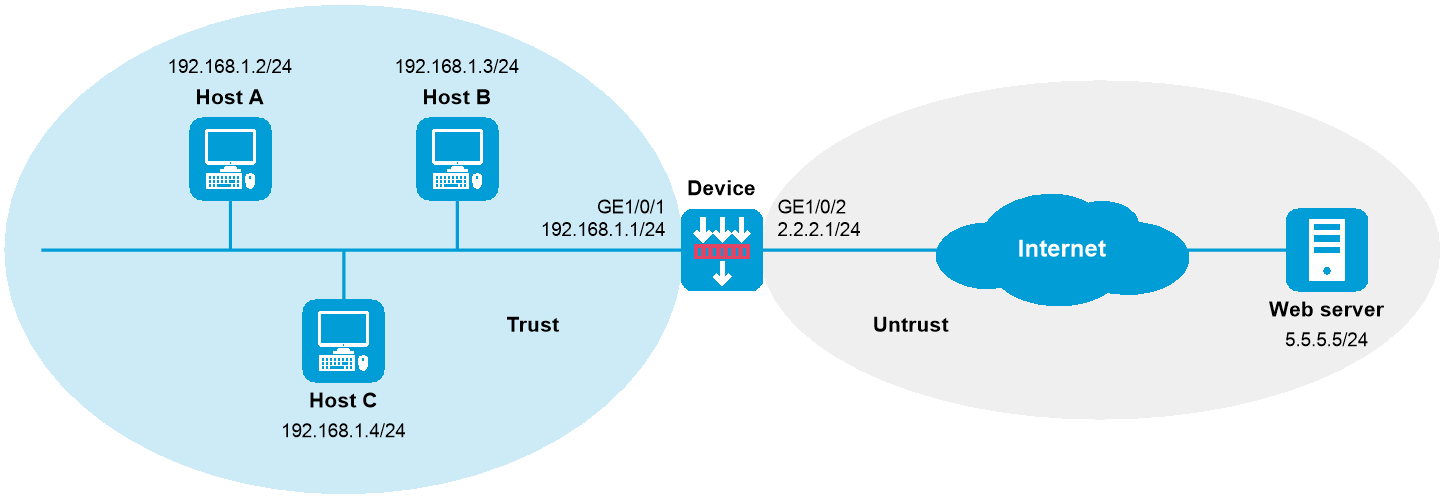
As shown in Figure 1, the device connects the LAN and the Internet. The LAN resides in security zone Trust and the Internet resides in security zone Untrust.
Configure the device to decrypt the HTTPS traffic and perform deep packet inspection on the traffic.
This configuration example was created and verified on F9900 of the F5000-AI120 device.
1. Assign IP addresses to interfaces:
# Assign an IP address to interface GigabitEthernet 1/0/1.
<Device> system-view
[Device] interface gigabitethernet 1/0/1
[Device-GigabitEthernet1/0/1] ip address 192.168.1.1 255.255.255.0
[Device-GigabitEthernet1/0/1] quit
# Assign IP addresses to other interfaces in the same way. (Details not shown.)
2. Configure settings for routing.
This example configures static routes, and the next hop in the routes is 2.2.2.2.
[Device] ip route-static 5.5.5.0 24 2.2.2.2
3. Add interfaces to security zones.
[Device] security-zone name trust
[Device-security-zone-Trust] import interface gigabitethernet 1/0/1
[Device-security-zone-Trust] quit
[Device] security-zone name untrust
[Device-security-zone-Untrust] import interface gigabitethernet 1/0/2
[Device-security-zone-Untrust] quit
4. Create an IP address object group named obj1 and configure an IP address object with subnet 192.168.1.0/24.
[Device] object-group ip address obj1
[Device-obj-grp-ip-obj1] network subnet 192.168.1.0 24
[Device-obj-grp-ip-obj1] quit
5. Import CA certificate trust.pem as a trusted SSL decryption certificate and CA certificate untrust.pem as an untrusted SSL decryption certificate to the device.
[Device] app-proxy ssl-decrypt-certificate import trust pem filename trust.pem
[Device] app-proxy ssl-decrypt-certificate import untrust pem filename untrust.pem
6. Install CA certificate trust.pem on all internal hosts and set the CA certificate trust.pem as a trusted SSL decryption certificate. (Details not shown.)
7. Create proxy policy rule https to match HTTPS traffic from internal hosts destined for the Web server and set the action for traffic matching rule https to SSL decryption.
[Device] app-proxy-policy
[Device-app-proxy-policy] rule 1 name https
[Device-app-proxy-policy-rule-1-https] source-zone trust
[Device-app-proxy-policy-rule-1-https] destination-zone untrust
[Device-app-proxy-policy-rule-1-https] source-ip object-group obj1
[Device-app-proxy-policy-rule-1-https] service object-group https
[Device-app-proxy-policy-rule-1-https] action ssl-decrypt
[Device-app-proxy-policy-rule-1-https] quit
[Device-app-proxy-policy] quit
8. Configure URL filtering:
# Create user-defined URL category https, set its severity level to 1001, and create URL filtering rule 1 to match HTTPS packets that contain host name www. baidu.com in the URL.
[Device] url-filter category https severity 1001
[Device-url-filter-category-https] rule host text www.baidu.com
[Device-url-filter-category-https] quit
# Create a URL filtering policy named p1. Specify action drop for URL category https, enable logging for the matching packets.
[Device] url-filter policy p1
[Device-url-filter-policy-p1] category https action reset logging
[Device-url-filter-policy-p1] quit
9. Apply URL filtering policy p1 to a DPI application profile and activate the URL filtering policy settings:
# Create a DPI application profile named sec, and apply URL filtering policy p1 to the DPI application profile.
[Device] app-profile sec
[Device-app-profile-sec] url-filter apply policy p1
[Device-app-profile-sec] quit
# Activate the URL filtering policy and rule settings.
[Device] inspect activate
10. Configure a security policy:
# Create a security policy rule named trust-untrust to permit the packets from security zone Trust to security zone Untrust and to perform URL filtering on the packets.
[Device] security-policy ip
[Device-security-policy-ip] rule name trust-untrust
[Device-security-policy-ip-10-trust-untrust] source-zone trust
[Device-security-policy-ip-10-trust-untrust] source-ip-subnet 192.168.1.0 24
[Device-security-policy-ip-10-trust-untrust] destination-zone untrust
[Device-security-policy-ip-10-trust-untrust] action pass
[Device-security-policy-ip-10-trust-untrust] profile sec
[Device-security-policy-ip-10-trust-untrust] quit
# Create a security policy rule named untrust-trust to permit the packets from security zone Untrust to security zone Trust.
[Device] security-policy ip
[Device-security-policy-ip] rule name untrust-trust
[Device-security-policy-ip-11-untrust-trust] source-zone untrust
[Device-security-policy-ip-11-untrust-trust] destination-zone trust
[Device-security-policy-ip-11-untrust-trust] destination-ip-subnet 192.168.1.0 24
[Device-security-policy-ip-11-untrust-trust] action pass
[Device-security-policy-ip-11-untrust-trust] profile sec
[Device-security-policy-ip-11-untrust-trust] quit
# Create two security policy rules named proxyserverlocalin and proxyserverlocalout to permit the traffic between the Trust and Local security zones. Thus, the device can proxy the traffic from internal hosts destined for the Web server.
[Device-security-policy-ip] rule name proxyserverlocalin
[Device-security-policy-ip-12-proxyserverlocalin] source-zone trust
[Device-security-policy-ip-12-proxyserverlocalin] source-ip-subnet 192.168.1.0 24
[Device-security-policy-ip-12-proxyserverlocalin] destination-zone local
[Device-security-policy-ip-12-proxyserverlocalin] action pass
[Device-security-policy-ip-12-proxyserverlocalin] quit
[Device-security-policy-ip] rule name proxyserverlocalout
[Device-security-policy-ip-13-proxyserverlocalout] source-zone local
[Device-security-policy-ip-13-proxyserverlocalout] destination-zone trust
[Device-security-policy-ip-13-proxyserverlocalout] destination-ip-subnet 192.168.1.0 24
[Device-security-policy-ip-13-proxyserverlocalout] action pass
[Device-security-policy-ip-13-proxyserverlocalout] quit
# Create two security policy rules named proxyclientlocalin and proxyclientlocalout to permit the traffic between the Untrust and Local security zones. Thus, the device can proxy the traffic from the Web server destined for internal hosts.
[Device-security-policy-ip] rule name proxyclientlocalin
[Device-security-policy-ip-14-proxyclientlocalin] source-zone untrust
[Device-security-policy-ip-14-proxyclientlocalin] destination-zone local
[Device-security-policy-ip-14-proxyclientlocalin] destination-ip-subnet 192.168.1.0 24
[Device-security-policy-ip-14-proxyclientlocalin] action pass
[Device-security-policy-ip-14-proxyclientlocalin] quit
[Device-security-policy-ip] rule name proxyclientlocalout
[Device-security-policy-ip-15-proxyclientlocalout] source-zone local
[Device-security-policy-ip-15-proxyclientlocalout] source-ip-subnet 192.168.1.0 24
[Device-security-policy-ip-15-proxyclientlocalout] destination-zone untrust
[Device-security-policy-ip-15-proxyclientlocalout] action pass
[Device-security-policy-ip-15-proxyclientlocalout] quit
# Activate rule matching acceleration.
[Device-security-policy-ip] accelerate enhanced enable
[Device-security-policy-ip] quit
Verify that the device can deny HTTPS requests to www.baidu.com and generate logs. You can also execute the display app-proxy server-certificate command to view the following information:
SSL server certificates received by the device as the SSL proxy client.
Number of times connections to the server had been proxied.
Most recent time the device proxied a connection to the server.
First time the device proxied a connection to the server.
#
object-group ip address obj1
0 network subnet 192.168.1.0 255.255.255.0
#
app-proxy ssl-decrypt-certificate import trust pem filename trust.pem
app-proxy ssl-decrypt-certificate import untrust pem filename untrust.pem
#
interface GigabitEthernet1/0/1
ip address 192.168.1.1 255.255.255.0
#
interface GigabitEthernet1/0/2
ip address 2.2.2.1 255.255.255.0
#
security-zone name Trust
import interface GigabitEthernet1/0/1
#
security-zone name Untrust
import interface GigabitEthernet1/0/2
#
ip route-static 5.5.5.0 24 2.2.2.2
#
url-filter policy p1
category https action reset logging
#
url-filter category https severity 1001
rule 1 host text www.baidu.com
#
app-profile sec
url-filter apply policy p1
#
inspect activate
#
app-proxy-policy
rule 1 name https
source-ip object-group obj1
service object-group https
source-zone trust
destination-zone untrust
action ssl-decrypt
#
security-policy ip
accelerate enhanced enable
rule 0 name trust-untrust
action pass
profile sec
source-zone trust
destination-zone untrust
source-ip-subnet 192.168.1.0 255.255.255.0
rule 1 name untrust-trust
action pass
profile sec
source-zone untrust
destination-zone trust
destination-ip-subnet 192.168.1.0 255.255.255.0
rule 2 name proxyserverlocalin
action pass
source-zone trust
destination-zone local
source-ip-subnet 192.168.1.0 255.255.255.0
rule 3 name proxyserverlocalout
action pass
source-zone local
destination-zone trust
destination-ip-subnet 192.168.1.0 255.255.255.0
rule 4 name proxyclientlocalin
action pass
source-zone untrust
destination-zone local
destination-ip-subnet 192.168.1.0 255.255.255.0
rule 5 name proxyclientlocalout
action pass
source-zone local
destination-zone untrust
source-ip-subnet 192.168.1.0 255.255.255.0