CLI example: Configuring a manual mode IPsec tunnel for IPv4 packets between gateways
Network configuration
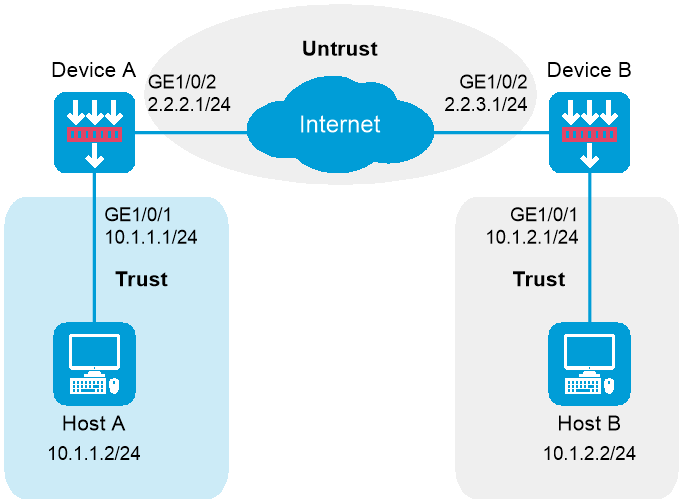
As shown in Figure-1, establish an IPsec tunnel between Device A and Device B to protect data flows between subnet 10.1.1.0/24 and subnet 10.1.2.0/24. Configure the tunnel as follows:
Software versions used
This configuration example was created and verified on E9900 of the F5000-AI-55-G device.
Procedures
Configuring Device A
Assign IP addresses to interfaces:
# Assign an IP address to interface GigabitEthernet 1/0/1.
<DeviceA> system-view
[DeviceA] interface gigabitethernet 1/0/1
[DeviceA-GigabitEthernet1/0/1] ip address 10.1.1.1 255.255.255.0
[DeviceA-GigabitEthernet1/0/1] quit
# Assign IP addresses to other interfaces in the same way. (Details not shown.)
Configure settings for routing.
This example configures static routes, and the next hop in the routes is 2.2.2.2.
[DeviceA] ip route-static 10.1.2.0 24 2.2.2.2
[DeviceA] ip route-static 2.2.3.1 24 2.2.2.2
Add interfaces to security zones.
[DeviceA] security-zone name trust
[DeviceA-security-zone-Trust] import interface gigabitethernet 1/0/1
[DeviceA-security-zone-Trust] quit
[DeviceA] security-zone name untrust
[DeviceA-security-zone-Untrust] import interface gigabitethernet 1/0/2
[DeviceA-security-zone-Untrust] quit
Configure a security policy:
Configure rules to permit traffic between the
Untrust andLocal security zones, so the devices can set up an IPsec tunnel:# Configure a rule named
ipseclocalout to allow Device A to send IPsec negotiation packets to Device B.[DeviceA] security-policy ip
[DeviceA-security-policy-ip] rule name ipseclocalout
[DeviceA-security-policy-ip-1-ipseclocalout] source-zone local
[DeviceA-security-policy-ip-1-ipseclocalout] destination-zone untrust
[DeviceA-security-policy-ip-1-ipseclocalout] source-ip-host 2.2.2.1
[DeviceA-security-policy-ip-1-ipseclocalout] destination-ip-host 2.2.3.1
[DeviceA-security-policy-ip-1-ipseclocalout] action pass
[DeviceA-security-policy-ip-1-ipseclocalout] quit
# Configure a rule named
ipseclocal in to allow Device A to receive the IPsec negotiation packets sent from Device B.[DeviceA-security-policy-ip] rule name ipseclocalin
[DeviceA-security-policy-ip-2-ipseclocalin] source-zone untrust
[DeviceA-security-policy-ip-2-ipseclocalin] destination-zone local
[DeviceA-security-policy-ip-2-ipseclocalin] source-ip-host 2.2.3.1
[DeviceA-security-policy-ip-2-ipseclocalin] destination-ip-host 2.2.2.1
[DeviceA-security-policy-ip-2-ipseclocalin] action pass
[DeviceA-security-policy-ip-2-ipseclocalin] quit
Configure rules to permit the traffic between Host A and Host B:
# Configure a rule named
trust-untrust to permit the packets from Host A to Host B.[DeviceA-security-policy-ip] rule name trust-untrust
[DeviceA-security-policy-ip-3-trust-untrust] source-zone trust
[DeviceA-security-policy-ip-3-trust-untrust] destination-zone untrust
[DeviceA-security-policy-ip-3-trust-untrust] source-ip-subnet 10.1.1.0 24
[DeviceA-security-policy-ip-3-trust-untrust] destination-ip-subnet 10.1.2.0 24
[DeviceA-security-policy-ip-3-trust-untrust] action pass
[DeviceA-security-policy-ip-3-trust-untrust] quit
# Configure a rule named
untrust-trust to permit the packets from Host B to Host A.[DeviceA-security-policy-ip] rule name untrust-trust
[DeviceA-security-policy-ip-4-untrust-trust] source-zone untrust
[DeviceA-security-policy-ip-4-untrust-trust] destination-zone trust
[DeviceA-security-policy-ip-4-untrust-trust] source-ip-subnet 10.1.2.0 24
[DeviceA-security-policy-ip-4-untrust-trust] destination-ip-subnet 10.1.1.0 24
[DeviceA-security-policy-ip-4-untrust-trust] action pass
[DeviceA-security-policy-ip-4-untrust-trust] quit
[DeviceA-security-policy-ip] quit
Define the data flow to be protected:
# Configure an IPv4 advanced ACL to identify the data flow from subnet 10.1.1.0/24 to subnet 10.1.2.0/24.
[DeviceA] acl advanced 3101
[DeviceA-acl-ipv4-adv-3101] rule permit ip source 10.1.1.0 0.0.0.255 destination 10.1.2.0 0.0.0.255
[DeviceA-acl-ipv4-adv-3101] quit
Configure an IPsec transform set to specify the packet encapsulation mode, security protocols, and algorithms.
The IPsec transform set settings at both sides of the IPsec tunnel must be the same.
[DeviceA] ipsec transform-set tran1
[DeviceA-ipsec-transform-set-tran1] encapsulation-mode tunnel
[DeviceA-ipsec-transform-set-tran1] protocol esp
[DeviceA-ipsec-transform-set-tran1] esp encryption-algorithm aes-cbc-128
[DeviceA-ipsec-transform-set-tran1] esp authentication-algorithm sha1
[DeviceA-ipsec-transform-set-tran1] quit
Configure an IPsec policy, so as to establish the IPsec tunnel to protect data:
# Create a manual IPsec policy entry, which specifies the ACL for IPsec, the IPsec transform set, and the remote IP address of the IPsec tunnel.
[DeviceA] ipsec policy map1 10 manual
[DeviceA-ipsec-policy-manual-map1-10] security acl 3101
[DeviceA-ipsec-policy-manual-map1-10] transform-set tran1
[DeviceA-ipsec-policy-manual-map1-10] remote-address 2.2.3.1
[DeviceA-ipsec-policy-manual-map1-10] sa spi outbound esp 12345
[DeviceA-ipsec-policy-manual-map1-10] sa spi inbound esp 54321
[DeviceA-ipsec-policy-manual-map1-10] sa string-key outbound esp simple abcdefg
[DeviceA-ipsec-policy-manual-map1-10] sa string-key inbound esp simple gfedcba
[DeviceA-ipsec-policy-manual-map1-10] quit
Apply the IPsec policy to GigabitEthernet 1/0/2 to protect traffic on the interface.
[DeviceA] interface gigabitethernet 1/0/2
[DeviceA-GigabitEthernet1/0/2] ipsec apply policy map1
[DeviceA-GigabitEthernet1/0/2] quit
Configuring Device B
Assign IP addresses to interfaces:
# Assign an IP address to interface GigabitEthernet 1/0/1.
<DeviceB> system-view
[DeviceB] interface gigabitethernet 1/0/1
[DeviceB-GigabitEthernet1/0/1] ip address 10.1.2.1 255.255.255.0
[DeviceB-GigabitEthernet1/0/1] quit
# Assign IP addresses to other interfaces in the same way. (Details not shown.)
Configure settings for routing.
This example configures static routes, and the next hop in the routes is 2.2.3.2.
[DeviceB] ip route-static 10.1.1.0 24 2.2.3.2
[DeviceB] ip route-static 2.2.2.1 24 2.2.3.2
Add interfaces to security zones.
[DeviceB] security-zone name trust
[DeviceB-security-zone-Trust] import interface gigabitethernet 1/0/1
[DeviceB-security-zone-Trust] quit
[DeviceB] security-zone name untrust
[DeviceB-security-zone-Untrust] import interface gigabitethernet 1/0/2
[DeviceB-security-zone-Untrust] quit
Configure a security policy:
Configure rules to permit traffic between the
Untrust andLocal security zones, so the devices can set up an IPsec tunnel:# Configure a rule named
ipseclocalout to allow Device B to send IPsec negotiation packets to Device A.[DeviceB] security-policy ip
[DeviceB-security-policy-ip] rule name ipseclocalout
[DeviceB-security-policy-ip-1-ipseclocalout] source-zone local
[DeviceB-security-policy-ip-1-ipseclocalout] destination-zone untrust
[DeviceB-security-policy-ip-1-ipseclocalout] source-ip-host 2.2.3.1
[DeviceB-security-policy-ip-1-ipseclocalout] destination-ip-host 2.2.2.1
[DeviceB-security-policy-ip-1-ipseclocalout] action pass
[DeviceB-security-policy-ip-1-ipseclocalout] quit
# Configure a rule named
ipseclocalin to allow Device B to receive the IPsec negotiation packets sent from Device A.[DeviceB-security-policy-ip] rule name ipseclocalin
[DeviceB-security-policy-ip-2-ipseclocalin] source-zone untrust
[DeviceB-security-policy-ip-2-ipseclocalin] destination-zone local
[DeviceB-security-policy-ip-2-ipseclocalin] source-ip-host 2.2.2.1
[DeviceB-security-policy-ip-2-ipseclocalin] destination-ip-host 2.2.3.1
[DeviceB-security-policy-ip-2-ipseclocalin] action pass
[DeviceB-security-policy-ip-2-ipseclocalin] quit
Configure rules to permit traffic between Host B and Host A:
# Configure a rule named
trust-untrust to permit the packets from Host B to Host A.[DeviceB-security-policy-ip] rule name trust-untrust
[DeviceB-security-policy-ip-3-trust-untrust] source-zone trust
[DeviceB-security-policy-ip-3-trust-untrust] destination-zone untrust
[DeviceB-security-policy-ip-3-trust-untrust] source-ip-subnet 10.1.2.0 24
[DeviceB-security-policy-ip-3-trust-untrust] destination-ip-subnet 10.1.1.0 24
[DeviceB-security-policy-ip-3-trust-untrust] action pass
[DeviceB-security-policy-ip-3-trust-untrust] quit
# Configure a rule named
untrust-trust to permit the packets from Host A to Host B.[DeviceB-security-policy-ip] rule name untrust-trust
[DeviceB-security-policy-ip-4-untrust-trust] source-zone untrust
[DeviceB-security-policy-ip-4-untrust-trust] destination-zone trust
[DeviceB-security-policy-ip-4-untrust-trust] source-ip-subnet 10.1.1.0 24
[DeviceB-security-policy-ip-4-untrust-trust] destination-ip-subnet 10.1.2.0 24
[DeviceB-security-policy-ip-4-untrust-trust] action pass
[DeviceB-security-policy-ip-4-untrust-trust] quit
[DeviceB-security-policy-ip] quit
Define the data flows to be protected:
# Configure an IPv4 advanced ACL to identify data flows from subnet 10.1.2.0/24 to subnet 10.1.1.0/24.
[DeviceB] acl advanced 3101
[DeviceB-acl-ipv4-adv-3101] rule permit ip source 10.1.2.0 0.0.0.255 destination 10.1.1.0 0.0.0.255
[DeviceB-acl-ipv4-adv-3101] quit
Configure an IPsec transform set to specify the packet encapsulation mode, security protocols, and algorithms.
The IPsec transform set settings at both sides of the IPsec tunnel must be the same.
[DeviceB] ipsec transform-set tran1
[DeviceB-ipsec-transform-set-tran1] encapsulation-mode tunnel
[DeviceB-ipsec-transform-set-tran1] protocol esp
[DeviceB-ipsec-transform-set-tran1] esp encryption-algorithm aes-cbc-128
[DeviceB-ipsec-transform-set-tran1] esp authentication-algorithm sha1
[DeviceB-ipsec-transform-set-tran1] quit
Configure an IPsec policy, so as to establish the IPsec tunnel to protect data:
# Create a manual IPsec policy entry, which specifies the ACL for IPsec, the IPsec transform set, and the remote IP address of the IPsec tunnel.
[DeviceB] ipsec policy use1 10 manual
[DeviceB-ipsec-policy-manual-use1-10] security acl 3101
[DeviceB-ipsec-policy-manual-use1-10] transform-set tran1
[DeviceB-ipsec-policy-manual-use1-10] remote-address 2.2.2.1
[DeviceB-ipsec-policy-manual-use1-10] sa spi outbound esp 54321
[DeviceB-ipsec-policy-manual-use1-10] sa spi inbound esp 12345
[DeviceB-ipsec-policy-manual-use1-10] sa string-key outbound esp simple gfedcba
[DeviceB-ipsec-policy-manual-use1-10] sa string-key inbound esp simple abcdefg
[DeviceB-ipsec-policy-manual-use1-10] quit
Apply the IPsec policy to GigabitEthernet 1/0/2 to protect traffic on the interface.
[DeviceB] interface gigabitethernet 1/0/2
[DeviceB-GigabitEthernet1/0/2] ipsec policy use1
[DeviceB-GigabitEthernet1/0/2] quit
Verifying the configuration
After the configuration is completed, an IPsec tunnel between Device A and Device B is established, and the traffic between subnet 10.1.1.0/24 and subnet 10.1.2.0/24 is IPsec-protected. This example uses Device A to verify the configuration.
# Display IPsec SAs on Device A.
[DeviceA] display ipsec sa
-------------------------------
Interface: GigabitEthernet 1/0/2
-------------------------------
-----------------------------
IPsec policy: map1
Sequence number: 10
Alisa: map1-10
Mode: Manual
-----------------------------
Tunnel id: 549
Encapsulation mode: tunnel
Path MTU: 1443
Tunnel:
local address/port: 2.2.2.1/0
remote address/port: 2.2.3.1/0
Flow:
as defined in ACL 3101
[Inbound ESP SA]
SPI: 54321 (0x0000d431)
Connection ID: 1
Transform set: ESP-ENCRYPT-AES-CBC-128 ESP-AUTH-SHA1
No duration limit for this SA
[Outbound ESP SA]
SPI: 12345 (0x00003039)
Connection ID: 2
Transform set: ESP-ENCRYPT-AES-CBC-128 ESP-AUTH-SHA1
No duration limit for this SA
Configuration files
Device A
#
interface GigabitEthernet1/0/1
ip address 10.1.1.1 255.255.255.0
#
interface GigabitEthernet1/0/2
ip address 2.2.2.1 255.255.255.0
ipsec apply policy map1
#
security-zone name Trust
import interface GigabitEthernet1/0/1
#
security-zone name Untrust
import interface GigabitEthernet1/0/2
#
ip route-static 2.2.3.0 24 2.2.2.2
ip route-static 10.1.2.0 24 2.2.2.2
#
acl advanced 3101
rule 0 permit ip source 10.1.1.0 0.0.0.255 destination 10.1.2.0 0.0.0.255
#
ipsec transform-set tran1
encapsulation-mode tunnel
protocol esp
esp encryption-algorithm aes-cbc-128
esp authentication-algorithm sha1
#
ipsec policy map1 10 manual
transform-set tran1
security acl 3101
remote-address 2.2.3.1
sa spi inbound esp 54321
sa string-key inbound esp simple abcdefg
sa spi outbound esp 12345
sa string-key outbound esp simple gfedcba
#
security-policy ip
rule 0 name ipseclocalout
action pass
source-zone local
destination-zone untrust
source-ip-host 2.2.2.1
destination-ip-host 2.2.3.1
rule 1 name ipseclocalin
action pass
source-zone untrust
destination-zone local
source-ip-host 2.2.3.1
destination-ip-host 2.2.2.1
rule 2 name trust-untrust
action pass
source-zone trust
destination-zone untrust
source-ip-subnet 10.1.1.0 255.255.255.0
destination-ip-subnet 10.1.2.0 255.255.255.0
rule 3 name untrust-trust
action pass
source-zone untrust
destination-zone trust
source-ip-subnet 10.1.2.0 255.255.255.0
destination-ip-subnet 10.1.1.0 255.255.255.0
#
Device B
#
interface GigabitEthernet1/0/1
ip address 10.1.2.1 255.255.255.0
#
interface GigabitEthernet1/0/2
ip address 2.2.3.1 255.255.255.0
ipsec apply policy use1
#
security-zone name Trust
import interface GigabitEthernet1/0/1
#
security-zone name Untrust
import interface GigabitEthernet1/0/2
#
ip route-static 2.2.2.0 24 2.2.3.2
ip route-static 10.1.1.0 24 2.2.3.2
#
acl advanced 3101
rule 0 permit ip source 10.1.2.0 0.0.0.255 destination 10.1.1.0 0.0.0.255
#
ipsec transform-set tran1
encapsulation-mode tunnel
protocol esp
esp encryption-algorithm aes-cbc-128
esp authentication-algorithm sha1
#
ipsec policy use1 10 manual
transform-set tran1
security acl 3101
remote-address 2.2.2.1
sa spi inbound esp 12345
sa string-key inbound esp simple gfedcba
sa spi outbound esp 54321
sa string-key outbound esp simple abcdefg
#
security-policy ip
rule 0 name ipseclocalout
action pass
source-zone local
destination-zone untrust
source-ip-host 2.2.3.1
destination-ip-host 2.2.2.1
rule 1 name ipseclocalin
action pass
source-zone untrust
destination-zone local
source-ip-host 2.2.2.1
destination-ip-host 2.2.3.1
rule 2 name trust-untrust
action pass
source-zone trust
destination-zone untrust
source-ip-subnet 10.1.2.0 255.255.255.0
destination-ip-subnet 10.1.1.0 255.255.255.0
rule 3 name untrust-trust
action pass
source-zone untrust
destination-zone trust
source-ip-subnet 10.1.1.0 255.255.255.0
destination-ip-subnet 10.1.2.0 255.255.255.0
#