Security Announcement-Statement on XStream Arbitrary File Deletion Server Request Fabrication CVE-2020-26259 CVE-2020-26258
25-02-2021Overview
Vulnerability background
XStream is a simple, easy-to-use Java class library designed to serialize and deserialize Java objects and XML. It supports all types, such as base types, arrays, and collections. When serializing JavaBeans or deserializing XML files, no additional helper classes and mapping files are required, making XML serialization easier. XStream can also serialize JavaBeans to JSON or deserialize them, making it very easy to use. Recently, New H3C offensive and defense laboratory monitoring XStream official updated two vulnerability risk notice (CVE-2020-26258, CVE-2020-26259), and repeat and analysis.
The principle of the vulnerability
There is a deserialization vulnerability in XStream that allows new instances to be created based on the type information used to recreate previously written objects in the data stream being deserialized. An unauthorized remote attacker can cause arbitrary file deletion or server-side request forgery by replacing the processed input stream or injecting objects into it.At present, the exploit code of the vulnerability has been made public, and the affected users are advised to take relevant protective measures as soon as possible to prevent losses.
The reproduce of security vulnerability
Set up the vulnerability environment (XStream 1.4.13) and successfully reproduce the two vulnerabilities.
XStream Arbitrary File Deletion Vulnerability (CVE-2020-26259) : Construct special serialized data and successfully delete files existing in the server.
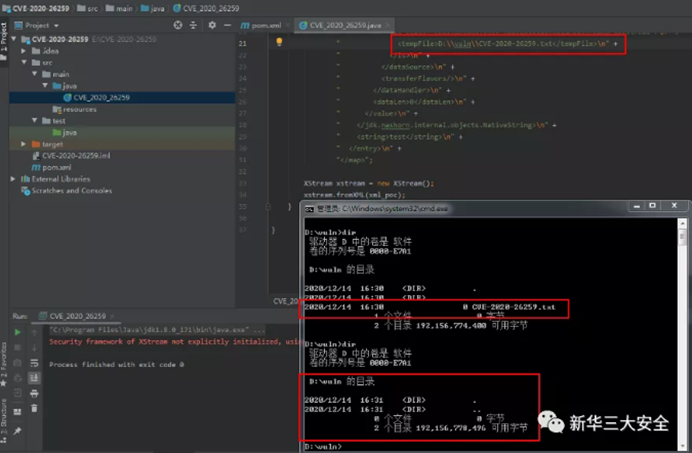
XStream Server Request Fabrication Vulnerability (CVE-2020-26258) : Construct special serialized data that can be used to send requests as a server to other hosts in the server's internal network environment.


The scope of influence
Affected version: XStream <= 1.4.14
Severity level: High Risk
Solution
The official patch
XStream has been officially fixed in the new version, please upgrade to XStream 1.4.15 and above, download link:https://x-stream.github.io/changes.html#1.4.15
Temporary Repair Plan
1. Users who use the default XStream blacklist in version 1.4.14 of XStream can add the following two lines of code to the XStream setup code:
xstream.denyTypes(new String[]{ "jdk.nashorn.internal.objects.NativeString" });
xstream.denyTypesByRegExp(new String[]{ ".*\\.ReadAllStream\\$FileStream" });
2. Users who want to use the default XStream blacklist in XStream 1.4.13 can add the following three lines of code to the XStream setup code:
xstream.denyTypes(new String[]{ "javax.imageio.ImageIO$ContainsFilter","jdk.nashorn.internal.objects.NativeString" });
xstream.denyTypes(new Class[]{ java.lang.ProcessBuilder.class });
xstream.denyTypesByRegExp(new String[]{ ".*\\.ReadAllStream\\$FileStream" });
3. If you want to use the XStream blacklist in versions 1.4.7-1.4.12, you need to set multiple blacklists:
xstream.denyTypes(new String[]{ "javax.imageio.ImageIO$ContainsFilter","jdk.nashorn.internal.
objects.NativeString" });
xstream.denyTypes(new Class[]{ java.lang.ProcessBuilder.class, java.beans.EventHandler.class, java.lang.ProcessBuilder.class, java.lang.Void.class, void.class });
xstream.denyTypesByRegExp(new String[]{ ".*\\$LazyIterator", "javax\\.crypto\\..*", ".*\\.
ReadAllStream\\$FileStream" });
4. Users of XStream 1.4.6 or lower can register their Converter to avoid deserializing currently known key Java types.
xstream.registerConverter(new Converter() {
public boolean canConvert(Class type) {
|type.getName().equals("javax.imageio.ImageIO$ContainsFilter")|type.getName().equals("jdk.nashorn.internal.objects.NativeString")| |
|type == java.lang.Void.class|void.class|Proxy.isProxy(type)|
|type.getName().startsWith("javax.crypto.")|type.getName().endsWith("$LazyIterator")|type.getName().endsWith(".ReadAllStream$FileStream"));|
}
public Object unmarshal(HierarchicalStreamReader reader, UnmarshallingContext context) {
throw new ConversionException("Unsupported type due to security reasons.");
}
public void marshal(Object source, HierarchicalStreamWriter writer, MarshallingContext context) {
throw new ConversionException("Unsupported type due to security reasons.");
}
}, XStream.PRIORITY_LOW);
The solution of H3C
1. H3C safety equipment protection scheme
The IPS rule base of H3C will support the identification of this vulnerability in version 1.0.115. The whole security products of H3C can identify the attack traffic of this vulnerability by upgrading the IPS feature library and take the initiative to intercept it.
2. Situational awareness solutions
The situational awareness solution of H3C has supported the detection of this vulnerability. Through comprehensive research and judgment methods such as information collection and integration, data association analysis, etc., the assets attacked and lost by this vulnerability in the network are found.
3. Solution of H3C Cloud Security Capability Center
The knowledge base of H3C Cloud Security Capability Center has been updated with the vulnerability information, and the corresponding vulnerability generation principle, upgrade patch and repair measures can be inquired.
Reference linking
1. http://x-stream.github.io/CVE-2020-26258.html
2. http://x-stream.github.io/CVE-2020-26259.html
H3C security emergency response external service
H3C advocates that every effort be made to safeguard the ultimate interests of product users, to abide by principles of responsible disclosure of security incidents, and to handle product security issues in accordance with security issues mechanisms. For information on H3C's security emergency response service and H3C product vulnerabilities, please visit https://www.h3c.com/en/Support/Online_Help/psirt/.

