Threat intelligence
This help contains the following topics:
IP reputation
Introduction
IP reputation uses the IP address information on the local IP reputation to filter network traffic. The local IP reputation includes the IP reputation signature library loaded on the device and the historical query results from the cloud server, that is, the local IP reputation cache.
IP reputation signature library
The IP reputation signature library contains the attack category, suggested action, and logging information for IP addresses with potential risks of attacks, such as DDoS, command injection attacks, Trojan virus download attacks, or port scan.
Cloud server
The cloud server provides the device with IP reputation cloud query to enhance the locally loaded IP reputation signature library. When the IP reputation signature library cannot match the IP address information in the packet, IP reputation cloud query can be used to send the IP address information to the cloud server for query. After the cloud server completes the detection, it sends the detection results to the device. Then, the device will save the results to the local IP reputation cache. This allows subsequent packets to be directly matched against IP reputation information locally, without the need for further cloud server queries.
Attack category and action
The device takes an action (
On the local IP reputation, an IP address might belong to multiple attack categories. Each attack category has an associated action.
If an IP address belongs to only one attack category, the action that the device takes on matching packets is consistent with the action of the attack category. If an IP address belongs to multiple attack categories, the device takes an action that has highest priority among all actions of the attack categories. The
If logging is enabled for any one of attack categories to which the IP address belongs, the device generates a log for the matching packets.
Exception IP list
A packet is forwarded if its source IP address or destination IP address has a match on the exception IP list. The device does not perform IP reputation check on subsequent IP packets with this source or destination IP address.
Blacklist operation
The device supports adding IP addresses on the local IP reputation to or removing them from the blacklist. An IP address on the local IP reputation can be added to the source address blacklist or destination address blacklist, depending on direction attribute of the IP address.
All IP addresses on the local IP reputation are public addresses. The VRF is public network for blacklist entries that are added based on IP reputation.
The default aging time for blacklist entries is 7 days. To modify the aging time, access the
For more information about the blacklist, see the attack defense help.
IP reputation workflow
Figure-1
Figure-1 IP reputation workflow
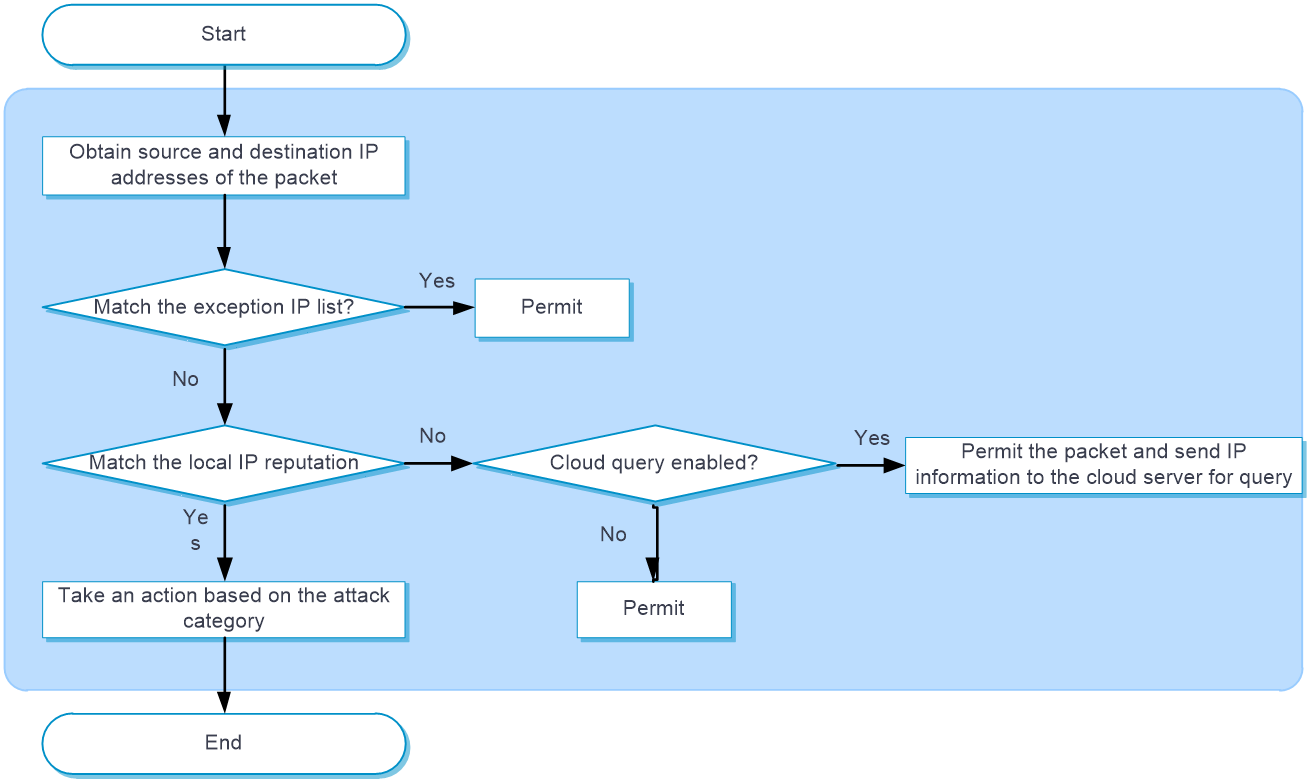
IP reputation processes a packet as follows:
The device determines whether the source IP address or destination IP address has a match on the exception IP list. If a match is found, the packet is passed through. If no match exists, the device proceeds to the next step.
The device determines whether the source IP address or destination IP address has a match on the local IP reputation. IP addresses on the local IP reputation has the direction attribute, including source, destination, and bidirection. The match succeeds only when the IP address in the packet has the same direction attribute as the IP address on the local IP reputation. If the direction attribute of an IP address is bidirection, the match succeeds if the source or destination IP address is the same as the IP address on the local IP reputation.
If a match is found, the device takes an action based on the attack category of the IP address. If no match exists, the device forwards the packet. The device supports the following actions:
Permit —Allows packets to pass through.Drop —Drops packets.Logging —Generates IP reputation logs.
If no match is found, the device identifies whether cloud query is enabled. If cloud query is enabled, the device will permit the packet to pass through and send the IP address information to the cloud server for query. The device will then save the query results from the server to the local IP reputation cache. This allows subsequent packets to be matched locally against the IP reputation, without the need for further cloud server query. If cloud query is not enabled, the device will directly permit the packet to pass through.
vSystem support information
Support of non-default vSystems for this feature depends on the device model. This feature is available on the Web interface only if it is supported.
Licensing requirements
To use IP reputation, you must purchase a threat intelligence license and install it correctly. When the license expires, the existing IP reputation signature library is still available. However, you cannot upgrade the signature library to the version released after the license expires and the cloud query feature is unavailable. For more information about licensing, see the license management help.
Restrictions and guidelines
Top hit statistics are cleared after you disable top hit statistics.
The source IP blacklist entries added by IP reputation do not carry DS-Lite peer address information. To modify DS-Lite peer address information, access the
Policies >Active Defense >Blacklist page.Before enabling cloud query for IP reputation, verify that the cloud server is connected on the
Objects >APP Security >Cloud Server page. If the connection status is abnormal, clickCheck and troubleshoot the issues as instructed.If cloud query for IP reputation is disabled in all contexts on the device, the device clears all the local IP reputation cache.
Make sure the system time is the same as the network time.
Configure IP reputation
Prerequisites
Complete the following tasks before you configure this feature:
Assign IP addresses to interfaces on the
Network >Interface Configuration >Interfaces page.Configure routes on the
Network >Routing page. Make sure the routes are available.Create security zones on the
Network >Security Zones page.Add interfaces to security zones. You can add interfaces to a security zone on the
Security Zones page or select a security zone for an interface on theInterfaces page.Configure security policies to permit the target traffic on the
Policies >Security Policies page.
Enable IP reputation
Click the
Policies tab.In the navigation pane, select
A ctive Defense >Threat Intelligence >IP Reputation .Enable
IP reputation .Figure-2 IP reputation
To query an IP address, click
IP address search , enter the IP address, and clickSearch . Information about the IP address is displayed. You can add the IP address to or remove it from the blacklist or exception IP list.Figure-3 Querying an IP address
Enable cloud query for IP reputation
Click the
Policies tab.In the navigation pane, select
A ctive Defense >Threat Intelligence In the IP reputation section, enable
IP reputation .In the IP reputation section, enable
Cloud query for IP reputation .Figure-4 Cloud query for IP reputation
Enable top hit statistics collection
Click the
Policies tab.In the navigation pane, select
Active Defense >Threat Intelligence >IP Reputation .Enable
IP reputation .Enable
IP address hit statistics .Figure-5 IP address hit statististics

To open the
Top Hit Statistics page, clickTop hit statistics . To view top hit statistics ranking information, configure statistics conditions. You can also add an IP address to or remove it from the blacklist or exception IP list.Figure-6 Top hit statistics
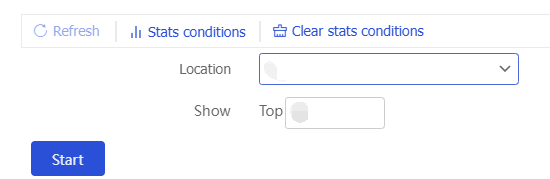
Configure the action for an attack category
Click the
Policies tab.In the navigation pane, select
Active Defense >Threat Intelligence >IP Reputation .Enable
IP reputation .In the
Action configuration area, configure an action for an attack category. The following actions are supported.Permit —Allows packets to pass through.Drop —Drops packets.
To restore the default configuration, click
Restore default .Figure-7 Action configuration
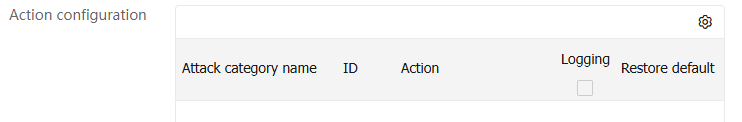
Click
Apply .
Configure the exception IP list
Click the
Policies tab.In the navigation pane, select
Active Defense >Threat Intelligence >IP Reputation .Enable
IP reputation .In the
Exception IP list area, enter IP addresses. Each IP address occupies a line.Figure-8 Exception IP list
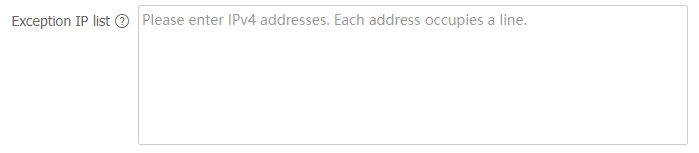
Click
Apply .
URL reputation
Introduction
URL reputation restricts user online behaviors by blocking access to malicious URLs based on the URL reputation signature library. The local URL reputation includes the URL reputation signature library loaded on the device and the historical query results from the cloud server, that is, the local URL reputation cache.
URL reputation signature library
The signature library is a collection of malicious URLs, including the attack category to which each URL belongs and the actions for an attack category.
Cloud server
The cloud server provides the device with URL reputation cloud query to enhance the locally loaded URL reputation signature library. When the URL reputation signature library cannot match the URL information in the packet, URL reputation cloud query can be used to send the URL information to the cloud server for query. After the cloud server completes the detection, it sends the detection results to the device. Then, the device will save the results to the local URL reputation cache. This allows subsequent packets to be directly matched against URL reputation information locally, without the need for further cloud server queries.
vSystem support information
Support of non-default vSystems for this feature depends on the device model. This feature is available on the Web interface only if it is supported.
Licensing requirements
To use URL reputation, you must purchase a threat intelligence license and install it correctly. When the license expires, the existing URL reputation signature library is still available but you cannot upgrade the signature library to the version released after the license expires. For more information about licensing, see the license management help.
Restrictions and guidelines
A threat intelligence license is required for URL reputation. If the license expires, the existing URL reputation signature library is still available but you cannot upgrade the library on the device. For more information about licenses, see license online help.
Configure URL reputation
Prerequisites
Complete the following tasks before you configure this feature:
Assign IP addresses to interfaces on the
Network >Interface Configuration >Interfaces page.Configure routes on the
Network >Routing page. Make sure the routes are available.Create security zones on the
Network >Security Zones page.Add interfaces to security zones. You can add interfaces to a security zone on the
Security Zones page or select a security zone for an interface on theInterfaces page.Configure security policies to permit the target traffic on the
Policies >Security Policies page.
Enable URL reputation
Click the
Objects tab.In the navigation pane, select
APP Security >URL Filtering >Profiles .Create or edit a URL filtering profile.
To create a URL filtering profile, click
Create . On the dialog box that opens, specify a name for the URL filtering profile. To edit an existing URL filtering profile, clickEdit for that URL filtering profile. On the dialog box that opens, edit the URL filtering profile.Configure the actions for individual attack categories in the URL reputation signature library. When the device receives a packet, it extracts the URL of the packet and determines whether the URL matches an attack category in the URL reputation signature library. If yes, the device takes the action specified for the attack category on the packet.
Turn on the
Enable URL reputation feature.Figure-9 URL reputation
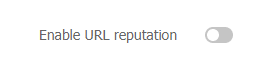
Click
OK .
Domain reputation
Introduction
Domain reputation uses the domain name information in the local domain reputation to filter network traffic. The local domain reputation includes the domain reputation signature library loaded on the device and the historical query results from the cloud server, that is, the local domain reputation cache.
Domain reputation signature library
The domain reputation signature library contains domain names with risks such as zombie host DDoS attacks, command injection attacks, Trojan virus download attacks, or port scan. The signature library contains information such as the attack type of each domain name, the recommended action, and whether to record logs. For more information, see the signature upgrade help.
Cloud server
The cloud server provides the device with domain reputation cloud query to enhance the locally loaded domain reputation signature library. When the domain reputation signature library cannot match the IP address information in the packet, domain reputation cloud query can be used to send the domain name information to the cloud server for query. After the cloud server completes the detection, it sends the detection results to the device. Then, the device will save the results to the local domain reputation cache. This allows subsequent packets to be directly matched against domain reputation information locally, without the need for further cloud server queries.
Attack category and action
The device takes an action (
In the domain reputation signature library, a domain name might belong to multiple attack categories. Each attack category has an associated action.
If a domain name belongs to only one attack category, the device takes the action of the attack category on the packet. If a domain name belongs to multiple attack categories, the device takes an action that has the highest priority among all actions of the attack categories. The
If logging is enabled for any one of attack categories to which the domain name belongs, the device generates a log for the matching packets.
Domain reputation workflow
Figure-10
Figure-10 Domain reputation workflow
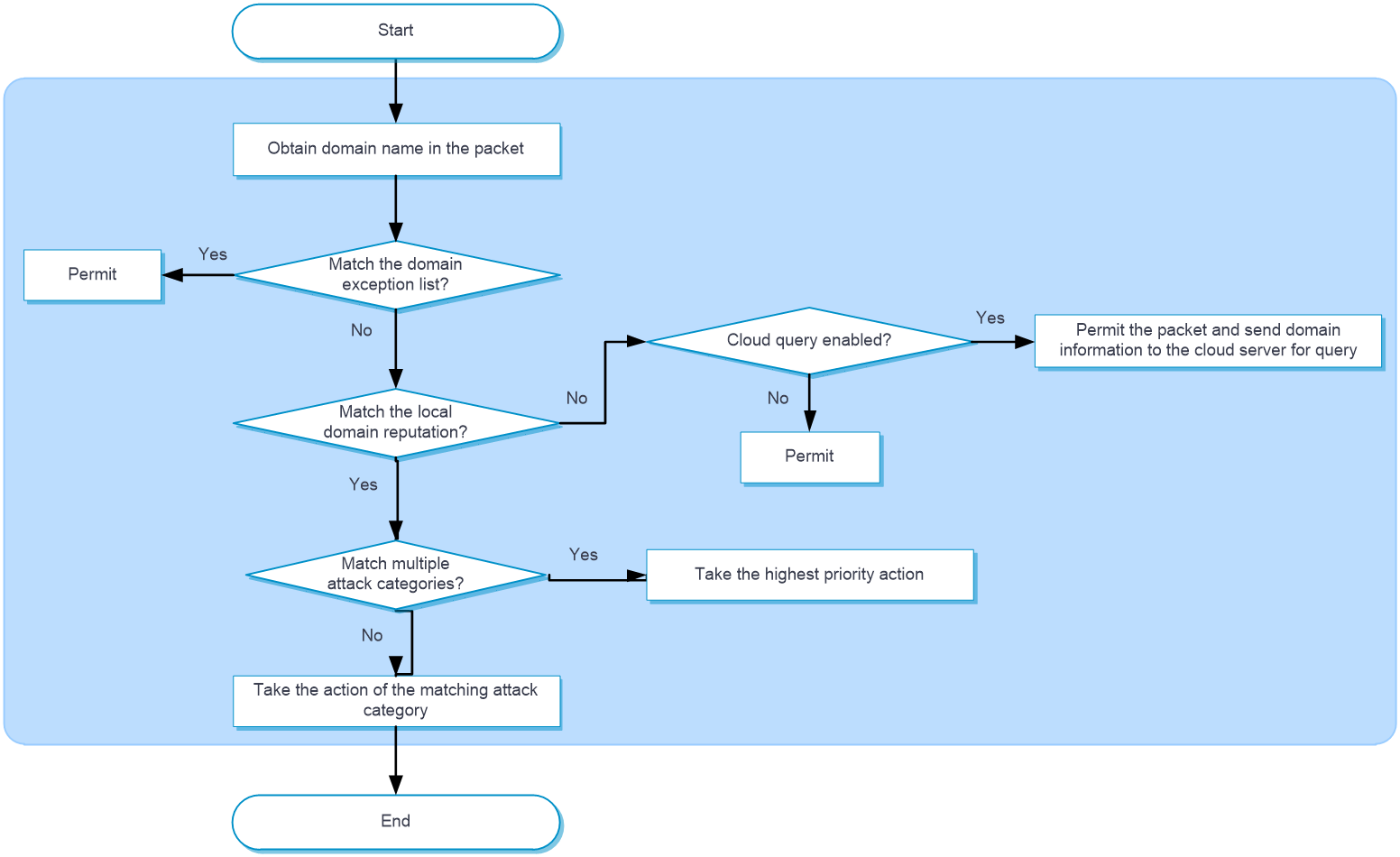
Domain reputation processes a packet as follows:
The device determines whether the domain name in the packet has a match on the domain name exception list. If a match is found, the packet is forwarded directly. If no match exists, the device proceeds to the next step.
The device determines whether the domain name has a match in the local domain reputation and takes the corresponding action.
If a match is found, the device takes the action of the matching attack category.
If more than one match is found, the device takes the action that has the highest priority among all the actions of the attack categories.
The following actions are supported:
Permit —Allows packets to pass through.Drop —Drops packets.Logging —Generates domain reputation logs.
If no match is found, the device identifies whether cloud query is enabled. If cloud query is enabled, the device will permit the packet to pass through and send the domain name information to the cloud server for query. The device will then save the query results from the server to the local domain reputation cache. This allows subsequent packets to be matched locally against the domain reputation, without the need for further cloud server query. If cloud query is not enabled, the device will directly permit the packet to pass through.
Domain name exception list
A packet is forwarded directly if it contains a domain name on the domain name exception list. The device does not perform domain reputation check on the packet.
vSystem support information
Support of non-default vSystems for this feature depends on the device model. This feature is available on the Web interface only if it is supported.
Licensing requirements
To use domain reputation, you must purchase a license and install it correctly. When the license expires, the existing domain reputation signature library is still available. However, you cannot upgrade the signature library to the version released after the license expires and the cloud query feature is unavailable. For more information about licensing, see the license management help.
Restrictions and guidelines
Top hit statistics are cleared after you disable top hit statistics.
Make sure the system time is the same as the network time.
Before enabling cloud query for domain reputation, verify that the cloud server is connected on the
Objects >APP Security >Cloud Server page. If the connection status is abnormal, clickCheck and troubleshoot the issues as instructed.If cloud query for domain reputation is disabled in all contexts on the device, the device clears all the local domain reputation cache.
Configure domain reputation
Prerequisites
Complete the following tasks before you configure this feature:
Assign IP addresses to interfaces on the
Network >Interface Configuration >Interfaces page.Configure routes on the
Network >Routing page. Make sure the routes are available.Create security zones on the
Network >Security Zones page.Add interfaces to security zones. You can add interfaces to a security zone on the
Security Zones page or select a security zone for an interface on theInterfaces page.Configure security policies to permit the target traffic on the
Policies >Security Policies page.
Enable domain reputation
In the navigation pane, select
Active Defense >Threat Intelligence >Domain Reputation .Enable
Domain Reputation .Figure-11 Domain reputation
To search for a domain name, click
Domain name search , enter the domain name, and clickSearch . Information about the matching domain name is displayed. You can add the domain name to or remove it from the domain name exception list.Figure-12 Searching for a domain name
Enable
Cloud query for domain name reputation .Figure-13 Cloud query for domain name reputation
Enable
Domain name hit statistics .Figure-14 Domain name hit statistics

To open the
Top Hit Statistics page, clickTop hit statistics . To view top hit statistics ranking information, configure statistics conditions. You can also add a domain name to or remove it from the domain name exception list.Figure-15 Top hit statistics
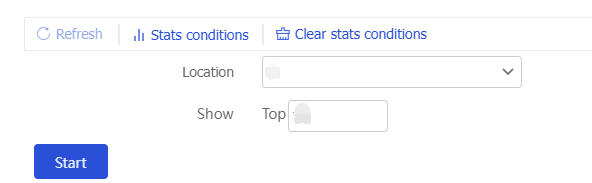
In the
Action configuration area, configure an action for an attack category. The following actions are supported:Permit —Allows packets to pass through.Drop —Drops packets.
To restore the default configuration, click
Restore default .Figure-16 Action configuration
Click
Apply .
Configure the domain name exception list
Click the
Policies tab.In the navigation pane, select
Active Defense >Threat Intelligence >Domain Reputation .In the
Advanced settings area, enter exceptional domain names. Each domain name occupies a line.Figure-17 Exceptional domain names
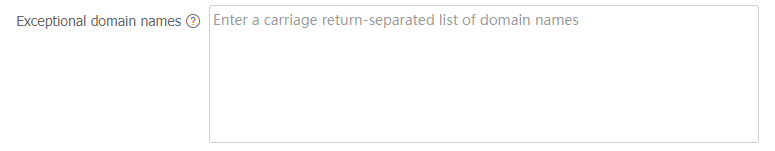
Click
Apply .
Intelligences from the threat management platform
Introduction
The device supports receiving intelligences from the threat management platform (Threat Discovery and Security Operations Platform), including IP reputation, URL reputation, domain reputation, and MD5 reputation. The intelligences supplement the locally loaded reputation and antivirus signature libraries, improving security for internal network users.
vSystem support information
Support of non-default vSystems for this feature depends on the device model. This feature is available on the Web interface only if it is supported.
Restrictions and guidelines
To ensure successful receiving of IP reputation and MD5 reputation from the threat management platform, enable NETCONF over SOAP on the device by executing the
netconf soap http enable andnetconf soap https enable commands in system view from the CLI of the device.To ensure successful receiving of URL reputation and domain reputation from the threat management platform, configure the domain name of the platform server by executing the
cloud-management server domain command in system view from the CLI of the device. You must also configure the device to carry its serial number in fast output logs by executing thecustomlog with-sn command in system view.To use the threat intelligences correctly, configure IP reputation, URL reputation, domain reputation, and anti-virus features first on the device.