-route bgp
[SwitchB-ospf-1] quit
6. Configure MSDP peers:
# Configure an MSDP peer on Switch B.
[SwitchB] msdp
[SwitchB-msdp] peer 192.168.1.2 connect-interface vlan-interface 101
[SwitchB-msdp] quit
# Configure an MSDP peer on Switch C.
[SwitchC] msdp
[SwitchC-msdp] peer 192.168.1.1 connect-interface vlan-interface 101
[SwitchC-msdp] peer 192.168.3.2 connect-interface vlan-interface 102
[SwitchC-msdp] quit
# Configure MSDP peers on Switch E.
[SwitchE] msdp
[SwitchE-msdp] peer 192.168.3.1 connect-interface vlan-interface 102
[SwitchE-msdp] quit
Verifying the configuration
# Display information about BGP peer groups on Switch B.
[SwitchB] display bgp peer ipv4
BGP local router ID: 1.1.1.1
Local AS number: 100
Total number of peers: 1 Peers in established state: 1
Peer AS MsgRcvd MsgSent OutQ PrefRcv Up/Down State
192.168.1.2 200 24 21 0 6 00:20:07 Established
# Display information about BGP peer groups on Switch C.
[SwitchC] display bgp peer ipv4
BGP local router ID: 2.2.2.2
Local AS number: 1
Total number of peers: 1 Peers in established state: 1
Peer AS MsgRcvd MsgSent OutQ PrefRcv Up/Down State
192.168.1.1 100 18 16 0 1 00:20:07 Established
# Display the BGP routing table on Switch C.
[SwitchC] display bgp routing-table ipv4
Total number of routes: 5
BGP local router ID is 2.2.2.2
Status codes: * - valid, > - best, d - dampened, h - history,
s - suppressed, S - stale, i - internal, e - external
Network NextHop MED LocPrf PrefVal Path/Ogn
* > 1.1.1.1/32 192.168.1.1 0 0 100?
* >i 2.2.2.2/32 0.0.0.0 0 0 ?
* > 192.168.1.0 0.0.0.0 0 0 ?
* > 192.168.1.1/32 0.0.0.0 0 0 ?
* > 192.168.1.2/32 0.0.0.0 0 0 ?
# Verify that hosts in PIM-SM 1 and PIM-SM 3 can receive the multicast data from Source 1 in PIM-SM 1 and Source 2 in PIM-SM 2. (Details not shown.)
# Display brief information about MSDP peer groups on Switch B.
[SwitchB] display msdp brief
Configured Established Listen Connect Shutdown Disabled
1 1 0 0 0 0
Peer address State Up/Down time AS SA count Reset count
192.168.1.2 Established 00:12:57 200 13 0
# Display brief information about MSDP peer groups on Switch C.
[SwitchC] display msdp brief
Configured Established Listen Connect Shutdown Disabled
1 1 0 0 0 0
Peer address State Up/Down time AS SA count Reset count
192.168.3.2 Established 01:43:57 ? 8 0
192.168.1.1 Established 01:43:57 ? 13 0
# Display brief information about MSDP peer groups on Switch E.
[SwitchE] display msdp brief
Configured Established Listen Connect Shutdown Disabled
1 1 0 0 0 0
Peer address State Up/Down time AS SA count Reset count
192.168.3.1 Established 01:07:57 200 8 0
# Display detailed MSDP peer information on Switch B.
[SwitchB] display msdp peer-status
MSDP Peer 192.168.1.2; AS 200
Description:
Information about connection status:
State: Established
Up/down time: 00:15:47
Resets: 0
Connection interface: Vlan-interface101 (192.168.1.1)
Received/sent messages: 16/16
Discarded input messages: 0
Discarded output messages: 0
Elapsed time since last connection or counters clear: 00:17:40
Mesh group peer joined: momo
Last disconnect reason: Hold timer expired with truncated message
Truncated packet: 5 bytes in buffer, type: 1, length: 20, without packet time: 75s
Information about (Source, Group)-based SA filtering policy:
Import policy: None
Export policy: None
Information about SA-Requests:
Policy to accept SA-Requests: None
Sending SA-Requests status: Disable
Minimum TTL to forward SA with encapsulated data: 0
SAs learned from this peer: 0, SA cache maximum for the peer: 4294967295
Input queue size: 0, Output queue size: 0
Counters for MSDP messages:
RPF check failure: 0
Incoming/outgoing SA: 0/0
Incoming/outgoing SA-Request: 0/0
Incoming/outgoing SA-Response: 0/0
Incoming/outgoing Keepalive: 867/867
Incoming/outgoing Notification: 0/0
Incoming/outgoing Traceroutes in progress: 0/0
Incoming/outgoing Traceroute reply: 0/0
Incoming/outgoing Unknown: 0/0
Incoming/outgoing data packet: 0/0
Inter-AS multicast configuration by leveraging static RPF peers
Network requirements
As shown in Figure 57:
· The network has two ASs: AS 100 and AS 200. OSPF runs within each AS. BGP runs between the two ASs.
· PIM-SM 1 belongs to AS 100, and PIM-SM 2 and PIM-SM 3 belong to AS 200. Each PIM-SM domain has a minimum of one multicast source or receiver.
Configure the switches to meet the network requirements:
· Configure Loopback 0 as the C-BSR and C-RP of the related PIM-SM domain on Switch A, Switch D and Switch G.
· According to the peer-RPF forwarding rule, the switches accept SA messages that pass the filtering policy from its static RPF peers. To share multicast source information among PIM-SM domains without changing the unicast topology structure, configure MSDP peering relationships for the RPs of the PIM-SM domains and configure the static RPF peering relationships.
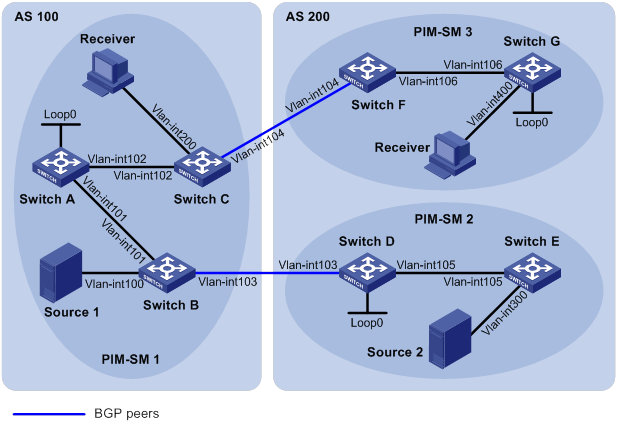
Table 12 Interface and IP address assignment
|
Device |
Interface |
IP address |
Device |
Interface |
IP address |
|
Source 1 |
— |
192.168.1.100/24 |
Switch D |
Vlan-int105 |
10.110.5.1/24 |
|
Source 2 |
— |
192.168.3.100/24 |
Switch D |
Vlan-int103 |
10.110.3.2/24 |
|
Switch A |
Vlan-int101 |
10.110.1.1/24 |
Switch D |
Loop0 |
2.2.2.2/32 |
|
Switch A |
Vlan-int102 |
10.110.2.1/24 |
Switch E |
Vlan-int105 |
10.110.5.2/24 |
|
Switch A |
Loop0 |
1.1.1.1/32 |
Switch E |
Vlan-int300 |
192.168.3.1/24 |
|
Switch B |
Vlan-int101 |
10.110.1.2/24 |
Switch F |
Vlan-int106 |
10.110.6.1/24 |
|
Switch B |
Vlan-int100 |
192.168.1.1/24 |
Switch F |
Vlan-int104 |
10.110.4.2/24 |
|
Switch B |
Vlan-int103 |
10.110.3.1/24 |
Switch G |
Vlan-int106 |
10.110.6.2/24 |
|
Switch C |
Vlan-int102 |
10.110.2.2/24 |
Switch G |
Vlan-int400 |
192.168.4.1/24 |
|
Switch C |
Vlan-int200 |
192.168.2.1/24 |
Switch G |
Loop0 |
3.3.3.3/32 |
|
Switch C |
Vlan-int104 |
10.110.4.1/24 |
Configuration procedure
1. Assign an IP address and subnet mask to each interface, as shown in Table 12. (Details not shown.)
2. Configure OSPF on the switches in the ASs. (Details not shown.)
3. Enable IP multicast routing, PIM-SM, and IGMP, and configure PIM-SM domain borders:
# On Switch C, enable IP multicast routing.
<SwitchC> system-view
[SwitchC] multicast routing
[SwitchC-mrib] quit
# Enable PIM-SM on each interface, and enable IGMP on the receiver-side interface (VLAN-interface 200).
[SwitchC] interface vlan-interface 102
[SwitchC-Vlan-interface102] pim sm
[SwitchC-Vlan-interface102] quit
[SwitchC] interface vlan-interface 200
[SwitchC-Vlan-interface200] igmp enable
[SwitchC-Vlan-interface200] quit
[SwitchC] interface vlan-interface 104
[SwitchC-Vlan-interface104] pim sm
[SwitchC-Vlan-interface104] quit
# Configure Switch A, Switch B, Switch D, Switch E, Switch F, and Switch G in the same way Switch C is configured. (Details not shown.)
# On Switch B, configure the PIM domain borders.
[SwitchB] interface vlan-interface 103
[SwitchB-Vlan-interface103] pim bsr-boundary
[SwitchB-Vlan-interface103] quit
# Configure the PIM domain borders on Switch C, Switch D, and Switch F in the same way Switch B is configured. (Details not shown.)
4. Configure C-BSRs and C-RPs:
# On Switch A, configure Loopback 0 as a C-BSR and a C-RP.
[SwitchA] pim
[SwitchA-pim] c-bsr 1.1.1.1
[SwitchA-pim] c-rp 1.1.1.1
[SwitchA-pim] quit
# Configure C-BSRs and C-RPs on Switch D and Switch G in the same way Switch A is configured. (Details not shown.)
5. Configure BGP, and redistribute BGP routing information into OSPF and OSPF routing information into BGP:
# On Switch B, configure an EBGP peer, and redistribute OSPF routing information.
[SwitchB] bgp 100
[SwitchB-bgp] router-id 1.1.1.2
[SwitchB-bgp] peer 10.110.3.2 as-number 200
[SwitchB-bgp] address-family ipv4 unicast
[SwitchB-bgp-ipv4] peer 10.110.3.2 enable
[SwitchB-bgp-ipv4] import-route ospf 1
[SwitchB-bgp-ipv4]quit
[SwitchB-bgp] quit
# On Switch D, configure an EBGP peer, and redistribute OSPF routing information.
[SwitchD] bgp 200
[SwitchD-bgp] router-id 2.2.2.2
[SwitchD-bgp] peer 10.110.3.1 as-number 100
[SwitchD-bgp] address-family ipv4 unicast
[SwitchD-bgp-ipv4] peer 10.110.3.1 enable
[SwitchD-bgp-ipv4] import-route ospf 1
[SwitchD-bgp-ipv4]quit
[SwitchD-bgp] quit
# On Switch C, configure an EBGP peer, and redistribute OSPF routing information.
[SwitchC] bgp 100
[SwitchC-bgp] router-id 1.1.1.3
[SwitchC-bgp] peer 10.110.4.2 as-number 200
[SwitchC-bgp] address-family ipv4 unicast
[SwitchC-bgp-ipv4] peer 10.110.4.2 enable
[SwitchC-bgp-ipv4] import-route ospf 1
[SwitchC-bgp-ipv4]quit
[SwitchC-bgp] quit
# On Switch F, configure an EBGP peer, and redistribute OSPF routing information.
[SwitchF] bgp 200
[SwitchF-bgp] router-id 3.3.3.1
[SwitchF-bgp] peer 10.110.4.1 as-number 100
[SwitchF-bgp] address-family ipv4 unicast
[SwitchF-bgp-ipv4] peer 10.110.4.1 enable
[SwitchF-bgp-ipv4] import-route ospf 1
[SwitchF-bgp-ipv4]quit
[SwitchF-bgp] quit
# On Switch B, redistribute BGP routing information into OSPF.
[SwitchB] ospf 1
[SwitchB-ospf-1] import-route bgp
[SwitchB-ospf-1] quit
# On Switch D, redistribute BGP routing information into OSPF.
[SwitchD] ospf 1
[SwitchD-ospf-1] import-route bgp
[SwitchD-ospf-1] quit
# On Switch C, redistribute BGP routing information into OSPF
[SwitchC] ospf 1
[SwitchC-ospf-1] import-route bgp
[SwitchC-ospf-1] quit
# On Switch F, redistribute BGP routing information into OSPF.
[SwitchF] ospf 1
[SwitchF-ospf-1] import-route bgp
[SwitchF-ospf-1] quit
6. Configure MSDP peers and static RPF peers:
# On Switch A, configure Switch D and Switch G as the MSDP peers and static RPF peers.
[SwitchA] ip prefix-list list-dg permit 10.110.0.0 16 greater-equal 16 less-equal 32
[SwitchA] msdp
[SwitchA-msdp] peer 10.110.3.2 connect-interface vlan-interface 101
[SwitchA-msdp] peer 10.110.6.2 connect-interface vlan-interface 102
[SwitchA-msdp] static-rpf-peer 10.110.3.2 rp-policy list-dg
[SwitchA-msdp] static-rpf-peer 10.110.6.2 rp-policy list-dg
[SwitchA-msdp] quit
# On Switch D, configure Switch A as the MSDP peer and static RPF peer.
[SwitchD] ip prefix-list list-a permit 10.110.0.0 16 greater-equal 16 less-equal 32
[SwitchD] msdp
[SwitchD-msdp] peer 10.110.1.1 connect-interface vlan-interface 103
[SwitchD-msdp] static-rpf-peer 10.110.1.1 rp-policy list-a
[SwitchD-msdp] quit
# On Switch G, configure Switch A as the MSDP peer and static RPF peer.
[SwitchG] ip prefix-list list-a permit 10.110.0.0 16 greater-equal 16 less-equal 32
[SwitchG] msdp
[SwitchG-msdp] peer 10.110.2.1 connect-interface vlan-interface 106
[SwitchG-msdp] static-rpf-peer 10.110.2.1 rp-policy list-a
[SwitchG-msdp] quit
Verifying the configuration
# Display the BGP peering relationships on Switch A.
[SwitchA] display bgp peer
No information is output, because no BGP peering relationship has been established between Switch A and Switch D, or between Switch A and Switch G. This means that the unicast topology is not changed.
# Display brief information about MSDP peers on Switch A.
[SwitchA] display msdp brief
Configured Established Listen Connect Shutdown Disabled
2 2 0 0 0 0
Peer address State Up/Down time AS SA count Reset count
10.110.3.2 Established 01:07:08 ? 8 0
10.110.6.2 Established 00:16:39 ? 13 0
# Display brief information about MSDP peers on Switch D.
[SwitchD] display msdp brief
Configured Established Listen Connect Shutdown Disabled
1 1 0 0 0 0
Peer address State Up/Down time AS SA count Reset count
10.110.1.1 Established 01:07:09 ? 8 0
# Display brief information about MSDP peers on Switch G.
[SwitchG] display msdp brief
Configured Established Listen Connect Shutdown Disabled
1 1 0 0 0 0
Peer address State Up/Down time AS SA count Reset count
10.110.2.1 Established 00:16:40 ? 13 0
# Verify that receivers in PIM-SM 1 and PIM-SM 3 can receive the multicast data from Source 1 and Source 2 to a multicast group. (Details not shown.)
Anycast RP configuration
Network requirements
As shown in Figure 58, OSPF runs within the domain to provide unicast routes.
Configure the Anycast RP application so that the receiver-side DRs and the source-side DRs can initiate a join process to their respective RPs that are topologically closest to them.
Configure the router IDs of Switch B and Switch D as 1.1.1.1 and 2.2.2.2, respectively. Set up an MSDP peering relationship between Switch B and Switch D.
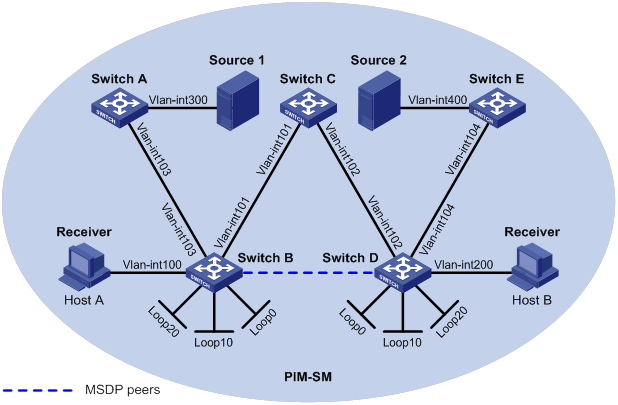
Table 13 Interface and IP address assignment
|
Device |
Interface |
IP address |
Device |
Interface |
IP address |
|
Source 1 |
— |
10.110.5.100/24 |
Switch C |
Vlan-int101 |
192.168.1.2/24 |
|
Source 2 |
— |
10.110.6.100/24 |
Switch C |
Vlan-int102 |
192.168.2.2/24 |
|
Switch A |
Vlan-int300 |
10.110.5.1/24 |
Switch D |
Vlan-int200 |
10.110.3.1/24 |
|
Switch A |
Vlan-int103 |
10.110.2.2/24 |
Switch D |
Vlan-int104 |
10.110.4.1/24 |
|
Switch B |
Vlan-int100 |
10.110.1.1/24 |
Switch D |
Vlan-int102 |
192.168.2.1/24 |
|
Switch B |
Vlan-int103 |
10.110.2.1/24 |
Switch D |
Loop0 |
2.2.2.2/32 |
|
Switch B |
Vlan-int101 |
192.168.1.1/24 |
Switch D |
Loop10 |
4.4.4.4/32 |
|
Switch B |
Loop0 |
1.1.1.1/32 |
Switch D |
Loop20 |
10.1.1.1/32 |
|
Switch B |
Loop10 |
3.3.3.3/32 |
Switch E |
Vlan-int400 |
10.110.6.1/24 |
|
Switch B |
Loop20 |
10.1.1.1/32 |
Switch E |
Vlan-int104 |
10.110.4.2/24 |
Configuration procedure
1. Assign an IP address and subnet mask to each interface, as shown in Figure 58. (Details not shown.)
2. Configure OSPF on the switches. (Details not shown.)
3. Enable IP multicast routing, IGMP, and PIM-SM:
# On Switch B, enable IP multicast routing.
<SwitchB> system-view
[SwitchB] multicast routing
[SwitchB-mrib] quit
# Enable IGMP on the receiver-side interface (VLAN-interface 100).
[SwitchB] interface vlan-interface 100
[SwitchB-Vlan-interface100] igmp enable
[SwitchB-Vlan-interface100] quit
# Enable PIM-SM on the other interfaces.
[SwitchB] interface vlan-interface 103
[SwitchB-Vlan-interface103] pim sm
[SwitchB-Vlan-interface103] quit
[SwitchB] interface Vlan-interface 101
[SwitchB-Vlan-interface101] pim sm
[SwitchB-Vlan-interface101] quit
[SwitchB] interface loopback 0
[SwitchB-LoopBack0] pim sm
[SwitchB-LoopBack0] quit
[SwitchB] interface loopback 10
[SwitchB-LoopBack10] pim sm
[SwitchB-LoopBack10] quit
[SwitchB] interface loopback 20
[SwitchB-LoopBack20] pim sm
[SwitchB-LoopBack20] quit
# Enable IP multicast routing, IGMP, and PIM-SM on Switch A, Switch C, Switch D, and Switch E in the same way Switch B is configured. (Details not shown.)
4. Configure C-BSRs and C-RPs:
# Configure Loopback 10 as a C-BSR and Loopback 20 as a C-RP on Switch B.
[SwitchB] pim
[SwitchB-pim] c-bsr 3.3.3.3
[SwitchB-pim] c-rp 10.1.1.1
[SwitchB-pim] quit
# Configure a C-BSR and a C-RP on Switch D in the same way Switch B is configured. (Details not shown.)
5. Configure MSDP peers:
# Configure an MSDP peer on Loopback 0 of Switch B.
[SwitchB] msdp
[SwitchB-msdp] originating-rp loopback 0
[SwitchB-msdp] peer 2.2.2.2 connect-interface loopback 0
[SwitchB-msdp] quit
# Configure an MSDP peer on Loopback 0 of Switch D.
[SwitchD] msdp
[SwitchD-msdp] originating-rp loopback 0
[SwitchD-msdp] peer 1.1.1.1 connect-interface loopback 0
[SwitchD-msdp] quit
Verifying the configuration
# Display brief information about MSDP peers on Switch B.
[SwitchB] display msdp brief
Configured Established Listen Connect Shutdown Disabled
1 1 0 0 0 0
Peer address State Up/Down time AS SA count Reset count
2.2.2.2 Established 00:10:57 ? 0 0
# Display brief information about MSDP peers on Switch D.
[SwitchD] display msdp brief
Configured Established Listen Connect Shutdown Disabled
1 1 0 0 0 0
Peer address State Up/Down time AS SA count Reset count
1.1.1.1 Established 00:10:57 ? 0 0
# Send an IGMP report from Host A to join multicast group 225.1.1.1. (Details not shown.)
# Send multicast data from Source 1 to multicast group 225.1.1.1. (Details not shown.)
# Display the PIM routing table on Switch D.
[SwitchD] display pim routing-table
No information is output on Switch D.
# Display the PIM routing table on Switch B.
[SwitchB] display pim routing-table
Total 1 (*, G) entry; 1 (S, G) entry
(*, 225.1.1.1)
RP: 10.1.1.1 (local)
Protocol: pim-sm, Flag: WC
UpTime: 00:15:04
Upstream interface: Register
Upstream neighbor: NULL
RPF prime neighbor: NULL
Downstream interface(s) information:
Total number of downstreams: 1
1: Vlan-interface100
Protocol: igmp, UpTime: 00:15:04, Expires: -
(10.110.5.100, 225.1.1.1)
RP: 10.1.1.1 (local)
Protocol: pim-sm, Flag: SPT 2MSDP ACT
UpTime: 00:46:28
Upstream interface: Vlan-interface103
Upstream neighbor: 10.110.2.2
RPF prime neighbor: 10.110.2.2
Downstream interface(s) information:
Total number of downstreams: 1
1: Vlan-interface100
Protocol: pim-sm, UpTime: - , Expires: -
The output shows that Switch B now acts as the RP for Source 1 and Host A.
# Send an IGMP leave message from Host A to leave multicast group 225.1.1.1. (Details not shown.),
# Send an IGMP report from Host B to join multicast group 225.1.1.1. (Details not shown.)
# Send multicast data from Source 2 to multicast group 225.1.1.1. (Details not shown.)
# Display the PIM routing table on Switch B.
[SwitchB] display pim routing-table
No information is output on Switch B.
# Display the PIM routing table on Switch D.
[SwitchD] display pim routing-table
Total 1 (*, G) entry; 1 (S, G) entry
(*, 225.1.1.1)
RP: 10.1.1.1 (local)
Protocol: pim-sm, Flag: WC
UpTime: 00:12:07
Upstream interface: Register
Upstream neighbor: NULL
RPF prime neighbor: NULL
Downstream interface(s) information:
Total number of downstreams: 1
1: Vlan-interface200
Protocol: igmp, UpTime: 00:12:07, Expires: -
(10.110.6.100, 225.1.1.1)
RP: 10.1.1.1 (local)
Protocol: pim-sm, Flag: SPT 2MSDP ACT
UpTime: 00:40:22
Upstream interface: Vlan-interface104
Upstream neighbor: 10.110.4.2
RPF prime neighbor: 10.110.4.2
Downstream interface(s) information:
Total number of downstreams: 1
1: Vlan-interface200
Protocol: pim-sm, UpTime: - , Expires: -
The output shows that Switch D now acts as the RP for Source 2 and Host B.
SA message filtering configuration
Network requirements
As shown in Figure 59:
· OSPF runs within and among the PIM-SM domains to provide unicast routing.
· Set up an MSDP peering relationship between Switch A and Switch C and between Switch C and Switch D.
· Source 1 sends multicast data to multicast groups 225.1.1.0/30 and 226.1.1.0/30, and Source 2 sends multicast data to the multicast group 227.1.1.0/30.
Configure SA message policies so that:
· Host A and Host B receive the multicast data only addressed to multicast groups 225.1.1.0/30 and 226.1.1.0/30.
· Host C receives the multicast data only addressed to multicast groups 226.1.1.0/30 and 227.1.1.0/30.
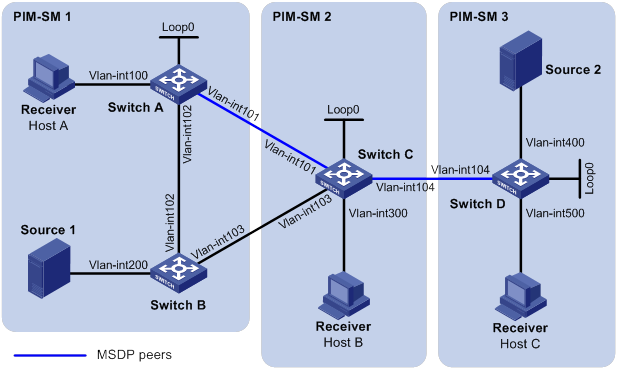
Table 14 Interface and IP address assignment
|
Device |
Interface |
IP address |
Device |
Interface |
IP address |
|
Source 1 |
— |
10.110.3.100/24 |
Switch C |
Vlan-int300 |
10.110.4.1/24 |
|
Source 2 |
— |
10.110.6.100/24 |
Switch C |
Vlan-int104 |
10.110.5.1/24 |
|
Switch A |
Vlan-int100 |
10.110.1.1/24 |
Switch C |
Vlan-int101 |
192.168.1.2/24 |
|
Switch A |
Vlan-int102 |
10.110.2.1/24 |
Switch C |
Vlan-int103 |
192.168.2.2/24 |
|
Switch A |
Vlan-int101 |
192.168.1.1/24 |
Switch C |
Loop0 |
2.2.2.2/32 |
|
Switch A |
Loop0 |
1.1.1.1/32 |
Switch D |
Vlan-int400 |
10.110.6.1/24 |
|
Switch B |
Vlan-int200 |
10.110.3.1/24 |
Switch D |
Vlan-int500 |
10.110.7.1/24 |
|
Switch B |
Vlan-int102 |
10.110.2.2/24 |
Switch D |
Vlan-int104 |
10.110.5.2/24 |
|
Switch B |
Vlan-int103 |
192.168.2.1/24 |
Switch D |
Loop0 |
3.3.3.3/32 |
Configuration procedure
1. Assign an IP address and subnet mask to each interface, as shown in Figure 59. (Details not shown.)
2. Configure OSPF on the switches in the PIM-SM domains. (Details not shown.)
3. Enable IP multicast routing, IGMP, and PIM-SM, and configure PIM domain borders:
# On Switch A, enable IP multicast routing.
<SwitchA> system-view
[SwitchA] multicast routing
[SwitchA-mrib] quit
# Enable IGMP on the receiver-side interface (VLAN-interface 100).
[SwitchA] interface vlan-interface 100
[SwitchA-Vlan-interface100] igmp enable
[SwitchA-Vlan-interface100] quit
# Enable PIM-SM on the other interfaces.
[SwitchA] interface vlan-interface 101
[SwitchA-Vlan-interface101] pim sm
[SwitchA-Vlan-interface101] quit
[SwitchA] interface vlan-interface 102
[SwitchA-Vlan-interface102] pim sm
[SwitchA-Vlan-interface102] quit
[SwitchA] interface loopback 0
[SwitchA-LoopBack0] pim sm
[SwitchA-LoopBack0] quit
# Enable IP multicast routing, IGMP, and PIM-SM on Switch B, Switch C, and Switch D in the same way Switch A is configured. (Details not shown.)
# Configure a PIM domain border on Switch C.
[SwitchC] interface vlan-interface 101
[SwitchC-Vlan-interface101] pim bsr-boundary
[SwitchC-Vlan-interface101] quit
[SwitchC] interface vlan-interface 103
[SwitchC-Vlan-interface103] pim bsr-boundary
[SwitchC-Vlan-interface103] quit
[SwitchC] interface vlan-interface 104
[SwitchC-Vlan-interface104] pim bsr-boundary
[SwitchC-Vlan-interface104] quit
# Configure PIM domain borders on Switch A, Switch B, and Switch D in the same way Switch C is configured. (Details not shown.)
4. Configure C-BSRs and C-RPs:
# Configure Loopback 0 as a C-BSR and a C-RP on Switch A.
[SwitchA] pim
[SwitchA-pim] c-bsr 1.1.1.1
[SwitchA-pim] c-rp 1.1.1.1
[SwitchA-pim] quit
# Configure C-BSRs and C-RPs on Switch C and Switch D in the same way Switch A is configured. (Details not shown.)
5. Configure MSDP peers:
# Configure an MSDP peer on Switch A.
[SwitchA] msdp
[SwitchA-msdp] peer 192.168.1.2 connect-interface vlan-interface 101
[SwitchA-msdp] quit
# Configure MSDP peers on Switch C.
[SwitchC] msdp
[SwitchC-msdp] peer 192.168.1.1 connect-interface vlan-interface 101
[SwitchC-msdp] peer 10.110.5.2 connect-interface vlan-interface 104
[SwitchC-msdp] quit
# Configure an MSDP peer on Switch D.
[SwitchD] msdp
[SwitchD-msdp] peer 10.110.5.1 connect-interface vlan-interface 104
[SwitchD-msdp] quit
6. Configure SA message policies:
# Configure an SA accepting and forwarding policy on Switch C so that Switch C will not forward SA messages for (Source 1, 225.1.1.0/30) to Switch D.
[SwitchC] acl advanced 3001
[SwitchC-acl-ipv4-adv-3001] rule deny ip source 10.110.3.100 0 destination 225.1.1.0 0.0.0.3
[SwitchC-acl-ipv4-adv-3001] rule permit ip source any destination any
[SwitchC-acl-ipv4-adv-3001] quit
[SwitchC] msdp
[SwitchC-msdp] peer 10.110.5.2 sa-policy export acl 3001
[SwitchC-msdp] quit
# Configure an SA creation policy on Switch D so that Switch D will not create SA messages for Source 2.
[SwitchD] acl basic 2001
[SwitchD-acl-ipv4-basic-2001] rule deny source 10.110.6.100 0
[SwitchD-acl-ipv4-basic-2001] quit
[SwitchD] msdp
[SwitchD-msdp] import-source acl 2001
[SwitchD-msdp] quit
Verifying the configuration
# Display the (S, G) entries in the SA message cache on Switch C.
[SwitchC] display msdp sa-cache
MSDP Total Source-Active Cache - 8 entries
Matched 8 entries
Source Group Origin RP Pro AS Uptime Expires
10.110.3.100 225.1.1.0 1.1.1.1 ? ? 02:03:30 00:05:31
10.110.3.100 225.1.1.1 1.1.1.1 ? ? 02:03:30 00:05:31
10.110.3.100 225.1.1.2 1.1.1.1 ? ? 02:03:30 00:05:31
10.110.3.100 225.1.1.3 1.1.1.1 ? ? 02:03:30 00:05:31
10.110.3.100 226.1.1.0 1.1.1.1 ? ? 02:03:30 00:05:31
10.110.3.100 226.1.1.1 1.1.1.1 ? ? 02:03:30 00:05:31
10.110.3.100 226.1.1.2 1.1.1.1 ? ? 02:03:30 00:05:31
10.110.3.100 226.1.1.3 1.1.1.1 ? ? 02:03:30 00:05:31
# Display the (S, G) entries in the SA message cache on Switch D.
[SwitchD] display msdp sa-cache
MSDP Total Source-Active Cache - 4 entries
Matched 4 entries
Source Group Origin RP Pro AS Uptime Expires
10.110.3.100 226.1.1.0 1.1.1.1 ? ? 00:32:53 00:05:07
10.110.3.100 226.1.1.1 1.1.1.1 ? ? 00:32:53 00:05:07
10.110.3.100 226.1.1.2 1.1.1.1 ? ? 00:32:53 00:05:07
10.110.3.100 226.1.1.3 1.1.1.1 ? ? 00:32:53 00:05:07
Troubleshooting MSDP
This section describes common MSDP problems and how to troubleshoot them.
MSDP peers stay in disabled state
Symptom
The configured MSDP peers stay in disabled state.
Analysis
Possible reasons for the problem might include the following:
· A TCP connection-based MSDP peering relationship is established between the local interface address and the MSDP peer.
· The TCP connection setup fails if the local interface address is not consistent with the MSDP peer address configured on the peer router.
· If no route is available between the MSDP peers, the TCP connection setup fails.
Solution
To resolve the problem:
1. Use the display ip routing-table command to verify that the unicast route between the routers is reachable.
2. Verify that a unicast route is available between the two routers that will become MSDP peers to each other.
3. Use the display current-configuration command to verify that the local interface address and the MSDP peer address of the remote router are the same.
4. If the problem persists, contact H3C Support.
No SA entries exist in the router's SA message cache
Symptom
MSDP fails to send (S, G) entries through SA messages.
Analysis
Possible reasons for the problem might include the following:
· The import-source command controls sending (S, G) entries through SA messages to MSDP peers. If this command is executed without the ipv4-acl-number argument, all the (S, G) entries are filtered out, and no (S, G) entries of the local domain are advertised.
· If you do not use the import-source command, the system advertises all the (S, G) entries of the local domain. If MSDP fails to send (S, G) entries through SA messages, verify that the import-source command has been correctly configured.
Solution
To resolve the problem:
1. Use the display ip routing-table command to verify that the unicast route between the routers is reachable.
2. Verify that a unicast route is available between the two routers that will become MSDP peers to each other.
3. Verify the configuration of the import-source command and its ipv4-acl-number argument, and make sure the ACL rule filters appropriate (S, G) entries.
4. If the problem persists, contact H3C Support.
No exchange of locally registered (S, G) entries between RPs
Symptom
RPs fail to exchange their locally registered (S, G) entries with one another in the Anycast RP application.
Analysis
Possible reasons for the problem might include the following:
· In the Anycast RP application, RPs in the same PIM-SM domain are configured to be MSDP peers to achieve redundancy backup among the RPs.
· An MSDP peer address must be different from the Anycast RP address, and the C-BSR and the C-RP must be configured on different devices or interfaces.
· If you configure the originating-rp command, MSDP replaces the RP address in the SA messages with the address of the interface specified in the command.
· When an MSDP peer receives an SA message, it performs an RPF check on the message. If the MSDP peer finds that the remote RP address is the local RP address, it discards the SA message.
Solution
To resolve the problem:
1. Use the display ip routing-table command to verify that the unicast route between the routers is reachable.
2. Verify that a unicast route is available between the two routers that will establish an MSDP peering relationship.
3. Verify the configuration of the originating-rp command. In the Anycast RP application environment, use the originating-rp command to configure the RP address in the SA messages, which must be the local interface address.
4. Verify that the C-BSR address is different from the Anycast RP address.
5. If the problem persists, contact H3C Support.
Configuring MLD snooping
Overview
As shown in Figure 60, when MLD snooping is not enabled, the Layer 2 switch floods IPv6 multicast packets to all hosts in a VLAN or VSI. When MLD snooping is enabled, the Layer 2 switch forwards multicast packets of known IPv6 multicast groups to only the receivers.
Figure 60 Multicast packet transmission processes without and with MLD snooping
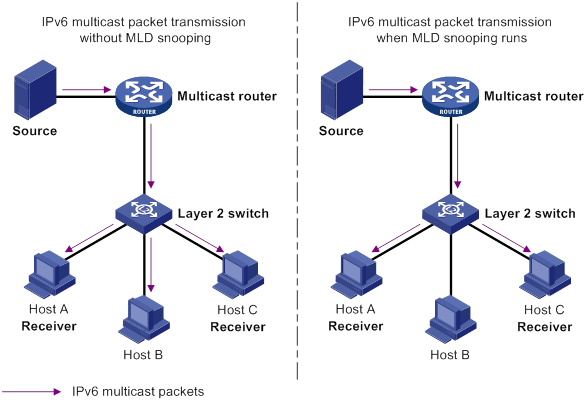
MLD snooping ports
As shown in Figure 61, MLD snooping runs on Switch A and Switch B, and Host A and Host C are receiver hosts in an IPv6 multicast group. MLD snooping ports are divided into member ports and router ports.
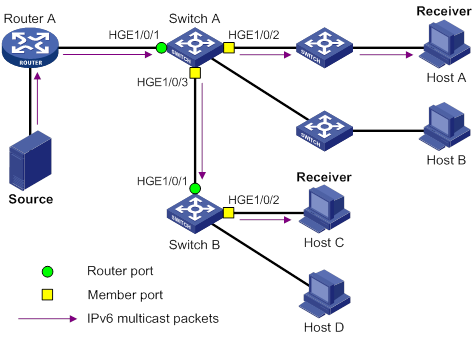
Router ports
On an MLD snooping Layer 2 device, the ports toward Layer 3 multicast devices are called router ports. In Figure 61, HundredGigE 1/0/1 of Switch A and HundredGigE 1/0/1 of Switch B are router ports.
Router ports contain the following types:
· Dynamic router port—When a port receives an MLD general query whose source address is not 0::0 or receives an IPv6 PIM hello message, the port is added into the dynamic router port list. At the same time, an aging timer is started for the port. If the port receives either of the messages before the timer expires, the timer is reset. If the port does not receive either of the messages when the timer expires, the port is removed from the dynamic router port list.
· Static router port—When a port is statically configured as a router port, it is added into the static router port list. The static router port does not age out, and it can be deleted only manually.
Do not confuse the "router port" in MLD snooping with the "routed interface" commonly known as the "Layer 3 interface." The router port in MLD snooping is a Layer 2 interface.
Member ports
On an MLD snooping Layer 2 device, the ports toward receiver hosts are called member ports. In Figure 61, HundredGigE 1/0/2 and HundredGigE 1/0/3 of Switch A and HundredGigE 1/0/2 of Switch B are member ports.
Member ports contain the following types:
· Dynamic member port—When a port receives an MLD report, it is added to the associated dynamic MLD snooping forwarding entry as an outgoing interface. At the same time, an aging timer is started for the port. If the port receives an MLD report before the timer expires, the timer is reset. If the port does not receive an MLD report when the timer expires, the port is removed from the associated dynamic forwarding entry.
· Static member port—When a port is statically configured as a member port, it is added to the associated static MLD snooping forwarding entry as an outgoing interface. The static member port does not age out, and it can be deleted only manually.
Unless otherwise specified, router ports and member ports in this document include both static and dynamic router ports and member ports.
How MLD snooping works
The ports in this section are dynamic ports. For information about how to configure and remove static ports, see "Configuring static ports."
General query
The MLD querier periodically sends MLD general queries to all hosts and routers on the local subnet to check for the existence of IPv6 multicast group members.
After receiving an MLD general query, the Layer 2 device forwards the query to all ports in the VLAN or VSI except the receiving port. The Layer 2 device also performs one of the following actions:
· If the receiving port is a dynamic router port in the dynamic router port list, the Layer 2 device restarts the aging timer for the router port.
· If the receiving port does not exist in the dynamic router port list, the Layer 2 device adds the port to the dynamic router port list. It also starts an aging timer for the port.
MLD report
A host sends an MLD report to the MLD querier for the following purposes:
· Responds to queries if the host is an IPv6 multicast group member.
· Applies for an IPv6 multicast group membership.
After receiving an MLD report from a host, the Layer 2 device forwards the report through all the router ports in the VLAN or VSI. It also resolves the IPv6 address of the reported IPv6 multicast group, and looks up the forwarding table for a matching entry as follows:
· If no match is found, the Layer 2 device creates a forwarding entry for the group with the receiving port an outgoing interface. It also marks the receiving port as a dynamic member port and starts an aging timer for the port.
· If a match is found but the matching forwarding entry does not contain the receiving port, the Layer 2 device adds the receiving port to the outgoing interface list. It also marks the port as a dynamic member port to the forwarding entry and starts an aging timer for the port.
· If a match is found and the matching forwarding entry contains the receiving port, the Layer 2 device restarts the aging timer for the port.
In an application with an IPv6 multicast group policy configured on an MLD snooping-enabled Layer 2 device, when a user requests a multicast program, the user's host initiates an MLD report. After receiving this report message, the Layer 2 device resolves the IPv6 multicast group address in the report and performs ACL filtering on the report. If the report passes ACL filtering, the Layer 2 device creates an MLD snooping forwarding entry for the group with the receiving port as an outgoing interface. If the report does not pass ACL filtering, the Layer 2 device drops this report message, in which case, the IPv6 multicast data for the IPv6 multicast group is not sent to this port, and the user cannot retrieve the program.
A Layer 2 device does not forward an MLD report through a non-router port because of the host MLD report suppression mechanism.
Done message
When a host leaves an IPv6 multicast group, the host sends an MLD done message to the Layer 3 devices. When the Layer 2 device receives the MLD done message on a dynamic member port, the Layer 2 device first examines whether a forwarding entry matches the IPv6 multicast group address in the message.
· If no match is found, the Layer 2 device discards the MLD done message.
· If a match is found but the receiving port is not an outgoing interface in the forwarding entry, the Layer 2 device discards the MLD done message.
· If a match is found and the receiving port is not the only outgoing interface in the forwarding entry, the Layer 2 device performs the following actions:
? Discards the MLD done message.
? Sends an MLD multicast-address-specific query to identify whether the group has active listeners attached to the receiving port.
? Sets the aging timer for the receiving port to twice the MLD last listener query interval.
· If a match is found and the receiving port is the only outgoing interface in the forwarding entry, the Layer 2 device performs the following actions:
? Forwards the MLD done message to all router ports in the VLAN or VSI.
? Sends an MLD multicast-address-specific query to identify whether the group has active listeners attached to the receiving port.
? Sets the aging timer for the receiving port to twice the MLD last listener query interval.
After receiving the MLD done message on a port, the MLD querier resolves the IPv6 multicast group address in the message. Then, it sends an MLD multicast-address-specific query to the IPv6 multicast group through the receiving port.
After receiving the MLD multicast-address-specific query, the Layer 2 device forwards the query through all router ports and member ports of the group in the VLAN or VSI. Then, it waits for the responding MLD report from the directly connected hosts. For the dynamic member port that received the done message, the Layer 2 device also performs one of the following actions:
· If the port receives an MLD report before the aging timer expires, the Layer 2 device resets the aging timer for the port.
· If the port does not receive any MLD report messages when the aging timer expires, the Layer 2 device removes the port from the forwarding entry for the IPv6 multicast group.
MLD snooping proxying
As shown in Figure 62, to reduce the number of MLD report and done messages received by the upstream device, you can enable MLD snooping proxying on the edge device. With MLD snooping proxying enabled, the edge device acts as a host for the upstream MLD snooping querier to send MLD report and done messages to Router A. The host MLD report suppression mechanism on the edge device does not take effect.
Figure 62 MLD snooping proxying
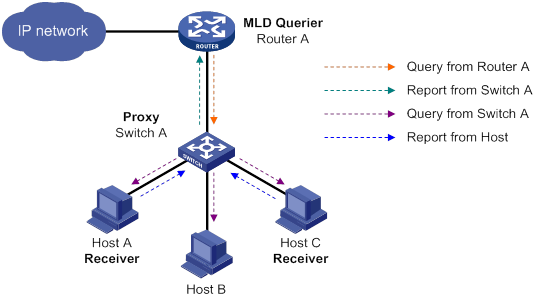
The MLD snooping proxy device processes different MLD messages as follows:
· General query.
After receiving an MLD general query, the device forwards the query to all ports in the VLAN except the receiving port. The device also generates an MLD report based on the local membership information and sends the report to all router ports.
· Multicast-address-specific query or multicast-address-and-source-specific query.
After receiving an MLD multicast-address-specific query or multicast-address-and-source-specific query, the device forwards the query to all ports in the VLAN except the receiving port. If the forwarding entry has a member port, the device sends a response to all router ports in the VLAN.
· Report.
After receiving an MLD report from a host, the device looks up the forwarding table for a matching entry as follows:
? If a match is found and the matching forwarding entry contains the receiving port, the device resets the aging timer for the port.
? If a match is found but the matching forwarding entry does not contain the receiving port, the device adds the receiving port to the outgoing interface list. It also marks the receiving port as a dynamic member port and starts an aging timer for the port.
? If no match is found, the device creates a forwarding entry with the receiving port as an outgoing interface. It also marks the receiving port as a dynamic member port and starts an aging timer for the port. Then it sends the report to all router ports.
· Done message.
After receiving the MLD done message on a port, the device sends an MLD multicast-address-specific query through the receiving port. The device sends the MLD done message to all router ports only when the last member port is removed from the forwarding entry.
MLD snooping version
Different MLD snooping versions can process different versions of MLD messages:
· MLDv1 snooping can process MLDv1 messages, but it floods MLDv2 messages in the VLAN instead of processing them.
· MLDv2 snooping can process MLDv1 and MLDv2 messages.
The switch supports only MLDv1 snooping.
Protocols and standards
RFC 4541, Considerations for Internet Group Management Protocol (IGMP) and Multicast Listener Discovery (MLD) Snooping Switches
MLD snooping configuration task list
You can configure MLD snooping for VLANs or VSIs.
MLD snooping configuration task list for VLANs
MLD snooping configuration task list for VSIs
|
Tasks at a glance |
|
Configuring basic MLD snooping features: · (Required.) Enabling MLD snooping · (Optional.) Setting the maximum number of MLD snooping forwarding entries · (Optional.) Setting the MLD last listener query interval |
|
Configuring MLD snooping port features: (Optional.) Setting aging timers for dynamic ports |
|
Configuring the MLD snooping querier: · (Optional.) Enabling the MLD snooping querier · (Optional.) Configuring parameters for MLD general queries and responses |
|
Configuring parameters for MLD messages: · (Optional.) Configuring source IPv6 addresses for MLD messages · (Optional.) Setting the 802.1p priority for MLD messages |
|
Configuring MLD snooping policies: · (Optional.) Enabling dropping unknown IPv6 multicast data · (Optional.) Enabling MLD report suppression |
The MLD snooping configurations made on Layer 2 aggregate interfaces do not interfere with the configurations made on member ports. In addition, the configurations made on Layer 2 aggregate interfaces do not take part in aggregation calculations. The configuration made on a member port of the aggregate group takes effect after the port leaves the aggregate group.
Configuring basic MLD snooping features
Before you configure basic MLD snooping features, complete the following tasks:
· Configure VLANs or VSIs.
· Determine the maximum number of MLD snooping forwarding entries.
· Determine the MLD last listener query interval.
Enabling MLD snooping
When you enable MLD snooping, follow these restrictions and guidelines:
· You must enable MLD snooping globally before you can enable it for a VLAN or VSI.
· MLD snooping configuration made in VLAN view or VSI view takes effect only on the member ports in that VLAN or VSI.
· You can enable MLD snooping for the specified VLANs in MLD-snooping view, for a VSI in VSI view, or for a VLAN in VLAN view. For a VLAN, the configuration in VLAN interface has the same priority as the configuration in MLD-snooping view, and the most recent configuration takes effect.
Enabling MLD snooping in MLD-snooping view
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable MLD snooping globally and enter MLD-snooping view. |
mld-snooping |
By default, MLD snooping is globally disabled. |
|
3. Enable MLD snooping for the specified VLANs. |
enable vlan vlan-list |
By default, MLD snooping is disabled for a VLAN. |
Enabling MLD snooping in VLAN or VSI view
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enable MLD snooping globally and enter MLD-snooping view. |
mld-snooping |
By default, MLD snooping is globally disabled. |
|
3. Return to system view. |
quit |
N/A |
|
4. Enter VLAN view or VSI view. |
·
Enter VLAN view: ·
Enter VSI view: |
N/A |
|
5. Enable MLD snooping for the VLAN or VSI. |
mld-snooping enable |
By default, MLD snooping is disabled in a VLAN or VSI. |
Setting the maximum number of MLD snooping forwarding entries
You can modify the maximum number of MLD snooping forwarding entries, including dynamic entries and static entries. When the number of forwarding entries on the device reaches the upper limit, the device does not automatically remove any existing entries. To allow new entries to be created, remove some entries manually.
To set the maximum number of MLD snooping forwarding entries:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter MLD-snooping view. |
mld-snooping |
N/A |
|
3. Set the maximum number of MLD snooping forwarding entries. |
entry-limit limit |
The default setting is 4294967295. |
Configuring static IPv6 multicast MAC address entries
In Layer 2 IPv6 multicast, IPv6 multicast MAC address entries can be dynamically created through Layer 2 multicast protocols (such as MLD snooping). You can also manually configure static IPv6 multicast MAC address entries by binding IPv6 multicast MAC addresses and ports to control the destination ports of the IPv6 multicast data.
Configuration restrictions and guidelines
When you configure a static IPv6 multicast MAC address entry, follow these restrictions and guidelines:
· You must specify an unused IPv6 multicast MAC address when configuring a static IPv6 multicast MAC address entry. An IPv6 multicast MAC address is a MAC address in which the least significant bit of the most significant octet is 1.
Configuring a static IPv6 multicast MAC address entry in system view
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Configure a static IPv6 multicast MAC address entry. |
mac-address multicast mac-address interface interface-list vlan vlan-id |
By default, no static IPv6 multicast MAC address entries exist. For more information about this command, see IP Multicast Command Reference. |
Configuring a static IPv6 multicast MAC address entry in interface view
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter Layer 2 Ethernet interface or Layer 2 aggregate interface view. |
interface interface-type interface-number |
N/A |
|
3. Configure a static IPv6 multicast MAC address entry. |
mac-address multicast mac-address vlan vlan-id |
By default, no static multicast MAC address entries exist. For more information about this command, see IP Multicast Command Reference. |
Setting the MLD last listener query interval
A receiver host starts a report delay timer for an IPv6 multicast group when it receives an MLD multicast-address-specific query for the group. This timer is set to a random value in the range of 0 to the maximum response time advertised in the query. When the timer value decreases to 0, the host sends an MLD report to the group.
The MLD last listener query interval defines the maximum response time advertised in MLD multicast-address-specific queries. Set an appropriate value for the MLD last listener query interval to speed up hosts' responses to MLD multicast-address-specific queries and avoid MLD report traffic bursts.
Configuration restrictions and guidelines
When you set the MLD last listener query interval, follow these restrictions and guidelines:
· The Layer 2 device does not send an MLD multicast-address-specific query if it receives an MLD done message from a port enabled with fast-leave processing.
· You can set the MLD last listener query interval globally for all VLANs and VSIs in MLD-snooping view, for a VSI in VSI view, or for a VLAN in VLAN view. For a VSI, the VSI-specific configuration takes priority over the global configuration. For a VLAN, the VLAN-specific configuration takes priority over the global configuration.
Setting the MLD last listener query interval globally
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter MLD-snooping view. |
mld-snooping |
N/A |
|
3. Set the MLD last listener query interval globally. |
last-listener-query-interval interval |
The default setting is 1 second. |
Setting the MLD last listener query interval in a VLAN or VSI
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter VLAN view or VSI view. |
·
Enter VLAN view: ·
Enter VSI view: |
N/A |
|
3. Set the MLD last listener query interval in the VLAN or VSI. |
mld-snooping last-listener-query-interval interval |
The default setting is 1 second. |
Configuring MLD snooping port features
Before you configure MLD snooping port features, complete the following tasks:
· Enable MLD snooping for the VLAN or VSI.
· Determine the aging timer for dynamic router ports.
· Determine the aging timer for dynamic member ports.
· Determine the addresses of the IPv6 multicast group and IPv6 multicast source.
Setting aging timers for dynamic ports
When you set aging timers for dynamic ports, follow these restrictions and guidelines:
· If the memberships of IPv6 multicast groups frequently change, set a relatively small value for the aging timer of the dynamic member ports. If the memberships of IPv6 multicast groups rarely change, you can set a relatively large value.
· If a dynamic router port receives an IPv6 PIMv2 hello message, the aging timer for the port is specified by the hello message. In this case, the mld-snooping router-aging-time command does not take effect on the port.
· MLD multicast-address-specific queries originated by the Layer 2 device trigger the adjustment of aging timers of dynamic member ports. If a dynamic member port receives such a query, its aging timer is set to twice the MLD last listener query interval. For more information about setting the MLD last listener query interval on the Layer 2 device, see "Setting the MLD last listener query interval."
· You can set the timers globally for all VLANs and VSIs in MLD-snooping view, for a VSI in VSI view, or for a VLAN in VLAN view. For a VSI, the VSI-specific configuration takes priority over the global configuration. For a VLAN, the VLAN-specific configuration takes priority over the global configuration.
Setting the aging timers for dynamic ports globally
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter MLD-snooping view. |
mld-snooping |
N/A |
|
3. Set the aging timer for dynamic router ports globally. |
router-aging-time seconds |
The default setting is 260 seconds. |
|
4. Set the aging timer for dynamic member ports globally. |
host-aging-time seconds |
The default setting is 260 seconds. |
Setting the aging timers for dynamic ports in a VLAN or VSI
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter VLAN view or VSI view. |
·
Enter VLAN view: ·
Enter VSI view: |
N/A |
|
3. Set the aging timer for dynamic router ports in the VLAN or VSI. |
mld-snooping router-aging-time seconds |
The default setting is 260 seconds. |
|
4. Set the aging timer for dynamic member ports in the VLAN or VSI. |
mld-snooping host-aging-time seconds |
The default setting is 260 seconds. |
Configuring static ports
You can configure the following types of static ports:
· Static member port—When you configure a port as a static member port for an IPv6 multicast group, all hosts attached to the port will receive IPv6 multicast data for the group.
The static member port does not respond to MLD queries. When you complete or cancel this configuration, the port does not send an unsolicited report or done message.
· Static router port—When you configure a port as a static router port for an IPv6 multicast group, all IPv6 multicast data for the group received on the port will be forwarded.
To configure a port as a static port:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter Layer 2 Ethernet interface view or Layer 2 aggregate interface view. |
interface interface-type interface-number |
N/A |
|
3. Configure the port as a static port. |
·
Configure the port as a static member port: ·
Configure the port as a static router port: |
By default, a port is not a static member port or a static router port. |
Configuring a port as a simulated member host
When a port is configured as a simulated member host, it is equivalent to an independent host in the following ways:
· It sends an unsolicited MLD report when you complete the configuration.
· It responds to MLD general queries with MLD reports.
· It sends an MLD done message when you remove the configuration.
The version of MLD running on the simulated member host is the same as the version of MLD snooping running on the port. The port ages out in the same ways as a dynamic member port.
To configure a port as a simulated member host:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter Layer 2 Ethernet interface view or Layer 2 aggregate interface view. |
interface interface-type interface-number |
N/A |
|
3. Configure the port as a simulated member host. |
mld-snooping host-join ipv6-group-address [ source-ip ipv6-source-address ] vlan vlan-id |
By default, the port is not a simulated member host. |
Enabling fast-leave processing
This feature enables the device to immediately remove a port from the forwarding entry for an IPv6 multicast group when the port receives a done message.
Configuration restrictions and guidelines
When you enable fast-leave processing, follow these restrictions and guidelines:
· Do not enable fast-leave processing on a port that have multiple receiver hosts attached in a VLAN. If fast-leave processing is enabled, the remaining receivers cannot receive IPv6 multicast data for a group after a receiver leaves that group.
· You can enable fast-leave processing globally for all ports in MLD-snooping view or for a port in interface view. For a port, the port-specific configuration takes priority over the global configuration.
Enabling fast-leave processing globally
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter MLD-snooping view. |
mld-snooping |
N/A |
|
3. Enable fast-leave processing globally. |
fast-leave [ vlan vlan-list ] |
By default, fast-leave processing is disabled globally. |
Enabling fast-leave processing on a port
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter Layer 2 Ethernet interface view or Layer 2 aggregate interface view. |
interface interface-type interface-number |
N/A |
|
3. Enable fast-leave processing on the port. |
mld-snooping fast-leave [ vlan vlan-list ] |
By default, fast-leave processing is disabled on a port. |
Disabling a port from becoming a dynamic router port
A receiver host might send MLD general queries or IPv6 PIM hello messages for testing purposes. On the Layer 2 device, the port that receives either of the messages becomes a dynamic router port. Before the aging timer for the port expires, the following problems might occur:
· All IPv6 multicast data for the VLAN to which the port belongs flows to the port. Then, the port forwards the data to attached receiver hosts. The receiver hosts will receive IPv6 multicast data that it does not expect.
· The port forwards the MLD general queries or IPv6 PIM hello messages to its upstream multicast routers. These messages might affect the multicast routing protocol state (such as the MLD querier or DR election) on the multicast routers. This might further cause network interruption.
To solve these problems, you can disable the router port from becoming a dynamic router port when receiving either of the messages. This also improves network security and the control over receiver hosts.
To disable a port from becoming a dynamic router port:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter Layer 2 Ethernet interface view or Layer 2 aggregate interface view. |
interface interface-type interface-number |
N/A |
|
3. Disable the port from becoming a dynamic router port. |
mld-snooping router-port-deny [ vlan vlan-list ] |
By default, a port is allowed to become a dynamic router port. This configuration does not affect the static router port configuration. |
Enabling inner VLAN ID-based forwarding
Use this feature to enable a port to create and maintain MLD snooping entries based on the inner VLAN IDs of the received double-tagged MLD packets.
To enable inner VLAN ID-based forwarding:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter Layer 2 Ethernet interface view or Layer 2 aggregate interface view. |
interface interface-type interface-number |
N/A |
|
3. Enable inner VLAN ID-based forwarding. |
mld-snooping cvid-forward |
By default, inner VLAN ID-based forwarding is disabled on a port. The port performs outer VLAN ID-based forwarding. |
Configuring the MLD snooping querier
This section describes how to configure the MLD snooping querier.
Configuration prerequisites
Before you configure the MLD snooping querier, complete the following tasks:
· Enable MLD snooping for the VLAN or VSI.
· Determine the MLD general query interval.
· Determine the maximum response time for MLD general queries.
Enabling the MLD snooping querier
This feature enables the device to periodically send MLD general queries to establish and maintain multicast forwarding entries at the data link Layer. You can configure an MLD snooping querier on a network without Layer 3 multicast devices.
Configuration restrictions and guidelines
When you enable the MLD snooping querier, follow these restrictions and guidelines:
· Do not enable the MLD snooping querier on an IPv6 multicast network that runs MLD. An MLD snooping querier does not participate in MLD querier elections. However, it might affect MLD querier elections if it sends MLD general queries with a low source IPv6 address.
· On a VXLAN network, the MLD snooping querier in a VSI does not include VLAN tags in MLD general queries. As a best practice, do not enable the MLD snooping querier in a VSI if the VSI uses the Ethernet access mode. For more information about the Ethernet access mode, see VXLAN Configuration Guide.
Configuration procedure
To enable the MLD snooping querier for a VLAN or VSI:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter VLAN view or VSI view. |
·
Enter VLAN view: ·
Enter VSI view: |
N/A |
|
3. Enable the MLD snooping querier for the VLAN or VSI. |
mld-snooping querier |
By default, the MLD snooping querier is disabled for a VLAN or VSI. |
Configuring parameters for MLD general queries and responses
|
|
CAUTION: To avoid mistakenly deleting IPv6 multicast group members, make sure the MLD general query interval is greater than the maximum response time for MLD general queries. |
You can modify the MLD general query interval for a VLAN or VSI based on the actual network conditions.
A receiver host starts a report delay timer for each IPv6 multicast group that it has joined when it receives an MLD general query. This timer is set to a random value in the range of 0 to the maximum response time advertised in the query. When the timer value decreases to 0, the host sends an MLD report to the corresponding IPv6 multicast group.
Set an appropriate value for the maximum response time for MLD general queries to speed up hosts' responses to MLD general queries and avoid MLD report traffic bursts.
You can set the maximum response time for MLD general queries globally for all VLANs and VSIs in MLD-snooping view, for a VSI in VSI view, or for a VLAN in VLAN view. For a VSI, the VSI-specific configuration takes priority over the global configuration. For a VLAN, the VLAN-specific configuration takes priority over the global configuration.
Configuring parameters for MLD general queries and responses globally
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter MLD-snooping view. |
mld-snooping |
N/A |
|
3. Set the maximum response time for MLD general queries. |
max-response-time seconds |
The default setting is 10 seconds. |
Configuring parameters for MLD general queries and responses in a VLAN or VSI
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter VLAN view or VSI view. |
·
Enter VLAN view: ·
Enter VSI view: |
N/A |
|
3. Set the MLD general query interval in the VLAN or VSI. |
mld-snooping query-interval interval |
The default setting is 125 seconds. |
|
4. Set the maximum response time for MLD general queries in the VLAN or VSI. |
mld-snooping max-response-time seconds |
The default setting is 10 seconds. |
Enabling MLD snooping proxying
Before you enable MLD snooping proxying for a VLAN, enable MLD snooping for the VLAN.
To enable MLD snooping proxying:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter VLAN view. |
vlan vlan-id |
N/A |
|
3. Enable MLD snooping proxying for the VLAN. |
mld-snooping proxy enable |
By default, MLD snooping proxying is disabled for a VLAN. |
Configuring parameters for MLD messages
This section describes how to configure parameters for MLD messages.
Configuration prerequisites
Before you configure parameters for MLD messages, complete the following tasks:
· Enable MLD snooping for the VLAN or VSI.
· Determine the source IPv6 address of MLD general queries.
· Determine the source IPv6 address of MLD multicast-address-specific queries.
· Determine the source IPv6 address of MLD reports.
· Determine the source IPv6 address of MLD done messages.
· Determine the 802.1p priority of MLD messages.
Configuring source IPv6 addresses for MLD messages
You can change the source IPv6 address of the MLD queries sent by an MLD snooping querier. This configuration might affect MLD querier election within the subnet.
You can also change the source IPv6 address of MLD reports or done messages sent by a simulated member host or an MLD snooping proxy.
Configuring the source IPv6 address for MLD messages in a VLAN
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter VLAN view. |
vlan vlan-id |
N/A |
|
3. Configure the source IPv6 address for MLD general queries. |
mld-snooping general-query source-ip ipv6-address |
By default, the source IPv6 address of MLD general queries is the IPv6 link-local address of the current VLAN interface. If the current VLAN interface does not have an IPv6 link-local address, the source IPv6 address is FE80::02FF:FFFF:FE00:0001. |
|
4. Configure the source IPv6 address for MLD multicast-address-specific queries. |
mld-snooping special-query source-ip ipv6-address |
By default, the source IPv6 address of MLD multicast-address-specific queries is one of the following: · The source address of MLD general queries if the MLD snooping querier of the VLAN has received MLD general queries. · The IPv6 link-local address of the current VLAN interface if the MLD snooping querier does not receive an MLD general query. · FE80::02FF:FFFF:FE00:0001 if the MLD snooping querier does not receive an MLD general query and the current VLAN interface does not have an IPv6 link-local address. |
|
5. Configure the source IPv6 address for MLD reports. |
mld-snooping report source-ip ipv6-address |
By default, the source IPv6 address of MLD reports is the IPv6 link-local address of the current VLAN interface. If the current VLAN interface does not have an IPv6 link-local address, the source IPv6 address is FE80::02FF:FFFF:FE00:0001. |
|
6. Configure the source IPv6 address for MLD done messages. |
mld-snooping done source-ip ipv6-address |
By default, the source IPv6 address of MLD done messages is the IPv6 link-local address of the current VLAN interface. If the current VLAN interface does not have an IPv6 link-local address, the source IPv6 address is FE80::02FF:FFFF:FE00:0001. |
Configuring the source IPv6 address for MLD messages in a VSI
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter VLAN view. |
vsi vsi-name |
N/A |
|
3. Configure the source IPv6 address for MLD general queries. |
mld-snooping general-query source-ip ipv6-address |
By default, the source IPv6 address of MLD general queries is the IPv6 link-local address of the gateway interface for a VSI. If the gateway interface does not have an IPv6 link-local address, the source IPv6 address is FE80::02FF:FFFF:FE00:0001. |
|
4. Configure the source IPv6 address for MLD multicast-address-specific queries. |
mld-snooping special-query source-ip ipv6-address |
By default, the source IPv6 address of MLD multicast-address-specific queries is one of the following: · The source address of MLD general queries if the MLD snooping querier of the VSI has received MLD general queries. · IPv6 link-local address of the gateway interface for the VSI if the MLD snooping querier does not receive an MLD general query. · FE80::02FF:FFFF:FE00:0001 if the gateway interface does not have an IPv6 link-local address. |
|
5. Configure the source IPv6 address for MLD reports. |
mld-snooping report source-ip ipv6-address |
By default, the source IPv6 address of MLD reports is the IPv6 link-local address of the gateway interface for a VSI. If the gateway interface does not have an IPv6 link-local address, the source IPv6 address is FE80::02FF:FFFF:FE00:0001. |
|
6. Configure the source IPv6 address for MLD dones. |
mld-snooping done source-ip ipv6-address |
By default, the source IPv6 address of MLD dones is the IPv6 link-local address of the gateway interface for a VSI. If the gateway interface does not have an IPv6 link-local address, the source IPv6 address is FE80::02FF:FFFF:FE00:0001. |
Setting the 802.1p priority for MLD messages
When congestion occurs on outgoing ports of the Layer 2 device, it forwards MLD messages in their 802.1p priority order, from highest to lowest. You can assign a higher 802.1p priority to MLD messages that are created or forwarded by the device.
You can configure the 802.1p priority of MLD messages for all VLANs and VSIs in MLD-snooping view or for a VLAN in VLAN view. For a VLAN, the VLAN-specific configuration takes priority over the global configuration.
Setting the 802.1p priority for MLD messages globally
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter MLD-snooping view. |
mld-snooping |
N/A |
|
3. Set the 802.1p priority for MLD messages. |
dot1p-priority priority |
By default, the 802.1p priority for MLD messages is not configured. For MLD messages created by the device, the 802.1p priority is 0. For MLD messages to be forwarded, the device does not change the 802.1p priority. |
Setting the 802.1p priority for MLD messages in a VLAN
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter VLAN view. |
vlan vlan-id |
N/A |
|
3. Set the 802.1p priority for MLD messages in the VLAN. |
mld-snooping dot1p-priority priority |
By default, the 802.1p priority for MLD messages is not configured. For MLD messages created by the device, the 802.1p priority is 0. For MLD messages to be forwarded, the device does not change the 802.1p priority. |
Configuring MLD snooping policies
Before you configure MLD snooping policies, complete the following tasks:
· Enable MLD snooping for the VLAN or VSI.
· Determine the ACL used by the IPv6 multicast group policy.
· Determine the maximum number of IPv6 multicast groups that a port can join.
Configuring an IPv6 multicast group policy
This feature enables the device to filter MLD reports by using an ACL that specifies the IPv6 multicast groups and the optional sources. It is used to control the IPv6 multicast groups that receiver hosts can join.
Configuration restrictions and guidelines
When you configure an IPv6 multicast group policy, follow these restrictions and guidelines:
· This configuration takes effect on the IPv6 multicast groups that ports join dynamically.
· You can configure an IPv6 multicast group policy globally for all ports in MLD-snooping view or for a port in interface view. For a port, the port-specific configuration takes priority over the global configuration.
Configuring an IPv6 multicast group policy globally
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter MLD-snooping view. |
mld-snooping |
N/A |
|
3. Configure an IPv6 multicast group policy globally. |
group-policy ipv6-acl-number [ vlan vlan-list ] |
By default, no IPv6 multicast group policies exist. Hosts can join any IPv6 multicast groups. |
Configuring an IPv6 multicast group policy on a port
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter Layer 2 Ethernet interface view or Layer 2 aggregate interface view. |
interface interface-type interface-number |
N/A |
|
3. Configure an IPv6 multicast group policy on the port. |
mld-snooping group-policy ipv6-acl-number [ vlan vlan-list ] |
By default, no IPv6 multicast group policies exist on a port. Hosts attached to the port can join any IPv6 multicast groups. |
Enabling IPv6 multicast source port filtering
This feature enables the device to discard all IPv6 multicast data packets and to accept IPv6 multicast protocol packets. You can enable this feature on ports that connect to only IPv6 multicast receivers.
You can enable multicast source port filtering for the specified ports in MLD-snooping view or for a port in interface view. For a port, the configuration in interface view has the same priority as the configuration in MLD-snooping view, and the most recent configuration takes effect.
Enabling IPv6 multicast source port filtering in MLD-snooping view
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter MLD-snooping view. |
mld-snooping |
N/A |
|
3. Enable IPv6 multicast source port filtering globally. |
source-deny port interface-list |
By default, IPv6 multicast source port filtering is disabled globally. |
Enabling IPv6 multicast source port filtering in interface view
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter Layer 2 Ethernet interface view. |
interface interface-type interface-number |
N/A |
|
3. Enable IPv6 multicast source port filtering on the port. |
mld-snooping source-deny |
By default, IPv6 multicast source port filtering is disabled on the port. |
Enabling dropping unknown IPv6 multicast data
Unknown IPv6 multicast data refers to IPv6 multicast data for which no forwarding entries exist in the MLD snooping forwarding table. This feature enables the device only to forward unknown IPv6 multicast data to the router port. If the device does not have a router port, unknown IPv6 multicast data will be dropped.
If you do not enable this feature, the unknown IPv6 multicast data is flooded in the VLAN to which the data belongs.
To enable dropping unknown IPv6 multicast data in a VLAN or VSI:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter VLAN view or VSI view. |
·
Enter VLAN view: ·
Enter VSI view: |
N/A |
|
3. Enable dropping unknown IPv6 multicast data for the VLAN or VSI. |
mld-snooping drop-unknown |
By default, dropping unknown IPv6 multicast data is disabled, and unknown IPv6 multicast data is flooded. |
Enabling MLD report suppression
This feature enables the Layer 2 device to forward only the first MLD report for an IPv6 multicast group to its directly connected Layer 3 device. Other reports for the same group in the same query interval are discarded. Use this feature to reduce the multicast traffic.
To enable MLD report suppression:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter MLD-snooping view. |
mld-snooping |
N/A |
|
3. Enable MLD report suppression. |
report-aggregation |
By default, MLD report suppression is enabled. |
Setting the maximum number of IPv6 multicast groups on a port
You can set the maximum number of IPv6 multicast groups on a port to regulate the port traffic.
Configuration restrictions and guidelines
When you set the maximum number of IPv6 multicast groups on a port, follow these restrictions and guidelines:
· This configuration takes effect only on the IPv6 multicast groups that the port joins dynamically.
· If the number of IPv6 multicast groups on a port exceeds the limit, the system removes all the forwarding entries related to that port. In this case, the receiver hosts attached to that port can join IPv6 multicast groups again before the number of IPv6 multicast groups on the port reaches the limit.
Configuration procedure
To set the maximum number of IPv6 multicast groups on a port:
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter Layer 2 Ethernet interface view or Layer 2 aggregate interface view. |
interface interface-type interface-number |
N/A |
|
3. Set the maximum number of IPv6 multicast groups on the port. |
mld-snooping group-limit limit [ vlan vlan-list ] |
By default, no limit is placed on the maximum number of IPv6 multicast groups on a port. |
Enabling IPv6 multicast group replacement
This feature enables the device to replace an existing group with a newly joined group when the number of groups exceeds the upper limit. This feature is typically used in the channel switching application. Without this feature, the device discards MLD reports for new groups, and the user cannot change to the new channel.
Configuration restrictions and guidelines
When you enable IPv6 multicast group replacement, follow these restrictions and guidelines:
· This configuration takes effect only on the multicast groups that the port joins dynamically.
· You can enable this feature globally for all ports in MLD-snooping view or for a port in interface view. For a port, the port-specific configuration takes priority over the global configuration.
Enabling IPv6 multicast group replacement globally
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter MLD-snooping view. |
mld-snooping |
N/A |
|
3. Enable IPv6 multicast group replacement globally. |
overflow-replace [ vlan vlan-list ] |
By default, IPv6 multicast group replacement is disabled globally. |
Enabling IPv6 multicast group replacement on a port
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter Layer 2 Ethernet interface view or Layer 2 aggregate interface view. |
interface interface-type interface-number |
N/A |
|
3. Enable IPv6 multicast group replacement on the port. |
mld-snooping overflow-replace [ vlan vlan-list ] |
By default, IPv6 multicast group replacement is disabled on a port. |
Enabling host tracking
This feature enables the device to record information about member hosts that are receiving IPv6 multicast data. The information includes IPv6 addresses of the hosts, length of time elapsed since the hosts joined IPv6 multicast groups, and remaining timeout time for the hosts. This feature facilitates monitoring and managing member hosts.
Enabling host tracking globally
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter MLD-snooping view. |
mld-snooping |
N/A |
|
3. Enable host tracking globally. |
host-tracking |
By default, host tracking is disabled globally. |
Enabling host tracking in a VLAN
|
Step |
Command |
Remarks |
|
1. Enter system view. |
system-view |
N/A |
|
2. Enter VLAN view. |
vlan vlan-id |
N/A |
|
3. Enable host tracking for the VLAN. |
mld-snooping host-tracking |
By default, host tracking is disabled in a VLAN. |
Displaying and maintaining MLD snooping
Execute display commands in any view and reset commands in user view.
|
Task |
Command |
|
(In standalone mode.) Display Layer 2 IPv6 multicast fast forwarding entries. |
display ipv6 l2-multicast fast-forwarding cache [ vlan vlan-id ] [ ipv6-group-address ] [ slot slot-number ] |
|
(In IRF mode.) Display Layer 2 IPv6 multicast fast forwarding entries. |
display ipv6 l2-multicast fast-forwarding cache [ vlan vlan-id ] [ ipv6-group-address ] [ chassis chassis-number slot slot-number ] |
|
(In standalone mode.) Display information about Layer 2 IPv6 multicast groups. |
display ipv6 l2-multicast ip [ group ipv6-group-address ] [ vlan vlan-id | vsi vsi-name ] [ slot slot-number ] |
|
(In IRF mode.) Display information about Layer 2 IPv6 multicast groups. |
display ipv6 l2-multicast ip [ group ipv6-group-address ] [ vlan vlan-id | vsi vsi-name ] [ chassis chassis-number slot slot-number ] |
|
(In standalone mode.) Display Layer 2 IPv6 multicast group entries. |
display ipv6 l2-multicast ip forwarding [ group ipv6-group-address ] [ vlan vlan-id | vsi vsi-name ] [ slot slot-number ] |
|
(In IRF mode.) Display Layer 2 IPv6 multicast group entries. |
display ipv6 l2-multicast ip forwarding [ group ipv6-group-address ] [ vlan vlan-id | vsi vsi-name ] [ chassis chassis-number slot slot-number ] |
|
(In standalone mode.) Display information about Layer 2 IPv6 MAC multicast groups. |
display ipv6 l2-multicast mac [ mac-address ] [ vlan vlan-id | vsi vsi-name ] [ slot slot-number ] |
|
(In IRF mode.) Display information about Layer 2 IPv6 MAC multicast groups. |
display ipv6 l2-multicast mac [ mac-address ] [ vlan vlan-id | vsi vsi-name ] [ chassis chassis-number slot slot-number ] |
|
(In standalone mode.) Display Layer 2 IPv6 MAC multicast group entries. |
display ipv6 l2-multicast mac forwarding [ mac-address ] [ vlan vlan-id | vsi vsi-name ] [ slot slot-number ] |
|
(In IRF mode.) Display Layer 2 IPv6 MAC multicast group entries. |
display ipv6 l2-multicast mac forwarding [ mac-address ] [ vlan vlan-id | vsi vsi-name ] [ chassis chassis-number slot slot-number ] |
|
Display static IPv6 multicast MAC address entries. |
display mac-address [ mac-address [ vlan vlan-id ] | [ multicast ] [ vlan vlan-id ] [ count ] ] |
|
Display MLD snooping status. |
display mld-snooping [ global | vlan vlan-id | vsi vsi-name ] |
|
(In standalone mode.) Display dynamic MLD snooping group entries. |
display mld-snooping group [ ipv6-group-address ] [ vlan vlan-id | vsi vsi-name ] [ verbose ] [ slot slot-number ] |
|
(In IRF mode.) Display dynamic MLD snooping group entries. |
display mld-snooping group [ ipv6-group-address ] [ vlan vlan-id | vsi vsi-name ] [ verbose ] [ chassis chassis-number slot slot-number ] |
|
(In standalone mode.) Display host tracking information. |
display mld-snooping host-tracking vlan vlan-id group ipv6-group-address [ slot slot-number ] |
|
(In IRF mode.) Display host tracking information. |
display mld-snooping host-tracking vlan vlan-id group ipv6-group-address [ chassis chassis-number slot slot-number ] |
|
(In standalone mode.) Display dynamic router port information. |
display mld-snooping router-port [ vlan vlan-id | vsi vsi-name ] [ verbose ] [ slot slot-number ] |
|
(In IRF mode.) Display dynamic router port information. |
display mld-snooping router-port [ vlan vlan-id | vsi vsi-name ] [ verbose ] [ chassis chassis-number slot slot-number ] |
|
(In standalone mode.) Display static MLD snooping group entries. |
display mld-snooping static-group [ ipv6-group-address ] [ vlan vlan-id ] [ verbose ] [ slot slot-number ] |
|
(In IRF mode.) Display static MLD snooping group entries. |
display mld-snooping static-group [ ipv6-group-address ] [ vlan vlan-id ] [ verbose ] [ chassis chassis-number slot slot-number ] |
|
(In standalone mode.) Display static router port information. |
display mld-snooping static-router-port [ vlan vlan-id ] [ verbose ] [ slot slot-number ] |
|
(In IRF mode.) Display static router port information. |
display mld-snooping static-router-port [ vlan vlan-id ] [ verbose ] [ chassis chassis-number slot slot-number ] |
|
Display statistics for the MLD messages and IPv6 PIM hello messages learned through MLD snooping. |
display mld-snooping statistics |
|
(In standalone mode.) Clear Layer 2 IPv6 multicast fast forwarding entries. |
reset ipv6 l2-multicast fast-forwarding cache [ vlan vlan-id ] { ipv6-source-address all } [ slot slot-number ] |
|
(In IRF mode.) Clear Layer 2 IPv6 multicast fast forwarding entries. |
reset ipv6 l2-multicast fast-forwarding cache [ vlan vlan-id ] { ipv6-source-address | all } [ chassis chassis-number slot slot-number ] |
|
Clear dynamic MLD snooping group entries. |
reset mld-snooping group { ipv6-group-address | all } [ vlan vlan-id | vsi vsi-name ] |
|
Clear dynamic router port information. |
reset mld-snooping router-port { all | vlan vlan-id | vsi vsi-name } |
|
Clear statistics for MLD messages and IPv6 PIM hello messages learned through MLD snooping. |
reset mld-snooping statistics |
For more information about the display mac-address multicast command, see IP Multicast Command Reference.
MLD snooping configuration examples
IPv6 group policy and simulated joining configuration example (for VLANs)
Network requirements
As shown in Figure 63, Router A runs MLDv1 and acts as the MLD querier, and Switch A runs MLDv1 snooping.
Configure the group policy and simulate joining to meet the following requirements:
· Host A and Host B receive only the IPv6 multicast data addressed to the IPv6 multicast group FF1E::101. IPv6 multicast data can be forwarded through HundredGigE 1/0/3 and HundredGigE 1/0/4 of Switch A uninterruptedly, even though Host A and Host B fail to receive the multicast data.
· Switch A will drop unknown IPv6 multicast data instead of flooding it in VLAN 100.
Configuration procedure
1. Assign an IPv6 address and prefix length to each interface, as shown in Figure 63. (Details not shown.)
2. Configure Router A:
# Enable IPv6 multicast routing.
<RouterA> system-view
[RouterA] ipv6 multicast routing
[RouterA-mrib6] quit
# Enable MLD on HundredGigE 1/0/1.
[RouterA] interface hundredgige 1/0/1
[RouterA-HundredGigE1/0/1] mld enable
[RouterA-HundredGigE1/0/1] quit
# Enable IPv6 PIM-DM on HundredGigE 1/0/2.
[RouterA] interface hundredgige 1/0/2
[RouterA-HundredGigE1/0/2] ipv6 pim dm
[RouterA-HundredGigE1/0/2] quit
3. Configure Switch A:
# Enable MLD snooping globally.
<SwitchA> system-view
[SwitchA] mld-snooping
[SwitchA-mld-snooping] quit
# Create VLAN 100, and assign HundredGigE 1/0/1 through HundredGigE 1/0/4 to the VLAN.
[SwitchA] vlan 100
[SwitchA-vlan100] port hundredgige 1/0/1 to hundredgige 1/0/4
# Enable MLD snooping, and enable dropping IPv6 unknown multicast data for VLAN 100.
[SwitchA-vlan100] mld-snooping enable
[SwitchA-vlan100] mld-snooping drop-unknown
[SwitchA-vlan100] quit
# Configure an IPv6 multicast group policy so that hosts in VLAN 100 can join only IPv6 multicast group FF1E::101.
[SwitchA] acl ipv6 basic 2001
[SwitchA-acl-ipv6-basic-2001] rule permit source ff1e::101 128
[SwitchA-acl-ipv6-basic-2001] quit
[SwitchA] mld-snooping
[SwitchA–mld-snooping] group-policy 2001 vlan 100
[SwitchA–mld-snooping] quit
# Configure HundredGigE 1/0/3 and HundredGigE 1/0/4 as simulated member hosts to join IPv6 multicast group FF1E::101.
[SwitchA] interface hundredgige 1/0/3
[SwitchA-HundredGigE1/0/3] mld-snooping host-join ff1e::101 vlan 100
[SwitchA-HundredGigE1/0/3] quit
[SwitchA] interface hundredgige 1/0/4
[SwitchA-HundredGigE1/0/4] mld-snooping host-join ff1e::101 vlan 100
[SwitchA-HundredGigE1/0/4] quit
Verifying the configuration
# Send MLD reports from Host A and Host B to join IPv6 multicast groups FF1E::101 and FF1E::202. (Details not shown.)
# Display brief information about dynamic MLD snooping group entries for VLAN 100 on Switch A.
[SwitchA] display mld-snooping group vlan 100
Total 1 entries.
VLAN 100: Total 1 entries.
(::, FF1E::101)
Host ports (2 in total):
HGE1/0/3 (00:03:23)
HGE1/0/4 (00:04:10)
The output shows the following information:
· Host A and Host B have joined IPv6 multicast group FF1E::101 through the member ports HundredGigE 1/0/4 and HundredGigE 1/0/3 on Switch A, respectively.
· Host A and Host B have failed to join the multicast group FF1E::202.
Static port configuration example (for VLANs)
Network requirements
As shown in Figure 64:
· Router A runs MLDv1 and acts as the MLD querier. Switch A, Switch B, and Switch C run MLDv1 snooping.
· Host A and Host C are permanent receivers of IPv6 multicast group FF1E::101.
Configure static ports to meet the following requirements:
· To enhance the reliability of IPv6 multicast traffic transmission, configure HundredGigE 1/0/3 and HundredGigE 1/0/5 on Switch C as static member ports for IPv6 multicast group FF1E::101.
· Suppose the STP runs on the network. To avoid data loops, the forwarding path from Switch A to Switch C is blocked. IPv6 multicast data flows to the receivers attached to Switch C only along the path of Switch A—Switch B—Switch C. When this path is blocked, a minimum of one MLD query-response cycle must be completed before IPv6 multicast data flows to the receivers along the path of Switch A—Switch C. In this case, the multicast delivery is interrupted during the process. For more information about the STP, see Layer 2—LAN Switching Configuration Guide.
Configure HundredGigE 1/0/3 on Switch A as a static router port. Then, IPv6 multicast data can flow to the receivers nearly uninterrupted along the path of Switch A—Switch C when the path of Switch A—Switch B—Switch C is blocked.
Configuration procedure
1. Assign an IPv6 address and prefix length to each interface, as shown in Figure 64. (Details not shown.)
2. Configure Router A:
# Enable IPv6 multicast routing.
<RouterA> system-view
[RouterA] ipv6 multicast routing
[RouterA-mrib6] quit
# Enable MLD on HundredGigE 1/0/1.
[RouterA] interface hundredgige 1/0/1
[RouterA-HundredGigE1/0/1] mld enable
[RouterA-HundredGigE1/0/1] quit
# Enable IPv6 PIM-DM on HundredGigE 1/0/2.
[RouterA] interface hundredgige 1/0/2
[RouterA-HundredGigE1/0/2] ipv6 pim dm
[RouterA-HundredGigE1/0/2] quit
3. Configure Switch A:
# Enable MLD snooping globally.
<SwitchA> system-view
[SwitchA] mld-snooping
[SwitchA-mld-snooping] quit
# Create VLAN 100, and assign HundredGigE 1/0/1 through HundredGigE 1/0/3 to the VLAN.
[SwitchA] vlan 100
[SwitchA-vlan100] port hundredgige 1/0/1 to hundredgige 1/0/3
# Enable MLD snooping for VLAN 100.
[SwitchA-vlan100] mld-snooping enable
[SwitchA-vlan100] quit
# Configure HundredGigE 1/0/3 as a static router port.
[SwitchA] interface hundredgige 1/0/3
[SwitchA-HundredGigE1/0/3] mld-snooping static-router-port vlan 100
[SwitchA-HundredGigE1/0/3] quit
4. Configure Switch B:
# Enable MLD snooping globally.
<SwitchB> system-view
[SwitchB] mld-snooping
[SwitchB-mld-snooping] quit
# Create VLAN 100, and assign HundredGigE 1/0/1 and HundredGigE 1/0/2 to the VLAN.
[SwitchB] vlan 100
[SwitchB-vlan100] port hundredgige 1/0/1 hundredgige 1/0/2
# Enable MLD snooping for VLAN 100.
[SwitchB-vlan100] mld-snooping enable
[SwitchB-vlan100] quit
5. Configure Switch C:
# Enable MLD snooping globally.
<SwitchC> system-view
[SwitchC] mld-snooping
[SwitchC-mld-snooping] quit
# Create VLAN 100, and assign HundredGigE 1/0/1 through HundredGigE 1/0/5 to the VLAN.
[SwitchC] vlan 100
[SwitchC-vlan100] port hundredgige 1/0/1 to hundredgige 1/0/5
# Enable MLD snooping for VLAN 100.
[SwitchC-vlan100] mld-snooping enable
[SwitchC-vlan100] quit
# Configure HundredGigE 1/0/3 and HundredGigE 1/0/5 as static member ports for IPv6 multicast group FF1E::101.
[SwitchC] interface hundredgige 1/0/3
[SwitchC-HundredGigE1/0/3] mld-snooping static-group ff1e::101 vlan 100
[SwitchC-HundredGigE1/0/3] quit
[SwitchC] interface hundredgige 1/0/5
[SwitchC-HundredGigE1/0/5] mld-snooping static-group ff1e::101 vlan 100
[SwitchC-HundredGigE1/0/5] quit
Verifying the configuration
# Display brief information about static router ports for VLAN 100 on Switch A.
[SwitchA] display mld-snooping static-router-port vlan 100
VLAN 100:
Router ports (1 in total):
HGE1/0/3
The output shows that HundredGigE 1/0/3 on Switch A has become a static router port.
# Display brief information about static MLD snooping group entries in VLAN 100 on Switch C.
[SwitchC] display mld-snooping static-group vlan 100
Total 1 entries).
VLAN 100: Total 1 entries).
(::, FF1E::101)
Host ports (2 in total):
HGE1/0/3
HGE1/0/5
The output shows that HundredGigE 1/0/3 and HundredGigE 1/0/5 on Switch C have become static member ports of IPv6 multicast group FF1E::101.
MLD snooping querier configuration example (for VLANs)
Network requirements
As shown in Figure 65:
· The network is a Layer 2-only network.
· Source 1 and Source 2 send multicast data to IPv6 multicast groups FF1E::101 and FF1E::102, respectively.
· Host A and Host C are receivers of IPv6 multicast group FF1E::101, and Host B and Host D are receivers of IPv6 multicast group FF1E::102.
· All host receivers run MLDv1 and all switches run MLDv1 snooping. Switch A (which is close to the multicast sources) acts as the MLD snooping querier.
To prevent the switches from flooding unknown IPv6 packets in the VLAN, enable all the switches to drop unknown IPv6 multicast packets.
Configuration procedure
1. Configure Switch A:
# Enable MLD snooping globally.
<SwitchA> system-view
[SwitchA] mld-snooping
[SwitchA-mld-snooping] quit
# Create VLAN 100, and assign HundredGigE 1/0/1 through HundredGigE 1/0/3 to the VLAN.
[SwitchA] vlan 100
[SwitchA-vlan100] port hundredgige 1/0/1 to hundredgige 1/0/3
# Enable MLD snooping, and enable dropping unknown IPv6 multicast data for VLAN 100.
[SwitchA-vlan100] mld-snooping enable
[SwitchA-vlan100] mld-snooping drop-unknown
# Configure Switch A as the MLD snooping querier.
[SwitchA-vlan100] MLD-snooping querier
[SwitchA-vlan100] quit
2. Configure Switch B:
# Enable MLD snooping globally.
<SwitchB> system-view
[SwitchB] mld-snooping
[SwitchB-mld-snooping] quit
# Create VLAN 100, and assign HundredGigE 1/0/1 through HundredGigE 1/0/4 to the VLAN.
[SwitchB] vlan 100
[SwitchB-vlan100] port hundredgige 1/0/1 to hundredgige 1/0/4
# Enable MLD snooping, and enable dropping unknown IPv6 multicast data for VLAN 100.
[SwitchB-vlan100] mld-snooping enable
[SwitchB-vlan100] mld-snooping drop-unknown
[SwitchB-vlan100] quit
3. Configure Switch C:
# Enable MLD snooping globally.
<SwitchC> system-view
[SwitchC] mld-snooping
[SwitchC-mld-snooping] quit
# Create VLAN 100, and assign HundredGigE 1/0/1 through HundredGigE 1/0/3 to the VLAN.
[SwitchC] vlan 100
[SwitchC-vlan100] port hundredgige 1/0/1 to hundredgige 1/0/3
# Enable MLD snooping, and enable dropping unknown IPv6 multicast data for VLAN 100.
[SwitchC-vlan100] mld-snooping enable
[SwitchC-vlan100] mld-snooping drop-unknown
[SwitchC-vlan100] quit
4. Configure Switch D:
# Enable MLD snooping globally.
<SwitchD> system-view
[SwitchD] mld-snooping
[SwitchD-mld-snooping] quit
# Create VLAN 100, and assign HundredGigE 1/0/1 and HundredGigE 1/0/2 to the VLAN.
[SwitchD] vlan 100
[SwitchD-vlan100] port hundredgige 1/0/1 to hundredgige 1/0/2
# Enable MLD snooping, and enable dropping unknown IPv6 multicast data for VLAN 100.
[SwitchD-vlan100] mld-snooping enable
[SwitchD-vlan100] mld-snooping drop-unknown
[SwitchD-vlan100] quit
Verifying the configuration
# Display statistics for MLD messages and IPv6 PIM hello messages learned through MLD snooping on Switch B.
[SwitchB] display mld-snooping statistics
Received MLD general queries: 3
Received MLDv1 specific queries: 0
Received MLDv1 reports: 12
Received MLD dones: 0
Sent MLDv1 specific queries: 0
Received MLDv2 reports: 0
Received MLDv2 reports with right and wrong records: 0
Received MLDv2 specific queries: 0
Received MLDv2 specific sg queries: 0
Sent MLDv2 specific queries: 0
Sent MLDv2 specific sg queries: 0
Received IPv6 PIM hello: 0
Received error MLD messages: 0
The output shows that all switches except Switch A can receive the MLD general queries after Switch A acts as the MLD snooping querier.
MLD snooping proxying configuration example (for VLANs)
Network requirements
As shown in Figure 66, Router A runs MLDv1 and acts as the MLD querier. Switch A runs MLDv1 snooping. Configure MLD snooping proxying so that Switch A can perform the following actions:
· Forward MLD report and done messages to Router A.
· Respond to MLD queries sent by Router A and forward the queries to downstream hosts.
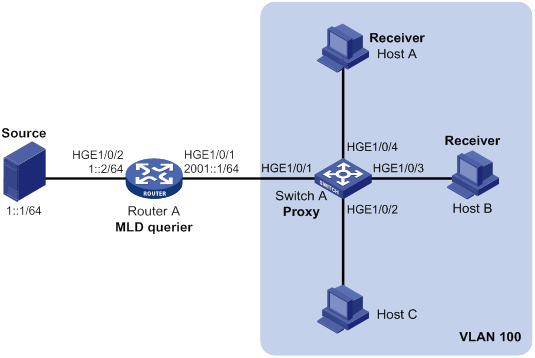
Configuration procedure
1. Assign an IPv6 address and subnet mask to each interface, as shown in Figure 66. (Details not shown.)
2. Configure Router A:
# Enable IPv6 multicast routing.
<RouterA> system-view
[RouterA] ipv6 multicast routing
[RouterA-mrib6] quit
# Enable MLD and IPv6 PIM-DM on HundredGigE 1/0/1.
[RouterA] interface hundredgige 1/0/1
[RouterA-HundredGigE1/0/1] mld enable
[RouterA-HundredGigE1/0/1] ipv6 pim dm
[RouterA-HundredGigE1/0/1] quit
# Enable IPv6 PIM-DM on HundredGigE 1/0/2.
[RouterA] interface hundredgige 1/0/2
[RouterA-HundredGigE1/0/2] ipv6 pim dm
[RouterA-HundredGigE1/0/2] quit
3. Configure Switch A:
# Enable MLD snooping globally.
<SwitchA> system-view
[SwitchA] mld-snooping
[SwitchA-mld-snooping] quit
# Create VLAN 100, and assign HundredGigE 1/0/1 through HundredGigE 1/0/4 to the VLAN.
[SwitchA] vlan 100
[SwitchA-vlan100] port hundredgige 1/0/1 to hundredgige 1/0/4
# Enable MLD snooping and MLD snooping proxying for the VLAN.
[SwitchA-vlan100] mld-snooping enable
[SwitchA-vlan100] mld-snooping proxy enable
[SwitchA-vlan100] quit
Verifying the configuration
# Send MLD reports from Host A and Host B to IPv6 multicast group FF1E::101. (Details not shown.)
# Display brief information about MLD snooping group entries on Switch A.
[SwitchA] display mld-snooping group
Total 1 entries.
VLAN 100: Total 1 entries.
(::, FF1E::101)
Host ports (2 in total):
HGE1/0/3 (00:04:09)
HGE1/0/4 (00:03:06)
The output shows that HundredGigE1/0/3 and HundredGigE1/0/4 have become member ports of IPv6 multicast group FF1E::101.
# Display MLD group membership information on Router A.
[RouterA] display mld group
MLD groups in total: 1
HundredGigE1/0/1(2001::1):
MLD groups reported in total: 1
Group address: FF1E::101
Last reporter: FE80::2FF:FFFF:FE00:1
Uptime: 00:00:31
Expires: 00:03:48
The output shows that HundredGigE1/0/1 has become the router port of IPv6 multicast group FF1E::101.
# Display MLD snooping group membership information on Switch A.
[SwitchA] display mld-snooping group
Total 1 entries.
VLAN 100: Total 1 entries.
(::, FF1E::101)
Host ports (1 in total):
HGE1/0/3 ( 00:01:23 )
The output shows that HundredGigE1/0/3 is the only member port of IPv6 multicast group FF1E::101.
Troubleshooting MLD snooping
Layer 2 multicast forwarding cannot function
Symptom
Layer 2 multicast forwarding cannot function through MLD snooping.
Solution
To resolve the problem:
1. Use the display mld-snooping command to display MLD snooping status.
2. If MLD snooping is not enabled, use the mld-snooping command in system view to enable MLD snooping globally. Then, use the mld-snooping enable command in VLAN view or VSI view to enable MLD snooping for the VLAN or VSI.
3. If MLD snooping is enabled globally but not enabled for the VLAN or VSI, use the mld-snooping enable command in VLAN view or VSI view to enable MLD snooping for the VLAN or VSI.
4. If the problem persists, contact H3C Support.
IPv6 multicast group policy does not work
Symptom
Hosts can receive IPv6 multicast data for IPv6 multicast groups that are not permitted by the IPv6 multicast group policy.
Solution
To resolve the problem:
1. Use the display acl ipv6 command to verify that the configured IPv6 ACL meets the IPv6 multicast group policy requirements.
2. Use the display this command in MLD-snooping view or in interface view to verify that the correct IPv6 multicast group policy has been applied. If the applied policy is not correct, use the group-policy or mld-snooping group-policy command to apply the correct IPv6 multicast group policy.
3. Use the display mld-snooping command to verify that dropping unknown IPv6 multicast data is enabled. If it is not, use the mld-snooping drop-unknown command to enable dropping unknown IPv6 multicast data.
4. If the problem persists, contact H3C Support.
Numerics
802
IGMP snooping message 802.1p priority, 29
MLD snooping 802.1p message priority, 193
A
ACL
IGMP snooping policy, 29
MLD snooping policy, 193
address
IP multicast, 5
MLD snooping message source IPv6 address, 191
adjusting
IGMP performance adjustment, 86
administrative scoping
PIM-SM domain divisions, 108
PIM-SM zone relationships, 108
PIM-SM zones, 108
admin-scoped zone
PIM-SM admin-scoped zone configuration, 134
aging
IGMP snooping dynamic port aging timer, 21
MLD snooping dynamic port aging timers, 185
Anycast
MSDP Anycast RP, 147
MSDP Anycast RP configuration, 166
PIM-SM RP, 104
troubleshooting MSDP RP entry exchange, 175
application
IP multicast data distribution, 4
architecture
IP multicast network, 5
AS
MSDP inter-AS multicast configuration (static RPF peers)(on switch), 162
ASM
IP multicast model), 4
assert
PIM-DM, 101
PIM-SM, 108
assigning
port-based multicast VLAN user port, 55
attribute
port-based multicast VLAN user port attribute, 55
B
BFD
PIM enable, 126
bootstrap router. See BSR
border
PIM domain border, 118
PIM-SM zone border router, 108
boundary
multicast forwarding, 70
broadcast
IP multicast transmission technique, 2
BSM
PIM-SM BSM semantic fragmentation disable, 118
PIM-SM administrative scoping zones, 108
PIM-SM BSR configuration, 117
PIM-SM C-BSR configuration, 117
PIM-SM RP discovery, 103
C
cache
MSDP SA message cache, 156
troubleshooting MSDP SA message cache entries, 174
candidate
bootstrap router. See C-BSR
RP. See C-RP
PIM-SM configuration, 117
PIM-SM RP discovery, 103
changing
multicast routing RPF route, 72
checking
multicast RPF check mechanism, 64
configuring
IGMP, 78, 84, 92
IGMP basic configuration, 92
IGMP basics, 84
IGMP multicast group policy, 85
IGMP multicast load splitting (IGMP proxy), 90
IGMP NSR, 91
IGMP performance adjustment, 86
IGMP proxying, 89, 97
IGMP query/response parameter (global), 87
IGMP query/response parameter (interface), 88
IGMP snooping, 12, 16, 35
IGMP snooping (for VLAN), 16
IGMP snooping (for VSI), 17
IGMP snooping basic features, 18
IGMP snooping fast-leave processing, 23
IGMP snooping general query/response parameters, 26
IGMP snooping general query/response parameters (global), 26
IGMP snooping group policy+simulated joining (for VLAN), 35
IGMP snooping message parameters, 27
IGMP snooping message source IP address, 27
IGMP snooping multicast group policy, 30
IGMP snooping multicast group policy (port), 30
IGMP snooping multicast source port filtering (IGMP-snooping view), 30
IGMP snooping multicast source port filtering (interface view), 31
IGMP snooping policy, 29
IGMP snooping port feature, 21
IGMP snooping proxying (for VLAN), 42
IGMP snooping querier, 25
IGMP snooping querier (for VLAN), 39
IGMP snooping query/response parameters (VLAN, VSI), 26
IGMP snooping simulated member host, 23
IGMP snooping static port, 22
IGMP snooping static port (for VLAN), 37
IGMP SSM mapping, 89
IGMP SSM mapping configuration, 94
IGMP static group member, 85
IPv6 static multicast MAC address entry, 183
MLD querier, 188
MLD snooping, 176, 180, 199
MLD snooping (for VLAN), 181
MLD snooping (for VSI), 181
MLD snooping basic features, 182
MLD snooping general query/response parameters, 189
MLD snooping general query/response parameters (global), 190
MLD snooping general query/response parameters (VLAN), 190
MLD snooping general query/response parameters (VSI), 190
MLD snooping group policy+simulated joining (for VLAN), 199
MLD snooping IPv6 multicast group policy, 193
MLD snooping IPv6 multicast group policy (global), 194
MLD snooping IPv6 multicast group policy (port), 194
MLD snooping IPv6 multicast source port filtering (interface view), 194
MLD snooping IPv6 multicast source port filtering (MLD-snooping view), 194
MLD snooping message parameters, 190
MLD snooping policy, 193
MLD snooping port features, 185
MLD snooping proxying (for VLAN), 205
MLD snooping querier (for VLAN), 203
MLD snooping report suppression, 195
MLD snooping simulated member host port, 186
MLD snooping static port (for VLAN), 201
MLD snooping static ports, 186
MSDP, 144, 150, 157
MSDP Anycast RP, 166
MSDP basics, 150
MSDP inter-AS multicast (static RPF peers)(on switch), 162
MSDP mesh group, 152
MSDP peer description, 152
MSDP peering connection, 151
MSDP PIM-SM inter-domain multicast, 157
MSDP RPF static peer, 151
MSDP SA message cache, 156
MSDP SA message filtering, 170
MSDP SA message originating RP, 154
MSDP SA message policy, 155
MSDP SA message-related parameters, 153
MSDP SA request message, 154
multicast forwarding boundary, 70
multicast group policy (global), 30
multicast routing load splitting, 70
multicast routing longest prefix match principle, 69
multicast routing+forwarding, 64, 68, 69, 72
multicast static route, 69
multicast VLAN, 52, 54, 57
PIM, 100, 128
PIM common features, 121
PIM common timer globally, 125
PIM common timer on interface, 125
PIM common timers, 124
PIM domain border, 118
PIM hello message option globally, 123
PIM hello message option on interface, 124
PIM hello message options, 123
PIM hello policy, 122
PIM message DSCP value, 127
PIM multicast source policy, 122
PIM snooping, 45, 46
PIM snooping (for VLAN), 47
PIM-DM, 112, 128
PIM-DM graft retry timer, 113
PIM-DM state-refresh parameter, 113
PIM-SM, 114
PIM-SM admin-scoped zone, 134
PIM-SM Anycast RP, 116
PIM-SM BSR, 117
PIM-SM C-BSR, 117
PIM-SM C-RP, 115
PIM-SM multicast source registration, 119
PIM-SM non-scoped zone, 131
PIM-SM RP, 115
PIM-SM static RP, 115
PIM-SSM, 120, 139
PIM-SSM group range, 121
port-based multicast VLAN, 55, 60
port-based multicast VLAN user port attribute, 55
source IP address for IGMP message (VLAN), 27
source IP address for IGMP message (VSI), 28
source IP address for MLD message (VLAN), 191
source IP address for MLD message (VSI), 192
static IPv6 multicast MAC address entry (system view), 183
static multicast MAC address entry, 20
static multicast MAC address entry (interface view), 20, 184
static multicast MAC address entry (system view), 20
sub-VLAN-based multicast VLAN, 54, 57
connecting
MSDP peering connection, 151
MSDP peering connection control, 152
connection
MSDP peer, 151
controlling
IGMPv3 host control capability, 80
MSDP peering connection, 152
creating
multicast routing RPF route, 74
PIM-SM RP discovery, 103
D
data
PIM multicast source policy, 122
describing
MSDP peer description, 152
device
IGMP basic configuration, 92
IGMP configuration, 92
IGMP proxying configuration, 97
IGMP SSM mapping configuration, 94
IGMPv3 host control, 80
MSDP configuration, 157
MSDP inter-AS multicast configuration (static RPF peers)(on switch), 162
MSDP PIM-SM inter-domain multicast configuration, 157
MSDP SA message filtering configuration, 170
multicast routing RPF route change, 72
multicast routing RPF route creation, 74
multicast routing+forwarding configuration, 72
PIM configuration, 128
PIM-DM configuration, 128
PIM-SM admin-scoped zone configuration, 134
PIM-SM non-scoped zone configuration, 131
PIM-SSM configuration, 139
disabling
IGMP snooping dynamic router port change, 24
MLD snooping dynamic router port change, 187
PIM-SM BSM forwarding, 119
PIM-SM BSM semantic fragmentation, 118
discovering
PIM-DM neighbor discovery, 100
PIM-SM neighbor discovery, 102
PIM-SM RP discovery, 103
PIM-SSM neighbor discovery, 110
displaying
IGMP, 91
IGMP snooping, 33
MLD snooping, 197
MSDP, 156
multicast routing+forwarding, 71
multicast VLAN, 56
PIM, 127
PIM snooping, 47
domain
MSDP configuration, 144
MSDP inter-domain multicast delivery, 145
MSDP PIM-SM inter-domain multicast, 157
PIM domain border, 118
PIM-SM administrative scoping, 108, 108
done message (MLD snooping), 178
DR
PIM BFD enable, 126
PIM hello message DR_Priority, 123
PIM passive mode enable, 126
PIM-SM DR election, 102
PIM-SM RPT building, 106
PIM-SSM DR election, 110
PIM-SSM SPT building, 110
DR election
PIM-SSM, 110
dropping
IGMP snooping unknown multicast data, 31
MLD snooping unknown IPv6 multicast data, 195
DSCP
PIM message DSCP value, 127
dynamic
IGMP snooping dynamic member port, 13
IGMP snooping dynamic port aging timer, 21
IGMP snooping dynamic router port, 13
IGMP snooping dynamic router port change, 24
MLD snooping dynamic member port, 177
MLD snooping dynamic port aging timers, 185
MLD snooping dynamic router port, 177
MLD snooping dynamic router port change, 187
E
electing
IGMPv2 querier election, 79
enabling
fast-leave processing (global), 23
fast-leave processing (port), 24
IGMP, 84
IGMP fast-leave processing, 88
IGMP forwarding (non-querier interface), 90
IGMP proxying, 89
IGMP snooping, 18
IGMP snooping (IGMP-snooping view), 18
IGMP snooping (VLAN view), 18
IGMP snooping (VSI view), 18
IGMP snooping host tracking (global), 33
IGMP snooping host tracking (VLAN), 33
IGMP snooping inner VLAN ID-based forwarding, 24
IGMP snooping proxying, 26
IGMP snooping querier, 25
IGMP snooping report suppression, 31
IP multicast routing, 68
MLD snooping, 182
MLD snooping (MLD-snooping view), 182
MLD snooping (VLAN view), 182
MLD snooping (VSI view), 182
MLD snooping fast-leave processing (global), 187
MLD snooping fast-leave processing (port), 187
MLD snooping host tracking (global), 197
MLD snooping host tracking (VLAN), 197
MLD snooping inner VLAN ID-based forwarding, 188
MLD snooping IPv6 multicast group replacement (global), 196
MLD snooping IPv6 multicast group replacement (port), 196
MLD snooping IPv6 multicast source port filtering, 194
MLD snooping proxying, 190
MLD snooping querier, 189
MSDP, 150
MSDP NSR, 156
MSDP SA message multicast data encapsulation, 153
multicast group replacement (global), 32
multicast group replacement (port), 32
PIM BFD, 126
PIM NSR, 127
PIM passive mode, 126
PIM SNMP notification, 127
PIM-DM, 112
PIM-DM state-refresh, 113
PIM-SM, 114
PIM-SM Auto-RP listening, 116
encapsulating
MSDP SA message multicast data encapsulation, 153
Ethernet
IP multicast MAC address, 8
IP multicast overview, 1
PIM configuration, 100, 128
PIM-DM configuration, 128
PIM-SM admin-scoped zone configuration, 134
PIM-SM non-scoped zone configuration, 131
PIM-SSM configuration, 139
F
fast
IGMP fast-leave processing, 88
IGMP snooping fast-leave processing, 23
fast-leave processing
MLD snooping, 187
filtering
IGMP snooping multicast source port filtering, 30
IGMP snooping unknown multicast data drop, 31
MLD snooping IPv6 multicast source port, 194
MLD snooping IPv6 multicast unknown data drop, 195
MLD snooping policy, 193
MSDP SA message filtering configuration, 170
MSDP SA message policy, 155
PIM hello policy, 122
PIM multicast source policy, 122
flooding
PIM-DM SPT building, 100
forwarding
IGMP forwarding (non-querier interface), 90
IGMP snooping forwarding entries, 19
IGMP snooping last member query interval, 20
IP multicast packets, 11
MLD snooping forwarding entries, 183
MLD snooping last member query interval, 184
multicast forwarding, 64, See also multicast routing+forwarding
multicast VLAN forwarding entries max, 56
PIM configuration, 100, 128
PIM snooping configuration, 45, 46
PIM snooping configuration (for VLAN), 47
PIM VPN support, 111
PIM-DM, 100
PIM-DM configuration, 128
PIM-SM admin-scoped zone configuration, 134
PIM-SM BSM forwarding disable, 119
PIM-SM non-scoped zone configuration, 131
PIM-SSM configuration, 139
troubleshooting MLD snooping Layer 2 forwarding, 207
G
global-scope zone
PIM-SM zone border router, 108
global-scoped zone
PIM-SM admin-scoped/global-scoped zone relationship, 108
graft
PIM-DM, 101
PIM-DM graft retry timer, 113
group
IGMP multicast group policy, 85
IGMP snooping multicast group policy, 30
IGMP snooping multicast group replacement, 32
IGMP static group member configuration, 85
MLD snooping IPv6 multicast group policy, 193
MLD snooping IPv6 multicast group replacement, 196
MLD snooping IPv6 multicast groups on port, 195
MSDP mesh group, 152
PIM-SSM group range, 121
H
hello
PIM common timer configuration (global), 125
PIM common timer configuration (on interface), 125
PIM hello message option configuration (global), 123
PIM hello message option configuration (on interface), 124
PIM hello message options, 123
PIM hello policy, 122
holdtime
PIM hello message option, 123
host
IGMP snooping host tracking, 33
IGMP snooping simulated member host, 23
IGMPv3 host control capability, 80
MLD snooping simulated member host port, 186
I
ID
PIM hello message Generation ID option, 123
basic configuration, 84, 92
configuration, 78, 84, 92
display, 91
enable, 84
fast-leave processing, 88
maintain, 91
multicast forwarding (non-querier interface), 90
multicast forwarding enable restrictions, 90
multicast group policy configuration, 85
multicast load splitting (IGMP proxy), 90
multicast VLAN configuration, 52, 54, 57
nonstop routing (NSR) enable, 91
performance adjustment, 86
PIM-SSM IGMPv3 relationship, 110
port-based multicast VLAN configuration, 60
protocols and standards, 83
proxying, 82
proxying configuration, 89, 97
proxying enable, 89
query/response parameter configuration, 86
query/response parameter configuration restrictions, 86
snooping. See IGMP snooping
SSM mapping, 81
SSM mapping configuration, 89, 94
static group member configuration, 85
static group member configuration restrictions, 85
sub-VLAN-based multicast VLAN configuration, 57
troubleshoot, 98
troubleshoot inconsistent membership information, 98
troubleshoot no membership information on router, 98
version specification, 85
versions, 78
VPN support, 83
basic configuration, 18
configuration, 12, 16, 35
display, 33
dynamic port aging timer, 21
dynamic router port change disable, 24
enable, 18
fast-leave processing enable, 23
fast-leave processing enable restrictions, 23
forwarding entries, 19
general query, 14
general query/response parameter configuration, 26
group policy+simulated joining configuration (for VLAN), 35
host tracking enable, 33
how it works, 14
IGMP last member query interval configuration restrictions, 21
inner VLAN ID-based forwarding, 24
last member query interval, 20
leave message, 14
maintain, 33
membership report, 14
message 802.1p priority, 29
message parameter configuration, 27
message source IP address, 27
multicast group policy configuration, 30
multicast group policy configuration restrictions, 30
multicast group replacement, 32
multicast group replacement restrictions, 32
multicast groups on port, 32
multicast groups on port restrictions, 32
multicast source port filtering, 30
policy configuration, 29
port, 12
port feature configuration, 21
protocols and standards, 16
proxying, 15
proxying configuration, 26
proxying configuration (for VLAN), 42
querier configuration, 25
querier configuration (for VLAN), 39
querier enable, 25
querier enable restrictions, 25
report suppression, 31
simulated member host configuration, 23
static port configuration, 22
static port configuration (for VLAN), 37
troubleshoot, 44
troubleshoot Layer 2 multicast forwarding, 44
troubleshoot multicast group filter, 44
unknown multicast data drop, 31
version specification, 19
VLAN configuration, 16
VSI configuration, 17
IGMPv1
IGMP versions, 78
implementation, 78, 78
version specification, 85
IGMPv1 snooping version, 19
IGMPv2
features, 79
IGMP versions, 78
leave group mechanism, 79
querier election, 79
version specification, 85
IGMPv2 snooping version, 19
IGMPv3
features, 80
host control capability, 80
IGMP versions, 78
query capability, 80
report capability, 80
version specification, 85
IGMPv3 snooping version, 19
inconsistent membership information (IGMP), 98
Internet
Group Management Protocol. Use IGMP
interval
IGMP snooping last member query interval, 20
IP addressing
IGMP snooping message source IP address, 27
IP multicast address, 5
IP multicast packet forwarding, 11
IP multicast
address, 5
architecture, 5
ASM model, 4
broadcast transmission technique, 2
common notation, 4
data distribution, 4
Ethernet multicast MAC address, 8
features, 3
IGMP basic configuration, 84, 92
IGMP configuration, 78, 84, 92
IGMP display, 91
IGMP fast-leave processing, 88
IGMP maintain, 91
IGMP multicast forwarding (non-querier interface), 90
IGMP multicast group policy, 85
IGMP multicast load splitting (IGMP proxy), 90
IGMP performance adjustment, 86
IGMP protocols and standards, 83
IGMP proxying, 82, 89
IGMP proxying configuration, 97
IGMP proxying enable, 89
IGMP query/response parameters, 86
IGMP snooping basic configuration, 18
IGMP snooping configuration, 12, 16, 35
IGMP snooping display, 33
IGMP snooping dynamic router port change, 24
IGMP snooping fast-leave processing, 23
IGMP snooping forwarding entries, 19
IGMP snooping general query, 14
IGMP snooping general query/response parameters, 26
IGMP snooping group policy, 30
IGMP snooping group policy+simulated joining configuration (for VLAN), 35
IGMP snooping groups on port, 32
IGMP snooping last member query interval, 20
IGMP snooping leave message, 14
IGMP snooping maintain, 33
IGMP snooping membership report, 14
IGMP snooping message 802.1p priority, 29
IGMP snooping message parameters, 27
IGMP snooping message source IP address, 27
IGMP snooping multicast group replacement, 32
IGMP snooping policy, 29
IGMP snooping port, 12
IGMP snooping port feature, 21
IGMP snooping protocols and standards, 16
IGMP snooping proxying, 15, 26
IGMP snooping proxying configuration (for VLAN), 42
IGMP snooping querier, 25
IGMP snooping querier configuration (for VLAN), 39
IGMP snooping report suppression, 31
IGMP snooping source port filtering, 30
IGMP snooping static port, 22
IGMP snooping static port configuration (for VLAN), 37
IGMP snooping unknown multicast data drop, 31
IGMP snooping version, 19
IGMP SSM mapping, 81
IGMP SSM mapping configuration, 94
IGMP static group member configuration, 85
IGMP version specification, 85
IGMP versions, 78
IGMP VPN support, 83
IGMPv1, 78, 78
IGMPv2, 79
IGMPv3, 80
Layer 2 protocols, 10
Layer 3 protocols, 9
MLD snooping 802.1p message priority, 193
MLD snooping basic configuration, 182
MLD snooping configuration, 176, 180, 199
MLD snooping display, 197
MLD snooping dynamic port aging timers, 185
MLD snooping dynamic router port change, 187
MLD snooping fast-leave processing enable, 187
MLD snooping forwarding entries, 183
MLD snooping general query/response parameters, 189
MLD snooping group policy, 193
MLD snooping group policy+simulated joining configuration (for VLAN), 199
MLD snooping group replacement, 196
MLD snooping groups on port, 195
MLD snooping host tracking, 196
MLD snooping last member query interval, 184
MLD snooping maintain, 197
MLD snooping message parameters, 190
MLD snooping message source IPv6 address, 191
MLD snooping policy, 193
MLD snooping port feature configuration, 185
MLD snooping port types, 176
MLD snooping protocols and standards, 180
MLD snooping proxying configuration (for VLAN), 205
MLD snooping querier configuration, 188
MLD snooping querier configuration (for VLAN), 203
MLD snooping report suppression, 195
MLD snooping simulated member host port, 186
MLD snooping source port filtering, 194
MLD snooping static port configuration, 186
MLD snooping static port configuration (for VLAN), 201
MLD snooping unknown data drop, 195
models, 4
MSDP Anycast RP, 147
MSDP Anycast RP configuration, 166
MSDP basics configuration, 150
MSDP configuration, 144, 150, 157
MSDP display, 156
MSDP inter-domain multicast delivery, 145
MSDP maintain, 156
MSDP mesh group, 152
MSDP peer, 144, 151
MSDP peer description, 152
MSDP peering connection, 151
MSDP peering connection control, 152
MSDP peer-RPF forwarding, 148
MSDP protocols and standards, 149
MSDP RPF static peer, 151
MSDP SA message cache, 156
MSDP SA message filtering configuration, 170
MSDP SA message multicast data encapsulation, 153
MSDP SA message originating RP, 154
MSDP SA message policy, 155
MSDP SA message-related parameters, 153
MSDP SA request message, 154
MSDP VPN support, 149
multicast routing+forwarding. See multicast routing+forwarding
multicast transmission technique, 2
multicast VLAN display, 56
multicast VLAN maintain, 56
overview, 1
packet forwarding, 11
PIM common features, 121
PIM common timers, 124
PIM configuration, 100, 128
PIM display, 127
PIM hello message options, 123
PIM hello policy, 122
PIM join/prune message size, 125
PIM message DSCP value, 127, 127
PIM multicast source policy, 122
PIM snooping configuration, 45, 46
PIM snooping configuration (for VLAN), 47
PIM snooping display, 47
PIM snooping maintain, 47
PIM VPN support, 111
PIM-DM, 100
PIM-DM assert, 101
PIM-DM configuration, 112, 128
PIM-DM enable, 112
PIM-DM graft, 101
PIM-DM graft retry timer, 113
PIM-DM neighbor discovery, 100
PIM-DM SPT building, 100
PIM-DM state-refresh, 113
PIM-DM state-refresh parameters, 113
PIM-SM, 102
PIM-SM administrative scoping, 108
PIM-SM admin-scoped zone configuration, 134
PIM-SM Anycast RP, 104
PIM-SM configuration, 114
PIM-SM DR election, 102
PIM-SM enable, 114
PIM-SM multicast source registration, 119
PIM-SM neighbor discovery, 102
PIM-SM non-scoped zone configuration, 131
PIM-SM RP configuration, 115
PIM-SM RP discovery, 103
PIM-SM RPT building, 106
PIM-SM source registration, 106
PIM-SM SPT switchover, 107
PIM-SSM, 110
PIM-SSM configuration, 120, 139
PIM-SSM DR election, 110
PIM-SSM group range, 121
PIM-SSM neighbor discovery, 110
PIM-SSM SPT building, 110
protocols and standards, 9
routing enable, 68
SFM model, 5
SSM model, 5
static MAC address entry configuration, 20
transmission techniques, 1
troubleshooting IGMP, 98
troubleshooting IGMP inconsistent membership information, 98
troubleshooting IGMP no membership information on router, 98
troubleshooting IGMP snooping, 44
troubleshooting IGMP snooping Layer 2 multicast forwarding, 44
troubleshooting IGMP snooping multicast group filter, 44
troubleshooting MLD snooping, 207
troubleshooting MLD snooping group policy, 208
troubleshooting MLD snooping Layer 2 forwarding, 207
troubleshooting MSDP, 173
troubleshooting PIM, 142
troubleshooting PIM abnormal multicast data termination, 142
troubleshooting PIM multicast distribution tree, 142
troubleshooting PIM snooping, 51
troubleshooting PIM snooping does not work, 51
troubleshooting PIM-SM multicast source registration failure, 143
unicast transmission technique, 1
IPv4
Ethernet multicast MAC address, 8
IGMP snooping multicast source port filtering, 30
IP multicast address, 5
IPv6
Ethernet multicast MAC address, 8
IP multicast address, 5
MLD snooping dynamic router port change, 187
MLD snooping simulated member host port, 186
PIM-DM configuration, 112
PIM-SM DR election, 102
IPv6 multicast
MLD snooping proxying, 179, 190
static MAC address entry configuration, 183
J
joining
PIM join/prune message size, 125
L
Layer 2
IP multicast protocols, 10
multicast routing+forwarding hardware resource mode, 70
PIM snooping configuration, 45, 46
PIM snooping configuration (for VLAN), 47
troubleshooting IGMP snooping Layer 2 multicast forwarding, 44
troubleshooting MLD snooping Layer 2 forwarding, 207
Layer 3
IP multicast protocols, 9
PIM configuration, 100, 128
PIM-DM configuration, 128
PIM-SM admin-scoped zone configuration, 134
PIM-SM non-scoped zone configuration, 131
PIM-SSM configuration, 139
leave message
IGMP snooping, 14
leaving
IGMPv2 leave group mechanism, 79
load splitting
IGMP multicast load splitting (IGMP proxy), 90
multicast routing configuration, 70
M
MAC addressing
Ethernet multicast MAC address, 8
IPv6 static multicast MAC address entry, 183
MLD snooping configuration, 176, 199
MLD snooping group policy+simulated joining configuration (for VLAN), 199
MLD snooping static port configuration (for VLAN), 201
static multicast MAC address entry, 20
maintaining
IGMP, 91
IGMP snooping, 33
MLD snooping, 197
MSDP, 156
multicast routing+forwarding, 71
multicast VLAN, 56
PIM snooping, 47
mapping
IGMP SSM mapping, 81, 89
IGMP SSM mapping configuration, 94
MLD snooping configuration, 176, 199
MLD snooping static port configuration (for VLAN), 201
member
IGMP snooping router port, 13
IGMP snooping simulated member host, 23
MLD snooping member port, 177
MLD snooping simulated member host port, 186
mesh
MSDP mesh group, 152
message
IGMP snooping leave, 14
IGMP snooping message 802.1p priority, 29
IGMP snooping message parameters, 27
MLD snooping 802.1p message priority, 193
MLD snooping configuration, 176, 199
MLD snooping done, 178
MLD snooping fast-leave processing enable, 187
MLD snooping group policy+simulated joining configuration (for VLAN), 199
MLD snooping message source IPv6 address, 191
MLD snooping static port configuration (for VLAN), 201
MSDP SA message cache, 156
MSDP SA message filtering configuration, 170
MSDP SA message multicast data encapsulation, 153
MSDP SA message originating RP, 154
MSDP SA message policy, 155
MSDP SA message-related parameters, 153
MSDP SA request message, 154
PIM hello message options, 123
PIM hello policy, 122
PIM join/prune message size, 125
PIM message DSCP value, 127
MLD
snooping. See MLD snooping
802.1p message priority, 193
basic configuration, 182
configuration, 176, 180, 199
display, 197
done message, 178
dynamic port aging timers, 185
dynamic router port change disable, 187
enable, 182
fast-leave processing enable, 187
fast-leave processing enable restrictions, 187
forwarding entries, 183
general query, 178
general query/response parameter configuration, 189
host tracking, 196
how it works, 178
inner VLAN ID-based forwarding, 188
IPv6 group policy+simulated joining configuration (for VLAN), 199
IPv6 multicast group configuration on port restrictions, 195
IPv6 multicast group policy, 193
IPv6 multicast group policy configuration restrictions, 193
IPv6 multicast group replacement, 196
IPv6 multicast group replacement restrictions, 196
IPv6 multicast groups on port, 195
IPv6 multicast source port filtering, 194
IPv6 multicast unknown data drop, 195
last listener query interval enable restrictions, 184
last member query interval, 184
maintain, 197
membership report, 178
message parameter configuration, 190
message source IPv6 address, 191
policy configuration, 193
port feature configuration, 185
port types, 176
protocols and standards, 180
proxying, 179
proxying configuration, 190
proxying configuration (for VLAN), 205
querier configuration, 188
querier configuration (for VLAN), 203
querier enable, 189
querier enable restrictions, 189
report suppression, 195
simulated member host port, 186
static port configuration, 186
static port configuration (for VLAN), 201
troubleshoot, 207
troubleshoot IPv6 multicast group policy, 208
troubleshoot MLD snooping Layer 2 forwarding, 207
VLAN configuration, 181
VSI configuration, 181
mode
PIM passive mode enable, 126
model
IP multicast, 4
IP multicast ASM, 4
IP multicast SFM, 5
IP multicast SSM, 5
Anycast RP, 147
Anycast RP configuration, 166
basics configuration, 150
configuration, 144, 150, 157
display, 156
enable, 150
how it works, 144
inter-AS multicast configuration (static RPF peers)(on switch), 162
inter-domain multicast delivery, 145
maintain, 156
mesh group, 152
nonstop routing (NSR) enable, 156
NSR enable, 156
peer, 144
peer configuration, 151
peer description, 152
peering connection, 151
peering connection control, 152
peer-RPF forwarding, 148
PIM-SM inter-domain multicast configuration, 157
protocols and standards, 149
RPF static peer, 151
SA message cache, 156
SA message filtering configuration, 170
SA message multicast data encapsulation, 153
SA message originating RP, 154
SA message policy, 155
SA message-related parameters, 153
SA request message, 154
troubleshoot, 173
troubleshoot peers stay in disabled state, 174
troubleshoot RP entry exchange, 175
troubleshoot SA message cache, 174
VPN support, 149
multicast
IP multicast transmission technique, 2
Multicast Source Discovery Protocol. Use MSDP
boundary configuration, 70
configuration, 64, 68, 69, 72
display, 71
IP multicast routing enable, 68
load splitting configuration, 70
longest prefix match principle, 69
maintain, 71
multicast hardware resource mode setting, 70
RPF check mechanism, 64
RPF route change, 66, 72
RPF route creation, 66, 74
static route, 66
static route configuration, 69
troubleshoot, 76
troubleshoot static route failure, 76
unicast subnets, 67
multicast VLAN
configuration, 52, 54, 57
display, 56
forwarding entries max, 56
maintain, 56
port-based configuration, 60
port-based multicast VLAN configuration, 55
port-based multicast VLAN user port assignment, 55
port-based multicast VLAN user port assignment restrictions, 55
port-based multicast VLAN user port attribute, 55
sub-VLAN-based configuration, 57
sub-VLAN-based multicast VLAN configuration, 54
sub-VLAN-based multicast VLAN configuration restrictions, 54
N
neighbor discovery
PIM-DM, 100
PIM-SM, 102
PIM-SSM, 110
network
IGMP basic configuration, 84, 92
IGMP fast-leave processing, 88
IGMP multicast group policy, 85
IGMP proxying configuration, 97
IGMP query/response parameters, 86
IGMP snooping basic configuration, 18
IGMP snooping group policy+simulated joining configuration (for VLAN), 35
IGMP snooping host tracking, 33
IGMP snooping multicast source port filtering, 30
IGMP snooping proxying configuration (for VLAN), 42
IGMP snooping querier configuration (for VLAN), 39
IGMP snooping static port configuration (for VLAN), 37
IGMP SSM mapping configuration, 94
IGMP static group member configuration, 85
IGMP version specification, 85
IP multicast address, 5
IP multicast architecture, 5
IP multicast models, 4
IP multicast packet forwarding, 11
IPv6 static multicast MAC address entry, 183
MLD snooping basic configuration, 182
MLD snooping group policy+simulated joining configuration (for VLAN), 199
MLD snooping IPv6 multicast source port filtering, 194
MLD snooping proxying configuration (for VLAN), 205
MLD snooping querier configuration (for VLAN), 203
MLD snooping static port configuration (for VLAN), 201
MSDP Anycast RP configuration, 166
MSDP basics configuration, 150
MSDP configuration, 157
MSDP inter-AS multicast configuration (static RPF peers)(on switch), 162
MSDP mesh group, 152
MSDP NSR enable, 156
MSDP peer, 151
MSDP peer description, 152
MSDP peering connection, 151
MSDP peering connection control, 152
MSDP PIM-SM inter-domain multicast configuration, 157
MSDP RPF static peer, 151
MSDP SA message filtering configuration, 170
MSDP SA message-related parameters, 153
multicast forwarding across unicast subnets, 67
multicast routing RPF route change, 72
multicast routing RPF route creation, 74
multicast routing+forwarding configuration, 69
multicast static route, 66
multicast VLAN forwarding entries max, 56
PIM BFD enable, 126
PIM common features, 121
PIM common timers, 124
PIM domain border, 118
PIM hello message options, 123
PIM hello policy, 122
PIM join/prune message size, 125
PIM message DSCP value, 127
PIM multicast source policy, 122
PIM NSR enable, 127
PIM passive mode enable, 126
PIM SNMP notification enable, 127
PIM-DM assert, 101
PIM-DM configuration, 128
PIM-DM graft, 101
PIM-DM graft retry timer, 113
PIM-DM neighbor discovery, 100
PIM-DM SPT building, 100
PIM-DM state-refresh, 113
PIM-DM state-refresh parameters, 113
PIM-SM C-RP, 115
PIM-SM administrative scoping, 108
PIM-SM admin-scoped zone configuration, 134
PIM-SM Anycast RP, 104, 116
PIM-SM Auto-RP, 116
PIM-SM BSM forwarding disable, 119
PIM-SM BSM semantic fragmentation, 118
PIM-SM BSR configuration, 117
PIM-SM C-BSR, 117
PIM-SM configuration, 114
PIM-SM DR election, 102
PIM-SM multicast source registration, 106, 119
PIM-SM neighbor discovery, 102
PIM-SM non-scoped zone configuration, 131
PIM-SM RP configuration, 115
PIM-SM RP discovery, 103
PIM-SM RPT building, 106
PIM-SM SPT switchover, 107
PIM-SM static RP, 115
PIM-SM zone relationships, 108
PIM-SSM configuration, 139
PIM-SSM DR election, 110
PIM-SSM group range, 121
PIM-SSM neighbor discovery, 110
PIM-SSM SPT building, 110
port-based multicast VLAN configuration, 55, 60
port-based multicast VLAN user port assignment, 55
port-based multicast VLAN user port attribute, 55
static multicast MAC address entry, 20
sub-VLAN-based multicast VLAN configuration, 54, 57
network management
IGMP configuration, 78, 84, 92
IGMP performance adjustment, 86
IGMP snooping configuration, 12, 16, 35
IP multicast overview, 1
MLD snooping configuration, 176, 180, 199
MSDP configuration, 144, 150
multicast routing+forwarding configuration, 64, 68, 72
multicast VLAN configuration, 52, 54, 57
PIM configuration, 100, 128
PIM snooping configuration, 45, 46
PIM snooping configuration (for VLAN), 47
PIM VPN support, 111
PIM-DM, 100
PIM-DM configuration, 112
PIM-SM, 102
PIM-SSM, 110
PIM-SSM configuration, 120
transmission techniques, 1
non-querier
IGMP forwarding (non-querier interface), 90
non-scoped zone
PIM-SM non-scoped zone configuration, 131
notifying
PIM SNMP notification enable, 127
NSR
IGMP, 91
MSDP NSR enable, 156
PIM NSR enable, 127
O
option
PIM hello message DR_Priority, 123
PIM hello message Generation ID, 123
PIM hello message holdtime, 123
PIM hello message LAN_Prune_Delay, 123
PIM hello message options, 123
P
packet
IP multicast forwarding, 11
multicast RPF check, 65
PIM snooping configuration, 45, 46
PIM snooping configuration (for VLAN), 47
parameter
IGMP query/response parameters, 86
IGMP snooping general query/response parameters, 26
IGMP snooping message parameters, 27
MSDP SA message-related parameters, 153
PIM-DM state-refresh, 113
peer
MSDP Anycast RP, 147
MSDP inter-AS multicast configuration (static RPF peers)(on switch), 162
MSDP inter-domain multicast delivery, 145
MSDP intermediate, 144
MSDP NSR enable, 156
MSDP peer, 151
MSDP peer description, 152
MSDP peering connection, 151
MSDP peering connection control, 152
MSDP peer-RPF forwarding, 148
MSDP receiver-side, 144
MSDP RPF static peer, 151
MSDP source-side, 144
troubleshooting MSDP peer stays in disabled state, 174
BFD enable, 126
common feature configuration, 121
common timer configuration, 124
common timer configuration (global), 125
common timer configuration (on interface), 125
configuration, 100, 128
display, 127
DM. See PIM-DM
hello message option configuration (global), 123
hello message option configuration (on interface), 124
hello message options, 123
hello policy configuration, 122
join/prune message size, 125
multicast source policy, 122
nonstop routing (NSR) enable, 127
outgoing packet DSCP value, 127
passive mode enable, 126
passive mode enable restrictions, 126
protocol relationships, 111
protocols and standards, 111
SM. See PIM-SM
SNMP notification enable, 127
snooping. See PIM snooping
SSM. See PIM-SSM
troubleshoot, 142
troubleshoot abnormal multicast data termination, 142
troubleshoot multicast distribution tree, 142
VPN support, 111
configuration, 45, 46
configuration (for VLAN), 47
display, 47
maintain, 47
troubleshoot, 51
troubleshoot PIM snooping does not work, 51
assert, 101
configuration, 112, 128
enable, 112
graft, 101
graft retry timer, 113
introduction, 100
multicast routing+forwarding configuration, 69
neighbor discovery, 100
PIM BFD enable, 126
PIM configuration, 100
PIM NSR enable, 127
PIM passive mode enable, 126
PIM protocol relationships, 111
PIM SNMP notification enable, 127
protocols and standards, 111
SPT building, 100
state-refresh enable, 113
state-refresh parameters, 113
administrative scoping, 108
administrative scoping zones, 108
admin-scoped zone configuration, 134
Anycast RP, 104
Anycast RP configuration, 116
assert, 108
Auto-RP listening configuration, 116
BSM forwarding disable, 119
BSM semantic fragmentation, 118
BSR configuration, 117
C-BSR configuration, 117
configuration, 114
C-RP configuration, 115
DR election, 102
enable, 114
introduction, 102
MSDP Anycast RP, 147
MSDP Anycast RP configuration, 166
MSDP basics configuration, 150
MSDP configuration, 144, 150, 157
MSDP enable, 150
MSDP inter-AS multicast configuration (static RPF peers)(on switch), 162
MSDP inter-domain multicast configuration, 157
MSDP inter-domain multicast delivery, 145
MSDP mesh group, 152
MSDP peer, 144, 151
MSDP peer description, 152
MSDP peering connection, 151
MSDP peering connection control, 152
MSDP peer-RPF forwarding, 148
MSDP RPF static peer, 151
MSDP SA message cache, 156
MSDP SA message filtering configuration, 170
MSDP SA message multicast data encapsulation, 153
MSDP SA message originating RP, 154
MSDP SA message policy, 155
MSDP SA message-related parameters, 153
MSDP SA request message, 154
multicast routing+forwarding configuration, 69
multicast source registration, 106, 119
neighbor discovery, 102
non-scoped zone configuration, 131
PIM BFD enable, 126
PIM configuration, 100
PIM domain border, 118
PIM NSR enable, 127
PIM passive mode enable, 126
PIM protocol relationships, 111
PIM SNMP notification enable, 127
protocols and standards, 111
RP configuration, 115
RP discovery, 103
RPT building, 106
SPT switchover, 107
static RP configuration, 115
troubleshoot multicast source registration failure, 143
troubleshoot RP cannot be built, 143
troubleshoot RP cannot join SPT, 143
zone relationships, 108
configuration, 120, 139
DR election, 110
group range configuration, 121
group range configuration restrictions, 121
model implementation, 110
neighbor discovery, 110
PIM configuration, 100
PIM protocol relationships, 111
protocols and standards, 111
SPT building, 110
policy
IGMP multicast group policy, 85
IGMP snooping group policy+simulated joining configuration (for VLAN), 35
IGMP snooping multicast group policy, 30
IGMP snooping policy, 29
MLD snooping group policy+simulated joining configuration (for VLAN), 199
MLD snooping IPv6 multicast group policy, 193
MLD snooping policy, 193
MSDP SA message policy, 155
port
IGMP snooping basic configuration, 18
IGMP snooping configuration, 12, 16, 35
IGMP snooping dynamic port aging timer, 21
IGMP snooping dynamic router port change, 24
IGMP snooping fast-leave processing, 23
IGMP snooping group policy+simulated joining configuration (for VLAN), 35
IGMP snooping inner VLAN ID-based forwarding, 24
IGMP snooping multicast group replacement, 32
IGMP snooping multicast groups on port, 32
IGMP snooping multicast source port filtering, 30
IGMP snooping port, 12
IGMP snooping port feature, 21
IGMP snooping simulated member host, 23
IGMP snooping static port, 22
IGMP snooping static port configuration (for VLAN), 37
MLD snooping basic configuration, 182
MLD snooping configuration, 176, 180, 199
MLD snooping dynamic port aging timers, 185
MLD snooping dynamic router port change, 187
MLD snooping fast-leave processing enable, 187
MLD snooping group policy+simulated joining configuration (for VLAN), 199
MLD snooping host tracking, 196
MLD snooping inner VLAN ID-based forwarding, 188
MLD snooping IPv6 multicast group policy, 193
MLD snooping IPv6 multicast group replacement, 196
MLD snooping IPv6 multicast groups on port, 195
MLD snooping IPv6 multicast source port filtering, 194
MLD snooping IPv6 multicast source port filtering (interface view), 194
MLD snooping IPv6 multicast unknown data drop, 195
MLD snooping policy, 193
MLD snooping port feature configuration, 185
MLD snooping port types, 176
MLD snooping simulated member host port, 186
MLD snooping static port configuration, 186
MLD snooping static port configuration (for VLAN), 201
PIM snooping configuration, 45, 46
PIM snooping configuration (for VLAN), 47
port-based multicast VLAN user port assignment, 55
port-based multicast VLAN user port attribute, 55
port-based multicast VLAN
configuration, 55, 57, 60
implementation, 53
user port assignment, 55
user port assignment restrictions, 55
user port attribute, 55
procedure
assigning port-based multicast VLAN user port, 55
changing multicast routing RPF route, 72
configuring IGMP, 84
configuring IGMP basic configuration, 92
configuring IGMP basics, 84
configuring IGMP multicast group policy, 85
configuring IGMP multicast load splitting (IGMP proxy), 90
configuring IGMP NSR, 91
configuring IGMP performance adjustment, 86
configuring IGMP proxying, 89, 97
configuring IGMP query/response parameter (global), 87
configuring IGMP query/response parameter (interface), 88
configuring IGMP snooping (for VLAN), 16
configuring IGMP snooping (for VSI), 17
configuring IGMP snooping basic features, 18
configuring IGMP snooping fast-leave processing configuration, 23
configuring IGMP snooping general query/response parameters, 26
configuring IGMP snooping general query/response parameters (global), 26
configuring IGMP snooping group policy+simulated joining (for VLAN), 35
configuring IGMP snooping message parameters, 27
configuring IGMP snooping message source IP address, 27
configuring IGMP snooping multicast group policy, 30
configuring IGMP snooping multicast group policy (port), 30
configuring IGMP snooping multicast source port filtering (IGMP-snooping view), 30
configuring IGMP snooping multicast source port filtering (interface view), 31
configuring IGMP snooping policy, 29
configuring IGMP snooping port feature, 21
configuring IGMP snooping proxying (for VLAN), 42
configuring IGMP snooping querier, 25
configuring IGMP snooping querier (for VLAN), 39
configuring IGMP snooping query/response parameters (VLAN, VSI), 26
configuring IGMP snooping simulated member host, 23
configuring IGMP snooping static port, 22
configuring IGMP snooping static port (for VLAN), 37
configuring IGMP SSM mapping, 89
configuring IGMP SSM mapping configuration, 94
configuring IGMP static group member, 85
configuring IPv6 static multicast MAC address entry, 183
configuring MLD snooping, 180
configuring MLD snooping (for VLAN), 181
configuring MLD snooping (for VSI), 181
configuring MLD snooping basic features, 182
configuring MLD snooping general query/response parameters, 189
configuring MLD snooping general query/response parameters (global), 190
configuring MLD snooping general query/response parameters (VLAN), 190
configuring MLD snooping general query/response parameters (VSI), 190
configuring MLD snooping group policy, 193
configuring MLD snooping group policy+simulated joining (for VLAN), 199
configuring MLD snooping IPv6 multicast group policy (global), 194
configuring MLD snooping IPv6 multicast group policy (port), 194
configuring MLD snooping IPv6 multicast source port filtering (interface view), 194
configuring MLD snooping IPv6 multicast source port filtering (MLD-snooping view), 194
configuring MLD snooping message parameters, 190
configuring MLD snooping policy, 193
configuring MLD snooping port features, 185
configuring MLD snooping proxying (for VLAN), 205
configuring MLD snooping querier, 188
configuring MLD snooping querier (for VLAN), 203
configuring MLD snooping report suppression, 195
configuring MLD snooping simulated member host port, 186
configuring MLD snooping static port (for VLAN), 201
configuring MLD snooping static ports, 186
configuring MSDP, 150
configuring MSDP Anycast RP, 166
configuring MSDP basics, 150
configuring MSDP inter-AS multicast (static RPF peers)(on switch), 162
configuring MSDP mesh group, 152
configuring MSDP peer description, 152
configuring MSDP peering connection, 151
configuring MSDP PIM-SM inter-domain multicast, 157
configuring MSDP RPF static peer, 151
configuring MSDP SA message cache, 156
configuring MSDP SA message filtering, 170
configuring MSDP SA message originating RP, 154
configuring MSDP SA message policy, 155
configuring MSDP SA message-related parameters, 153
configuring MSDP SA request message, 154
configuring multicast forwarding boundary, 70
configuring multicast group policy (global), 30
configuring multicast routing load splitting, 70
configuring multicast routing+forwarding, 68, 69
configuring multicast static route, 69
configuring multicast VLAN, 54
configuring PIM common features, 121
configuring PIM common timer globally, 125
configuring PIM common timer on interface, 125
configuring PIM common timers, 124
configuring PIM domain border, 118
configuring PIM hello message option globally, 123
configuring PIM hello message option on interface, 124
configuring PIM hello message options, 123
configuring PIM hello policy, 122
configuring PIM message DSCP value, 127
configuring PIM multicast source policy, 122
configuring PIM snooping, 46
configuring PIM snooping (for VLAN), 47
configuring PIM-DM, 112, 128
configuring PIM-DM graft retry timer, 113
configuring PIM-DM state-refresh parameter, 113
configuring PIM-SM, 114
configuring PIM-SM admin-scoped zone, 134
configuring PIM-SM Anycast RP, 116
configuring PIM-SM BSR, 117
configuring PIM-SM C-BSR, 117
configuring PIM-SM C-RP, 115
configuring PIM-SM multicast source registration, 119
configuring PIM-SM non-scoped zone, 131
configuring PIM-SM RP, 115
configuring PIM-SM static RP, 115
configuring PIM-SSM, 120, 139
configuring PIM-SSM group range, 121
configuring port-based multicast VLAN, 55, 60
configuring port-based multicast VLAN user port attribute, 55
configuring source IP address for IGMP message (VLAN), 27
configuring source IP address for IGMP message (VSI), 28
configuring source IP address for MLD message (VLAN), 191
configuring source IP address for MLD message (VSI), 192
configuring static IPv6 multicast MAC address entry (system view), 183
configuring static multicast MAC address entry, 20
configuring static multicast MAC address entry (interface view), 20, 184
configuring static multicast MAC address entry (system view), 20
configuring sub-VLAN-based multicast VLAN, 54, 57
controlling MSDP peering connection, 152
creating multicast routing RPF route, 74
disabling IGMP snooping dynamic router port change, 24
disabling MLD snooping dynamic router port change, 187
disabling PIM-SM BSM forwarding, 119
disabling PIM-SM BSM semantic fragmentation, 118
displaying IGMP, 91
displaying IGMP snooping, 33
displaying MLD snooping, 197
displaying MSDP, 156
displaying multicast routing+forwarding, 71
displaying multicast VLAN, 56
displaying PIM, 127
displaying PIM snooping, 47
enabling fast-leave processing (global), 23
enabling fast-leave processing (port), 24
enabling IGMP, 84
enabling IGMP fast-leave processing, 88
enabling IGMP forwarding (non-querier interface), 90
enabling IGMP proxying, 89
enabling IGMP snooping, 18
enabling IGMP snooping (IGMP-snooping view), 18
enabling IGMP snooping (VLAN view), 18
enabling IGMP snooping (VSI view), 18
enabling IGMP snooping host tracking (global), 33
enabling IGMP snooping host tracking (VLAN), 33
enabling IGMP snooping inner VLAN ID-based forwarding, 24
enabling IGMP snooping proxying, 26
enabling IGMP snooping querier, 25
enabling IGMP snooping report suppression, 31
enabling IP multicast routing, 68
enabling MLD snooping, 182
enabling MLD snooping (MLD-snooping view), 182
enabling MLD snooping (VLAN view), 182
enabling MLD snooping (VSI view), 182
enabling MLD snooping fast-leave processing (global), 187
enabling MLD snooping fast-leave processing (port), 187
enabling MLD snooping host tracking (global), 197
enabling MLD snooping host tracking (VLAN), 197
enabling MLD snooping inner VLAN ID-based forwarding, 188
enabling MLD snooping IPv6 multicast group replacement (global), 196
enabling MLD snooping IPv6 multicast group replacement (port), 196
enabling MLD snooping IPv6 multicast source port filtering, 194
enabling MLD snooping proxying, 190
enabling MLD snooping querier, 189
enabling MSDP, 150
enabling MSDP NSR, 156
enabling MSDP SA message multicast data encapsulation, 153
enabling multicast group replacement (global), 32
enabling multicast group replacement (port), 32
enabling PIM BFD, 126
enabling PIM NSR, 127
enabling PIM passive mode, 126
enabling PIM SNMP notification, 127
enabling PIM-DM, 112
enabling PIM-DM state-refresh, 113
enabling PIM-SM, 114
enabling PIM-SM Auto-RP listening, 116
maintaining IGMP, 91
maintaining IGMP snooping, 33
maintaining MLD snooping, 197
maintaining MSDP, 156
maintaining multicast routing+forwarding, 71
maintaining multicast VLAN, 56
maintaining PIM snooping, 47
setting IGMP last member query interval (global), 21
setting IGMP last member query interval (VLAN), 21
setting IGMP last member query interval (VSI), 21
setting IGMP snooping dynamic port aging timer (global), 22
setting IGMP snooping dynamic port aging timer (VLAN, VSI), 22
setting IGMP snooping forwarding entries, 19
setting IGMP snooping last member query interval, 20
setting IGMP snooping message 802.1 priority (global), 29
setting IGMP snooping message 802.1p priority (VLAN), 29
setting IGMP snooping multicast groups on port, 32
setting MLD last listener query interval (global), 184
setting MLD last listener query interval (VLAN), 184
setting MLD last listener query interval (VSI), 184
setting MLD snooping 802.1p message priority, 193
setting MLD snooping 802.1p message priority (global), 193
setting MLD snooping 802.1p message priority (VLAN), 193
setting MLD snooping dynamic port aging timers, 185
setting MLD snooping dynamic port aging timers (global), 185
setting MLD snooping dynamic port aging timers (VLAN), 185
setting MLD snooping dynamic port aging timers (VSI), 185
setting MLD snooping forwarding entries, 183
setting MLD snooping IPv6 multicast groups on port, 195
setting MLD snooping last member query interval, 184
setting multicast hardware resource mode, 70
setting multicast VLAN forwarding entries max, 56
setting PIM join/prune message size, 125
specifying IGMP snooping version, 19, 19
specifying IGMP snooping version (IGMP-snooping view), 19
specifying IGMP snooping version (VLAN view), 19
specifying IGMP snooping version (VSI view), 19
specifying IGMP version, 85
specifying MSDP peer, 151
specifying multicast routing longest prefix match principle, 69
troubleshoot multicast static route failure, 76
troubleshooting IGMP inconsistent membership information, 98
troubleshooting IGMP no membership information on router, 98
troubleshooting IGMP snooping Layer 2 forwarding, 44
troubleshooting IGMP snooping multicast group filter, 44
troubleshooting MLD snooping group policy, 208
troubleshooting MLD snooping Layer 2 forwarding, 207
troubleshooting MSDP peer stays in disabled state, 174
troubleshooting MSDP RP entry exchange, 175
troubleshooting MSDP SA message cache, 174
troubleshooting PIM abnormal multicast data termination, 142
troubleshooting PIM multicast distribution tree, 142
troubleshooting PIM RP cannot join SPT, 143
troubleshooting PIM snooping does not work, 51
troubleshooting PIM-SM multicast source registration failure, 143
Protocol Independent Multicast. Use PIM
protocols and standards
IGMP, 83
IGMP snooping, 16
IP multicast, 9
Layer 2 multicast, 10
Layer 3 multicast, 9
MLD snooping, 180
MSDP, 149
PIM, 111
PIM protocol relationships, 111
proxying
IGMP, 82
IGMP multicast load splitting (IGMP proxy), 90
IGMP proxying, 89
IGMP proxying configuration, 97
IGMP snooping proxying, 15, 26
IGMP snooping proxying configuration (for VLAN), 42
MLD snooping proxying, 179, 190
MLD snooping proxying configuration (for VLAN), 205
pruning
PIM hello message LAN_Prune_Delay option, 123
PIM join/prune message size, 125
PIM-DM SPT building, 100
Q
querier
IGMP snooping querier, 25, 25
IGMP snooping querier configuration (for VLAN), 39
IGMPv2 querier election, 79
MLD snooping querier configuration, 188
MLD snooping querier configuration (for VLAN), 203
MLD snooping querier enable, 189
querying
IGMP query/response parameters, 86
IGMP snooping general query, 14
IGMP snooping general query/response parameters, 26
IGMP snooping querier, 25, 25
IGMP snooping querier configuration (for VLAN), 39
IGMPv2 querier election, 79
IGMPv3 query capability, 80
MLD snooping general query, 178
MLD snooping general query/response parameters, 189
MLD snooping message parameters, 190
MLD snooping querier configuration, 188
MLD snooping querier configuration (for VLAN), 203
MLD snooping querier enable, 189
R
refreshing
PIM-DM state-refresh, 113
PIM-DM state-refresh parameters, 113
registering
PIM-SM multicast source registration, 119
remote source
MSDP NSR enable, 156
rendezvous point tree. Use RPT
reporting
IGMP snooping membership, 14
IGMP snooping report suppression, 31
IGMPv3 report capability), 80
MLD snooping membership report, 178
MLD snooping report suppression, 195
restrictions
IGMP last member query interval configuration, 21
IGMP multicast forwarding enable, 90
IGMP query/response parameter configuration, 86
IGMP snooping fast-leave processing enable, 23
IGMP snooping multicast group policy configuration, 30
IGMP snooping multicast group replacement, 32
IGMP snooping multicast groups on port, 32
IGMP snooping querier enable, 25
IGMP static group member configuration, 85
MLD snooping fast-leave processing enable, 187
MLD snooping IPv6 multicast group configuration on port, 195
MLD snooping IPv6 multicast group policy configuration, 193
MLD snooping IPv6 multicast group replacement, 196
MLD snooping last listener query interval enable, 184
MLD snooping querier enable, 189
PIM passive mode enable, 126
PIM-SSM group range configuration, 121
port-based multicast VLAN user port assignment, 55
sub-VLAN-based multicast VLAN configuration, 54
reverse path forwarding. Use RPF
route
multicast routing RPF route change, 72
multicast routing RPF route creation, 74
router
IGMP snooping router port, 13
MLD snooping router port, 177
routing
IGMP basic configuration, 84, 92
IGMP configuration, 78, 84, 92
IGMP fast-leave processing, 88
IGMP NSR, 91
IGMP performance adjustment, 86
IGMP proxying, 82, 89
IGMP proxying configuration, 97
IGMP query/response parameters, 86
IGMP snooping basic configuration, 18
IGMP snooping configuration, 12, 16, 35
IGMP snooping dynamic router port change, 24
IGMP snooping forwarding entries, 19
IGMP snooping general query/response parameters, 26
IGMP snooping group policy+simulated joining configuration (for VLAN), 35
IGMP snooping last member query interval, 20
IGMP snooping message 802.1p priority, 29
IGMP snooping message parameters, 27
IGMP snooping message source IP address, 27
IGMP snooping multicast group policy, 30
IGMP snooping multicast source port filtering, 30
IGMP snooping policy, 29
IGMP snooping port feature, 21
IGMP snooping proxying, 15, 26
IGMP snooping proxying configuration (for VLAN), 42
IGMP snooping querier configuration (for VLAN), 39
IGMP snooping simulated member host, 23
IGMP snooping static port, 22
IGMP snooping static port configuration (for VLAN), 37
IGMP snooping version, 19
IGMP SSM mapping, 81, 89
IGMP SSM mapping configuration, 94
IGMP version specification, 85
IP multicast address, 5
IP multicast overview, 1
IP multicast packet forwarding, 11
IP multicast transmission techniques, 1
MLD MP snooping proxying, 190
MLD snooping 802.1p message priority, 193
MLD snooping basic configuration, 182
MLD snooping configuration, 176, 180, 199
MLD snooping dynamic router port change, 187
MLD snooping forwarding entries, 183
MLD snooping general query/response parameters, 189
MLD snooping group policy+simulated joining configuration (for VLAN), 199
MLD snooping last member query interval, 184
MLD snooping message parameters, 190
MLD snooping message source IPv6 address, 191
MLD snooping port feature configuration, 185
MLD snooping proxying, 179
MLD snooping proxying configuration (for VLAN), 205
MLD snooping querier configuration (for VLAN), 203
MLD snooping simulated member host port, 186
MLD snooping static port configuration (for VLAN), 201
MSDP Anycast RP, 147
MSDP Anycast RP configuration, 166
MSDP basics configuration, 150
MSDP configuration, 144, 150, 157
MSDP inter-AS multicast configuration (static RPF peers)(on switch), 162
MSDP inter-domain multicast delivery, 145
MSDP mesh group, 152
MSDP NSR enable, 156
MSDP peer, 144, 151
MSDP peer description, 152
MSDP peering connection, 151
MSDP peering connection control, 152
MSDP peer-RPF forwarding, 148
MSDP PIM-SM inter-domain multicast configuration, 157
MSDP RPF static peer, 151
MSDP SA message filtering configuration, 170
MSDP SA message-related parameters, 153
multicast routing, 64, See also multicast routing+forwarding
PIM common features, 121
PIM common timers, 124
PIM configuration, 100, 128
PIM domain border, 118
PIM hello message options, 123
PIM hello policy, 122
PIM join/prune message size, 125
PIM multicast source policy, 122
PIM NSR enable, 127
PIM snooping configuration, 45, 46
PIM snooping configuration (for VLAN), 47
PIM VPN support, 111
PIM-DM, 100
PIM-DM assert, 101
PIM-DM configuration, 112, 128
PIM-DM graft, 101
PIM-DM neighbor discovery, 100
PIM-DM SPT building, 100
PIM-SM, 102
PIM-SM administrative scoping, 108
PIM-SM administrative zones, 108
PIM-SM admin-scoped zone configuration, 134
PIM-SM Anycast RP, 104, 116
PIM-SM Auto-RP listening, 116
PIM-SM BSM forwarding disable, 119
PIM-SM BSM semantic fragmentation, 118
PIM-SM BSR configuration, 117
PIM-SM C-BSR, 117
PIM-SM configuration, 114
PIM-SM C-RP, 115
PIM-SM DR election, 102
PIM-SM multicast source registration, 106, 119
PIM-SM neighbor discovery, 102
PIM-SM non-scoped zone configuration, 131
PIM-SM RP configuration, 115
PIM-SM RP discovery, 103
PIM-SM RPT building, 106
PIM-SM SPT switchover, 107
PIM-SM static RP, 115
PIM-SM zone relationships, 108
PIM-SSM, 110
PIM-SSM configuration, 120, 139
PIM-SSM DR election, 110
PIM-SSM group range, 121
PIM-SSM neighbor discovery, 110
PIM-SSM SPT building, 110
routing table
multicast RPF check mechanism, 64
RP
MSDP Anycast RP, 147
MSDP Anycast RP configuration, 166
MSDP peer-RPF forwarding, 148
MSDP RPF static peer, 151
MSDP SA message originating RP, 154
PIM-SM Anycast RP, 104, 116
PIM-SM Auto-RP listening, 116
PIM-SM configuration, 115
PIM-SM C-RP, 115
PIM-SM discovery, 103
PIM-SM RPT building, 106
PIM-SM static RP, 115
troubleshooting PIM-SM RP cannot be built, 143
troubleshooting PIM-SM RP cannot join SPT, 143
longest prefix match principle, 69
MSDP inter-AS multicast configuration (static RPF peers)(on switch), 162
MSDP peer-RPF forwarding, 148
multicast check mechanism, 64
multicast check process, 64
multicast routing RPF route change, 72
multicast routing RPF route creation, 74
multicast RPF check implementation, 65
multicast RPF route change, 66
multicast RPF route creation, 66
multicast static route, 66
multicast static route configuration, 69
IP multicast notation, 4
PIM-SM multicast source registration, 106
PIM-SM RPT building, 106
rule
MSDP SA message policy, 155
S
SA
MSDP peer-RPF forwarding, 148
MSDP SA message cache, 156
MSDP SA message filtering configuration, 170
MSDP SA message multicast data encapsulation, 153
MSDP SA message originating RP, 154
MSDP SA message policy, 155
MSDP SA message-related parameters, 153
MSDP SA request message, 154
semantic fragmentation
PIM-SM BSM, 118
setting
IGMP last member query interval, 20
IGMP last member query interval (global), 21
IGMP last member query interval (VLAN), 21
IGMP last member query interval (VSI), 21
IGMP snooping dynamic port aging timer (global), 22
IGMP snooping dynamic port aging timer (VLAN, VSI), 22
IGMP snooping forwarding entries, 19
IGMP snooping message 802.1p priority (global), 29
IGMP snooping message 802.1p priority (VLAN), 29
IGMP snooping multicast groups on port, 32
MLD last listener query interval (global), 184
MLD last listener query interval (VLAN), 184
MLD last listener query interval (VSI), 184
MLD snooping 802.1p message priority, 193
MLD snooping 802.1p message priority (global), 193
MLD snooping 802.1p message priority (VLAN), 193
MLD snooping dynamic port aging timers, 185
MLD snooping dynamic port aging timers (global), 185
MLD snooping dynamic port aging timers (VLAN), 185
MLD snooping dynamic port aging timers (VSI), 185
MLD snooping forwarding entries, 183
MLD snooping IPv6 multicast groups on port, 195
MLD snooping last listener query interval, 184
multicast routing+forwarding hardware resource mode, 70
multicast VLAN forwarding entries max, 56
PIM join/prune message size, 125
SFM
IP multicast model, 5
shortest path tree. Use SPT
simulated member host, 23
SNMP
PIM SNMP notification enable, 127
snooping
IGMP snooping configuration, 12
IGMP snooping host tracking, 33
MLD snooping, 176
PIM snooping configuration, 45, 46
PIM snooping configuration (for VLAN), 47
source registration
PIM-SM, 106
PIM-SM multicast, 119
troubleshooting PIM-SM multicast source registration failure, 143
specifying
IGMP snooping version, 19, 19
IGMP snooping version (IGMP-snooping view), 19
IGMP snooping version (VLAN view), 19
IGMP snooping version (VSI view), 19
IGMP version, 85
MSDP peer, 151
IP multicast notation, 4
PIM-DM SPT building, 100
PIM-SM multicast source registration, 106
PIM-SM switchover, 107
PIM-SSM SPT building, 110
troubleshooting PIM-SM RP cannot join SPT, 143
SSM
IGMP SSM mapping, 89
IGMP SSM mapping configuration, 94
IP multicast model, 5
state
PIM-DM state-refresh, 113
PIM-DM state-refresh parameters, 113
static
IGMP snooping static member port, 13
IGMP snooping static port, 22
IGMP snooping static port configuration (for VLAN), 37
IGMP snooping static router port, 13
IGMP static group member configuration, 85, 85
IPv6 static multicast MAC address entry, 183
MLD snooping static member port, 177
MLD snooping static port configuration, 186
MLD snooping static router port, 177
MSDP RPF static peer, 151
multicast static route configuration, 69
multicast static RPF route, 66
PIM-SM static RP, 115
static multicast MAC address entry, 20
subnetting
multicast forwarding across unicast subnets, 67
sub-VLAN-based multicast VLAN
configuration, 54, 57, 57
configuration restrictions, 54
implementation, 52
suppressing
IGMP snooping report suppression, 31
MLD snooping report suppression, 195
switching
IP multicast overview, 1
IP multicast transmission techniques, 1
MSDP inter-AS multicast configuration (static RPF peers)(on switch), 162
MSDP PIM-SM inter-domain multicast configuration, 157
multicast forwarding across unicast subnets, 67
multicast routing RPF route change, 72
multicast routing RPF route creation, 74
multicast routing+forwarding configuration, 64, 68, 72
switchover
PIM-SM SPT switchover, 107
T
table
multicast routing+forwarding configuration, 64, 68, 72
TCP/IP
IGMP basic configuration, 84, 92
IGMP configuration, 78, 84, 92
IGMP proxying configuration, 97
IGMP SSM mapping configuration, 94
MSDP peering connection control, 152
timer
IGMP snooping dynamic member port aging timer, 13
IGMP snooping dynamic port aging timer, 21
IGMP snooping dynamic router port aging timer, 13
MLD snooping dynamic port aging timers, 185
PIM common, 124
PIM-DM graft retry, 113
topology
multicast RPF route change, 66
multicast RPF route creation, 66
tracking
IGMP snooping host tracking, 33
traffic
multicast routing load splitting, 70
transmitting
IP multicast, 2
IP multicast broadcast, 2
IP multicast overview, 1
IP multicast transmission techniques, 1
IP multicast unicast, 1
trapping
PIM SNMP notification enable, 127
troubleshooting
IGMP, 98
IGMP inconsistent membership information, 98
IGMP no membership information on router, 98
IGMP snooping, 44
IGMP snooping Layer 2 multicast forwarding, 44
IGMP snooping multicast group filter, 44
MLD snooping, 207
MLD snooping IPv6 multicast group policy, 208
MLD snooping Layer 2 forwarding, 207
MSDP, 173
MSDP peers stay in disabled state, 174
MSDP RP entry exchange, 175
MSDP SA message cache, 174
multicast routing+forwarding, 76
multicast static route failure, 76
PIM, 142
PIM abnormal multicast data termination, 142
PIM multicast distribution tree, 142
PIM snooping, 51
PIM snooping does not work, 51
PIM-SM multicast source registration failure, 143
PIM-SM RP cannot be built, 143
PIM-SM RP cannot join SPT, 143
tunneling
multicast forwarding across unicast subnets, 67
U
unicast
IP multicast transmission technique, 1
multicast forwarding across unicast subnets, 67
multicast routing+forwarding configuration, 69
V
verifying
multicast RPF check mechanism, 64
multicast RPF check process, 64
version
IGMP snooping specification, 19
IGMP specification, 85
IGMPv1, 78, 78, 78
IGMPv1 snooping, 19
IGMPv2, 78, 79
IGMPv2 snooping, 19
IGMPv3, 78, 80
IGMPv3 snooping, 19
VLAN
IGMP snooping basic configuration, 18
IGMP snooping configuration, 12, 16, 16, 35
IGMP snooping dynamic port aging timer, 21
IGMP snooping enable, 18
IGMP snooping fast-leave processing, 23
IGMP snooping general query/response parameters, 26
IGMP snooping inner VLAN ID-based forwarding, 24
IGMP snooping message 802.1p priority, 29
IGMP snooping message parameters, 27
IGMP snooping message source IP address, 27
IGMP snooping multicast group replacement, 32
IGMP snooping multicast groups on port, 32
IGMP snooping policy, 29, 29
IGMP snooping port feature, 21
IGMP snooping querier, 25
IGMP snooping querier enable, 25
IGMP snooping simulated member host, 23
IGMP snooping static port, 22
IGMP snooping unknown multicast data drop, 31
IGMP snooping version, 19
MLD snooping 802.1p message priority, 193
MLD snooping basic configuration, 182
MLD snooping configuration, 180, 181, 199
MLD snooping dynamic port aging timers, 185
MLD snooping dynamic port aging timers setting, 185
MLD snooping enable, 182
MLD snooping fast-leave processing enable, 187
MLD snooping general query/response parameter configuration (VLAN), 190
MLD snooping general query/response parameters, 189
MLD snooping host tracking, 196
MLD snooping inner VLAN ID-based forwarding, 188
MLD snooping message parameters, 190
MLD snooping message source IPv6 address, 191
MLD snooping policy, 193, 193
MLD snooping port feature configuration, 185
MLD snooping querier enable, 189
MLD snooping static port configuration, 186
multicast VLAN configuration, 52, 54, 57
PIM configuration, 100, 128
PIM snooping configuration, 47
PIM-DM configuration, 128
PIM-SM admin-scoped zone configuration, 134
PIM-SM non-scoped zone configuration, 131
PIM-SSM configuration, 139
port-based multicast VLAN configuration, 60
sub-VLAN-based multicast VLAN configuration, 57
VPN
IGMP support, 83
MSDP support, 149
PIM support, 111
VSI
IGMP snooping basic configuration, 18
IGMP snooping configuration, 16, 17
IGMP snooping enable, 18
IGMP snooping general query/response parameters, 26
IGMP snooping message 802.1p priority, 29
IGMP snooping message parameters, 27
IGMP snooping message source IP address, 27
IGMP snooping policy, 29
IGMP snooping port feature, 21
IGMP snooping querier enable, 25
IGMP snooping unknown multicast data drop, 31
IGMP snooping version, 19
MLD snooping 802.1p message priority, 193
MLD snooping basic configuration, 182
MLD snooping configuration, 180, 181
MLD snooping dynamic port aging timers set, 185
MLD snooping enable, 182
MLD snooping general query/response parameters, 189
MLD snooping message parameters, 190
MLD snooping message source IPv6 address, 191
MLD snooping policy, 193
MLD snooping port feature configuration, 185
MLD snooping querier enable, 189
MLD snooping query/response parameter configuration (VSI), 190
Z
PIM-SM administrative scoping, 108
zone
border router. See ZBR
PIM-SM admin-scoped zone configuration, 134
PIM-SM admin-scoped/global-scoped zone relationship, 108
PIM-SM non-scoped zone configuration, 131