02-S12500_IP_Source_Guard_Configuration_Examples
Chapters Download (111.78 KB)
| Title | Size | Download |
|---|---|---|
| 02-S12500_IP_Source_Guard_Configuration_Examples | 111.78 KB |
Contents
Example: Configuring static IP source guard binding entries
Configuration restrictions and guidelines
Example: Configuring dynamic IP source guard with DHCP snooping
This document provides IP source guard configuration examples.
IP source guard prevents spoofed attacks by using an IP source guard binding table to match legitimate packets. It drops all packets that do not match the table.
The IP source guard binding table can include the following binding entries:
· IP-interface binding entries.
· MAC-interface binding entries.
· IP-MAC-interface binding entries.
· IP-VLAN-interface binding entries.
· MAC-VLAN-interface binding entries.
· IP-MAC-VLAN-interface binding entries.
The IP source guard configuration examples use IP-MAC-interface binding entries.
The configuration examples in this document were created and verified in a lab environment, and all the devices were started with the factory default configuration. When you are working on a live network, make sure you understand the potential impact of every command on your network.
This document assumes that you have basic knowledge of H3C IP source guard.
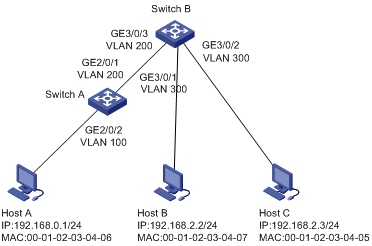
As shown in Figure 1, all hosts use static IP addresses.
Configure static IP source guard binding entries (IP-MAC-interface binding) on Switch A and Switch B to meet the following requirements:
· GE 2/0/2 on Switch A allows only IP packets from Host A to pass through.
· GE 3/0/1 on Switch B allows only IP packets from Host B to pass through.
· GE 3/0/2 on Switch B allows only IP packets from Host C to pass through.
The configuration examples were created and verified on S12500-CMW710-R7129.
By default, Ethernet, VLAN, and aggregate interfaces are shut down. You must use the undo shutdown command to bring them up. This example assumes that all these interfaces are already up.
1. Configure Switch A:
# Configure IP source guard on GigabitEthernet 2/0/2 to filter incoming packets.
<SwitchA> system-view
[SwitchA] interface GigabitEthernet2/0/2
[SwitchA-GigabitEthernet2/0/2] ip verify source ip-address mac-address
# Configure a static binding entry for Host A on GigabitEthernet 2/0/2.
[SwitchA-GigabitEthernet2/0/2] ip source binding ip-address 192.168.0.1 mac-address 0001-0203-0406
2. Configure Switch B:
# Configure IP source guard on GigabitEthernet 3/0/1 to filter incoming packets.
[SwitchB] interface GigabitEthernet3/0/1
[SwitchB-GigabitEthernet3/0/1] ip verify source ip-address mac-address
# Configure a static binding entry for Host B on GigabitEthernet 3/0/1.
[SwitchB] interface GigabitEthernet3/0/1
[SwitchB-GigabitEthernet3/0/1] ip source binding ip-address 192.168.2.2 mac-address 0001-0203-0407
# Configure IP source guard on GigabitEthernet 3/0/2 to filter incoming packets.
<SwitchB> system-view
[SwitchB] interface GigabitEthernet3/0/2
[SwitchB-GigabitEthernet3/0/2] ip verify source ip-address mac-address
# Configure a static binding entry for Host C on GigabitEthernet 3/0/2.
[SwitchB-GigabitEthernet3/0/2] ip source binding ip-address 192.168.2.3 mac-address 0001-0203-0405
[SwitchB-GigabitEthernet3/0/2] quit
# Display static IP source guard binding entries on Switch A.
<SwitchA> display ip source binding static
Total entries found: 1
IP Address MAC Address Interface VLAN Type
192.168.0.1 0001-0203-0406 GE2/0/2 N/A Static
# Display static IP source guard binding entries on Switch B.
<SwitchB> display ip source binding static
Total entries found: 2
IP Address MAC Address Interface VLAN Type
192.168.2.2 0001-0203-0407 GE3/0/1 N/A Static
192.168.2.3 0001-0203-0405 GE3/0/2 N/A Static
· Switch A:
#
interface GigabitEthernet2/0/2
port link-mode bridge
ip source binding ip-address 192.168.0.1 mac-address 0001-0203-0406
ip verify source ip-address mac-address
#
· Switch B:
#
interface GigabitEthernet3/0/1
port link-mode bridge
ip source binding ip-address 192.168.2.2 mac-address 0001-0203-0407
ip verify source ip-address mac-address
#
interface GigabitEthernet3/0/2
port link-mode bridge
ip source binding ip-address 192.168.2.3 mac-address 0001-0203-0405
ip verify source ip-address mac-address
#
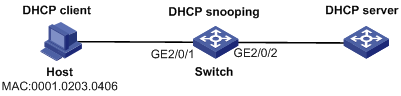
As shown in Figure 2, the DHCP client obtains an IP address through the DHCP server.
Configure IP source guard binding entries (IP-MAC-interface binding) to prevent attackers from using forged IP addresses to attack the server.
To use DHCP snooping entries as dynamic IP source guard entries, you must perform the following tasks:
· Configure the port that connects to the DHCP server as a trusted port.
· Enable DHCP snooping entry recording on the port that connects to the DHCP client.
The configuration examples were created and verified on S12500-CMW710-R7129.
# Enable DHCP snooping.
[Switch] dhcp-snooping enable
# Configure GigabitEthernet 2/0/2 as a trusted interface.
[Switch] interface GigabitEthernet2/0/2
[Switch-GigabitEthernet2/0/2] undo shutdown
[Switch-GigabitEthernet2/0/2] dhcp snooping trust
[Switch-GigabitEthernet2/0/2] quit
# Enable IP source guard on GigabitEthernet 2/0/1 to filter incoming packets.
<Switch> system-view
[Switch] interface GigabitEthernet2/0/1
[Switch-GigabitEthernet2/0/1] undo shutdown
[Switch-GigabitEthernet2/0/1] ip verify source ip-address mac-address
# Enable DHCP snooping entry recording on GigabitEthernet 2/0/1.
[Switch-GigabitEthernet2/0/1] dhcp snooping binding record
# Display IP source guard binding entries obtained from DHCP snooping on GigabitEthernet 2/0/1.
[Switch-GigabitEthernet2/0/1] display ip source binding dhcp-snooping
Total entries found: 1
IP Address MAC Address Interface VLAN Type
192.168.0.1 0001-0203-0406 GE2/0/1 1 DHCP snooping
The output shows that a dynamic IP source guard binding entry was obtained after the IP source guard was enabled.
#
interface GigabitEthernet2/0/1
port link-mode bridge
ip verify source ip-address mac-address
dhcp snooping binding record
#
dhcp snooping enable
#
interface GigabitEthernet2/0/2
port link-mode bridge
dhcp snooping trust
#
· H3C S12500 Routing Switch Series Security Configuration Guide
· H3C S12500 Routing Switch Series Security Command Reference