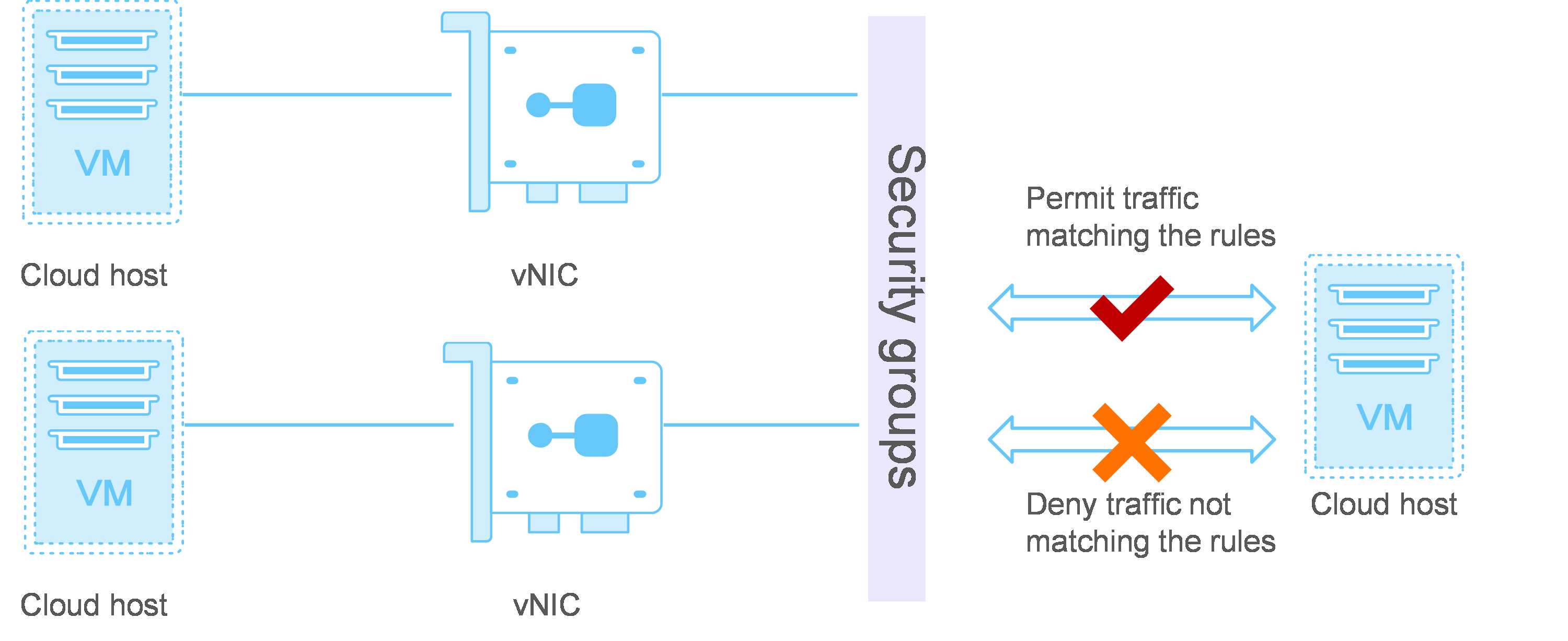
About security groups
A security group is a logical group comprised of cloud hosts that trust each other and have the same security protection requirements. In a security group, you can define rules to restrict the inbound and outbound traffic of the security group. For example, you can configure a rule to permit SSH access, ping, and UDP traffic. Security groups deny all traffic that does not match the security group rules. A security group protects a cloud host immediately after the cloud host is added to the security group.
The security group of a cloud host is the security group where the vNIC of the cloud host belongs.
Figure-1 Cloud hosts and security groups
Concepts
Directions of rules
A security group rule's direction can be inbound or outbound. An inbound rule takes effect on the traffic from objects outside the security group to the could hosts inside the security group. An outbound rule takes effect on the traffic from the cloud hosts inside the security group to the objects outside the security group.
Default security group and security group template
The default security group is named default. A security group template defines the initial rules for the default security group. By default, the default security group contains four rules, as shown in Table-1, which permit all inbound and outbound traffic. The cloud administrator can Edit the security group template to customize the initial rules for the default security group. The default security group for an organization is available for users in this organization.
When creating a cloud host, you can select a security group or use the default security group. After a cloud host is created, you can Edit the security group of a vNIC to change the security group of the cloud host. You can also configure more rules for the security group of the cloud host (see Configure a security group rule).
Table-1 Initial rules in the default security group
|
Direction |
IP Protocol Type |
Protocol |
Port |
Remote |
|
Inbound |
IPv6 |
Any |
Any |
::/0 |
|
Inbound |
IPv4 |
Any |
Any |
0.0.0.0/0 |
|
Outbound |
IPv6 |
Any |
Any |
::/0 |
|
Outbound |
IPv4 |
Any |
Any |
0.0.0.0/0 |
User-defined security groups
User-defined security groups are created by users. Common users cannot use the user-defined security groups created by an organization administrator. Organization administrators can use the user-defined security groups created by common users. You can create security groups before you creating cloud hosts. These security groups then are available for selection during creation of a cloud host. By default, a user-defined security group has two outbound rules to permit all outbound traffic and zero inbound rules to deny all inbound traffic, as shown in Table-2. You can add or delete rules in a security group as needed, and you can bind a security group to vNICs to protect cloud hosts.
Table-2 Default rules in a user-defined security group
|
Direction |
IP Protocol Type |
Protocol |
Port |
Remote |
|
Outbound |
IPv6 |
Any |
Any |
::/0 |
|
Outbound |
IPv4 |
Any |
Any |
0.0.0.0/0 |
Table-3 Availability of user-defined security groups
|
The l icon represents available. The ¡ icon represents unavailable. The -- icon represents partially available. |
|
Role of Creator |
Cloud Administrator |
Organization Administrators |
Organization Common Users (excluding the creator when the creator is a common user) |
|
Common user |
l |
l |
¡ |
|
Organization administrator |
l |
-- (available to the administrator of an organization and unavailable to the administrators of the organization's lower-level organizations. |
¡ |
|
Cloud administrator |
l |
-- (available to the administrator of the root organization and unavailable to the administrators of the root organization's lower-level organizations.) |
¡ |
Relationship between security group and other cloud services
Table-4 Relationship between security group and other cloud services
|
Service |
Relationship with security group |
|
Cloud host |
A security group protects a cloud host immediately after the cloud host is added to the security group. The inbound and outbound traffic of the cloud host is restricted according to the security group rules. |
|
vNIC |
A vNIC links a cloud host with a security group. To add or remove a cloud host to or from a security group, edit the security group of the vNIC of the cloud host. |
Restrictions and guidelines
A vNIC can be bound to multiple security groups, but only one of the security groups takes effect to the vNIC. The effective security group is determined by the security group obtaining order by the virtualized platform and is independent of the security group configuration order or display order. As a best practice for you to identify the effective security group, bind a vNIC to only one security group.