Security Announcement-Statement on Apache Unomi remote code execution vulnerability CVE-2020-13942
25-02-2021Overview
The background of security vulnerability
Apache Unomi is a java open source customer data platform used to manage customer and visitor data online and provide a personalized experience that complies with visitor privacy rules. Unomi was announced as the top project of Apache in 2019, with a high degree of scalability and ease of use. Recently, the H3C Offensive and Defense Laboratory monitored the foreign security research team to disclose the detailed technical analysis of Apache Unomi remote code execution vulnerabilities, The vulnerability number is CVE-2020-13942, with a CVSS score of 10.0 (high risk and extremely easy to exploit).
The principle of the vulnerability
Unomi relies on expression languages such as OGNL or MVEL, allowing users to write complex and detailed query statements. Before version 1.5.1, these expression languages are completely unrestricted, making Unomi vulnerable to expression injection attacks. Attackers can execute arbitrary codes and system commands by sending malicious requests to the Unomi server. The vulnerability is classified as CVE-2020-11975.
In version 1.5.1 of Aache Unomi, the SecureFilteringClassLoader function was introduced to fix the vulnerability CVE-2020-11975, and the classes used in expressions were filtered by a blacklist. However, in some cases, the MVEL expression can directly use the instantiated class, thus bypassing the restrictions of SecureFilteringClassLoader. A remote attacker can execute arbitrary code or system commands by sending malicious requests to the Unomi server by bypassing the blacklist type of patch detection
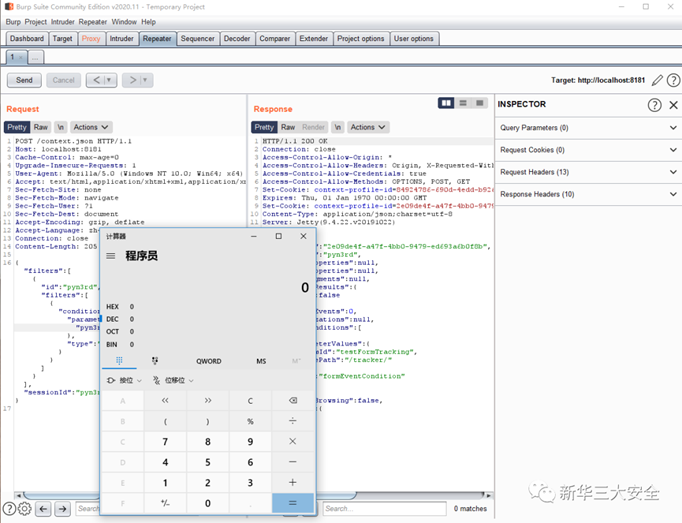
The reproduce of security vulnerability
At present, the POC for the exploit of this vulnerability has been made public. Affected users please update the version in time. The screenshot of the successful exploit is as follows:
The scope of influence
Affected version: ApacheUnomi < = 1.5.1
Solution
The official patch
The latest version of the official release has fixed this vulnerability, affected users are requested to upgrade the Apache Unomi version.
Download link: http://unomi.apache.org/download.html
The solution of H3C
The H3C IPS rule base will support the interception of this vulnerability in version 1.0.111. It is recommended to pay attention to the H3C official website to update the version in time and enable relevant rules.
H3C security emergency response external service
H3C advocates that every effort be made to safeguard the ultimate interests of product users, to abide by principles of responsible disclosure of security incidents, and to handle product security issues in accordance with security issues mechanisms. For information on H3C's security emergency response service and H3C product vulnerabilities, please visit https://www.h3c.com/en/Support/Online_Help/psirt/.

