Policy-based NAT
This help contains the following topics:
Introduction
Network Address Translation (NAT) translates an IP address in the IP packet header to another IP address. Typically, NAT is configured on gateways to enable private hosts to access external networks and external hosts to access private network resources such as a Web server.
Policy-based NAT contains a set of NAT rules to identify and translate matching packets. The packet match criteria include source security zone, destination security zone, source IP address, destination IP address, and service.
Policy-based NAT is applicable to the scenario where the external interface is not fixed. You do not need to change relevant configurations if the external interface changes, which reduces maintenance costs.
Rule types
Policy-based NAT supports the following types of rules, which are applicable to different scenarios:
NAT44 rule —Used for NAT translation between IPv4 networks.NAT64 rule —Used for NAT translation between IPv4 networks and IPv6 networks.NAT66 rule —Used for NAT translation between IPv6 networks.
Translation modes
Policy-based NAT supports the following translation modes:
Source address translation —Translates the source IP address and source port of packets. Source address translation can hide the IP addresses of internal hosts to external devices. The NO-PAT and PAT modes are supported.For more information about NO-PAT and PAT, see "IPv4 (NAT44)." Destination address translation —Translates the destination IP address and destination port of packets. Destination address translation is commonly used for internal servers to access external users. This translation mode supports many-to-one NAT and many-to-many NAT modes.Many-to-one NAT —Translates different destination IP addresses and destination ports of the matching packets to the same IP address and port. You only need to configure only one IP address and one port for destination address translation.Many-to-many NAT —Translates destination IP addresses and destination ports based on the numbers of destination IP addresses and services (ports) in the original packets and the numbers of destination IP addresses and destination ports after destination address translation. Make sure the number of public addresses multiplied by the number of public ports is equal to the number of private addresses multiplied by the number of private ports. In this translation mode, you can configure multiple destination IP addresses and one destination port or one destination IP address and multiple destination ports.Table-1 describes the address translation configuration available for many-to-many NAT in different scenarios.
Table-1 Many-to-many NAT configuration guide
Application scenario
Item
Public network (destination IP addresses and services in the original packets)
Private network (IP addresses and ports after destination address translation)
External users can use one public address to access internal servers
One public address
One private address
External users can use one public address and one public port to access internal servers
One public address and one public port number
One private address and one private port number
External users can use one public address and multiple different public port numbers to access internal servers
One public address and
N public port numbersN private addresses and one private port numberOne public address and
N public port numbersOne private address and
N private port numbersExternal users can use multiple different public addresses to access internal servers
N public addressesN private addressesExternal users can use multiple different public addresses and one public port number to access internal servers
N public addresses and one public port numberOne private address and
N private port numbersN public addresses and one public port numberN private addresses and one private port number
Source and d estination address translation —Translates the source IP address, source port, destination IP address, and destination port of packets. Source address translation supports NO-PAT and PAT modes. Destination address translation supports many-to-one NAT and many-to-many NAT modes.
Hot backup for NAT
If only one NAT device is deployed in the internal network, internal users cannot access the external network when the NAT device fails. To avoid this situation, configure a two-node hot backup system to provide redundant NAT services. The two devices in the system synchronize session entries, session relation entries, NAT port block entries, and NAT configurations through the hot backup channel. When one device fails, the other device takes over. For more information about configuring a hot backup system, see "Hot backup".
Typically, the master device in the VRRP group processes NAT services in the hot backup system. On an active/standby hot backup system, some translation rules for static, source, or destination address translation issue the translated public IP addresses or the public IP addresses of internal servers to the address management module. Then, both the active and standby devices advertise the mappings between the public IP addresses and MAC addresses of their own physical interfaces to all nodes in the same LAN or local link. As a result, the upstream Layer 3 device directly connected to the hot backup system might incorrectly send downlink packets to a VRRP backup device, causing service anomalies. This issue might also occur on a dual-active hot backup system.
To avoid such an issue, bind address translation methods to the VRRP group in use. This ensures that only the VRRP master device responds to the ARP requests or NS requests for the translated public IP addresses or the public IP addresses of internal servers. The MAC addresses in the responses are the virtual MAC address of the VRRP group.
vSystem support information
Support of non-default vSystems for this feature depends on the device model. This feature is available on the Web interface only if it is supported.
Restrictions and guidelines
Policy NAT has higher priority than interface NAT for the traffic that matches both of them.
By default, the NAT rules in policy-based NAT are sorted in descending order of their configuration order. You can rearrange NAT rules to change their priorities. A rule has a higher priority than rules listed after it.
If you select
Automatically generate security policy when creating or copying a NAT rule, the device generates a security policy based on the original packet information you configured. If you modify the original packet information, you must clickRefresh to reflect the modification in the generated security policy.A NAT address group cannot be used by both PAT and NO-PAT modes.
If a packet matches both a policy-based NAT rule and an interface NAT rule, the packet is translated as follows:
For source and destination address translation method:
If the translation methods of the policy-based NAT rule and the interface NAT rule are the same, the device translates the packet by using the policy-based NAT rule.
If the translation methods of the policy-based NAT rule and the interface NAT rule are different, the device translates the packet by using the two rules.
If the translation method of the policy-based NAT rule is bidirectional, the device translates the packet by using the policy-based NAT rule, and the interface NAT rule does not take effect.
When you add address ranges to a NAT address group, make sure address ranges do not overlap.
The address object group used by a NAT rule cannot contain a host name.
Referencing an address object group that contains an object group or wildcard mask might affect configuration performance and traffic matching performance. As a best practice to ensure network stability and smoothness, do not use an object group or wildcard mask to add objects.
The number of IP addresses in all NAT address groups cannot be smaller than the number of security engines. Otherwise, some security engines cannot obtain NAT address resources.
Configure policy-based NAT
NAT can be performed in the inbound or outbound direction.
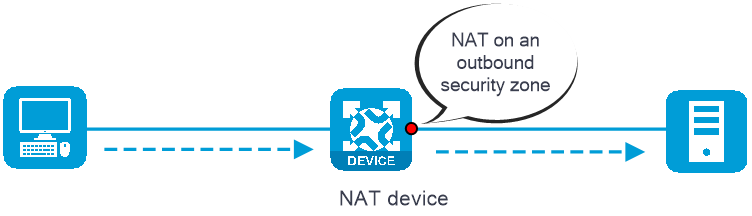
Inbound NAT —Performs address translation for packets received in a security zone, as shown in Figure-1.Outbound NAT —Performs address translation for packets sent out of a security zone, as shown in Figure-2.
Figure-1 NAT on an inbound security zone
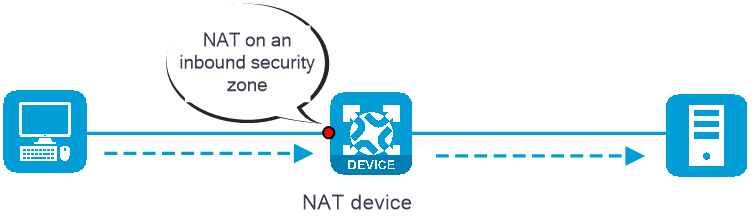
Figure-2 NAT on an outbound security zone
Configuration flowchart
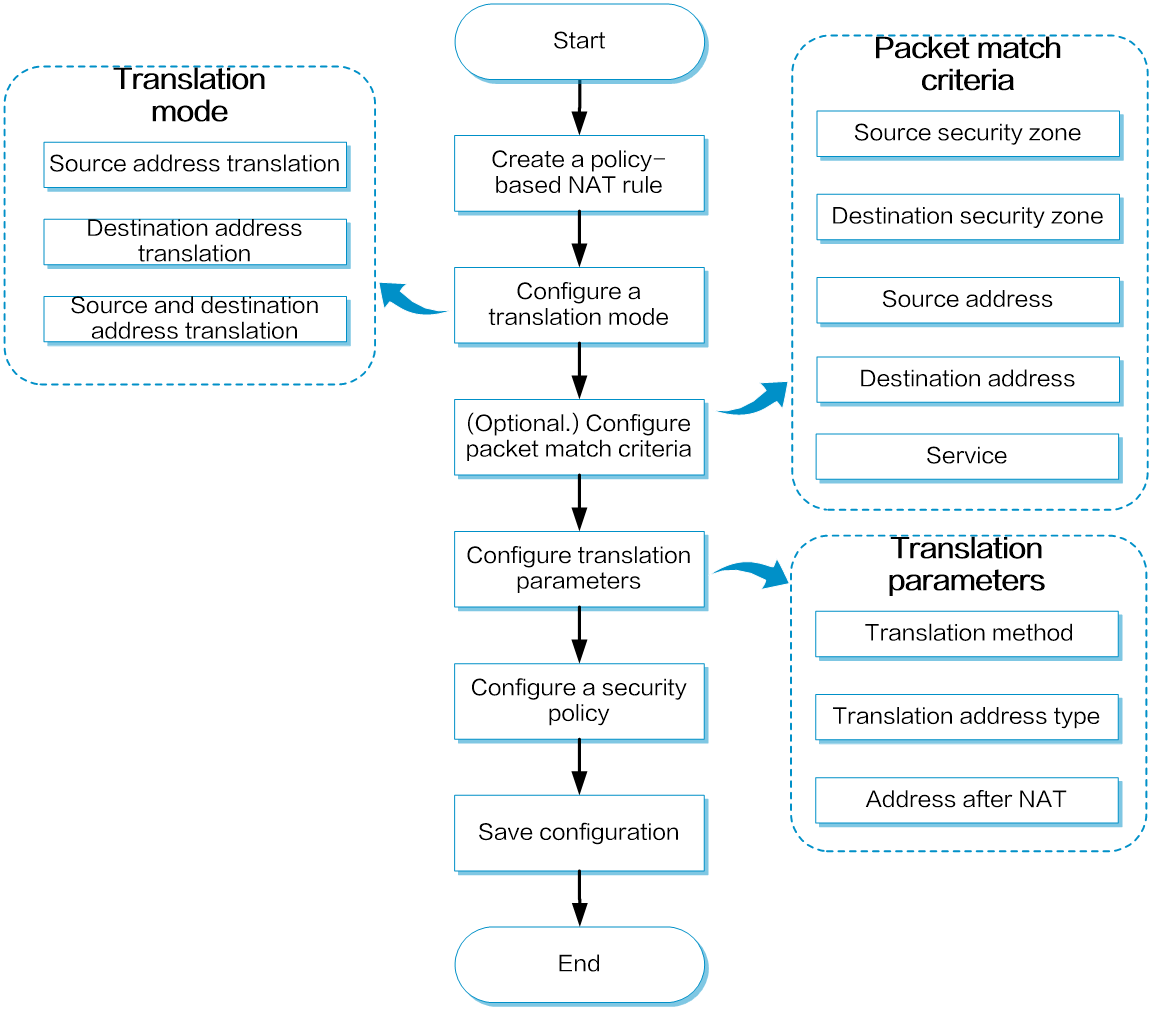
Policy-based NAT supports packet match criteria including security zone, address object group, and service object group. Policy-based NAT supports source address translation, destination address translation, and source and destination address translation. Figure-3 shows the configuration flowchart.
Figure-3 Policy-based NAT configuration flowchart
Prerequisites
Complete the following tasks before you configure this feature:
Assign IP addresses to interfaces on the
Network >Interface Configuration >Interfaces page.Configure routes on the
Network >Routing page. Make sure the routes are available.Create security zones on the
Network >Security Zones page.Add interfaces to security zones. You can add interfaces to a security zone on the
Security Zones page or select a security zone for an interface on theInterfaces page.Configure security policies to permit the target traffic on the
Policies >Security Policies page.
Configure a policy-based NAT44 rule
Procedure
(Optional.) Create a security zone. (Details not shown.)
(Optional.) Create an address object group. For more information, see "Object groups."
(Optional.) Create a service object group. (Details not shown.)
(Optional.) Create a NAT address group.
Click the
Objects tab.In the navigation pane, select
Object Groups >NAT Address Groups . For more information, see "Object groups."Click
Create .Create a NAT address group.
Click
OK .
Create a policy-based NAT44 rule.
Click the
Policies tab.In the navigation pane, select
Policy -based NAT .Select a translation mode as required.
Figure-4 Selecting a translation mode
Table-2 Translation mode description
Translation mode
Description
Create SNAT
Translates the source address information of packets.
Create DNAT
Translates the destination address information of packets.
Create SNAT+DNAT
Translates both the source and destination address information of packets.
Click the
NAT44 tab.Figure-5 Configuring a policy-based NAT44 rule
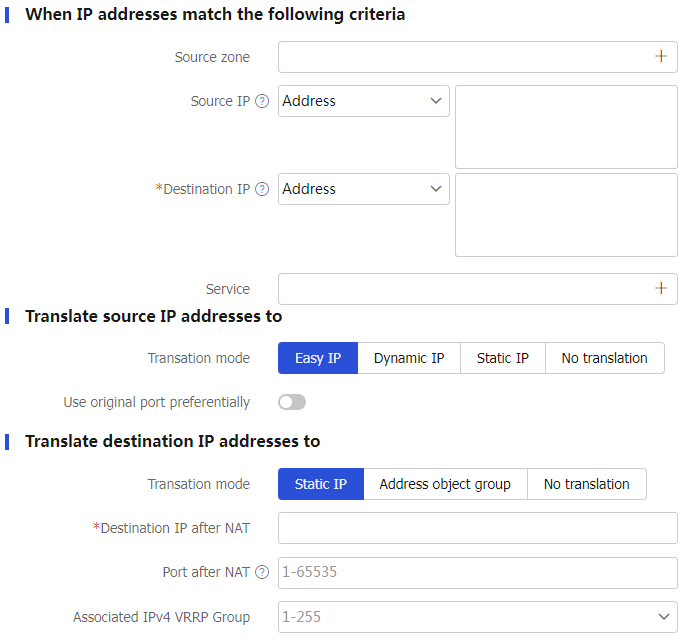
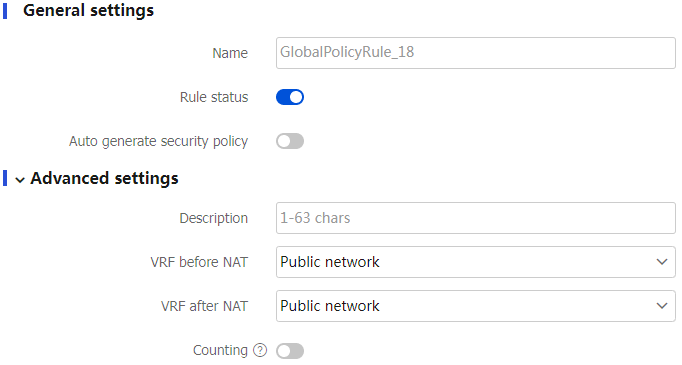
Table-3 Configuration items for policy-based NAT44 rules
Item
Description
When IP addresses match the following criteria
Source zone
Select source security zones for packet match.
Destination zone
Select destination security zones for packet match. This field is displayed only when you select the
Create SNAT translation mode.Source IP
Select a source IP address, IP subnet, or address object group for packet match.
Destination IP
Select a destination IP address, IP subnet, or address object group for packet match.
If the translation mode is destination address translation or source and destination address translation, this field must be specified.
Service
Select a service object group for packet match.
Translate source IP addresses to
Translation mode
Select a source address translation method:
Easy IP —Uses the outgoing interface IP address of the device for source address translation.Dynamic IP —Uses the PAT or NO-PAT method to perform address translation.Static IP —Translates the source IP addresses of packets to a fixed IP address.No translation —This rule and rules with lower priority than this rule are not used for source address translation.
Address
Select a NAT address type for source address translation:
Address object group —Uses IP addresses in an address object group for source address translation.NAT address group —Uses IP addresses in a NAT address group for source address translation.IP address —Uses a fixed IP address for source address translation.Network address —Uses IP addresses on a network for source address translation.
Source IP after NAT
Select a NAT address for source address translation.
Associated IPv4 VRRP Group
After you configure this feature, the master device in the IPv4 source VRRP group uses the virtual IP address and virtual MAC address to reply packets. On a stateful failover network, you must configure this feature. Support for this feature varies by device.
Allow reverse NAT
Enable reverse address translation. Reverse address translation uses existing NO-PAT entries to translate the destination address for connections actively initiated from the external network to the internal network.
This option is available only when the translation mode is set to
Dynamic IP .Port translation
If you enable port translation, the device uses the PAT method to translate the source IP addresses and source ports of packets. If you disable port translation, the device uses the NO-PAT method to translate only the source IP addresses of packets.
User original port preferentially
Preferentially use the original port for PAT. When the original port has been allocated, another port is used.
This option is available only when the translation mode is set to
Dynamic IP or Easy IP .Translate destination IP addresses to
Translation mode
Select a destination address translation method:
Static IP —Translates the destination IP addresses of packets to a fixed IP address.Address object group —Translates the destination IP addresses of packets to addresses in an address object group.No translation —This rule and rules with lower priority than this rule are not used for source address translation.
Destination IP after NAT
Set the destination IP address after translation.
Port after NAT
Set the destination port after translation.
Associated IPv4 VRRP Group
After you configure this feature, the master device in the IPv4 destination VRRP group uses the virtual IP address and virtual MAC address to reply packets. On a stateful failover network, you must configure this feature. Support for this feature varies by device.
General settings
Name
Name of the NAT44 rule, which supports Chinese characters.
Rule status
Whether to enable the NAT44 rule.
Auto generate security policy
After you enable this feature, the device generates a security policy based on the original packet information configured above.
Advanced settings
Description
Remarks for the NAT44 rule.
VRF before NAT
VPN instance to which packets belong before address translation.
VRF after NAT
VPN instance to which packets belong after address translation.
Counting
Enable the counting of times that the NAT44 rule is matched.
Click
Apply .
Configure a policy-based NAT66 rule
Procedure
(Optional.) Create a security zone. (Details not shown.)
(Optional.) Create an address object group. For more information, see "Object groups."
(Optional.) Create a service object group. For more information, see "Object groups."
Create a policy-based NAT66 rule.
Click the
Policies tab.In the navigation pane, select
Policy -based NAT .Select a translation mode as required.
Figure-6 Selecting a translation mode
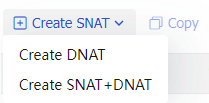
Table-4 Translation mode description
Translation mode
Description
Create SNAT
Translates the source address information of packets.
Create DNAT
Translates the destination address information of packets.
Create SNAT+DNAT
Translates both the source and destination address information of packets.
Click the
NAT 66 tab.Figure-7 Configuring a policy-based NAT66 rule
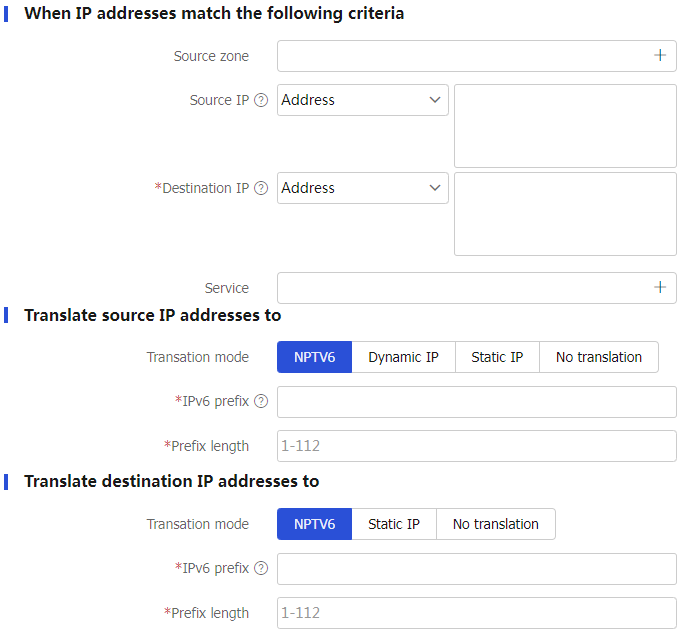
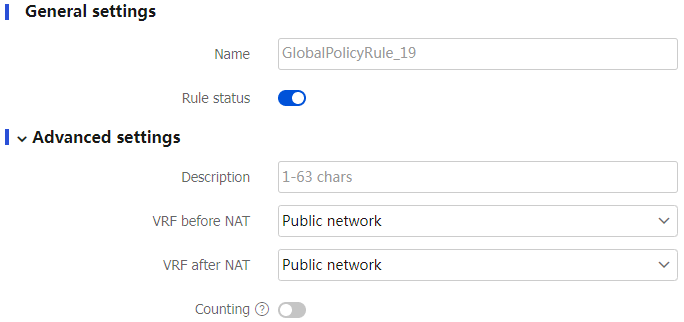
Table-5 Configuration items for policy-based NAT66 rules
Item
Description
When IP addresses match the following criteria
Source zone
Select source security zones for packet match.
Destination zone
Select destination security zones for packet match. This field is displayed only when you select the
Create SNAT translation mode.Source IP
Select a source IP address, IP subnet, or address object group for packet match.
Destination IP
Select a destination IP address, IP subnet, or address object group for packet match.
If the translation mode is destination address translation or source and destination address translation, this field must be specified.
Service
Select a service object group for packet match.
Translate source IP addresses to
Translation mode
Select a source address translation method:
NPTV6 —Uses the NPTV6 method to translate the prefixes in the source IPv6 addresses of packets to the configured prefix. To use this method, you must configure packet match rules for original packets.Dynamic IP —Uses the PAT or NO-PAT method to perform address translation.Static IP —Translates the source IP addresses of packets to a fixed IP addressNo translation —This rule and rules with lower priority than this rule are not used for source address translation.
Source IP after NAT
Select a NAT address for source address translation.
Port translation
If you enable port translation, the device uses the PAT method to translate the source IP addresses and source ports of packets. If you disable port translation, the device uses the NO-PAT method to translate only the source IP addresses of packets.
Associated IPv6 VRRP Group
After you configure this feature, the master device in the IPv6 source VRRP group uses the virtual IP address and virtual MAC address to reply packets. On a stateful failover network, you must configure this feature. Support for this feature varies by device.
IPv6 prefix
Configure the IPv6 address prefix for the prefix translation method.
This option is available only when the prefix translation method is
NPTV6 .Prefix length
Configure the IPv6 prefix length.
This option is available only when the prefix translation method is
NPTV6 .Translate destination IP addresses to
Translation method
Select a destination address translation method:
NPTV6 —Uses the NPTV6 method to translate the prefixes in the destination IPv6 addresses of packets to the configured prefix.Static IP —Translates the destination IP addresses and destination ports of packets to a fixed IP address and a fixed port, respectively.No translation —This rule and rules with lower priority than this rule are not used for destination address translation.
Destination IP after NAT
Set the destination IP address after translation.
Port after NAT
Set the destination port after translation.
IPv6 prefix
Configure the IPv6 address prefix for the prefix translation method.
This option is available only when the translation method is
NPTV6 .Prefix length
Configure the IPv6 prefix length.
This option is available only when the translation method is
NPTV6 .General settings
Name
Name of the NAT66 rule, which supports Chinese characters.
Rule status
Whether to enable the NAT66 rule.
Advanced settings
Description
Remarks for the NAT66 rule.
VRF before NAT
VPN instance to which packets belong before address translation.
VRF after NAT
VPN instance to which packets belong after address translation.
Counting
Enable the counting of times that the NAT66 rule is matched.
Click
Apply .
Configure a policy-based NAT64 rule
Procedure
(Optional.) Create a security zone. (Details not shown.)
(Optional.) Create an address object group. For more information, see "Object groups."
(Optional.) Create a service object group. For more information, see "Object groups."
Create a policy-based NAT64 rule.
Click the
Policies tab.In the navigation pane, select
Policy -based NAT .Click the chevron icon next to
Create SNAT , and then selectCreate SNAT+DNAT .Figure-8 Selecting Create SNAT+DNAT
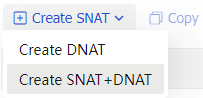
Click the
NAT64 tab.Figure-9 Configuring a policy-based NAT64 rule
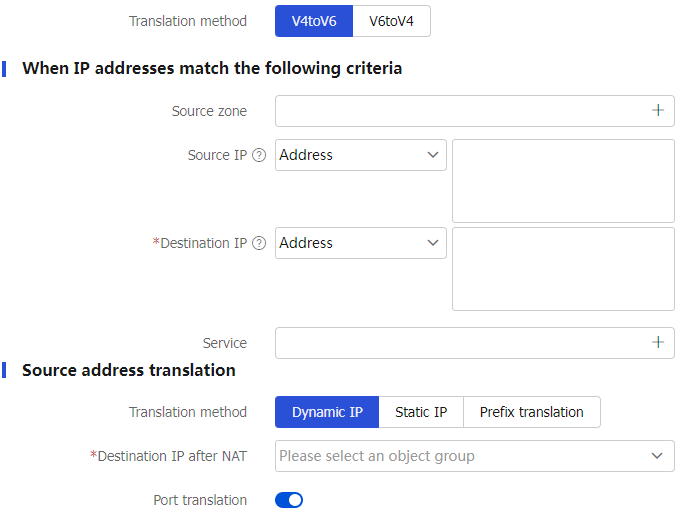
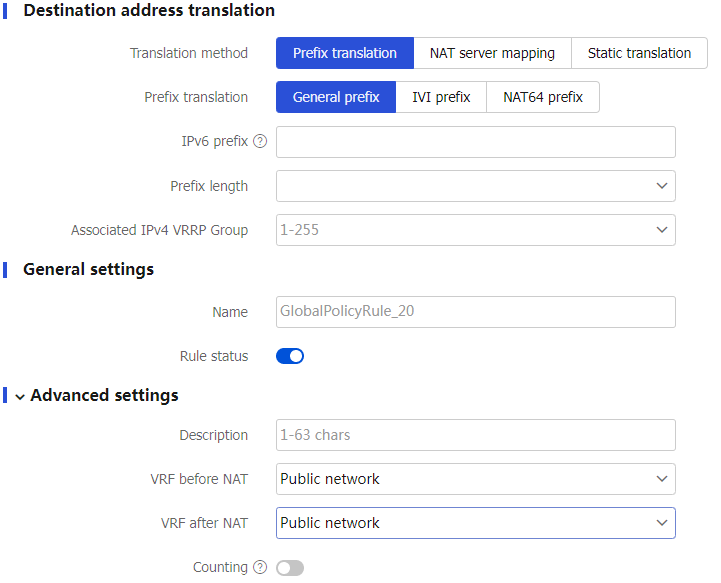
Table-6 Configuration items for policy-based NAT64 rules
Item
Description
Translation method
V4toV6 Translates the source IP address and destination IP address of packets when an IPv4 host first initiates a connection to the IPv6 network.
V6toV4 Translates the source IP address and destination IP address of packets when an IPv6 host first initiates a connection to the IPv4 network.
When IP addresses match the following criteria
Source zone
Select source security zones for packet match.
Source IP
Select a source IP address, IP subnet, or address object group for packet match.
Destination IP
Select a destination IP address, IP subnet, or address object group for packet match.
Service
Select a service object group for packet match.
Source address translation
Translation method
Select a source address translation method:
Dynamic IP —Uses the PAT or NO-PAT method to perform address translation.Static IP —Translates the source IP addresses of packets to a fixed IP address.Prefix translation —Uses IPv6 prefixes to translate the source IP addresses of packets.
Source IP after NAT
Select a NAT address for source address translation.
This option is available only when the translation method is
Dynamic IP orS tatic IP .Port translation
If you enable port translation, the device uses the PAT method to translate the source IP addresses and source ports of packets. If you disable port translation, the device uses the NO-PAT method to translate only the source IP addresses of packets.
Associated IPv4 VRRP Group
After you configure this feature, the master device in the IPv4 source VRRP group uses the virtual IP address and virtual MAC address to reply packets. On a stateful failover network, you must configure this feature. Support for this feature varies by device.
Associated IPv6 VRRP Group
After you configure this feature, the master device in the IPv6 source VRRP group uses the virtual IP address and virtual MAC address to reply packets. On a stateful failover network, you must configure this feature. Support for this feature varies by device.
Prefix translation
Select a prefix translation type:
General prefix —Uses the general prefix for source address translation.IVI prefix —Uses the IVI prefix for source address translation.NAT64 prefix —Uses the NAT64 prefix for source address translation.
This option is available only when the translation method is
Prefix translation .IPv6 prefix
Configure the IPv6 address prefix for the prefix translation method.
This option is available only when the prefix translation type is
General prefix orNAT64 prefix .Prefix length
Configure the IPv6 prefix length.
This option is available only when the prefix translation type is
General prefix orNAT64 prefix .Destination address translation
Translation method
Select a destination address translation method:
Prefix translation —Uses the IPv6 prefixes for destination address translation.NAT s erver mapping —Translates the destination IP addresses and destination port numbers of packets to a fixed destination IP address and destination port number.Static translation —Translates the destination IP addresses of packets to a fixed IP address.
Prefix translation
Select a prefix translation type:
General prefix —Uses the general prefix for source address translation.IVI prefix —Uses the IVI prefix for source address translation.NAT64 prefix —Uses the NAT64 prefix for source address translation.
This option is available only when the translation method is
Prefix translation .IPv6 prefix
Configure the IPv6 address prefix for the prefix translation method.
This option is available only when the prefix translation type is
General prefix orIVI prefix .Prefix length
Configure the IPv6 prefix length.
This option is available only when the prefix translation type is
General prefix .Associated IPv4 VRRP Group
After you configure this feature, the master device in the IPv4 destination VRRP group uses the virtual IP address and virtual MAC address to reply packets. On a stateful failover network, you must configure this feature. Support for this feature varies by device.
Associated IPv6 VRRP Group
After you configure this feature, the master device in the IPv6 destination VRRP group uses the virtual IP address and virtual MAC address to reply packets. On a stateful failover network, you must configure this feature. Support for this feature varies by device.
Destination IP after NAT
Set the destination IP address after translation.
Port after NAT
Set the destination port after translation.
This option is available only when the translation method is
NAT server mapping .General settings
Name
Name of the NAT64 rule, which supports Chinese characters.
Rule status
Whether to enable the NAT64 rule.
Advanced settings
Description
Remarks for the NAT64 rule.
VRF before NAT
VPN instance to which packets belong before address translation.
VRF after NAT
VPN instance to which packets belong after address translation.
Counting
Enable the counting of times that the NAT64 rule is matched.
Click
Apply .