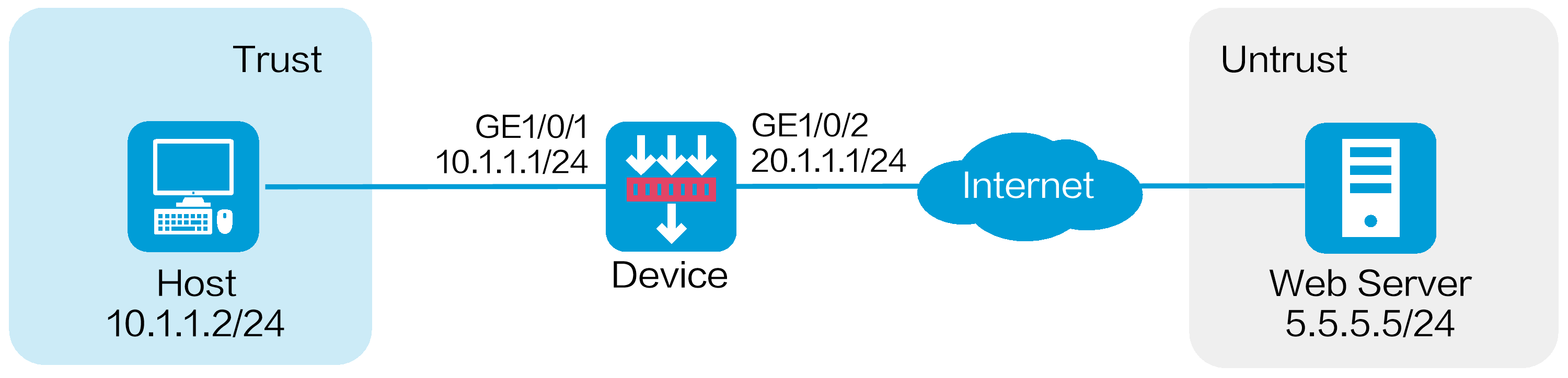
As shown in Figure 1, the device acts as the security gateway of the internal network. Configure the WAF feature on the device to protect the internal network against Web application attacks from the Internet.
This configuration example was created and verified on F9900 of the F5000-AI120 device.
The WAF feature requires a license to run on the device. After the license expires, WAF can use the existing WAF signature library on the device, but the library cannot be updated.
Assign IP addresses to interfaces:
# On the top navigation bar, click Network.
# From the navigation pane, select Interface Configuration > Interfaces.
# Click the Edit icon for GE 1/0/1.
# In the dialog box that opens, configure the interface:
Select the Trust security zone.
On the IPv4 Address tab, enter the IP address and mask length of the interface. In this example, enter 10.1.1.1/24.
Use the default settings for other parameters.
# Click OK.
# Add GE 1/0/2 to the Untrust security zone and set its IP address to 20.1.1.1./24 in the same way you configure GE 1/0/1.
Configure routing settings.
This example configures a static route. To use dynamic routing, configure dynamic routing protocols as required.
Configure the next hop IP address to reach the Web server in the external network according to the actual network conditions. In this example, the next hop IP address is 20.1.1.2.
To configure a static route:
# On the top navigation bar, click Network.
# From the navigation pane, select Routing > Static Routing.
# On the IPv4 Static Routing tab, click Create.
# In the dialog box that opens, configure a static IPv4 route to reach 0.0.0.0:
Enter destination IP address 5.5.5.0.
Enter mask length 24.
Enter next hop address 20.1.1.2.
Use the default settings for other parameters.
# Click OK.
Update the WAF signature library to the latest version. (Details not shown.)
Configure a WAF profile:
# On the top navigation bar, click Objects.
# From the navigation pane, select APPSecurity > WAF > Profiles.
# Click Create.
The Create WAF Profile dialog box opens.
# In the basic configuration area, configure the following parameters:
Enter name waf.
Set the action to drop.
Enable logging.
Use the default settings for other parameters.
Figure 2 Configuring the basic settings
# In the Signature filtering criteria area, perform the following settings:
Select All for the protected targets.
Select All for the attack categories.
Set To-server and To-client for the direction.
Set the default actions to drop, permit, reset, and blacklist.
Set the severity levels to critical, high, medium, and low.
Figure 3 Signature filtering criteria configuration
# Click OK.
Create security policies:
# On the top navigation bar, click Policies.
# From the navigation pane, select Security Policies > Security Policies.
# Click Create, and then click Create a policy.
# In the dialog box that opens, configure a security policy named untrust-trust to permit the specified traffic from the Untrust to Trust security zones:
Enter policy name untrust-trust.
Select source zone Untrust.
Select destination zone Trust.
Select type IPv4.
Select action Permit.
Select destination IP address 10.1.1.0/24.
Select WAF profile waf in the Content security area.
Use the default settings for other parameters.
# Click OK.
# Create security policy trust-untrust to permit the specified traffic from the Trust to Untrust security zones:
Enter policy name trust-untrust.
Select source zone Trust.
Select destination zone Untrust.
Select type IPv4.
Select action Permit.
Select source IP addresses 10.1.1.0/24.
Select WAF profile waf in the Content security area.
Use the default settings for other parameters.
# Click OK.
Activate the settings on the Security Policies page:
# After you apply the WAF profile to the security policy, click Submit (the second Submit in Figure 4) to have the content security configuration take effect.
# Click Activate (the first Submit in Figure 4) to activate security policy matching acceleration.
Figure 4 Activate security policy settings
Enable logging:
# On the top navigation bar, click System.
# From the navigation pane, select Log Settings > Basic Settings.
# Click the Storage Space Settings tab.
# Edit the storage space settings for the WAF service and enable logging for the service.
Verify that WAF can protect the internal network from known Web application layer attacks.
To view the logs generated for these events, click Monitor on the top navigation bar, and then select Security Logs > Threat Logs > WAF Logs from the navigation pane.