L2TP
This help contains the following topics:
Introduction
The Layer 2 Tunneling Protocol (L2TP) is a Virtual Private Dialup Network (VPDN) tunneling protocol. L2TP sets up point-to-point tunnels across a public network (for example, the Internet) and transmits encapsulated PPP frames (L2TP packets) over the tunnels. With L2TP, remote users can access the private networks through L2TP tunnels after connecting to a public network by using PPP.
Typical L2TP network components
A typical L2TP network has the following components:
Remote system —A remote system is usually a remote user's host or a remote branch's device that needs to access the private network.LAC —An L2TP access concentrator (LAC) is both PPP and L2TP capable. It is usually a network access server (NAS) located at a local ISP, which provides access services mainly for PPP users.An LAC is an endpoint of an L2TP tunnel and lies between an LNS and a remote system. It encapsulates packets received from a remote system by using L2TP and then sends the encapsulated packets to the LNS. It decapsulates packets received from the LNS and then sends the decapsulated packets to the intended remote system.
LNS —An L2TP network server (LNS) is both PPP and L2TP capable. It is usually an edge device on an enterprise network.An LNS is the other endpoint of an L2TP tunnel. It is the logical termination point of a PPP session tunneled by the LAC. L2TP extends the termination point of a PPP session from a NAS to an LNS by establishing a tunnel.
L2TP tunneling modes
L2TP tunneling modes include NAS-initiated, client-initiated, and LAC-auto-initiated.
NAS-initiated tunneling mode
As shown in
Figure-1 NAS-initiated tunneling mode
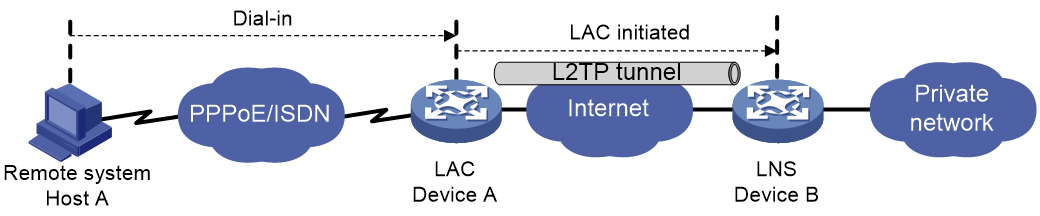
A NAS-initiated tunnel has the following characteristics:
The remote system only needs to support PPP, and it does not need to support L2TP.
Authentication and accounting of the remote system can be implemented on the LAC or LNS.
Client-initiated tunneling mode
As shown in Figure-2, a remote system running L2TP (LAC client) has a public IP address to communicate with the LNS through the Internet. The LAC client can directly initiate a tunneling request to the LNS without any dedicated LAC devices.
Figure-2 Client-initiated tunneling mode
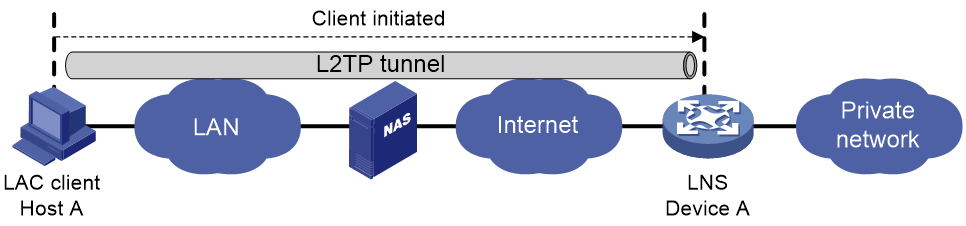
A client-initiated tunnel has the following characteristics:
A client-initiated tunnel has higher security because it is established between a remote system and the LNS.
The remote system must support L2TP and be able to communicate with the LNS. This causes poor expandability.
LAC-auto-initiated tunneling mode
In NAS-initiated mode, a remote system must successfully dial in to the LAC through PPPoE or ISDN.
In LAC-auto-initiated mode, you can configure tunnel settings on the LAC to trigger the LAC to initiate a tunneling request to the LNS. When a remote system accesses the private network, the LAC forwards data through the L2TP tunnel.
Figure-3 LAC-auto-initiated tunneling mode

An LAC-auto-initiated tunnel has the following characteristics:
The connection between a remote system and the LAC is not confined to a dial-up connection and can be any IP-based connection.
You do not need to trigger L2TP tunnel establishment by dialup on the remote system.
An L2TP session is established immediately after an L2TP tunnel is established. Then, the LAC and LNS, acting as the PPPoE client and PPPoE server, respectively, perform PPP negotiation.
An L2TP tunnel can carry only one L2TP session.
The LNS assigns a private IP address to the LAC instead of to the remote system.
vSystem support information
Support of non-default vSystems for this feature depends on the device model. This feature is available on the Web interface only if it is supported.
Configuration guidelines
Prerequisites
Complete the following tasks before you configure this feature:
Assign IP addresses to interfaces on the
Network >Interface Configuration >Interfaces page.Configure routes on the
Network >Routing page. Make sure the routes are available.Create security zones on the
Network >Security Zones page.Add interfaces to security zones. You can add interfaces to a security zone on the
Security Zones page or select a security zone for an interface on theInterfaces page.Configure security policies to permit the target traffic on the
Policies >Security Policies page.
Configure basic settings on an LAC
Click the
Network tab.In the navigation pane, select
VPN >L2TP >L2TP .Click
Enable L2TP .Figure-4 Enabling L2TP
On the
L2TP page, clickCreate . On theCreate L2TP Tunnel page opens, selectLAC for theGroup type field.The following table shows the parameter settings.
Figure-5 Selecting LAC for the group type
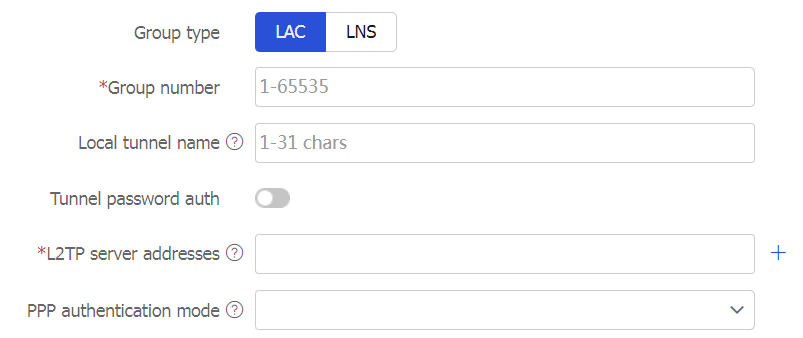
Table-1 Basic configuration items for an LAC group
Item
Description
Group type
L2TP group types include LAC and LNS. An LAC is an endpoint of an L2TP tunnel, and is located between the LNS and remote system. An LAC is used to transmit packets between the LNS and remote system. LAC L2TP groups and LNS L2TP groups can coexist.
LAC —This device can initiate tunneling requests to the LNS as the LAC of an L2TP tunnel.LNS —This device can accept tunneling requests from the LAC as the LNS of an L2TP tunnel.
Group number
Number of an L2TP group.
Local tunnel name
The local tunnel name is used during tunnel negotiation between LAC and LNS. It identifies the local tunnel for the peer end to recognize. If you do not configure a local tunnel name, the device name is used as the local tunnel name by default.
Tunnel password auth
L2TP tunnel authentication is used to prevent the local device from setting up an L2TP tunnel to an invalid device and improves the network security.
Tunnel password
If you need to modify the tunnel authentication password, do that before the tunnel starts negotiation. If you do that after the tunnel starts negotiation, the password modification does not take effect.
Confirm tunnel password
Enter the tunnel password again to confirm the password.
L2TP server addresses
Specify the LNS IP addresses. You can specify up to five addresses.
PPP authentication mode
When you select PAP or CHAP authentication, make sure the user information is consistent with that on the LNS side.
Username
Username for PAP or CHAP authentication.
Password
Password for PAP or CHAP authentication.
Click
OK .
(Optional.) Configure advanced settings on an LAC
Click the
Network tab.In the navigation pane, select
VPN >L2TP >L2TP .Click
Enable L2TP .Figure-6 Enabling L2TP
On the
L2TP page, clickCreate . On theCreate L2TP Tunnel page opens, access theAdvanced configuration area.The following table shows the parameter settings.
Figure-7 Advanced configuration for an LAC group
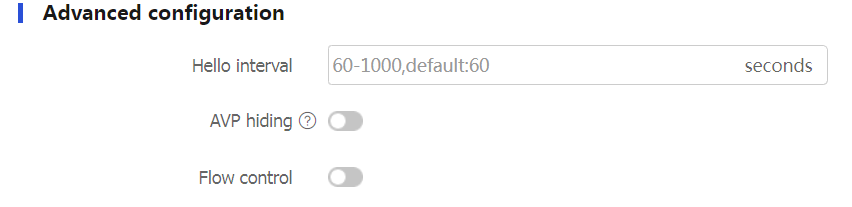
Table-2 Advanced configuration items for an LAC group
Parameter
Description
Hello interval
The device periodically sends Hello packets at the configured interval to prevent the L2TP tunnel and session between the LAC and LNS from being deleted after they time out.
AVP hiding
To prevent information such as user password from being intercepted, you can use this feature to transmit the AVP data in hidden mode. This feature takes effect only after the tunnel password authentication feature is enabled.
Flow control
L2TP session flow control adds sequence numbers to transmitted packets and uses them to reorder packets arriving out of order and to detect lost packets.
Click
OK .
Configure basic settings on an LNS
Click the
Network tab.In the navigation pane, select
VPN >L2TP >L2TP .Click
Enable L2TP .Figure-8 Enabling L2TP
On the
L2TP page, clickCreate . On theCreate L2TP Tunnel page opens, selectLNS for theGroup type field.The following table shows the parameter settings.
Figure-9 Creating an LNS group
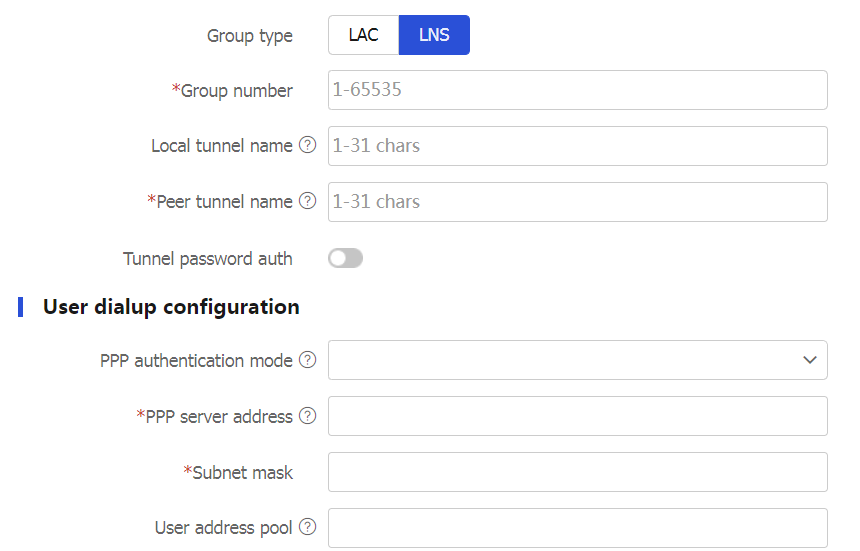
Table-3 Basic configuration items for an LNS group
Parameter
Description
Group type
L2TP group types include LAC and LNS. An LAC is an endpoint of an L2TP tunnel, and is located between the LNS and remote system. An LAC is used to transmit packets between the LNS and remote system. LAC L2TP groups and LNS L2TP groups can coexist.
LAC —This device can initiate tunneling requests to the LNS as the LAC of an L2TP tunnel.LNS —This device can accept tunneling requests from the LAC as the LNS of an L2TP tunnel.
Group number
Number of an L2TP group.
Local tunnel name
The local tunnel name is used during tunnel negotiation between LAC and LNS. It identifies the local tunnel for the peer end to recognize. If you do not configure a local tunnel name, the device name is used as the local tunnel name by default.
Peer tunnel name
When the L2TP group number is not 1, you must configure a peer tunnel name.
Tunnel password auth
L2TP tunnel authentication is used to prevent the local device from setting up an L2TP tunnel to an invalid device and improves the network security.
Tunnel password
If you need to modify the tunnel authentication password, do that before the tunnel starts negotiation. If you do that after the tunnel starts negotiation, the password modification does not take effect.
Confirm tunnel password
Enter the tunnel password again to confirm the password.
PPP authentication mode
When you select PAP or CHAP authentication, make sure the user information is consistent with that on the LNS side.
PPP server address
IP address of the virtual PPP interface used for negotiating PPP connections.
Subnet mask
Mask for the IP address of the virtual PPP interface.
User address pool
Address pool range that can be used by the users. You can specify a single address or an address range.
Click
OK .
(Optional.) Configure advanced settings on an LNS
Click the
Network tab.In the navigation pane, select
VPN >L2TP >L2TP .Click
Enable L2TP .Figure-10 Enabling L2TP
On the
L2TP page, clickCreate . On theCreate L2TP Tunnel page opens, access theAdvanced configuration area.The following table shows the parameter settings.
Figure-11 Advanced configuration for an LNS group
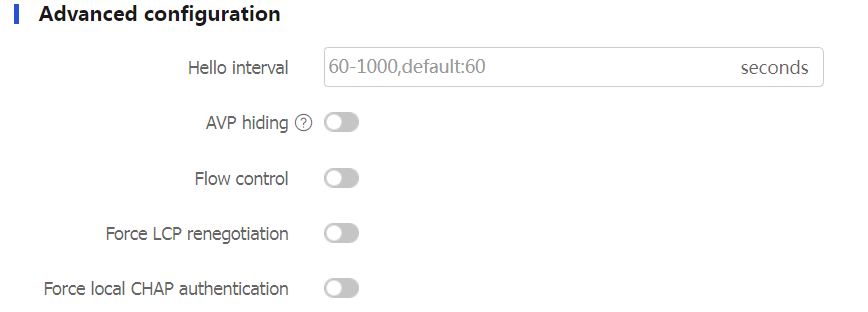
Table-4 Advanced configuration items for an LNS group
Parameter
Description
Hello interval
To check the connectivity of the tunnel between LAC and LNS, the LAC and LNS send Hello packets to each other periodically. The receiver will respond upon receiving a Hello packet. When the LAC or LNS does not receive a Hello response from the peer within the specified interval, it resends the Hello packet. If no response is received after five attempts, the L2TP tunnel is considered disconnected. The device periodically sends Hello packets at the configured interval to prevent the L2TP tunnel and session between the LAC and LNS from being deleted after they time out.
AVP hiding
To prevent information such as user password from being intercepted, you can use this feature to transmit the AVP data in hidden mode. This feature takes effect only after the tunnel password authentication feature is enabled.
Flow control
L2TP session flow control adds sequence numbers to transmitted packets and uses them to reorder packets arriving out of order and to detect lost packets.
Force LCP renegotiation
An LNS can be configured to authenticate a user that has passed authentication on the LAC to increase security. In this case, the user is authenticated once on the LAC and once on the LNS. An L2TP tunnel can be established only when both authentications succeed.
An LNS provides the following authentication methods in ascending order of priority:
Proxy authentication —The LNS uses the LAC as an authentication proxy. The LAC sends the LNS all user authentication information from users and the authentication method configured on the LAC itself. The LNS then checks the user validity according to the received information and the locally configured authentication method.Force local CHAP authentication —Also called mandatory CHAP authentication. The LNS uses CHAP authentication to reauthenticate users who have passed authentication on the LAC.Force LCP renegotiation —Also called mandatory LCP negotiation. The LNS ignores the LAC proxy authentication information and performs a new round of LCP negotiation with the user.
The LNS chooses an authentication method depending on your configuration.
If you configure both mandatory LCP renegotiation and mandatory local CHAP authentication, the LNS uses mandatory LCP renegotiation.
If you configure only mandatory CHAP authentication, the LNS performs CHAP authentication for users after proxy authentication succeeds.
If you configure neither mandatory LCP renegotiation nor mandatory local CHAP authentication, the LNS uses the LAC for proxy authentication.
Force local CHAP authentication
Click
OK .
View tunnel info
On the
Troubleshooting L2TP
Tunnel setup failure
Symptom
After you select
Solution
To resolve the problem, verify the following items to avoid tunnel setup failures:
The address of the LNS is configured correctly on the LAC.
The same PPP authentication mode is configured for the LAC and the LNS.
Usernames and passwords are correctly configured on the LAC and the LNS.
If the L2TP group number is not 1 on the LNS, the same tunnel name is configured for the LAC and the LNS.
Tunnel authentication succeeds.
You can enable tunnel authentication on both sides or either side. To ensure a successful tunnel establishment when tunnel authentication is enabled on both sides or either side, set the same non-null key on the LAC and the LNS.
Data transmission failure
Symptom
After you select
Solution
To resolve the problem:
Verify that the LAC has a route to the private network behind the LNS, and vice versa. If no route is available, configure a static route or a dynamic routing protocol.
Add the Virtual-Template interface on the LNS to a security zone, and permit the traffic from the security zone to security zone Local.
Increase the link bandwidth to enhance the link availability.
Internet backbone congestion and high packet loss ratio might cause data transmission failures. L2TP data transmission is based on UDP, which does not provide the packet error control feature. If the line is unstable, the LAC and LNS might be unable to ping each other.