Packet trace
This help contains the following topics:
Introduction
The packet trace feature traces packets processed by security services, and provides detailed information about the packets to help you troubleshoot network failures. The security services include attack protection, uRPF, session management, and concurrent connection limit.
Application scenarios
Packet trace applies to scenarios where a large number of security services are deployed and it is difficult to locate network failures rapidly and accurately.
Packet trace modes
To meet troubleshooting requirements in various situations, the packet trace feature provides the following packet trace modes:
Tracing real traffic—Traces real traffic on the device in a live network. Use this mode for troubleshooting in a live network.
Tracing imported packets—Imports captured packets from a .cap or .pcap file and analyzes the packets. Use this mode if packets required for troubleshooting have been captured. Using this mode, you can help troubleshoot failures on other networks.
Tracing constructed packets—Uses settings configured by the administrator to construct a packet and verify packet processing results for configured security services. When you complete device configuration, use this mode to create a packet to verify the expected packet processing result.
vSystem support information
Support of non-default vSystems for this feature depends on the device model. This feature is available on the Web interface only if it is supported.
Restrictions and guidelines
The system generates .cap files only if you select Capture diagnose packets before clicking Diagnose.
You cannot export the same .cap files repeatedly. Once being exported, .cap files are deleted from the device.
Importing captured packets from a .cap or .pcap file imports only packets of the first 10 data flows, 10 packets each data flow. The packet trace feature traces only imported packets that are complete. It does not trace packets that are incomplete.
When an interface enabled with the last hop holding feature forwards packets successfully, the device cannot read the next hop information for the packets. The next hop address displays 255.255.255.255 for an IPv4 flow or :: for an IPv6 flow.
Configure packet trace
Prerequisites
Complete the following tasks before you configure this feature:
Assign IP addresses to interfaces on the Network > Interface Configuration > Interfaces page.
Configure routes on the Network > Routing page. Make sure the routes are available.
Create security zones on the Network > Security Zones page.
Add interfaces to security zones. You can add interfaces to a security zone on the Security Zones page or select a security zone for an interface on the Interfaces page.
Configure security policies to permit the target traffic on the Policies > Security Policies page.
Procedure
Select System > Diagnosis Center > Packet Trace.
Configure packet trace parameters as shown in Table-1.
Figure-1 Configuring packet trace parameters
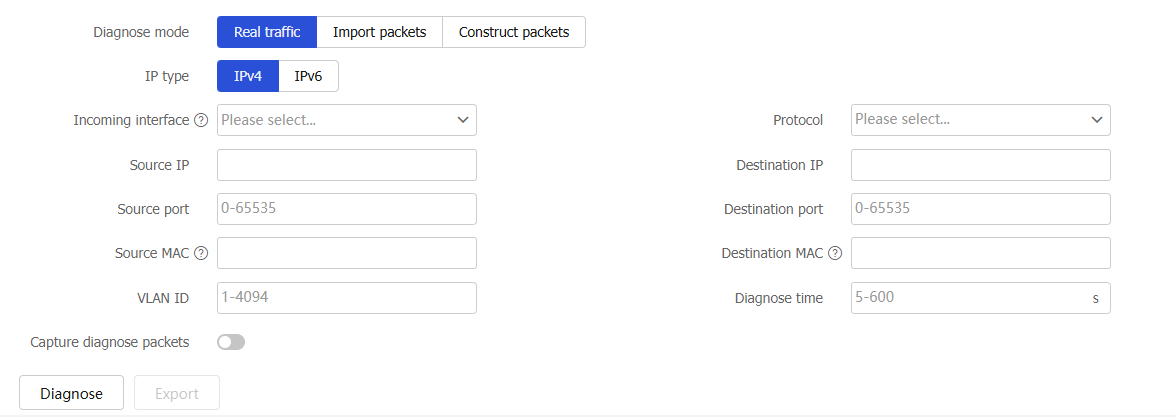
Table-1 Packet trace configuration items
Item
Description
Diagnose mode
Select a packet trace mode. Options:
Real traffic.
Import packets.
Construct packets.
IP type
Select an IP address type. Options:
IPv4—Traces IPv4 packets.
IPv6—Traces IPv6 packets.
Incoming interface
Select an ingress interface for traced packets.
Protocol
Select a protocol for traced packets.
Source IP
Specify a source IP address for traced packets.
Source port
Specify a source port for traced packets.
Destination IP
Specify a destination IP address for traced packets.
Destination port
Specify a destination port for traced packets.
Source MAC
Specify a source MAC address for traced packets.
Destination MAC
Specify a destination MAC address for traced packets.
VLAN ID
Specify a VLAN ID for traced packets
Diagnose time
Specify packet trace duration. When the specified time expires, packet trace stops. This setting is supported only in real traffic mode.
Capture diagnose packets
Select whether to capture traced packets and save the packets to .cap files. To capture and save the packets, select this option. To export the .cap files, click Export, select Captured diagnostic packets, and then click OK.
Click Diagnose.
The packet trace output shows the packet processing procedures of security service modules. If a service module processes packets correctly, the system displays  . If a service module drops packets, the system displays
. If a service module drops packets, the system displays  and the packet loss causes.
and the packet loss causes.