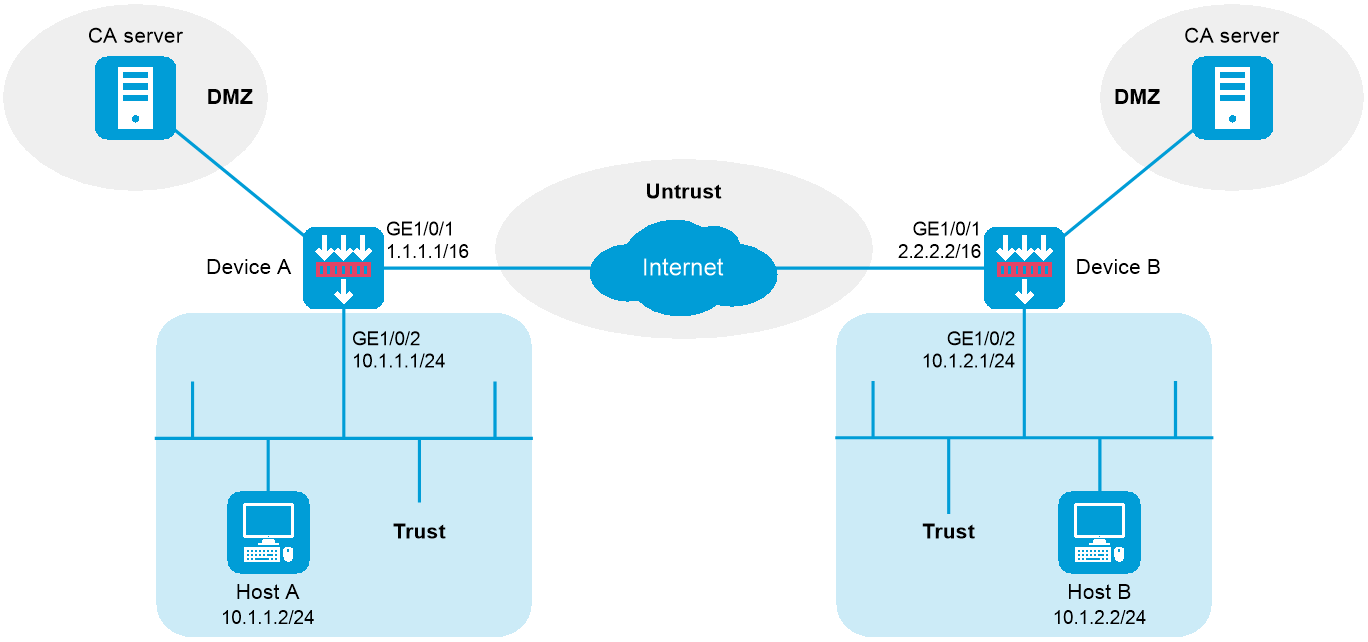
As shown in Figure 1, configure an IKE-based IPsec tunnel between Device A and Device B to secure the communication between subnet 10.1.1.0/24 and subnet 10.1.2.0/24.
Configure Device A and Device B to use aggressive mode for IKE negotiation phase 1 and to use RSA signature authentication. Device A acts as the initiator, and the subnet where Device A resides uses IP addresses dynamically allocated.
This configuration example was created and verified on F9900 of the F5000-AI120 device.
Device A has obtained CA certificate ca.cer and local certificate server.pfx.
Device B has obtained CA certificate ca.cer and local certificate server.pfx.
1. Assign IP addresses to interfaces:
# Assign an IP address to interface GigabitEthernet 1/0/1.
<DeviceA> system-view
[DeviceA] interface gigabitethernet 1/0/1
[DeviceA-GigabitEthernet1/0/1] ip address 1.1.1.1 255.255.0.0
[DeviceA-GigabitEthernet1/0/1] quit
# Assign IP addresses to other interfaces in the same way. (Details not shown.)
2. Configure settings for routing.
This example configures static routes, and the next hop in the routes is 1.1.1.2.
[DeviceA] ip route-static 10.1.2.0 24 1.1.1.2
[DeviceA] ip route-static 2.2.2.2 16 1.1.1.2
3. Add interfaces to security zones.
[DeviceA] security-zone name trust
[DeviceA-security-zone-Trust] import interface gigabitethernet 1/0/2
[DeviceA-security-zone-Trust] quit
[DeviceA] security-zone name untrust
[DeviceA-security-zone-Untrust] import interface gigabitethernet 1/0/1
[DeviceA-security-zone-Untrust] quit
4. Configure a security policy:
Configure rules to permit traffic between the Untrust and Local security zones, so the devices can set up an IPsec tunnel:
# Configure a rule named ipseclocalout to allow Device A to send IPsec negotiation packets to Device B.
[DeviceA] security-policy ip
[DeviceA-security-policy-ip] rule name ipseclocalout
[DeviceA-security-policy-ip-1-ipseclocalout] source-zone local
[DeviceA-security-policy-ip-1-ipseclocalout] destination-zone untrust
[DeviceA-security-policy-ip-1-ipseclocalout] source-ip-host 1.1.1.1
[DeviceA-security-policy-ip-1-ipseclocalout] destination-ip-host 2.2.2.2
[DeviceA-security-policy-ip-1-ipseclocalout] action pass
[DeviceA-security-policy-ip-1-ipseclocalout] quit
# Configure a rule named ipseclocalin to allow Device A to receive the IPsec negotiation packets sent from Device B.
[DeviceA-security-policy-ip] rule name ipseclocalin
[DeviceA-security-policy-ip-2-ipseclocalin] source-zone untrust
[DeviceA-security-policy-ip-2-ipseclocalin] destination-zone local
[DeviceA-security-policy-ip-2-ipseclocalin] source-ip-host 2.2.2.2
[DeviceA-security-policy-ip-2-ipseclocalin] destination-ip-host 1.1.1.1
[DeviceA-security-policy-ip-2-ipseclocalin] action pass
[DeviceA-security-policy-ip-2-ipseclocalin] quit
Configure rules to permit the traffic between Host A and Host B:
# Configure a rule named trust-untrust to permit the packets from Host A to Host B.
[DeviceA-security-policy-ip] rule name trust-untrust
[DeviceA-security-policy-ip-3-trust-untrust] source-zone trust
[DeviceA-security-policy-ip-3-trust-untrust] destination-zone untrust
[DeviceA-security-policy-ip-3-trust-untrust] source-ip-subnet 10.1.1.0 24
[DeviceA-security-policy-ip-3-trust-untrust] destination-ip-subnet 10.1.2.0 24
[DeviceA-security-policy-ip-3-trust-untrust] action pass
[DeviceA-security-policy-ip-3-trust-untrust] quit
# Configure a rule named untrust-trust to permit the packets from Host B to Host A.
[DeviceA-security-policy-ip] rule name untrust-trust
[DeviceA-security-policy-ip-4-untrust-trust] source-zone untrust
[DeviceA-security-policy-ip-4-untrust-trust] destination-zone trust
[DeviceA-security-policy-ip-4-untrust-trust] source-ip-subnet 10.1.2.0 24
[DeviceA-security-policy-ip-4-untrust-trust] destination-ip-subnet 10.1.1.0 24
[DeviceA-security-policy-ip-4-untrust-trust] action pass
[DeviceA-security-policy-ip-4-untrust-trust] quit
[DeviceA-security-policy-ip] quit
5. Define the data flows to be protected:
# Configure IPv4 advanced ACL 3101 to identify traffic from subnet 10.1.1.0/24 to subnet 10.1.2.0/24.
[DeviceA] acl advanced 3101
[DeviceA-acl-ipv4-adv-3101] rule permit ip source 10.1.1.0 0.0.0.255 destination 10.1.2.0 0.0.0.255
[DeviceA-acl-ipv4-adv-3101] quit
6. Configure an IPsec transform set to specify the packet encapsulation mode, security protocols, and algorithms.
The IPsec transform set settings at both sides of the IPsec tunnel must be the same.
[DeviceA] ipsec transform-set tran1
[DeviceA-ipsec-transform-set-tran1] encapsulation-mode tunnel
[DeviceA-ipsec-transform-set-tran1] protocol esp
[DeviceA-ipsec-transform-set-tran1] esp encryption-algorithm des-cbc
[DeviceA-ipsec-transform-set-tran1] esp authentication-algorithm sha1
[DeviceA-ipsec-transform-set-tran1] quit
7. Configure a PKI entity.
[DeviceA] pki entity entity1
[DeviceA-pki-entity-entity1] common-name devicea
[DeviceA-pki-entity-entity1] quit
8. Configure a PKI domain for certificate requests.
[DeviceA] pki domain domain1
[DeviceA-pki-domain-domain1] public-key rsa general name rsa1
[DeviceA-pki-domain-domain1] undo crl check enable
[DeviceA-pki-domain-domain1] quit
[DeviceA] pki import domain domain1 der ca filename ca.cer
[DeviceA] pki import domain domain1 p12 local filename server.pfx
9. Configure a certificate-based access control policy to control user access rights.
A peer certificate is regarded valid only if it contains the specified string (1 in this example) in the DN attribute of the subject name field.
[DeviceA] pki certificate access-control-policy policy1
[DeviceA-pki-cert-acp-policy1] rule 1 permit group1
[DeviceA] pki certificate attribute-group group1
[DeviceA-pki-cert-attribute-group-group1] attribute 1 subject-name dn ctn 1
10. Configure an IKE profile to specify the security parameters used for setting up IKE SAs.
[DeviceA] ike profile profile1
[DeviceA-ike-profile-profile1] certificate domain domain1
[DeviceA-ike-profile-profile1] exchange-mode aggressive
[DeviceA-ike-profile-profile1] local-identity dn
[DeviceA-ike-profile-profile1] match remote certificate policy1
[DeviceA-ike-profile-profile1] quit
11. Configure an IKE proposal to specify the parameters used for IKE negotiation.
[DeviceA] ike proposal 10
[DeviceA-ike-proposal-10] authentication-algorithm md5
[DeviceA-ike-proposal-10] authentication-method rsa-signature
[DeviceA-ike-proposal-10] quit
12. Configure an IPsec policy to establish an IPsec tunnel to protect the specified data:
[DeviceA] ipsec policy map1 10 isakmp
[DeviceA-ipsec-policy-isakmp-map1-10] remote-address 2.2.2.2
[DeviceA-ipsec-policy-isakmp-map1-10] transform-set tran1
[DeviceA-ipsec-policy-isakmp-map1-10] security acl 3101
[DeviceA-ipsec-policy-isakmp-map1-10] ike-profile profile1
[DeviceA-ipsec-policy-isakmp-map1-10] quit
13. Apply the IPsec policy to GigabitEthernet 1/0/1 to protect the traffic on the interface.
[DeviceA] interface gigabitethernet 1/0/1
[DeviceA-GigabitEthernet1/0/1] ipsec apply policy map1
[DeviceA-GigabitEthernet1/0/1] quit
1. Assign IP addresses to interfaces:
# Assign an IP address to interface GigabitEthernet 1/0/1.
<DeviceB> system-view
[DeviceB] interface gigabitethernet 1/0/1
[DeviceB-GigabitEthernet1/0/1] ip address 2.2.2.2 255.255.0.0
[DeviceB-GigabitEthernet1/0/1] quit
# Assign IP addresses to other interfaces in the same way. (Details not shown.)
2. Configure settings for routing.
This example configures static routes, and the next hop in the routes is 2.2.2.1.
[DeviceB] ip route-static 10.1.1.0 24 2.2.2.1
[DeviceB] ip route-static 1.1.1.1 16 2.2.2.1
3. Add interfaces to security zones.
[DeviceB] security-zone name trust
[DeviceB-security-zone-Trust] import interface gigabitethernet 1/0/2
[DeviceB-security-zone-Trust] quit
[DeviceB] security-zone name untrust
[DeviceB-security-zone-Untrust] import interface gigabitethernet 1/0/1
[DeviceB-security-zone-Untrust] quit
4. Configure a security policy:
Configure rules to permit traffic between the Untrust and Local security zones, so the devices can set up an IPsec tunnel:
# Configure a rule named ipseclocalout to allow Device B to send IPsec negotiation packets to Device A.
[DeviceB] security-policy ip
[DeviceB-security-policy-ip] rule name ipseclocalout
[DeviceB-security-policy-ip-1-ipseclocalout] source-zone local
[DeviceB-security-policy-ip-1-ipseclocalout] destination-zone untrust
[DeviceB-security-policy-ip-1-ipseclocalout] source-ip-host 2.2.2.2
[DeviceB-security-policy-ip-1-ipseclocalout] destination-ip-host 1.1.1.1
[DeviceB-security-policy-ip-1-ipseclocalout] action pass
[DeviceB-security-policy-ip-1-ipseclocalout] quit
# Configure a rule named ipseclocalin to allow Device B to receive the IPsec negotiation packets sent from Device A.
[DeviceB-security-policy-ip] rule name ipseclocalin
[DeviceB-security-policy-ip-2-ipseclocalin] source-zone untrust
[DeviceB-security-policy-ip-2-ipseclocalin] destination-zone local
[DeviceB-security-policy-ip-2-ipseclocalin] source-ip-host 1.1.1.1
[DeviceB-security-policy-ip-2-ipseclocalin] destination-ip-host 2.2.2.2
[DeviceB-security-policy-ip-2-ipseclocalin] action pass
[DeviceB-security-policy-ip-2-ipseclocalin] quit
Configure rules to permit traffic between Host B and Host A:
# Configure a rule named trust-untrust to permit the packets from Host B to Host A.
[DeviceB-security-policy-ip] rule name trust-untrust
[DeviceB-security-policy-ip-3-trust-untrust] source-zone trust
[DeviceB-security-policy-ip-3-trust-untrust] destination-zone untrust
[DeviceB-security-policy-ip-3-trust-untrust] source-ip-subnet 10.1.2.0 24
[DeviceB-security-policy-ip-3-trust-untrust] destination-ip-subnet 10.1.1.0 24
[DeviceB-security-policy-ip-3-trust-untrust] action pass
[DeviceB-security-policy-ip-3-trust-untrust] quit
# Configure a rule named untrust-trust to permit the packets from Host A to Host B.
[DeviceB-security-policy-ip] rule name untrust-trust
[DeviceB-security-policy-ip-4-untrust-trust] source-zone untrust
[DeviceB-security-policy-ip-4-untrust-trust] destination-zone trust
[DeviceB-security-policy-ip-4-untrust-trust] source-ip-subnet 10.1.1.0 24
[DeviceB-security-policy-ip-4-untrust-trust] destination-ip-subnet 10.1.2.0 24
[DeviceB-security-policy-ip-4-untrust-trust] action pass
[DeviceB-security-policy-ip-4-untrust-trust] quit
[DeviceB-security-policy-ip] quit
5. Define the data flows to be protected:
# Configure IPv4 advanced ACL 3101 to identify traffic from subnet 10.1.2.0/24 to subnet 10.1.1.0/24.
[DeviceB] acl advanced 3101
[DeviceB-acl-ipv4-adv-3101] rule permit ip source 10.1.2.0 0.0.0.255 destination 10.1.1.0 0.0.0.255
[DeviceB-acl-ipv4-adv-3101] quit
6. Configure an IPsec transform set to specify the packet encapsulation mode, security protocols, and algorithms.
The IPsec transform set settings at both sides of the IPsec tunnel must be the same.
[DeviceB] ipsec transform-set tran1
[DeviceB-ipsec-transform-set-tran1] encapsulation-mode tunnel
[DeviceB-ipsec-transform-set-tran1] protocol esp
[DeviceB-ipsec-transform-set-tran1] esp encryption-algorithm des-cbc
[DeviceB-ipsec-transform-set-tran1] esp authentication-algorithm sha1
[DeviceB-ipsec-transform-set-tran1] quit
7. Configure a PKI entity.
[DeviceB] pki entity entity2
[DeviceB-pki-entity-entity2] common-name deviceb
[DeviceB-pki-entity-entity2] quit
8. Configure a PKI domain for certificate request.
[DeviceB] pki domain domain2
[DeviceB-pki-domain-domain2] public-key rsa general name rsa1
[DeviceB-pki-domain-domain2] undo crl check enable
[DeviceB-pki-domain-domain2] quit
[DeviceB] pki import domain domain2 der ca filename ca.cer
[DeviceB] pki import domain domain2 p12 local filename server.pfx
9. Configure a certificate-based access control policy to control user access rights.
A peer certificate is regarded valid only if it contains the specified string (1 in this example) in the DN attribute of the subject name field.
[DeviceB] pki certificate access-control-policy policy1
[DeviceB-pki-cert-acp-policy1] rule 1 permit group1
[DeviceB] pki certificate attribute-group group1
[DeviceB-pki-cert-attribute-group-group1] attribute 1 subject-name dn ctn 1
10. Configure an IKE profile to specify the security parameters used for setting up IKE SAs.
[DeviceB] ike profile profile2
[DeviceB-ike-profile-profile2] certificate domain domain2
[DeviceB-ike-profile-profile2] exchange-mode aggressive
[DeviceB-ike-profile-profile2] local-identity dn
[DeviceB-ike-profile-profile2] match remote certificate policy1
[DeviceB-ike-profile-profile2] quit
11. Configure an IKE proposal to specify the security parameters for IKE negotiation.
[DeviceB] ike proposal 10
[DeviceB-ike-proposal-10] authentication-algorithm md5
[DeviceB-ike-proposal-10] authentication-method rsa-signature
[DeviceB-ike-proposal-10] quit
12. Configure an IPsec policy template, which is used to create an IPsec policy:
# Create an IPsec policy template entry. Specify template1 as the template name and set the sequence number to 1.
[DeviceB] ipsec policy-template template1 1
[DeviceB-ipsec-policy-template-template1-1] transform-set tran1
[DeviceB-ipsec-policy-template-template1-1] ike-profile profile2
[DeviceB-ipsec-policy-template-template1-1] quit
13. Create an IKE-based IPsec policy entry by using IPsec policy template template1, so as to establish the IPsec tunnel to protect data.
[DeviceB] ipsec policy use1 1 isakmp template template1
14. Apply the IPsec policy to GigabitEthernet 1/0/1 to protect the traffic on the interface.
[DeviceB] interface gigabitethernet 1/0/1
[DeviceB-GigabitEthernet1/0/1] ipsec apply policy use1
[DeviceB-GigabitEthernet1/0/1] quit
# Initiate a connection from subnet 10.1.1.0/24 to subnet 10.1.2.0/24 to trigger IKE negotiation. After IPsec SAs are successfully negotiated by IKE, traffic between the two subnets is IPsec-protected.
# Display the IKE SA on Device A.
[DeviceA] display ike sa
Connection-ID Remote Flag DOI
------------------------------------------------------------------
13 2.2.2.2/500 RD IPsec
Flags:
RD--READY RL--REPLACED FD-FADING RK-REKEY
[DeviceA] display ike sa verbose
-----------------------------------------------
Connection ID: 13
Outside VPN:
Inside VPN:
Profile: profile1
Transmitting entity: Initiator
Initiator cookie: 1bcf453f0a217259
Responder cookie: 5e32a74dfa66a0a4
-----------------------------------------------
Local IP/port: 1.1.1.1/500
Local ID type: FQDN
Local ID: www.devicea.com
Remote IP/port: 2.2.2.2/500
Remote ID type: IPV4_ADDR
Remote ID: 2.2.2.2
Authentication-method: PRE-SHARED-KEY
Authentication-algorithm: SHA1
Encryption-algorithm: DES-CBC
Life duration(sec): 86400
Remaining key duration(sec): 84565
Exchange-mode: Aggressive
Diffie-Hellman group: Group 1
NAT traversal: Detected
Extend authentication: Disabled
Assigned IP address:
Vendor ID index: 0xa1d
Vendor ID sequence number: 0x0
# Display the IPsec SAs generated on Device A.
[DeviceA] display ipsec sa
-------------------------------
Interface: GigabitEthernet1/0/1
-------------------------------
-----------------------------
IPsec policy: policy1
Sequence number: 1
Mode: ISAKMP
-----------------------------
Tunnel id: 0
Encapsulation mode: tunnel
Perfect Forward Secrecy:
Inside VPN:
Extended Sequence Numbers enable: N
Traffic Flow Confidentiality enable: N
Transmitting entity: Initiator
Path MTU: 1435
Tunnel:
local address/port: 1.1.1.1/500
remote address/port: 2.2.2.2/500
Flow:
sour addr: 10.1.1.0/255.255.255.0 port: 0 protocol: ip
dest addr: 10.1.2.0/255.255.255.0 port: 0 protocol: ip
[Inbound ESP SAs]
SPI: 830667426 (0x3182faa2)
Connection ID: 90194313219
Transform set: ESP-ENCRYPT-3DES-CBC ESP-AUTH-MD5
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843200/2313
Max received sequence-number:
Anti-replay check enable: Y
Anti-replay window size: 64
UDP encapsulation used for NAT traversal: Y
Status: Active
[Outbound ESP SAs]
SPI: 3516214669 (0xd1952d8d)
Connection ID: 64424509441
Transform set: ESP-ENCRYPT-3DES-CBC ESP-AUTH-MD5
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843200/2313
Max sent sequence-number:
UDP encapsulation used for NAT traversal: Y
Status: Active
#
interface GigabitEthernet1/0/1
ip address 1.1.1.1 255.255.0.0
ipsec apply policy map1
#
interface GigabitEthernet1/0/2
ip address 10.1.1.1 255.255.255.0
#
security-zone name Trust
import interface GigabitEthernet1/0/2
#
security-zone name Untrust
import interface GigabitEthernet1/0/1
#
ip route-static 2.2.0.0 16 1.1.1.2
ip route-static 10.1.2.0 24 1.1.1.2
#
acl advanced 3101
rule 0 permit ip source 10.1.1.0 0.0.0.255 destination 10.1.2.0 0.0.0.255
#
pki domain domain1
public-key rsa general name rsa1
undo crl check enable
#
pki entity entity1
common-name devicea
#
pki import domain domain2 der ca filename ca.cer
pki import domain domain2 p12 local filename server.pfx
#
pki certificate access-control-policy policy1
rule 1 permit group1
#
pki certificate attribute-group group1
attribute 1 subject-name dn ctn 1
#
ipsec transform-set tran1
encapsulation-mode tunnel
protocol esp
esp encryption-algorithm des-cbc
esp authentication-algorithm sha1
#
ipsec policy map1 10 isakmp
transform-set tran1
security acl 3101
remote-address 2.2.2.2
ike-profile profile1
#
ike profile profile1
certificate domain domain1
exchange-mode aggressive
local-identity dn
match remote certificate policy1
#
ike proposal 10
authentication-method rsa-signature
authentication-algorithm md5
#
security-policy ip
rule 0 name ipseclocalout
action pass
source-zone local
destination-zone untrust
source-ip-host 1.1.1.1
destination-ip-host 2.2.2.2
rule 1 name ipseclocalin
action pass
source-zone untrust
destination-zone local
source-ip-host 2.2.2.2
destination-ip-host 1.1.1.1
rule 2 name trust-untrust
action pass
source-zone trust
destination-zone untrust
source-ip-subnet 10.1.1.0 255.255.255.0
destination-ip-subnet 10.1.2.0 255.255.255.0
rule 3 name untrust-trust
action pass
source-zone untrust
destination-zone trust
source-ip-subnet 10.1.2.0 255.255.255.0
destination-ip-subnet 10.1.1.0 255.255.255.0
#
#
interface GigabitEthernet1/0/1
ip address 2.2.2.2 255.255.0.0
ipsec apply policy use1
#
interface GigabitEthernet1/0/2
ip address 10.1.2.1 255.255.255.0
#
security-zone name Trust
import interface GigabitEthernet1/0/2
#
security-zone name Untrust
import interface GigabitEthernet1/0/1
#
ip route-static 1.1.0.0 16 2.2.2.1
ip route-static 10.1.1.0 24 2.2.2.1
#
acl advanced 3101
rule 0 permit ip source 10.1.2.0 0.0.0.255 destination 10.1.1.0 0.0.0.255
#
pki domain domain2
public-key rsa general name rsa1
undo crl check enable
#
pki entity entity2
common-name deviceb
#
pki import domain domain2 der ca filename ca.cer
pki import domain domain2 p12 local filename server.pfx
#
pki certificate access-control-policy policy1
rule 1 permit group1
#
pki certificate attribute-group group1
attribute 1 subject-name dn ctn 1
#
ipsec transform-set tran1
encapsulation-mode tunnel
protocol esp
esp encryption-algorithm des-cbc
esp authentication-algorithm sha1
#
ipsec policy-template template1 1
transform-set tran1
ike-profile profile2
#
ipsec policy use1 1 isakmp template template1
#
ike profile profile2
certificate domain domain2
exchange-mode aggressive
local-identity dn
match remote certificate policy1
#
ike proposal 10
authentication-method rsa-signature
authentication-algorithm md5
#
security-policy ip
rule 0 name ipseclocalout
action pass
source-zone local
destination-zone untrust
source-ip-host 2.2.2.2
destination-ip-host 1.1.1.1
rule 1 name ipseclocalin
action pass
source-zone untrust
destination-zone local
source-ip-host 1.1.1.1
destination-ip-host 2.2.2.2
rule 2 name trust-untrust
action pass
source-zone trust
destination-zone untrust
source-ip-subnet 10.1.2.0 255.255.255.0
destination-ip-subnet 10.1.1.0 255.255.255.0
rule 3 name untrust-trust
action pass
source-zone untrust
destination-zone trust
source-ip-subnet 10.1.1.0 255.255.255.0
destination-ip-subnet 10.1.2.0 255.255.255.0