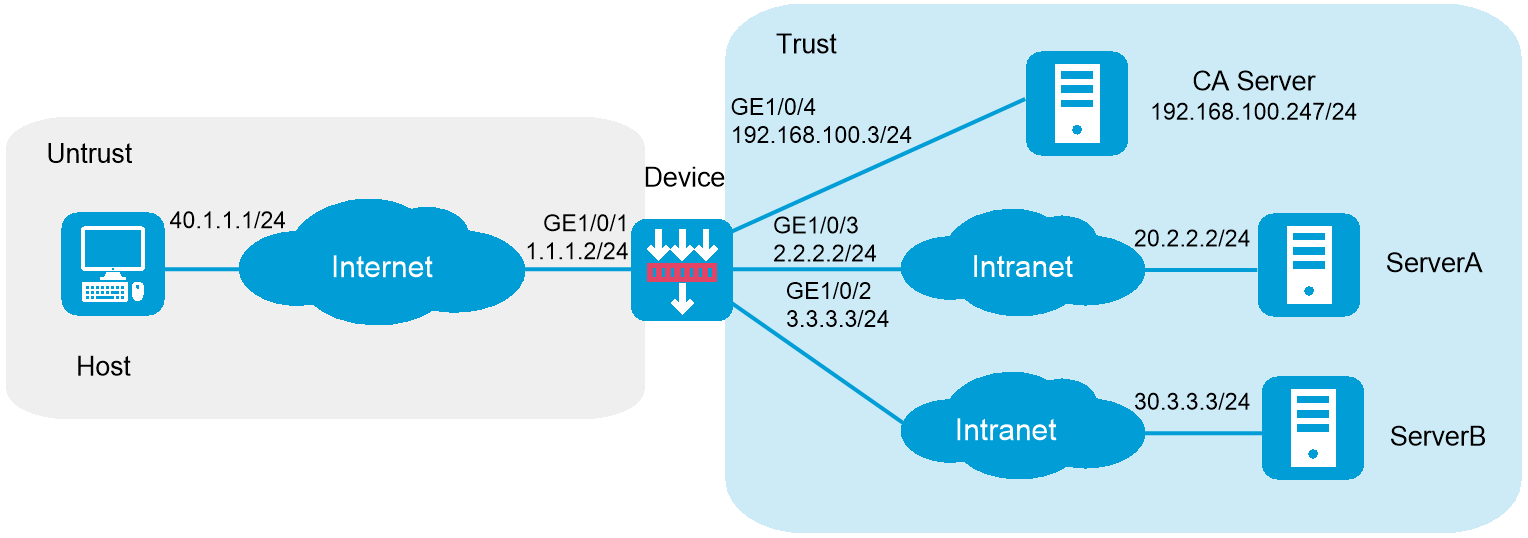
As shown in Figure 1, the device acts as the SSL VPN gateway that connects the public network and the private network. A Windows Server 2008 R2 CA server is deployed on the private network. Users need to access resources on internal Web servers Server A and Server B. Both Web servers use HTTP over port 80.
Configure the SSL VPN Web access service on the device to allow users to access Server A and Server B in Web access mode.
Configure the device to perform local authentication and authorization for Web access users. Require users to pass both password and certificate authentication for Web access. To enhance security, request an SSL server certificate for the device from the CA server rather than use the default certificate.
This configuration example was created and verified on F9900 of the F5000-AI120 device.
Assign IP addresses to interfaces and add the interfaces to security zones.
# On the top navigation bar, click the Network tab.
# From the navigation pane, select Interface Configuration > Interfaces.
# Click the Edit icon for GE 1/0/1.
# In the dialog box that opens, configure the interface:
Select the Untrust security zone.
On the IPv4 Address tab, enter the IP address and mask length of the interface. In this example, enter 1.1.1.2/24.
Use the default settings for other parameters.
Click OK.
# Add GE 1/0/2 to the Trust security zone and set its IP address to 3.3.3.3/24 in the same way you configure GE 1/0/1.
# Add GE 1/0/3 to the Trust security zone and set its IP address to 2.2.2.2/24 in the same way you configure GE 1/0/1.
# Add GE 1/0/4 to the Trust security zone and set its IP address to 192.168.100.3/24 in the same way you configure GE 1/0/1.
Configure settings for routing:
This example configures static routes.
# On the top navigation bar, click Network.
# From the navigation pane, select Routing > Static Routing.
# On the IPv4 Static Routing tab, click Create.
# In the dialog box that opens, configure a static IPv4 route to reach 40.1.1.1:
Enter destination IP address 40.1.1.1.
Enter mask length 24.
Enter next hop address 1.1.1.3.
Use the default settings for other parameters.
Click OK.
# Configure a static IPv4 route to reach 20.2.2.2:
Enter destination IP address 20.2.2.2.
Enter mask length 24.
Enter next hop address 2.2.2.3.
Use the default settings for other parameters.
Click OK.
# Configure a static IPv4 route to reach 30.3.3.3:
Enter destination IP address 30.3.3.3.
Enter mask length 24.
Enter next hop address 3.3.3.4.
Use the default settings for other parameters.
Click OK.
Create security policies:
# On the top navigation bar, click Policies.
# From the navigation pane, select Security Policies > Security Policies.
# Click Create.
# In the dialog box that opens, configure a security policy named untrust-local to permit the specified traffic from the Untrust to Local security zones:
Enter policy name untrust-local.
Select source zone Untrust.
Select destination zone Local.
Select type IPv4.
Select action Permit.
Select source IPv4 address 40.1.1.1.
Select destination IPv4 address 1.1.1.2.
Use the default settings for other parameters.
# Click OK.
# Create security policy local-trust to permit the specified traffic from the Local to Trust security zones:
Enter policy name local-trust.
Select source zone Local.
Select destination zone Trust.
Select type IPv4.
Select action Permit.
Select source IPv4 addresses 2.2.2.2, 3.3.3.3, and 192.168.100.3.
Select destination IPv4 addresses 20.2.2.2, 30.3.3.3, and 192.168.100.247.
Use the default settings for other parameters.
# Click OK.
Request a server certificate for the device:
Create a certificate subject:
# On the top navigation bar, click Objects.
# From the navigation pane, select PublicKey Cert > PKI > Certificate Subject.
# Click Create.
# Create a certificate subject as shown in Figure 2, and the click Apply.
Figure 2 Creating a certificate subject
Create a PKI domain:
# On the Certificate page, click Create PKI domain.
# Create a PKI domain as shown in Figure 3, and then click OK.
Figure 3 Creating a PKI domain
Create a certificate request:
# On the Certificate page, click Submit Cert Request.
# Configure the certificate request settings as shown in Figure 4.
Figure 4 Creating a certificate request
# Click OK.
The certificate request content will be displayed, as shown in Figure 5.
Figure 5 Certificate request content
# Copy the certificate request content and click OK. In this example, a Windows Server 2008 R2 CA server is used.
Request a server certificate from the CA:
# Enter http://192.168.100.247/certsrv in the browser address bar.
# On the certificate service home page shown in Figure 6, click Request a certificate.
Figure 6 Certificate service home page
# On the Request a Certificate page shown in Figure 7, click advanced certificate request.
Figure 7 Request a Certificate page
# Paste the previously copied certificate request content in the Base-64-encoded certificate request CMC or PKCS # 10 or PKCS # 7) field, as shown in Figure 8.
Figure 8 Pasting the certificate request content
# Click Submit.
After the certificate request is approved by the CA administrator, enter http://192.168.100.247/certsrv in the browser address bar.
# On the certificate service home page shown in Figure 9, click View the status of a pending certificate request.
Figure 9 Certificate service home page
# Select the certificate request you want to view.
Figure 10 View the Status of a Pending Certificate Request page
The Certificate Issued page opens, indicating that the requested server certificate has been issued, as shown in Figure 11.
Figure 11 Certificate Issued page
# Click Download certificate to download the server certificate and save it locally.
Download the CA certificate:
# Enter http://192.168.100.247/certsrv in the browser address bar.
# On the certificate service home page shown in Figure 12, click Download a CA certificate, certificate chain, or CRL.
Figure 12 Certificate service home page
# On the Download a CA certificate, certificate chain, or CRL page shown in Figure 13, click Download CA certificate.
Figure 13 Download a CA certificate, certificate chain, or CRL page
# Save the downloaded CA certificate locally.
Import the CA certificate and server certificate to the PKI domain:
Import the CA certificate:
# On the top navigation bar, click Objects.
# From the navigation pane, select PublicKey Cert > PKI > Certificate.
# Click Import certificate.
# Import the locally saved CA certificate, as shown in Figure 14, and then click OK.
Figure 14 Importing the CA certificate
Import the server certificate:
# On the Certificate page, click Import certificate.
# Import the locally saved server certificate, as shown in Figure 15, and then click OK.
Figure 15 Importing the server certificate
Configure an SSL server policy:
# On the top navigation bar, click Objects.
# From the navigation pane, select SSL > SSL Server Policies.
# Click Create.
# Configure an SSL server policy as shown in Figure 16, and then click OK.
Figure 16 Creating an SSL server policy
Configure the SSL VPN gateway:
# On the top navigation bar, click Network.
# From the navigation pane, select VPN > SSL VPN > SSL VPN Gateways.
# Click Create.
# Create an SSL VPN gateway as shown in Figure 17, and then click OK.
Figure 17 Creating an SSL VPN gateway
Configure an SSL VPN context:
# On the top navigation bar, click Network.
# From the navigation pane, select VPN > SSL VPN > SSL VPN Contexts.
# Click Create.
# Configure the basic settings for the SSL VPN context as shown in Figure 3, and then click Next.
Figure 18 Configuring basic settings for an SSL VPN context
# Enable Web proxy, select SSL client policy sslvpnclient, and configure Web access resources, as shown in Figure 19. Then, click Next.
Figure 19 Configuring Web access resources
# Create a resource group named resourcegrp, as shown in Figure 21.
Figure 20 Creating an SSL VPN resource group
# Click Apply,
The newly created resource group is displayed on the Resource groups area, as shown in Figure 22.
Figure 21 Resource groups configuration page
# Click Next to configure authentication settings, as shown in Figure 22.
Figure 22 Configuring authentication settings
# Click Finish.
Create an SSL VPN user:
# On the top navigation bar, click Objects.
# From the navigation pane, select User > User Management > Local Users.
# Click Create.
# Create an SSL VPN user, as shown in Figure 24.
Figure 23 Creating an SSL VPN user
# Authorize the user to use SSL VPN resource group resourcegrp, as shown in Figure 24.
Figure 24 Configuring authorization attributes
# Click OK.
Configure the IP address and gateway address settings for the host and make sure it can reach the SSL VPN gateway and the CA server.
Submit a client certificate request to the CA server:
# Enter http://192.168.100.247/certsrv in the browser address bar.
# On the certificate service home page shown in Figure 26, click Request a certificate.
Figure 25 Certificate service home page
# On the Request a Certificate page shown in Figure 27, click advanced certificate request.
Figure 26 Request a Certificate page
# Create a client certificate request, as shown in Figure 28.
Figure 27 Creating a client certificate request
# Use the default settings for other parameters and click Submit.
Install the client certificate on the host:
# After the certificate request is approved by the CA administrator, enter http://192.168.100.247/certsrv in the browser address bar.
# On the certificate service home page shown in Figure 29, click View the status of a pending certificate request.
Figure 28 Certificate service home page
The View the Status of a Pending Certificate Request page opens, as shown in Figure 30.
Figure 29 View the Status of a Pending Certificate Request page
# Click the client certificate whose status you want to view.
# On the Certificate Issued page shown in Figure 31, click Install this certificate to install the client certificate. If the host does not have a CA certificate, the page shown in Figure 32 opens. You must install the CA certificate first.
Figure 30 Installing the client certificate
# To install the CA certificate, click install this CA certificate. Then, click Install this certificate to install the client certificate.
Figure 31 Installing the CA certificate and then the client certificate
After the client certificate is installed, the Certificate Installed page shown in Figure 33 opens.
Figure 32 Certificate Installed page
In the browser address bar of the host, enter https://1.1.1.2:2000 and press Enter.
Select the client certificate for authentication and click OK.
Click domainweb to go to the SSL VPN login page, and then enter username user1 and password 123456.
Click Login.
The SSL VPN home page opens, displaying the Web resources the user can access in the BookMark area, as shown in Figure 37.
Figure 34 Accessible Web resources
Click ServerA to access Web resources on Server A.
Click ServerB to access Web resources on Server B.