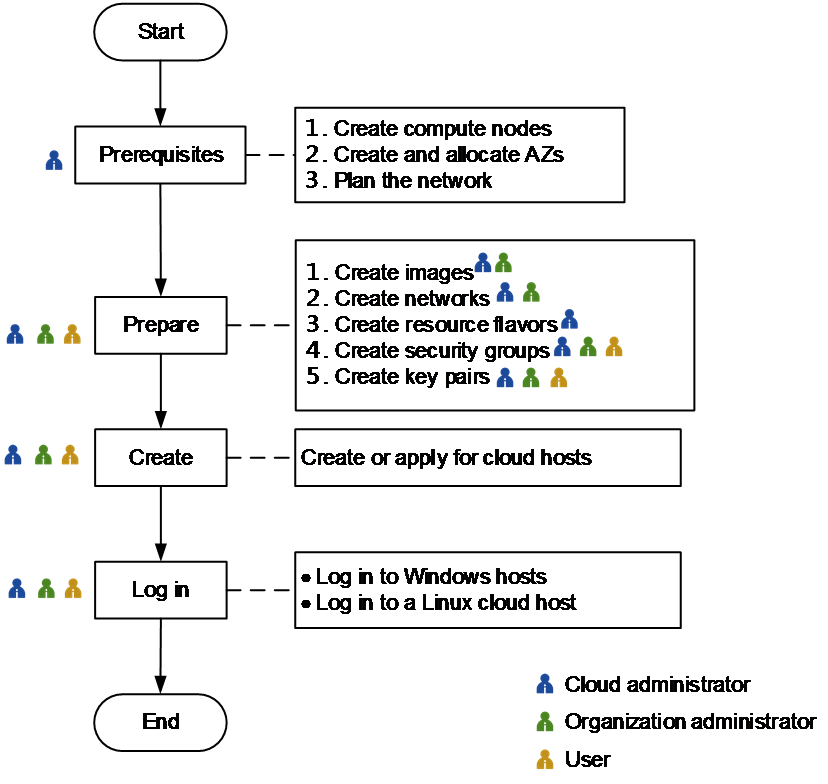
Cloud host creation workflow
Figure-1 shows the workflow of creating a cloud host.
Figure-1 cloud host creation workflow
Table-1 Cloud host creation workflow
|
Step |
Description |
|
|
Prerequisites |
Create compute nodes |
For a cloud host to collaborate with virtualization platforms, you must create compute nodes. For resource isolation, you must create AZs. Plan the network and set the egress VLAN range for compute nodes. For more information about how to configure compute nodes, see the quick start for cloud administrators in Service Guide. |
|
Create and allocate AZs |
||
|
Plan the network |
||
|
Preparation |
Required. An image is the operating system of cloud hosts. You must provide an image when creating a cloud host. Images include public and private images. A public image can be created by a cloud administrator and is available to all users. A private image can be created by an organization administrator or cloud administrator. A private image created by an organization administrator is available only to users in the organization, and a private image created by a cloud administrator is available only to the cloud administrator. If the expected image does not exist in the system, a user can upload the expected image in the image service or convert a snapshot to an image. |
|
|
Required. You must assign an IP address in the network to a cloud host when creating the cloud host. If the network to which the cloud host belongs does not exist, you must create the network. For more information about networks, see networks in Network and Security. |
||
|
Optional. You must select cloud host flavors for a cloud host when creating the cloud host. The system provides common resource flavors by default. If you specify custom flavors for the cloud host, you need to create cloud host flavors. |
||
|
Optional. A security group provides security protections for cloud hosts by using access control rules to filter incoming and outgoing traffic for the cloud hosts. By default, the system applies security group default to the vNIC of a cloud host. All incoming and outgoing traffic for the cloud host is permitted. You can first create a security group and access control rules in the group, and then apply the security group to the cloud host when creating the cloud host. |
||
|
Optional. The system supports the following authentication policies for cloud host login: Auto Generated Password, Manually Specified Password, Key, and Image Default Password. To use the Key authentication policy when creating a cloud host, you must first create a key pair. |
||
|
Creation |
To create a cloud host, you need to set parameters of the cloud host. |
|
|
Login |
You can log in to a Windows cloud host through the console or MSTSC. |
|
|
You can log in to a Linux cloud host through an SSH tool by using the SSH password or key or through the control. |
|
For information about cloud services used in preparation, see the cloud services in Service Guide. |