

![]() Chapters Download(192.45 KB)
Chapters Download(192.45 KB)
| Title | Size | Download |
|---|---|---|
| 01-ARP Configuration | 192.45 KB |
Table of Contents
1.2.1 Enabling/Disabling ARP Entry Checking
1.2.2 Adding/Deleting a Static ARP Entry
1.2.3 Configuring the Dynamic ARP Aging Timer
1.2.4 Adding/Deleting Multicast ARP Ports
1.2.6 Gratuitous ARP Learning Configuration
1.2.7 Configuring ARP Packets Not to Broadcast in VLAN
1.3 Displaying and Debugging ARP
Chapter 2 ARP Table Size Configuration
2.1 Introduction to ARP Table Size Configuration
2.2 Configuring ARP Table Size Dynamically
2.2.2 Configuring ARP Table Size Dynamically
2.3 Displaying ARP Table Size Configuration
2.4 ARP Table Size Configuration Example
Chapter 3 ARP Attack Prevention Configuration
3.1 ARP Spoofing Attack Prevention
3.1.1 Introduction to ARP Spoofing Attack Prevention
3.1.2 Configuring ARP Spoofing Attack Prevention
3.2 ARP Duplicate Gateway Attack Prevention
3.2.1 Introduction to ARP Duplicate Gateway Attack Prevention
3.2.2 Configuring ARP Duplicate Gateway Attack Prevention
3.3 ARP Packet Attack Prevention
3.3.1 Introduction to ARP Packet Attack Prevention
3.3.2 Configuring ARP Packet Attack Prevention
3.4 ARP Attack Prevention Configuration Example
Chapter 4 IP Packet Attack Prevention Configuration
4.1 Introduction to IP Packet Attack Prevention
4.2 Configuring IP Packet Attack Prevention
When configuring ARP, go to these sections for information you are interested in:
l Displaying and Debugging ARP
Address resolution protocol (ARP) is used to resolve an IP address into a MAC address.
An IP address cannot be directly used for communication on an Ethernet because network devices can identify only MAC addresses. An IP address is a network layer address. To send datagrams through the network layer to the destination host, the MAC address of the host is required. Therefore, the IP address must be resolved into a MAC address.
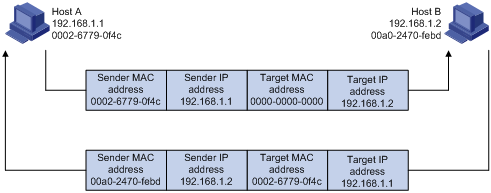
Figure 1-1 ARP address resolution process
Suppose that Host A and Host B are on the same subnet and Host A sends a packet to Host B. The resolution process is as follows:
1) Host A checks its ARP table to see whether there is an ARP entry for Host B. If yes, Host A uses the MAC address in the entry to encapsulate the IP packet into a data link layer frame and sends the frame to Host B.
2) If Host A finds no entry for Host B, Host A buffers the packet and broadcasts an ARP request, in which the sender IP address and sender MAC address are respectively the IP address and MAC address of Host A and the target IP address and target MAC address are respectively the IP address of Host B and an all-zero MAC address. Because the ARP request is broadcast, all hosts on this subnet can receive the request, but only the requested host (namely, Host B) will process the request.
3) Host B compares its own IP address with the target IP address in the ARP request. If they are the same, Host B saves the sender IP address and sender MAC address into its ARP table, encapsulates its MAC address into an ARP reply, and unicasts the reply to Host A.
4) After receiving the ARP reply, Host A adds the MAC address of Host B into its ARP table.
If Host A and Host B are not on the same subnet, Host A first sends an ARP request to the gateway. The target IP address in the ARP request is the IP address of the gateway. After obtaining the MAC address of the gateway from an ARP reply, Host A sends the packet to the gateway. If the gateway maintains the ARP entry of Host B, it forwards the packet to Host B directly; if not, it broadcasts an ARP request, in which the target IP address is the IP address of Host B. After obtaining the MAC address of Host B, the gateway sends the packet to Host B.
ARP entries used in S9500 series routing switches include dynamic ARP entries and static ARP entries.
l Dynamic ARP entries are automatically created and maintained by the ARP protocol through ARP packets. They can be discarded after the aging time expires, and updated by new ARP packets. They can also be overwritten by permanent static ARP entries and non-permanent static ARP entries. When the aging time expires, a port is disabled or a VLAN interface is disabled, the corresponding dynamic ARP entry will be deleted.
l Static ARP entries are configured and maintained manually.
Static entries are further divided into permanent static ARP entries and non-permanent static ARP entries.
l Permanent ARP entries contain all elements of an ARP entry. They can forward data directly. They cannot be aged, or overwritten by dynamic ARP entries.
l Non-permanent ARP entries are configured with only IP addresses and MAC addresses other than VLANs and output interfaces. They are generally used for users requiring IP-MAC bindings. Its initial state is non-resolution, so it cannot forward data directly. It can obtain VLANs and egresses dynamically through ARP packets. A resolved non-permanent static ARP entry can forward data and will not be aged. When a port or VLAN interface is disabled, the corresponding static ARP entry will be restored to the non-resolution state.
The ARP table can be maintained dynamically or manually. Usually, the manually configured mappings are known as static ARP entries. The user can display, add or delete such entries with commands.
The following sections describe static ARP configuration tasks:
l Enabling/Disabling ARP Entry Checking
l Adding/Deleting a Static ARP Entry
l Configuring the Dynamic ARP Aging Timer
l Adding/Deleting Multicast ARP Ports
l Gratuitous ARP Learning Configuration
l Configuring ARP Packets Not to Broadcast in VLAN
Perform the following configuration in system view to enable/disable ARP entry checking:
|
To do… |
Use the command… |
|
Enable the ARP entry checking function so that the switch will not learn any ARP entry containing a multicast MAC address |
arp check enable |
|
Disable the ARP entry checking function so that the switch can learn ARP entries containing multicast MAC addresses |
undo arp check enable |
By default, the ARP entry checking function is enabled, that is, the switch is disabled from learning ARP entries for multicast MAC addresses.
Perform the following configuration in system view to add/delete a static ARP mapping entry.
|
To do… |
Use the command… |
|
Add a static ARP entry |
arp static ip-address [ mac-address [ vlan-id { interface-type interface-number } ] [ vpn-instance vpn-instance-name ] ] |
|
Delete a static ARP entry |
undo arp ip-address |
By default, the ARP table is empty and ARP entries are obtained through dynamic ARP.
Note that:
l As long as a switch operates, its static ARP entries remain valid unless you change or remove a VLAN interface, remove a VLAN, or remove a port from a VLAN. These operations cause the corresponding static ARP mapping entries to be automatically removed.
l The vlan-id argument must be the ID of an existing VLAN, and the Ethernet port specified behind this argument must belong to the VLAN.
l The vpn-instance-name argument must be the VPN instance name of an existing MPLS VPN.
l The port specified in an ARP entry can be a manually aggregated port, instead of a statically or dynamically aggregated port.
l If the mac-address of an ARP entry is a multicast MAC address, the system will take this ARP entry as a multicast ARP entry.
l Automatic fill-in of MAC addresses is enabled only after IP address protection is enabled on the interface.
l After the first automatic fill-in, the corresponding ARP entries become common static ARP entries and cannot be filled in again.
You can configure an age for dynamic ARP entries.
Perform the following configuration in system view to configure the dynamic ARP aging timer.
|
To do… |
Use the command… |
|
Configure the dynamic ARP aging timer |
arp timer aging aging-time |
|
Restore the default dynamic ARP aging time |
undo arp timer aging |
By default, the dynamic ARP aging timer is 20 minutes.
The multicast ARP feature allows you to associate a common unicast route to a Layer 2 multicast group by creating a static multicast ARP entry. In this way, a packet matching the entry can be forwarded out multiple ports. In brief, a multicast ARP entry is a static ARP entry with a multicast MAC address and corresponds to multiple ports.
You can use the multi-port keyword in the following command to add a port for a multicast ARP entry. Only one port can be added every time the command is executed. If the multicast ARP entry does not exist, a new multicast ARP entry is generated. If the multicast ARP entry exists and the same port exists, the switch will not add the port.
Follow these steps to add a port for a multicast ARP entry in system view:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Add a port for the multicast ARP entry |
arp static ip-address mac-address vlan-id multi-port interface-type interface-number [ vpn-instance vpn-instance-name ] |
— |
To remove the configuration, use the corresponding undo command.
After the configuration, you can use the display arp multi-port command in any view to check the detailed information about multicast ARP entry configuration.
![]() Caution:
Caution:
l Up to 64 multicast ARP entries are supported, with each entry having up to 100 outgoing ports. A manual port aggregation group is considered a single port.
l An outgoing port of a multicast ARP entry can be a manually aggregated port or a common port, but cannot be a statically or dynamically aggregated port.
l As specified in the IEEE 802.3ad standard, if a port is disabled but the dynamic port aggregation function is enabled, the port is not an aggregated port, but a common one. Therefore, the port can be configured as a port for a multicast ARP entry. After the port is enabled, the port becomes a dynamically aggregated port and will be removed from the multicast ARP entry.
l The IP addresses of multicast ARP entries are unicast IP addresses.
l For the MAC addresses of multicast ARP entries, well-known multicast MAC addresses are not recommended.
l Multicast static ARP entries overwrite dynamic, non-permanent static and permanent static ARP entries with the same IP addresses, but not vice versa.
l If a port with a number smaller than those in an aggregation group (for example, the port is on an interface card with a smaller slot number) is added into the group, the ports in this aggregation group will be removed from multicast ARP; while other ports will not be affected.
l For an aggregation of ports on different interface cards, if removing an interface card with a smaller slot number can cause primary port switchover, doing so will remove the ports of this aggregation group from multicast ARP; while other ports will not be affected.
l If an aggregation group is removed, ports in this group are removed from multicast ARP; while other ports are not affected.
l No matter the state of the primary port in an aggregation is up or down, ports in the aggregation group will not be removed from multicast ARP.
With the super VLAN function enabled, a device also needs to be enabled with the proxy ARP function for Layer 3 communications between sub-VLANs. If you enable the proxy ARP function on a device that is connected to two sub-VLANs, the device forwards packets between the sub-VLANs at Layer 3. In this way, ports isolated at Layer 2 can communicate at Layer 3.
Follow these steps to enable proxy ARP in VLAN view:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enter VLAN view |
vlan vlan-id |
Use the vlan-id argument to specify the ID of a sub-VLAN. |
|
Enable ARP proxy |
arp proxy enable |
By default, proxy ARP is disabled. |
Use the undo form of the command to remove the configuration.
With proxy ARP enabled in VLAN interface view, upon receiving an ARP request, a device sends back an ARP response directly if the following conditions are met:
l The sender IP address of the ARP request is on the same network segment as the receiving VLAN interface.
l The target IP address of the ARP request is on another network segment.
l The route corresponding to the target IP address of the ARP request exists and the outgoing interface of the route is not the receiving interface of the ARP request.
Follow these steps to enable proxy ARP in VLAN interface view:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enter VLAN interface view |
vlan-interface vlan-id |
Use the vlan-id argument to specify the ID of a common VLAN. |
|
Enable proxy ARP |
arp proxy enable |
By default, proxy ARP is disabled. |
With local proxy ARP enabled, the device directly sends back an ARP response if it receives an ARP request whose sender and target IP addresses are on the same network segment as the receiving VLAN interface.
Follow these steps to enable local proxy ARP:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enter VLAN interface view |
vlan-interface vlan-id |
Use the vlan-id argument to specify the ID of a common VLAN. |
|
Enable local proxy ARP |
arp local-proxy enable |
By default, local proxy ARP is disabled. |
The following are the characteristics of gratuitous ARP packets:
l Both source and destination IP addresses carried in a gratuitous ARP packet are the local IP address, and the source MAC address carried in it is the local MAC address.
l If a device finds that the IP address carried in a received gratuitous packet is its IP address, it returns an ARP response to the sending device.
By sending a gratuitous ARP packet, a network device can:
l Check whether its IP address conflicts with that of any other device;
l Trigger other network devices to update its hardware address stored in their caches.
With the gratuitous ARP packet learning function enabled, a network device stores the source IP and MAC addresses of a received gratuitous ARP packet in its ARP table if it has no such an entry or updates the entry if it has.
Follow these steps to configure the gratuitous ARP packet learning function:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enable the gratuitous ARP packet learning function |
gratuitous-arp-learning enable |
Required By default, the gratuitous ARP packet learning function is enabled. |
In order to disable any two hosts in the same network segment from access to each other, you can configure the device to forward ARP requests as trap packets to the CPU rather than broadcast in the VLAN. Thus, the two hosts cannot learn the addresses of each other through ARP packets.
Follow these steps to limit the flooding of ARP request packets in a VLAN:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enter Ethernet port view |
interface interface-type interface-number |
The port specified by the interface-type argument can be an Ethernet port only |
|
Limit the flooding of ARP requests in a VLAN |
arp non-flooding enable |
Required This function is disabled by default. |
|
To do… |
Use the command… |
Remarks |
|
Display ARP entry information |
display arp [ ip-address | [ dynamic | static | vlan vlan-id | interface interface-type interface-number ] [ | { begin | include | exclude } text ] ] |
Available in any view |
|
Display the current setting of the dynamic ARP aging timer |
display arp timer aging |
|
|
Display multicast ARP entry configuration information |
display arp multi-port [ ip-address ] |
|
|
Display proxy ARP information |
display arp proxy [ vlan vlan-id] |
|
|
Clear specified ARP entries |
reset arp [ dynamic | static | interface { interface-type interface-number } | all ] |
Available in user view |
|
Enable ARP debugging |
debugging arp { error | info | packet | entry-check } |
|
|
Disable ARP debugging |
undo debugging arp { error | info | packet | entry-check } |
When configuring the ARP table size, go to these sections for information you are interested in:
l Introduction to ARP Table Size Configuration
l Configuring ARP Table Size Dynamically
l Displaying ARP Table Size Configuration
l ARP Table Size Configuration Example
You can manually configure the maximum number of ARP entries (that is, the size of a ARP table) on an S9500 routing switch as needed.
Table 2-1 lists the specifications and numbers of ARP entries on cards with different model suffixes.
Table 2-1 Specifications and numbers of ARP entries on cards with different model suffixes
|
Model suffix |
IP address format and number of FIB entries supported |
MPLS support |
Maximum number of ARP entries supported by the whole switch if the card exists in the system |
Maximum number of ARP entries supported by the card |
Maximum number of aggregation ARP entries supported by the card |
|
B |
IPv4-128K |
Not supported |
4K |
4K |
0K, 1K, 3K |
|
DA |
IPv4-128K/IPv6-7K |
||||
|
DB |
IPv4-128K/IPv6-64K |
||||
|
DC |
IPv4-256K/IPv6-128K |
||||
|
C |
IPv4-128K |
Supported |
4K, 64K |
4K, 5K, 6K, 7K, 8K |
0K, 1K, 3K, 7K, 8K |
|
CA |
IPv4-256K |
||||
|
CB |
IPv4-512K |
& Note:
l You can distinguish the model suffix of a card by the silkscreen at the upper right corner of the front panel. For example, the silkscreen of the LSB1GP12B0 card is GP12B, and so the suffix of this card is B.
l If the suffix of a card is "C" or "CA", you can configure the maximum ARP entries as 64 K only when only this type of cards exist in the system. Up to 8K of ARP entries can be configured for a card.
![]() Caution:
Caution:
l After the configuration of a non-permanent static ARP entry, the system will include it into the number of non-aggregation ARP entries. If the non-permanent static ARP entry is resolved from a non-aggregated port, the number of non-aggregation ARP entries will remain unchanged; if the non-permanent static ARP entry is resolved from an aggregated port, it will be deducted from the number of non-aggregation ARP entries and included into the number of aggregation ARP entries.
l As a non-permanent static ARP entry is included into the number of normal ARP entries like a normal permanent static ARP entry, if a card is configured to support up to 8K aggregation ARP entries, the card does not support the configuration of neither kind.
l Configuring the maximum number of ARP entries supported by a card
l Configuring the maximum number of aggregation ARP entries supported by a card
l Configuring the maximum number of ARP entries supported by the switch
Follow these steps to configure ARP table size dynamically:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Configure the maximum number of ARP entries supported by a card |
arp max-entry slot-num max-num |
The maximum number of ARP entries supported by a card is 4K by default. |
|
Configure the maximum number of aggregation ARP entries supported by a card |
arp max-aggregation-entry max-aggnum |
The maximum number of aggregation ARP entries supported by a card is 1K by default. |
|
Configure the maximum number of ARP entries supported by the switch |
arp enable size { 4 | 64 } |
The maximum number of ARP entries supported by the whole switch is 4K by default. |
To remove the configurations, use the corresponding undo commands.
![]() Caution:
Caution:
l Restart the system to make the above configurations effective.
l After the above configurations, do not change cards or slots before you restart the system. Otherwise, the configurations may fail to take effect.
l After the above configurations, do not perform active/standby switchover before you restart the system. Otherwise, the configurations will not take effect even if you restart the system.
|
To do… |
Use the command… |
Remarks |
|
Display the maximum numbers of current ARP entries and entries that will take effect after the switch restarts |
display arp max-entry |
Available in any view |
A host is connected to an S9500 series routing switch. The model names of all the cards in the switch system are suffixed with C, CA, or CB.
Figure 2-1 Diagram for ARP table size configuration
# Configure the maximum number of ARP entries supported by the whole switch as 64K.
<H3C> system-view
System View: return to User View with Ctrl+Z.
[H3C] arp enable size 64
The configuration won't be enabled until the system is rebooted
# Configure the maximum number of ARP entries supported by the interface card in slot 2 as 8K.
[H3C] arp max-entry 2 8
The configuration won't be enabled until the system is rebooted
# Configure the maximum number of aggregation ARP entries supported by each interface card in the system as 8K.
[H3C] arp max-aggregation-entry 8
The configuration won't be enabled until the system is rebooted
Restart the system for the configurations to take effect.
When configuring ARP attack prevention, go to these sections for information you are interested in:
l ARP Spoofing Attack Prevention
l ARP Duplicate Gateway Attack Prevention
l ARP Packet Attack Prevention
l ARP Attack Prevention Configuration Example
There are diversified ARP attacks. We here only discuss the following three ARP attacks:
l ARP Spoofing Attack Prevention
l ARP Duplicate Gateway Attack Prevention
l ARP Packet Attack Prevention
ARP provides no security mechanism, and a network using ARP is thus susceptible to attacks.
l If devices in the network are configured with static IP addresses, you can prevent illegal modification of ARP entries only by configuring static ARP entries. Such configuration is complex and difficult to maintain.
l If devices in the network obtain IP addresses dynamically, attackers may send ARP packets using forged source addresses, causing the gateway to modify the ARP entries and thus disconnecting legal users.
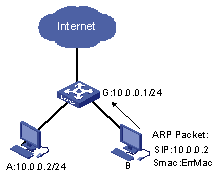
Figure 3-1 ARP spoofing attack
As shown in Figure 3-1, A is a legal user connected to the Internet through the switch G. By forging the ARP packets from A, the attacker B changes the ARP entry of A on G, thereby disconnecting A from G.
To prevent ARP source address spoofing attacks, the S9500 series switches provide the following methods.
For a dynamic ARP entry already learned by the switch, the corresponding MAC address cannot be modified by learning a new MAC address through ARP. A new MAC address can be learned for this ARP entry only after this ARP entry ages out, ensuring that the ARP entries for legal users are not modified. This method can be divided into two modes: fixed-mac and fixed-all.
l In the fixed-mac mode, MAC addresses cannot be modified, but VLANs and ports can be modified. This mode applies to the condition where user addresses are assigned statically but redundant Layer 2 links exist. When link switching occurs, the ports in the ARP entry can be changed immediately.
l In the fixed-all mode, none of the dynamic, resolved non-permanent static ARP entries, MAC addresses, VLANs, or ports can be modified. This mode only applies to the condition where IP addresses are assigned statically, no redundant links exist, and a user with a fixed IP address will not access the switch through different ports.
Upon receiving an ARP packet with a modified MAC address, the switch sends a unicast acknowledgement to the corresponding user associated with the original ARP entry, instead of modifying the ARP entry directly.
l If a response is received from the original user within the specified period, the original user is still connected. In this case, no MAC address modification can be made for this ARP entry in the coming one minute (likewise, no MAC address modification is allowed within one minute after a new ARP entry is created).
l If no response is received from the original user within the specified period, a unicast request is sent to the new user. After a response is received, the ARP entry can be modified so that the new user becomes a legal user.
This mode applies to the condition where IP addresses are assigned dynamically but redundant links exist.
Follow these steps to configure ARP spoofing attack prevention:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Configure ARP spoofing attack prevention |
arp entry-check { fixed-mac | fixed-all | send-ack } |
Required Disabled by default. |
|
Display the ARP spoofing attack prevention configuration |
display arp entry-check |
Available in any view |
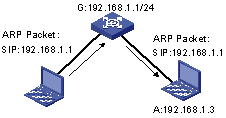
Figure 3-2 ARP duplicate gateway attack
An attacker sends gratuitous ARP packets with the source IP address being the gateway within the LAN. The internal hosts will then change the address of the gateway to that of the attacker. As a result, the hosts are unable to access the network. Such an attack is called an ARP duplicate gateway attack.
To prevent such attacks, S9500 series switches provide the duplicate gateway attack prevention function. If any of the following conditions occurs, the system generates an ARP attack prevention entry:
l The source IP address of the ARP packet is the same as the IP address of the receiving interface.
l The source IP address of the ARP packet belongs to the NAT address pool or is the same as one of the internal servers’ IP address.
l The source IP address of the ARP packet is the virtual IP address of the receiving interface, but the source MAC address of the ARP packet is not the virtual MAC address of the VRRP group.
Based on this entry, the switch discards those packets with the same source MAC address within a certain period, thus preventing the ARP packets containing the duplicate gateway address from being broadcasted within the VLAN.
![]() Caution:
Caution:
l The ARP duplicate gateway attack prevention function can detect and prevent VLAN interface address conflicts, VRRP virtual address conflicts, and NAT address pool conflicts.
l After detecting an address conflict on the console port, the switch only logs the event, without preventing the attack.
l If the VRRP group has a real MAC address, the switch logs the event after detecting an address conflict, without preventing the attack.
Follow these steps to configure ARP duplicate gateway attack prevention:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Configure ARP duplicate gateway attack prevention |
anti-attack gateway-duplicate{ enable | disable } |
Required Disabled by default. |
|
Display information about the ARP duplicate gateway attack prevention configuration of a specific slot |
display anti-attack gateway-duplicate slot slotid |
Available in any view |
ARP provides no authentication mechanism, and a network using ARP is thus susceptible to various kinds of attacks. Sending a large amount of ARP packets with a fixed MAC address is just one kind of attacks, which affects ARP entry learning of the switch.
S9500 series switches can detect and prevent such ARP packet attacks. If the number of ARP packets with a fixed source MAC address received by the switch CPU reaches the set threshold within a certain period, the user with this MAC address is considered an attacker. Then, the system generates an attack prevention entry to filter this user, who will then be unable to access the network.
Follow these steps to configure ARP packet attack prevention:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Configure ARP packet attack prevention |
anti-attack arp { enable | monitor | disable } |
Required By default, the ARP packet attack prevention function is in monitor state. |
|
Configure a threshold for ARP packet attack detection |
anti-attack arp threshold threshold-value |
Optional The threshold value ranges from 5 to 300 pps, and defaults to 30 pps. |
|
Configure the aging time for ARP packet attack prevention entries |
anti-attack arp aging-time time |
Optional 600 seconds by default. The aging time for duplicate gateway attack prevention entries is synchronized with that of the ARP packet attack prevention entries. |
|
Specify a protected MAC address for ARP packet attack prevention |
anti-attack arp exclude-mac mac-address |
Optional A protected MAC address will not be filtered out by the ARP attack prevention function. The system supports up to 16 protected MAC addresses. |
|
Display ARP packet attack prevention information |
display anti-attack arp slot slotid |
Available in any view |
& Note:
l If the CPU of an interface card does not receive any packet, the ARP packet attack prevention entries of the interface card will not be aged out.
l If an ARP attack prevention entry is not aged out, the dynamic address entry with the same MAC address will not be aged out either.
l The ARP packet attack prevention function is not supported on the console port.
l An S9500 switch (Switch 1) is connected to two low-end switches Switch 3 and Switch 2 through Ethernet 1/1/1 and Ethernet 1/1/2, respectively.
l PC 1 is attached to Switch 1; PC 2 and PC 3 on the same network segment are attached to Switch 2; PC 4 and PC 5 on another network segment are attached to Switch 3.
l PC 1 sends a large amount of ARP packets. Some have the source IP addresses changing constantly, while some share the same source IP address with the gateway. PC 4 generates a large amount of ARP packets with a fixed MAC address.
l Switch 1 can prevent attacks from PC 1 and PC 4.
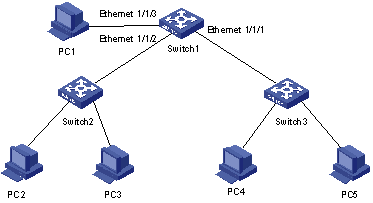
Figure 3-3 Network diagram for ARP packet attack prevention
# Enter system view.
<Switch1> system-view
# Specify the ARP spoofing attack prevention mode to send-ack, preventing ARP spoofing attacks from PC 1.
[Switch1] arp entry-check send-ack
# Enable ARP duplicate gateway attack prevention, preventing duplicate gateway attacks from PC 1.
[Switch1] anti-attack gateway-duplicate enable
# Enable ARP packet attack prevention, preventing ARP packet attacks from PC 4.
[Switch1] anti-attack arp enable
# Configure the threshold for ARP packet attack detection to 40 pps.
[Switch1] anti-attack arp threshold 40
# Configure the aging time for ARP packet attack prevention entries to 300 seconds.
[Switch1] anti-attack arp aging-time 300
# Configure the protective MAC address for ARP packet attack prevention to 0-0-1.
[Switch1] anti-attack arp exclude-mac 0-0-1
After the above configurations, you can use the display current command to view the ARP attack prevention configuration information, and use the display anti-attack command to view the information about duplicate gateway attacks and ARP packet attacks from a fixed MAC address.
Note that:
l The implementation of ARP spoofing attack prevention may result in high CPU usage.
l The duplicate gateway attack prevention only ensures that attacking packets received on a port will not be forwarded to other ports, but the hosts attached to this port may still be attacked.
l With the duplicate gateway attack prevention and ARP packet attack prevention enabled, the switch can not only isolate attackers, but also prevent the attackers from accessing network resources.
When configuring IP packet attack prevention, go to these sections for information you are interested in:
l Introduction to IP Packet Attack Prevention
l Configuring IP Packet Attack Prevention
With the expansion of the Internet and the increase of Internet users, network devices are susceptible to attacks. You can configure the IP packet attack prevention function on S9500 series switches to defend against IP packet attacks or unknown multicast attacks.
l An IP packet attack occurs when an S9500 switch receives excessive IP packets. If the destination IP addresses of the packets and the IP address of a VLAN interface are on the same network segment, these packets will be delivered to the CPU for processing, which may affect normal packet forwarding due to high CPU usage.
l When an S9500 switch receives a large amount of IP packets with the TTL field being 1, a large amount of ICMP time exceeded packets will be generated, thus increasing the burden of CPU.
Follow these steps to configure IP packet attack prevention:
|
To do… |
Use the command… |
Remarks |
|
Enter system view |
system-view |
— |
|
Enable/disable IP packet attack prevention |
anti-attack ip { disable | enable } |
Required Enabled by default. |
|
Configure the switch not to process the packets with the TTL field being 1 |
anti-attack ttl1 enable slot slotid |
By default, the switch processes the packets with the TTL field being 1. |
& Note:
Currently, the anti-attack ttl1 enable slot command is supported only on the cards suffixed with DB or DC.