Trusted API proxies
This help contains the following topics:
Introduction
Trusted API proxies are proxies for user traffic to access APIs. The device can direct received user requests to a trusted access controller for authentication and authorization. The trusted access controller returns the associated result to the device to control user access permissions.
vSystem support information
Support of non-default vSystems for this feature depends on the device model. This feature is available on the Web interface only if it is supported.
Configure a trusted API proxy
Prerequisites
Complete the following tasks before you configure this feature:
Procedure
Click the
LB tab.In the navigation pane, select
Zero Trust >Trusted API Proxies .Click
Create .Figure-1 Trusted API Proxies page
Configure the trusted API proxy parameters.
Figure-2 Configuring basic settings of the the trusted API proxy
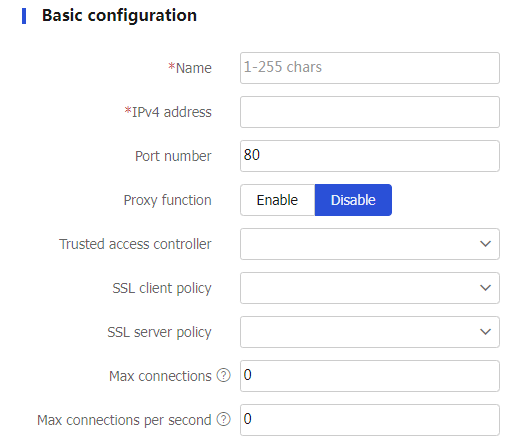
Figure-3 Configuring advanced settings of the the trusted API proxy
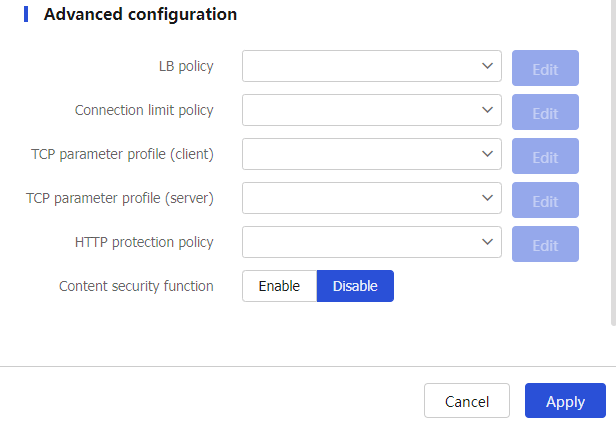
Table-1 Basic trusted API proxy configuration items
Item
Description
Name
Enter the name of the trusted API proxy, which is a case-insensitive string.
IPv4 address
Enter the IPv4 address used to provide trusted API proxy services.
Port number
Enter the port number for the trusted API proxy.
If the trusted API proxy uses an SSL policy, you must specify a non-default port number for it (a typical example is 443).
Proxy function
Enable or disable the trusted API proxy.
Trusted access controller
Specify a trusted access controller for the trusted API proxy. The device will direct traffic matching the trusted API proxy to the specified trusted access controller for authentication and authorization. Only the users passing the authentication and authorization are allowed to proceed with subsequent procedures.
You can select an existing trusted access controller or create a new trusted access controller.
For more information about the trusted access controller, see the description for the trusted access controller module.
SSL client policy
Specify the SSL client policy used by the trusted API proxy to encrypt traffic exchanged between the device (SSL client) and the SSL server.
You can select an existing SSL client policy or create a new SSL client policy.
SSL server policy
Specify the SSL server policy used by the trusted API proxy to encrypt traffic exchanged between the device (SSL server) and the SSL client.
You can select an existing SSL server policy or create a new SSL server policy.
Max connections
Set the maximum number of connections allowed by the trusted API proxy. 0 means not limited.
Max connections per second
Set the maximum number of connections allowed by the trusted API proxy per second. 0 means not limited.
Table-2 Advanced trusted API proxy configuration items
Item
Description
LB policy
Specify an LB policy for the trusted API proxy. Based on the LB policy rules, the device performs load balancing for packets matching the trusted API proxy according to their content.
You can select an existing LB policy or create a new LB policy.
A HTTP-type trusted API proxy can use only an LB policy of the generic or HTTP type.
Connection limit policy
Specify a connection limit policy for the trusted API proxy. The number of connections to the trusted API proxy will be limited by the specified policy.
You can select an existing connection limit policy or create a new connection limit policy.
TCP parameter profile (client)
Specify a TCP parameter profile for the trusted API proxy. The device uses the parameter profile settings to process matching traffic. The client-side TCP parameter profile applies only to TCP connections between the device and the client.
You can select an existing TCP parameter profile or create a new TCP parameter profile.
TCP parameter profile (server)
Specify a TCP parameter profile for the trusted API proxy. The device uses the parameter profile settings to process matching traffic. The server-side TCP parameter profile applies only to TCP connections between the device and the server.
You can select an existing TCP parameter profile or create a new TCP parameter profile.
HTTP protection policy
Specify an HTTP protection policy for the trusted API proxy. The device uses the protection policy settings to protect traffic matching the trusted API proxy.
You can select an existing HTTP protection policy or create a new HTTP protection policy.
Content security function
Enable or disable the content security function.
Content security-WAF profile
Specify a WAF profile for content security. The device performs web application protection for traffic matching the trusted API proxy.
For more information about WAF profiles, see WAF help.
Content security-IPS profile
Specify an IPS profile for content security. The device performs intrusion prevention for traffic matching the trusted API proxy.
For more information about IPS profiles, see IPS help.
Content security-Anti-virus profile
Specify an anti-virus profile for content security. The device performs anti-virus prevention for traffic matching the trusted API proxy.
For more information about anti-virus profiles, see anti-virus help.
Click
OK .The trusted API proxy will be displayed on the trusted API proxy page.