Security Announcement -Statement on Zabbix remote code execution vulnerability CVE-2020-11800
25-02-2021Vulnerability overview
The Background of security vulnerabilities
Zabbix is an enterprise-level open source solution based on WEB interface that provides distributed system monitoring and network monitoring functions. Zabbix can monitor various network parameters, ensure the safe operation of the server system, and provide a flexible notification mechanism to allow system administrators to quickly locate and solve various problems. Zabbix is composed of Zabbix server and optional component Zabbix agent. Zabbix server can provide remote server/network status monitoring, data collection and other functions through SNMP, Zabbix agent, ping, port monitoring and other methods. It can run on Linux, Solaris, HP-UX, AIX, Free BSD, Open BSD, On platforms such as OS X.
On October 9, 2020, Zabbix officially announced the CVE-2020-11800 security bulletin. The bulletin stated that there are remote code execution vulnerabilities in Zabbix proxy 3.0-3.0.31 version and Zabbix server 3.0-3.0.31 version.
On January 11, 2021, the threat early warning team of the New H3C Offensive and Defense Laboratory monitored the disclosure of the details of the CVE-2020-11800 remote code execution vulnerability on the Internet. The risk of this vulnerability being exploited by hackers has greatly increased.
The principle of the vulnerability
The vulnerability is caused by the incomplete repair of the CVE-2017-2824 Zabbix remote code execution vulnerability. If the administrator turns on the automatic registration function in Zabbix Server, anyone can actively register the host to the Server for monitoring. Since the IP parameters are not verified, the commands can be spliced after the IP. After Zabbix Server receives the command to add the host, the attacker can execute splicing in the IP by requesting the built-in monitoring command of the host ID of the added host. After the order. Zabbix's official method of repairing CVE-2017-2824 is to verify the IP, but the repair is not perfect. As a result, CVE-2020-11800 can be used to bypass IPv6 and inject arbitrary commands.
The reproduce of security vulnerability
Use docker to build the Zabbix environment and enable the automatic registration function on the server. Send a maliciously added host request to the server, and then request the monitoring command that comes with the host id. You can see that the command is executed successfully and the success file is successfully created.
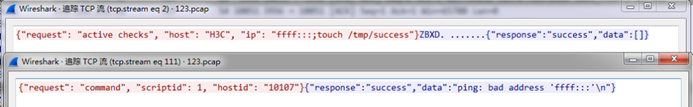
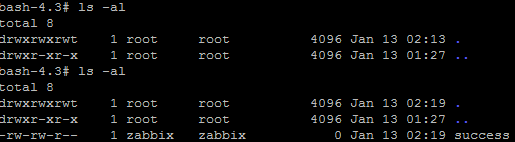
The scope of influence
Zabbix 2.2.18-2.2.23
Zabbix 3.0 – 3.0.30
Zabbix 3.2-3.2.11
Solution
The official patch
The latest version of the official release has fixed this vulnerability, affected users are requested to upgrade the Zabbix version. download link:
https://support.zabbix.com/browse/ZBX-17600
The solution of H3C
1. New H3C safety equipment protection plan
The H3C IPS rule database will support the identification of this vulnerability in version 1.0.117. All of H3C’s security products can identify the attack traffic of this vulnerability by upgrading the IPS signature database and actively intercept it.
2. New H3C Situational Awareness Solution
New H3C Situational Awareness has supported the detection of this vulnerability. Through comprehensive research and judgment methods such as information collection and integration, data association analysis, etc., it has discovered the assets that have been attacked by the vulnerability and lost in the network.
3. New H3C Cloud Security Competence Center Solution
The knowledge base of New H3C Cloud Security Competence Center has updated the vulnerability information, and can query the generation principle of the corresponding vulnerability, upgrade patches, and repair measures.
H3C security emergency response external service
H3C advocates that every effort be made to safeguard the ultimate interests of product users, to abide by principles of responsible disclosure of security incidents, and to handle product security issues in accordance with security issues mechanisms. For information on H3C's security emergency response service and H3C product vulnerabilities, please visit https://www.h3c.com/en/Support/Online_Help/psirt/.

