PKI
This help contains the following topics:
Introduction
Public Key Infrastructure (PKI) is an asymmetric key infrastructure to encrypt and decrypt data for securing network services.
PKI uses digital certificates to distribute and employ public keys, and provides network communication and e-commerce with security services such as user authentication, data confidentiality, and data integrity.
The PKI system of the device provides certificate management for SSL.
Digital certificate and certificate revocation list
Digital certificate
A digital certificate is an electronic document signed by a certificate authority (CA). A digital certificate binds a public key with the identity of its owner.
A digital certificate includes the following information:
Issuer name (name of the CA that issued the certificate).
Certificate subject (name of the individual or group to which the certificate is issued).
Identity information of the subject.
Subject's public key.
Signature of the CA.
Validity period.
This help covers the following types of certificates:
CA certificate —Certificate of a CA. Multiple CAs in a PKI system form a CA tree, with the root CA at the top. The root CA generates a self-signed certificate, and each lower level CA holds a CA certificate issued by the CA immediately above it. The chain of these certificates forms a chain of trust.Local certificate —Digital certificate issued by a CA to a local PKI entity, which contains the entity's public key.
Certificate revocation list
A certificate revocation list (CRL) is a list of serial numbers for certificates that have been revoked. A CRL is created and signed by the CA that originally issued the certificates.
The CA publishes CRLs periodically to revoke certificates. Revoked certificates should not be trusted.
The CA must revoke a certificate when any of the following conditions occurs:
The certificate subject information is changed.
The private key is compromised.
The association between the certificate subject and CA is changed. For example, when an employee terminates employment with an organization.
The device allows you to enable automatic update of CRLs and set the CRL update interval. The device automatically obtains the CRL from the CRL repository at the specified intervals.
PKI architecture
A PKI system consists of certificate subjects, CAs, RAs and a certificate/CRL repository.
Certificate subject
A certificate subject is an end user using PKI certificates. The certificate applicant can be an operator, an organization, a device, or a process running on a computer.
A certificate applicant uses a certificate subject to provide its identity information to a CA. A valid certificate subject must include one or more of following identity categories:
Certificate subject name, which further includes the common name, country code, state or province name, locality, organization name, and organization unit name. If you configure the certificate subject name, a common name is required.
FQDN of the certificate applicant. It identifies a PKI entity in the network.
IP address of the certificate applicant.
CA
A certification authority (CA) issues certificates, defines the certificate validity periods, and revokes certificates by publishing CRLs.
RA
The registration authority (RA) offloads the CA by processing certificate enrollment requests. The RA accepts certificate requests, verifies user identity, and determines whether to ask the CA to issue certificates.
The RA is optional in a PKI system. In cases when there is security concern over exposing the CA to direct network access, it is advisable to delegate some of the tasks to an RA. Then, the CA can concentrate on its primary tasks of signing certificates and CRLs.
Certificate/CRL repository
A certificate/CRL repository is certificate distribution point that stores certificates and CRLs, and distributes the certificates and CRLs to certificate applicants. It also provides the query function. A PKI repository can be a directory server using the LDAP or HTTP protocol, of which LDAP is commonly used.
PKI applications
The PKI technology can meet security requirements of online transactions. As an infrastructure, PKI has a wide range of applications. Here are some application examples.
Secure emails
PKI can address the email requirements for confidentiality, integrity, authentication, and non-repudiation. A common secure email protocol is Secure/Multipurpose Internet Mail Extensions (S/MIME), which is based on PKI and allows for transfer of encrypted mails with signature.
Web security
PKI can be used in the SSL handshake phase to verify the identities of the communicating parties by digital certificates.
Certificate management
The device manages certificates based on PKI domains and provides the PKI domain-based certificate service for applications such as SSL. A PKI domain contains enrollment information for a certificate subject, including the key pairs for certificate request and the certificate usage extensions.
Import certificates
You can import the CA certificate and local certificates related to a PKI domain from the CA.
Use this method when the CRL repository is not specified, the CA server does not support SCEP, or the CA server generates the key pair for the certificates.
Before you import certificates to a PKI domain, complete the following tasks:
Use FTP or TFTP to upload the certificate files to the storage media of the device.
To import a local certificate, a CA certificate chain must exist in the PKI domain, or be contained in the certificate to be imported. If the CA certificate chain is not available, import it before you import the local certificate.
When you import a local certificate, follow these restrictions and guidelines:
If the local certificate contains the CA certificate chain, you can import the CA certificate and the local certificate at the same time.
If the local certificate does not contain the CA certificate chain, but the CA certificate already exists in a PKI domain, you can directly import the certificate.
If the certificate file to be imported contains the root certificate, the system will prompt you to confirm the root certificate's fingerprint before the import. Contact the CA administrator to obtain the correct root certificate fingerprint.
If the local certificate to be imported contains a key pair, the system will prompt for the challenge password used for encrypting the private key. Contact the CA administrator to obtain the challenge password.
When you import a local certificate file that contains a key pair, the device saves the key pair in the PKI domain as follows.
If the PKI domain already contains a key pair that matches key pair in the certificate file, the device prompts whether you want to overwrite the existing key pair.
If the PKI domain does not have a key pair, the device creates a key pair according to the key algorithm and the purpose of the key pair in the certificate file. The PKI domain name will be used as the key pair name.
If the PKI domain contains a key pair that is different from the key pair in the certificate file, you must specify a different name to save the key pair in the certificate file.
You can import the CA certificate to a PKI domain when either of the following conditions is met:
The CA certificate to be imported is the root CA certificate or contains the certificate chain with the root certificate.
The CA certificate contains a certificate chain without the root certificate, but can form a complete certificate chain with an existing CA certificate on the device.
Export certificates
You can export the CA certificate and the local certificates in a PKI domain to certificate files. The exported certificate files can then be imported back to the device or other PKI applications.
Request certificates
Before you request a local certificate for a certificate subject in a PKI domain, make sure a CA certificate already exists in the PKI domain. The CA certificate will be used to verify the validity of the obtained local certificate.
To request a certificate for a certificate subject in a PKI domain, perform the following tasks:
Configure the certificate subject.
Use the certificate subject in a PKI domain. In the PKI domain, configure the certificate enrollment settings such as the key pair for certificate request.
The public key of the key pair is sent along other information in the certificate request to the CA. The CA then signs the request and generates the requested certificate.
If you specify a nonexistent key pair in the PKI domain, the system automatically generates the key pair according to the key pair settings when generating the certificate request.
Generate a certificate request for the certificate subject in the PKI domain.
Submit the certificate request to the CA by using an out-of-band method, such as phone or email.
Certificate access control policy
Certificate access control policies allow you to authorize access to a device (for example, an HTTPS server) based on the attributes of an authenticated client's certificate.
A certificate access control policy is a set of permit or deny rules. Each rule contains a set of certificate attribute filters. A certificate attribute filter filters certificates based on an attribute in the certificate issuer name, subject name, or alternative subject name field. A certificate matches a rule if it matches all the certificate attribute filters in the rule.
The device matches a received certificate against the rules on the rule list of the certificate access policy from top to bottom. The match process stops once a matching rule is found.
If a certificate matches a permit rule, the certificate passes the verification.
If a certificate matches a deny rule or does not match any rules in the policy, the certificate is regarded invalid.
If the certificate access control policy specified for a security application (for example, HTTPS) does not exist, all certificates in the application pass the verification.
vSystem support information
Support of non-default vSystems for this feature depends on the device model. This feature is available on the Web interface only if it is supported.
Restrictions and guidelines
Whether the identity categories are required or optional depends on the CA policy. Follow the CA policy to configure the certificate subject settings.
The SCEP add-on on the Windows 2000 CA server has restrictions on the data length of a certificate request. If a request from a PKI entity exceeds the data length limit, the CA server does not respond to the certificate request. In this case, you can use an out-of-band means to submit the request. Other types of CA servers, such as RSA servers and OpenCA servers, do not have such restrictions.
Configure PKI
Configure a certificate subject
Click the
Objects tab.In the navigation pane, select
PKI >Certificate Subject .Click
Create .Create a certificate subject.
Figure-1
Certificate Subject page 
Figure-2 Creating a certificate subject
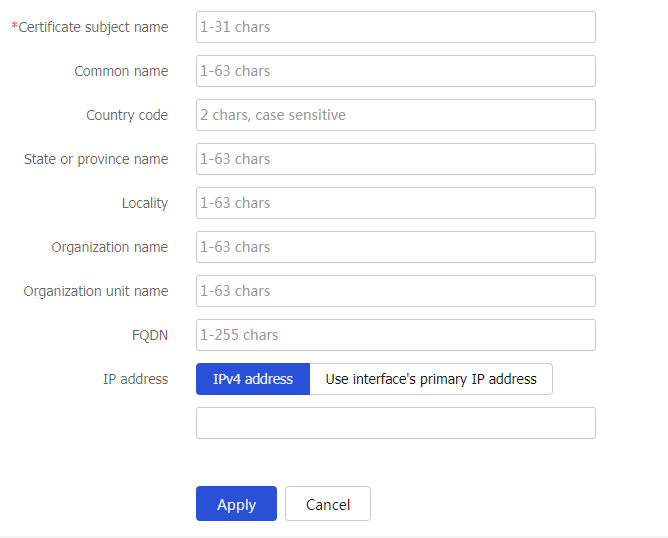
Table-1 Certificate subject configuration items
Item
Description
Certificate subject name
Name of certificate subject.
Common name
Common name of the PKI entity.
Country code
Country code of the PKI entity.
State or province name
State or province name of the PKI entity.
Locality
Locality information of the PKI entity.
Organization name
Name of the organization of the PKI entity.
Organization unit name
Name of the organization unit of the PKI entity.
FQDN
FQDN of the PKI entity.
IP address
IP address of the PKI entity. Options include:
IPv4 address.
Use interface's primary IP address.
Click
OK .
Configure a PKI domain
In a PKI domain, you can certificate subject related parameters, including CRL checking on certificate subject related certificates, certificate usage extensions, and key pairs for certificate requests.
To configure a PKI domain:
Click the
Objects tab.In the navigation pane, select
PKI >Certificate .Click
Create PKI Domain .Configure PKI domain parameters.
Figure-3
Certificate page 
Figure-4 Configuring PKI domain parameters
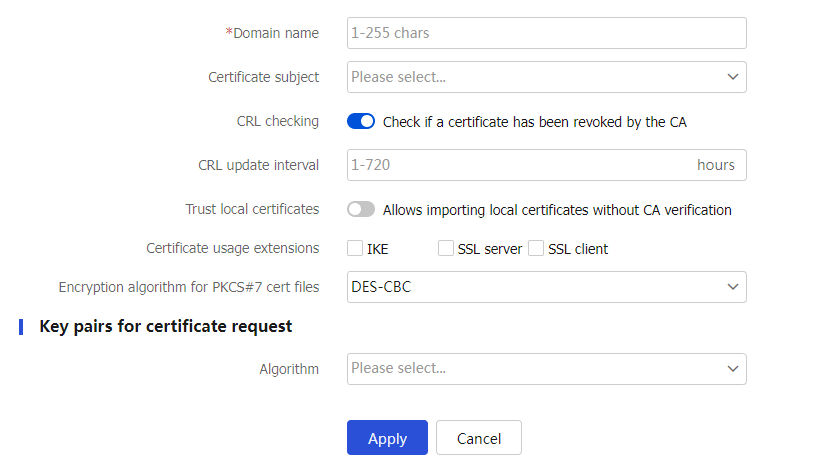
Table-2 PKI domain configuration items
Item
Description
Domain name
Name of a PKI domain.
Certificate subject
Select the certificate subject used to request certificates.
CRL checking
CRL checking checks whether a certificate is in the CRL. If it is, the certificate has been revoked and its home entity is not trusted.
CRL Repository URL
Enter the URL of the CRL repository. To use CRL checking, first obtain a CRL from a CRL repository.
The URL format is ldap://
server_location , http://server_location , or ftp://server_location , whereserver_location can be the IP address or domain name of the CRL repository server.CRL Repository Server Username
Enter the username used to log in to the CRL repository server.
If a username has been configured on a LDAP or FTP server, you must configure this parameter. For an HTTP server, you can leave this parameter blank.
CRL Repository Server Password
Enter the password used to log in to the CRL repository server.
If a password has been configured on a LDAP or FTP server, you must configure this parameter. For an HTTP server, you can leave this parameter blank.
CRL update interval
Specify a CRL update interval.
In scenarios that require strict certificate verification (such as bank systems), the device must be able to obtain the latest CRL in time. This feature enables the device to automatically connect to the CRL repository at the specified intervals to obtain the latest CRL.
Trust local certificates
After you select the
Allows importing local certificates without CA verification option, the device does not use a CA certificate to verify the local certificates to be imported.Certificate usage extensions
Specify the certificate extensions, including:
IKE.
SSL server.
SSL client.
Encryption algorithm for PKCS#7 cert files
Specify the encryption algorithm for encryption and decryption of certificate files in PKCS#7 format.
Make sure the specified encryption algorithm is supported on the CA server.
Algorithm
Algorithm used to request certificates. Options include:
RSA
DSA
ECDSA
SM2
Click
OK .
Import a certificate
Click the
Objects tab.In the navigation pane, select
PKI >Certificate .Click
Import certificate .Figure-5
Certificate page 
Configure the certificate import.
Figure-6 Certificate import
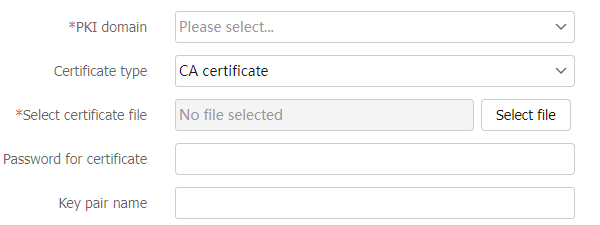
Table-3 Certificate import configuration items
Item
Description
PKI domain
Specify the PKI domain used to save the certificate.
Certificate type
Specify the certificate type, including CA certificate and local certificate.
Select certificate file
Select the certificate file to be imported.
Password for certificate
Enter the password for importing a local certificate that contains a key pair. You need to obtain the password from the CA server administrator.
Key pair name
To import the key pair together with the certificate to the PKI domain, enter the key pair name.
Click
OK .
Submit a certificate request
Click the
Objects tab.In the navigation pane, select
PKI >Certificate .Click
Submit cert request .Figure-7
Certificate page 
Configure the certificate request submit parameters.
Figure-8 Configuring certificate request submit parameters
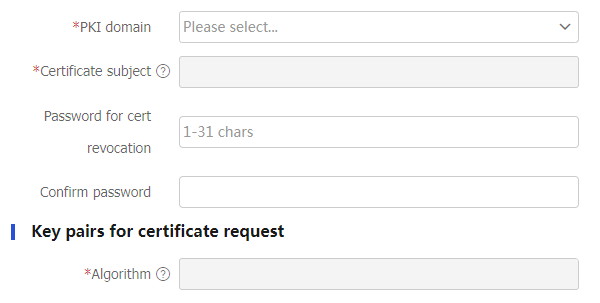
Table-4 Certificate request configuration items
Item
Description
PKI domain
Select a PKI domain for certificate request.
Certificate subject
Specify the certificate subject used for certificate request.
Algorithm
Specify the algorithm used for certificate request.
Password for cert revocation
Enter the password used to revoke a certificate.
Confirm password
Confirm the password used to revoke a certificate.
Click
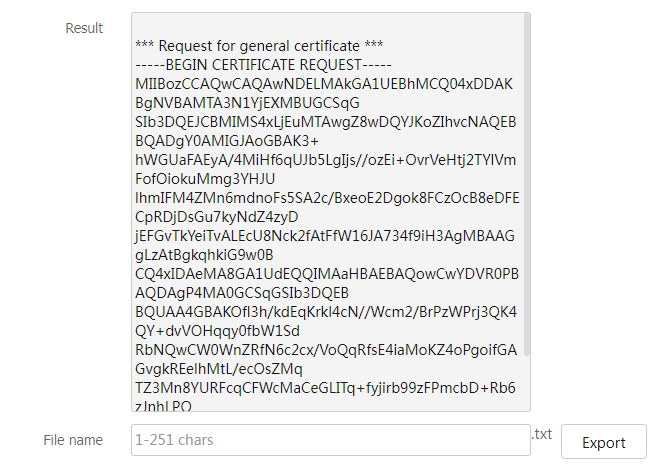
OK . The page will display certificate request information. To export the request file, enter the file name and clickExport . To copy the request information, copy it from theResult box.Figure-9 Request information
Configure a certificate access control policy
Certificate access control policies implement further access control of security application users to servers. For example, an HTTPS server can use a certificate access control policy to verify a client's certificate validity.
A certificate access control policy is a set of access control rules (with permit or deny action). A rule contains multiple attribute filters, each defining a matching criterion for an attribute in the certificate issuer name, subject name, or alternative subject name field.
If a certificate matches all attribute filters in a certificate access control rule, the system determines that the certificate matches the rule. If a certificate does not contain the attribute specified in an attribute filter or does not match an attribute filter, the certificate does not match the certificate access control rule.
Procedure
Click the
Objects tab.In the navigation pane, select
PKI >Certificate Access Control .Click
Create .Figure-10
Certificate Access Control page 
On the
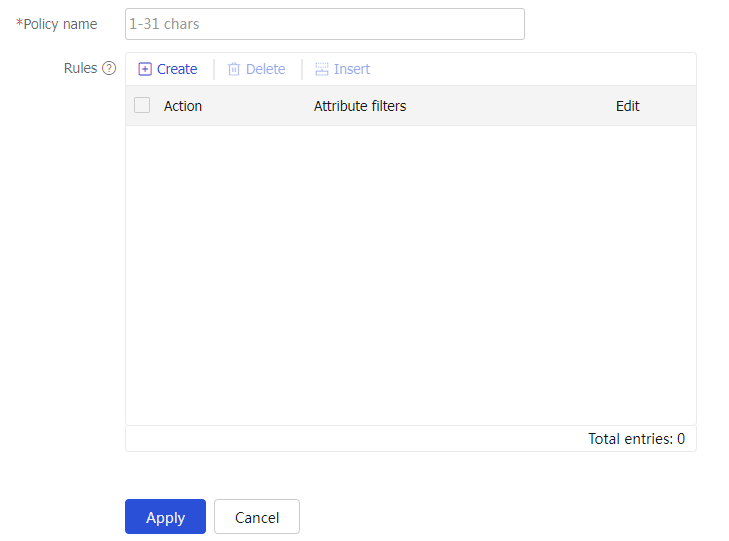
Create Certificate Access Control Policy page, configure the policy name.Figure-11 Configuring the policy name
Click
Create .On the
Create Rule page, configure the action of the rule as permit or deny.Figure-12 Creating a rule
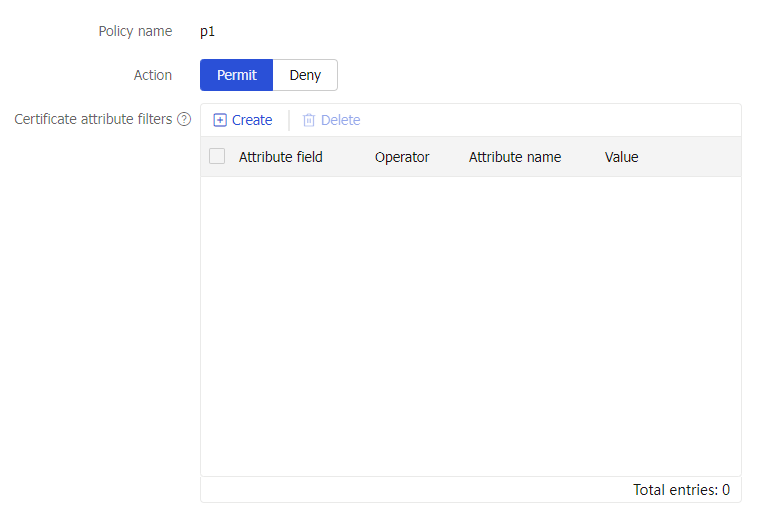
Click
Create to configure certificate attribute filters.Figure-13 Configuring certificate attribute filters
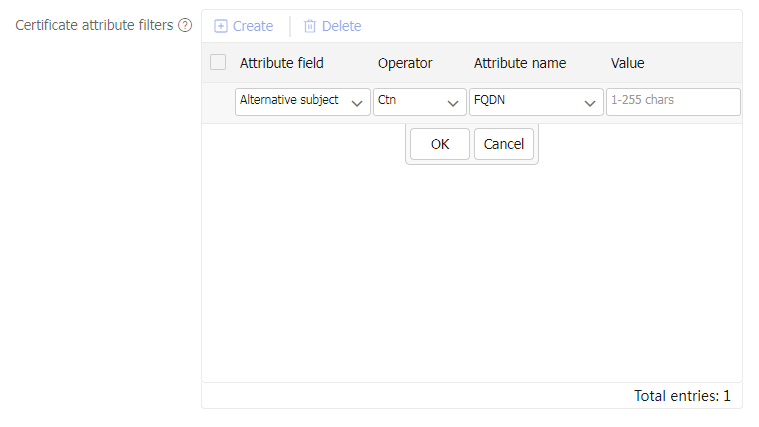
Table-5 Certificate attribute filter configuration items
Item
Description
Attribute field
Field of a certificate, which can be:
Alternative subject name.
Issuer name.
Certificate subject name.
Operator
Operator (matching condition) for the certificate attribute. Values include:
Ctn —Contain.Equ —Equal.N ctn —Not contain.Nequ —Not equal.
Attribute name
Name of the certificate attribute:
DN
FQDN
IP
Value
Value of the certificate attribute.
Assume that an attribute filter specifies the attribute field as the
Certificate subject name , the operator asCtn (contain), the attribute name asDN , and the value asab . If the value of the DN attribute in the subject name of a certificate containsab , the certificate matches the attribute filter.Click
OK to complete the attribute filter configuration.Click
OK to complete the rule configuration.Click
OK to complete configuration for the certificate access control policy.